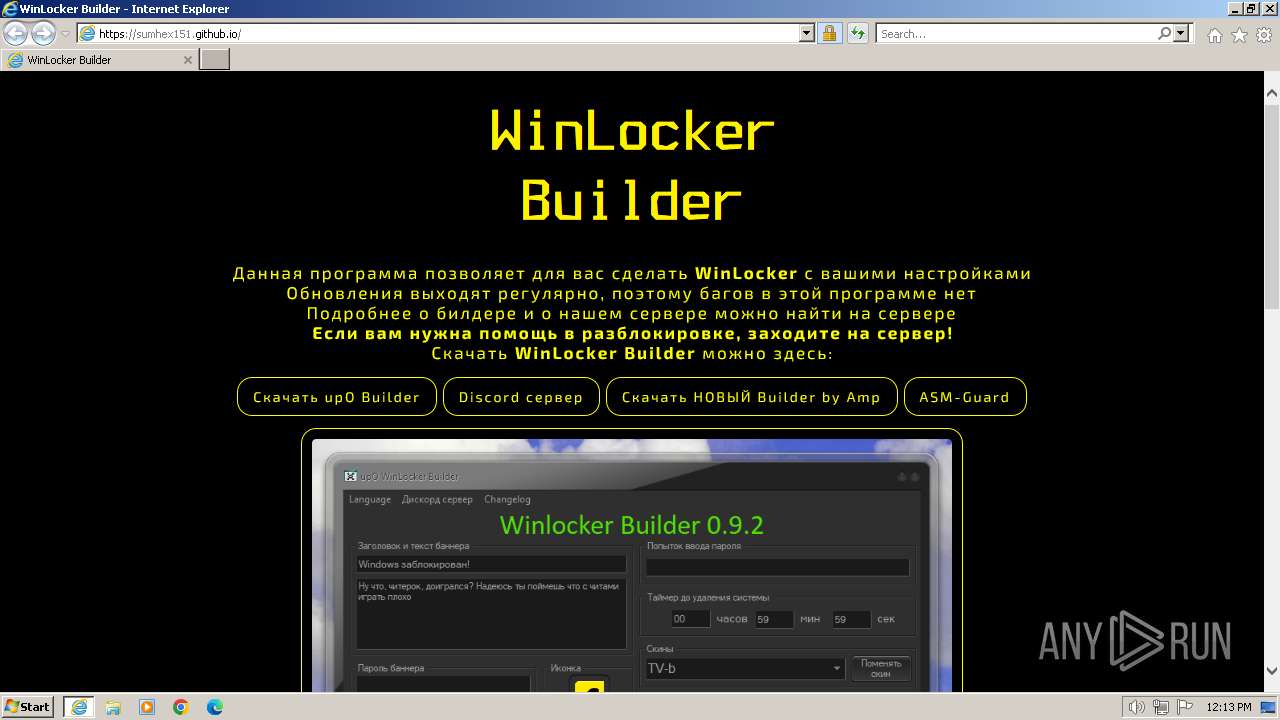
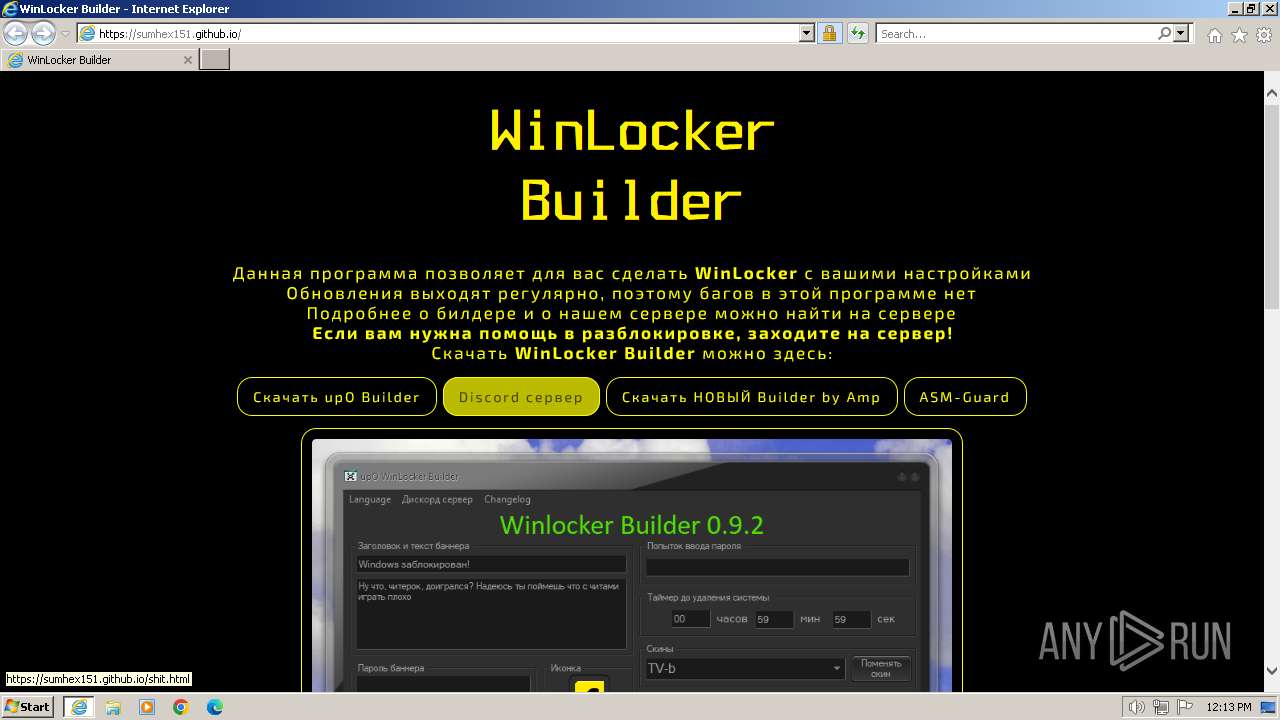
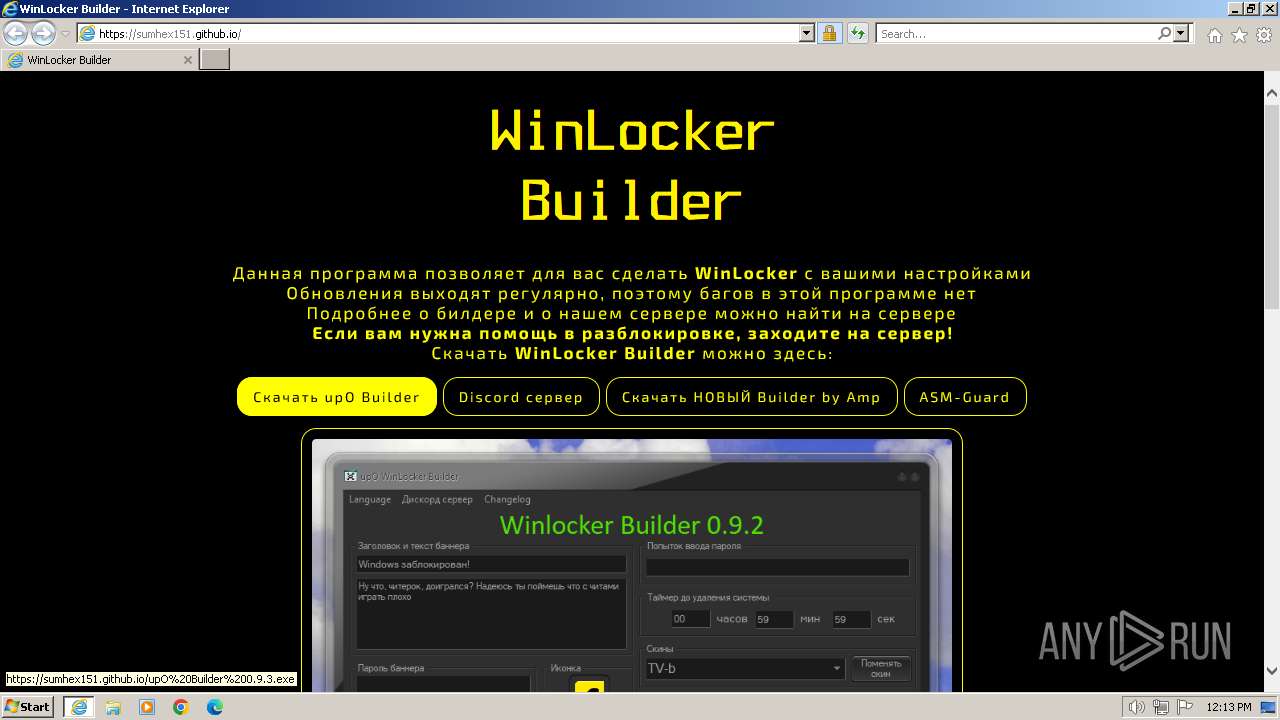
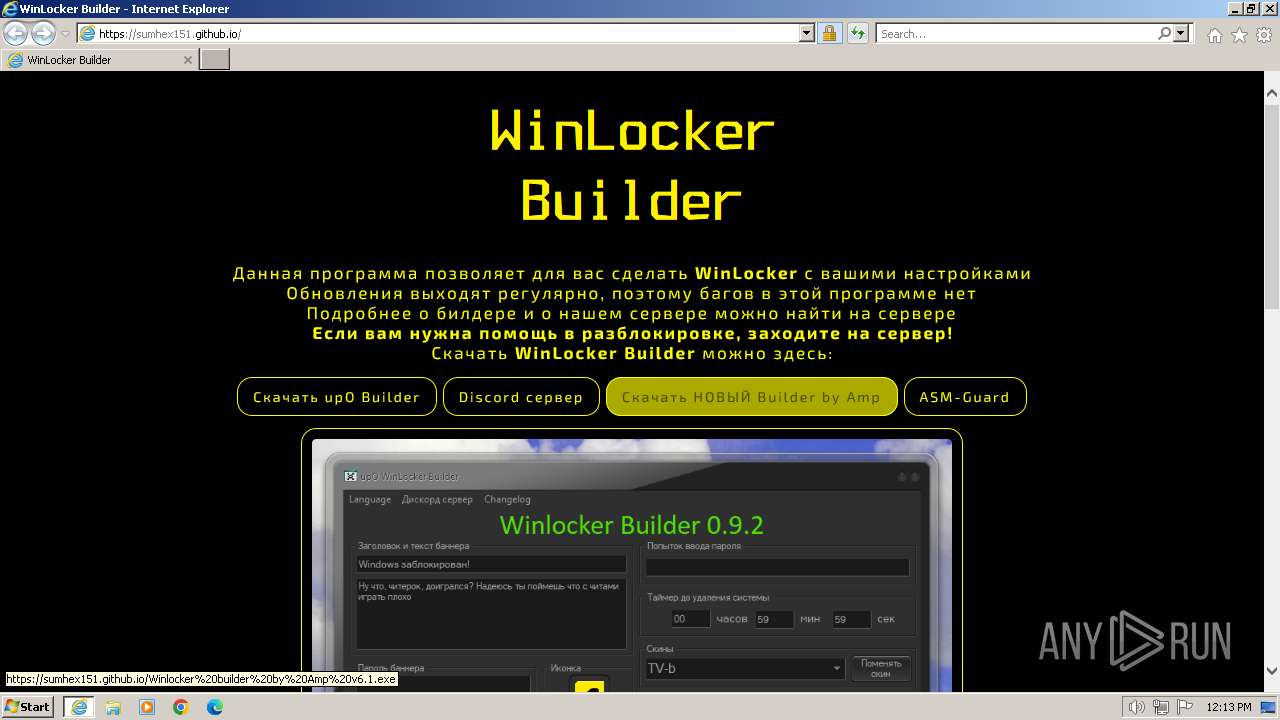
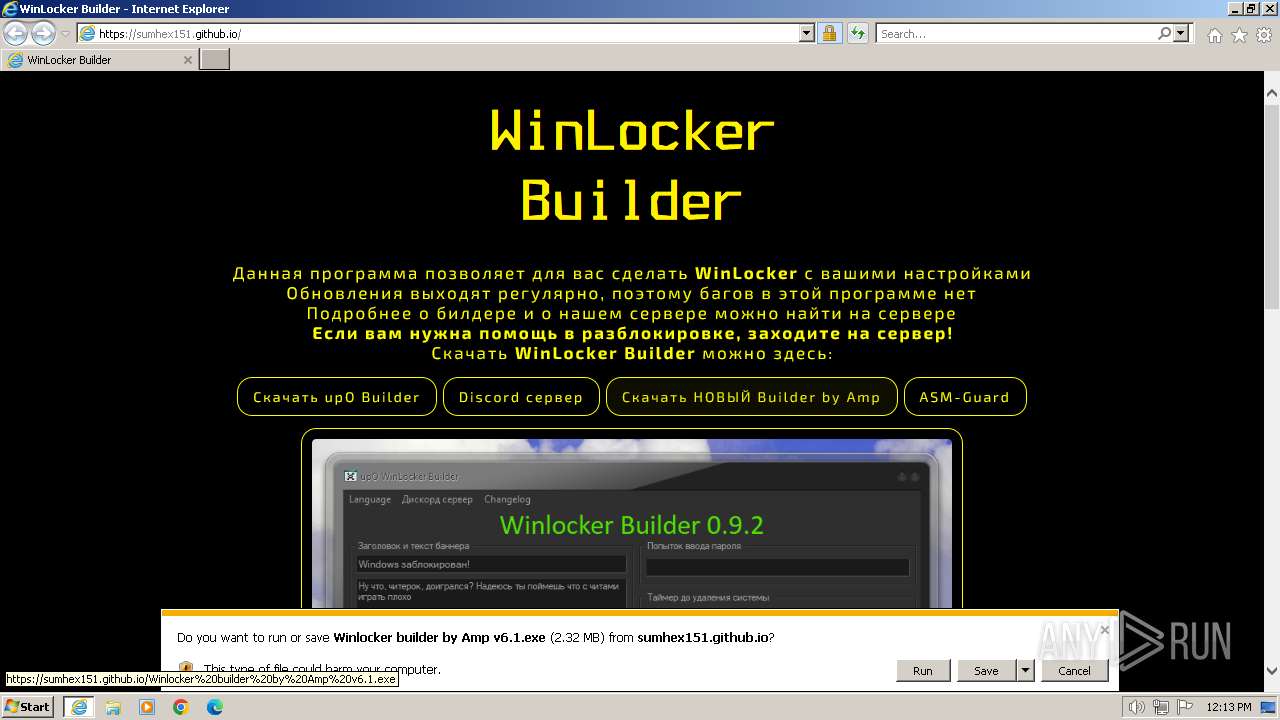
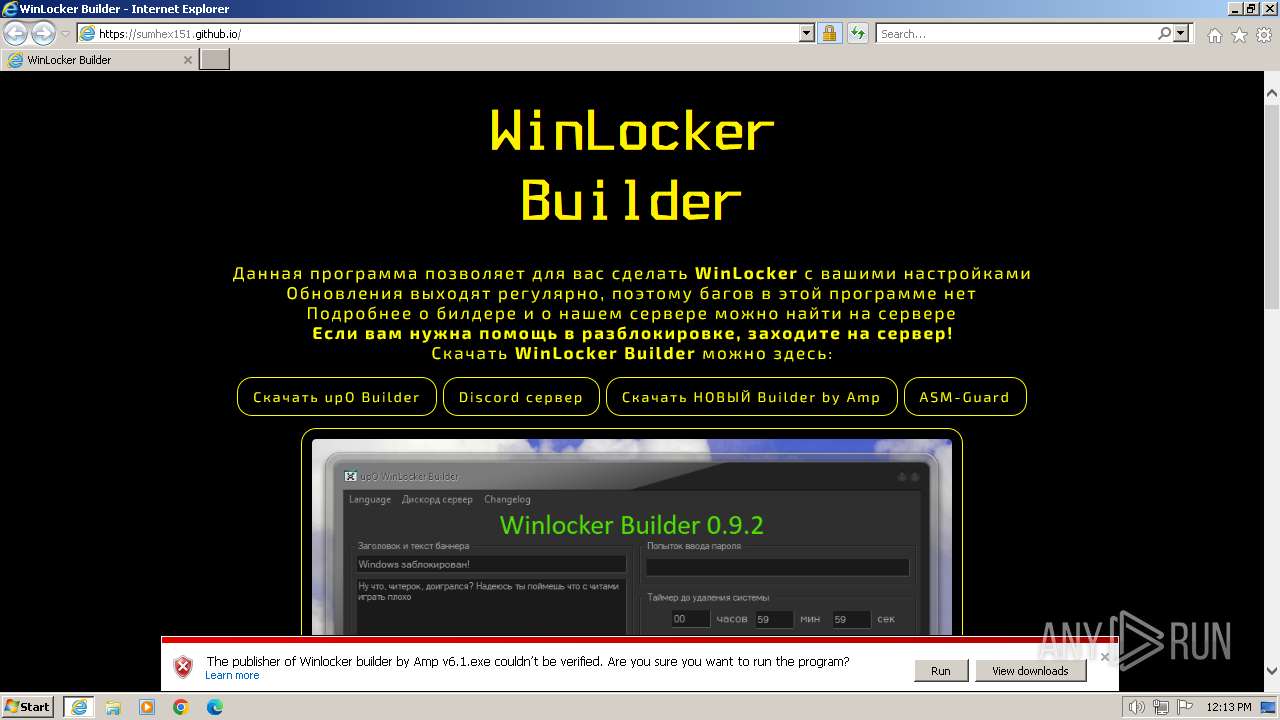
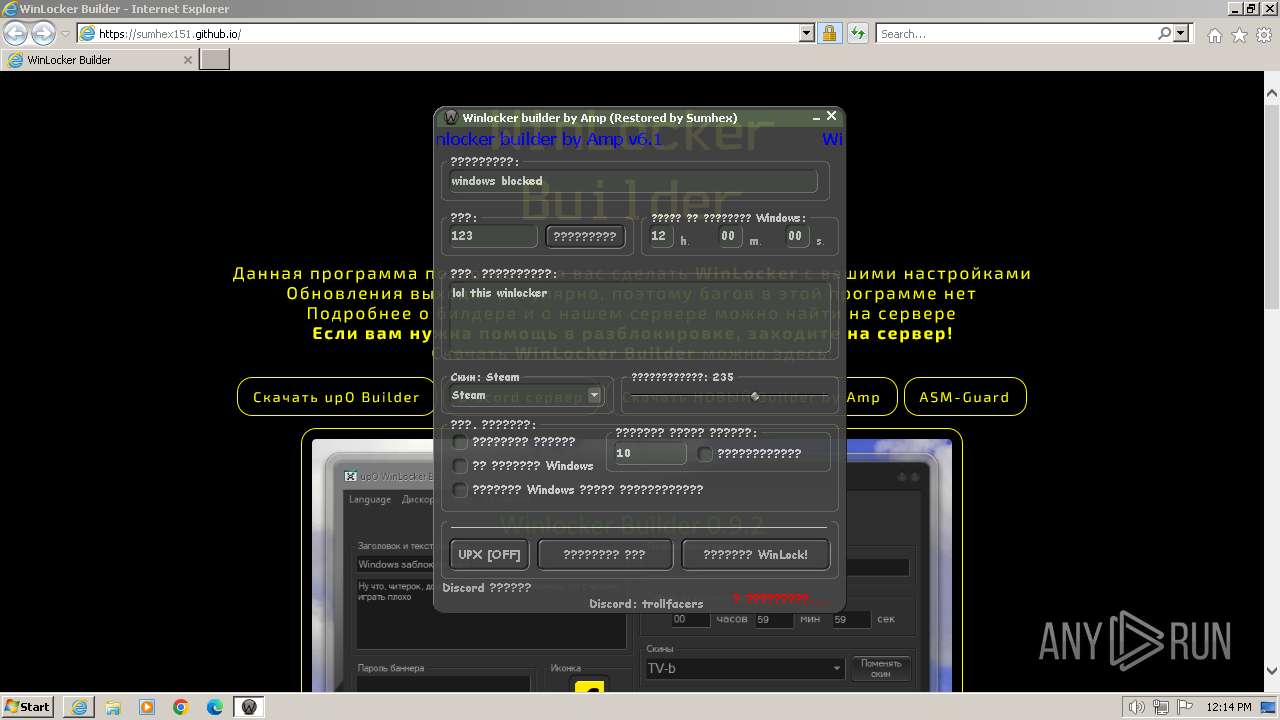
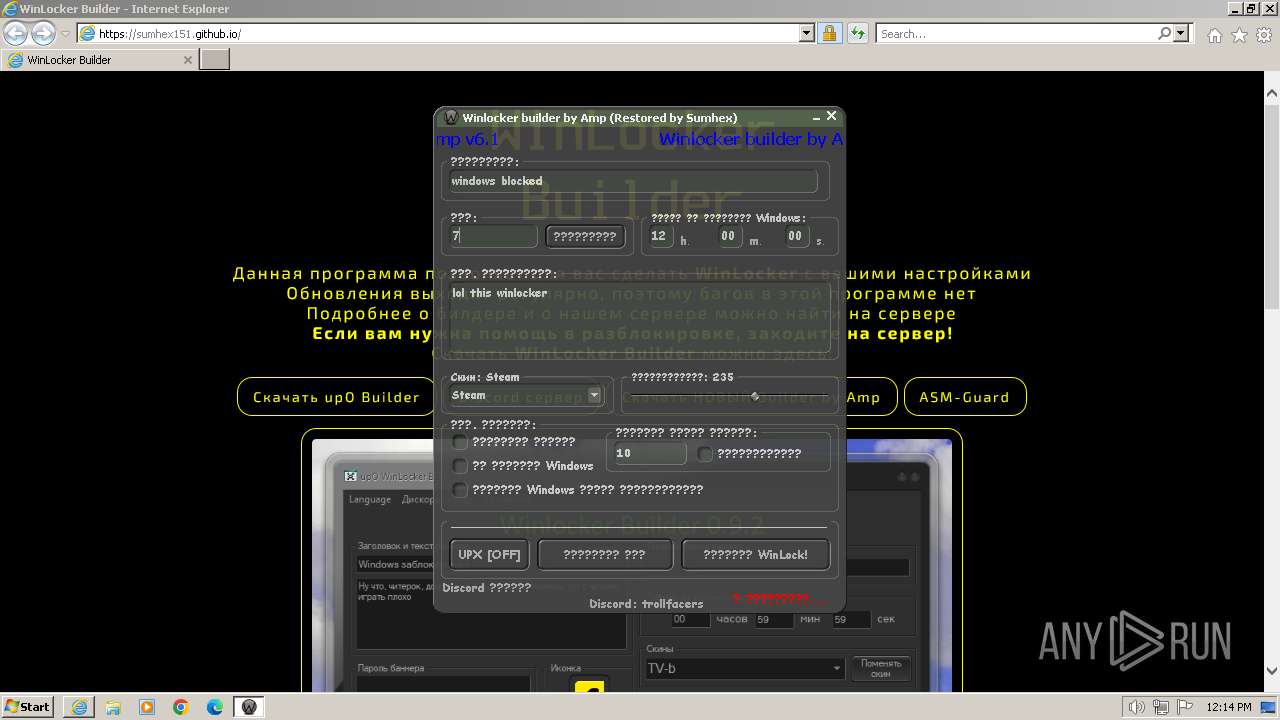
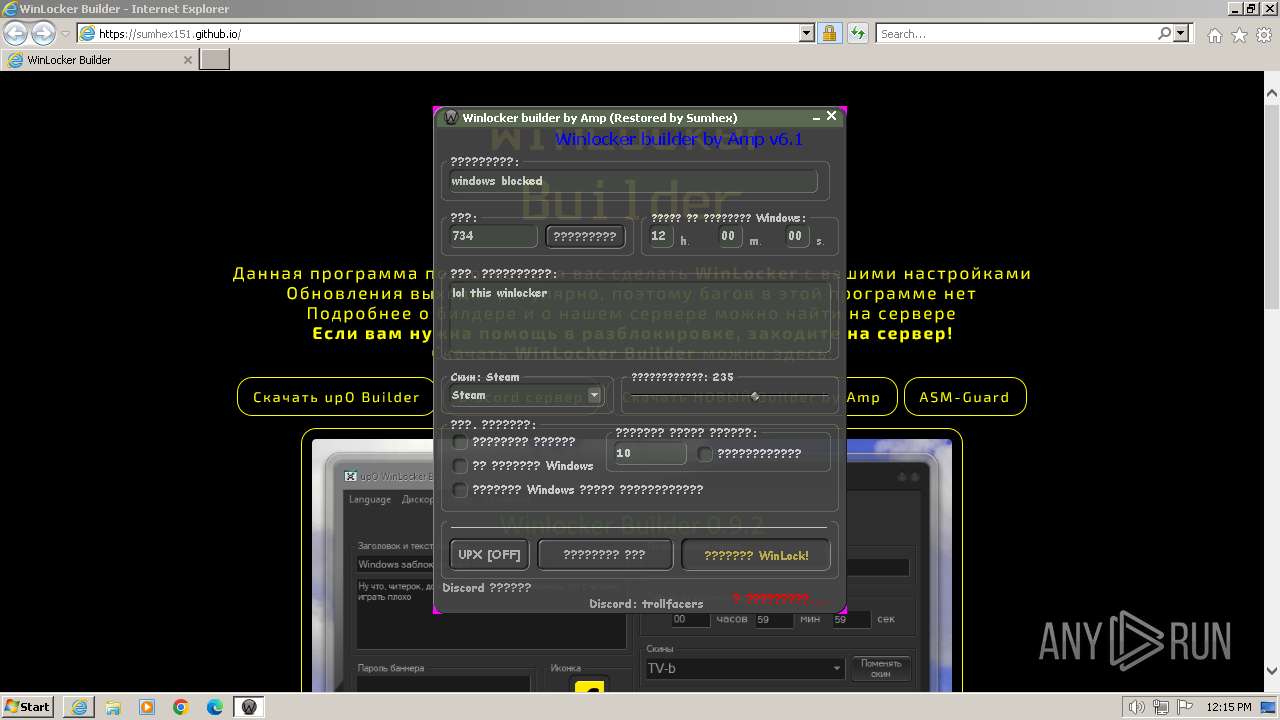
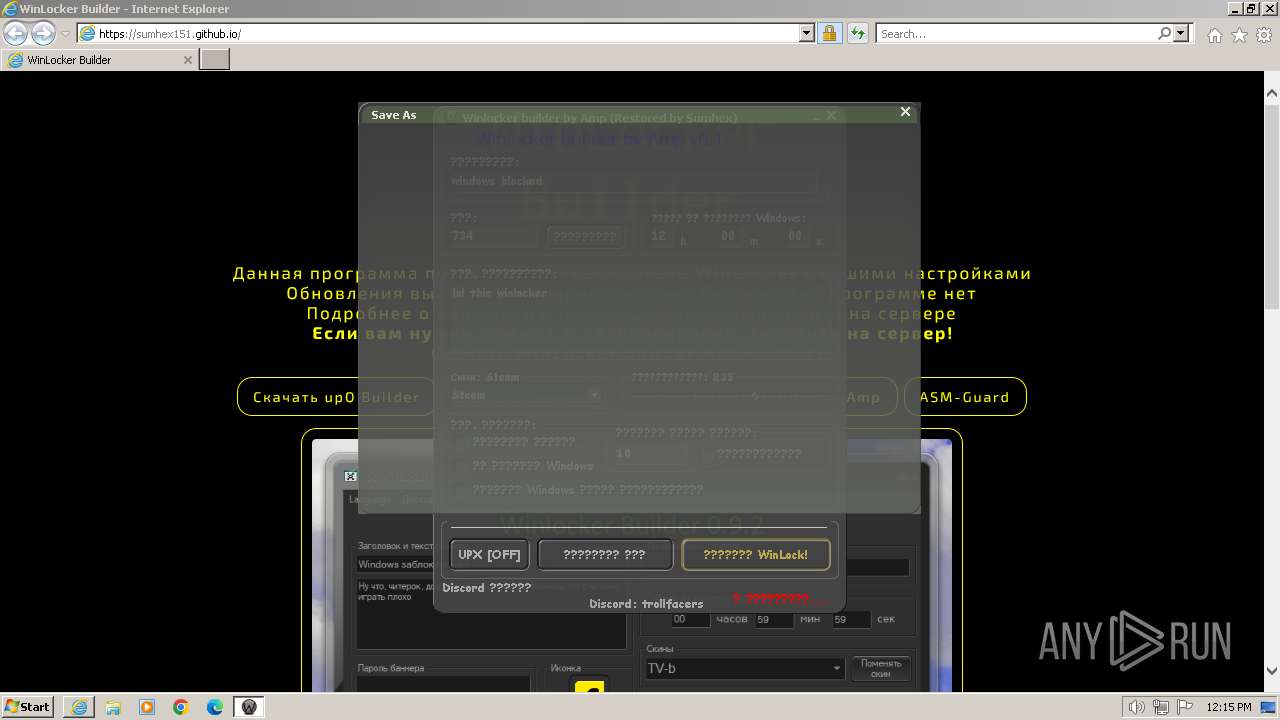
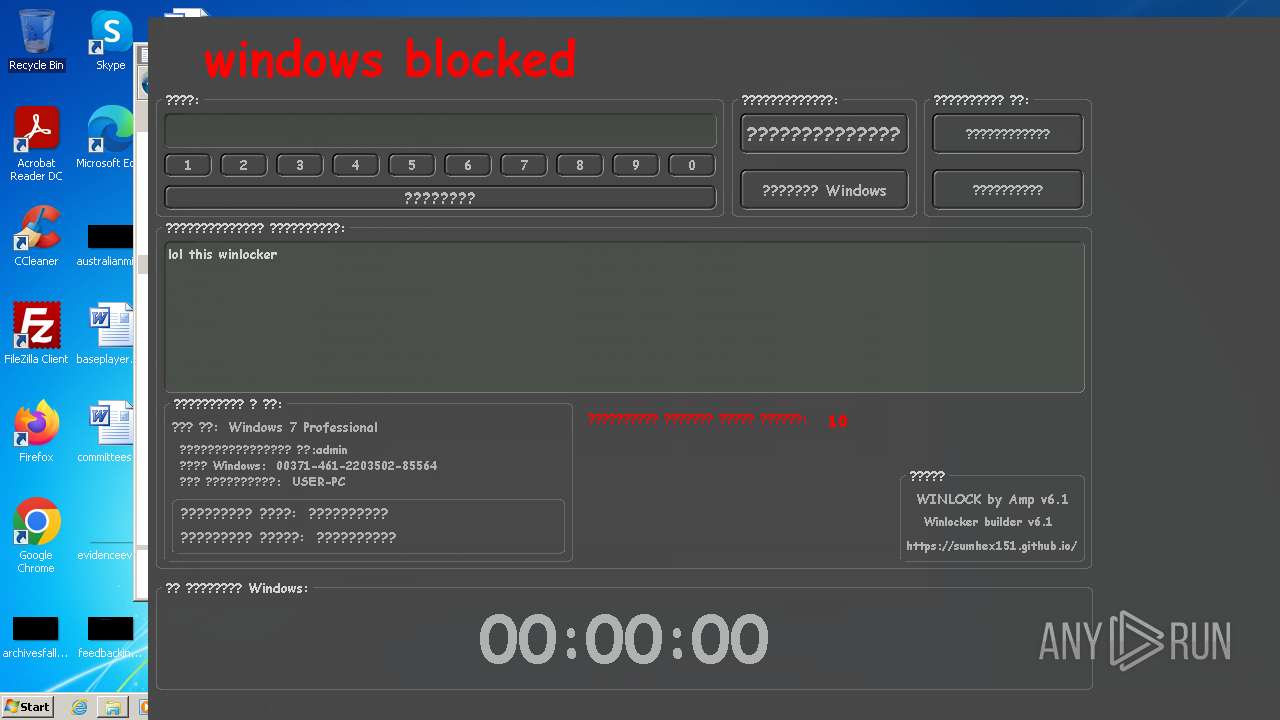
| URL: | https://sumhex151.github.io/ |
| Full analysis: | https://app.any.run/tasks/9bd0228c-f1f1-46f2-94f8-ef55ce1cfbe4 |
| Verdict: | Malicious activity |
| Analysis date: | January 01, 2024, 12:13:30 |
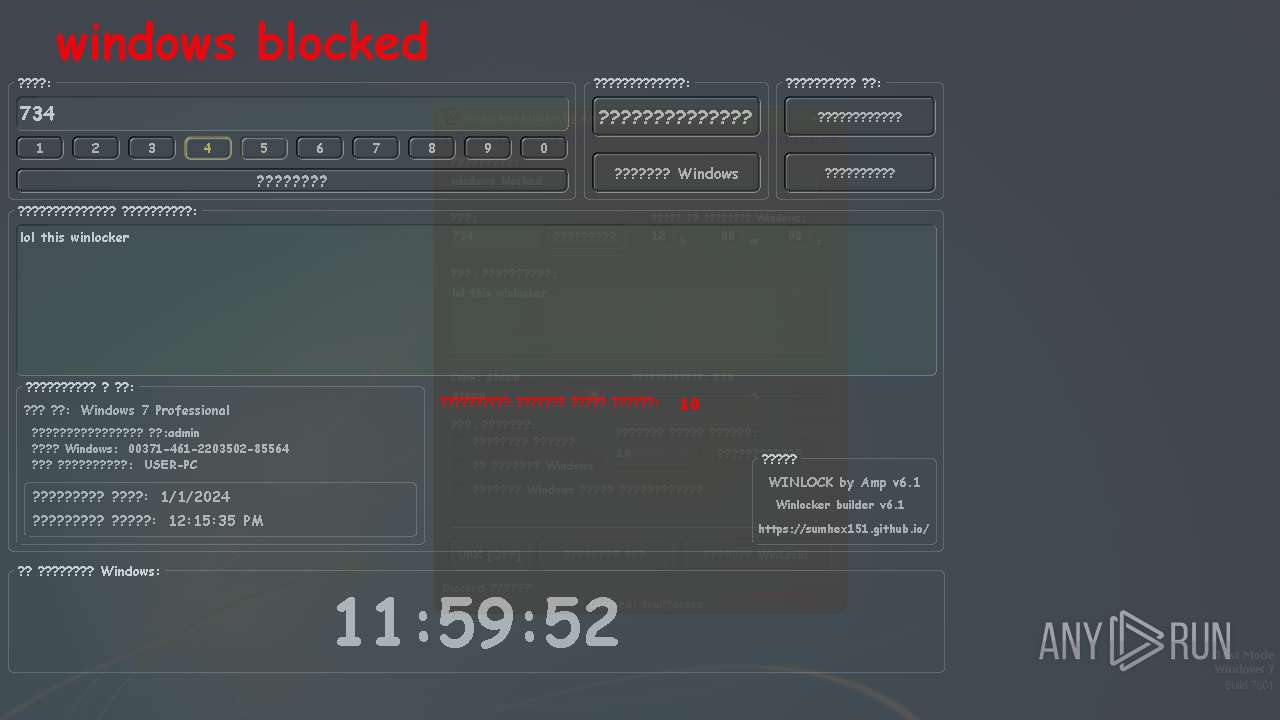
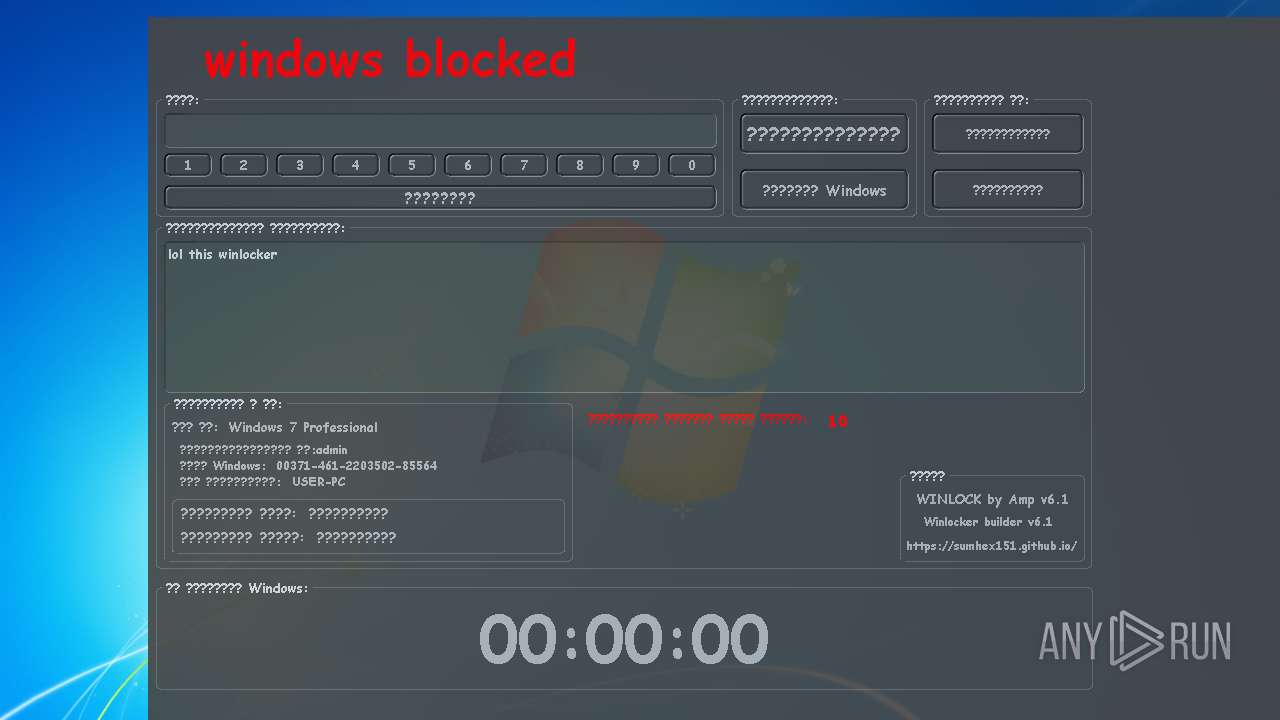
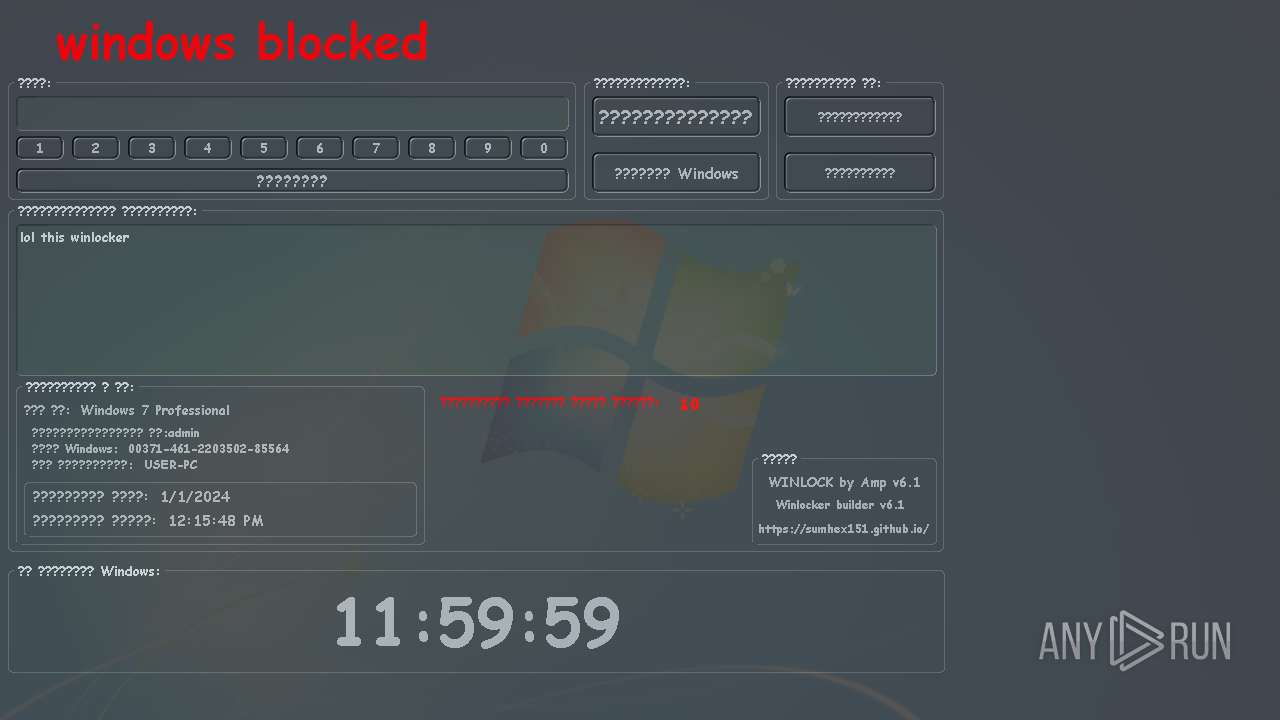
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 6FD8FC51A0741091074DBBEDA81DF913 |
| SHA1: | 87D99C744A594413FB31DF8208FCC5633F16D2DC |
| SHA256: | BC221BFDA562CF78B8B8C427A04BB6D10A7C5C79A428E99364CDCABC9B467538 |
| SSDEEP: | 3:N8dXaI+:29R+ |
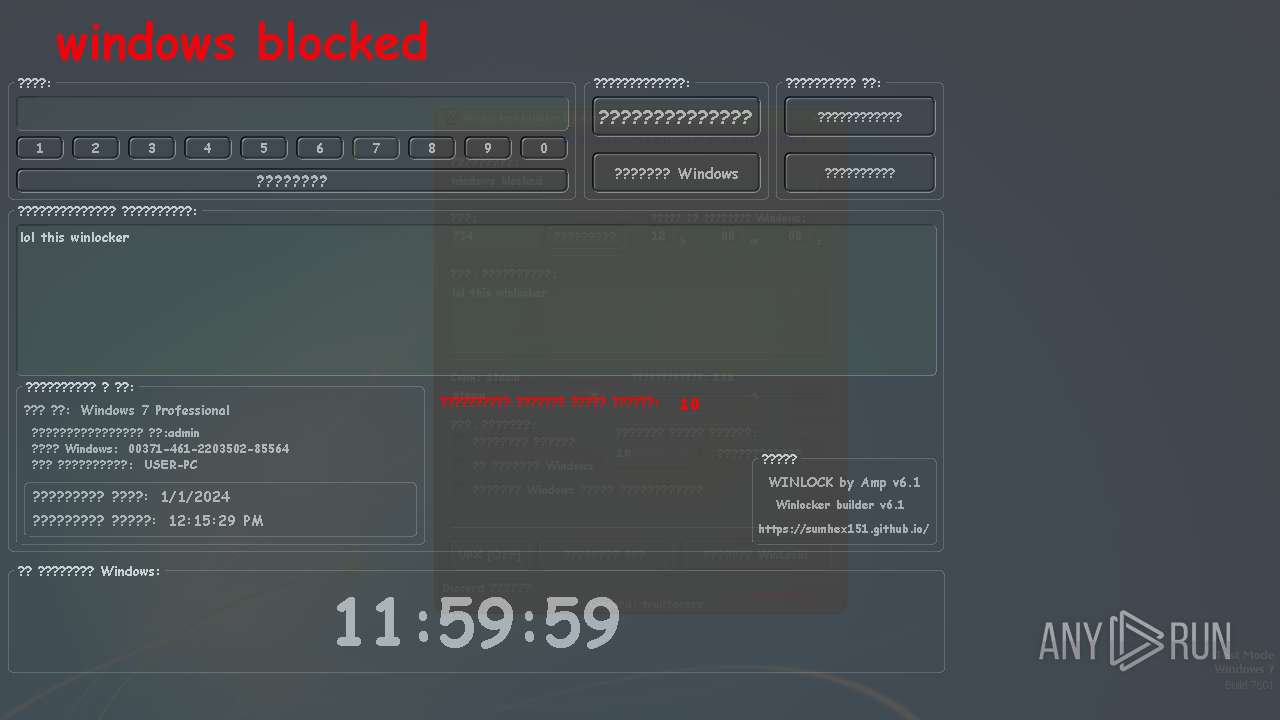
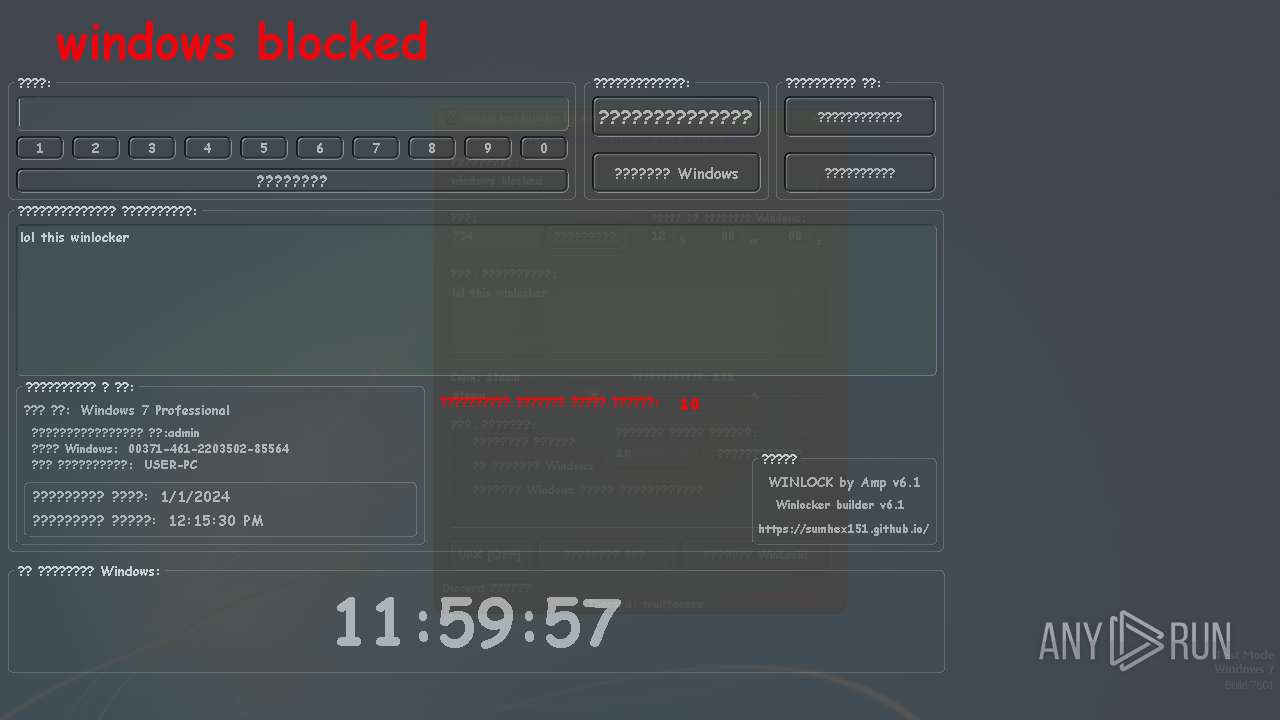
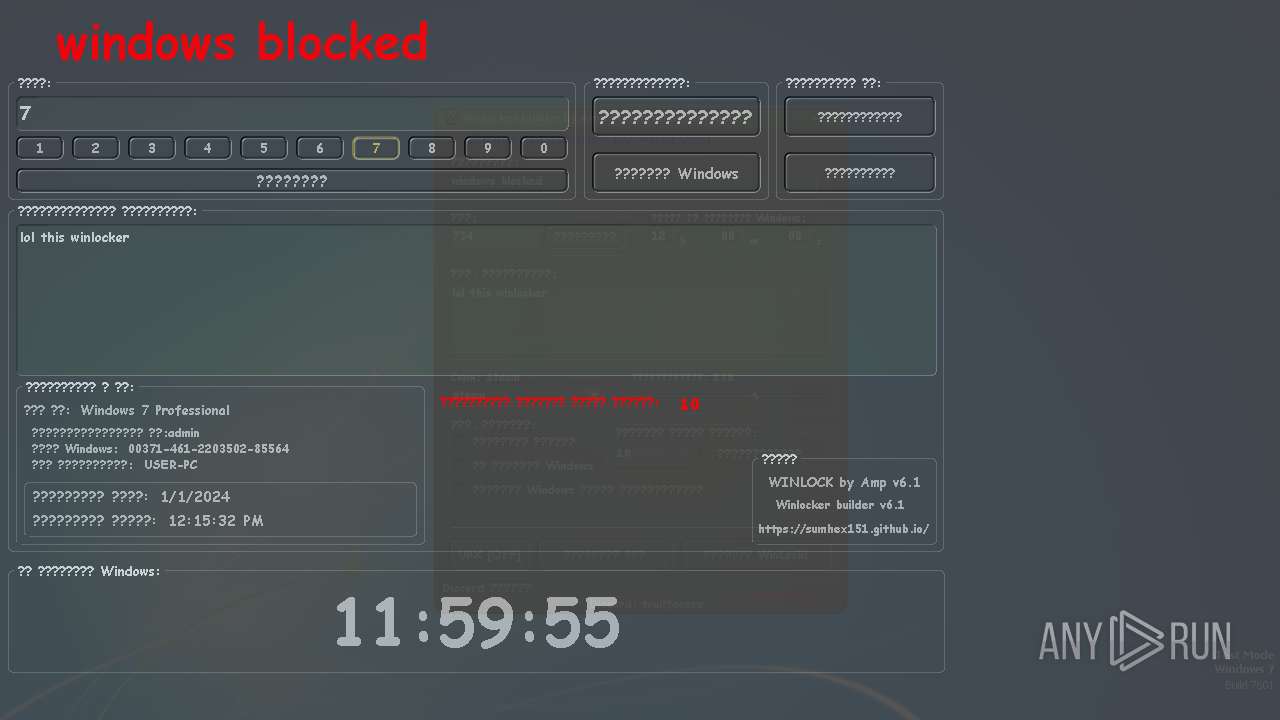
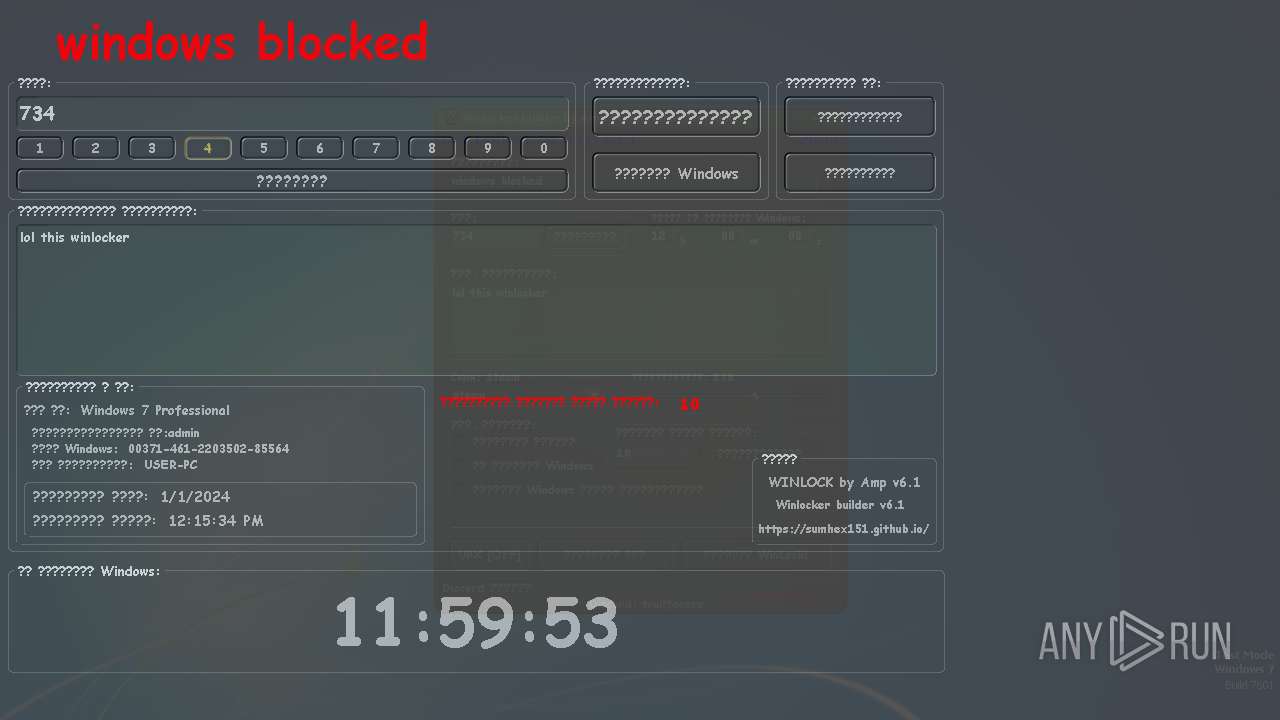
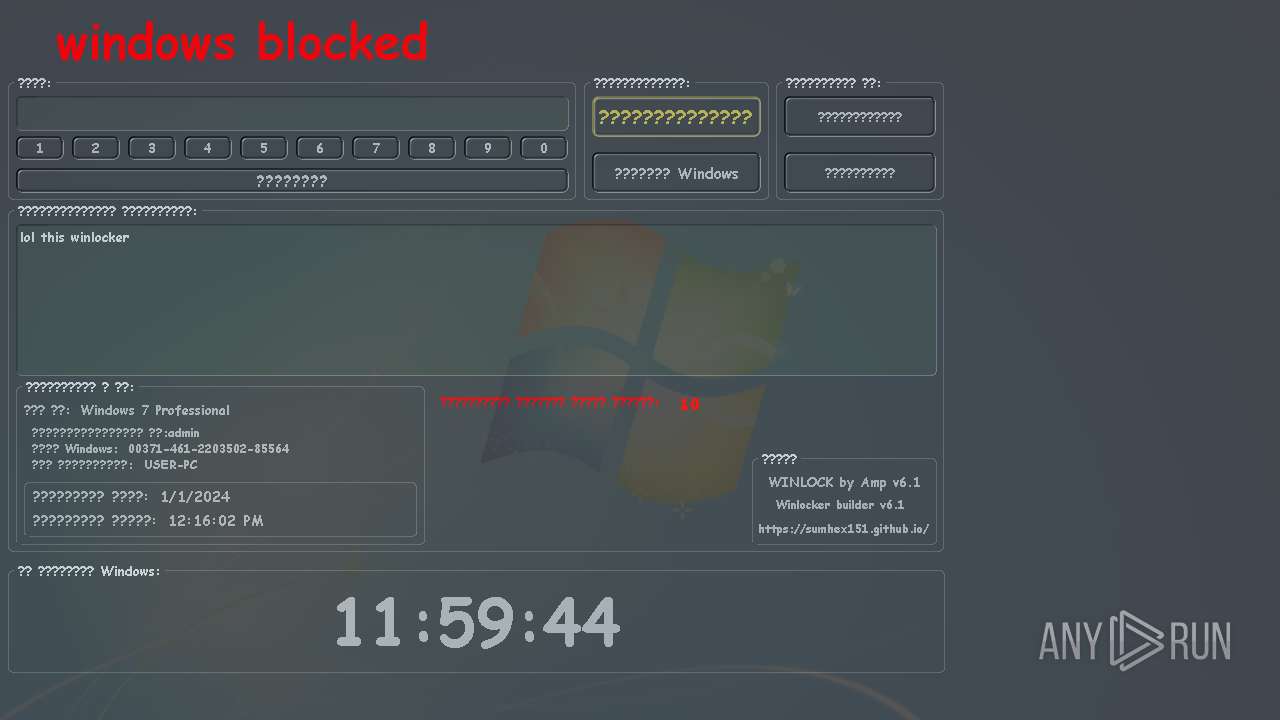
MALICIOUS
UAC/LUA settings modification
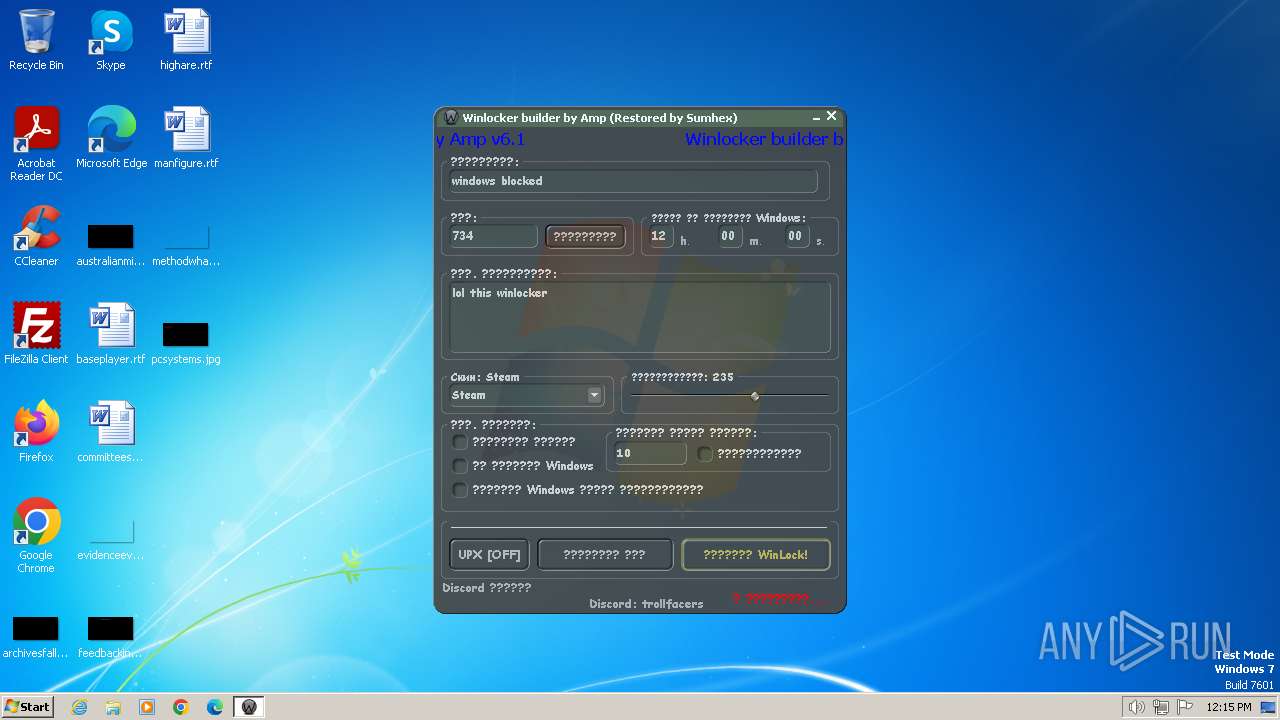
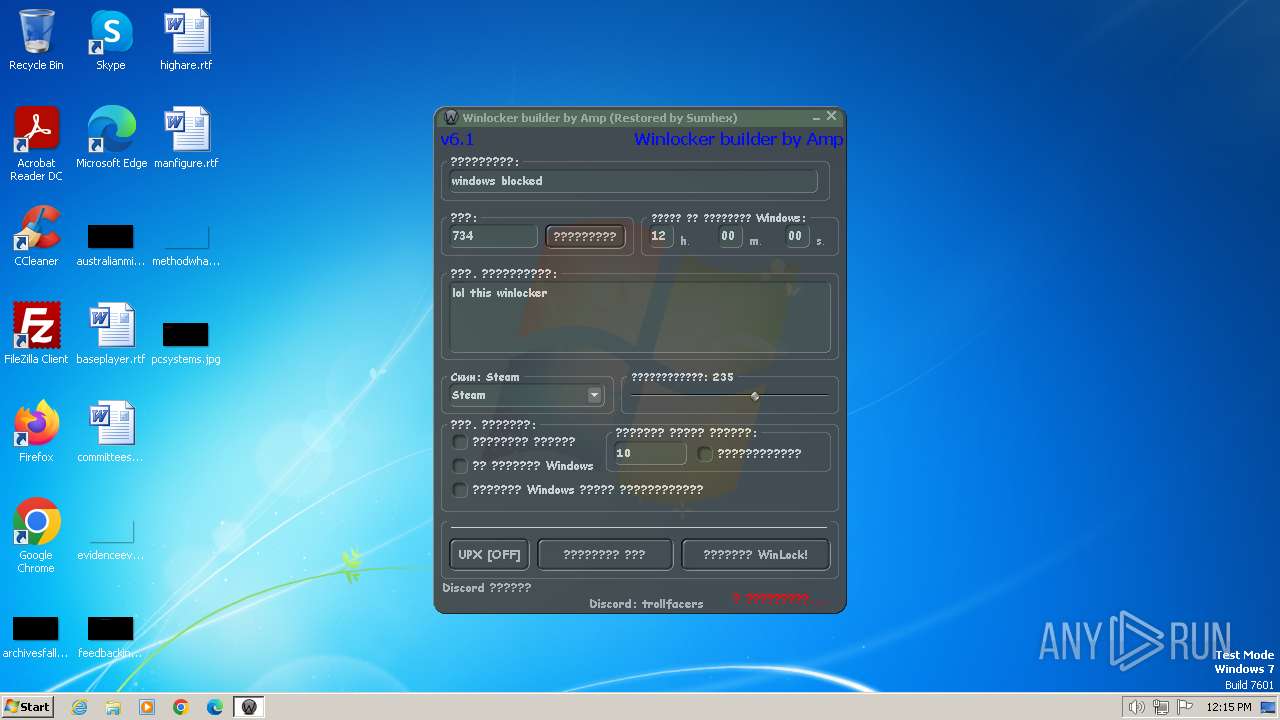
- WinLocker.exe (PID: 3148)
- WinLocker.exe (PID: 3888)
SUSPICIOUS
Reads the Internet Settings
- Winlocker builder by Amp v6.1.exe (PID: 848)
- WinLocker.exe (PID: 3148)
Reads the Windows owner or organization settings
- WinLocker.exe (PID: 3148)
- WinLocker.exe (PID: 3888)
INFO
Application launched itself
- iexplore.exe (PID: 2184)
Checks supported languages
- Winlocker builder by Amp v6.1.exe (PID: 848)
- WinLocker.exe (PID: 3148)
- wmpnscfg.exe (PID: 3644)
- wmpnscfg.exe (PID: 3844)
- WinLocker.exe (PID: 3888)
Drops the executable file immediately after the start
- iexplore.exe (PID: 2184)
- iexplore.exe (PID: 1056)
- Winlocker builder by Amp v6.1.exe (PID: 848)
Reads the computer name
- Winlocker builder by Amp v6.1.exe (PID: 848)
- WinLocker.exe (PID: 3148)
- wmpnscfg.exe (PID: 3644)
- wmpnscfg.exe (PID: 3844)
- WinLocker.exe (PID: 3888)
Reads the machine GUID from the registry
- Winlocker builder by Amp v6.1.exe (PID: 848)
The process uses the downloaded file
- iexplore.exe (PID: 2184)
Manual execution by a user
- WinLocker.exe (PID: 3148)
- WinLocker.exe (PID: 3052)
Reads Environment values
- WinLocker.exe (PID: 3148)
- WinLocker.exe (PID: 3888)
Reads product name
- WinLocker.exe (PID: 3148)
- WinLocker.exe (PID: 3888)
Reads Windows Product ID
- WinLocker.exe (PID: 3148)
- WinLocker.exe (PID: 3888)
Reads the Internet Settings
- explorer.exe (PID: 3248)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
56
Monitored processes
9
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
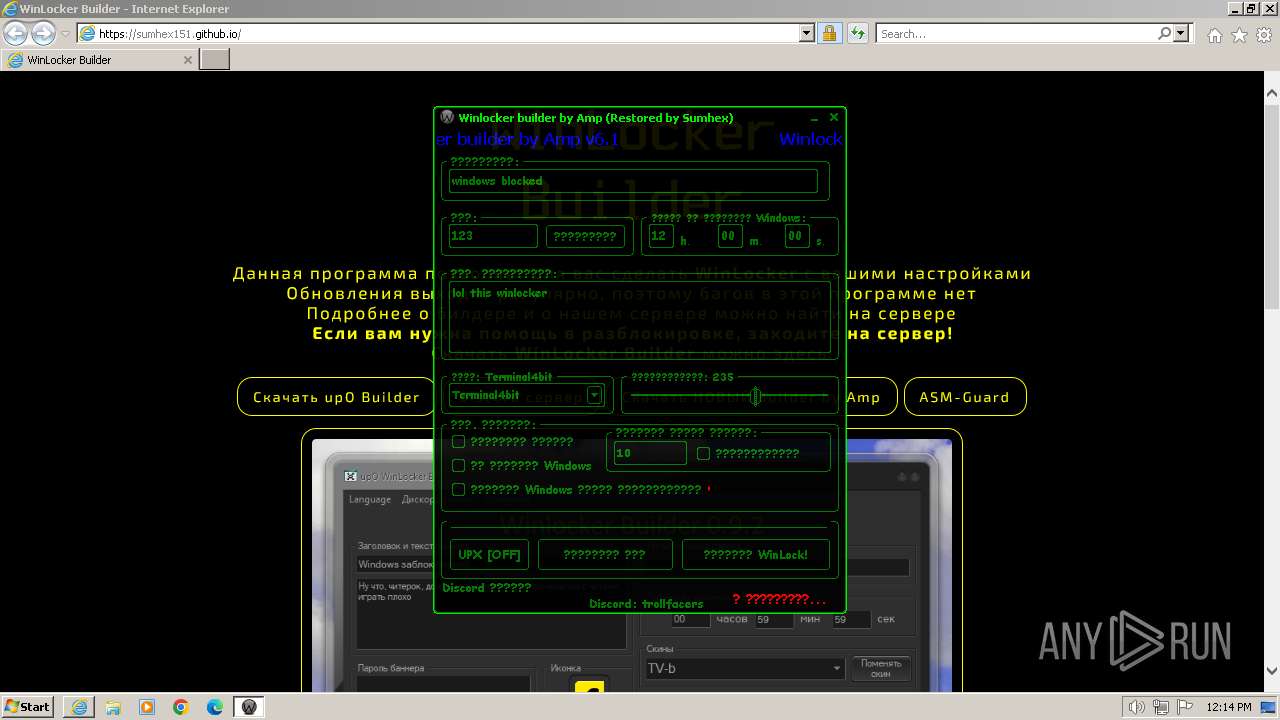
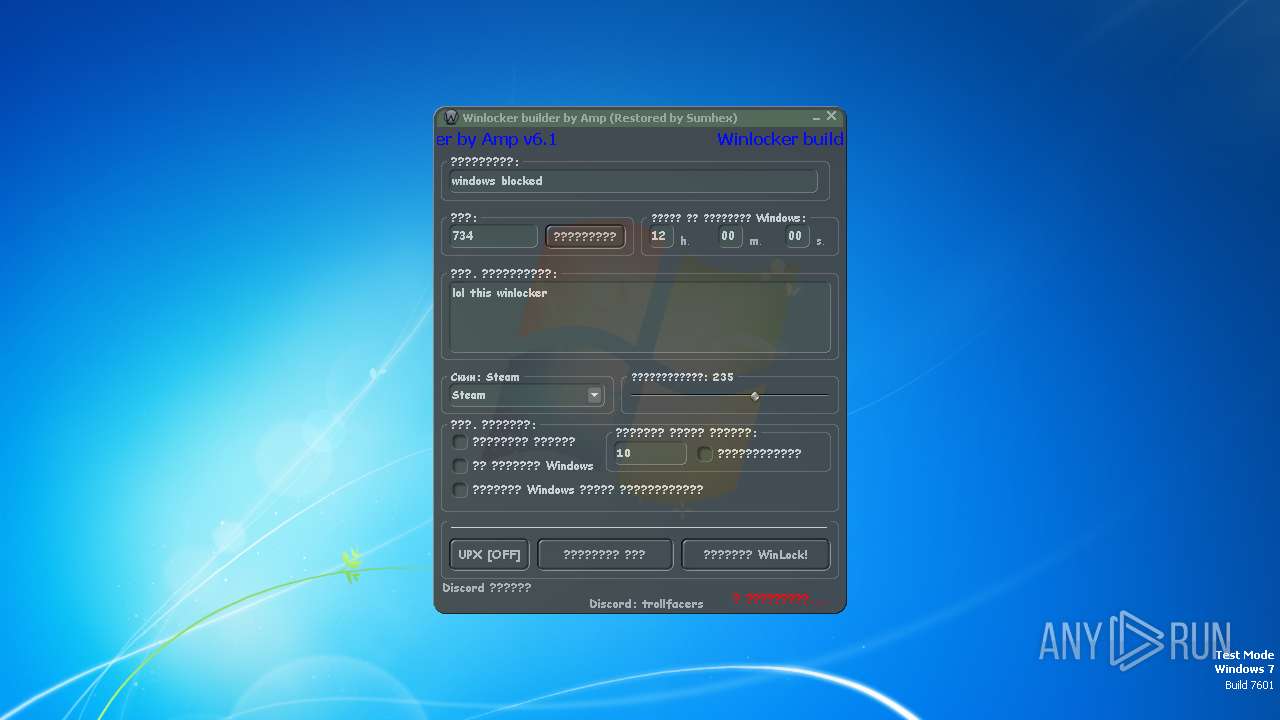
| 848 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\Winlocker builder by Amp v6.1.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\Winlocker builder by Amp v6.1.exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1073807364 Modules
| |||||||||||||||
| 1056 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2184 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2184 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://sumhex151.github.io/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3052 | "C:\Users\admin\Documents\WinLocker.exe" | C:\Users\admin\Documents\WinLocker.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3148 | "C:\Users\admin\Documents\WinLocker.exe" | C:\Users\admin\Documents\WinLocker.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3248 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | WinLocker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3644 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3844 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3888 | "C:\Users\admin\Documents\WinLocker.exe" | C:\Users\admin\Documents\WinLocker.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1073807364 Modules
| |||||||||||||||
Total events
22 324
Read events
22 003
Write events
289
Delete events
32
Modification events
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
22
Suspicious files
40
Text files
29
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1056 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\logo[1].png | image | |
MD5:4F691B6974135B344A621EBF8BE4727E | SHA256:2EB2AC08E81F52944E6E7D39ABF4F18775EA8029B95A9AFF1D9078C3B3C65561 | |||
| 1056 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:4FDB70826589C399F6A51FEF02EEE99A | SHA256:B2AEC7B536A73A0BF301B98ADD72FD95422E6E4978C396E912D094012DC1B82E | |||
| 1056 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 1056 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\styles[1].css | text | |
MD5:6C5A5F48D4AD83B3BD6A9310173B9588 | SHA256:053B0319B41995DF48EDCAD24D1EC192FBEF5D7D768ED4E3E9F981D6895A862A | |||
| 1056 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 1056 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:034EC3B760B9B922D37EC2D86820EBFA | SHA256:015E7444EB0FDF2CAE85AEF5C1D3D1AEE98ED7E692C848EA45BFEC3A35CCD821 | |||
| 1056 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:C9F92CE1A5EB8CF8D9FC955258D0B462 | SHA256:FB9BFF49A39E09DFC7178A779EEEBF5672B5E54E4E8769E3E7693EDBE9D29673 | |||
| 1056 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:C07CBC6B3698044212CC6998C9FF3D34 | SHA256:DEE3DBE7B3435CA75E8BECA8A32132B4684807065F7AC05DF0F9300BBC6DD5CB | |||
| 1056 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:8F98792A81345B73F340D27FB8E0BBA3 | SHA256:D2C472CE0F17467211FDCF153622352E205029C09937015FC554577C78B9B05D | |||
| 1056 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\scrin[1].png | image | |
MD5:D0291E42768E2B1647472381E5593F71 | SHA256:7A7C3A3161B9ED103864CAE250BD41821260CCF3A857CEA8E8323CFE321CFDCA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
33
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1056 | iexplore.exe | GET | 200 | 23.216.77.50:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f6bf34dbb61e71d7 | unknown | compressed | 4.66 Kb | unknown |
1056 | iexplore.exe | GET | 200 | 23.216.77.50:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?608cb4ab6d3f68d3 | unknown | compressed | 4.66 Kb | unknown |
1056 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
1056 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
1056 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
1056 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEA1uFYrLabZxEtE2U5X5DGM%3D | unknown | binary | 471 b | unknown |
1056 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQClj3zJOwEs2AlR6v%2BfUXog | unknown | binary | 472 b | unknown |
2184 | iexplore.exe | GET | 304 | 23.216.77.50:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d8f761b8c0f86c21 | unknown | — | — | unknown |
2184 | iexplore.exe | GET | 304 | 23.216.77.50:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?111b88f027149bc7 | unknown | — | — | unknown |
2184 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1056 | iexplore.exe | 185.199.109.153:443 | sumhex151.github.io | FASTLY | US | shared |
1056 | iexplore.exe | 23.216.77.50:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1056 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1056 | iexplore.exe | 142.250.186.42:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
1056 | iexplore.exe | 142.250.184.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1056 | iexplore.exe | 142.250.185.163:443 | fonts.gstatic.com | GOOGLE | US | whitelisted |
2184 | iexplore.exe | 185.199.109.153:443 | sumhex151.github.io | FASTLY | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
sumhex151.github.io |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |