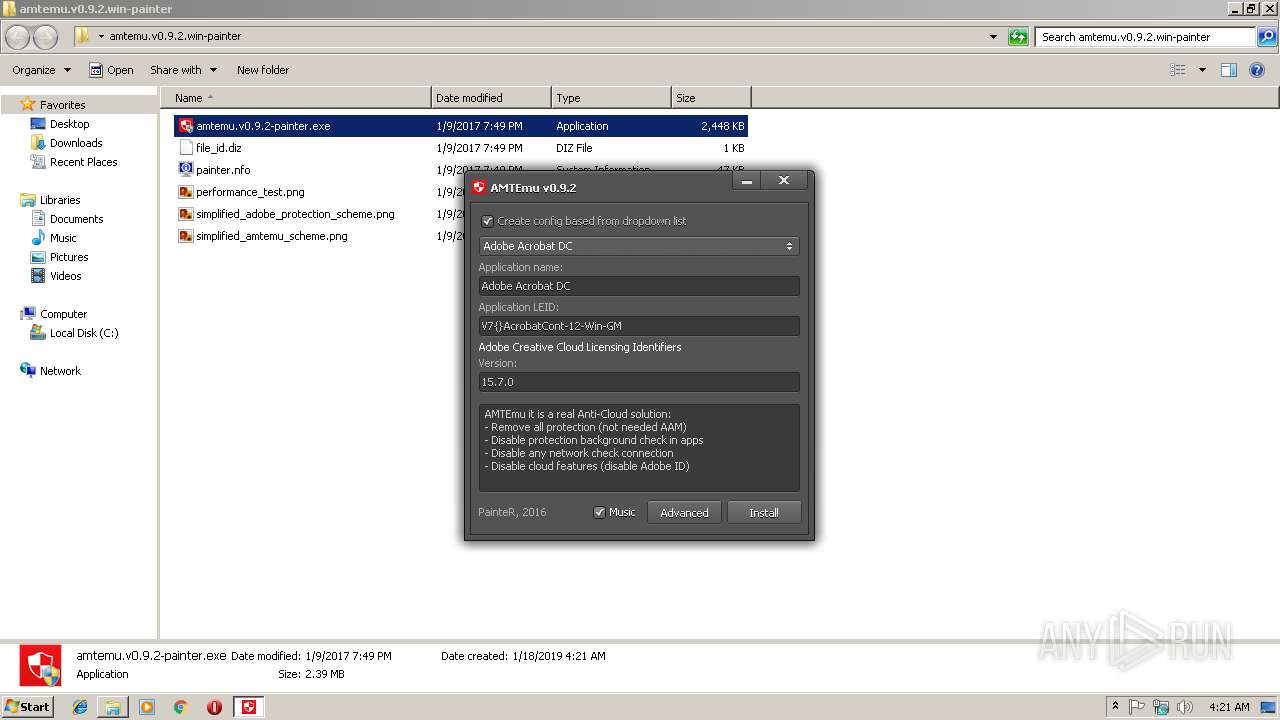
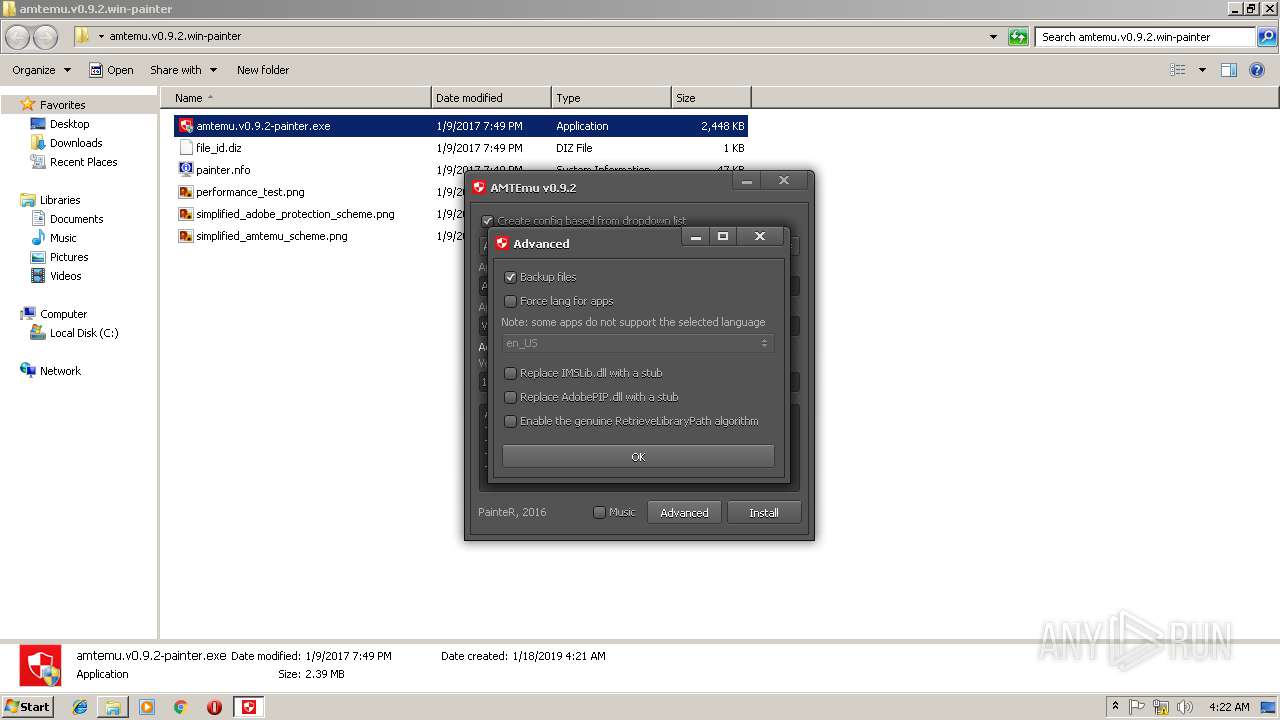
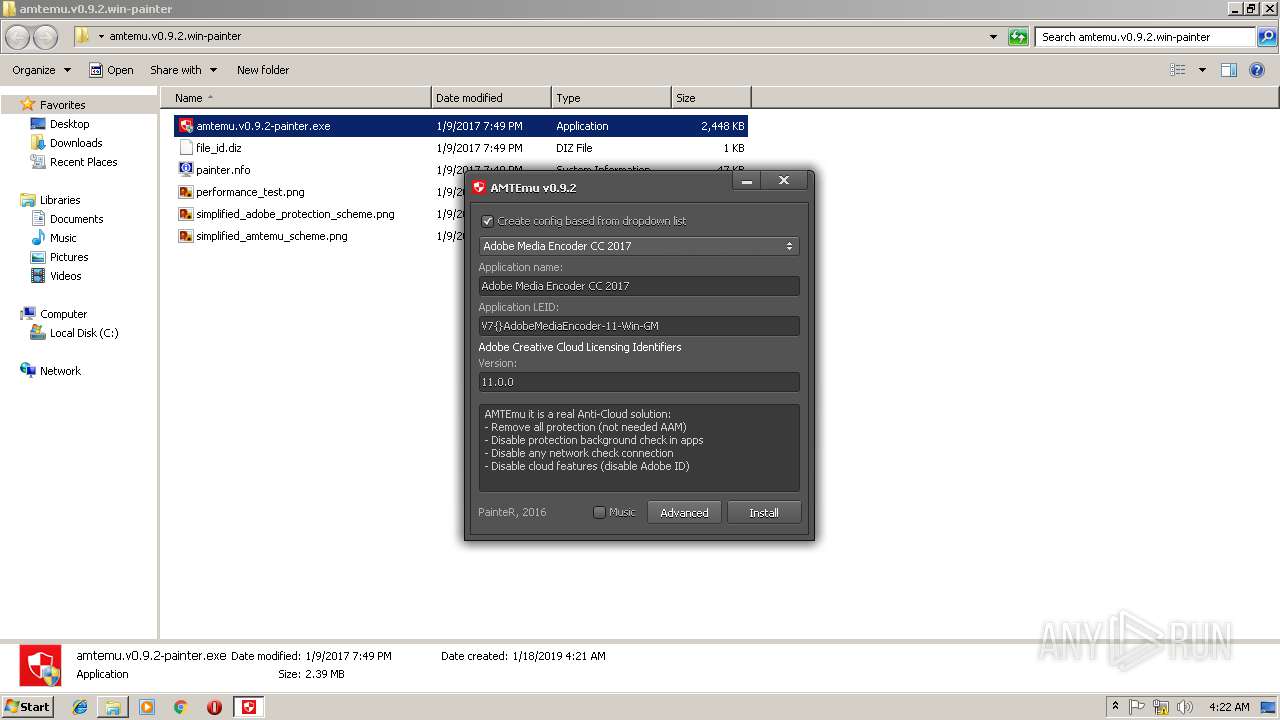
| File name: | pconline1483962590187.zip |
| Full analysis: | https://app.any.run/tasks/fc4e8eeb-c1a1-4ad6-aee8-d027c3aae825 |
| Verdict: | Malicious activity |
| Analysis date: | January 18, 2019, 04:20:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 111301F57B606DE96054DEBF920ACECF |
| SHA1: | AF13269BCDE334C48DEC7D433F4D1B56CEBFDFD4 |
| SHA256: | BC67DA564F8AC347519E5F57F0D635F8AD8C934180F9B5D49EFF9DA10302E2F3 |
| SSDEEP: | 24576:xf+ahmj8MGz2EvnopBP3vdxCej6qgr/Ru6Yi8/x1tD/jxW32JnadXZWNJ0WNyjVW:dNgTPvLrtg7Ru6jWPXi04XaJxsjyz |
MALICIOUS
Loads dropped or rewritten executable
- amtemu.v0.9.2-painter.exe (PID: 3216)
SUSPICIOUS
Executable content was dropped or overwritten
- amtemu.v0.9.2-painter.exe (PID: 3216)
INFO
Application launched itself
- chrome.exe (PID: 2072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2017:01:09 19:49:25 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | amtemu.v0.9.2.win-painter/ |
Total processes
51
Monitored processes
17
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1036 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=912,5786413451813299152,12196097477579485913,131072 --enable-features=PasswordImport --service-pipe-token=EBC9BB28733C8CC926ADF457ABE921D4 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=EBC9BB28733C8CC926ADF457ABE921D4 --renderer-client-id=5 --mojo-platform-channel-handle=1868 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2052 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=912,5786413451813299152,12196097477579485913,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=F7EBA077E3814C43B328F4DEB42D8318 --mojo-platform-channel-handle=4468 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2072 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2312 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=912,5786413451813299152,12196097477579485913,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=0AABA2CC38CB75D0CDCDD7966978F41B --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=0AABA2CC38CB75D0CDCDD7966978F41B --renderer-client-id=11 --mojo-platform-channel-handle=2072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2576 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=912,5786413451813299152,12196097477579485913,131072 --enable-features=PasswordImport --service-pipe-token=C9E90BA2698ABEC081CAA1C6157153B1 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=C9E90BA2698ABEC081CAA1C6157153B1 --renderer-client-id=3 --mojo-platform-channel-handle=2032 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2596 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2804 --on-initialized-event-handle=304 --parent-handle=308 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2720 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=912,5786413451813299152,12196097477579485913,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=EBD943217C2852843270D796B310A081 --mojo-platform-channel-handle=1864 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
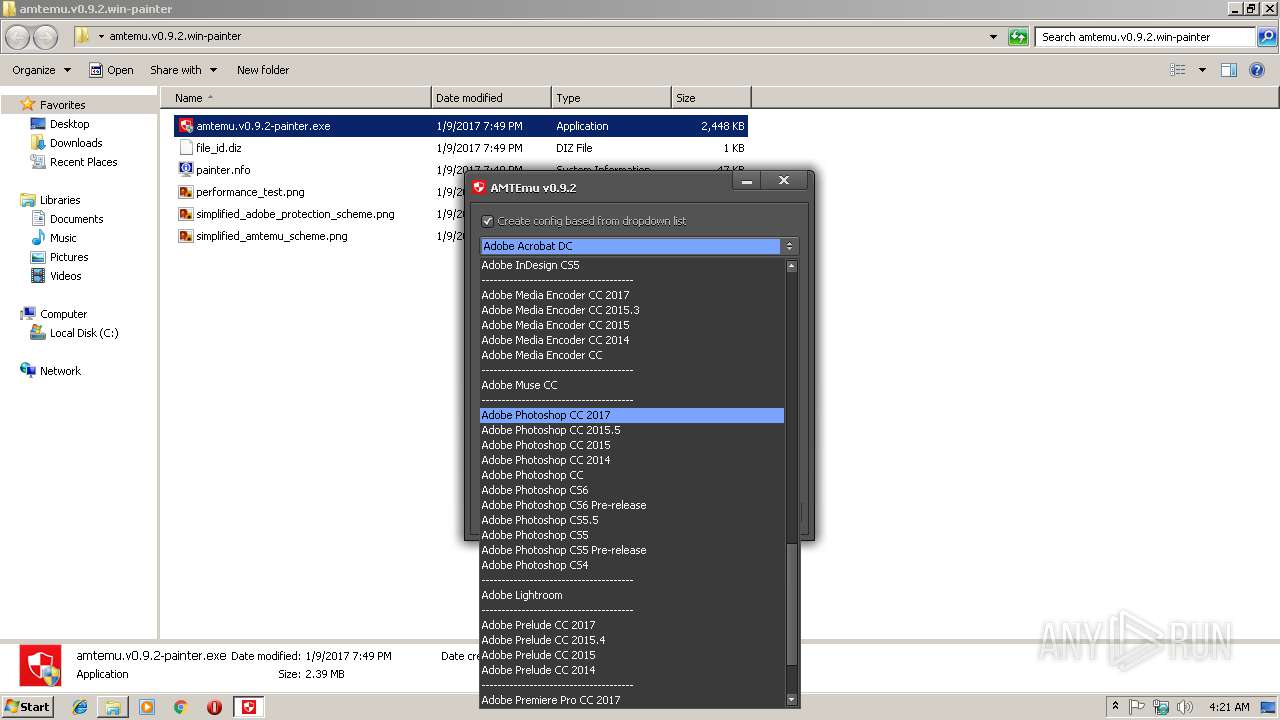
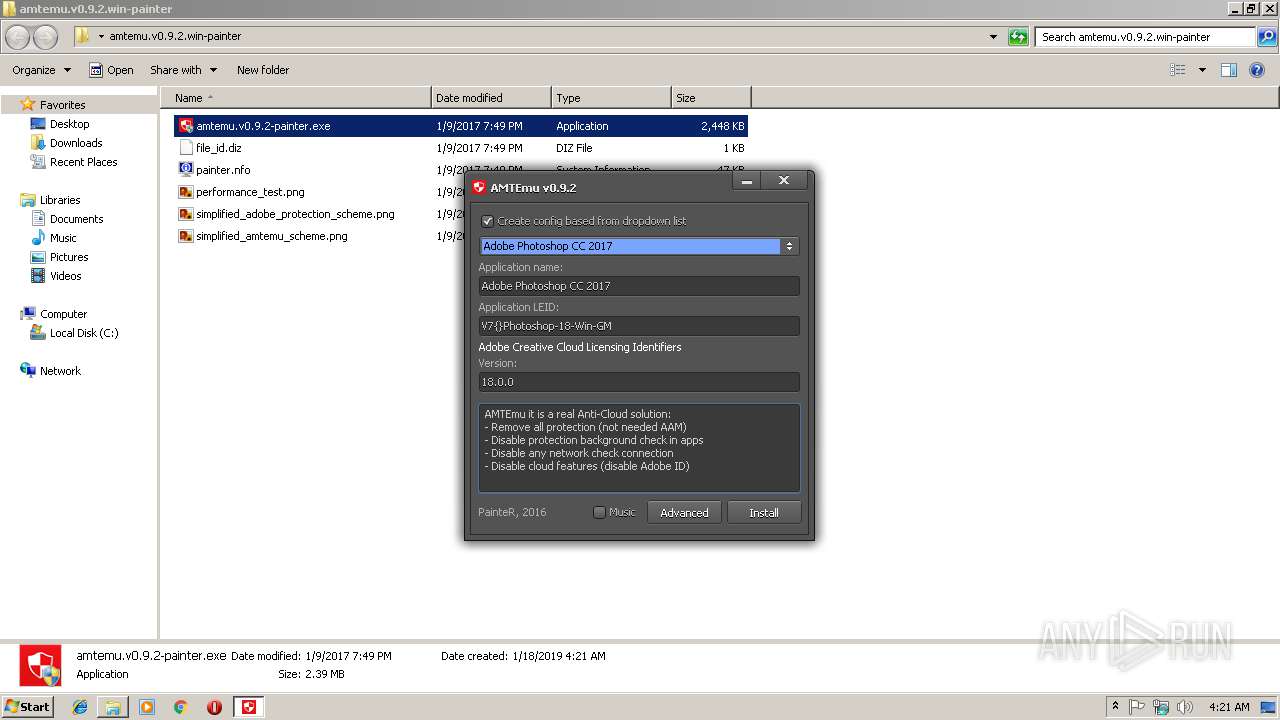
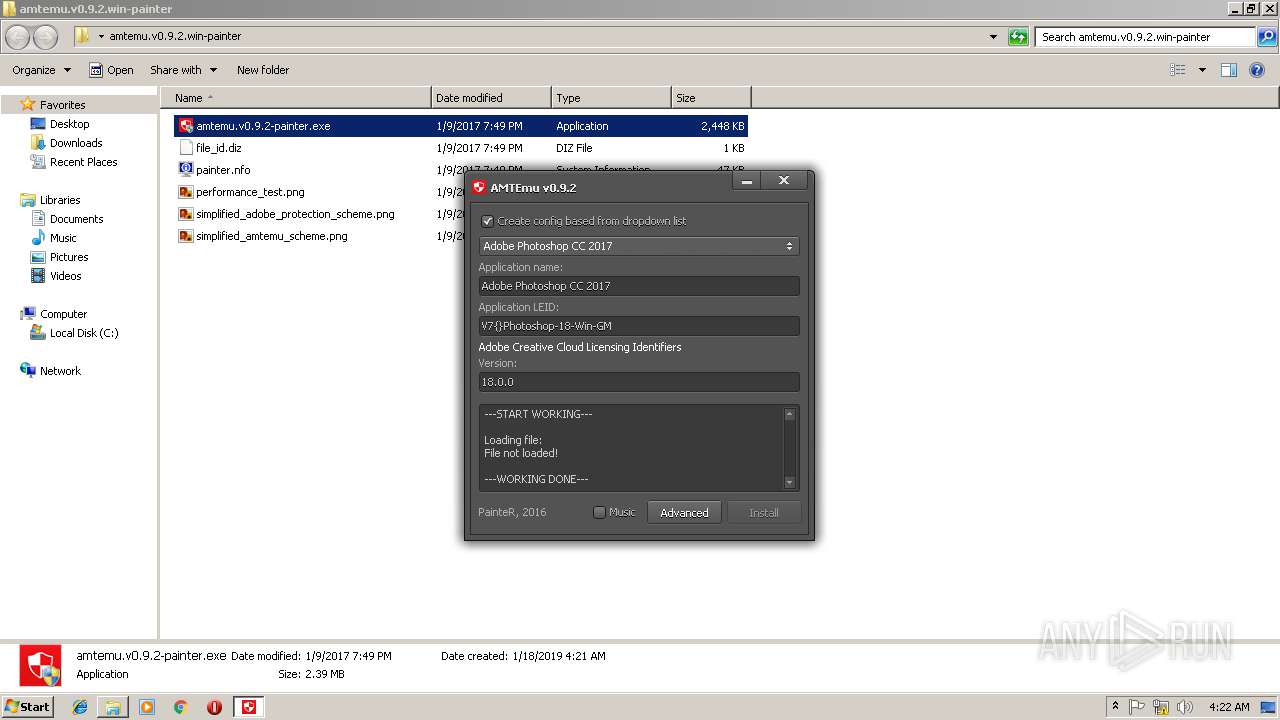
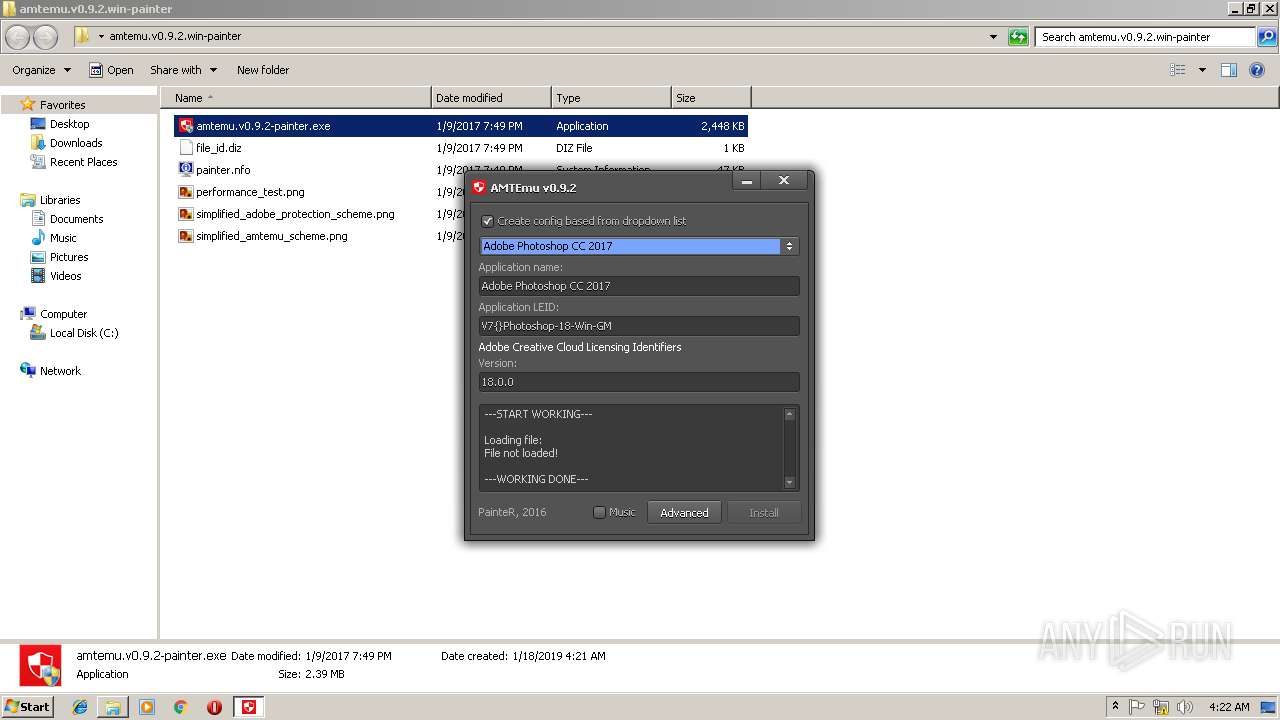
| 2856 | "C:\Users\admin\Desktop\amtemu.v0.9.2.win-painter\amtemu.v0.9.2-painter.exe" | C:\Users\admin\Desktop\amtemu.v0.9.2.win-painter\amtemu.v0.9.2-painter.exe | — | explorer.exe | |||||||||||
User: admin Company: PainteR Integrity Level: MEDIUM Description: ProxyEmu Exit code: 3221226540 Version: 0.9.2.0 Modules
| |||||||||||||||
| 3028 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\pconline1483962590187.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3216 | "C:\Users\admin\Desktop\amtemu.v0.9.2.win-painter\amtemu.v0.9.2-painter.exe" | C:\Users\admin\Desktop\amtemu.v0.9.2.win-painter\amtemu.v0.9.2-painter.exe | explorer.exe | ||||||||||||
User: admin Company: PainteR Integrity Level: HIGH Description: ProxyEmu Exit code: 0 Version: 0.9.2.0 Modules
| |||||||||||||||
Total events
1 475
Read events
1 332
Write events
138
Delete events
5
Modification events
| (PID) Process: | (3028) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3028) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3028) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3028) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\pconline1483962590187.zip | |||
| (PID) Process: | (3028) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3028) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3028) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3028) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3028) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\msinfo32.exe,-10001 |
Value: System Information File | |||
| (PID) Process: | (3028) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
1
Suspicious files
131
Text files
159
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3028 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3028.28404\amtemu.v0.9.2.win-painter\amtemu.v0.9.2-painter.exe | — | |
MD5:— | SHA256:— | |||
| 3028 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3028.28404\amtemu.v0.9.2.win-painter\file_id.diz | — | |
MD5:— | SHA256:— | |||
| 3028 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3028.28404\amtemu.v0.9.2.win-painter\painter.nfo | — | |
MD5:— | SHA256:— | |||
| 3028 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3028.28404\amtemu.v0.9.2.win-painter\performance_test.png | — | |
MD5:— | SHA256:— | |||
| 3028 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3028.28404\amtemu.v0.9.2.win-painter\simplified_adobe_protection_scheme.png | — | |
MD5:— | SHA256:— | |||
| 3028 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3028.28404\amtemu.v0.9.2.win-painter\simplified_amtemu_scheme.png | — | |
MD5:— | SHA256:— | |||
| 2072 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\46748bad-4d45-424c-a337-aaf8514c7382.tmp | — | |
MD5:— | SHA256:— | |||
| 2072 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2072 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2072 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\CacheStorage\e6622492fa163609ddd4212f54512baa07929ed3\caecb3bd-7969-4305-84d6-3a376453ec73\index-dir\temp-index | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
181
TCP/UDP connections
257
DNS requests
170
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
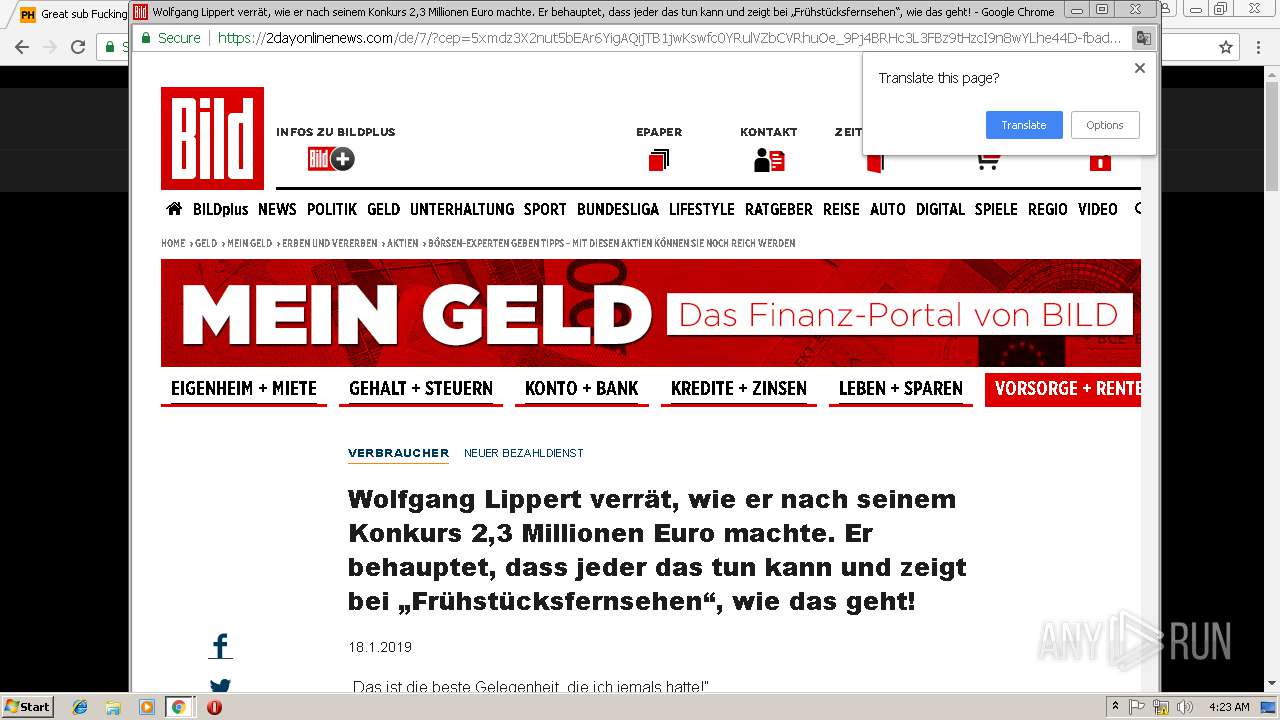
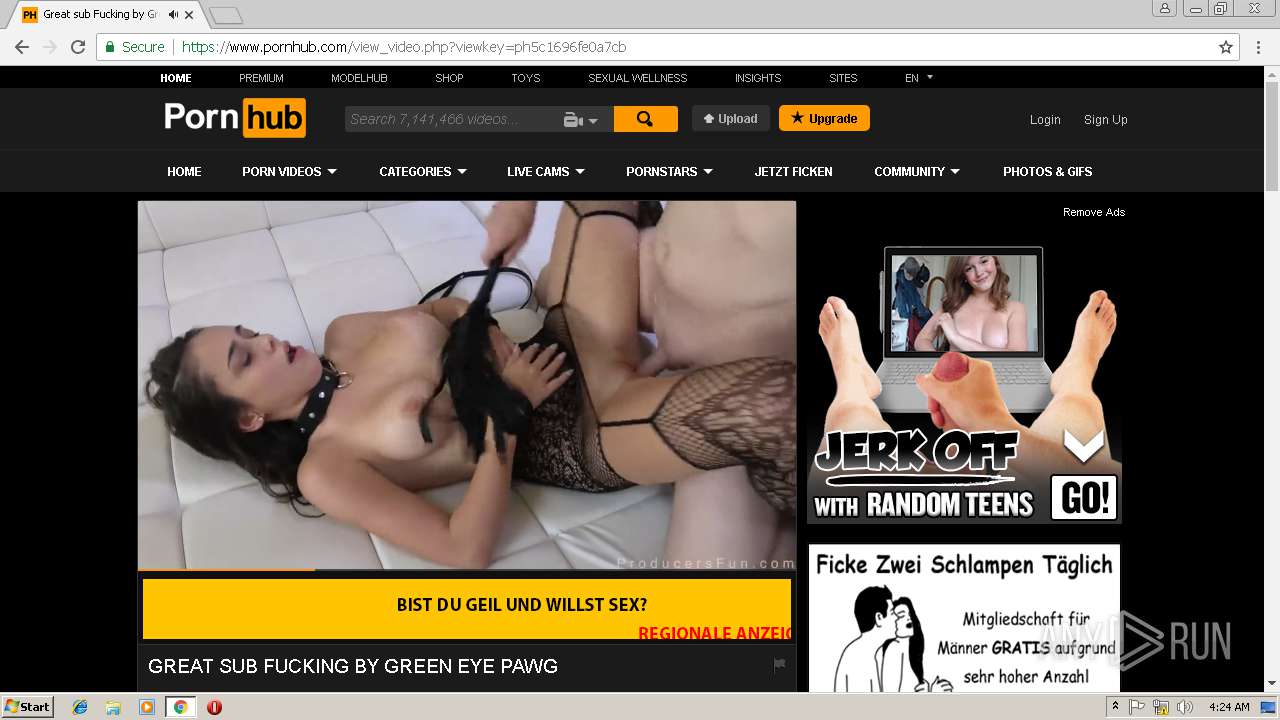
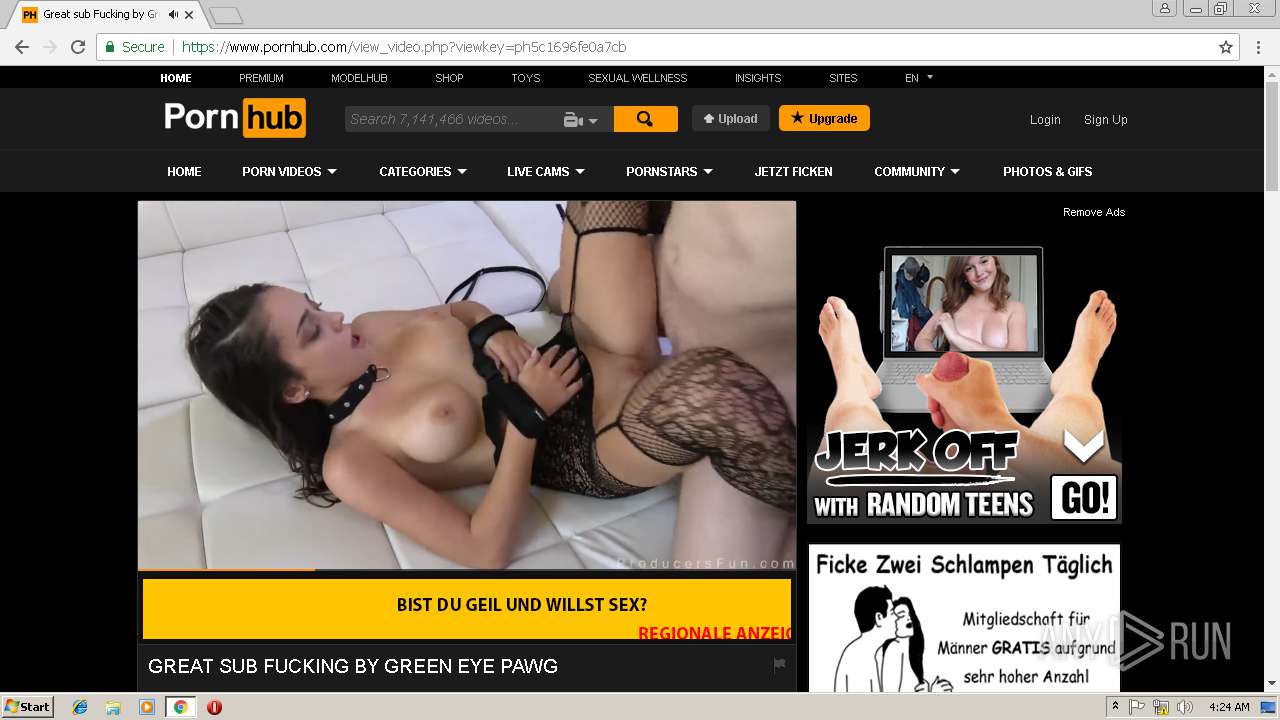
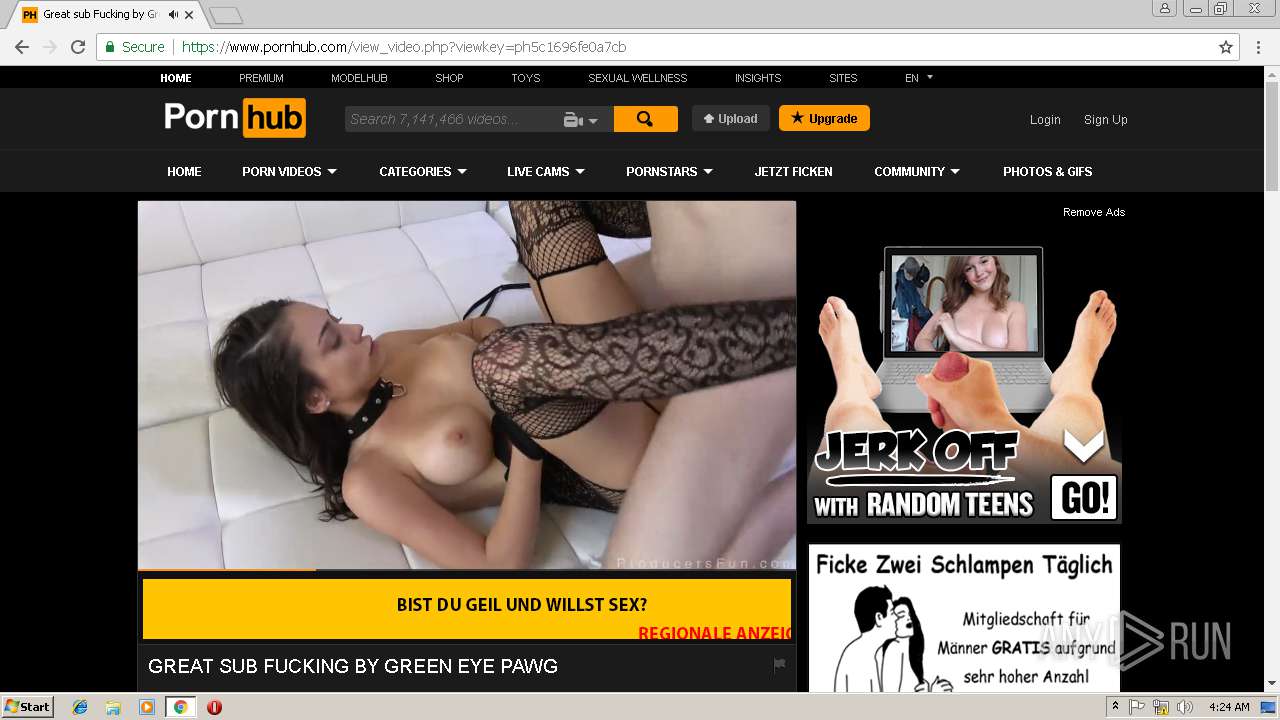
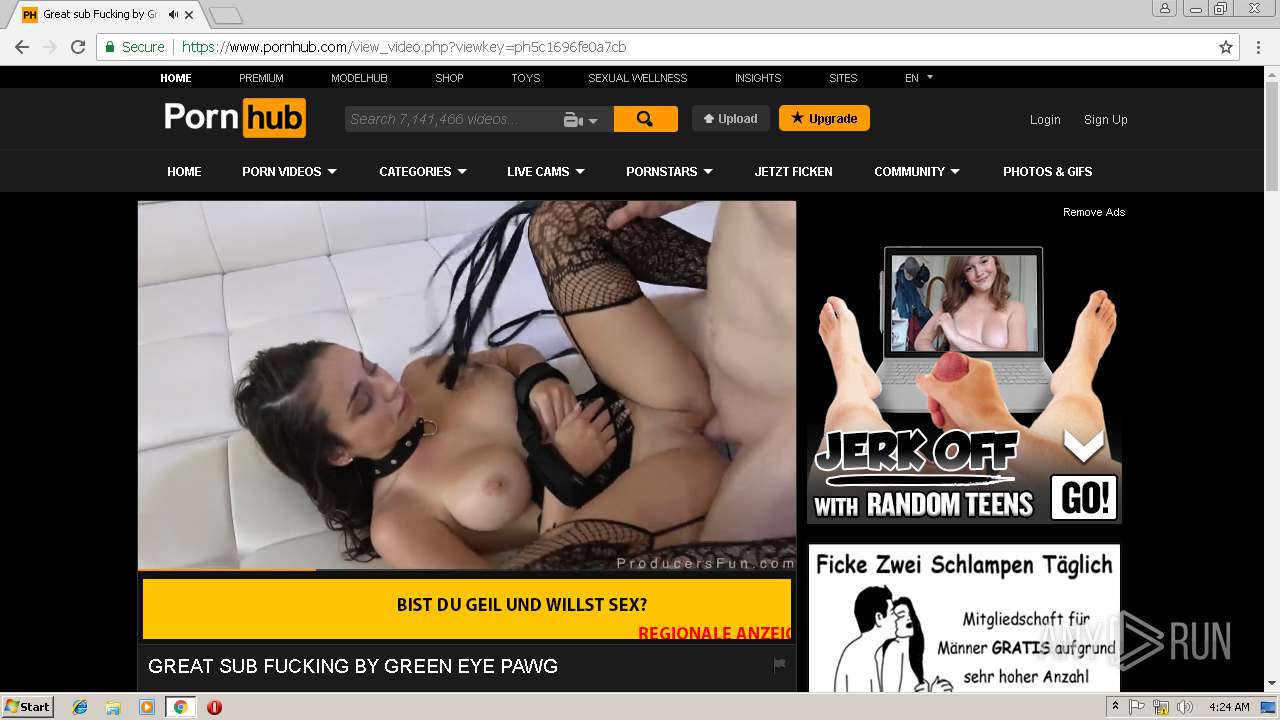
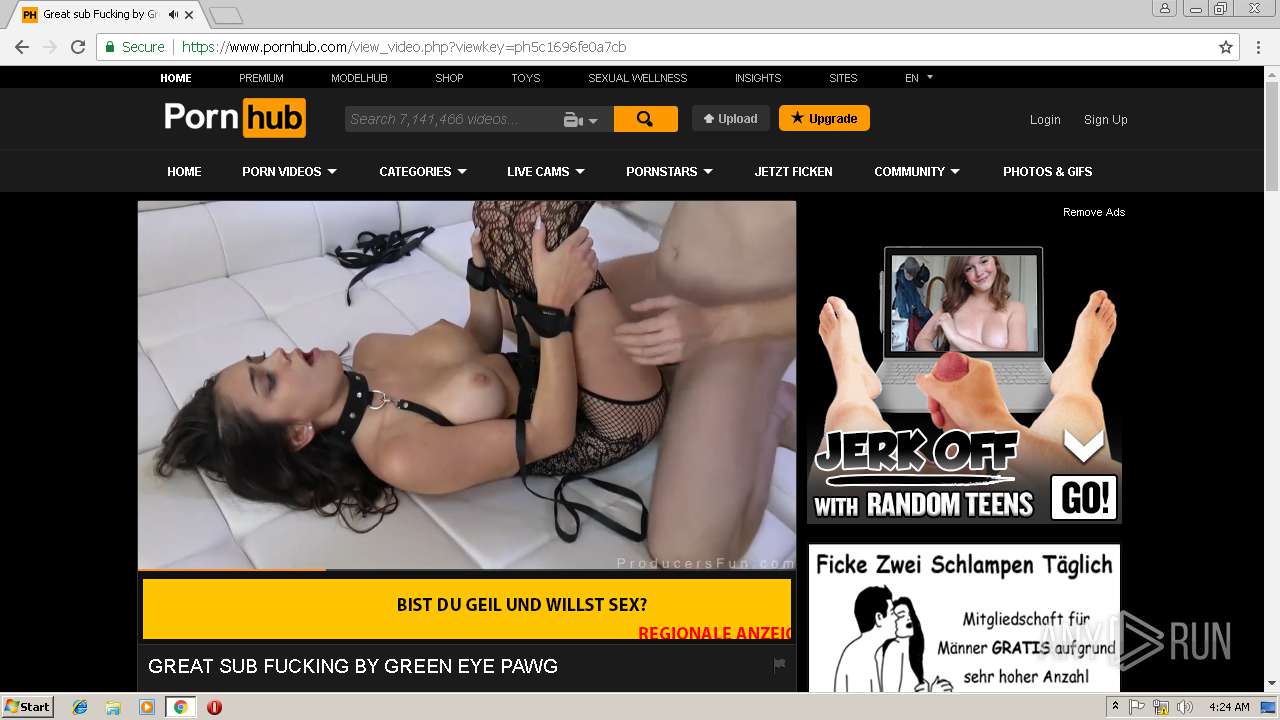
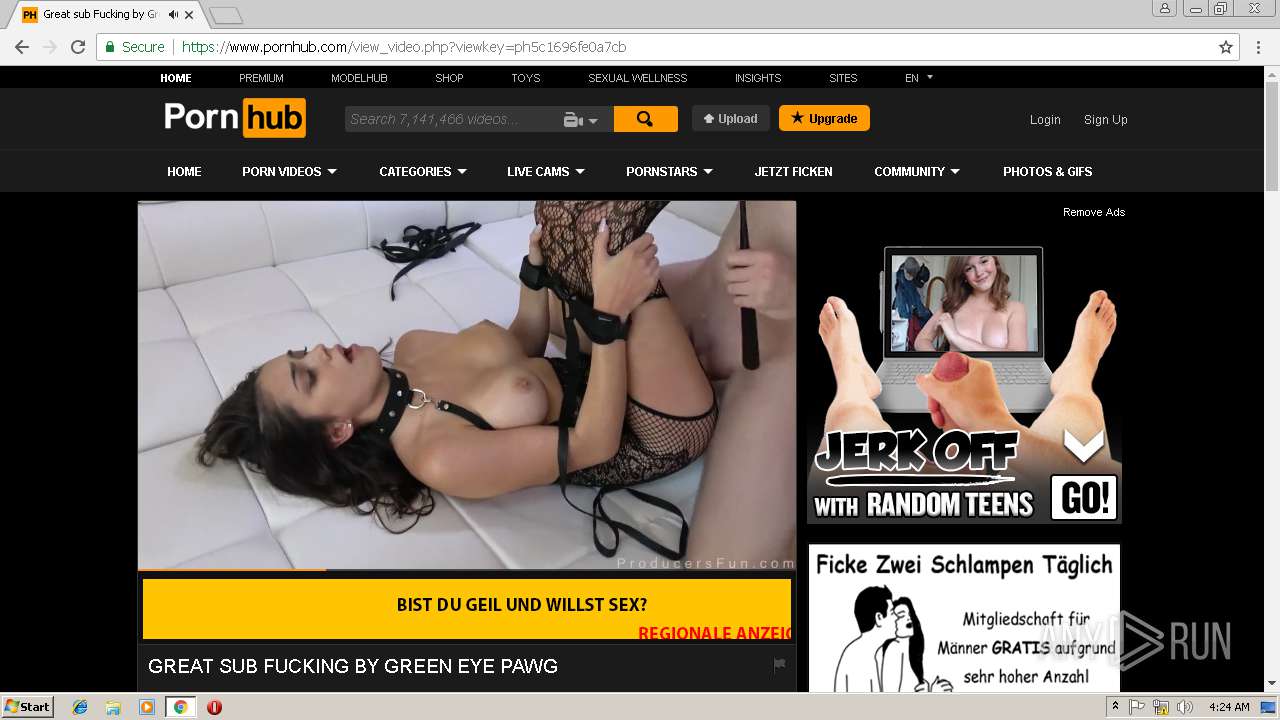
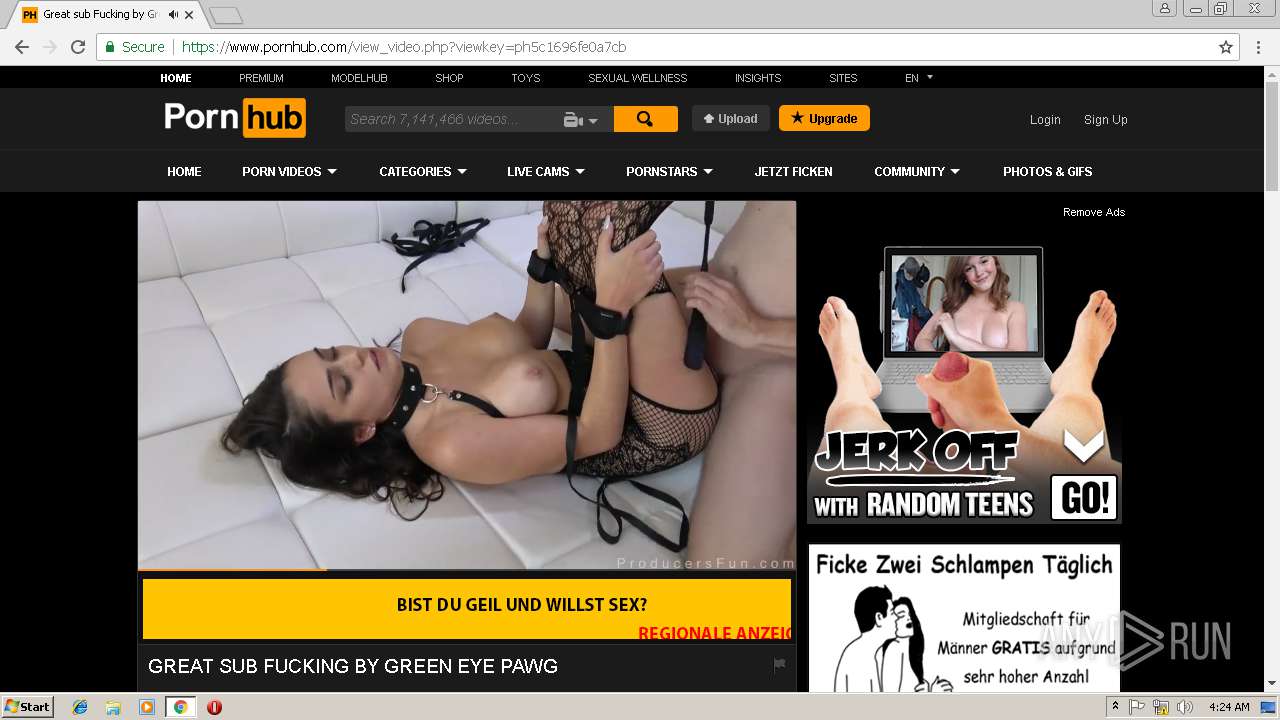
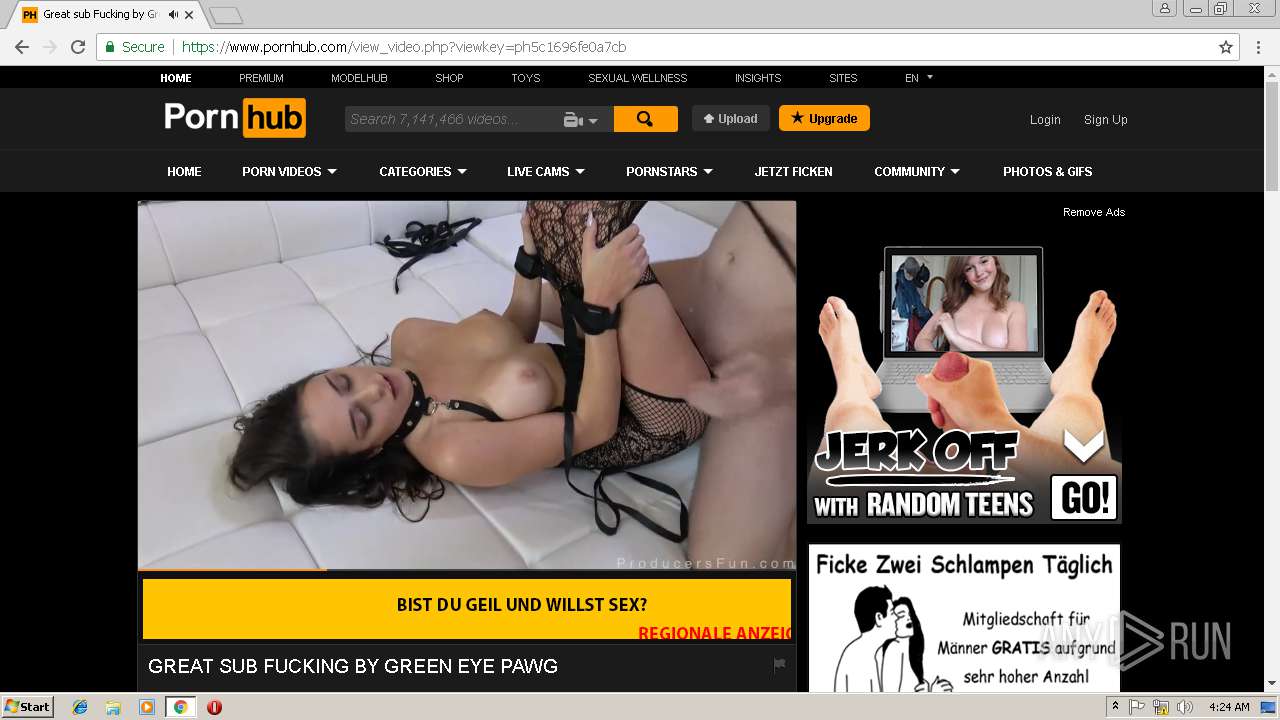
2072 | chrome.exe | GET | 301 | 104.27.133.194:80 | http://2dayonlinenews.com/de/7/?cep=5xmdz3X2nut5bEAr6YigAQijTB1jwKswfc0YRulVZbCVRhuOe_9Pj4BRHc3L3FBz9tHzcI9n8wYLhe44D-fbadxi-0UjdImjy5F1foEknmVn4on7-lpXwaTPlerVa0L303cg5oDwWFrHyPyoaZA1-AbkHS1ZUhaGEBqh5WqlXOMdBzd-xEYbH0yO_gKskFjeWvKPdQxlj5fWgyIonvxwXJROjN_2YVpO9PR0jeeUAhVYvGvvJ8KcHMnmWQNbto3jffYeGbBa2ICOjl2Z0hO5eYD15S3KcXhR9MkserUkr0xxVHesBnIGVMsx1Y3T82GOY841UUHRJfDI9sTNtZZL3ZLfaG-4RgnhyceUIkKzlP3EOW86UIG88CnvbvzhW-5y2iZMo7Q_-Z3SqXs3hCQC13h0Q65cwV8a4EC2xI157UI2ZjY4IK9I-FBQiO0iIYNATe7kCoPz6VDLOZwK_eA7BeS0P-qmrtT1By0-Z8j_t74&extpub=pornhub.com&campaignName=Germany%20-%200020%20-%20Web%20Mob%20-%20PL%20-%20PopUp%20-%20VR&browser=Chrome&country=DE&city=Volkach&bid=0&placementid=30471&placementname=Germany%20-%200020%20-%20Web%20-%20PL%20-%20PopUp%20-%20VR_Germany_Page-Under_1&campaignid=18312&s2sparam=%7Bs2sparam%7D | US | — | — | suspicious |
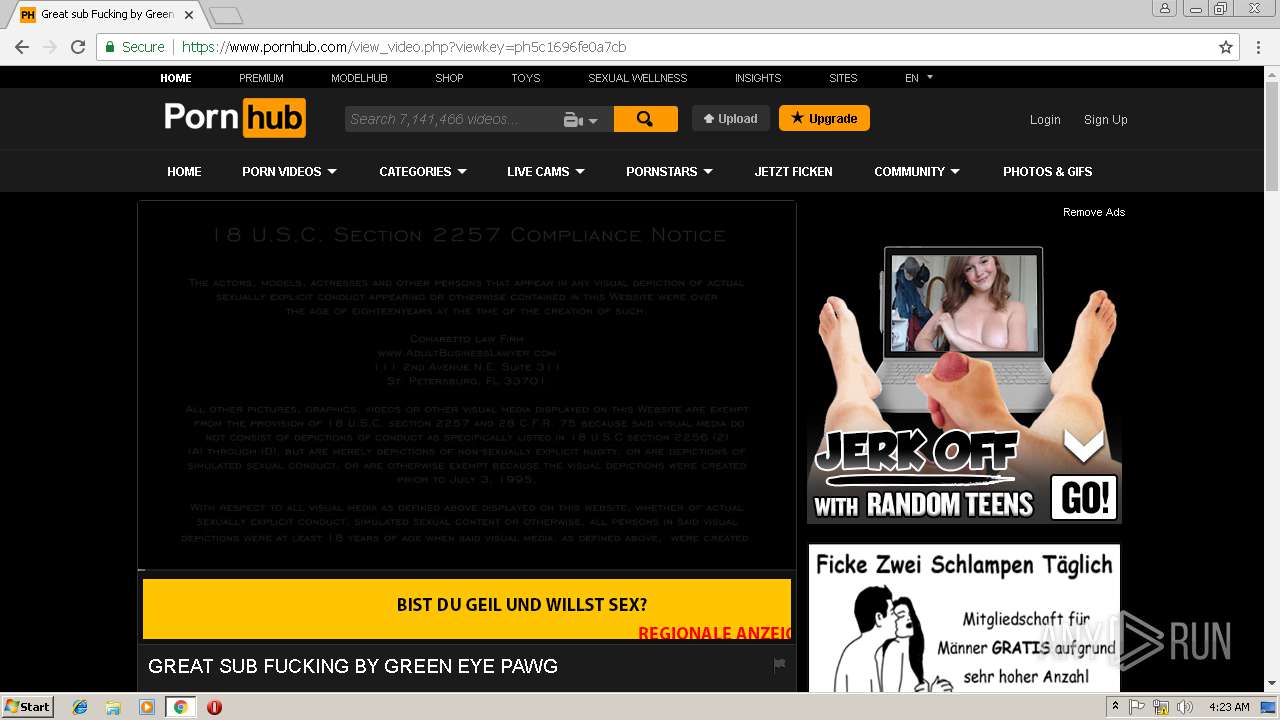
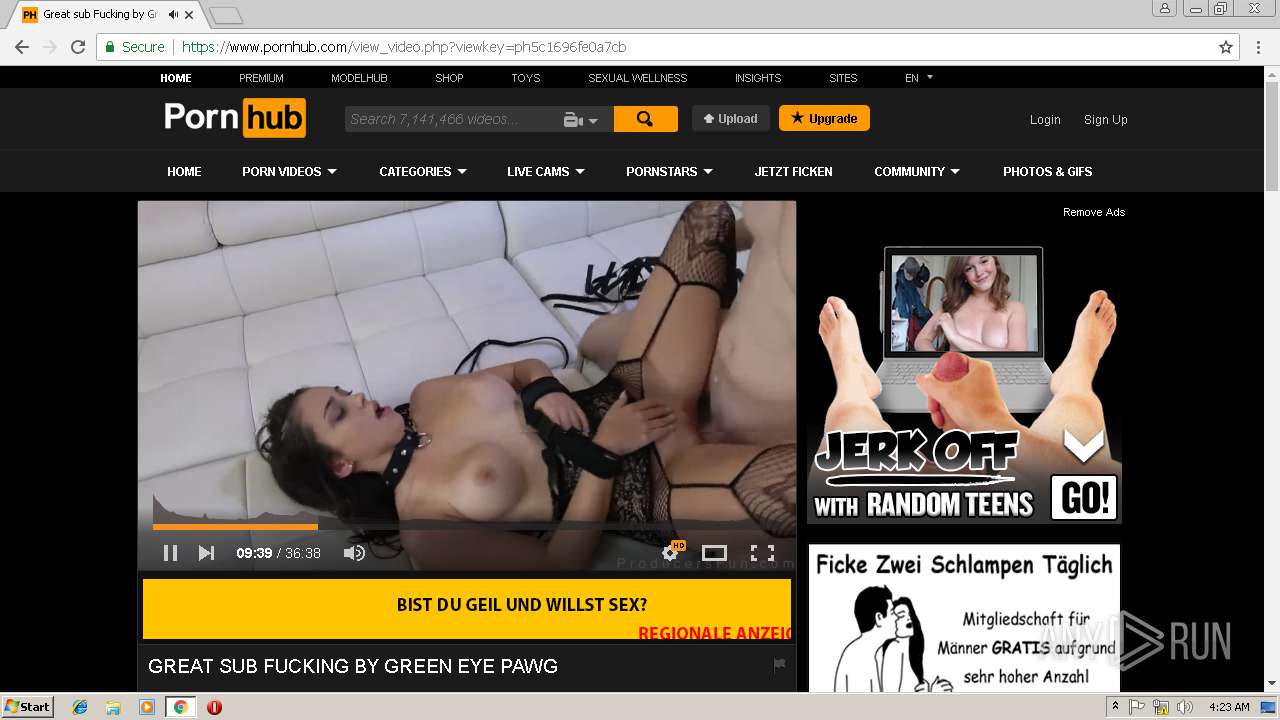
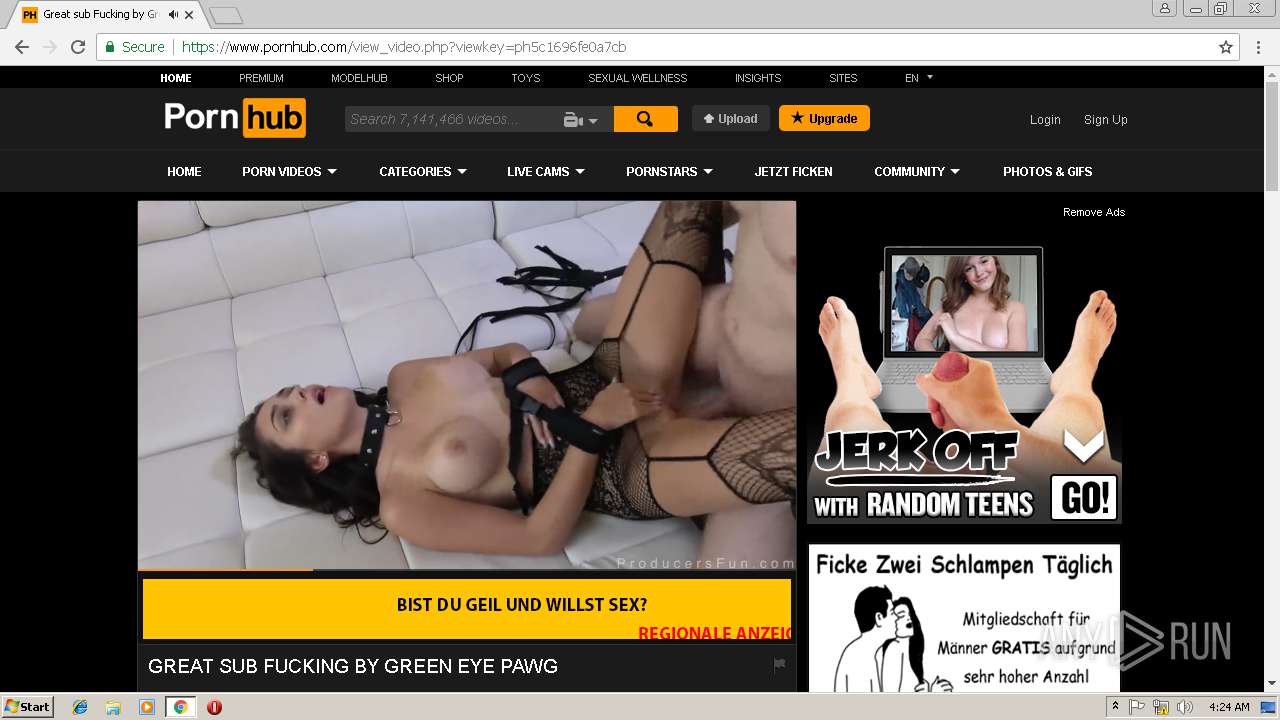
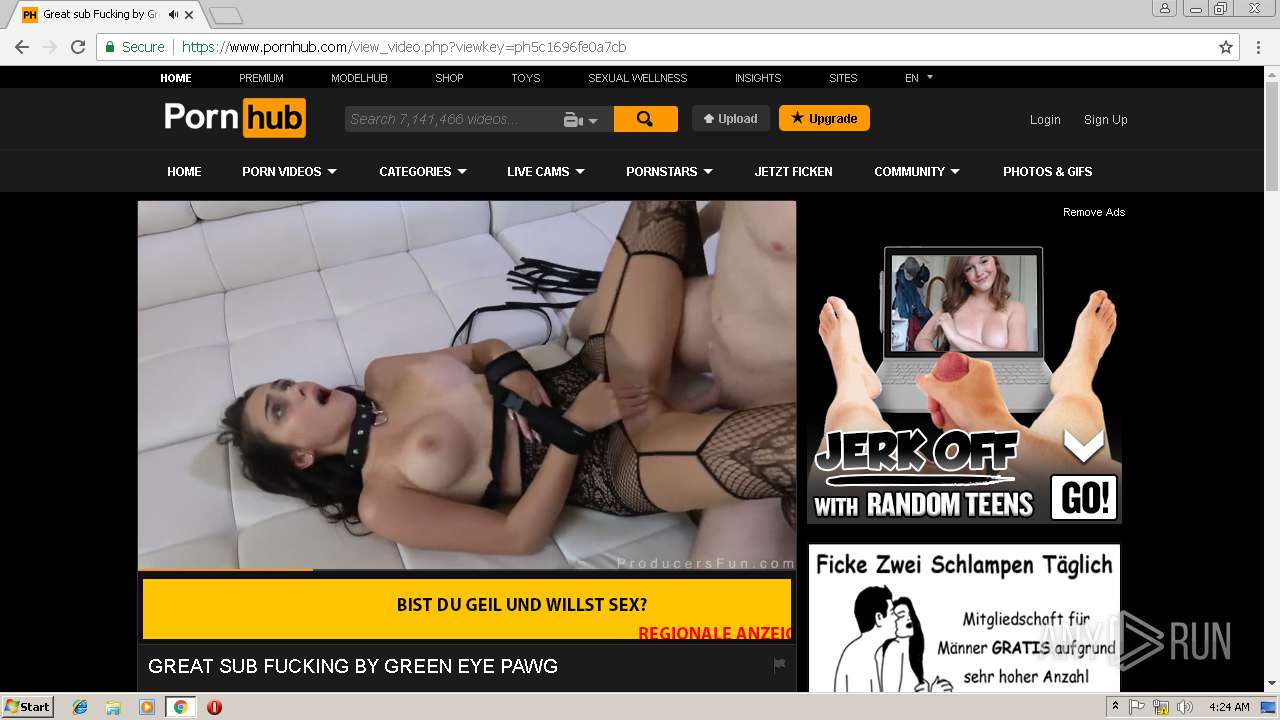
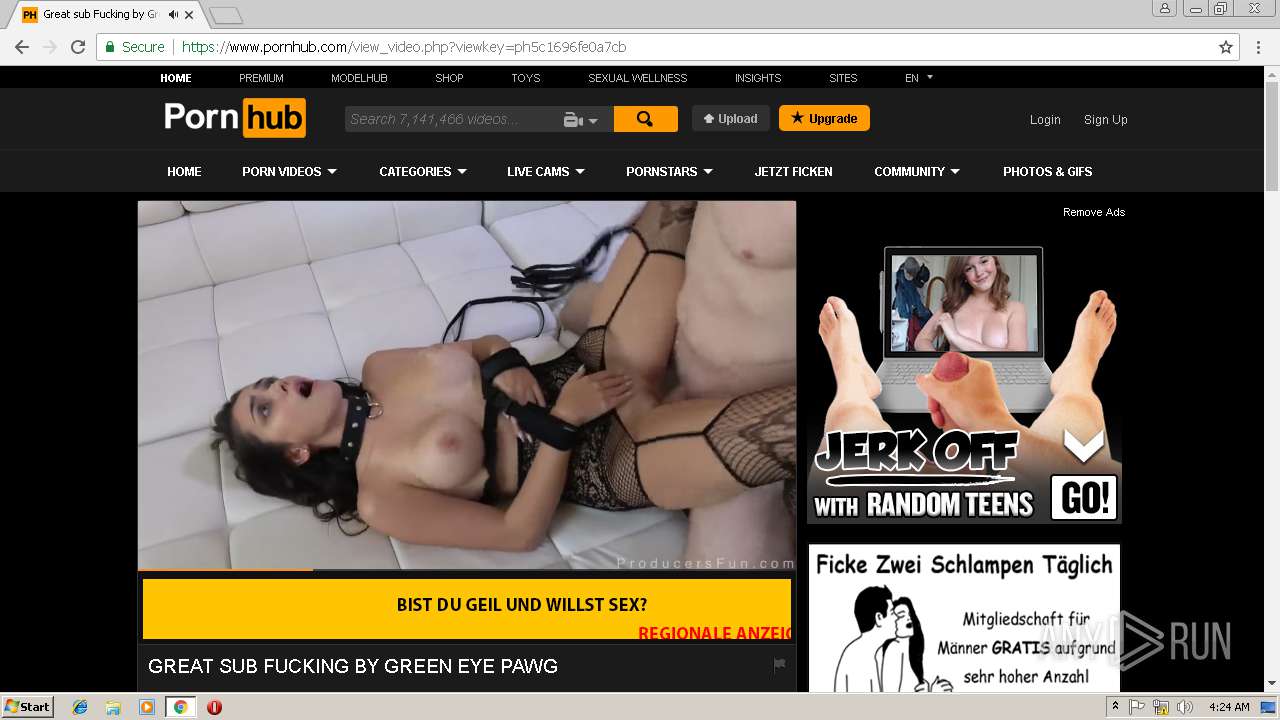
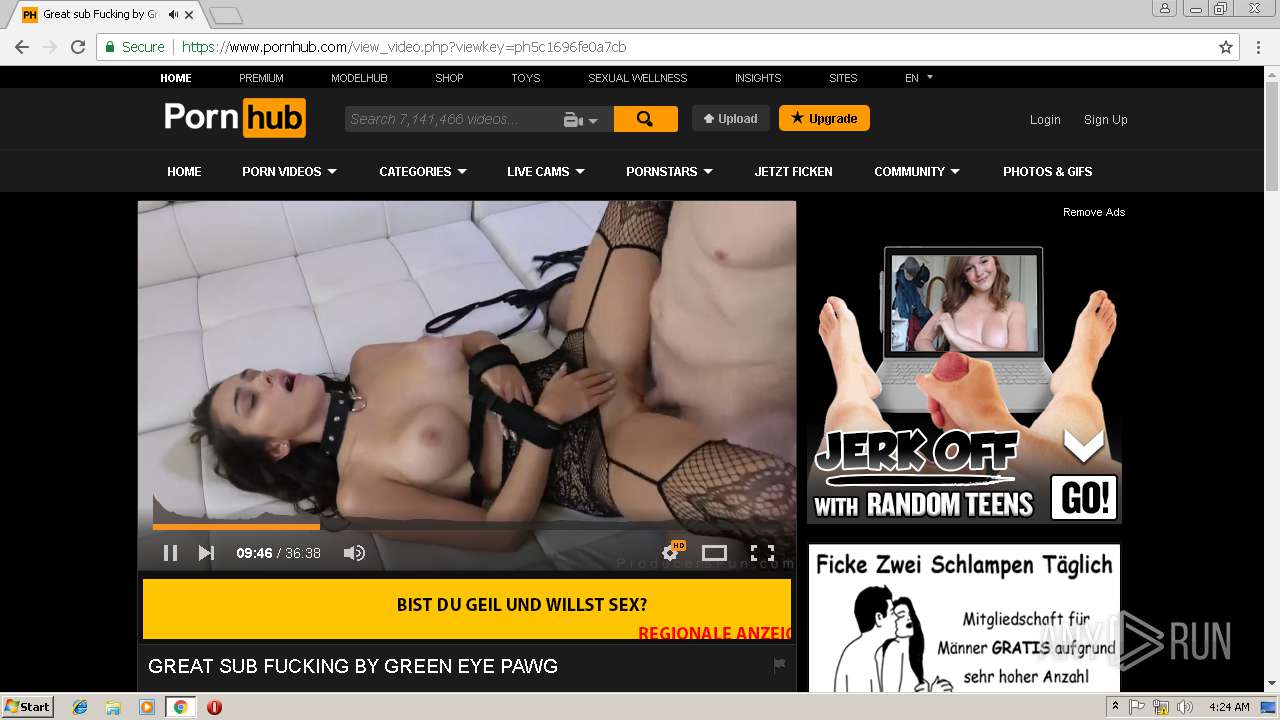
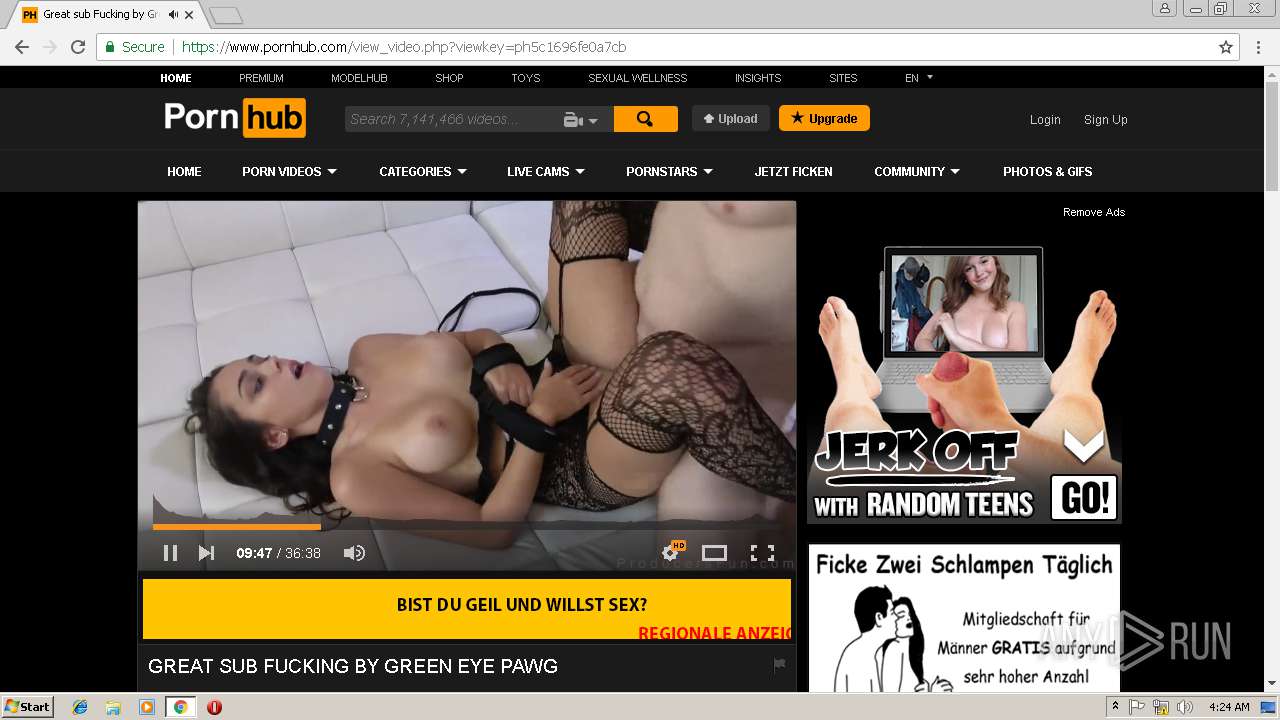
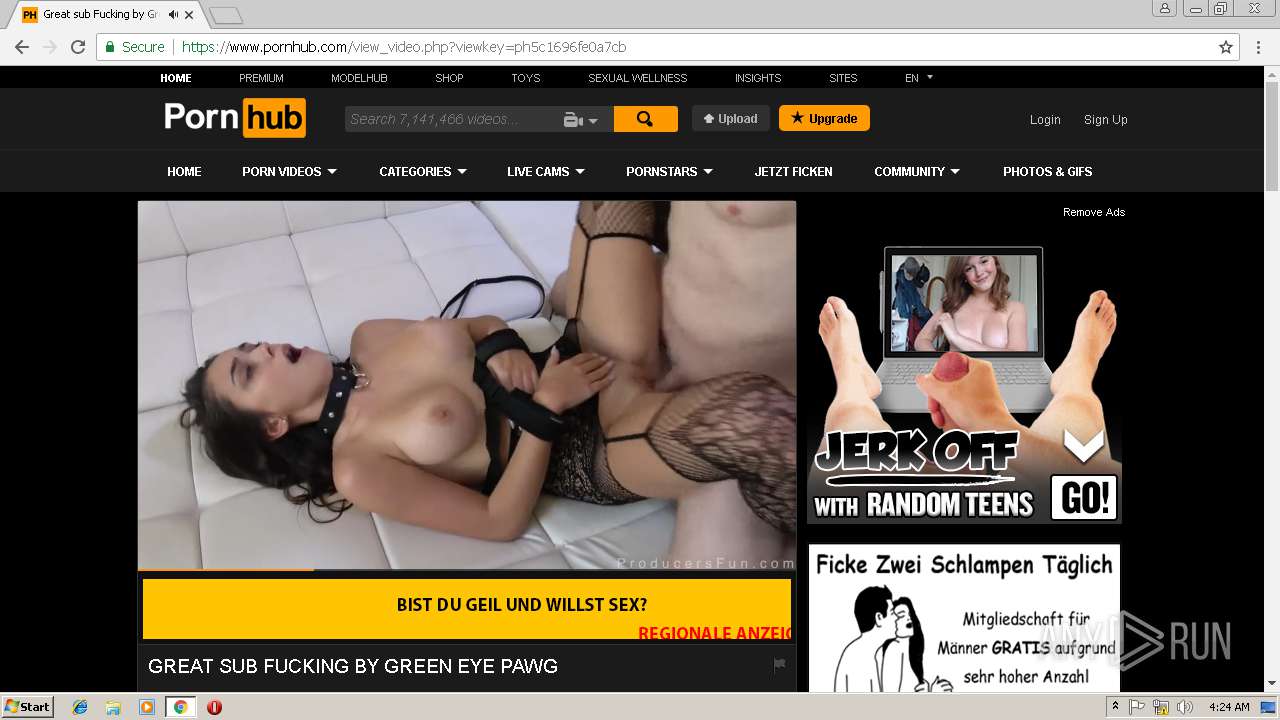
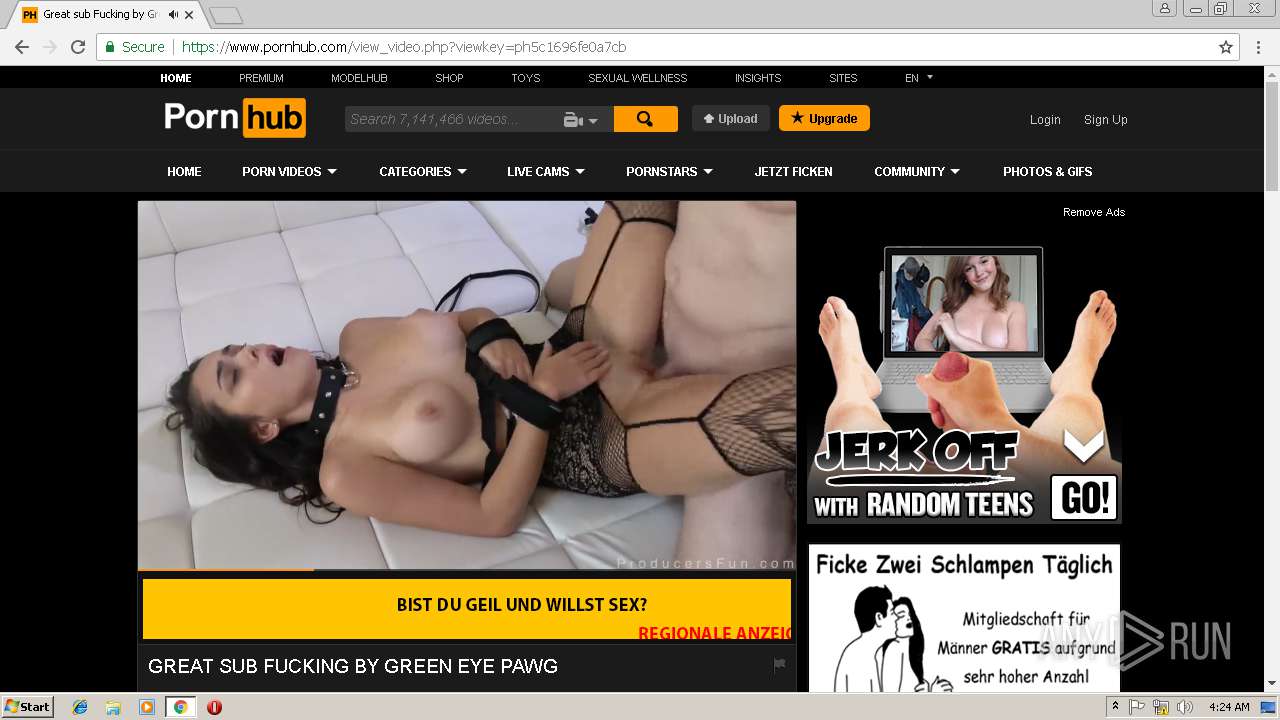
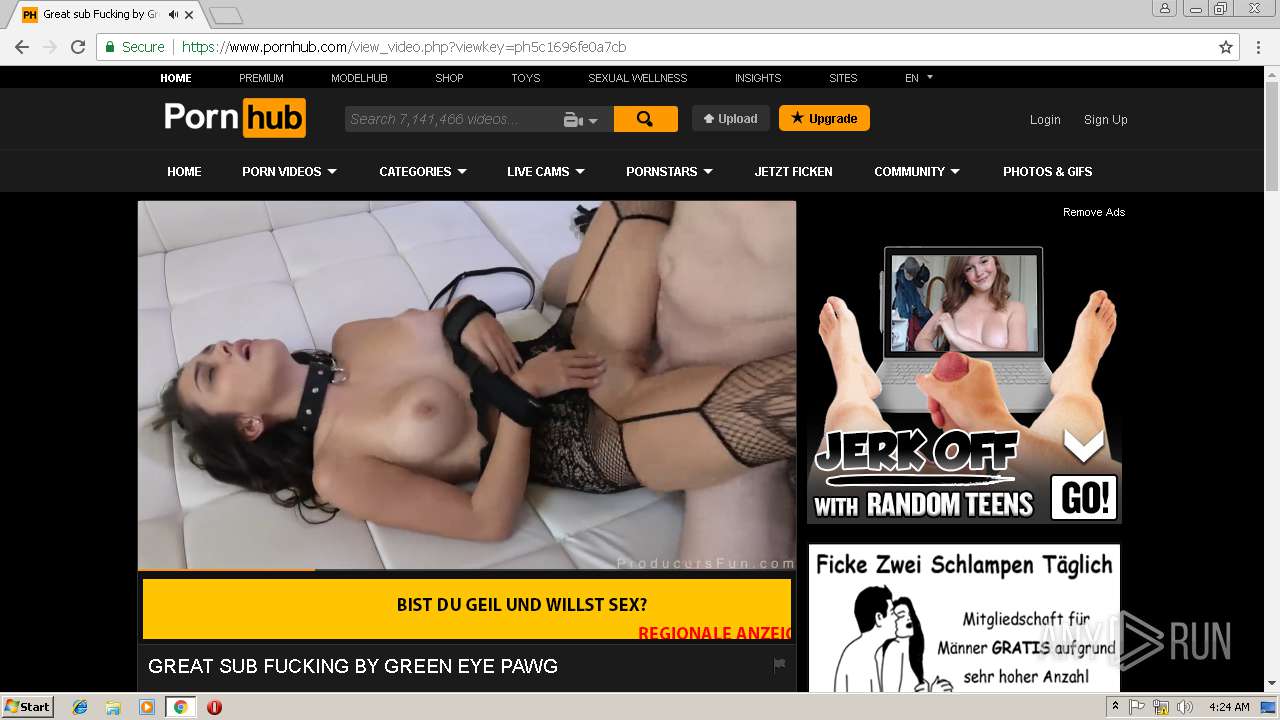
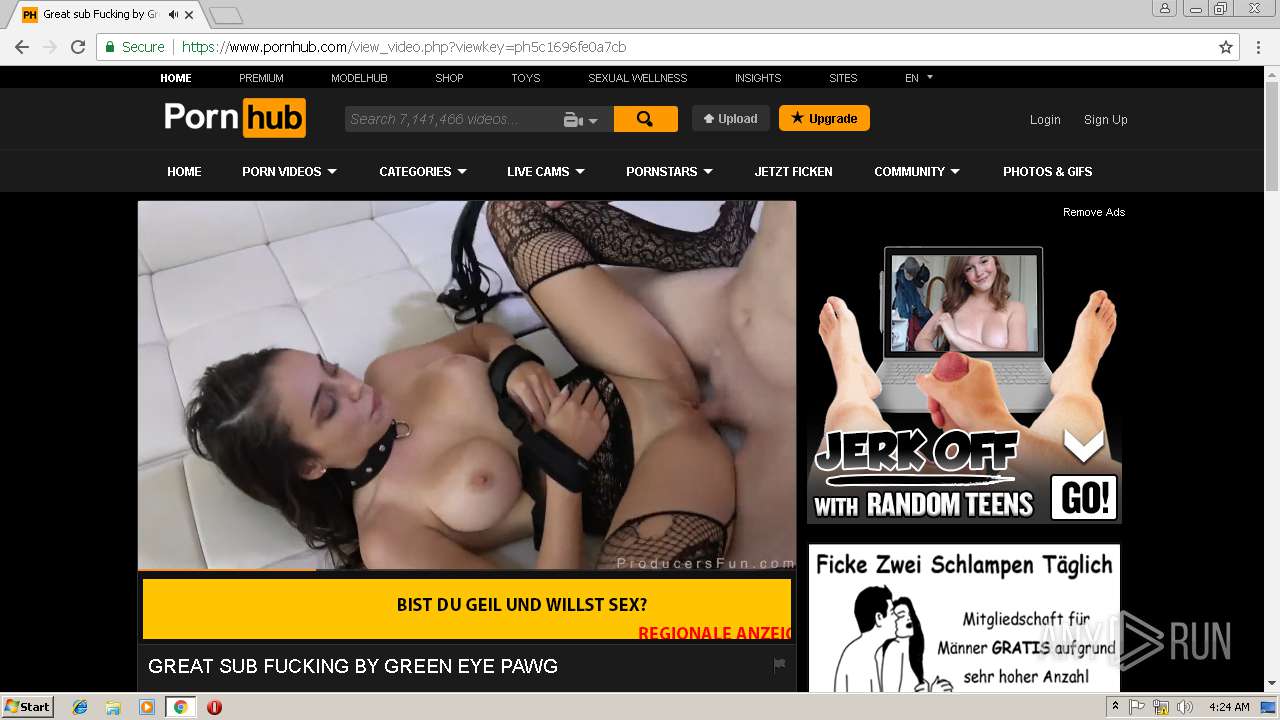
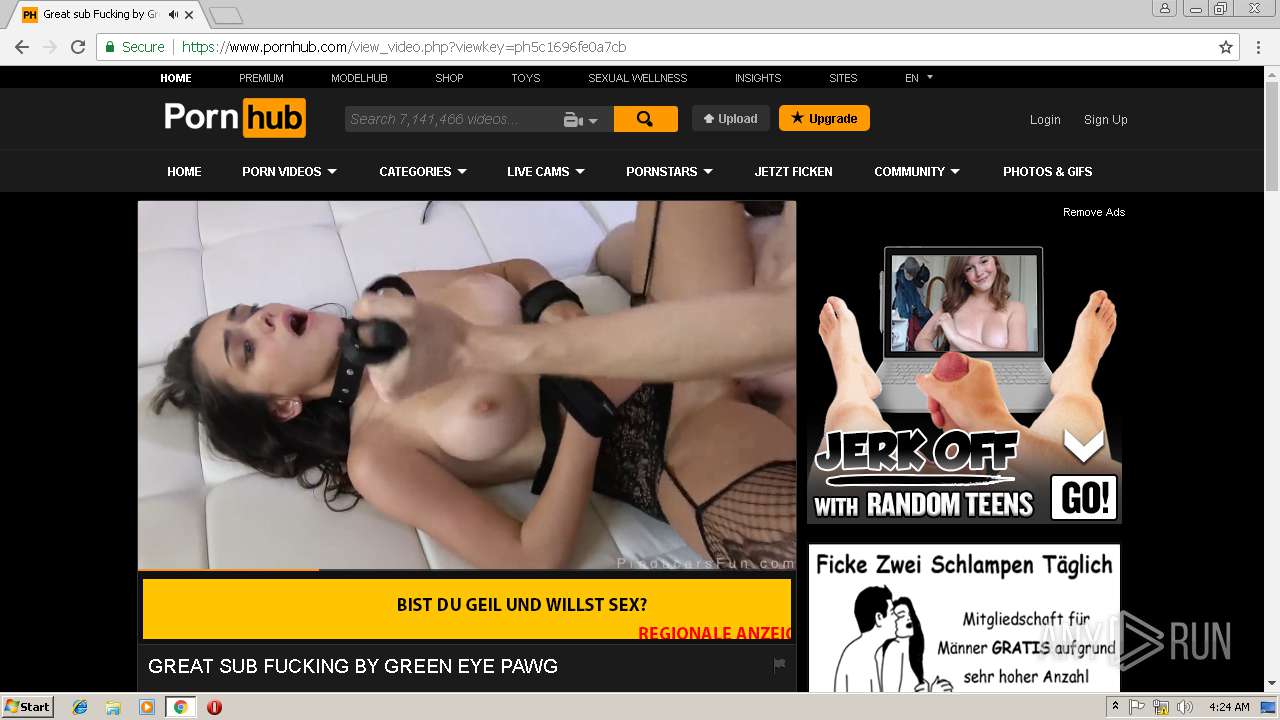
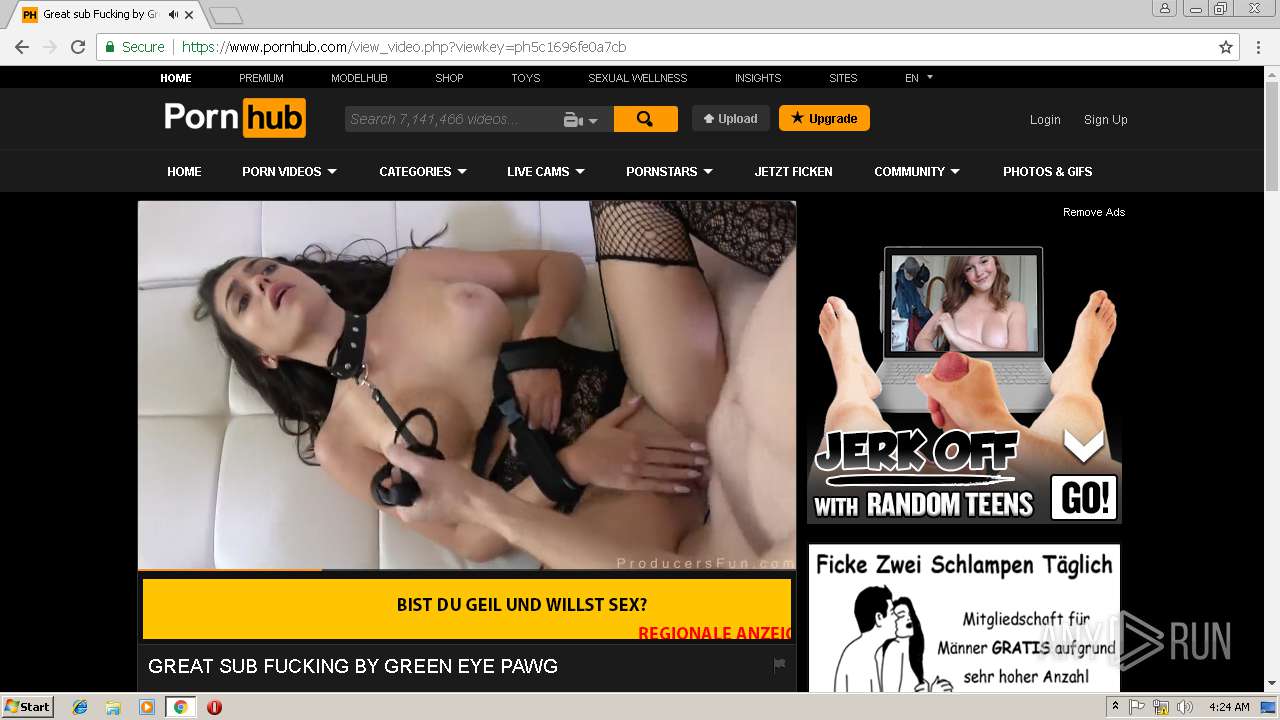
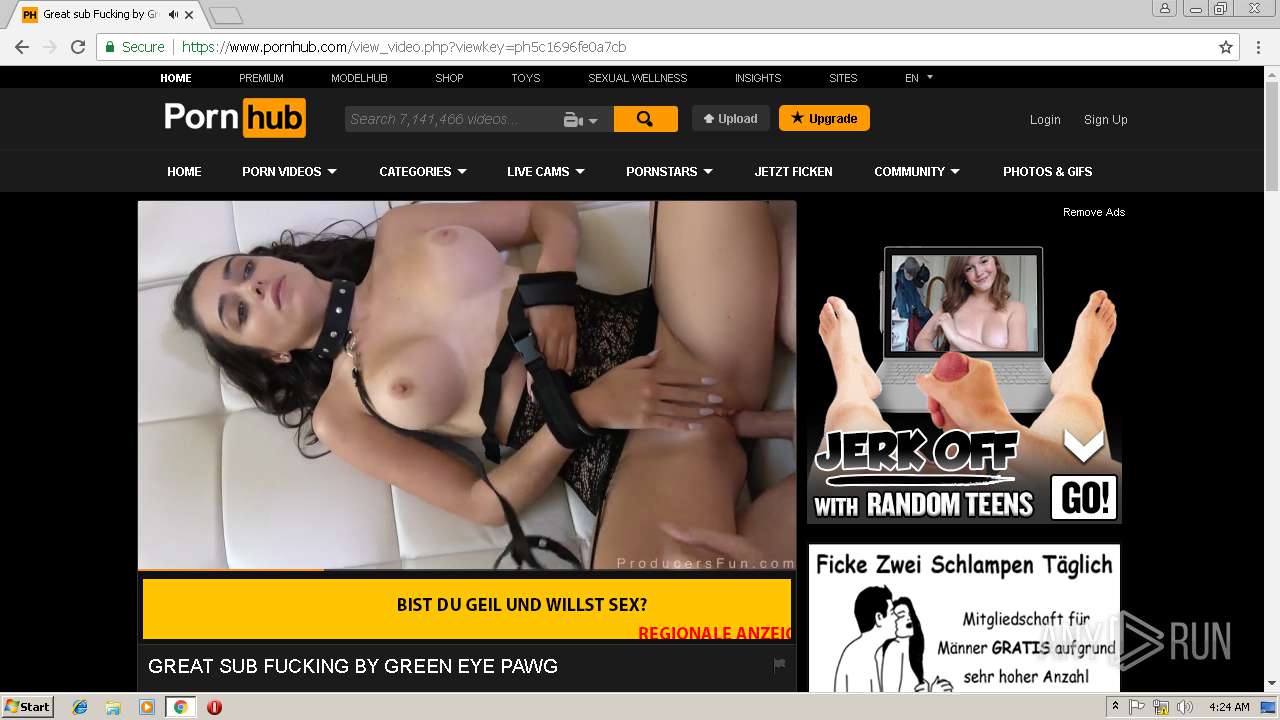
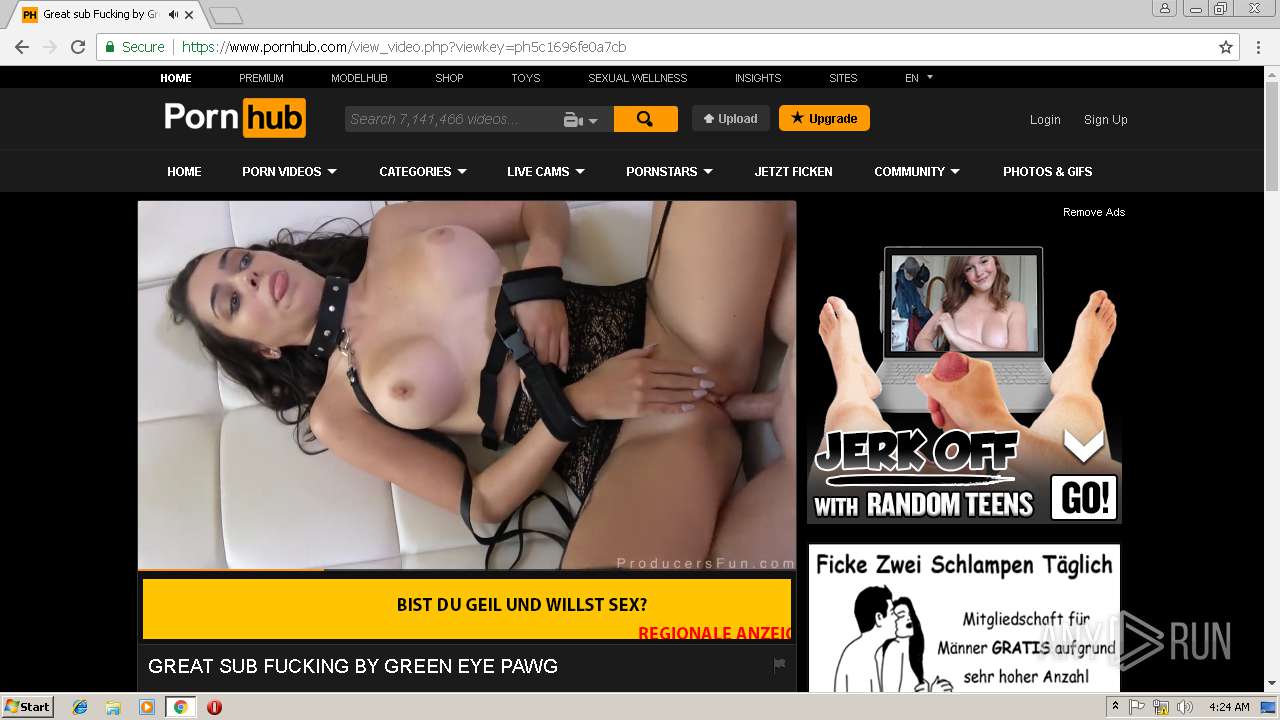
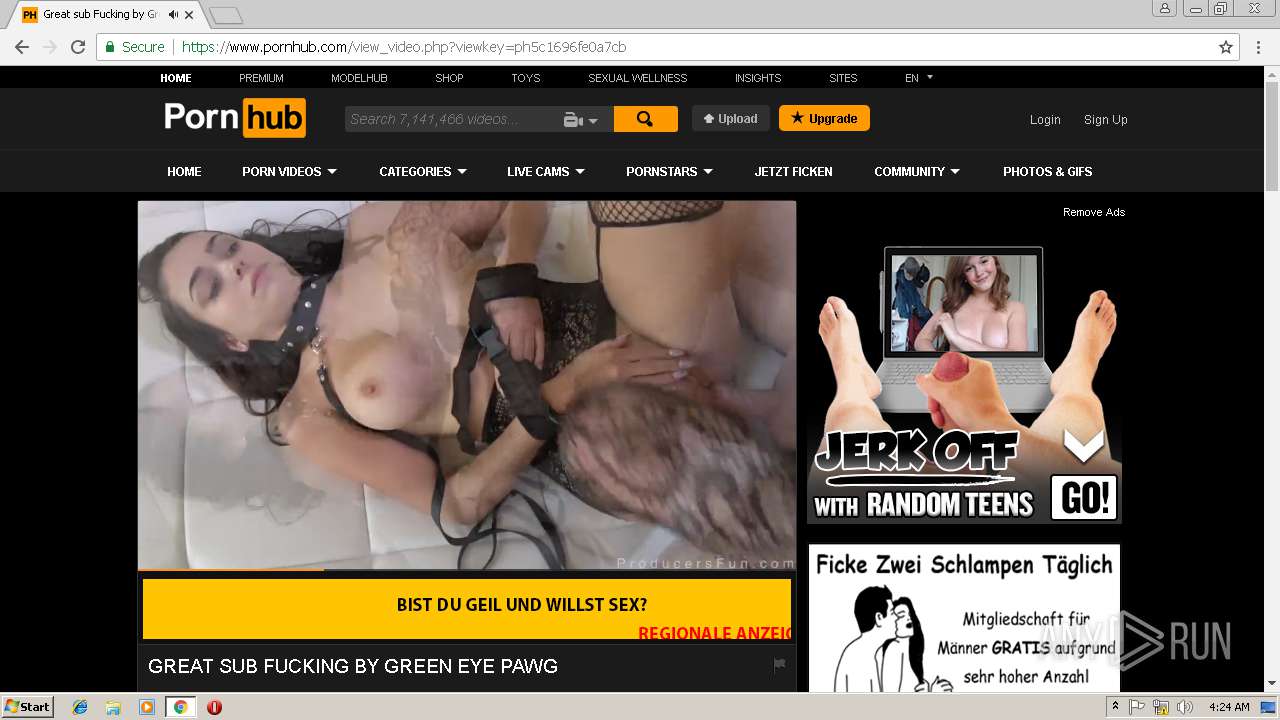
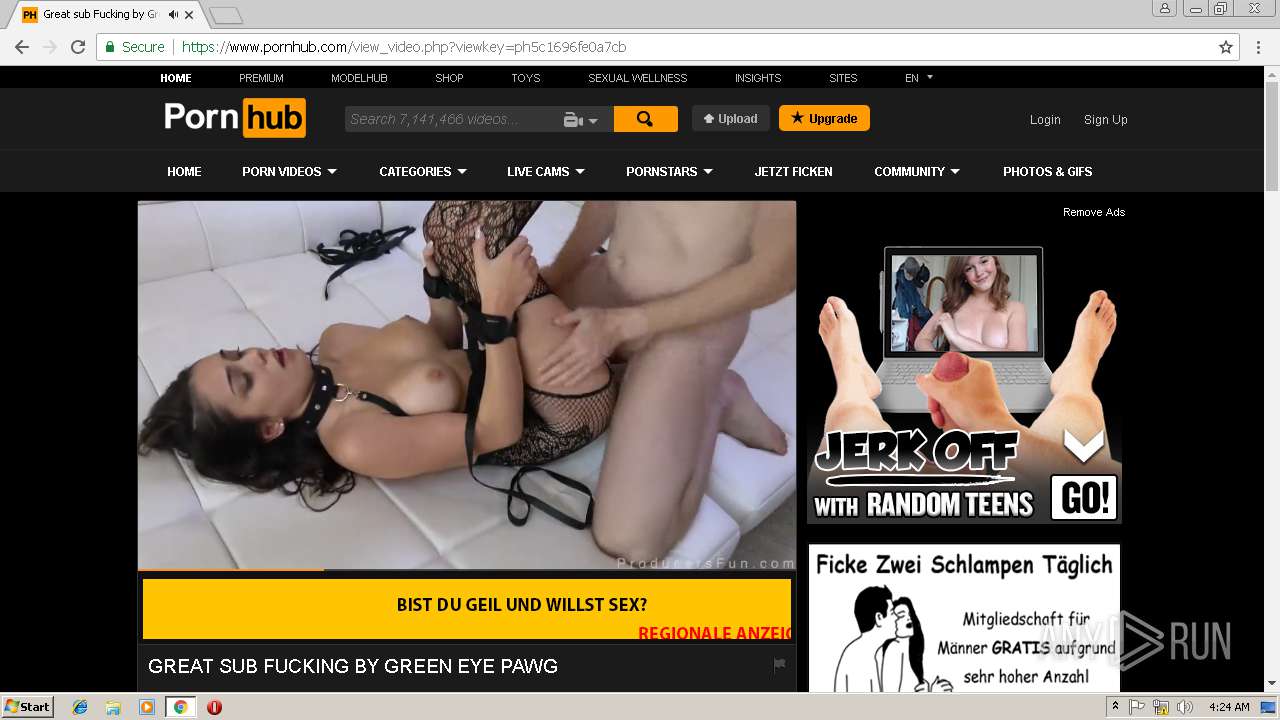
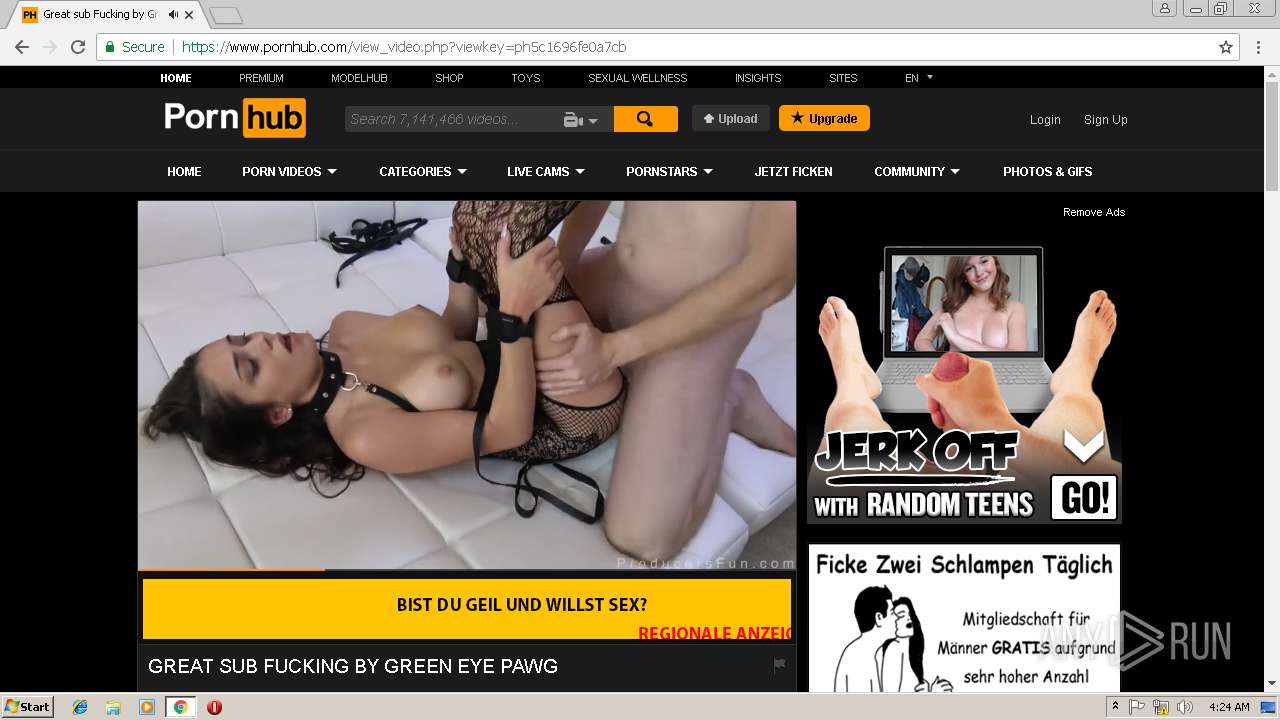
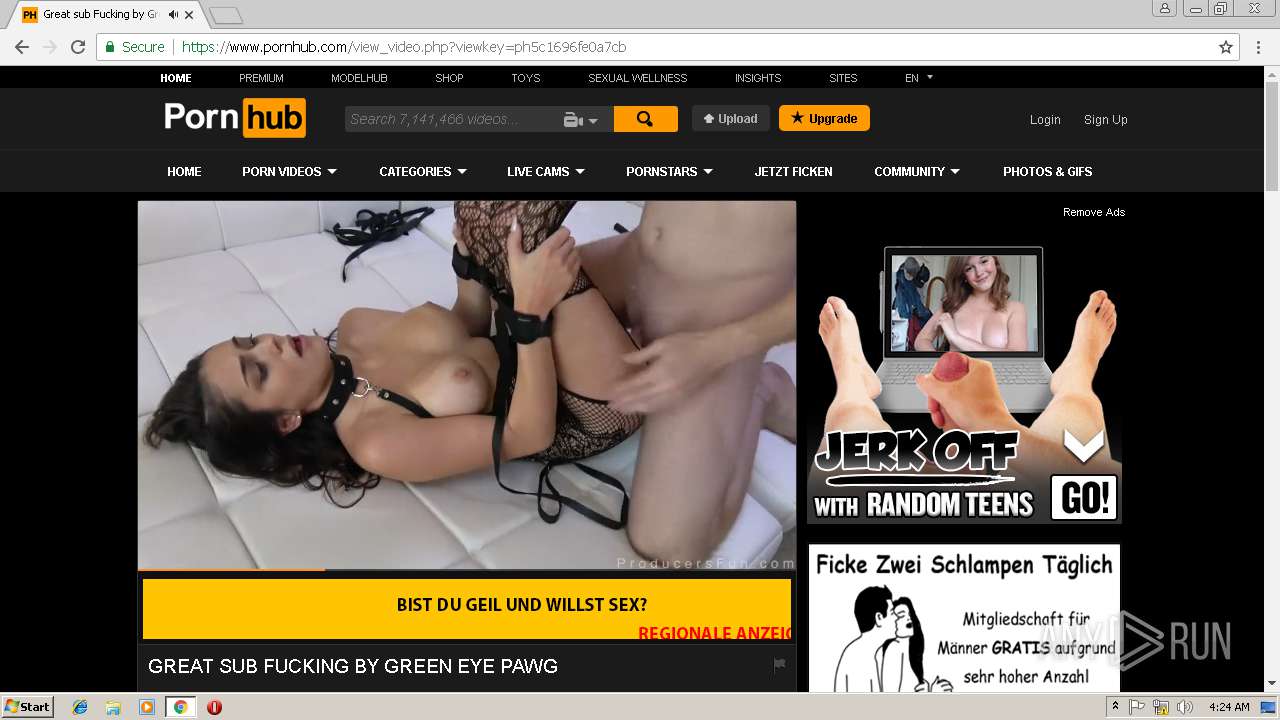
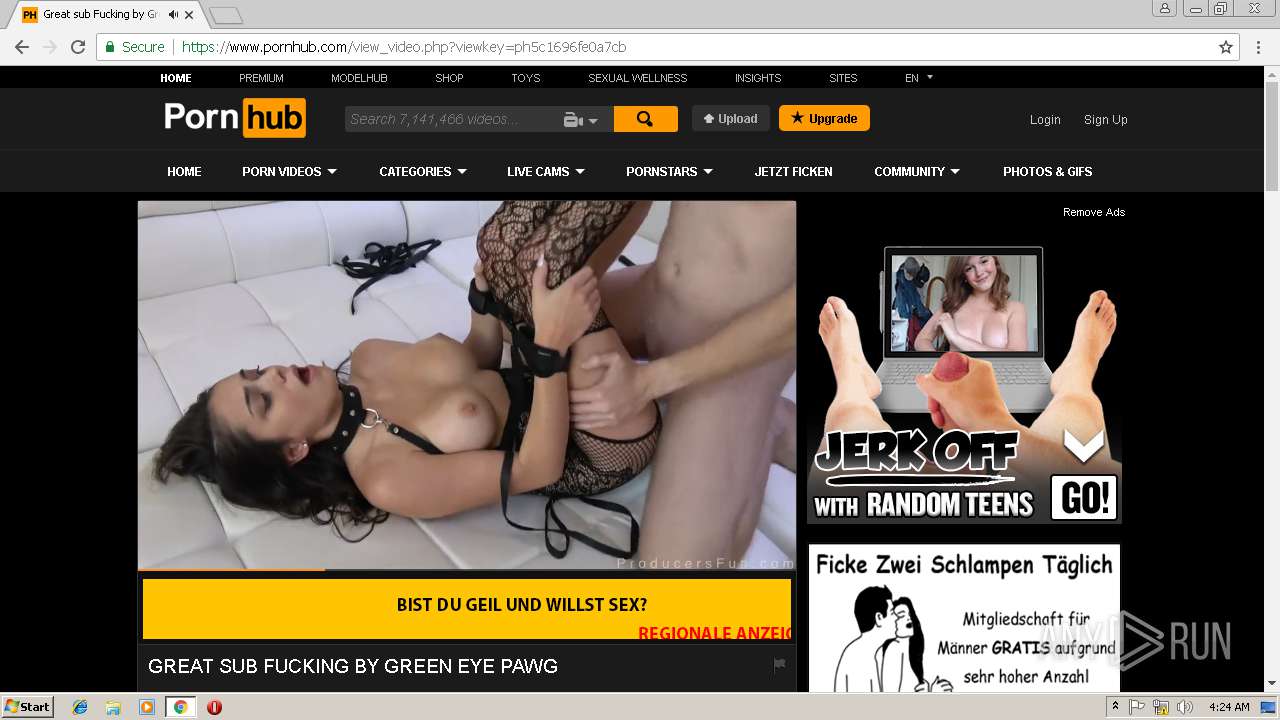
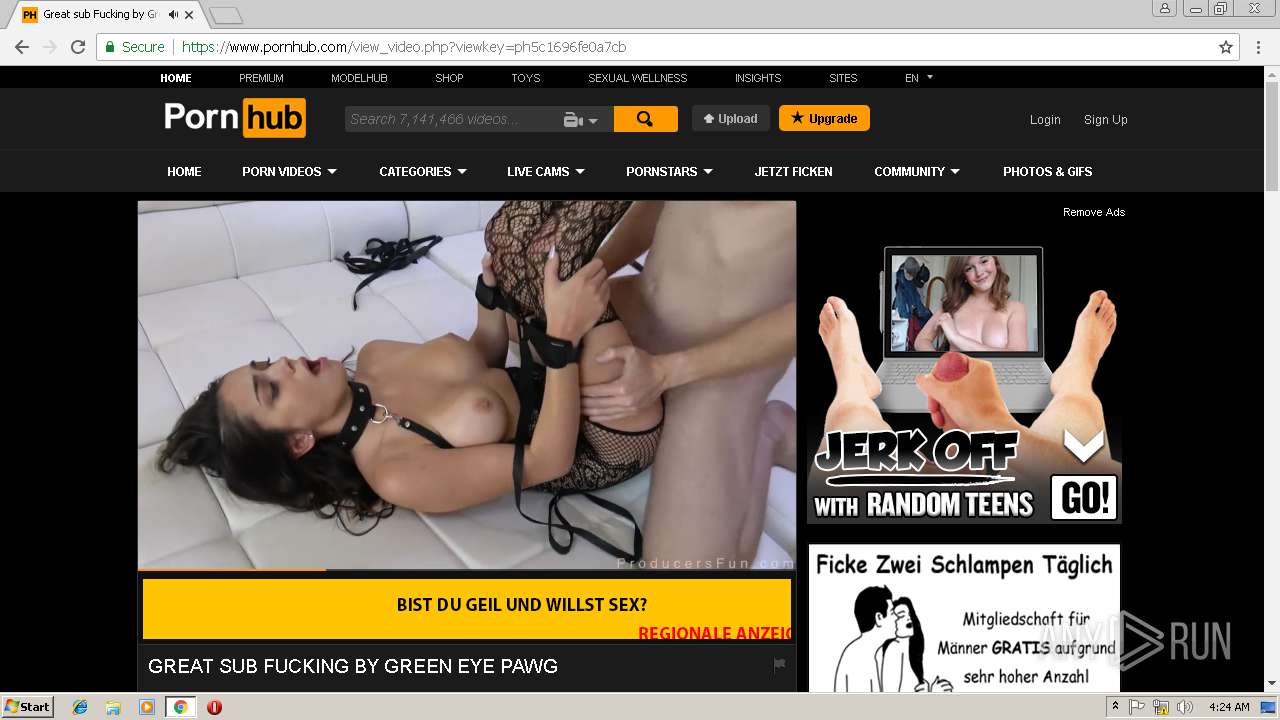
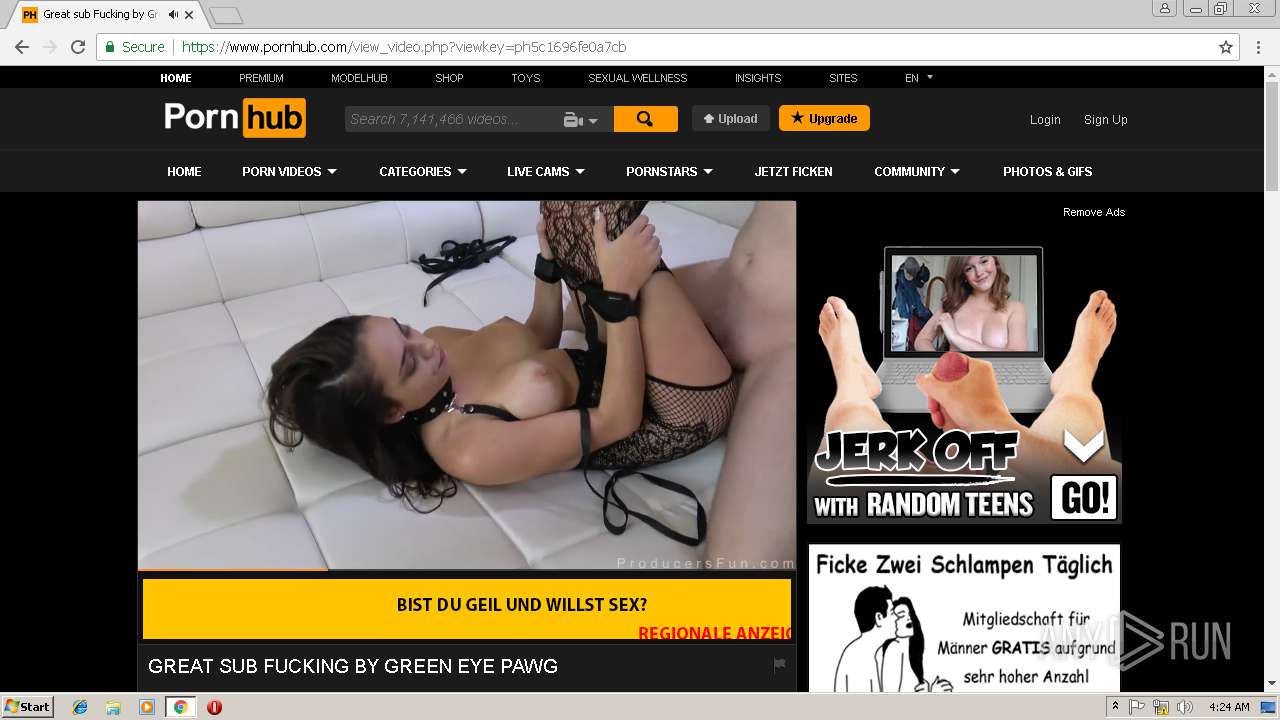
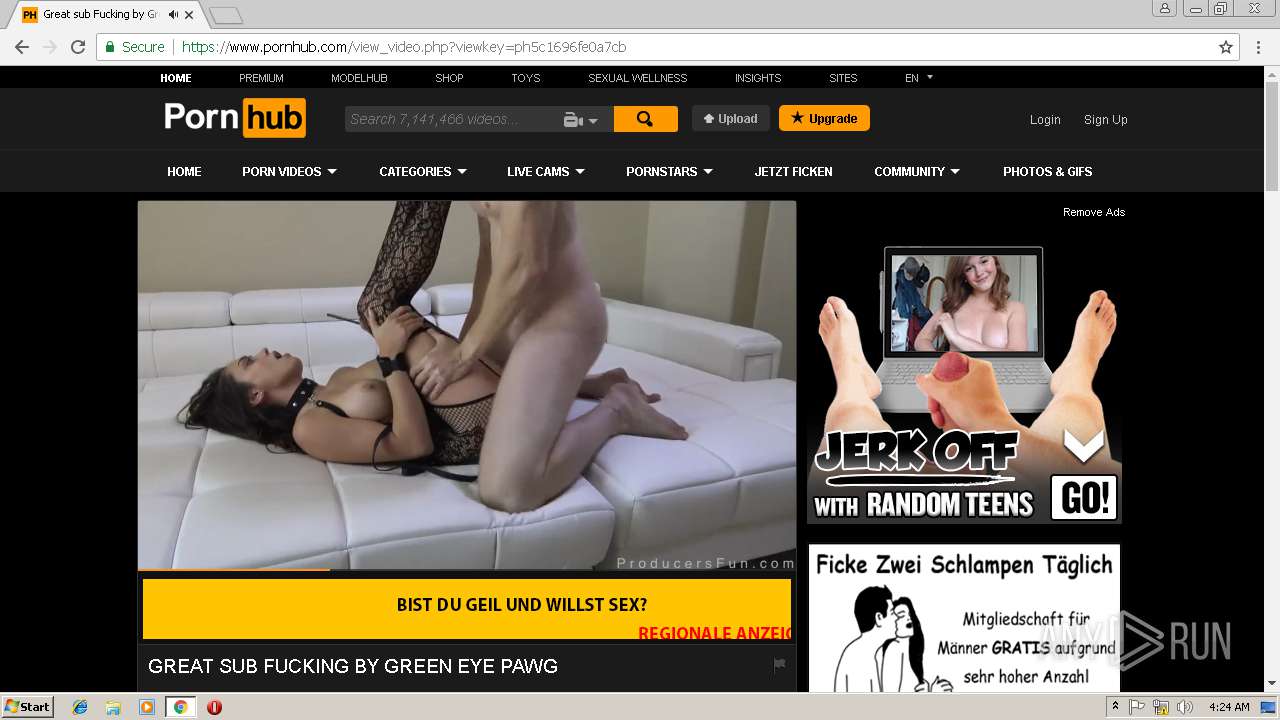
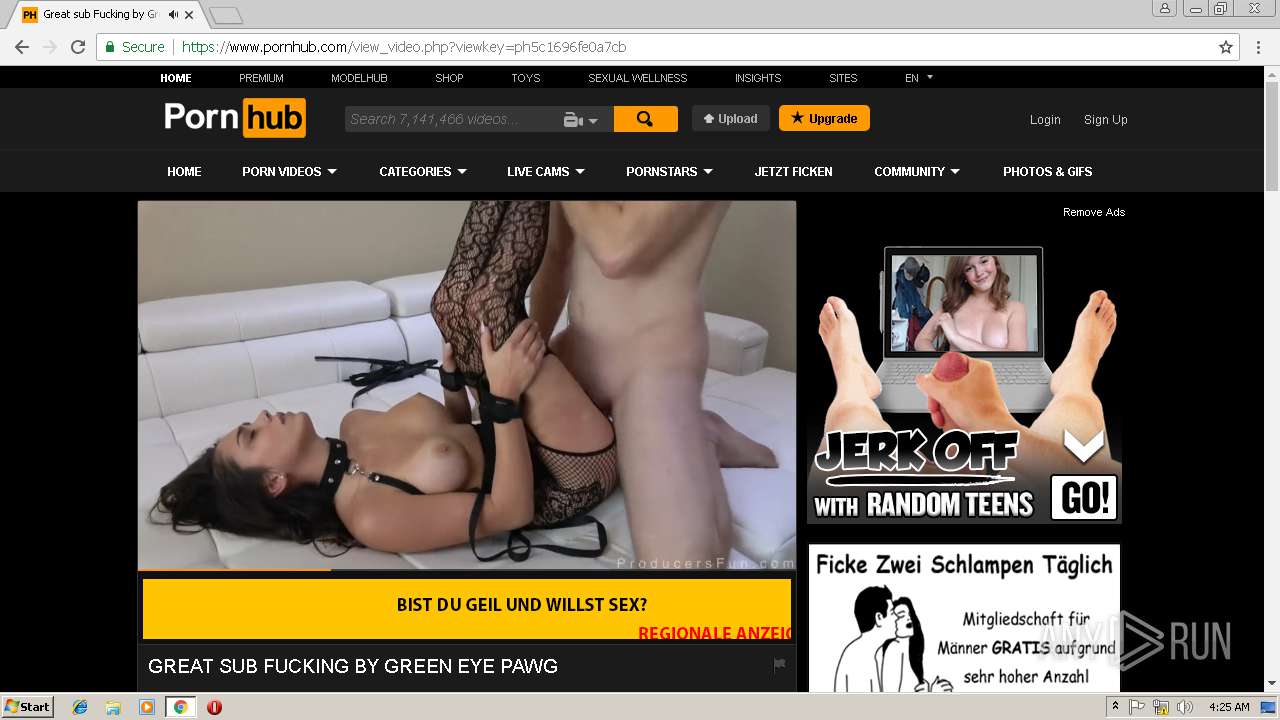
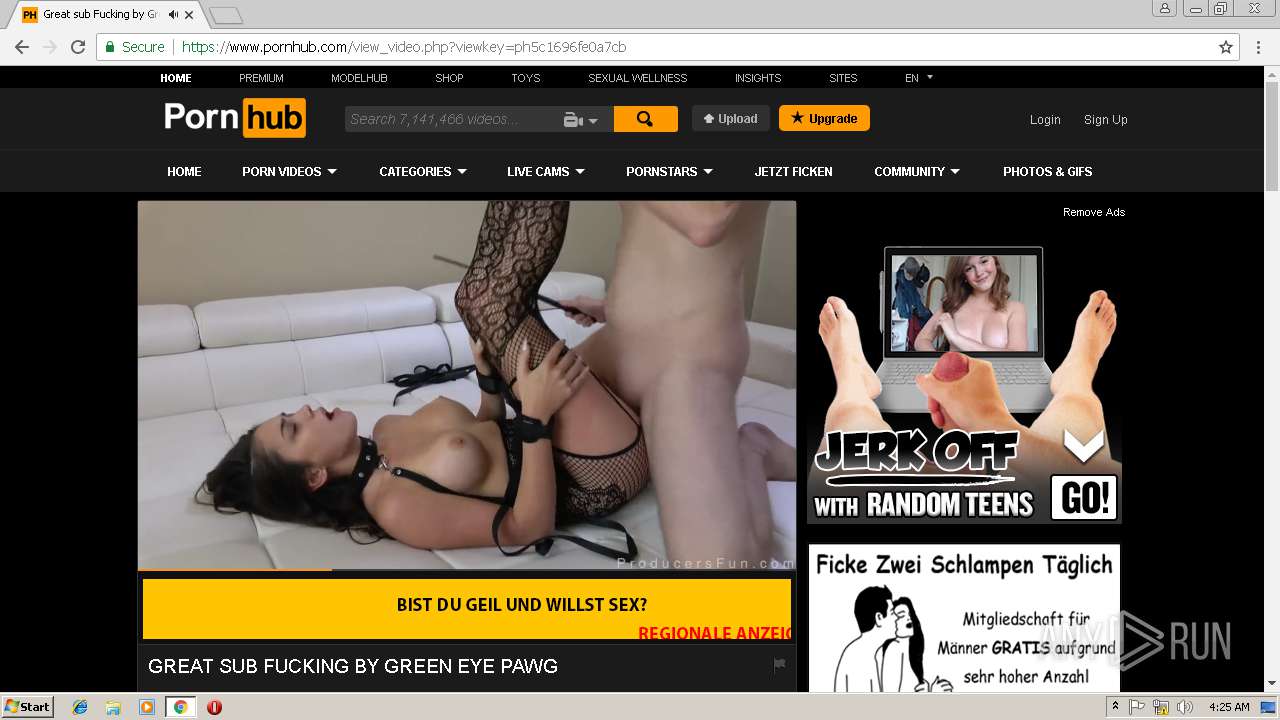
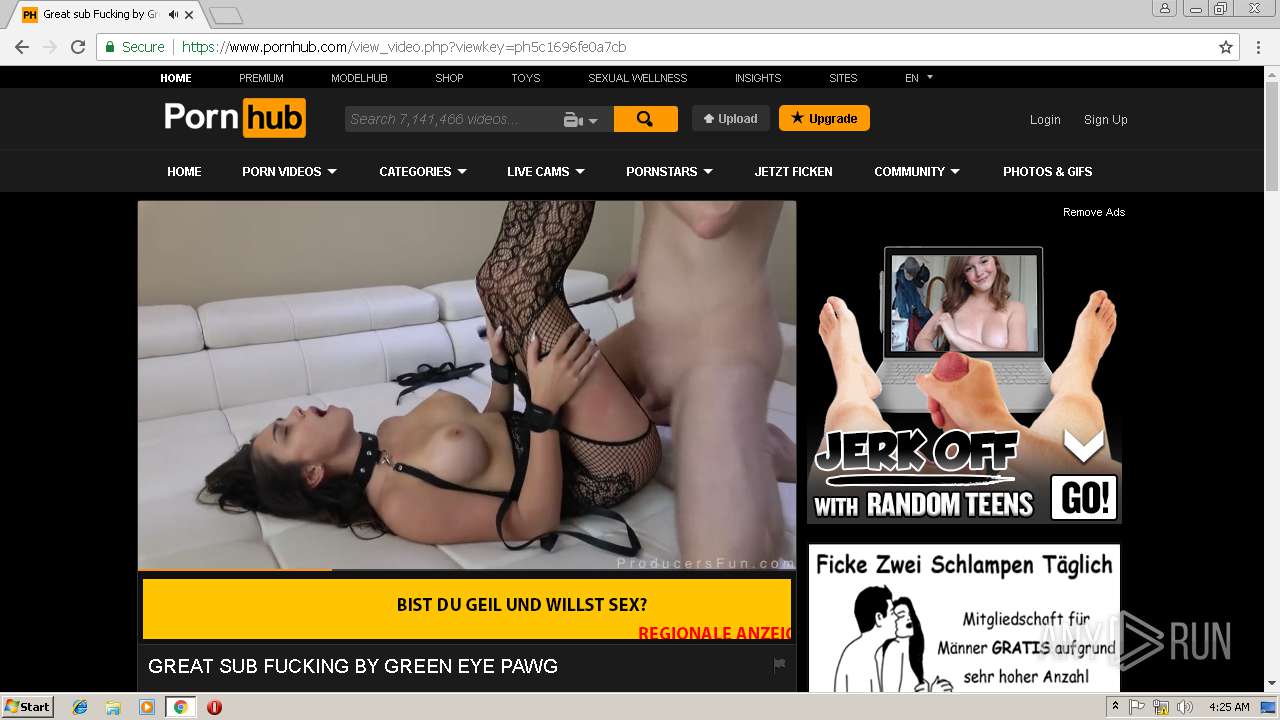
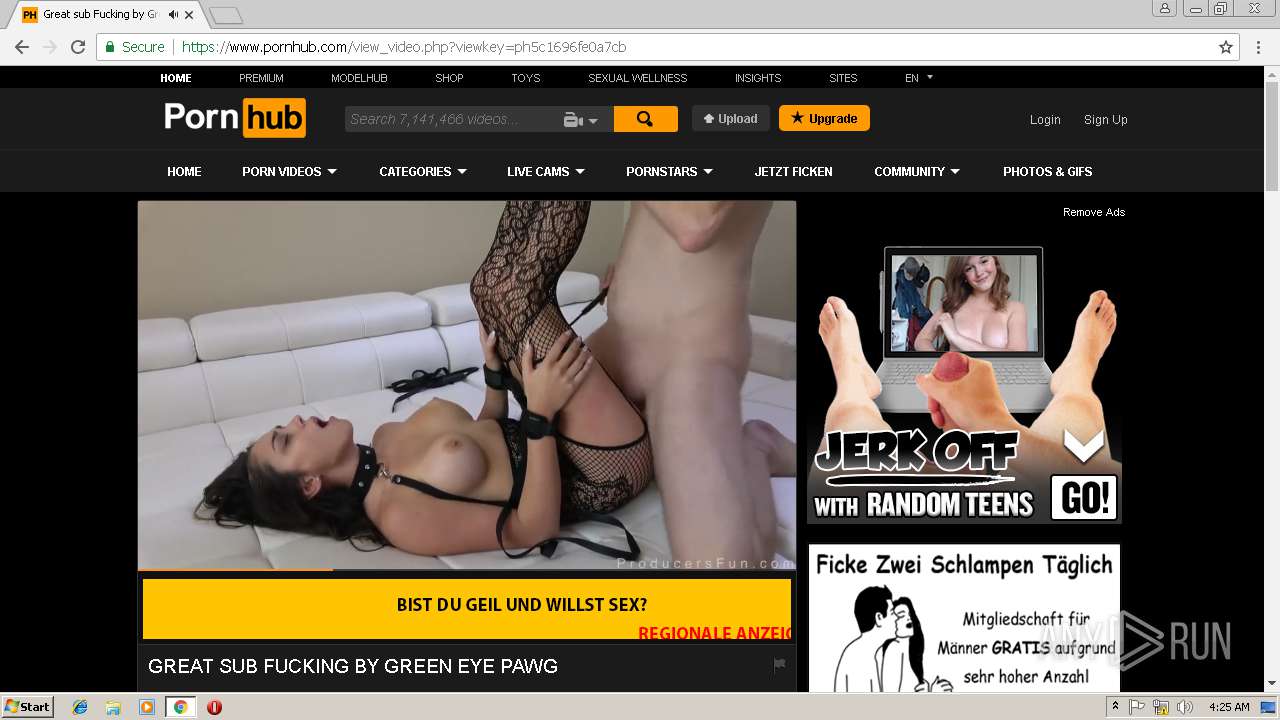
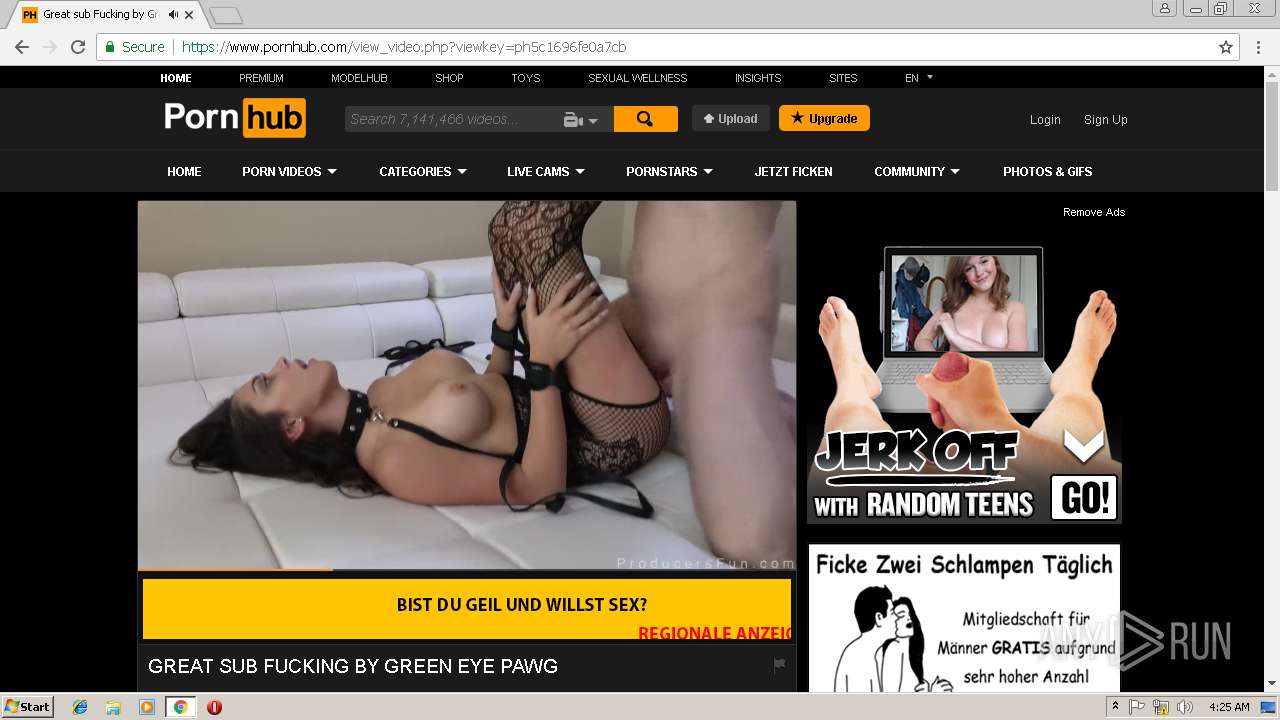
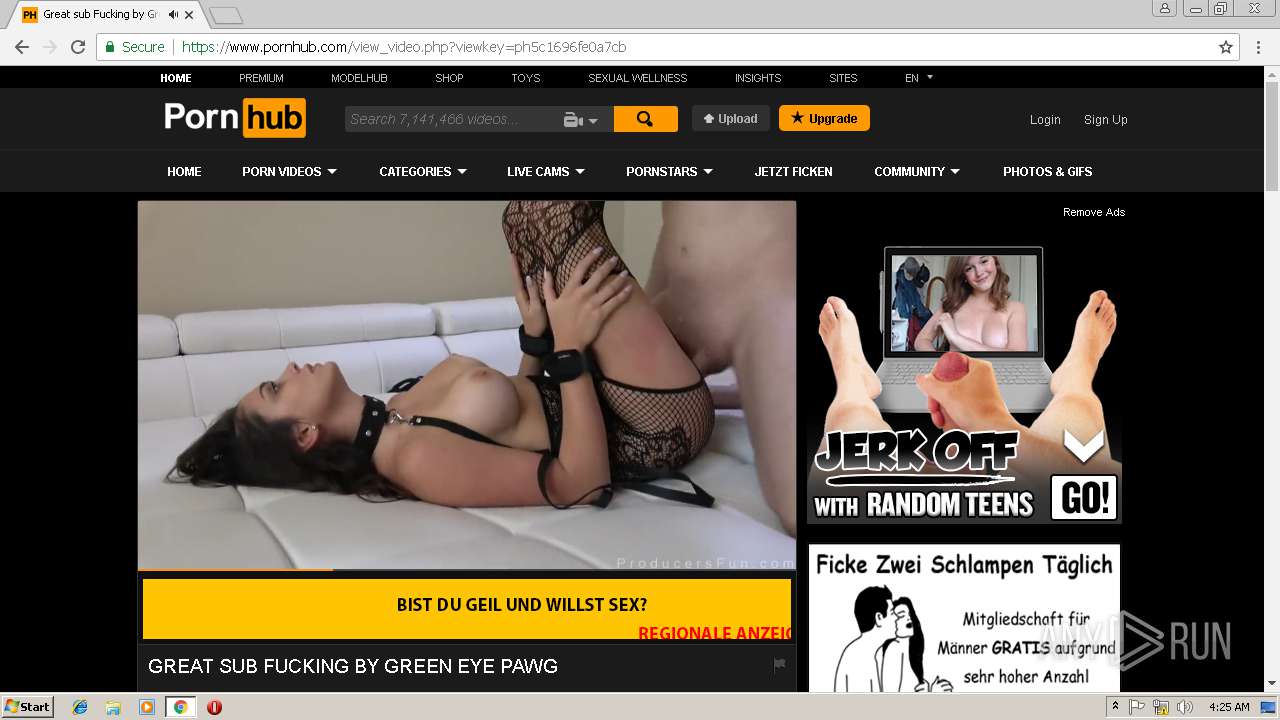
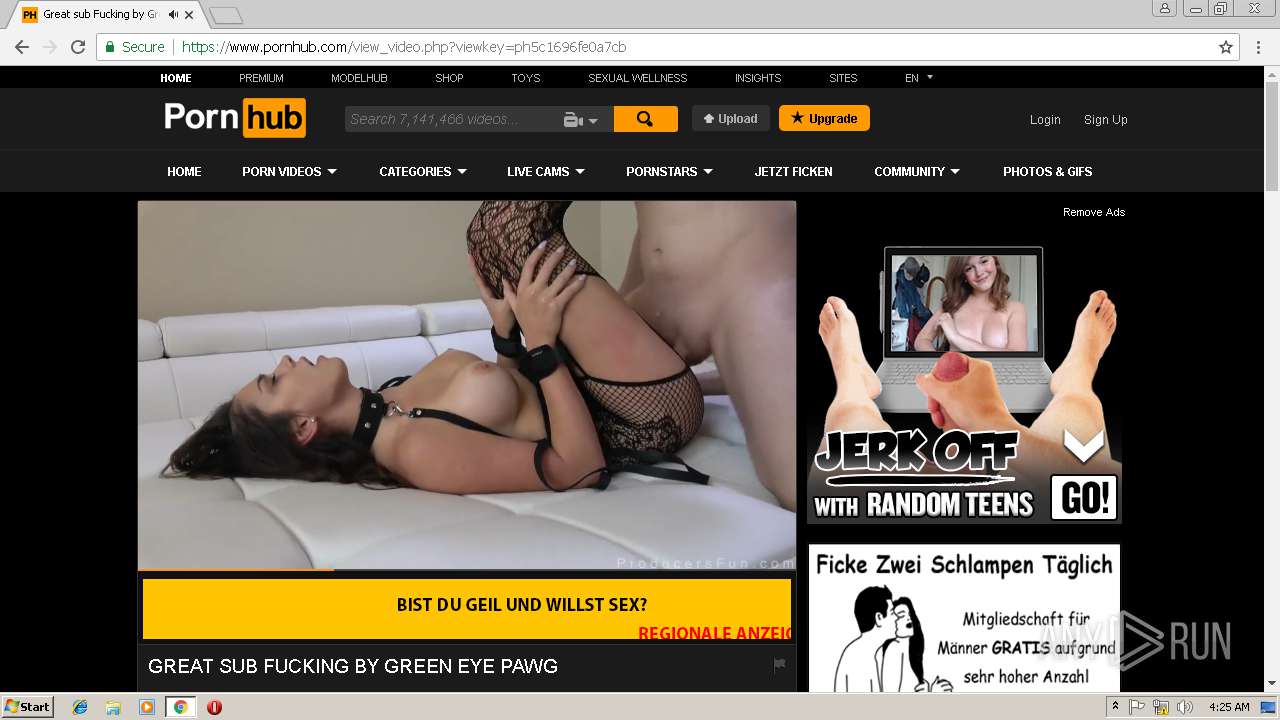
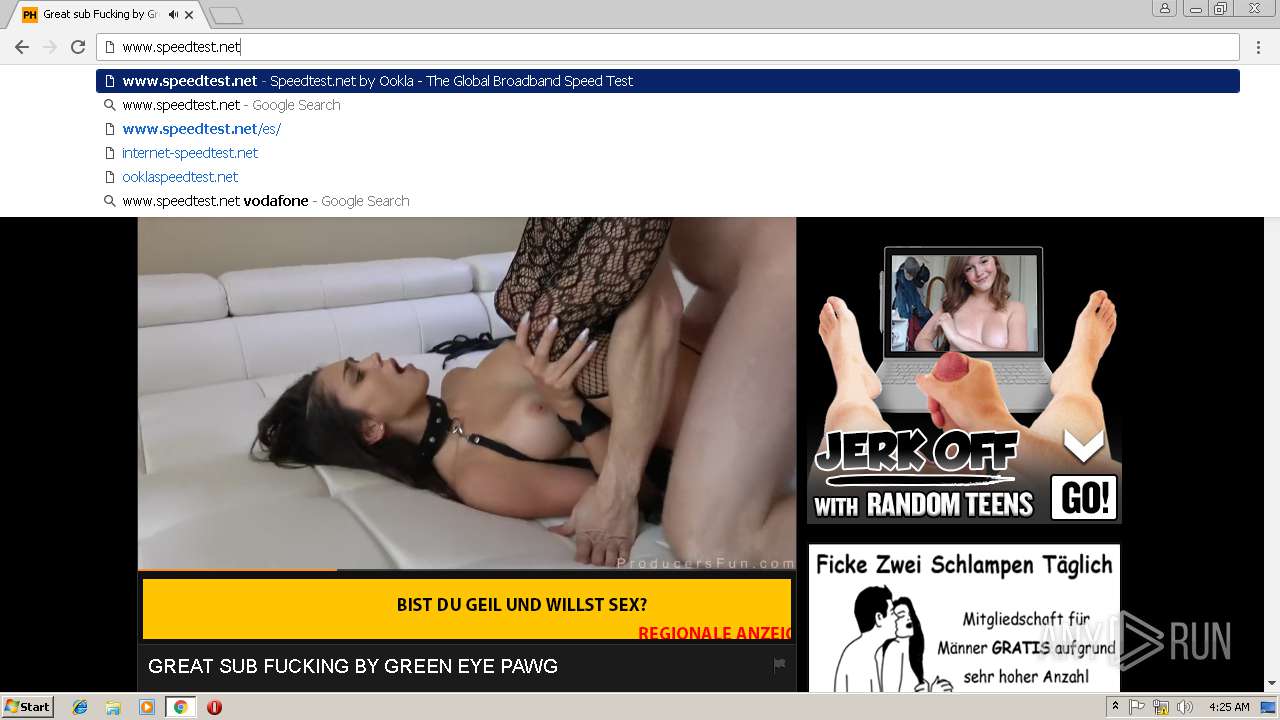
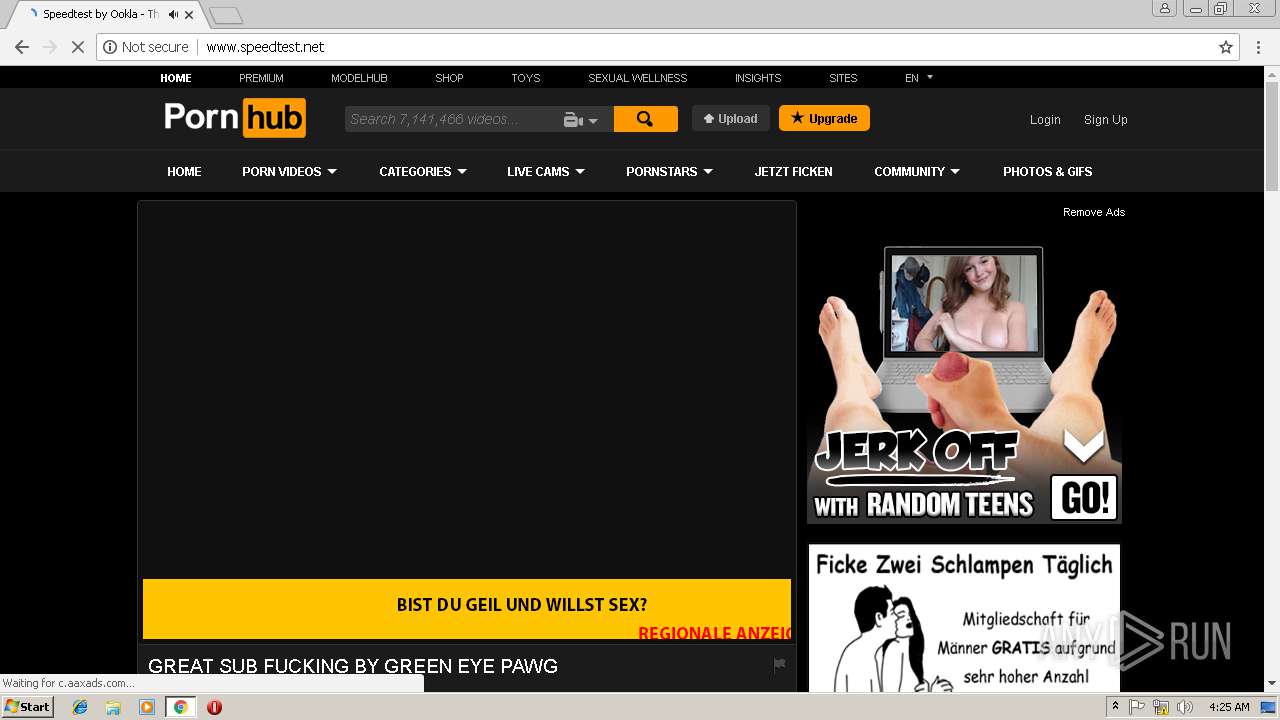
2072 | chrome.exe | GET | 301 | 216.18.168.16:80 | http://pornhub.com/ | US | — | — | whitelisted |
2072 | chrome.exe | GET | 302 | 23.38.55.104:80 | http://zdstatic.speedtest.net/jst/zdconsent.js?version=2579642 | NL | — | — | whitelisted |
2072 | chrome.exe | GET | 204 | 35.168.154.40:80 | http://l.betrad.com/site/v3/660/150/3/1/3/2/18610?consent=0 | US | — | — | whitelisted |
2072 | chrome.exe | GET | 200 | 151.101.2.219:80 | http://b.cdnst.net/javascript/prebid.1.17.0.min.js | US | text | 43.1 Kb | whitelisted |
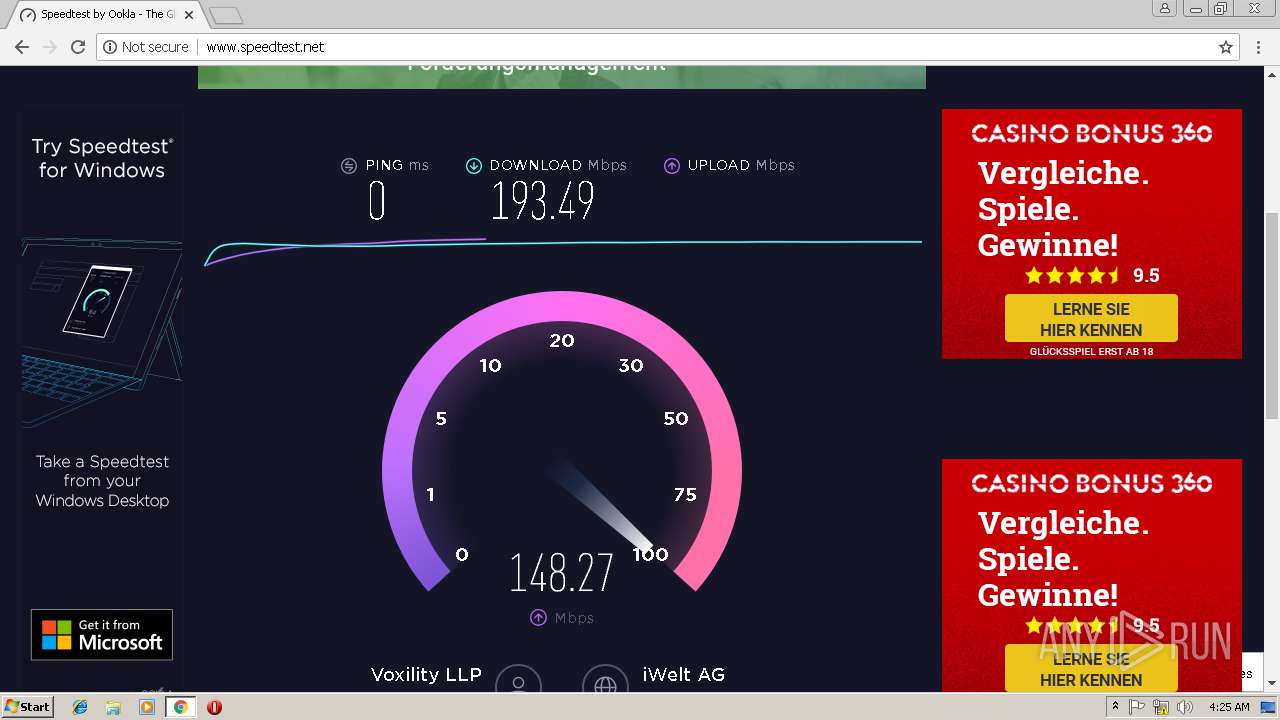
2072 | chrome.exe | GET | 200 | 151.101.2.219:80 | http://www.speedtest.net/ | US | html | 27.6 Kb | whitelisted |
2072 | chrome.exe | GET | 200 | 151.101.2.219:80 | http://b.cdnst.net/fonts/HCo_fonts.css | US | text | 108 Kb | whitelisted |
2072 | chrome.exe | GET | 200 | 23.45.98.199:80 | http://c.aaxads.com/aax.js?pub=AAXB54Y5G&hst=www.speedtest.net&ver=1.2 | NL | text | 90.4 Kb | whitelisted |
2072 | chrome.exe | GET | 200 | 151.101.1.194:80 | http://clarium.global.ssl.fastly.net/gpt/a/wrap.js | US | text | 9.79 Kb | whitelisted |
2072 | chrome.exe | GET | 200 | 23.38.55.104:80 | http://zdstatic.speedtest.net/jst/eu/zdconsent.js?version=2579642 | NL | text | 5.25 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2072 | chrome.exe | 216.58.208.35:443 | www.google.de | Google Inc. | US | whitelisted |
2072 | chrome.exe | 172.217.21.195:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2072 | chrome.exe | 172.217.23.164:443 | www.google.com | Google Inc. | US | whitelisted |
2072 | chrome.exe | 172.217.18.110:443 | apis.google.com | Google Inc. | US | whitelisted |
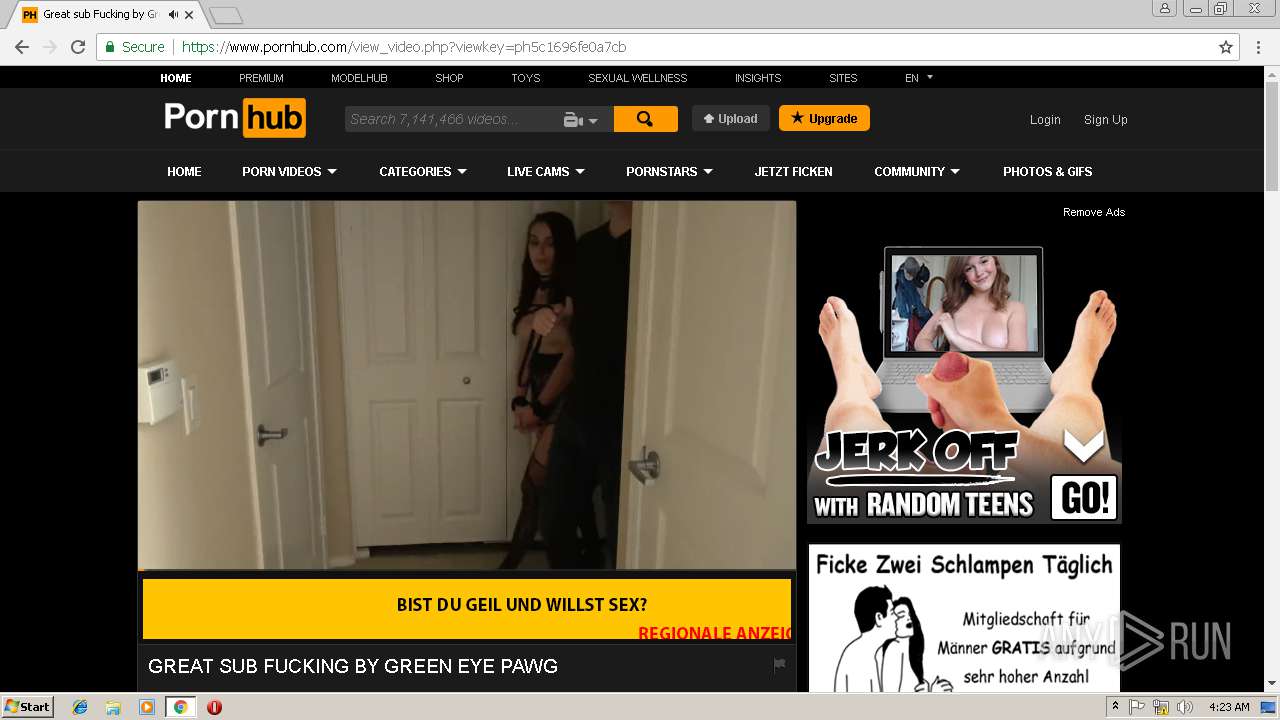
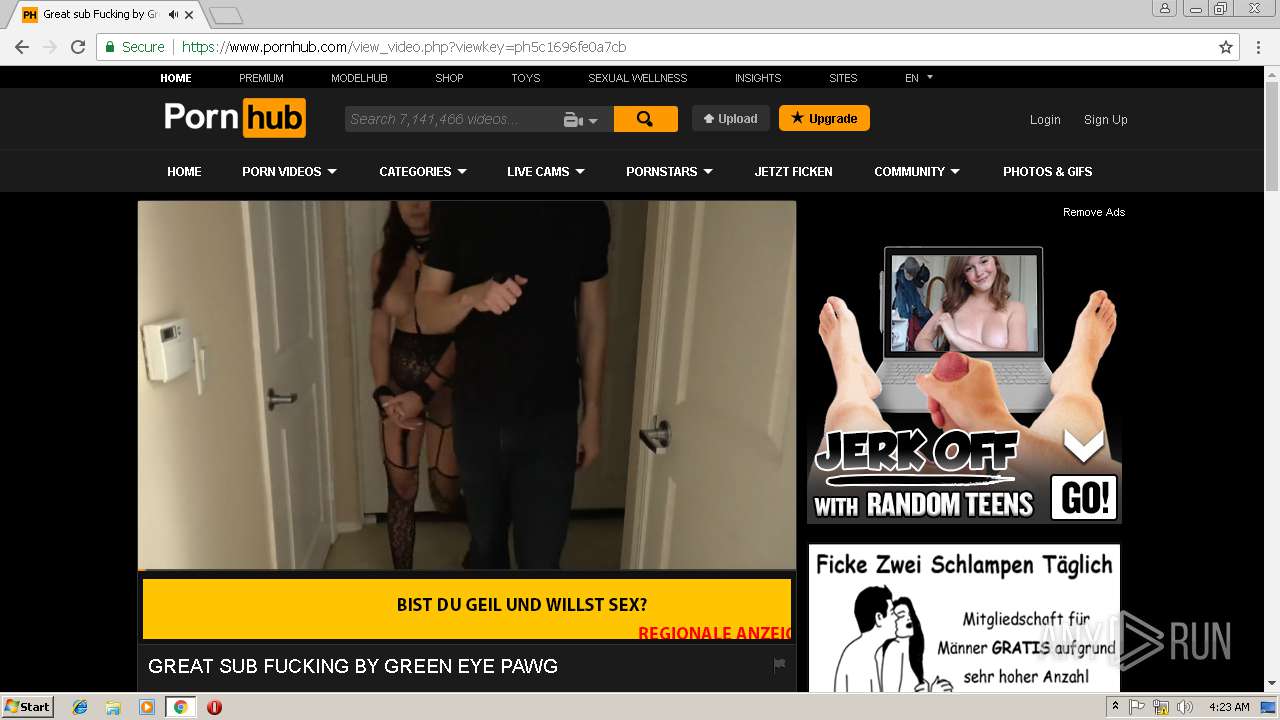
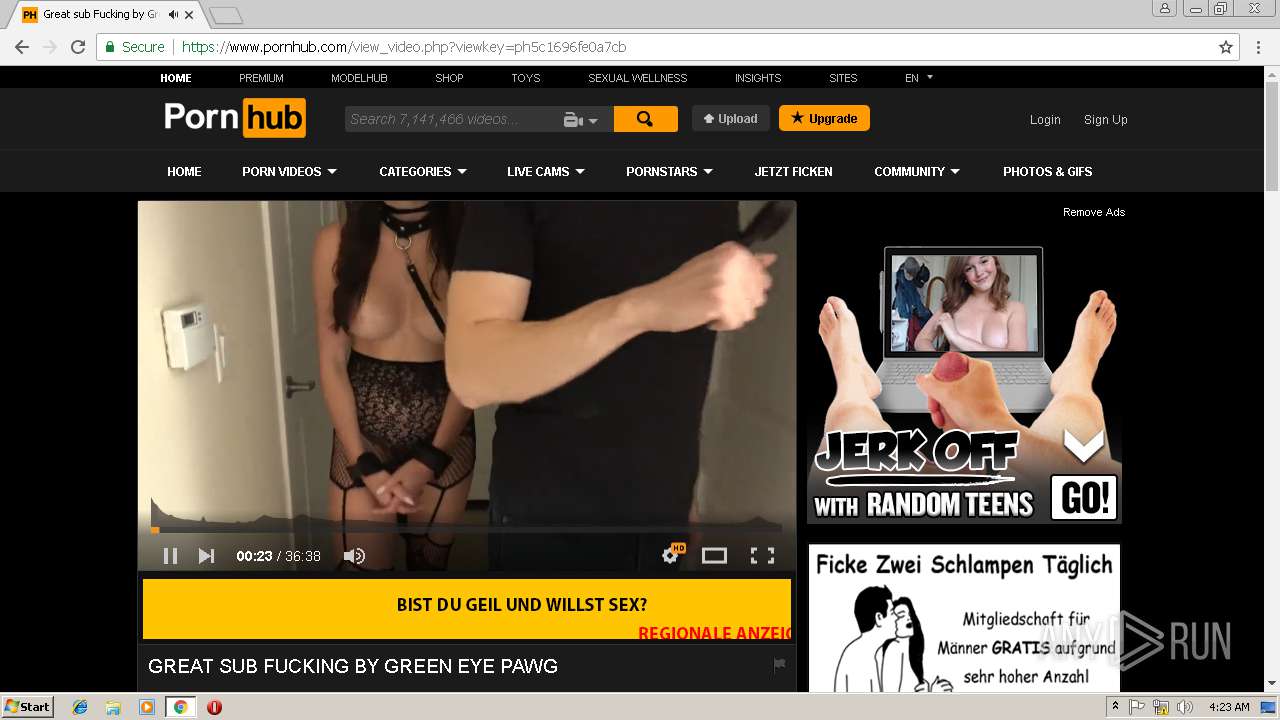
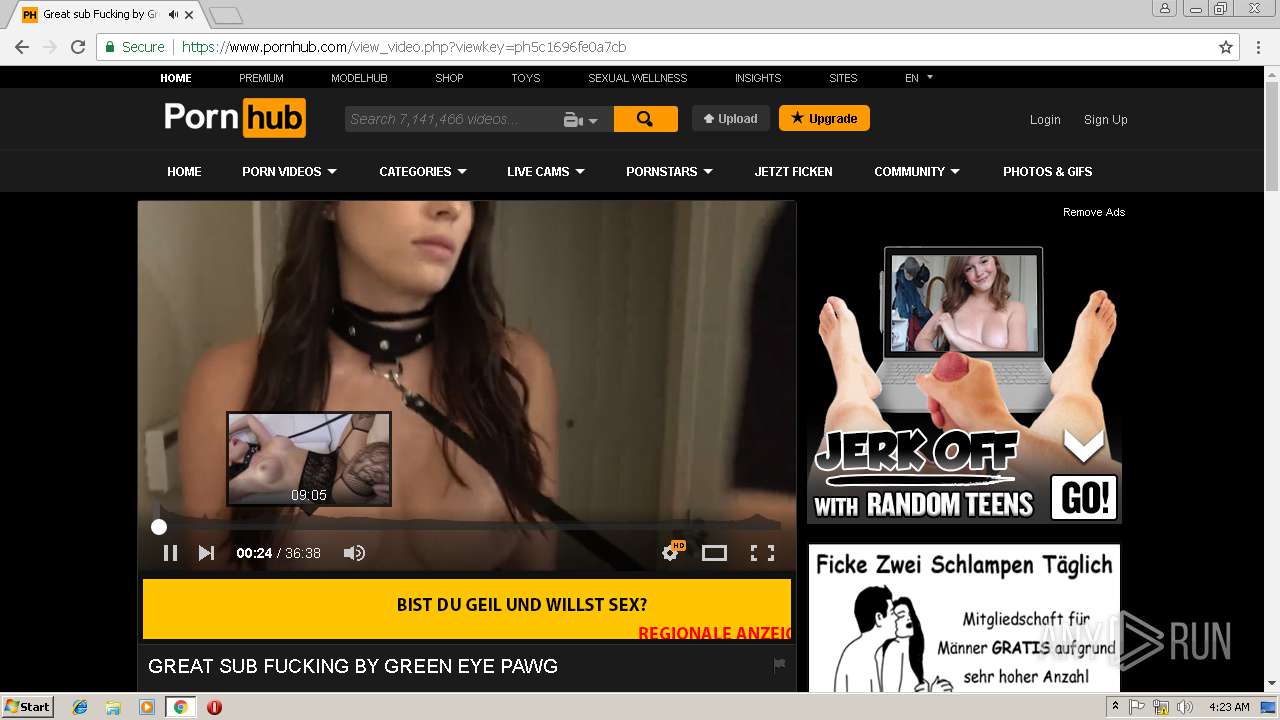
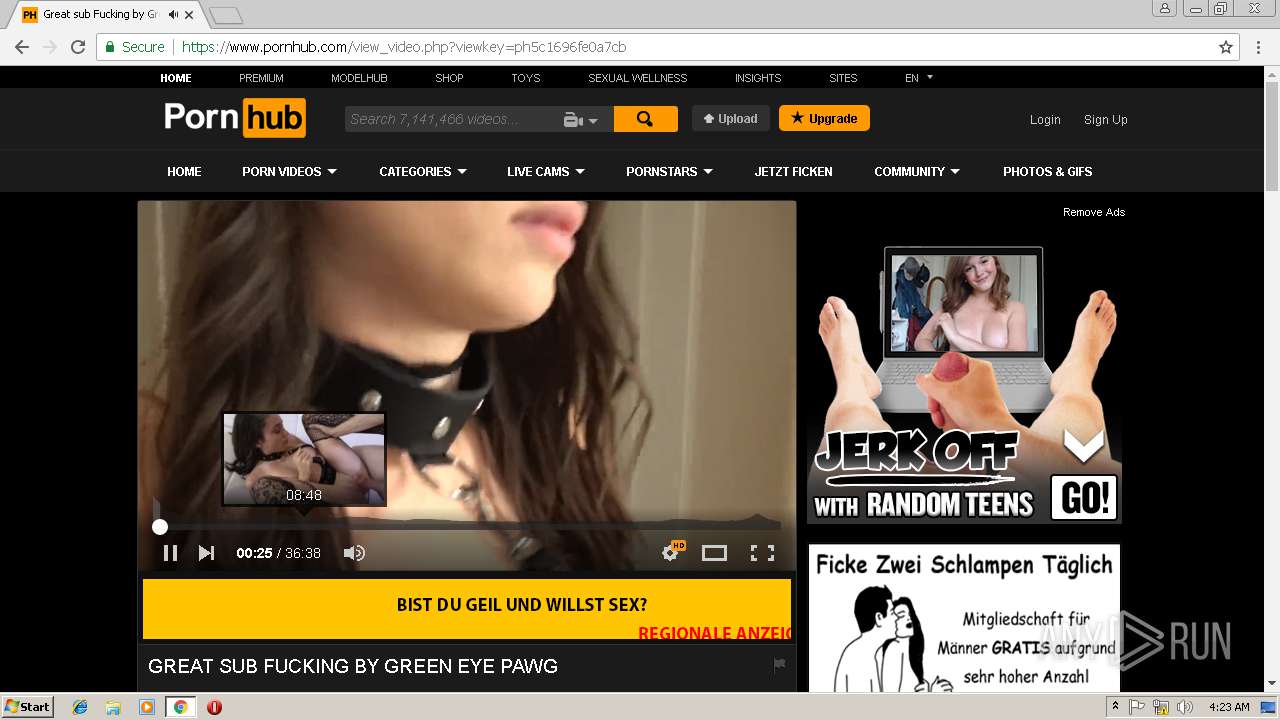
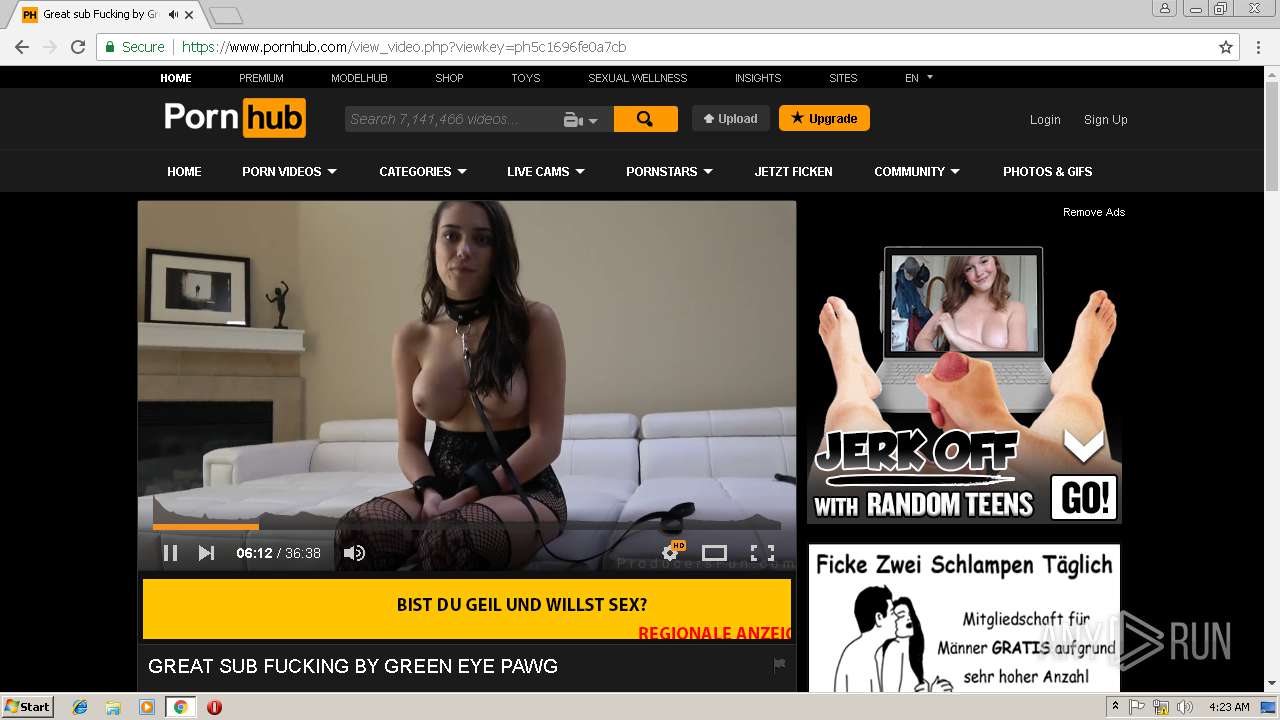
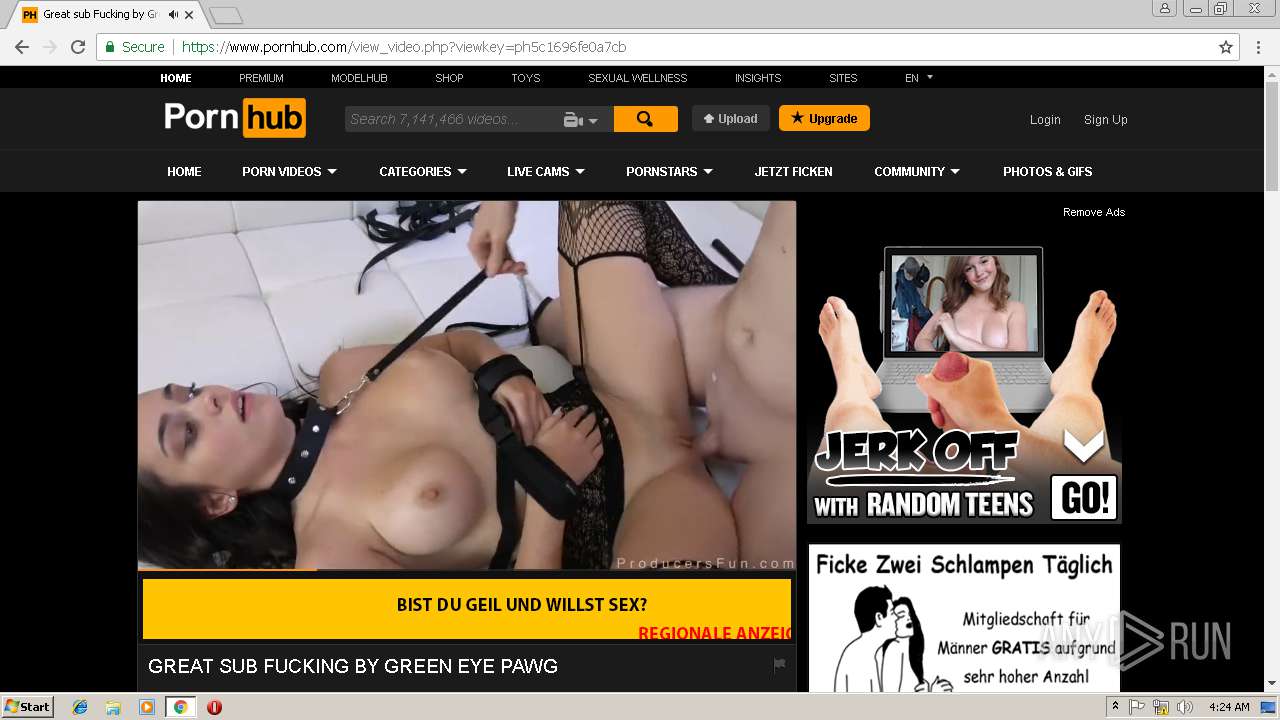
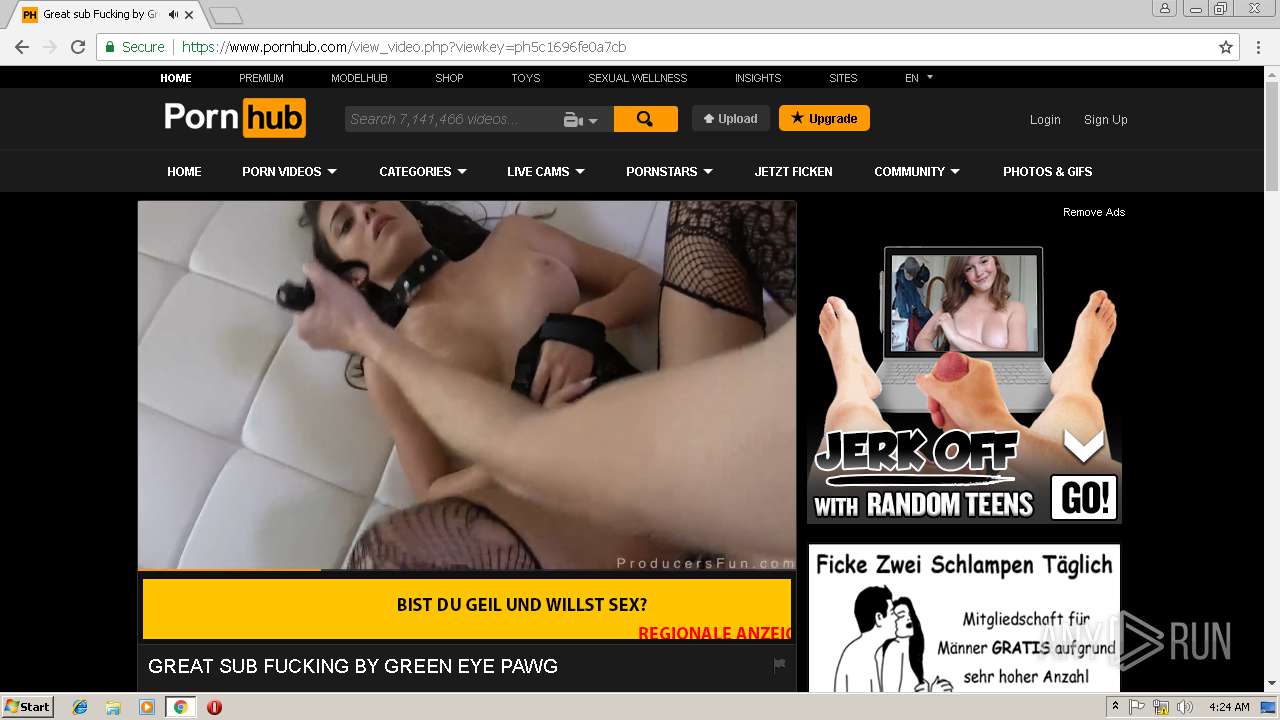
2072 | chrome.exe | 216.18.168.16:80 | pornhub.com | Reflected Networks, Inc. | US | suspicious |
2072 | chrome.exe | 216.18.168.16:443 | pornhub.com | Reflected Networks, Inc. | US | suspicious |
2072 | chrome.exe | 205.185.208.142:443 | di.phncdn.com | Highwinds Network Group, Inc. | US | suspicious |
2072 | chrome.exe | 205.185.208.85:443 | media.trafficjunky.net | Highwinds Network Group, Inc. | US | unknown |
2072 | chrome.exe | 104.16.222.128:443 | cdn.doublepimpssl.com | Cloudflare Inc | US | shared |
2072 | chrome.exe | 216.18.168.28:443 | hubt.pornhub.com | Reflected Networks, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.gstatic.com |
| whitelisted |
www.google.de |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
www.google.com |
| malicious |
pornhub.com |
| whitelisted |
www.pornhub.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2072 | chrome.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
2072 | chrome.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
2072 | chrome.exe | Misc activity | ET INFO JAVA - ClassID |