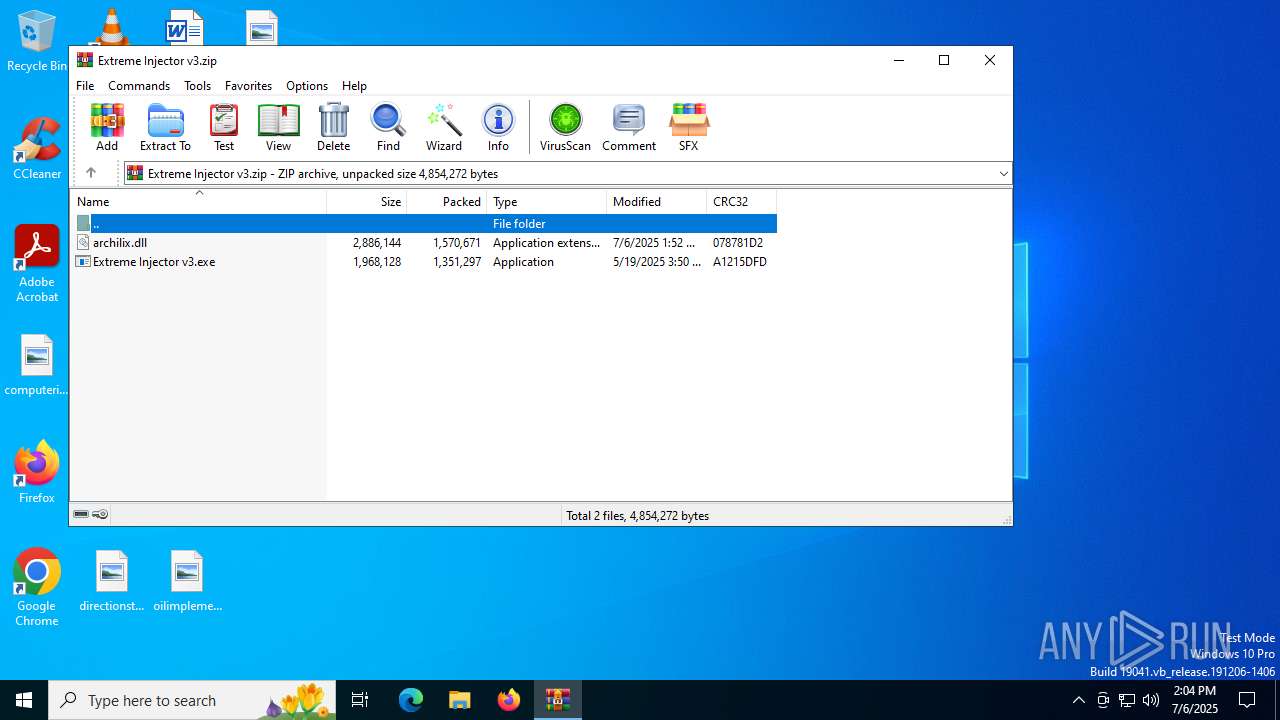
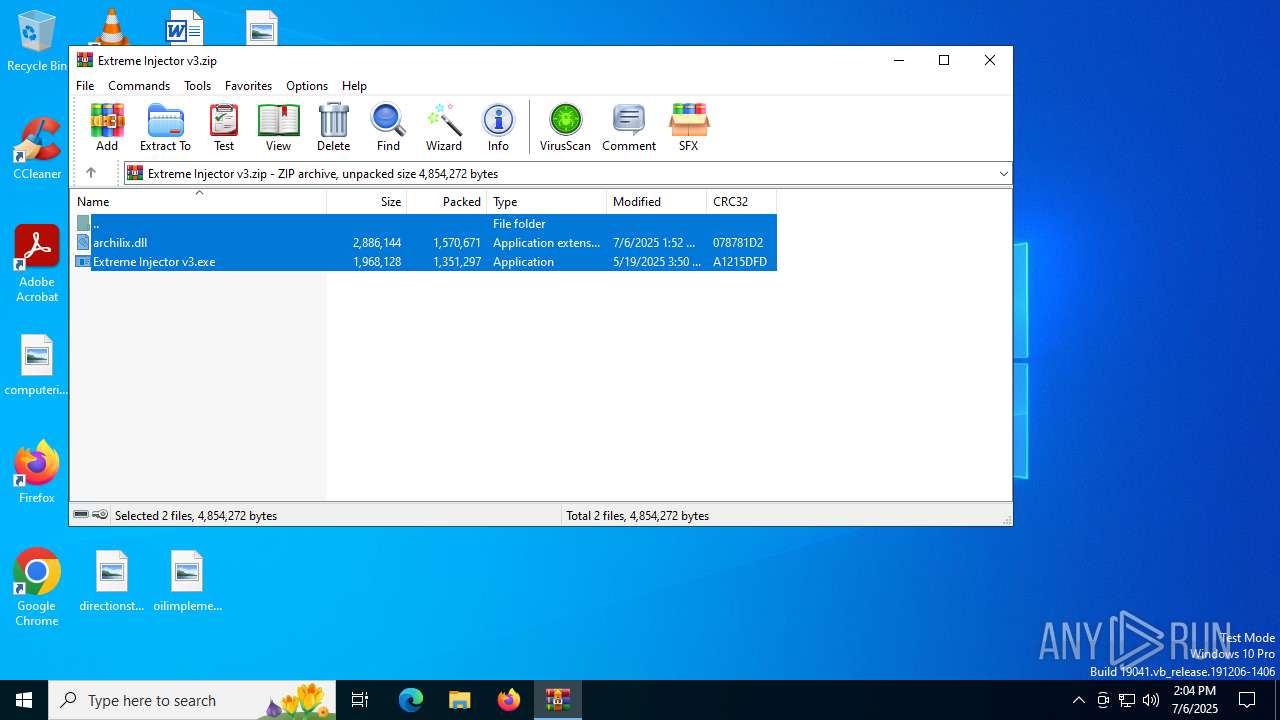
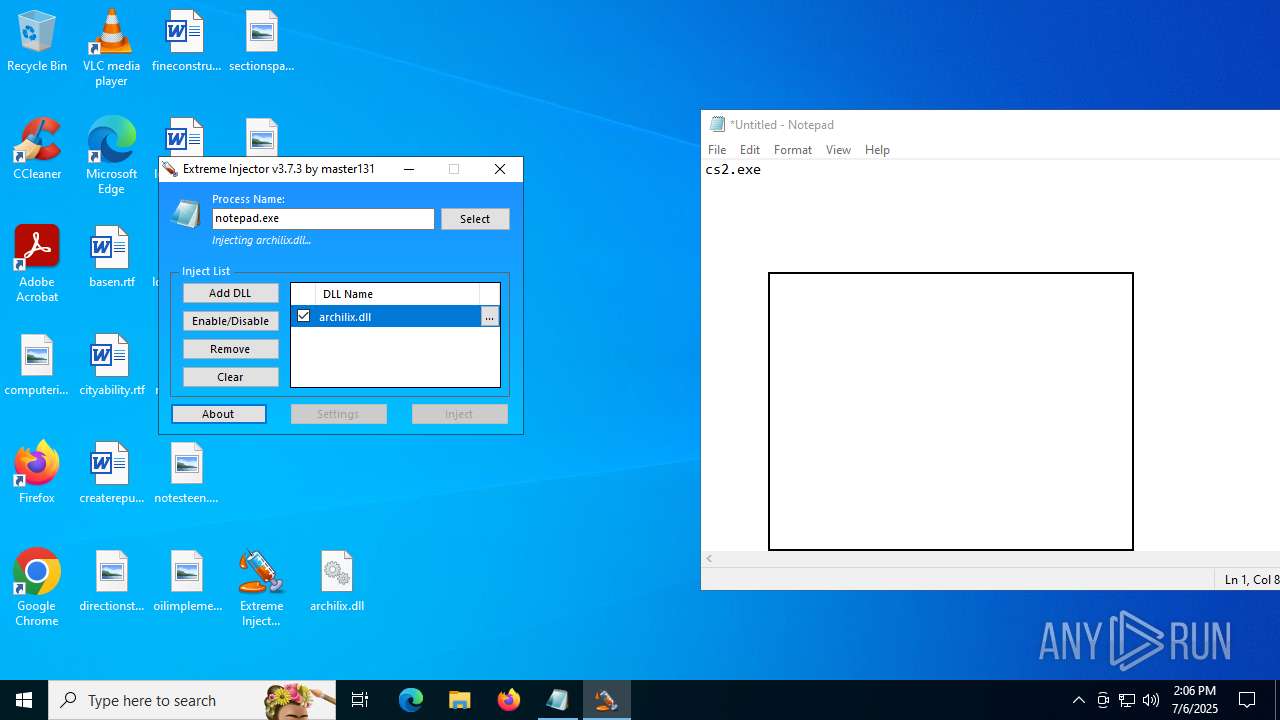
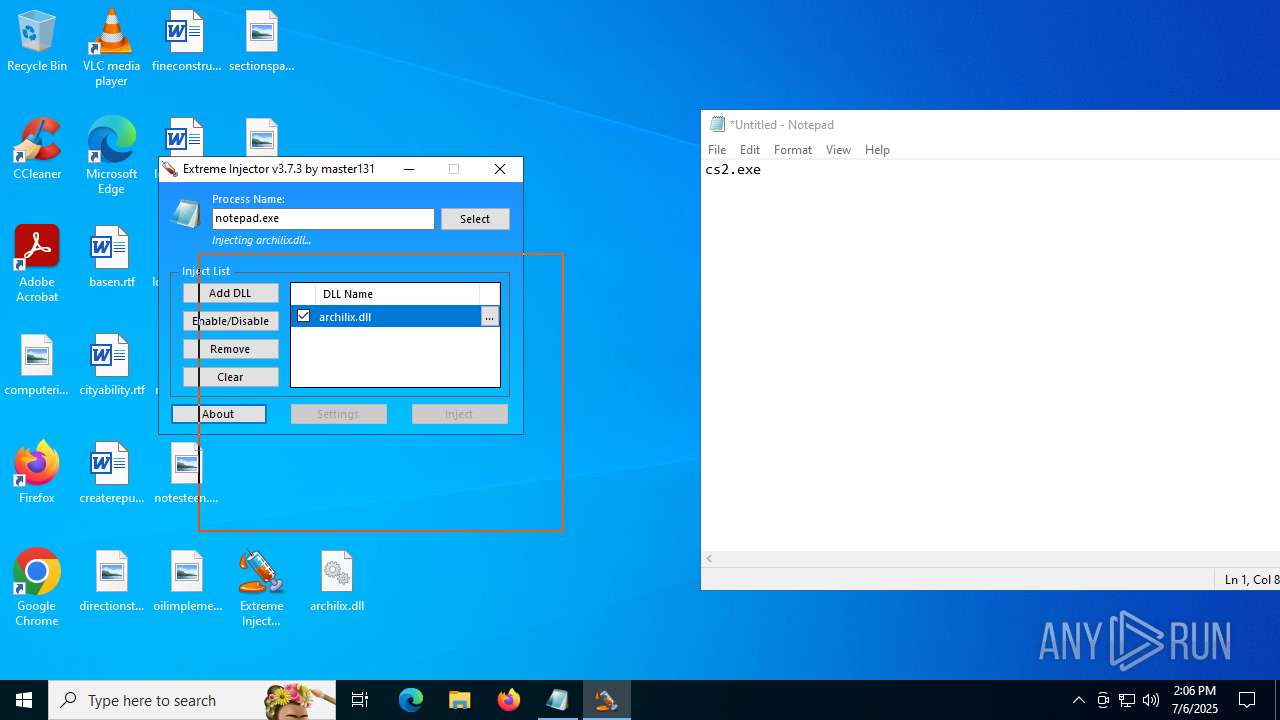
| File name: | Extreme Injector v3.zip |
| Full analysis: | https://app.any.run/tasks/ab89d3ed-c8ae-4c41-9818-dc2b76a032d5 |
| Verdict: | Malicious activity |
| Analysis date: | July 06, 2025, 14:04:43 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 4DED2B8C37F1C5579C82243DB6DD7A76 |
| SHA1: | 80D39BEA978F809BD034E430B0291B67335565C4 |
| SHA256: | BC3830418479A835058169EFAFAFF39E0DAD62E5C06BBC5F366AC1FD2DA41A97 |
| SSDEEP: | 98304:HXHw0FMrH4yxPUPSM+IAyRTEe2hfKYC1DnTGWerfkUKzaeeTMo2wHmhu2AuEjxXo:HXtJD |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7048)
SUSPICIOUS
Reads security settings of Internet Explorer
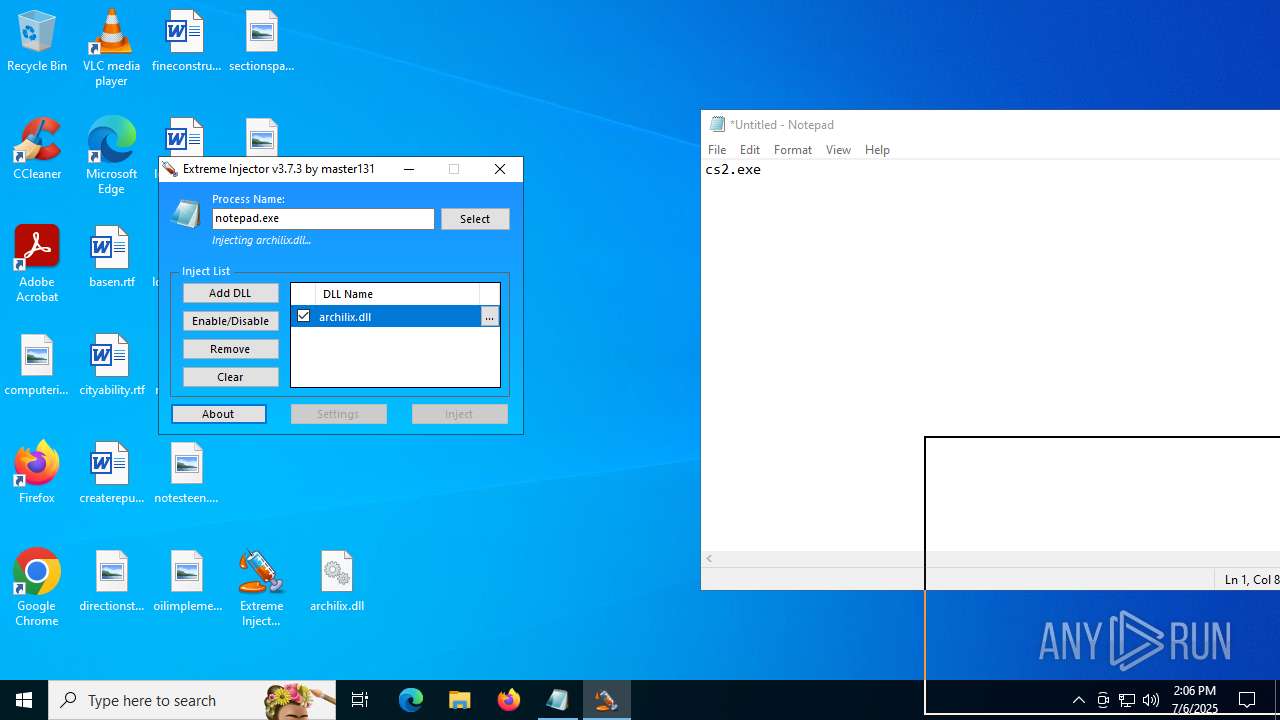
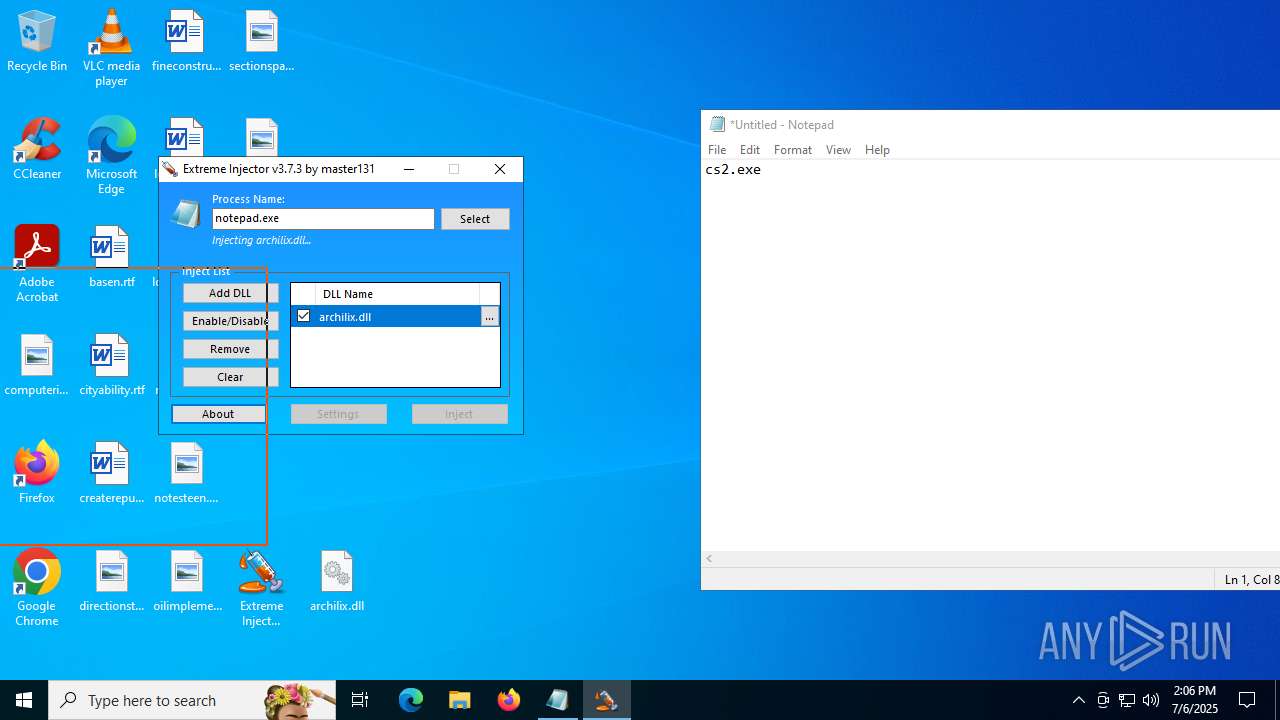
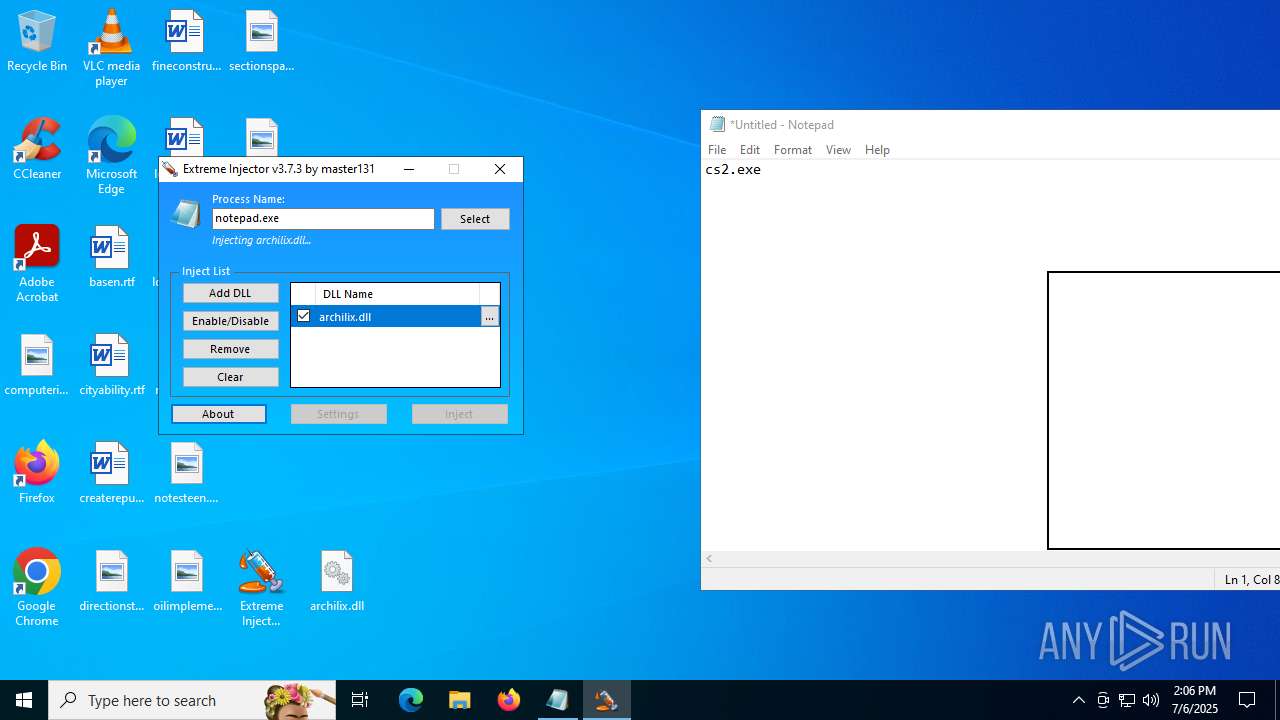
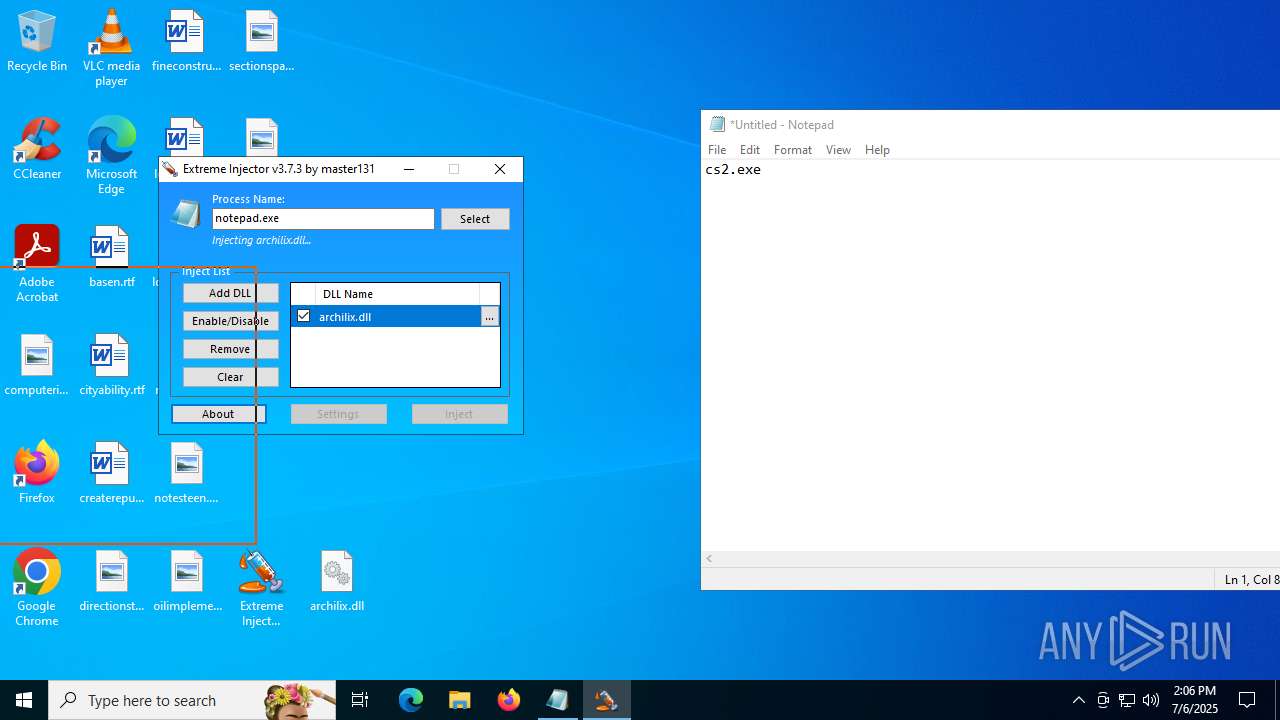
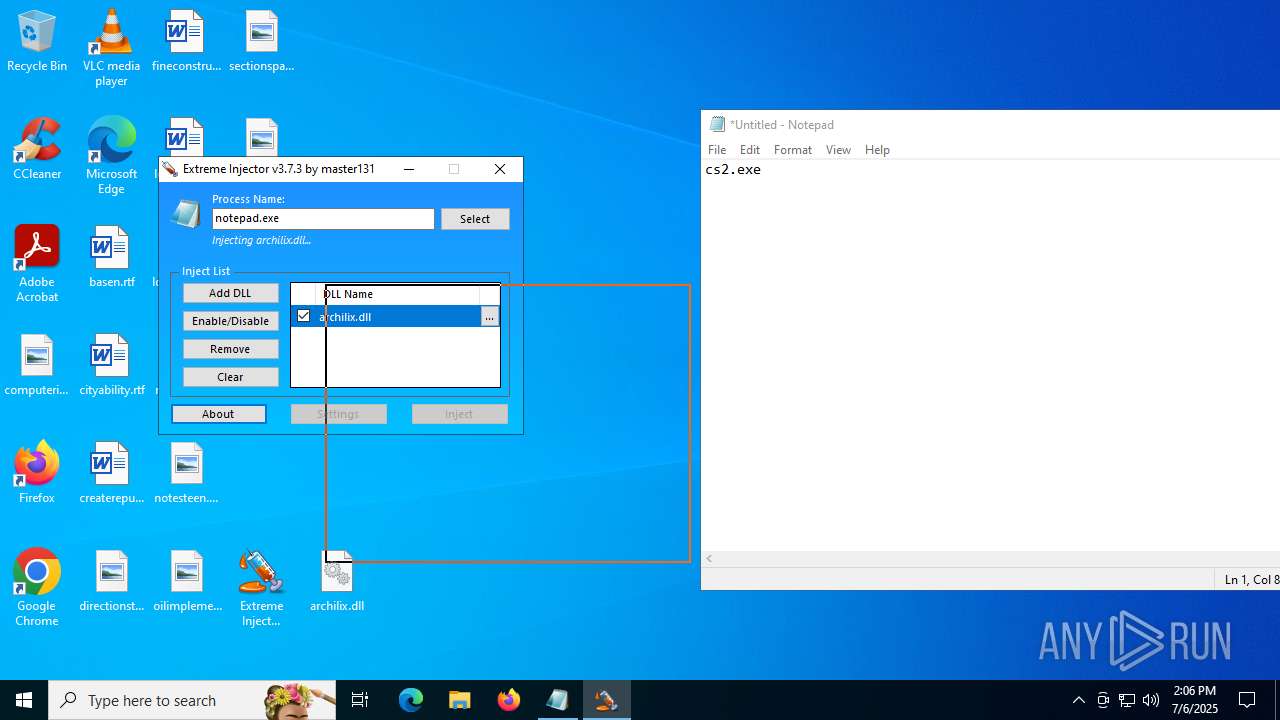
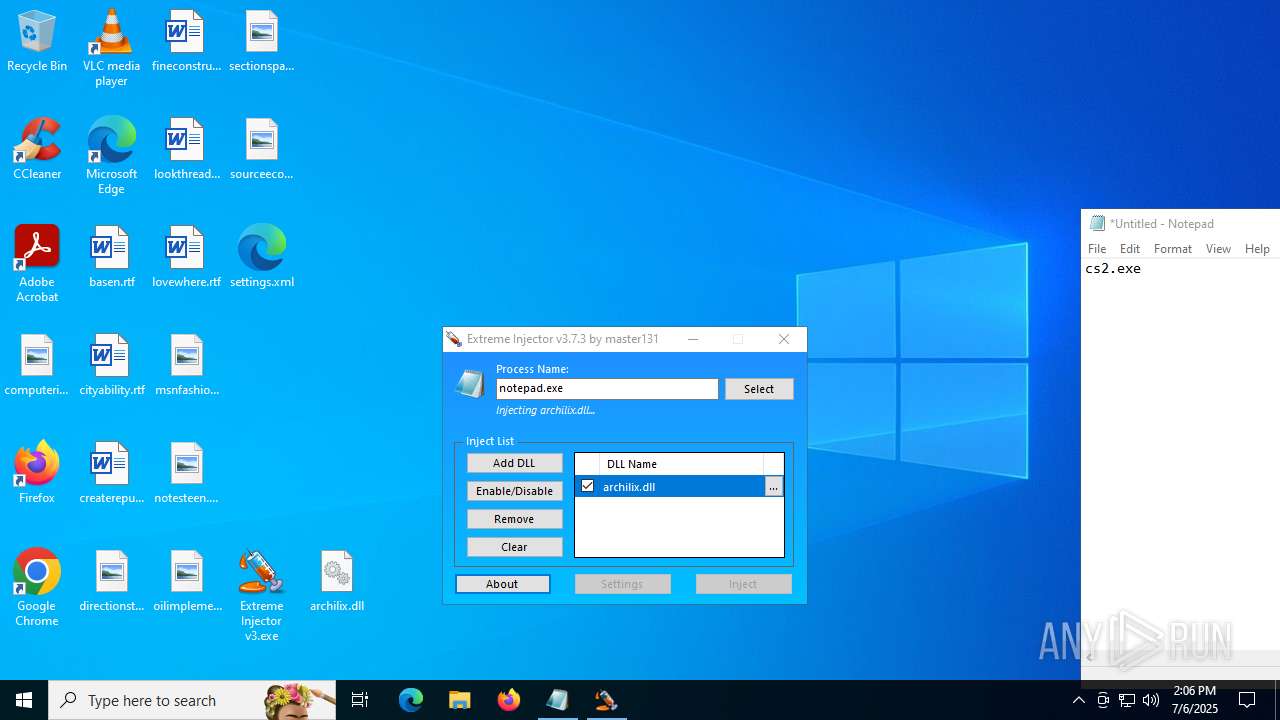
- Extreme Injector v3.exe (PID: 6412)
- Extreme Injector v3.exe (PID: 3476)
Application launched itself
- Extreme Injector v3.exe (PID: 6412)
The process creates files with name similar to system file names
- WerFault.exe (PID: 6224)
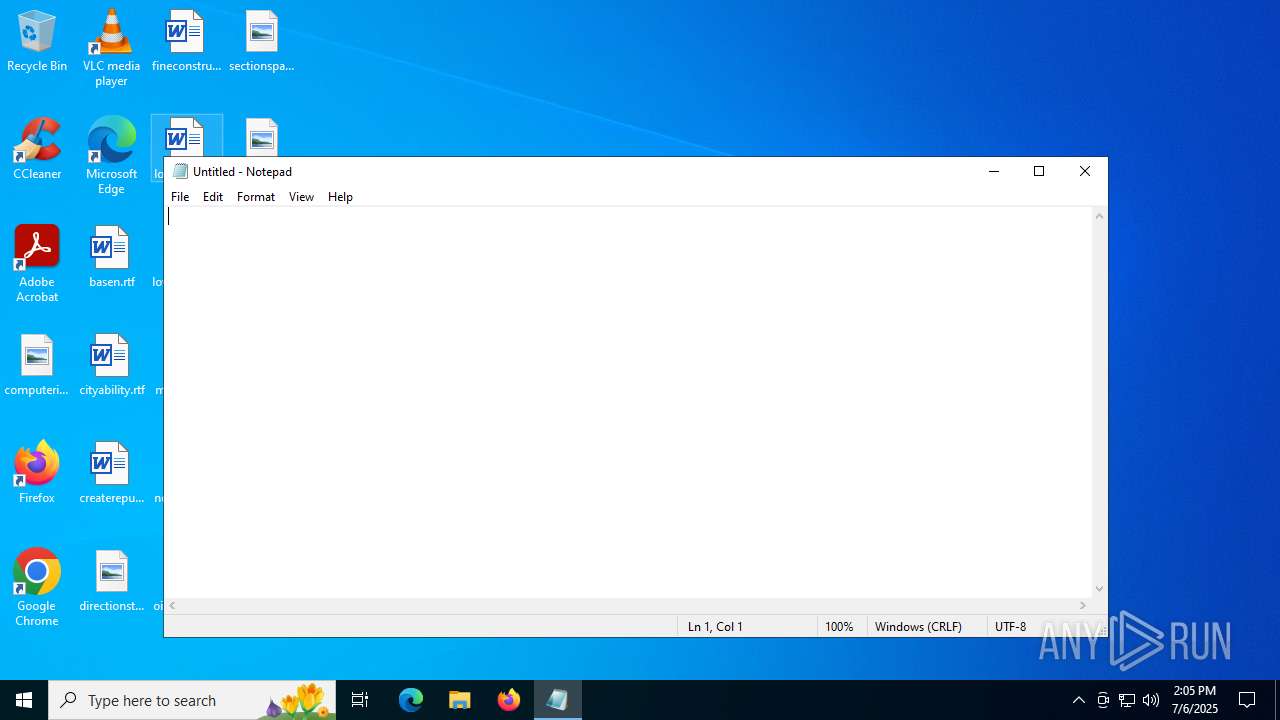
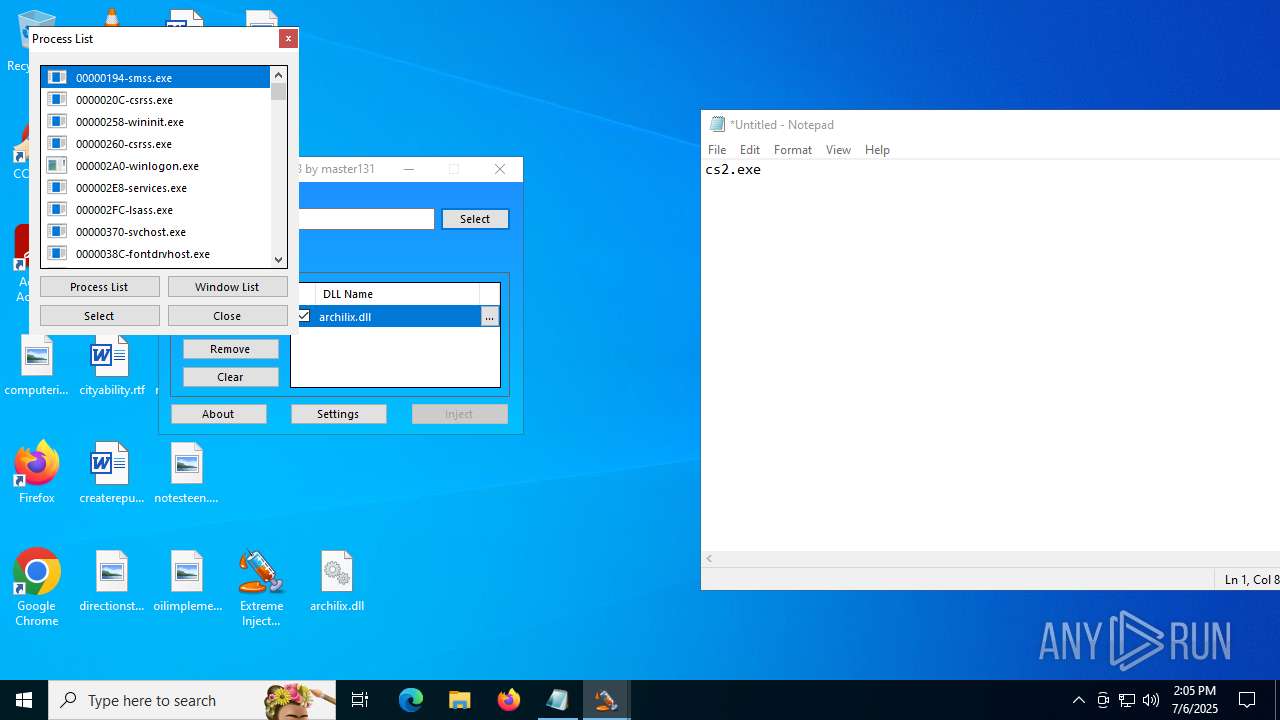
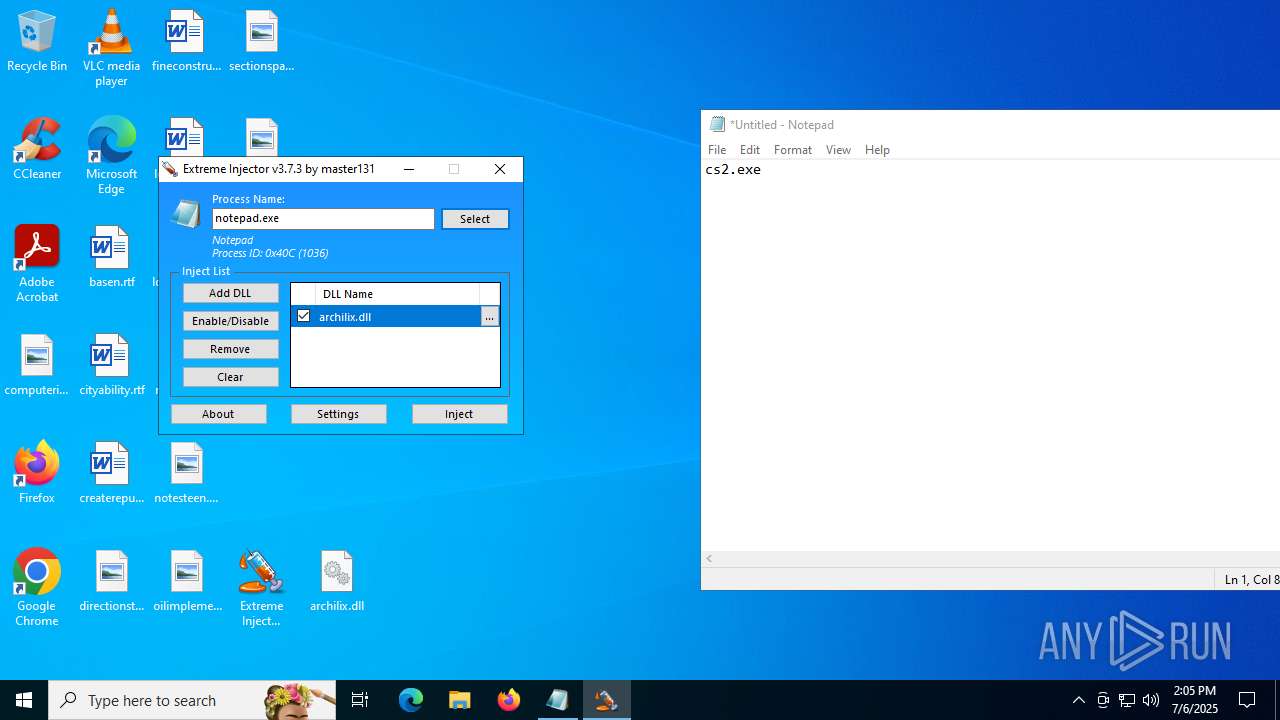
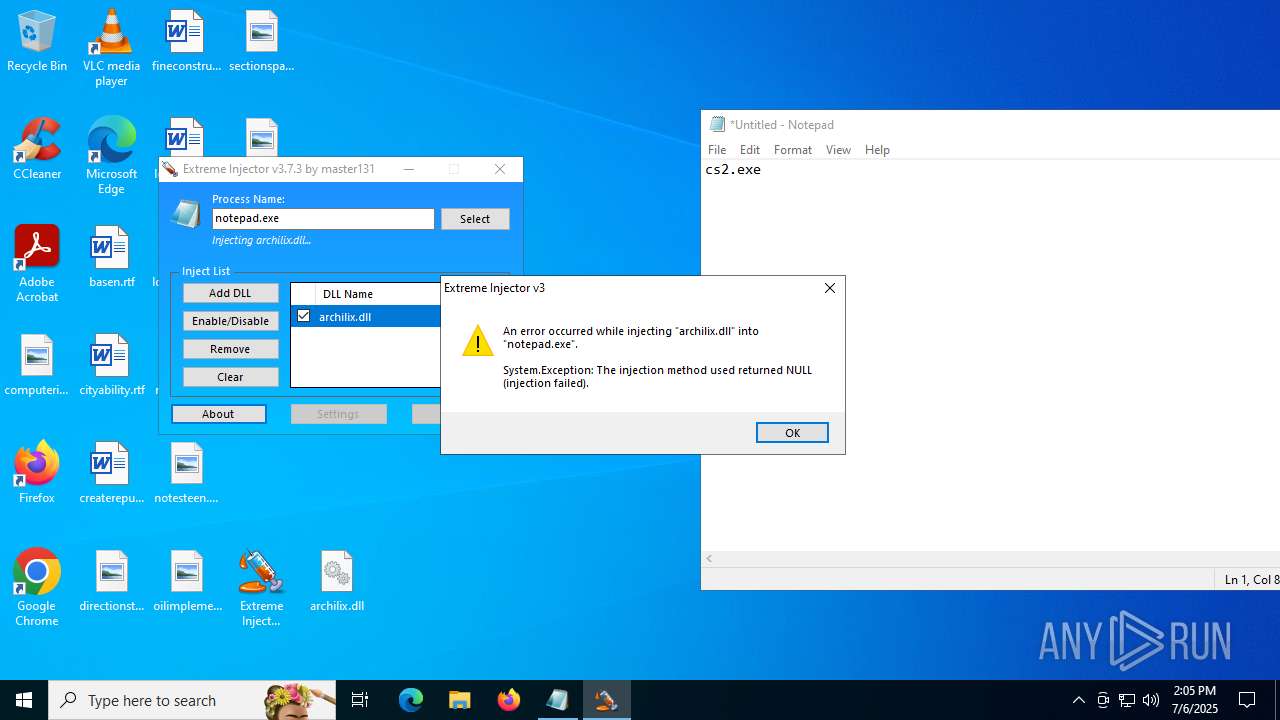
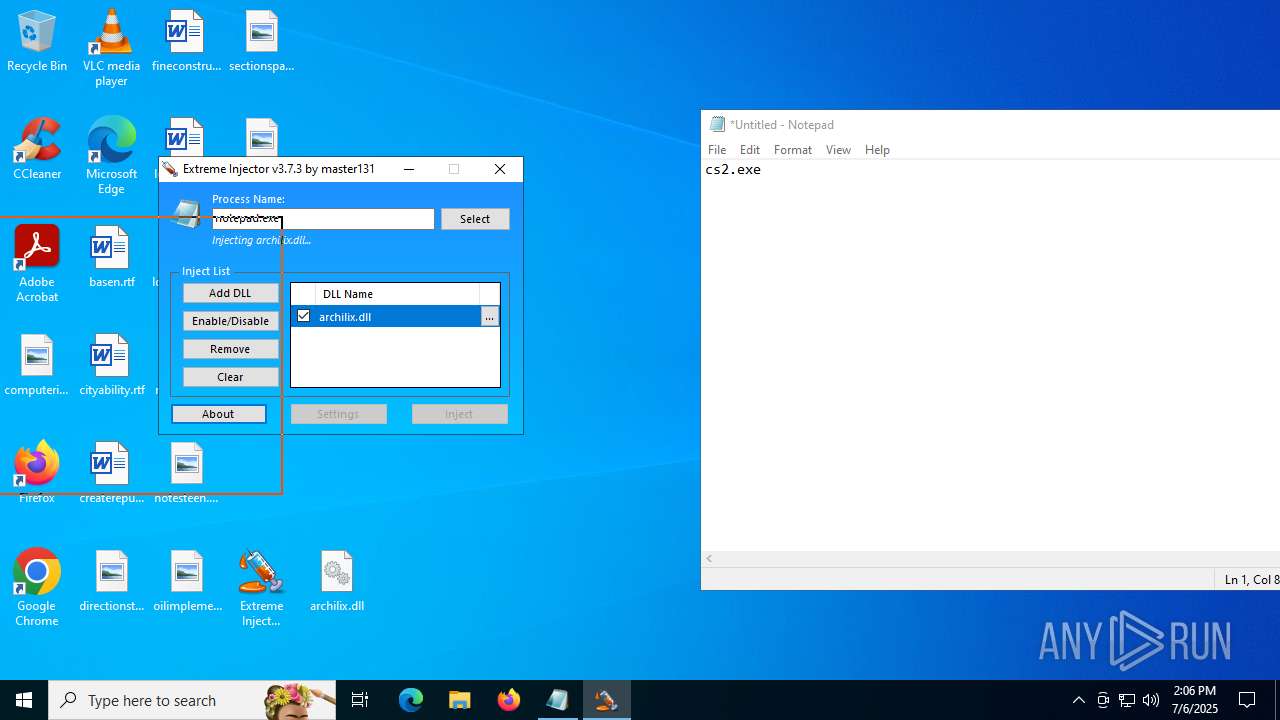
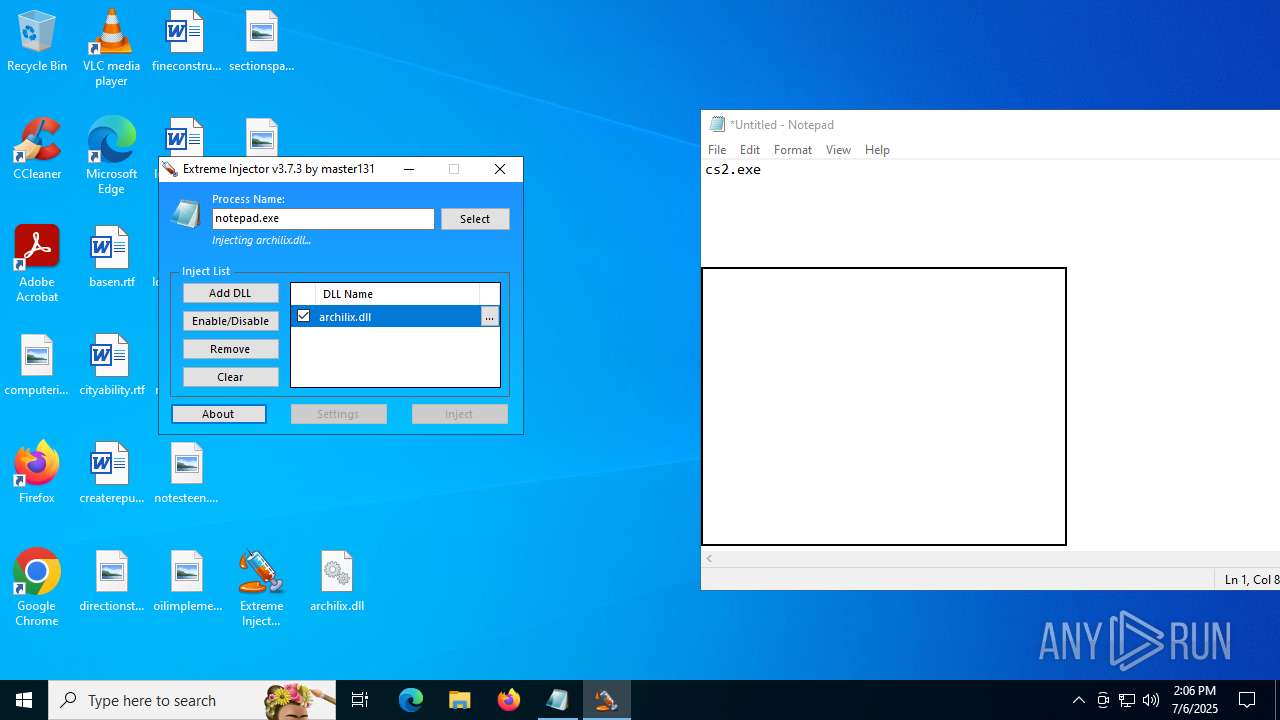
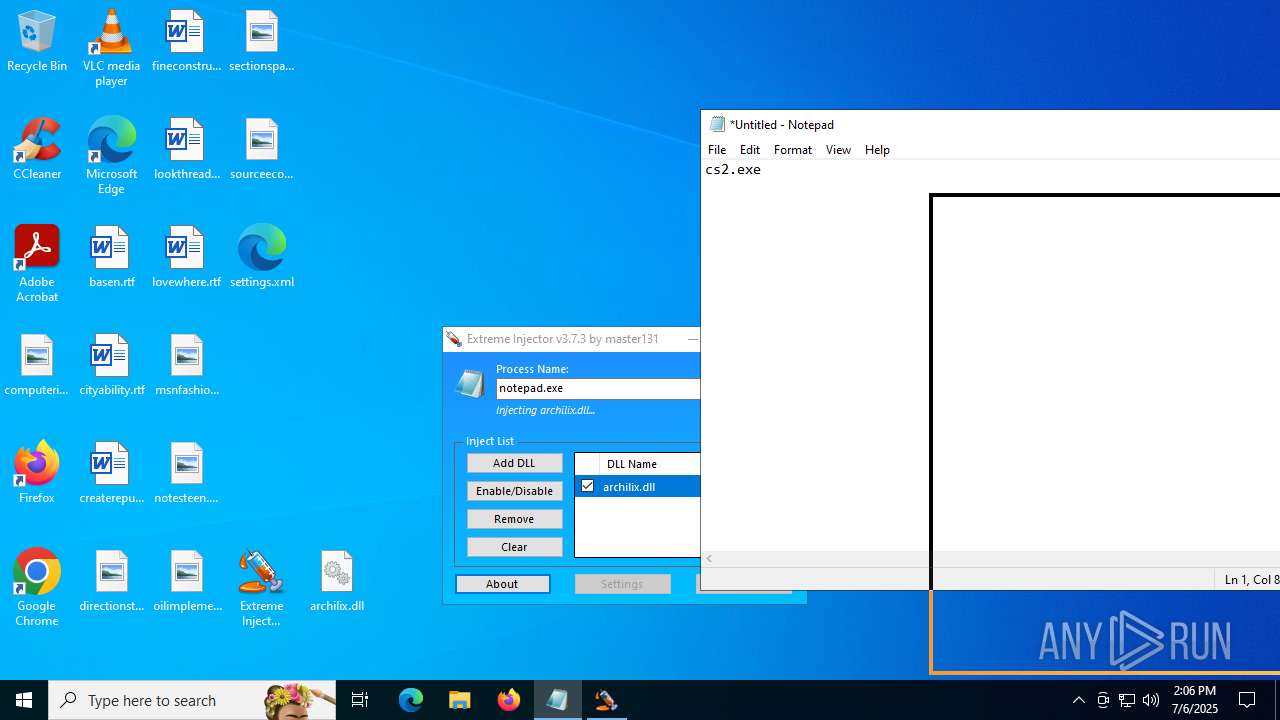
Executes application which crashes
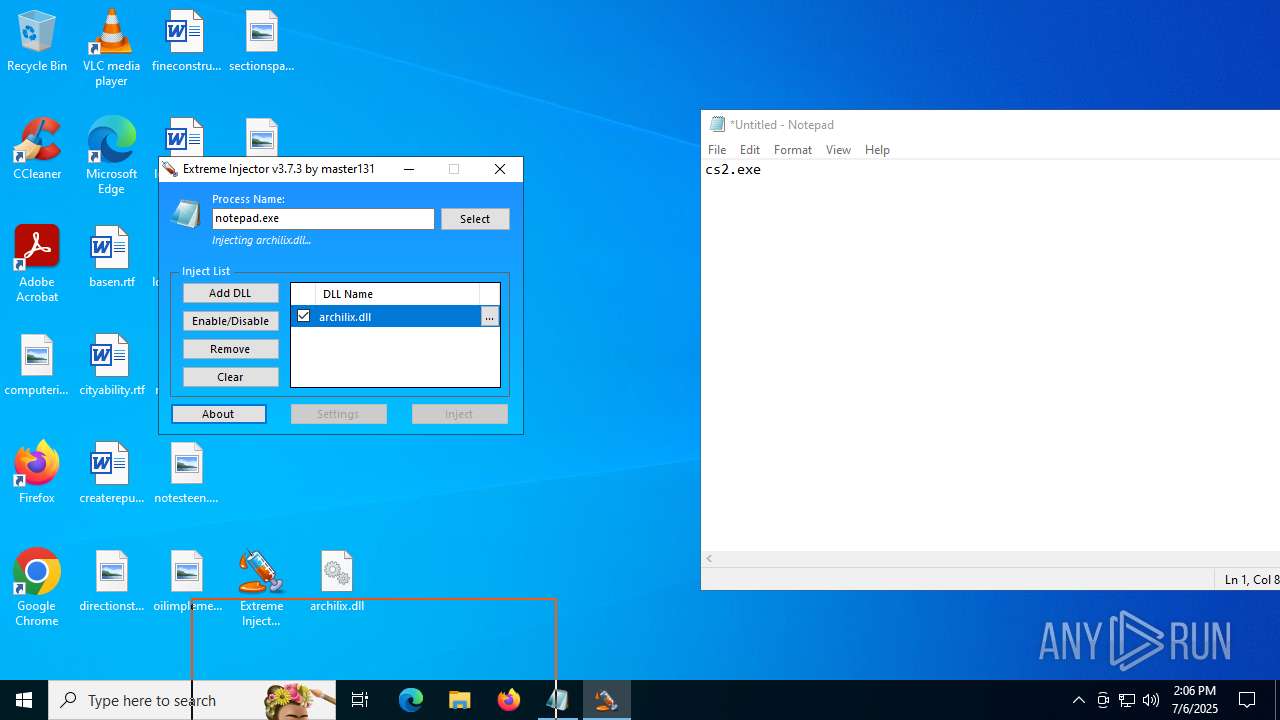
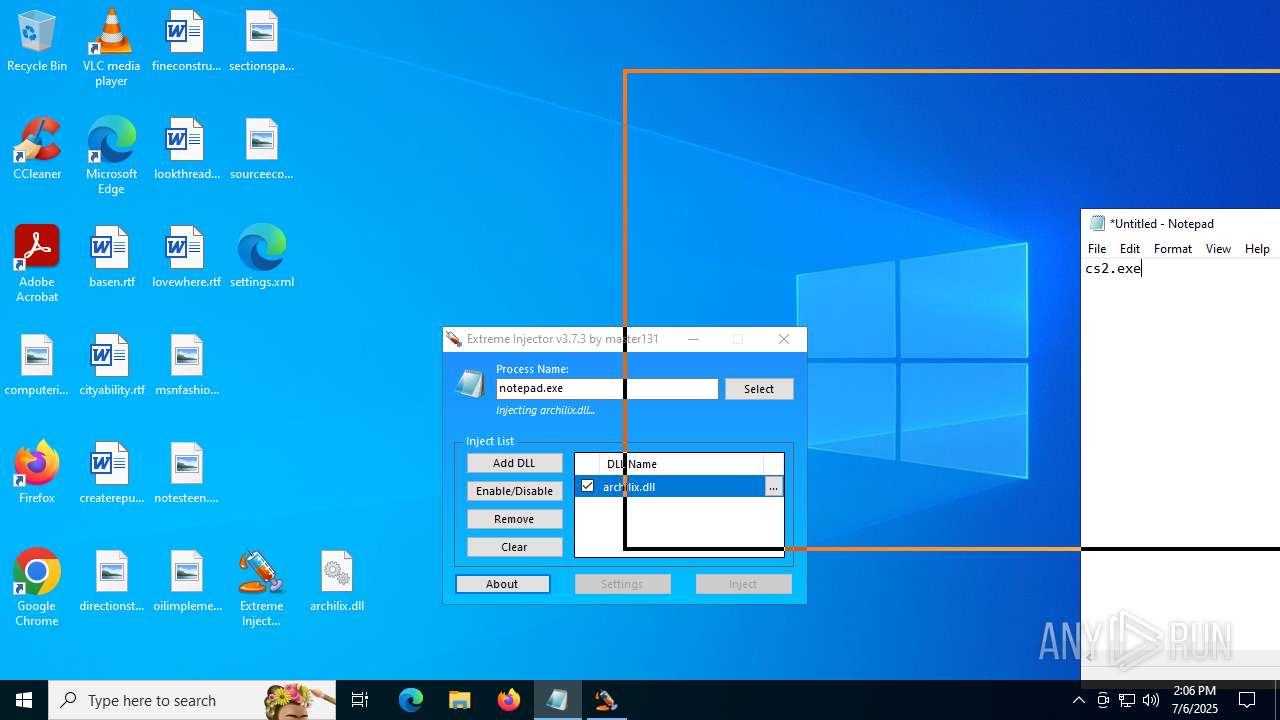
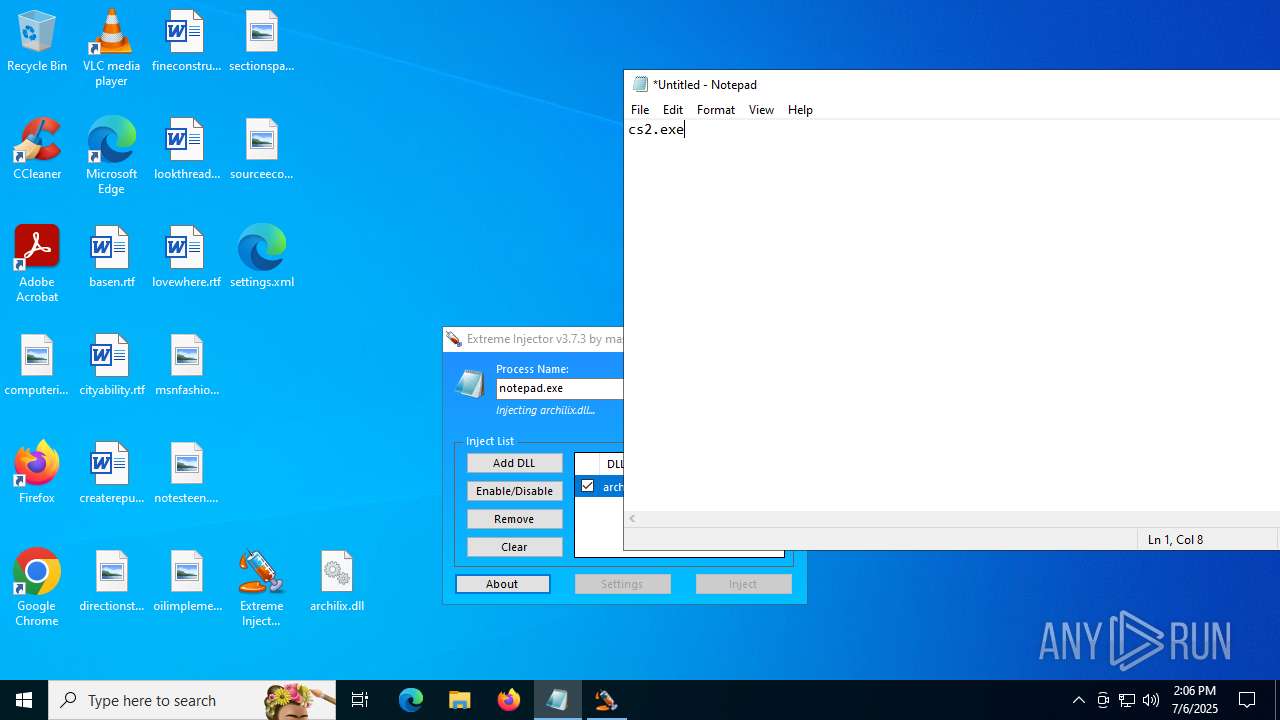
- notepad.exe (PID: 1036)
Reads the date of Windows installation
- Extreme Injector v3.exe (PID: 6412)
INFO
Checks supported languages
- Extreme Injector v3.exe (PID: 6412)
- Extreme Injector v3.exe (PID: 3476)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7048)
Manual execution by a user
- notepad.exe (PID: 1036)
- Extreme Injector v3.exe (PID: 6412)
Process checks computer location settings
- Extreme Injector v3.exe (PID: 6412)
Reads the computer name
- Extreme Injector v3.exe (PID: 6412)
- Extreme Injector v3.exe (PID: 3476)
Checks proxy server information
- Extreme Injector v3.exe (PID: 3476)
- slui.exe (PID: 3960)
Reads Environment values
- Extreme Injector v3.exe (PID: 3476)
Potential access to remote process (Base64 Encoded 'OpenProcess')
- Extreme Injector v3.exe (PID: 3476)
Reads the software policy settings
- Extreme Injector v3.exe (PID: 3476)
- slui.exe (PID: 3960)
Creates files or folders in the user directory
- WerFault.exe (PID: 6224)
Potential library load (Base64 Encoded 'LoadLibrary')
- Extreme Injector v3.exe (PID: 3476)
Disables trace logs
- Extreme Injector v3.exe (PID: 3476)
Create files in a temporary directory
- Extreme Injector v3.exe (PID: 3476)
Reads the machine GUID from the registry
- Extreme Injector v3.exe (PID: 3476)
- Extreme Injector v3.exe (PID: 6412)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0008 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:19 16:50:30 |
| ZipCRC: | 0xa1215dfd |
| ZipCompressedSize: | 1351297 |
| ZipUncompressedSize: | 1968128 |
| ZipFileName: | Extreme Injector v3.exe |
Total processes
147
Monitored processes
6
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
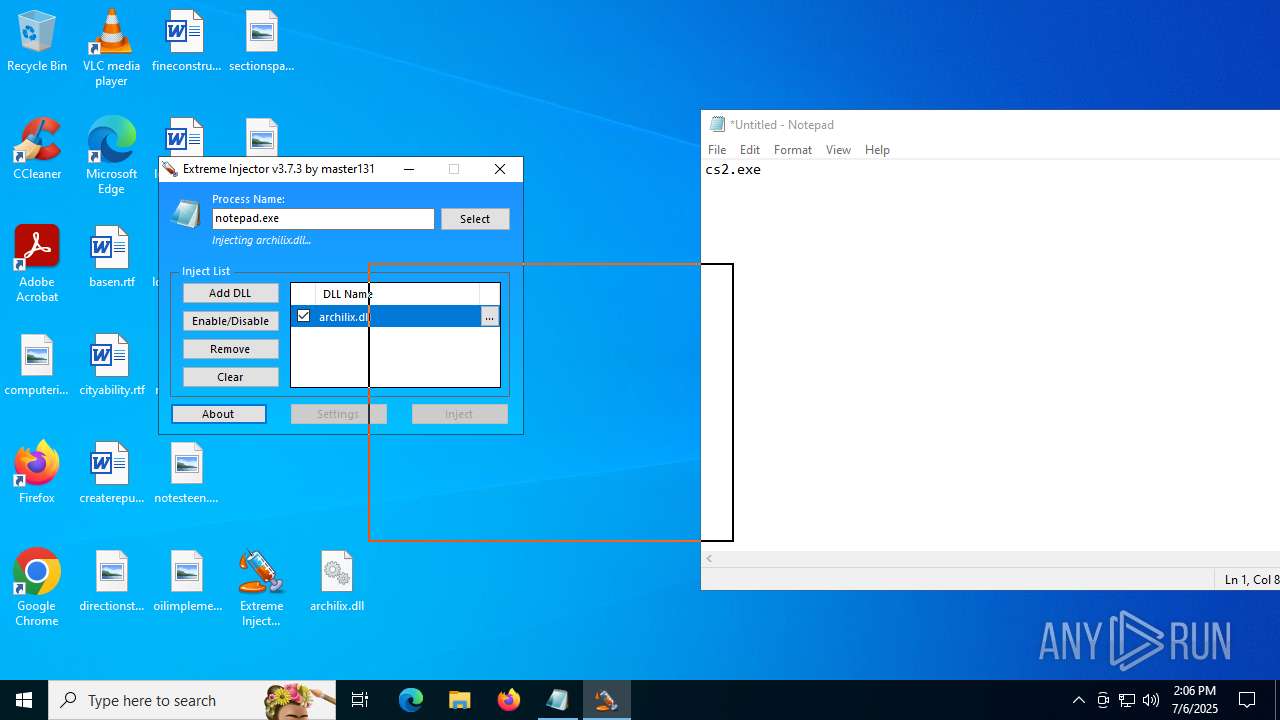
| 1036 | "C:\WINDOWS\system32\notepad.exe" | C:\Windows\System32\notepad.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
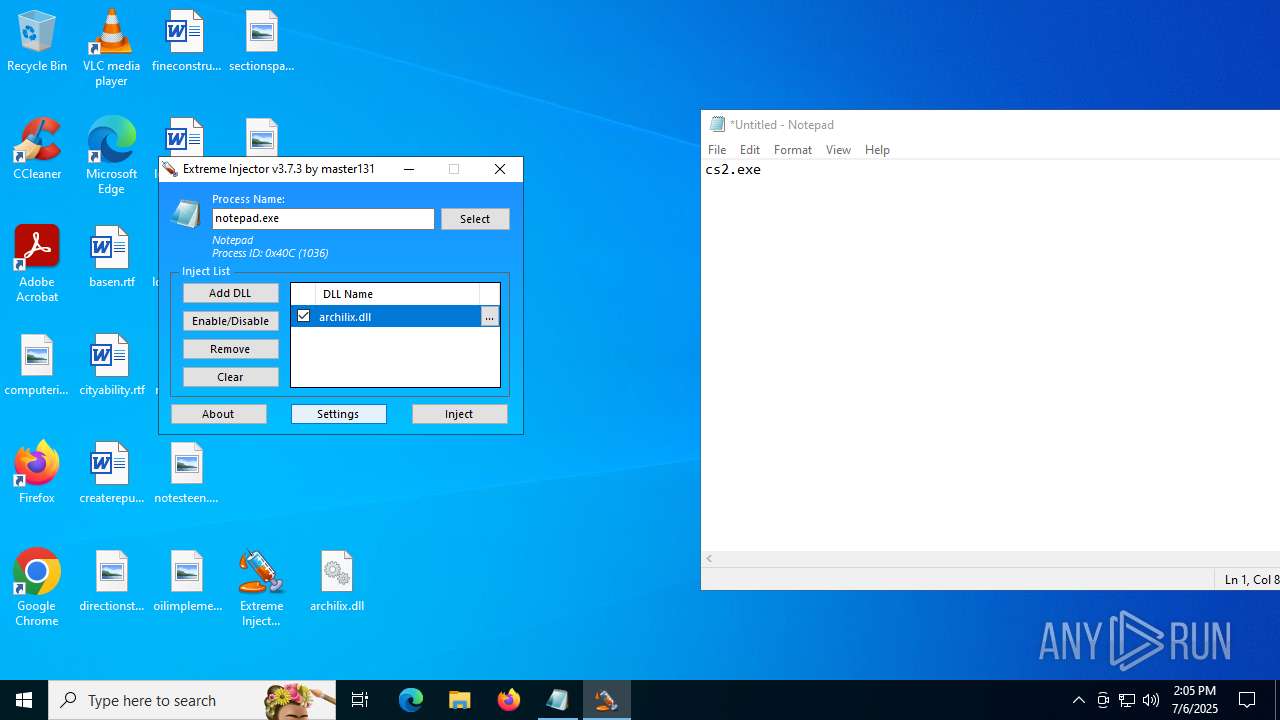
| 3476 | "C:\Users\admin\Desktop\Extreme Injector v3.exe" | C:\Users\admin\Desktop\Extreme Injector v3.exe | Extreme Injector v3.exe | ||||||||||||
User: admin Company: master131 Integrity Level: HIGH Description: Extreme Injector Version: 3.7.3.0 Modules
| |||||||||||||||
| 3960 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6224 | C:\WINDOWS\system32\WerFault.exe -u -p 1036 -s 1004 | C:\Windows\System32\WerFault.exe | — | notepad.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6412 | "C:\Users\admin\Desktop\Extreme Injector v3.exe" | C:\Users\admin\Desktop\Extreme Injector v3.exe | — | explorer.exe | |||||||||||
User: admin Company: master131 Integrity Level: MEDIUM Description: Extreme Injector Exit code: 0 Version: 3.7.3.0 Modules
| |||||||||||||||
| 7048 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Extreme Injector v3.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
10 366
Read events
10 296
Write events
68
Delete events
2
Modification events
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Extreme Injector v3.zip | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
2
Suspicious files
2
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6224 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_notepad.exe_853940e3f59be9588c82bfbfc22488a4523fde_b67ebdd8_0b8fe1c9-d0cf-476c-ae54-e1ab5665da7a\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7048 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7048.393\archilix.dll | executable | |
MD5:0D92579B5D1947203C22619184B41D51 | SHA256:B171F3782F2B48E579D244EBA8E4F8646E90F88411360C2E53E72CBACB271D02 | |||
| 6224 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERF493.tmp.xml | xml | |
MD5:585C3F788372797B91D917E479E5D6B8 | SHA256:6032418460D7C29BAB723DA8AC2E9C59F22A1221244E5FE094651BBFD1C04D1F | |||
| 6224 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERF473.tmp.WERInternalMetadata.xml | xml | |
MD5:DF63E2E2196260FEF79CD401A8416FE3 | SHA256:E6CF86F70EC6D79EE75ACBA5B3277CC595B453AFD8A4BCDE70D5604142396C9C | |||
| 7048 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7048.393\Extreme Injector v3.exe | executable | |
MD5:EC801A7D4B72A288EC6C207BB9FF0131 | SHA256:B65F40618F584303CA0BCF9B5F88C233CC4237699C0C4BF40BA8FACBE8195A46 | |||
| 6224 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\notepad.exe.1036.dmp | binary | |
MD5:8237EFBDA36B1E07BCABFFF6183F3607 | SHA256:41C4E1F6198F1DF92EE856C48F8D216C499024D207BA1FFBE00C94BF06D1604F | |||
| 6224 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERF404.tmp.dmp | binary | |
MD5:4EBFC52FC3B4090F68D616D35EA7AAED | SHA256:078661EFC312730C18EB785799080B30CE27EC475EDC7EFBD692BE1691D02BC6 | |||
| 3476 | Extreme Injector v3.exe | C:\Users\admin\Desktop\settings.xml | xml | |
MD5:1A1161C72A47D86DBB83F6A965485EF8 | SHA256:6118F0F883B414305A5C906453182E84977075CD75B33475AB34DB7D45D2EB7C | |||
| 3476 | Extreme Injector v3.exe | C:\Users\admin\AppData\Local\Temp\tmp1B24.tmp | xml | |
MD5:1E4A89B11EAE0FCF8BB5FDD5EC3B6F61 | SHA256:4BB79DCEA0A901F7D9EAC5AA05728AE92ACB42E0CB22E5DD14134F4421A3D8DF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
40
DNS requests
25
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.38:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2876 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
4748 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4748 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5560 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.216.77.38:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 2.16.253.202:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2876 | svchost.exe | 20.190.160.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2876 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
mcr-ring.msedge.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |