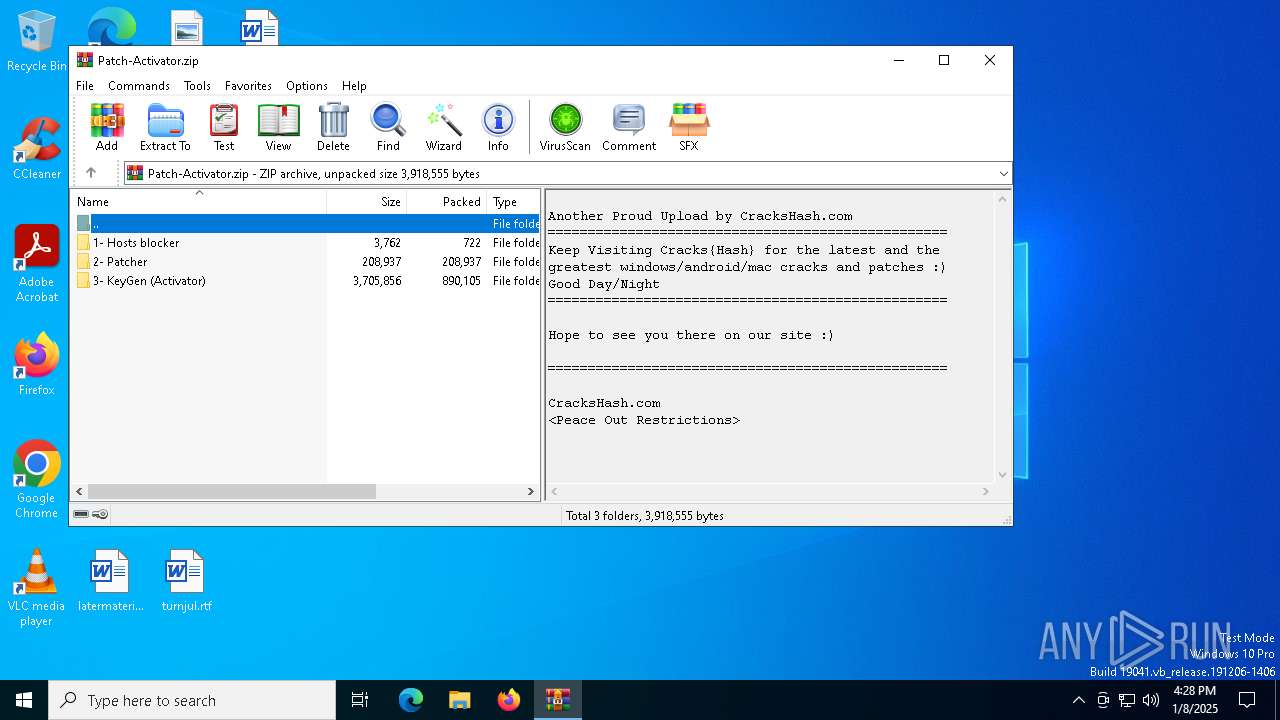
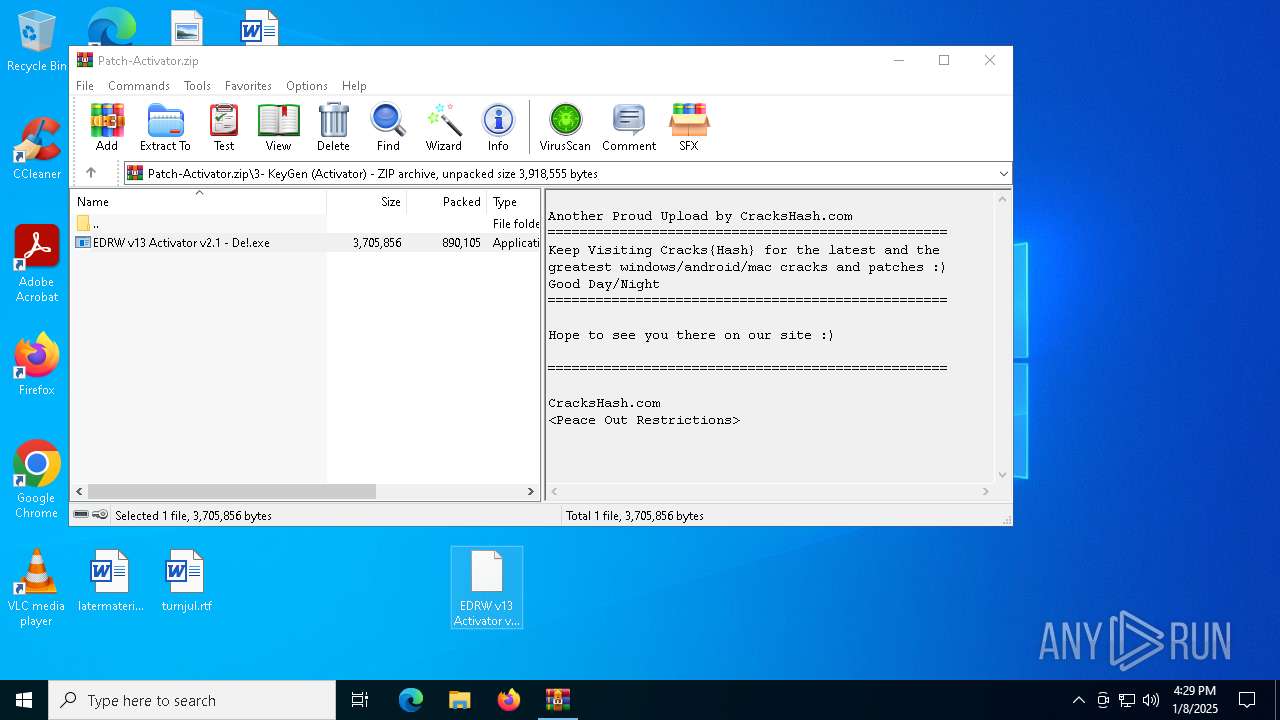
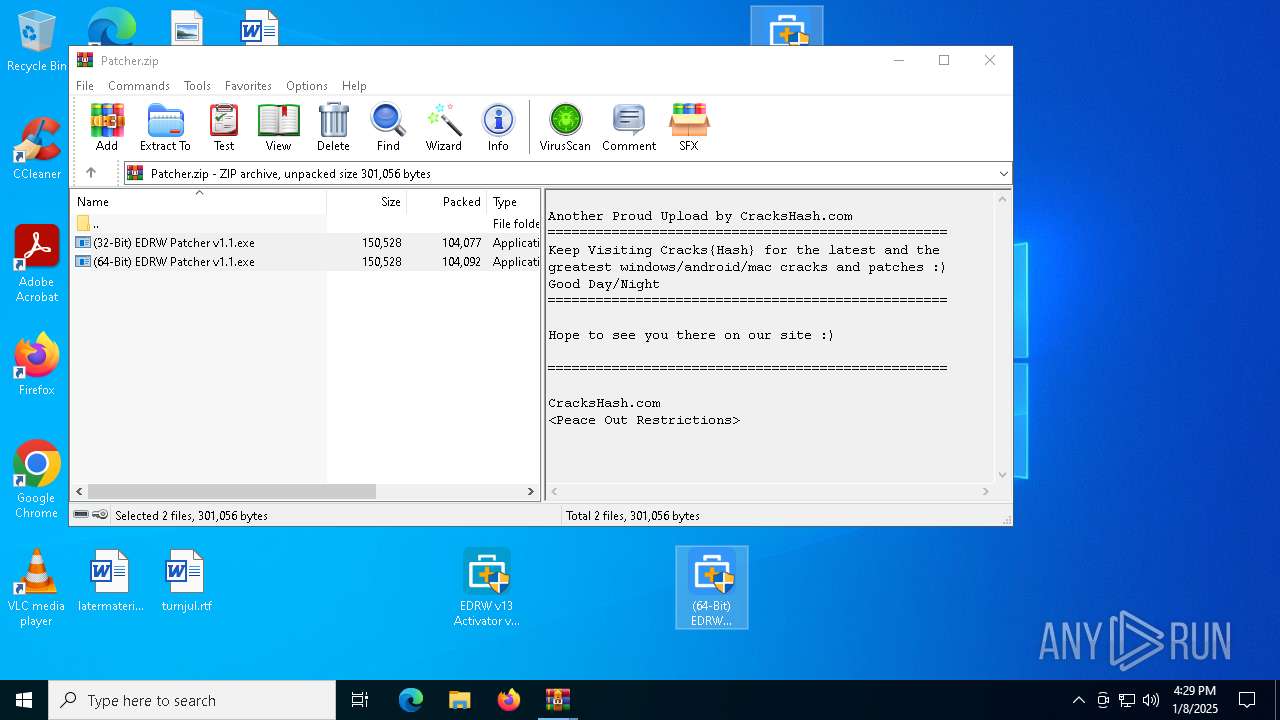
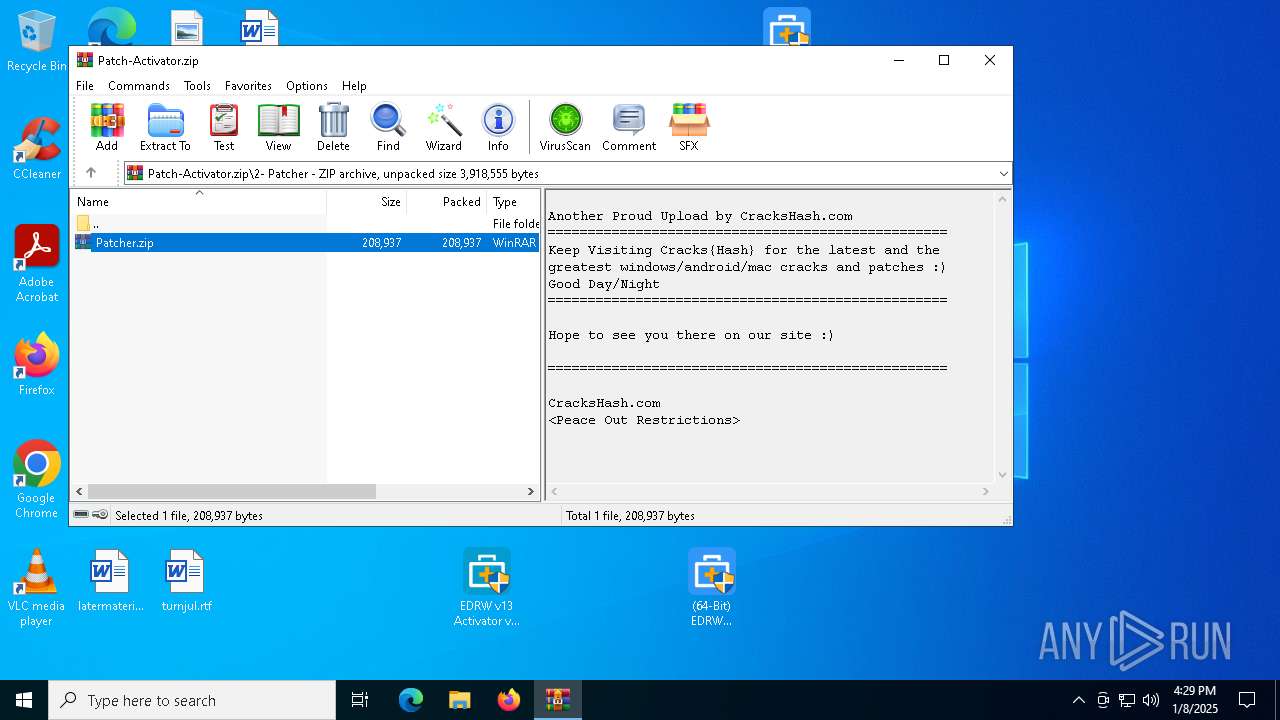
| File name: | Patch-Activator.zip |
| Full analysis: | https://app.any.run/tasks/a54492fc-abe8-4d74-91ca-9278430922ce |
| Verdict: | Malicious activity |
| Analysis date: | January 08, 2025, 16:28:34 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 1827E311D07F5D99951E4A2589D164A4 |
| SHA1: | ADE1A00A7ABCA3DC8CF013274B244DBB7B046718 |
| SHA256: | BBDA179721155C4FA6BAC7C8276333516FE3BDA81C4ECAAD65F1A4000C7838A3 |
| SSDEEP: | 49152:Tl/8zqTyaZifB2l/8zLpwGYu/32enMkJZCYuO8EZF7vuAh1BT+MVmczBfanu5nL8:TR8zqTyjgR8zLvYY32yMVSH7f1BT+MVw |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 6800)
Executable content was dropped or overwritten
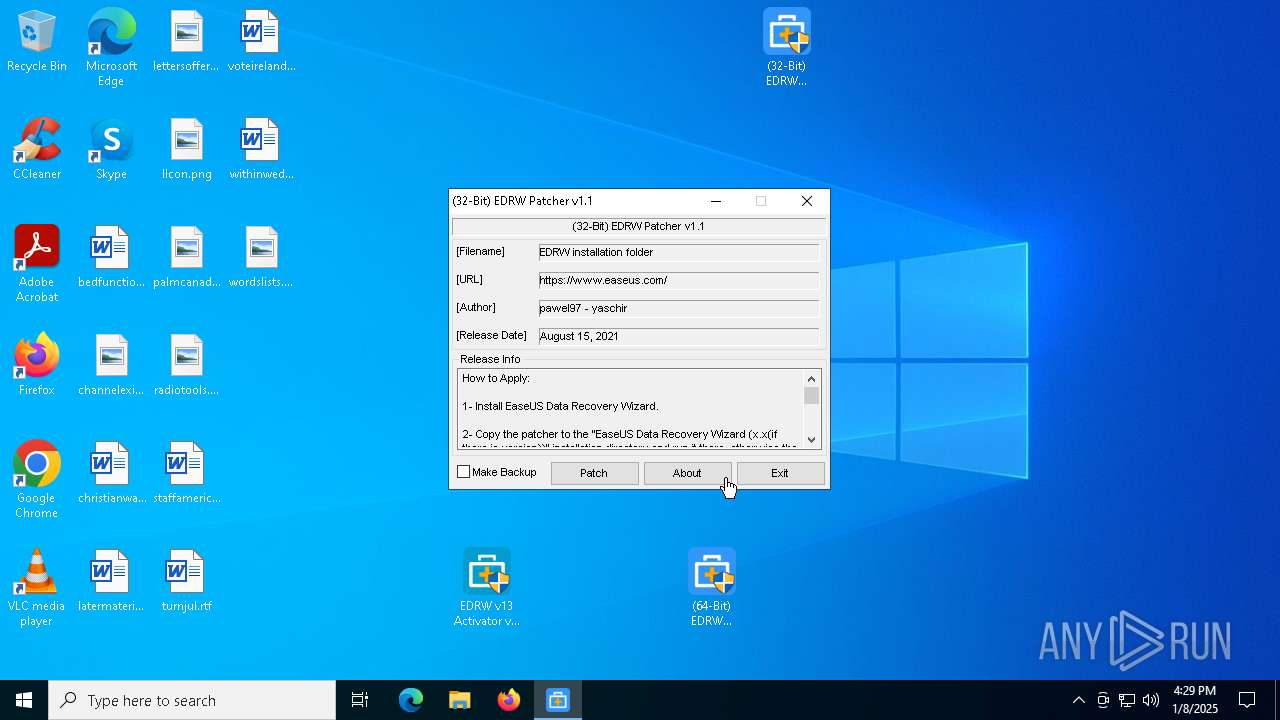
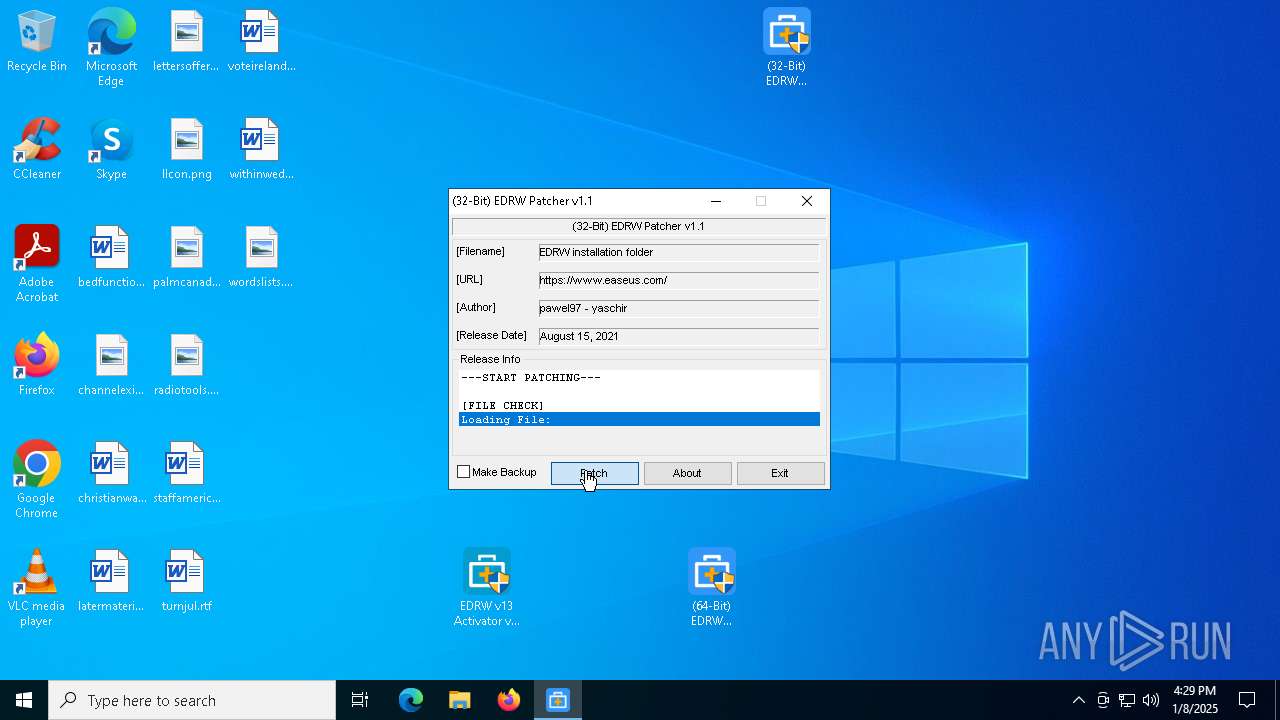
- (32-Bit) EDRW Patcher v1.1.exe (PID: 5156)
Reads security settings of Internet Explorer
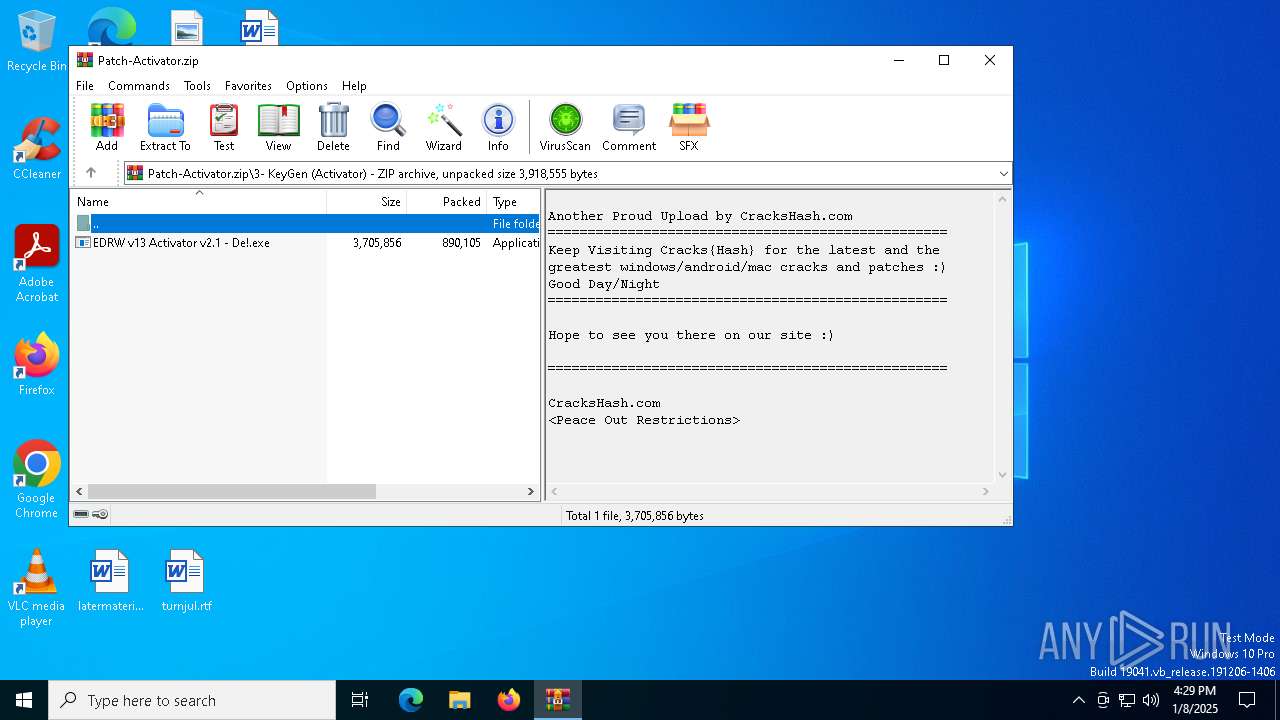
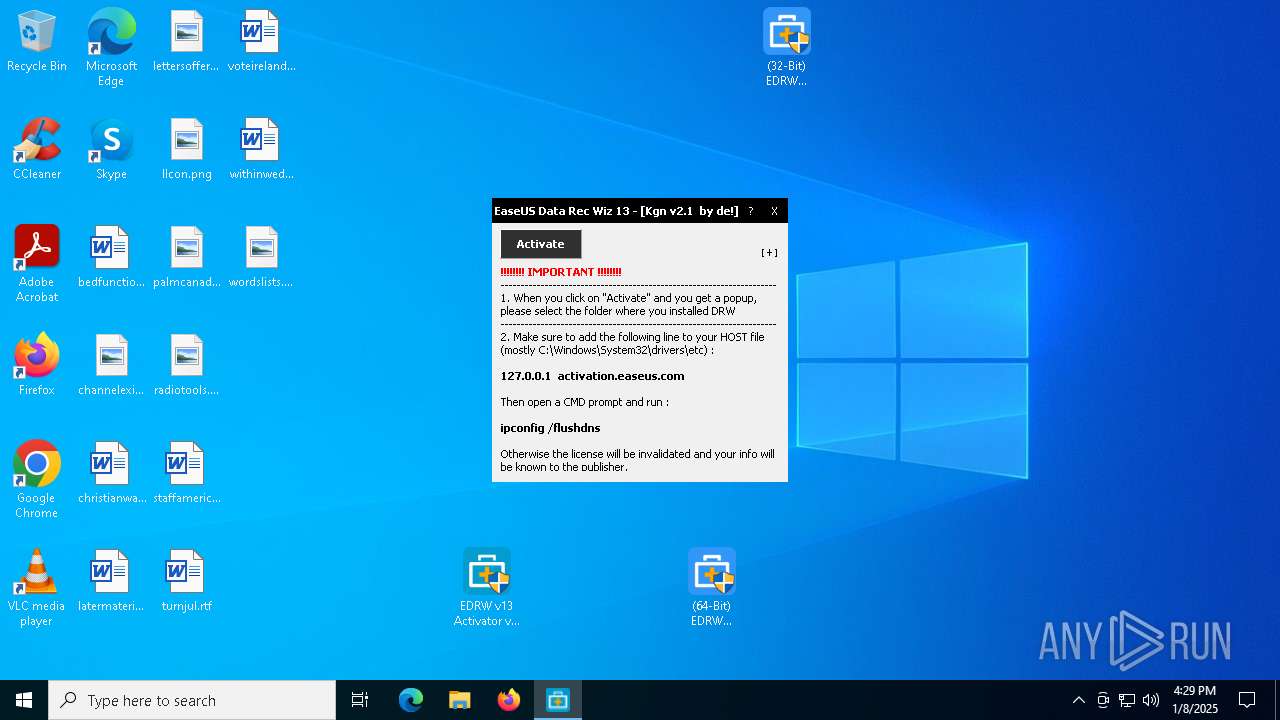
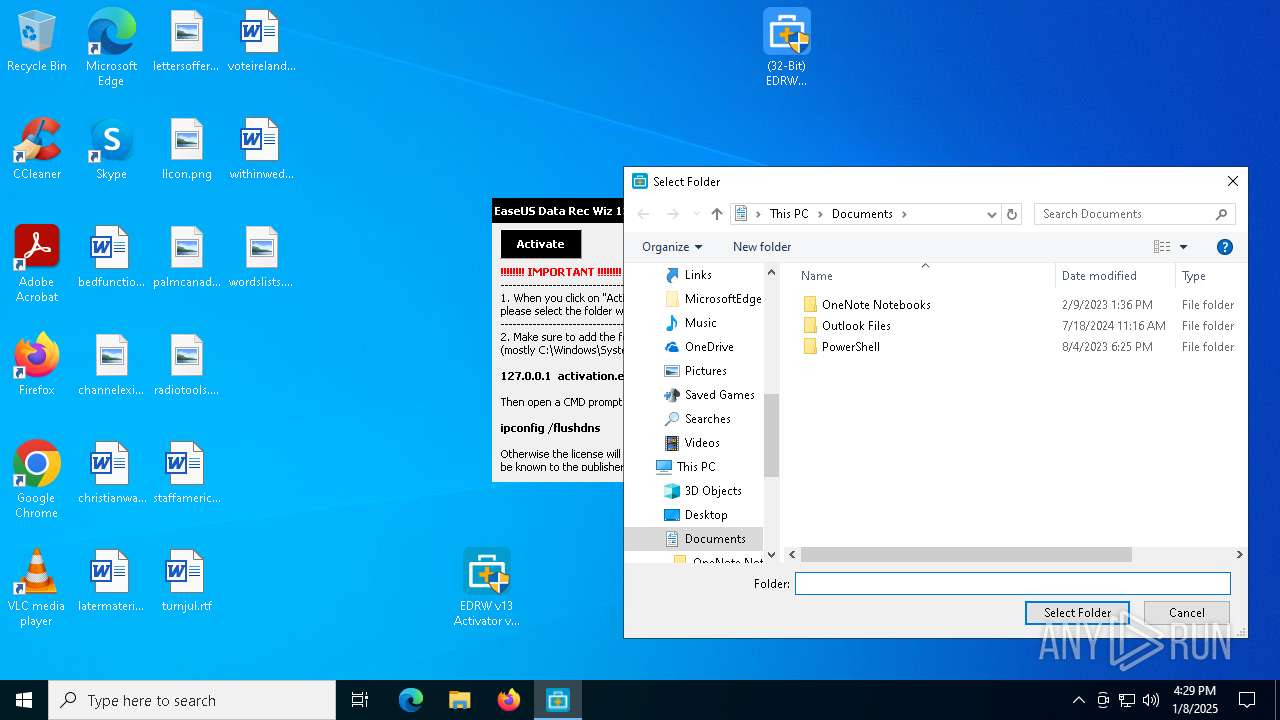
- EDRW v13 Activator v2.1 - De!.exe (PID: 836)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 6800)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6800)
- WinRAR.exe (PID: 6420)
The process uses the downloaded file
- WinRAR.exe (PID: 6420)
- WinRAR.exe (PID: 6800)
Manual execution by a user
- (32-Bit) EDRW Patcher v1.1.exe (PID: 6404)
- EDRW v13 Activator v2.1 - De!.exe (PID: 836)
- (32-Bit) EDRW Patcher v1.1.exe (PID: 5156)
- EDRW v13 Activator v2.1 - De!.exe (PID: 1512)
Create files in a temporary directory
- (32-Bit) EDRW Patcher v1.1.exe (PID: 5156)
Reads the computer name
- EDRW v13 Activator v2.1 - De!.exe (PID: 836)
Checks supported languages
- EDRW v13 Activator v2.1 - De!.exe (PID: 836)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2022:03:17 11:02:20 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
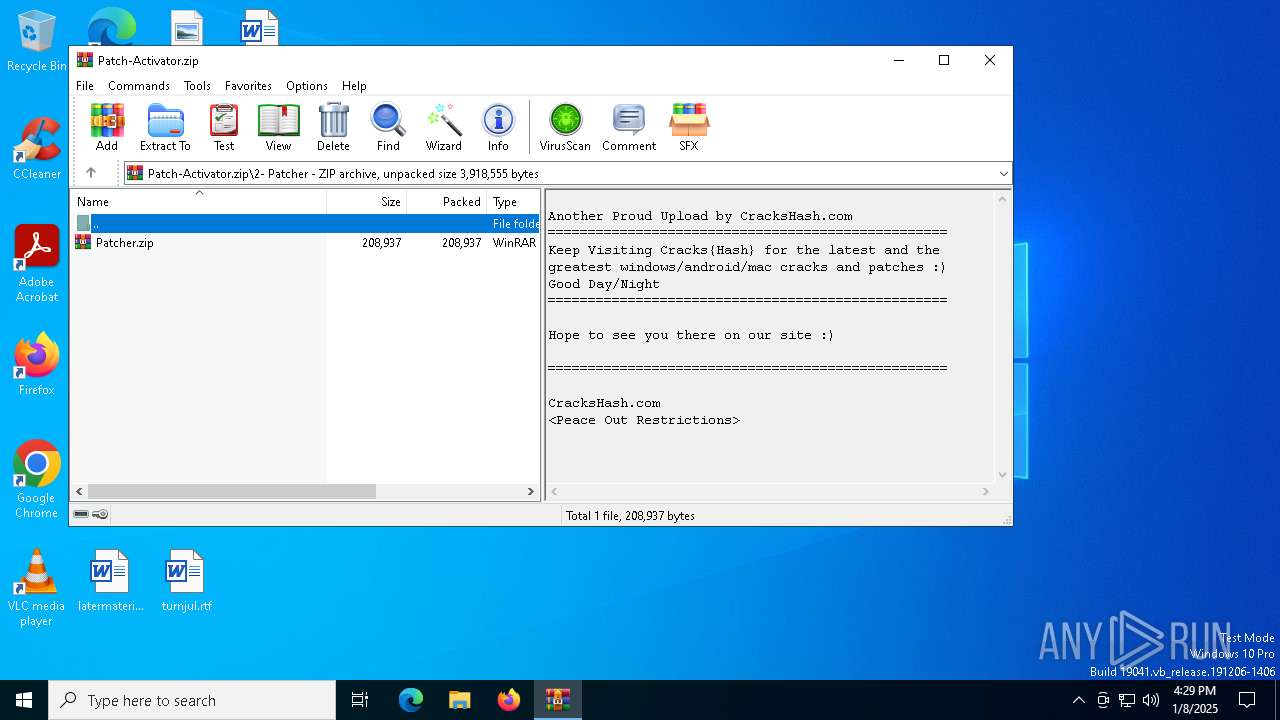
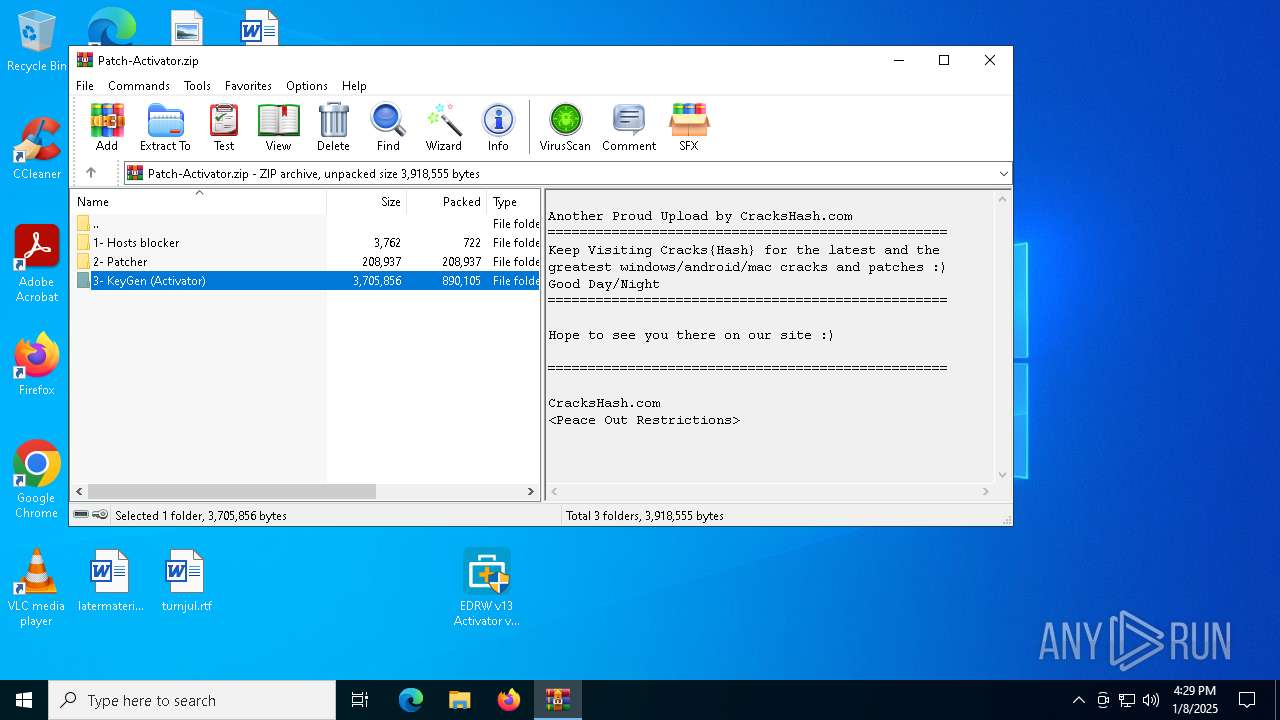
| ZipFileName: | 2- Patcher/ |
Total processes
129
Monitored processes
6
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 836 | "C:\Users\admin\Desktop\EDRW v13 Activator v2.1 - De!.exe" | C:\Users\admin\Desktop\EDRW v13 Activator v2.1 - De!.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: EaseUS_DRW Exit code: 0 Version: 2.0.0.0 Modules
| |||||||||||||||
| 1512 | "C:\Users\admin\Desktop\EDRW v13 Activator v2.1 - De!.exe" | C:\Users\admin\Desktop\EDRW v13 Activator v2.1 - De!.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: EaseUS_DRW Exit code: 3221226540 Version: 2.0.0.0 Modules
| |||||||||||||||
| 5156 | "C:\Users\admin\Desktop\(32-Bit) EDRW Patcher v1.1.exe" | C:\Users\admin\Desktop\(32-Bit) EDRW Patcher v1.1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 6404 | "C:\Users\admin\Desktop\(32-Bit) EDRW Patcher v1.1.exe" | C:\Users\admin\Desktop\(32-Bit) EDRW Patcher v1.1.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6420 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa6800.6557\ Patcher.zip" | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6800 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Patch-Activator.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
7 386
Read events
7 315
Write events
70
Delete events
1
Modification events
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Patch-Activator.zip | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
Executable files
4
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6800 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6800.5812\3- KeyGen (Activator)\EDRW v13 Activator v2.1 - De!.exe | executable | |
MD5:284182F0388FE891ED6B6A1DA5B4196E | SHA256:10BADD3B49C88AC87CE720C47CCD79F0DB4F8125D63B52D328E554FB549C44A8 | |||
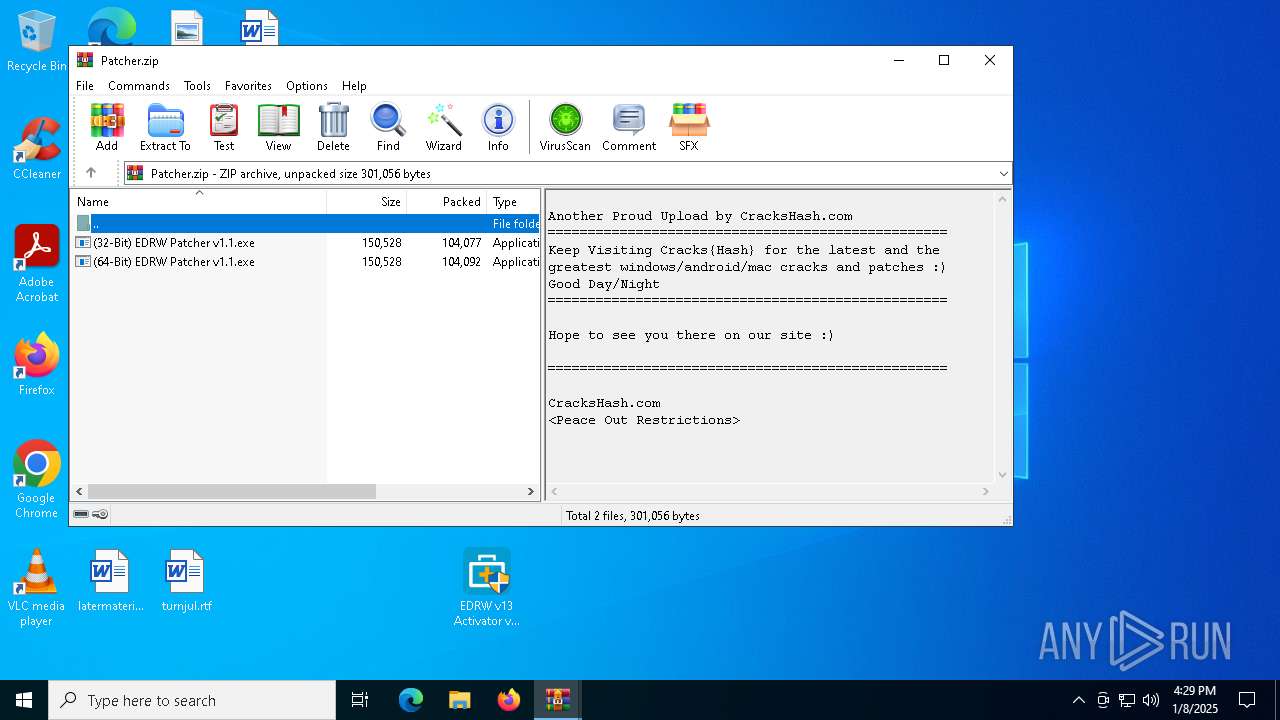
| 6420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6420.7262\(64-Bit) EDRW Patcher v1.1.exe | executable | |
MD5:087406E501B283F538D66C98B7EA1991 | SHA256:04491956A8B8993E031D632304FF57667BC4C77885DA153E75454FF2E25DBC1D | |||
| 6420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6420.7262\(32-Bit) EDRW Patcher v1.1.exe | executable | |
MD5:D0D44869D0B87FD8E960951687417CC9 | SHA256:8A66E54EB6A022EEB9063BF8182D3D1DEE11AA6990742E25CCD64CC5B7DBE3B0 | |||
| 5156 | (32-Bit) EDRW Patcher v1.1.exe | C:\Users\admin\AppData\Local\Temp\dup2patcher.dll | executable | |
MD5:4D9AB4032AFF2644CE0D1E54D3DE1D7D | SHA256:F9585DE5B2442E841FABB7F4A61DFAFE28849FBECE57A372A9110137ECC4A6F8 | |||
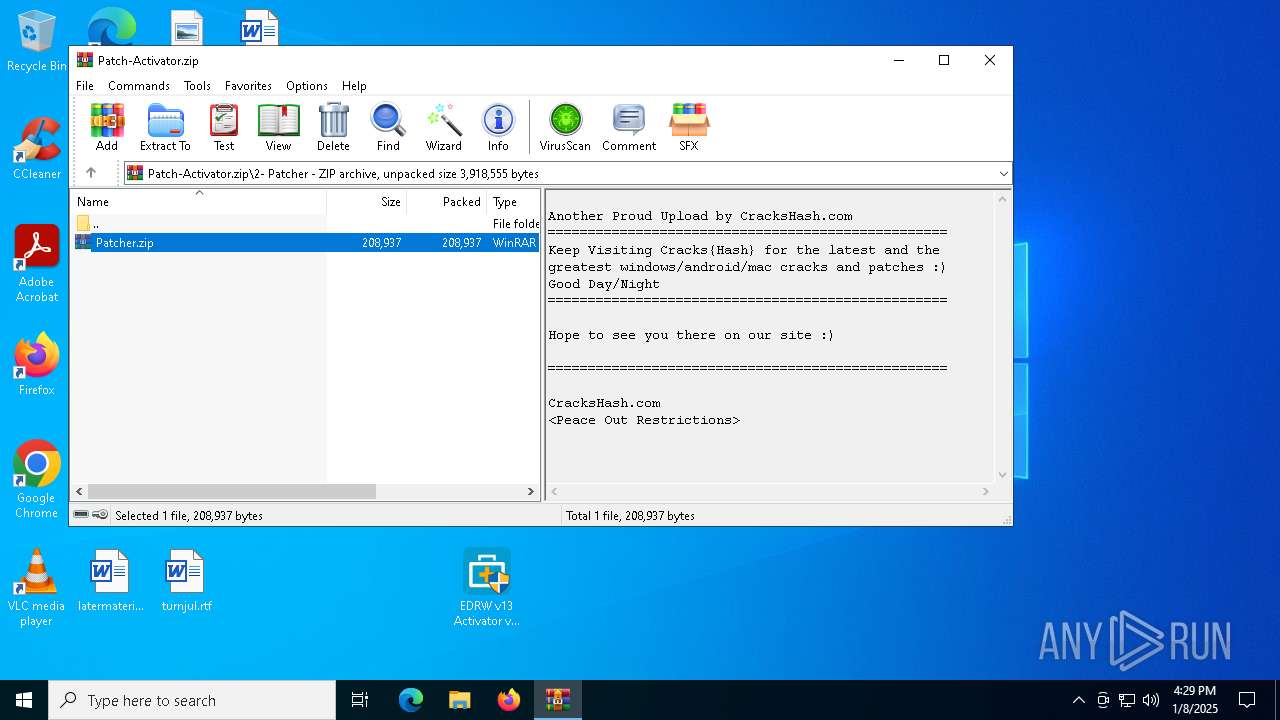
| 6800 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6800.6557\ Patcher.zip | compressed | |
MD5:3A94D10DD4CE5A2E054EA0B2544D357D | SHA256:192C9DA5366A7230982909C8891183B1F9C313E324DE9FDBA9A2F340CC25E45A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
22
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6520 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2940 | SIHClient.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | SIHClient.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.229.221.95:80 | — | EDGECAST | US | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1076 | svchost.exe | 23.56.254.14:443 | go.microsoft.com | Mobile Telecommunications Company | KW | whitelisted |
1356 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6520 | backgroundTaskHost.exe | 20.103.156.88:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6520 | backgroundTaskHost.exe | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
2940 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |