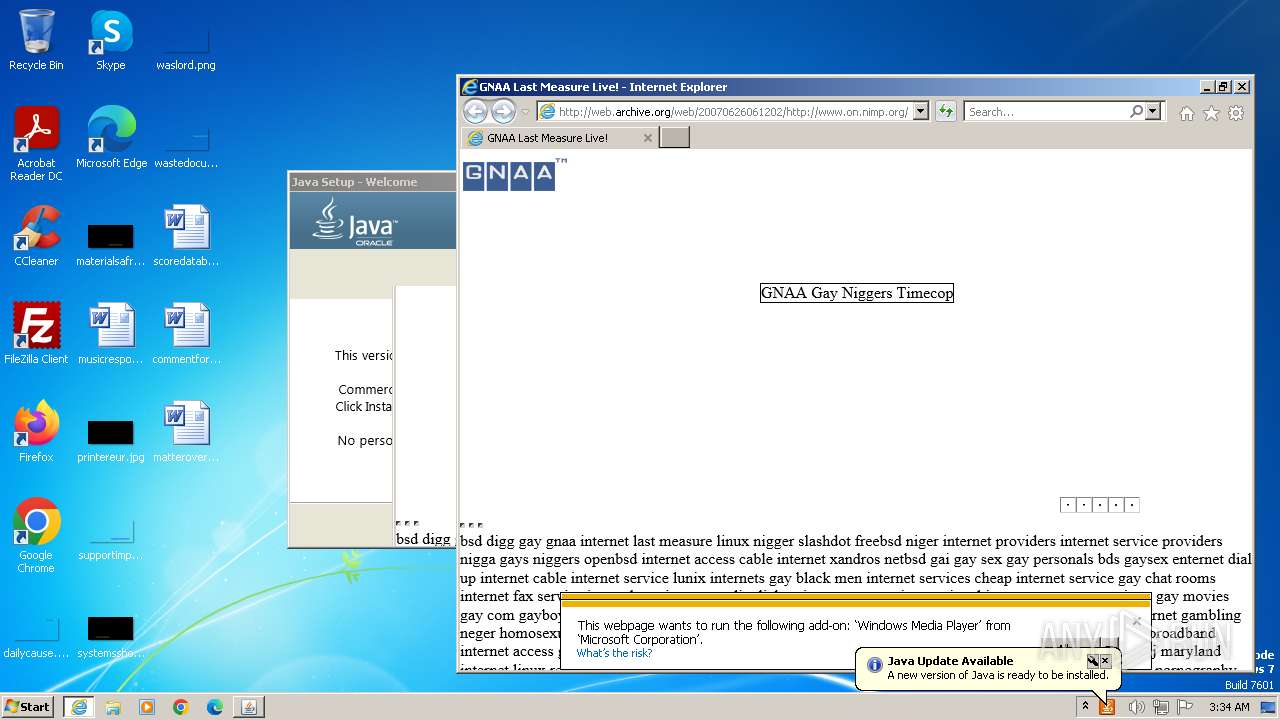
| URL: | web.archive.org/web/20070626061202/on.nimp.org |
| Full analysis: | https://app.any.run/tasks/de4e755c-62ca-4334-a54c-613ac5938d7d |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2023, 03:33:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 5695361D37FDE0A09E865386ED5A4446 |
| SHA1: | 0A528F17BE0069C3717327A4F00EE51C2C6A6DD8 |
| SHA256: | BC3D266C157282E9D8B7DE395D095CE0C49A48E1051E037E47629AD4B51C1531 |
| SSDEEP: | 3:fEhXJevS5dOVaUb+XCn:f+X8KqoUbf |
MALICIOUS
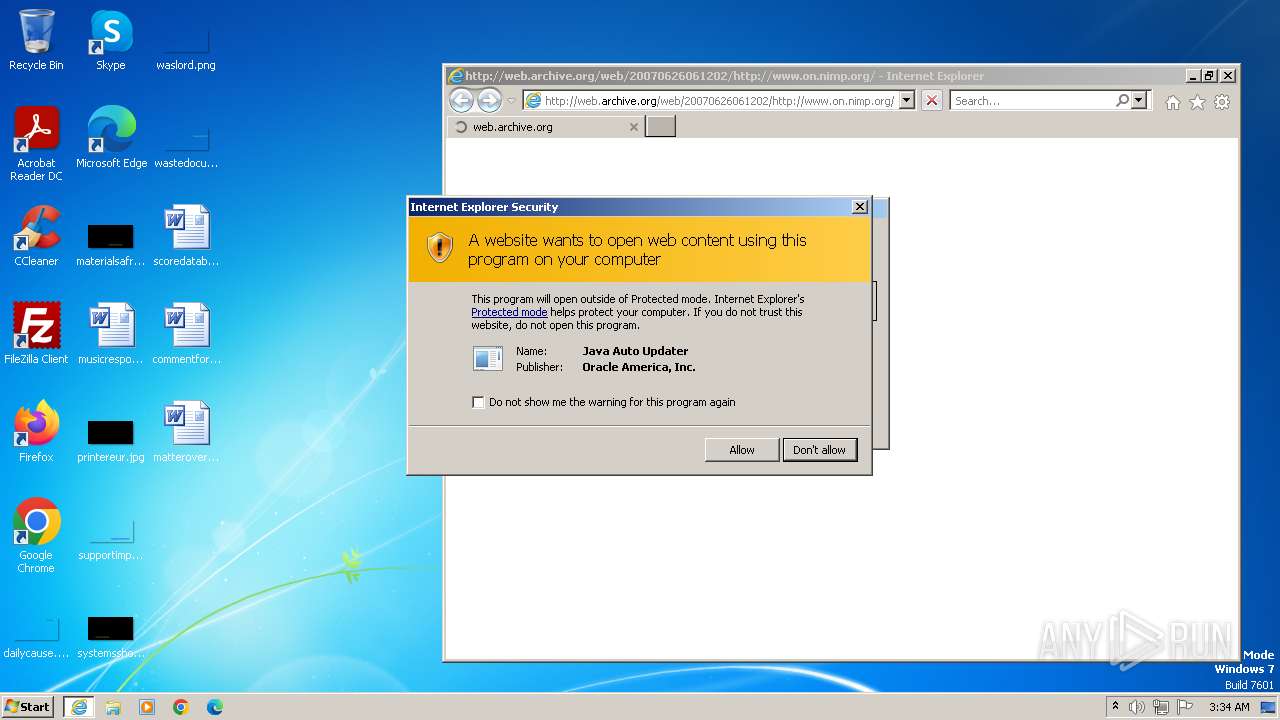
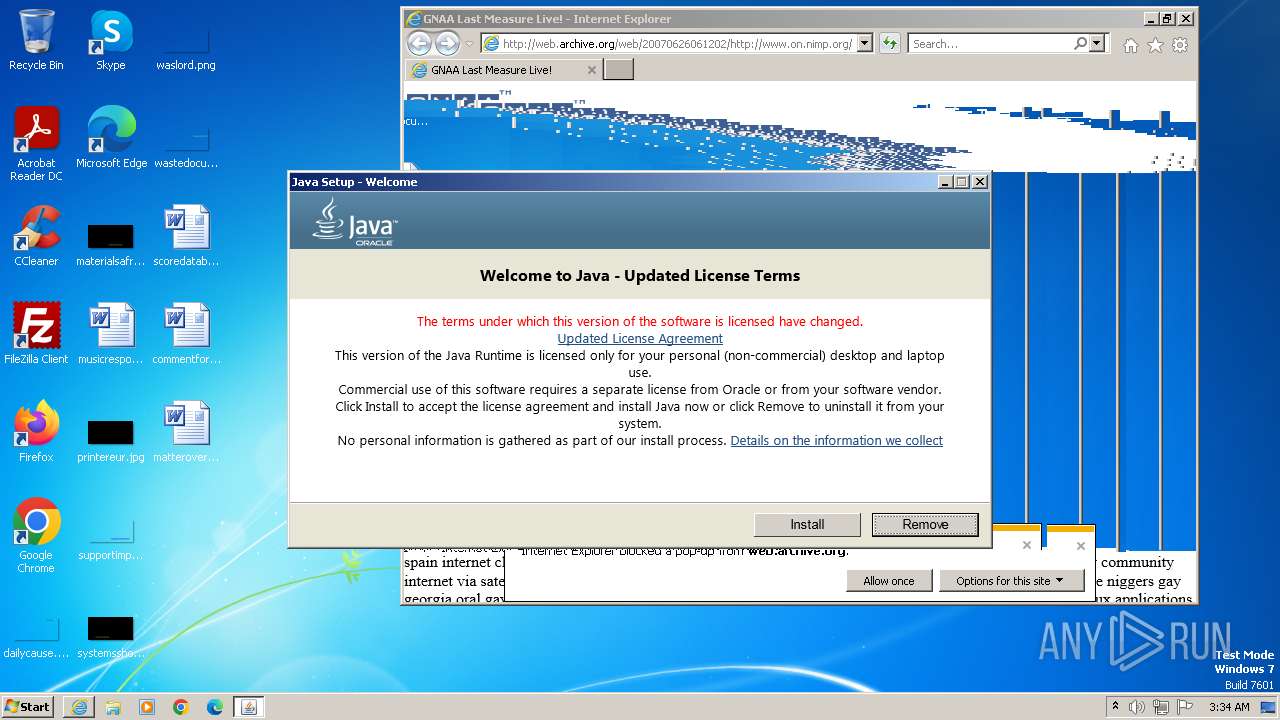
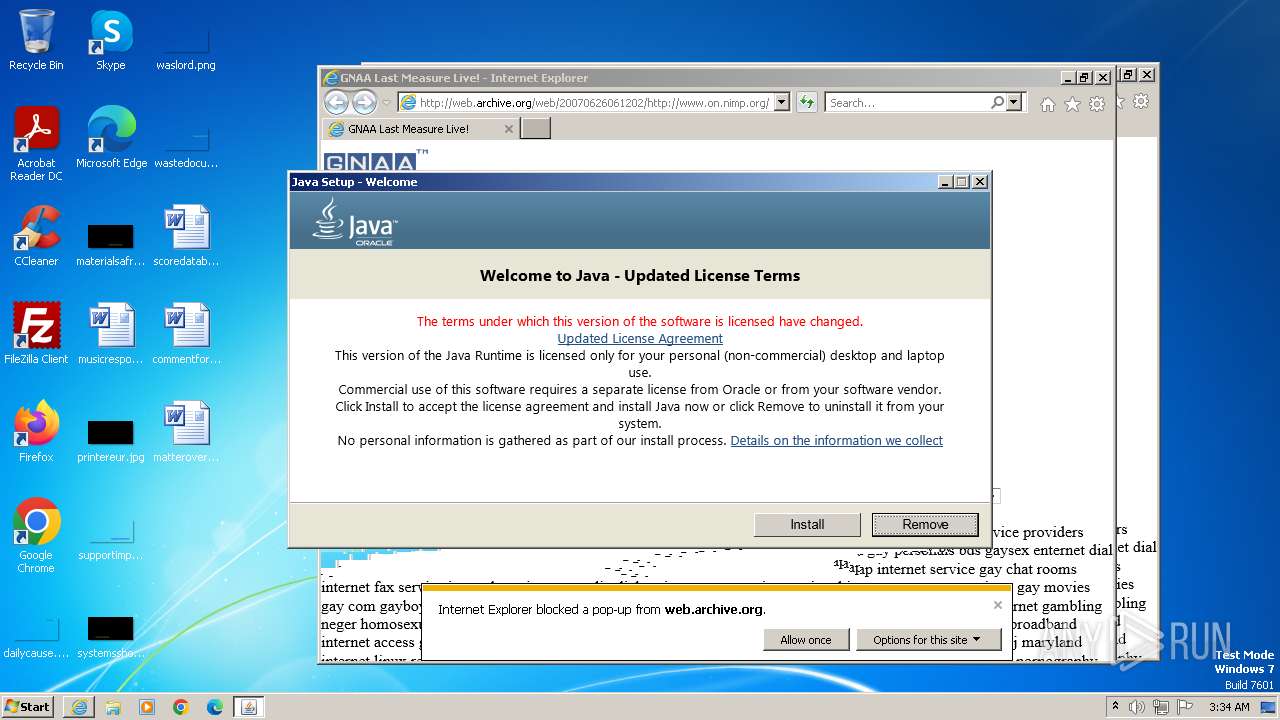
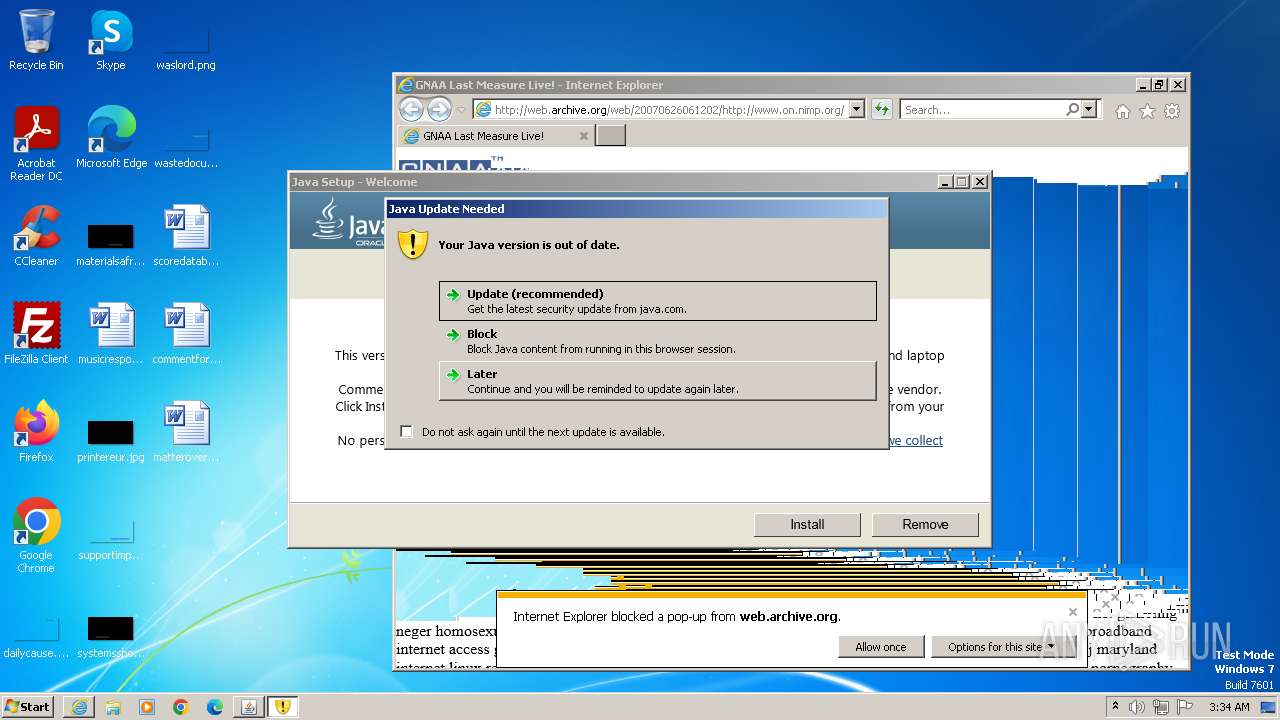
Drops the executable file immediately after the start
- jucheck.exe (PID: 3916)
- jre-8u391-windows-au.exe (PID: 2376)
SUSPICIOUS
Checks for Java to be installed
- javaw.exe (PID: 3140)
- javaw.exe (PID: 3084)
- javaw.exe (PID: 3684)
- jp2launcher.exe (PID: 2968)
- jp2launcher.exe (PID: 1872)
- jucheck.exe (PID: 3916)
- jp2launcher.exe (PID: 1828)
- javaw.exe (PID: 2408)
- javaw.exe (PID: 2400)
- javaw.exe (PID: 3976)
- jp2launcher.exe (PID: 1608)
- jucheck.exe (PID: 3048)
- jp2launcher.exe (PID: 1936)
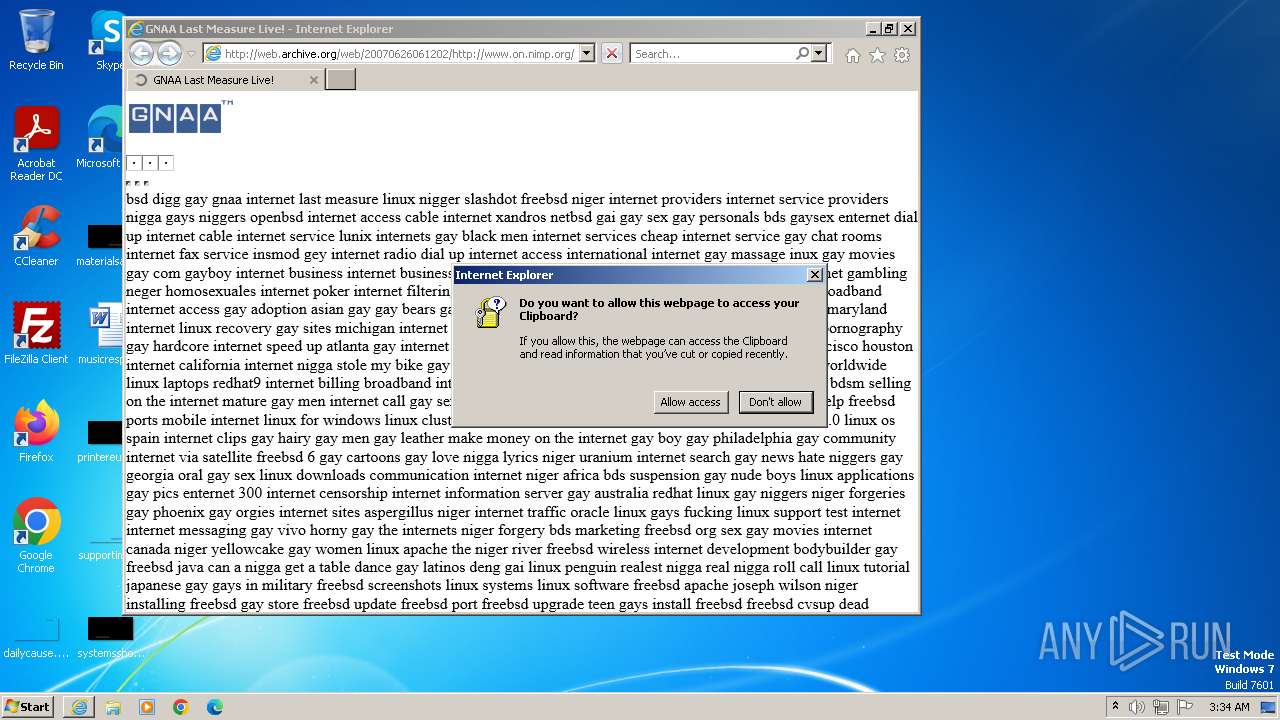
Reads the Internet Settings
- jucheck.exe (PID: 3916)
- jp2launcher.exe (PID: 2968)
- jp2launcher.exe (PID: 1872)
- jre-8u391-windows-au.exe (PID: 2500)
- jucheck.exe (PID: 3048)
- jp2launcher.exe (PID: 1608)
Reads security settings of Internet Explorer
- jucheck.exe (PID: 3916)
- jre-8u391-windows-au.exe (PID: 2500)
- jucheck.exe (PID: 3048)
Checks Windows Trust Settings
- jucheck.exe (PID: 3916)
- jre-8u391-windows-au.exe (PID: 2500)
- jucheck.exe (PID: 3048)
Reads settings of System Certificates
- jucheck.exe (PID: 3916)
- jp2launcher.exe (PID: 2968)
- jre-8u391-windows-au.exe (PID: 2500)
- jucheck.exe (PID: 3048)
- jp2launcher.exe (PID: 1608)
- jp2launcher.exe (PID: 1872)
Reads Microsoft Outlook installation path
- jucheck.exe (PID: 3916)
- jre-8u391-windows-au.exe (PID: 2500)
- jucheck.exe (PID: 3048)
Reads Internet Explorer settings
- jucheck.exe (PID: 3916)
- jre-8u391-windows-au.exe (PID: 2500)
- jucheck.exe (PID: 3048)
INFO
Application launched itself
- iexplore.exe (PID: 564)
Reads the computer name
- wmpnscfg.exe (PID: 3832)
- javaw.exe (PID: 3140)
- javaw.exe (PID: 3084)
- javaw.exe (PID: 3684)
- jucheck.exe (PID: 3916)
- jp2launcher.exe (PID: 2968)
- jp2launcher.exe (PID: 1872)
- jre-8u391-windows-au.exe (PID: 2376)
- jre-8u391-windows-au.exe (PID: 2500)
- javaw.exe (PID: 2408)
- javaw.exe (PID: 2400)
- jucheck.exe (PID: 3048)
- javaw.exe (PID: 3976)
- jp2launcher.exe (PID: 1608)
Manual execution by a user
- wmpnscfg.exe (PID: 3832)
Create files in a temporary directory
- javaw.exe (PID: 3140)
- javaw.exe (PID: 3684)
- javaw.exe (PID: 3084)
- jucheck.exe (PID: 3916)
- jp2launcher.exe (PID: 2968)
- jp2launcher.exe (PID: 1872)
- jre-8u391-windows-au.exe (PID: 2376)
- javaw.exe (PID: 2408)
- javaw.exe (PID: 2400)
- javaw.exe (PID: 3976)
- jp2launcher.exe (PID: 1608)
- jucheck.exe (PID: 3048)
Checks supported languages
- javaw.exe (PID: 3140)
- javaw.exe (PID: 3084)
- javaw.exe (PID: 3684)
- jucheck.exe (PID: 3916)
- jp2launcher.exe (PID: 2968)
- javaws.exe (PID: 3448)
- jp2launcher.exe (PID: 1872)
- jre-8u391-windows-au.exe (PID: 2376)
- jre-8u391-windows-au.exe (PID: 2500)
- jp2launcher.exe (PID: 1828)
- javaw.exe (PID: 2408)
- javaw.exe (PID: 2400)
- javaw.exe (PID: 3976)
- jucheck.exe (PID: 3048)
- javaws.exe (PID: 2764)
- jp2launcher.exe (PID: 1608)
- wmpnscfg.exe (PID: 3832)
- jp2launcher.exe (PID: 1936)
Creates files in the program directory
- javaw.exe (PID: 3140)
Reads the machine GUID from the registry
- jucheck.exe (PID: 3916)
- jp2launcher.exe (PID: 2968)
- jre-8u391-windows-au.exe (PID: 2500)
- jucheck.exe (PID: 3048)
- jp2launcher.exe (PID: 1608)
- jp2launcher.exe (PID: 1872)
Checks proxy server information
- jucheck.exe (PID: 3916)
- jp2launcher.exe (PID: 2968)
- jp2launcher.exe (PID: 1872)
- jre-8u391-windows-au.exe (PID: 2500)
- jucheck.exe (PID: 3048)
- jp2launcher.exe (PID: 1608)
Creates files or folders in the user directory
- jucheck.exe (PID: 3916)
- jp2launcher.exe (PID: 2968)
- jre-8u391-windows-au.exe (PID: 2500)
- jucheck.exe (PID: 3048)
Reads Internet Explorer settings
- OUTLOOK.EXE (PID: 2368)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
76
Monitored processes
31
Malicious processes
12
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
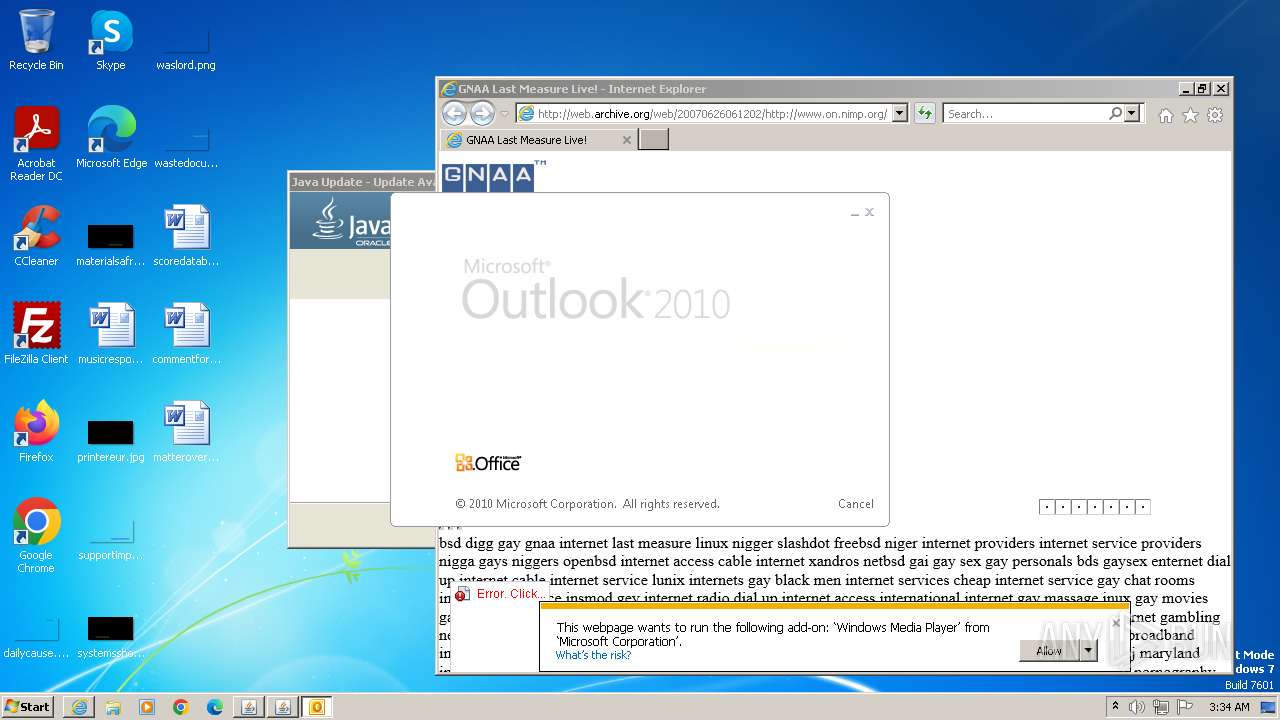
| 564 | "C:\Program Files\Internet Explorer\iexplore.exe" "web.archive.org/web/20070626061202/on.nimp.org" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
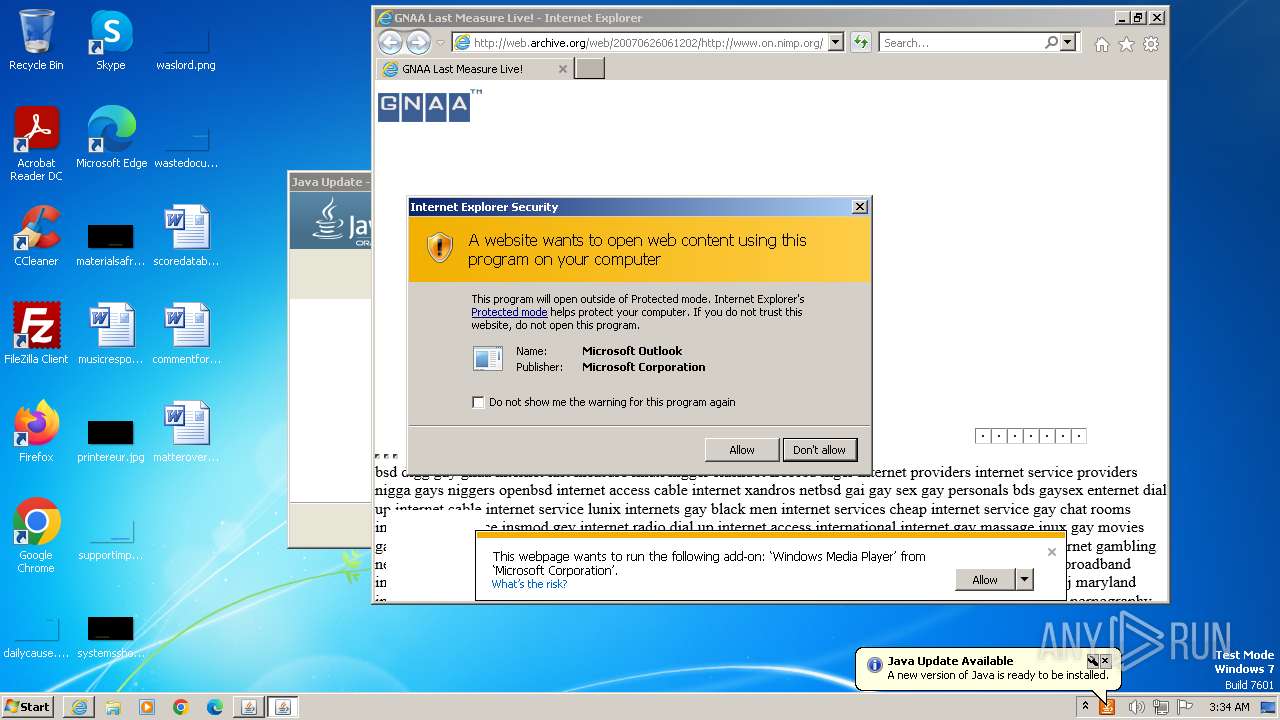
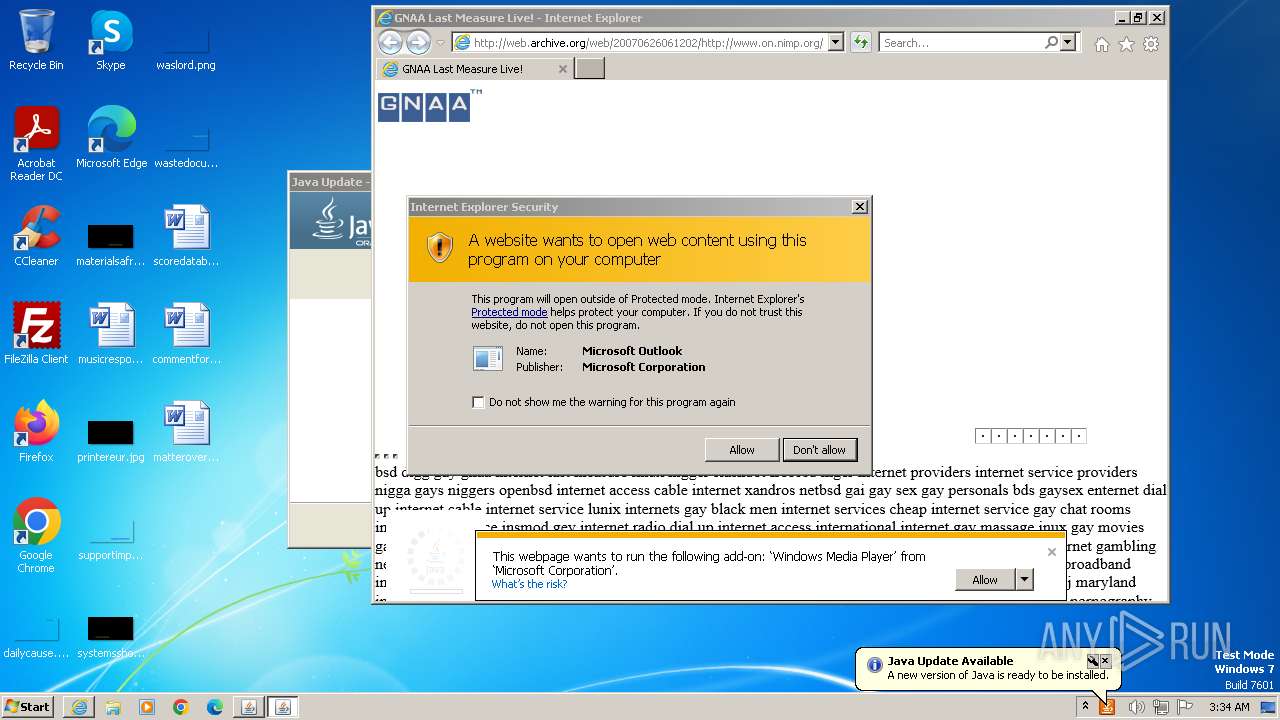
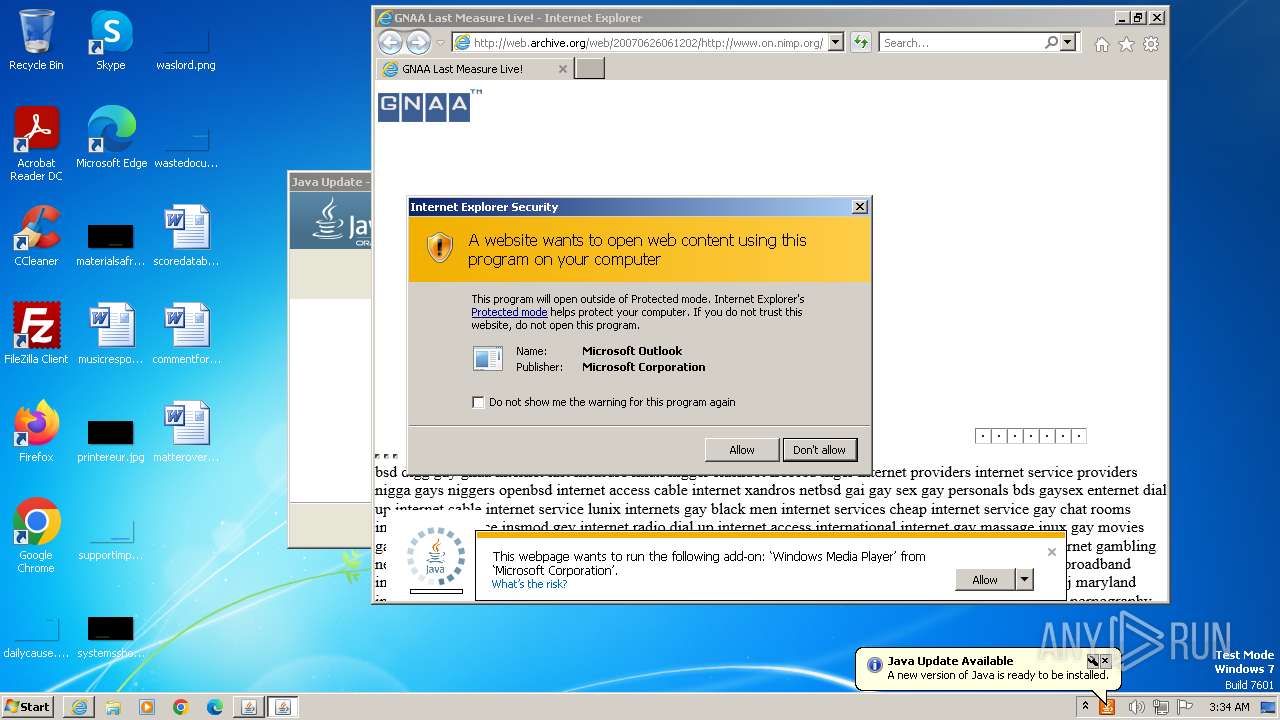
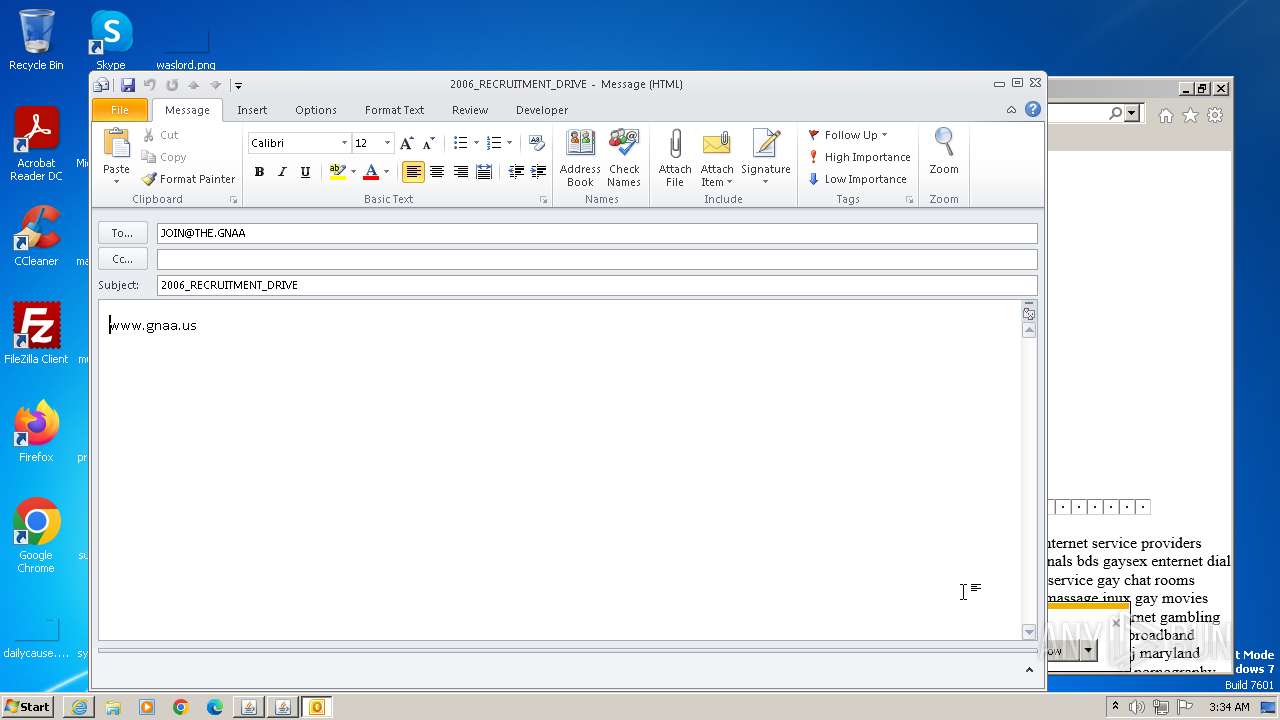
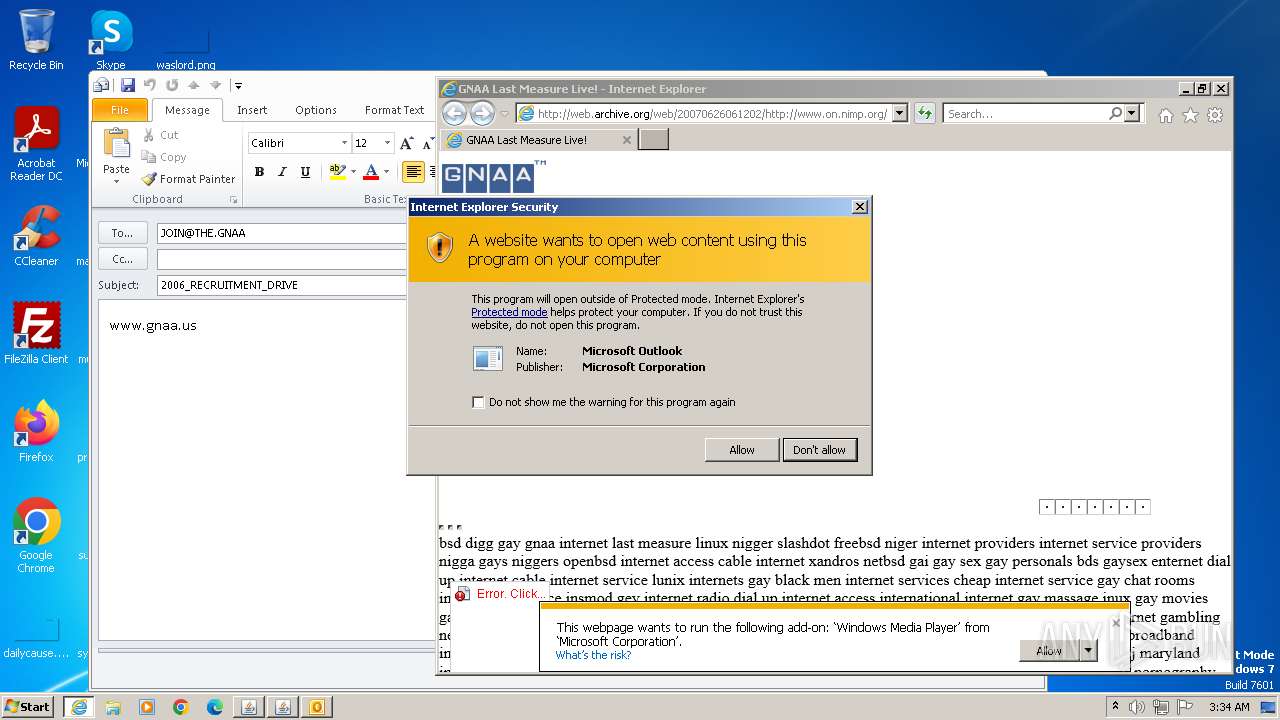
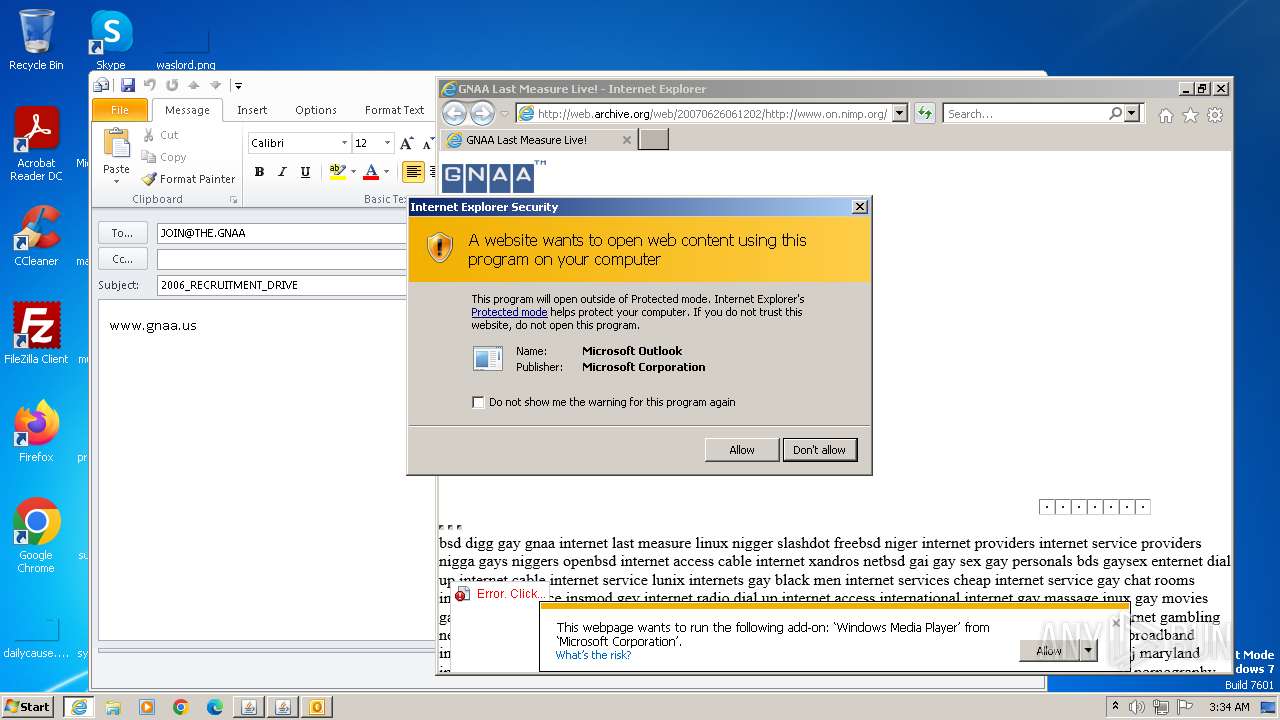
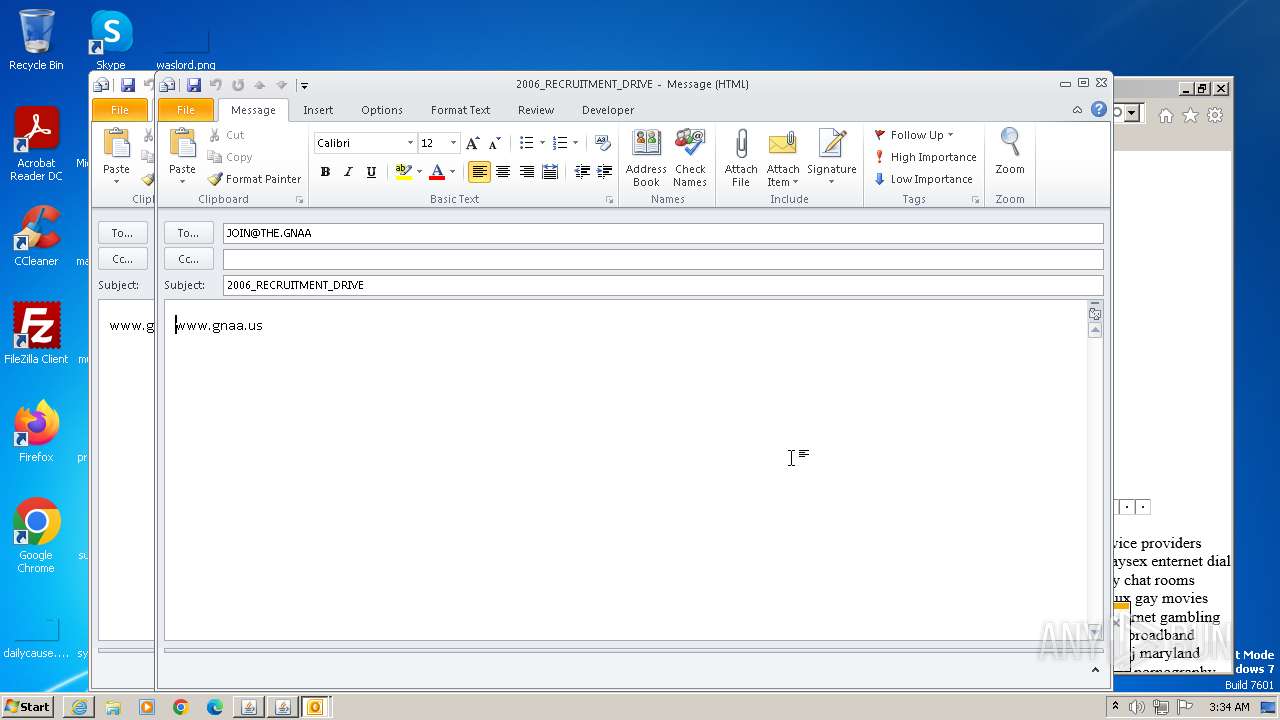
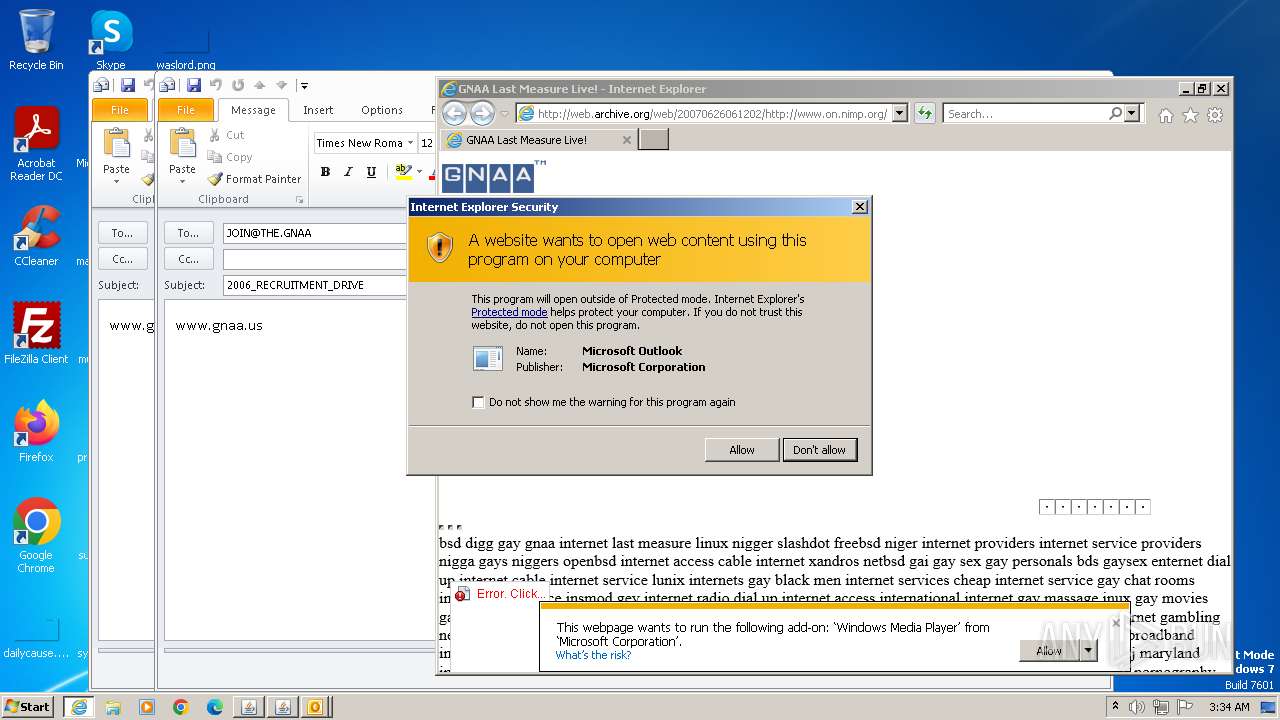
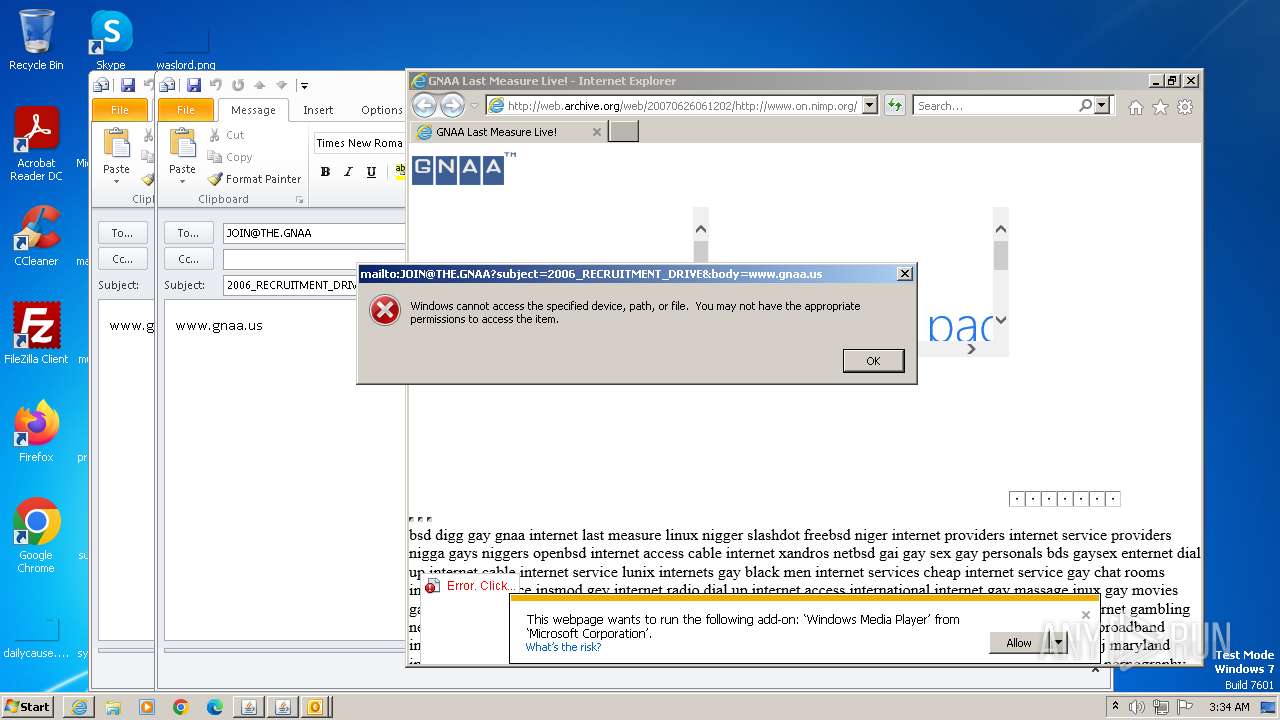
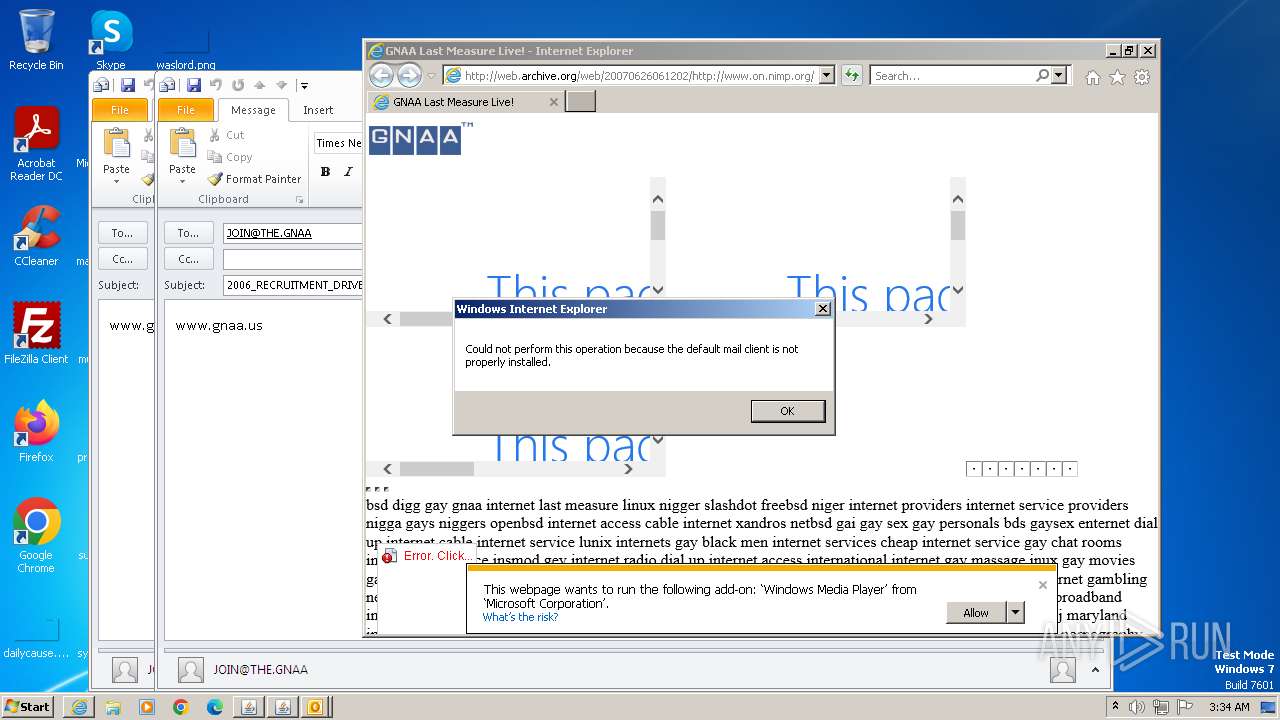
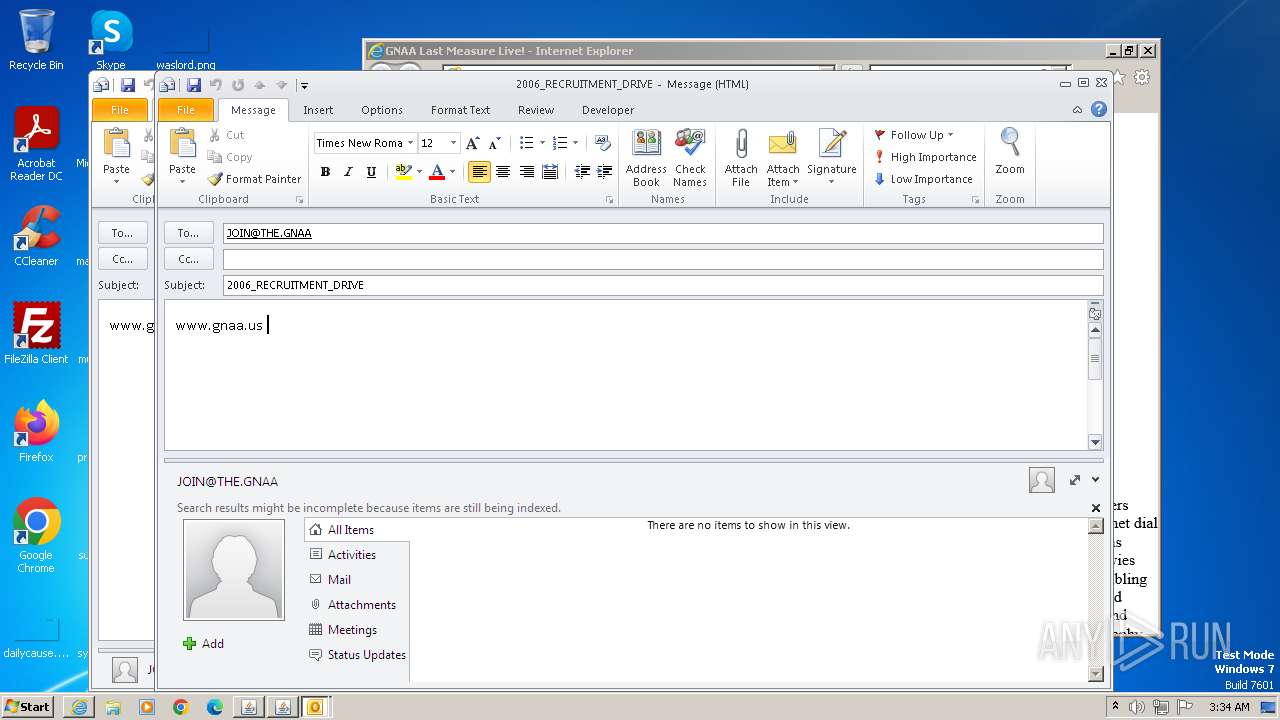
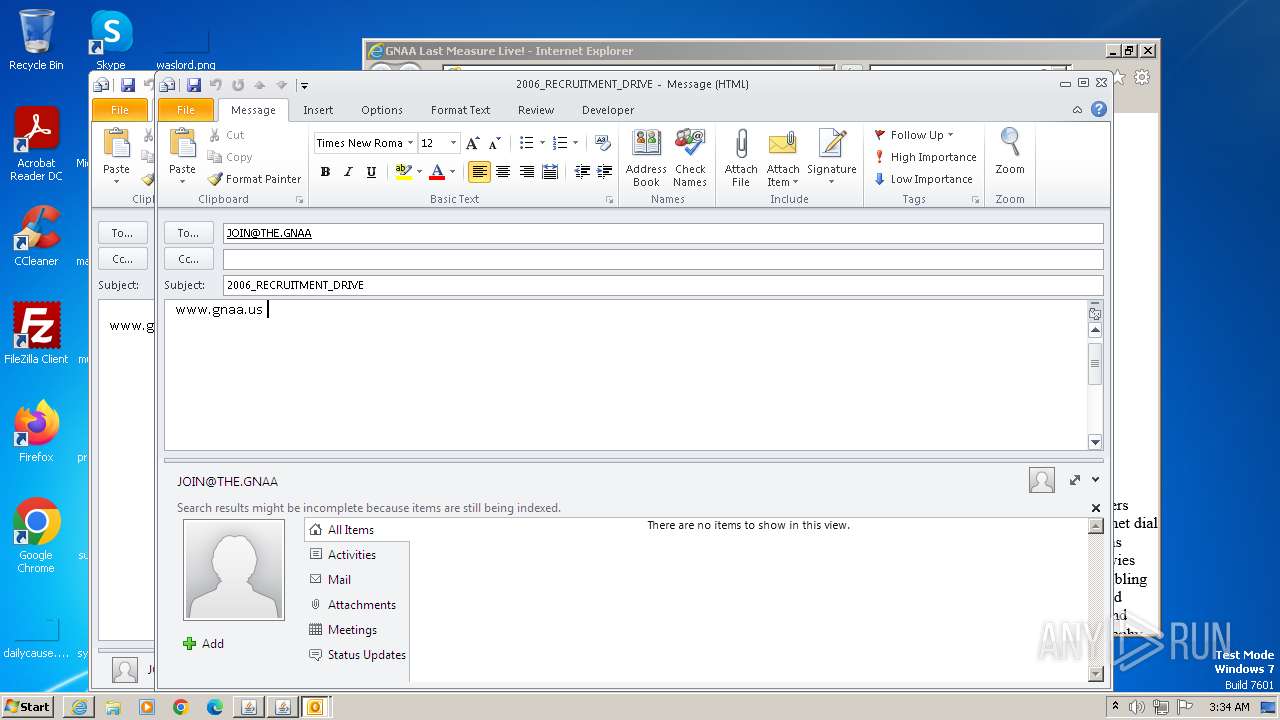
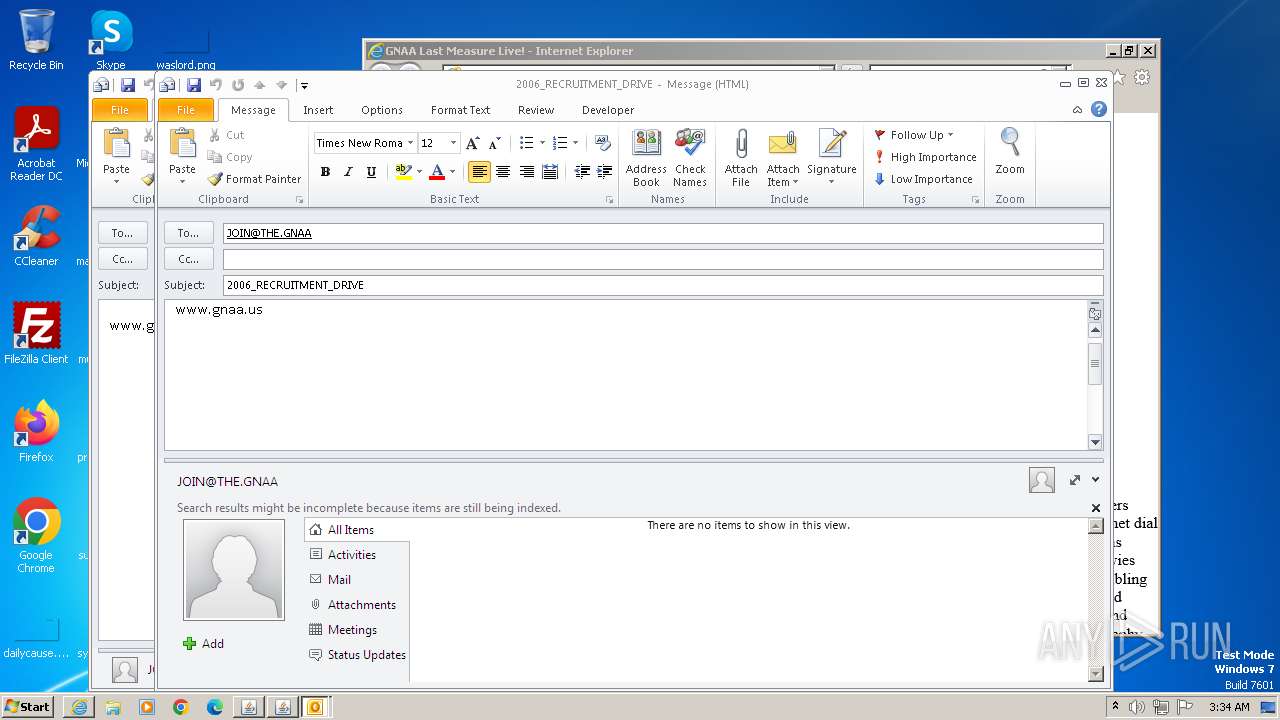
| 752 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" -c IPM.Note /m "mailto:JOIN@THE.GNAA?subject=2006_RECRUITMENT_DRIVE&body=www.gnaa.us" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 1608 | "C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe" -secure -javaws -jre "C:\Program Files\Java\jre1.8.0_271" -vma LWNsYXNzcGF0aABDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxkZXBsb3kuamFyAC1EamF2YS5zZWN1cml0eS5wb2xpY3k9ZmlsZTpDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxzZWN1cml0eVxqYXZhd3MucG9saWN5AC1EdHJ1c3RQcm94eT10cnVlAC1YdmVyaWZ5OnJlbW90ZQAtRGpubHB4LmhvbWU9QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzI3MVxiaW4ALURqYXZhLnNlY3VyaXR5Lm1hbmFnZXIALURzdW4uYXd0Lndhcm11cD10cnVlAC1YYm9vdGNsYXNzcGF0aC9hOkM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF8yNzFcbGliXGphdmF3cy5qYXI7QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzI3MVxsaWJcZGVwbG95LmphcjtDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxwbHVnaW4uamFyAC1EamRrLmRpc2FibGVMYXN0VXNhZ2VUcmFja2luZz10cnVlAC1Eam5scHguanZtPUM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF8yNzFcYmluXGphdmF3LmV4ZQAtRGpubHB4LnZtYXJncz1MVVJxWkdzdVpHbHpZV0pzWlV4aGMzUlZjMkZuWlZSeVlXTnJhVzVuUFhSeWRXVUE= -ma LVNTVkJhc2VsaW5lVXBkYXRlAC1ub3RXZWJKYXZh | C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe | javaws.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 1828 | "C:\PROGRA~1\Java\JRE18~1.0_2\bin\jp2launcher.exe" -sjed | C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe | — | iexplore.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Launcher Exit code: 1 Version: 11.271.2.09 Modules
| |||||||||||||||
| 1872 | "C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe" -secure -plugin -jre "C:\Program Files\Java\jre1.8.0_271" -vma LURfX2p2bV9sYXVuY2hlZD0yMTM5MzQ5MTQ4AC1EX19hcHBsZXRfbGF1bmNoZWQ9MjEzOTMyMjgyMAAtRHN1bi5hd3Qud2FybXVwPXRydWUALURqYXZhLnNlY3VyaXR5Lm1hbmFnZXIA -ma cmVhZF9waXBlX25hbWU9anBpMl9waWQzODcyX3BpcGUyLHdyaXRlX3BpcGVfbmFtZT1qcGkyX3BpZDM4NzJfcGlwZTMA | C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe | iexplore.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 1936 | "C:\PROGRA~1\Java\JRE18~1.0_2\bin\jp2launcher.exe" -sjed | C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe | — | iexplore.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Launcher Exit code: 1 Version: 11.271.2.09 Modules
| |||||||||||||||
| 2368 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" -c IPM.Note /m "mailto:JOIN@THE.GNAA?subject=2006_RECRUITMENT_DRIVE&body=www.gnaa.us" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 2376 | "C:\Users\admin\AppData\Local\Temp\jre-8u391-windows-au.exe" /installmethod=jau-m FAMILYUPGRADE=1 | C:\Users\admin\AppData\Local\Temp\jre-8u391-windows-au.exe | jucheck.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java Platform SE binary Exit code: 0 Version: 8.0.3910.13 Modules
| |||||||||||||||
| 2400 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_2\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.timestamp.11.271.2" "1701833673" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | jp2launcher.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 2404 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" -c IPM.Note /m "mailto:JOIN@THE.GNAA?subject=2006_RECRUITMENT_DRIVE&body=www.gnaa.us" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
Total events
58 993
Read events
58 121
Write events
817
Delete events
55
Modification events
| (PID) Process: | (564) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (564) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (564) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (564) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (564) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (564) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (564) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (564) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (564) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (564) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
4
Suspicious files
25
Text files
54
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3872 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3872 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\gnaa[1].png | image | |
MD5:DE8C2448611E49F721BD47E417A4B51B | SHA256:B24D4D860215C902A3000E49ADBC0CB279EF7ADF3B6E187160ABD4679976D150 | |||
| 3872 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\analytics[1].js | text | |
MD5:CBC1B007EB7DE0B65EDA9EF00E069EBE | SHA256:A1F3D3BE0AF279C2DA371163D037A3D46569453A855CF91ACECA0F3695C57017 | |||
| 3872 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\www.on.nimp[1].htm | html | |
MD5:46A4FF7A8E14A333F383EB97485D6D2A | SHA256:B05455CAF4DC770EAC0E7D0280A15B85306D98E13F4A67BDDADD13382C2CFB6E | |||
| 3872 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:ABC796FBD432A94EE37509411E5526A9 | SHA256:F024D0F965701C9F29514817ABAA407A6CFDA58F1A73F222055D87D831676B51 | |||
| 3872 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EB2C4AB8B68FFA4B7733A9139239A396_D76DB901EE986B889F30D8CC06229E2D | binary | |
MD5:D28DEEAA0A76DF915C8ADF9C0D172B5B | SHA256:712717A99328DC8818182A6D9E6373C33D08364E9BD5B4B192C92806A49FA64B | |||
| 3872 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\wm_tb_prv_on[1].png | image | |
MD5:A4F0D56855C698DD583529AF88E28D42 | SHA256:5D09C087A37CEB85DDBD9B25C0F8D94FD4CF0A22E5579AAF679908E7F095D62F | |||
| 3872 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\J157G7J4.txt | text | |
MD5:1CBAF87FDF5ADE88081EA3EAF62A3122 | SHA256:867D85A2BBC39518EA15CBCE48F223D1403AD7A3021B6C7750B1F35CED6FE729 | |||
| 3872 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\bundle-playback[1].js | text | |
MD5:B7505FE0F63F3CFE4EC1489052A728E5 | SHA256:3B31419BB24F50BFD372BBC434C110BBCF893E66D61C53A985858968E4DE3CDD | |||
| 3872 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\loading[1].gif | image | |
MD5:FEB463F3270AFEE4352651AAC697D7E5 | SHA256:5A3BB1567FFD3CF6269B276F47563078B2D0A846156BCA648D9624EB9EF6AF1D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
70
TCP/UDP connections
522
DNS requests
19
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3872 | iexplore.exe | GET | 302 | 207.241.237.3:80 | http://web.archive.org/web/20070626061202im_/http://www.on.nimp.org/gnaa.png | unknown | — | — | unknown |
3872 | iexplore.exe | GET | 302 | 207.241.237.3:80 | http://web.archive.org/web/20070626061202/on.nimp.org | unknown | — | — | unknown |
3872 | iexplore.exe | GET | 200 | 207.241.237.3:80 | http://web.archive.org/web/20070626061202/http://www.on.nimp.org/ | unknown | html | 11.8 Kb | unknown |
3872 | iexplore.exe | GET | 200 | 207.241.224.2:80 | http://archive.org/includes/analytics.js?v=cf34f82 | unknown | text | 5.01 Kb | unknown |
3872 | iexplore.exe | GET | 200 | 207.241.237.3:80 | http://web.archive.org/web/20060718234336im_/http://www.on.nimp.org/gnaa.png | unknown | image | 2.04 Kb | unknown |
3872 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4606156345daae19 | unknown | compressed | 4.66 Kb | unknown |
3872 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?db75743a42db342c | unknown | compressed | 4.66 Kb | unknown |
3872 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f5d063458958b218 | unknown | compressed | 4.66 Kb | unknown |
3872 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4cfc645c95bc45a8 | unknown | compressed | 4.66 Kb | unknown |
3872 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5da9bd5cc1693f70 | unknown | compressed | 4.66 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3872 | iexplore.exe | 207.241.237.3:80 | web.archive.org | INTERNET-ARCHIVE | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3872 | iexplore.exe | 207.241.224.2:80 | archive.org | INTERNET-ARCHIVE | US | malicious |
3872 | iexplore.exe | 207.241.237.2:443 | web-static.archive.org | INTERNET-ARCHIVE | US | unknown |
3872 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3872 | iexplore.exe | 192.124.249.22:80 | ocsp.godaddy.com | SUCURI-SEC | US | unknown |
3872 | iexplore.exe | 207.241.224.2:443 | archive.org | INTERNET-ARCHIVE | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
web.archive.org |
| whitelisted |
archive.org |
| whitelisted |
web-static.archive.org |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.godaddy.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
analytics.archive.org |
| whitelisted |
javadl-esd-secure.oracle.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2968 | jp2launcher.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
2968 | jp2launcher.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |