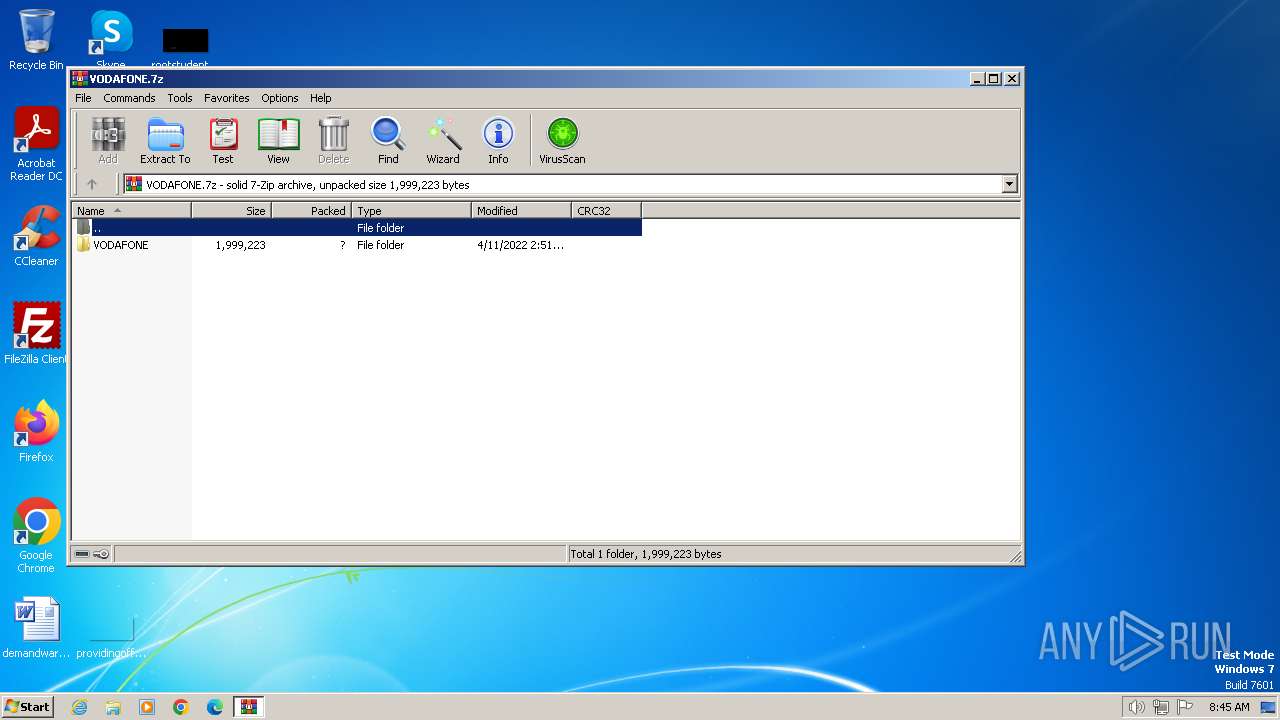
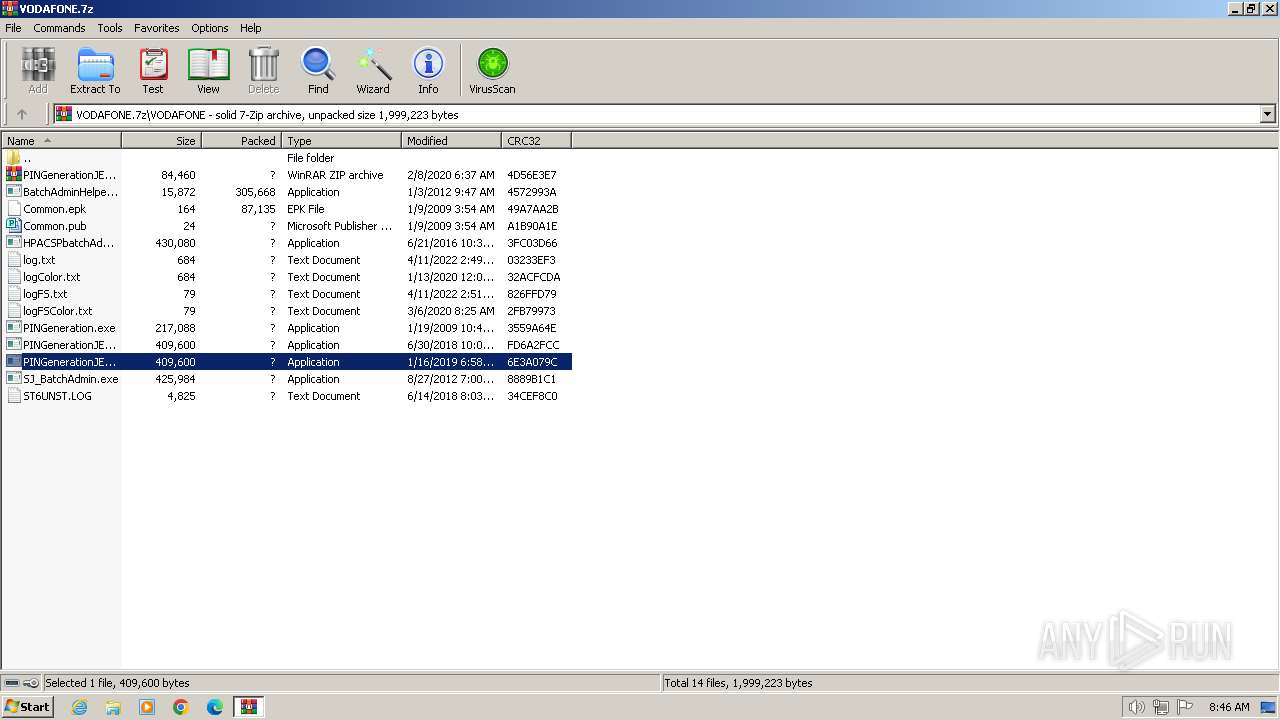
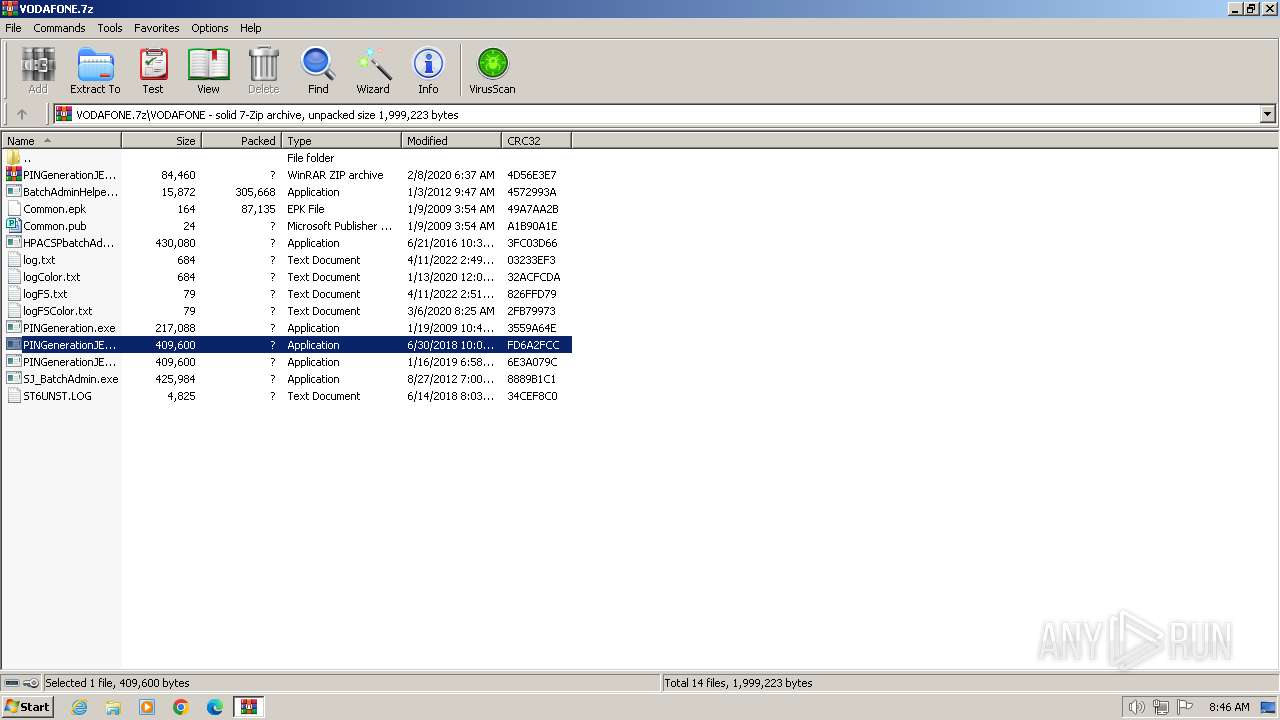
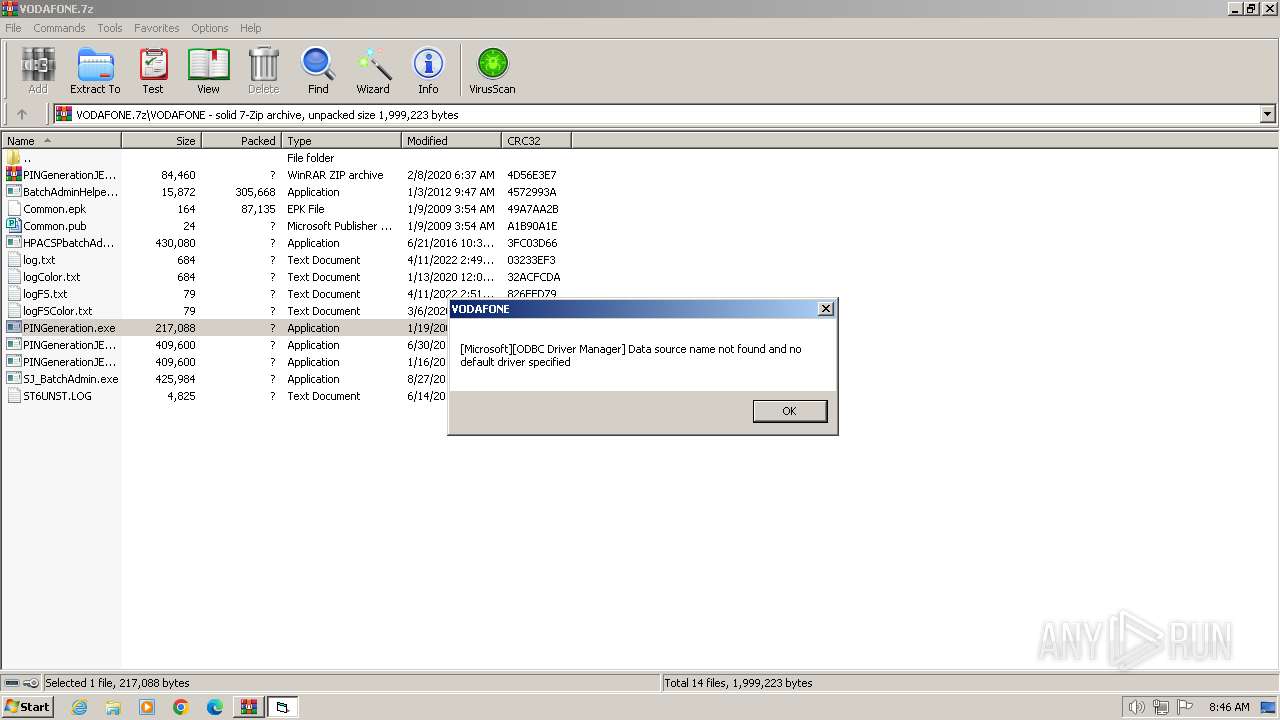
| File name: | VODAFONE.7z |
| Full analysis: | https://app.any.run/tasks/fe55f931-c809-41a0-989a-ed4a5123f83d |
| Verdict: | Malicious activity |
| Analysis date: | February 07, 2024, 08:45:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 2CC1B77D23A4BFA9FE50F296B51DD85F |
| SHA1: | 48AB895F068618AD203F18A6C21B88D00D268A04 |
| SHA256: | BBD956893842500BAE34261DC8E160EA5966CD6EDA91A574AD6D9883DED89733 |
| SSDEEP: | 12288:6UeDQ7xSBgRjYvtQ+9A8ZNlhNj5PrVzYHfrVMzfUJs6V94e8nxjE0:koxSBgRjYvtV9AuNlhNjp6/rKzfUSU9Q |
MALICIOUS
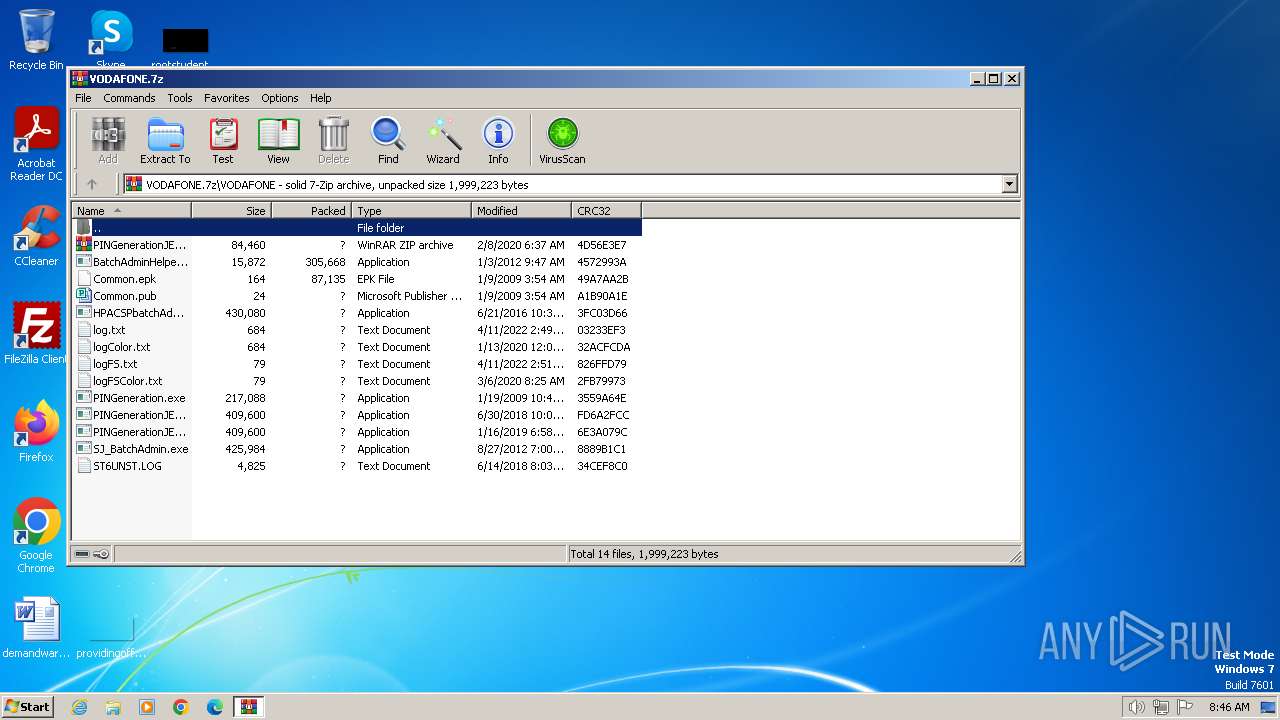
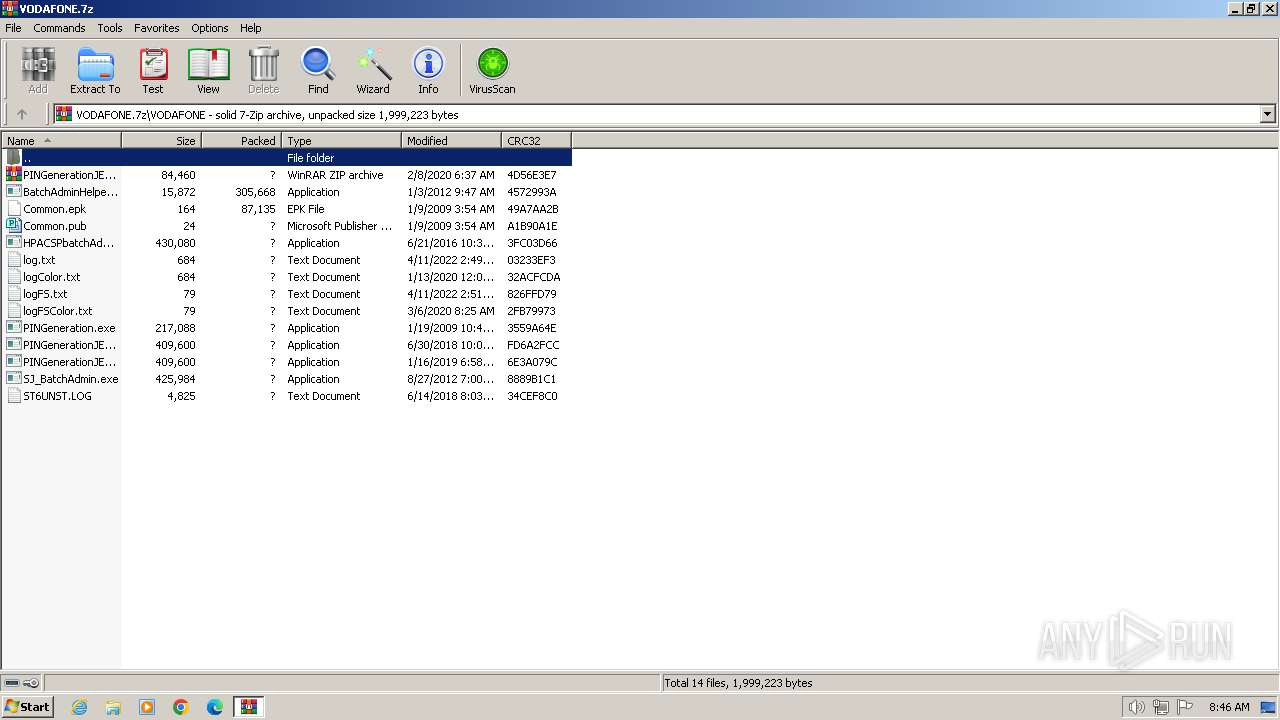
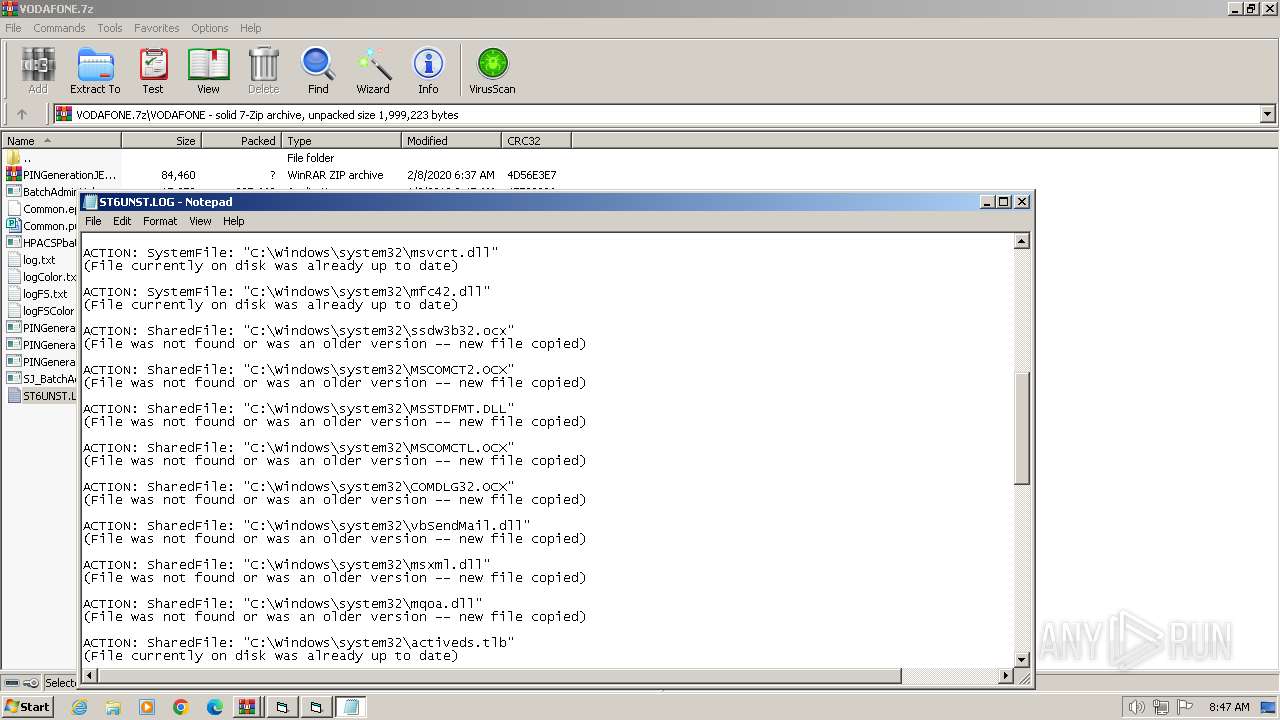
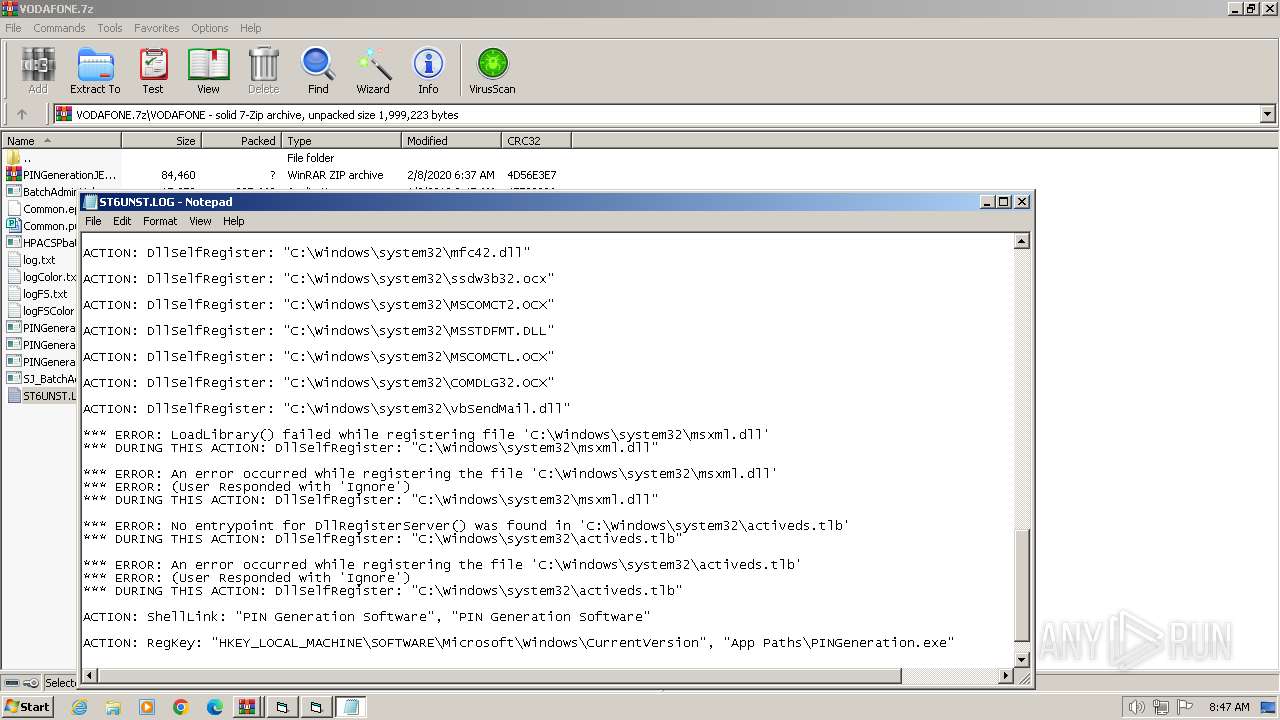
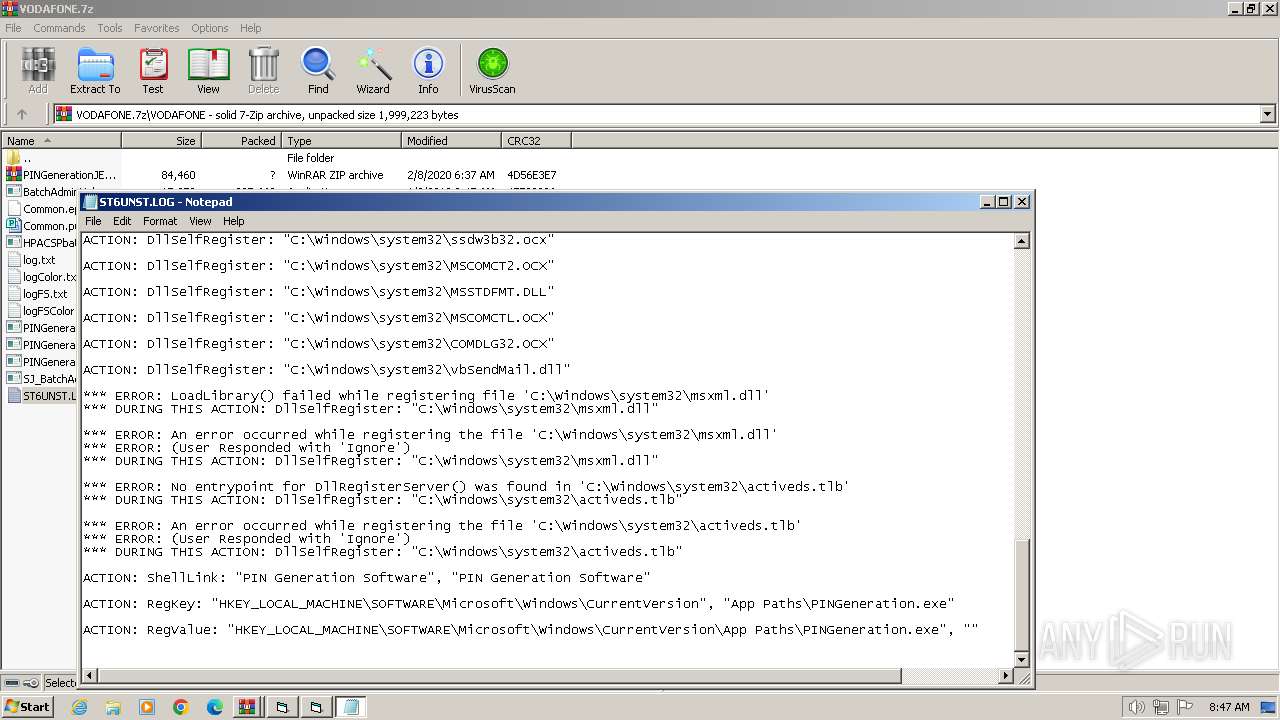
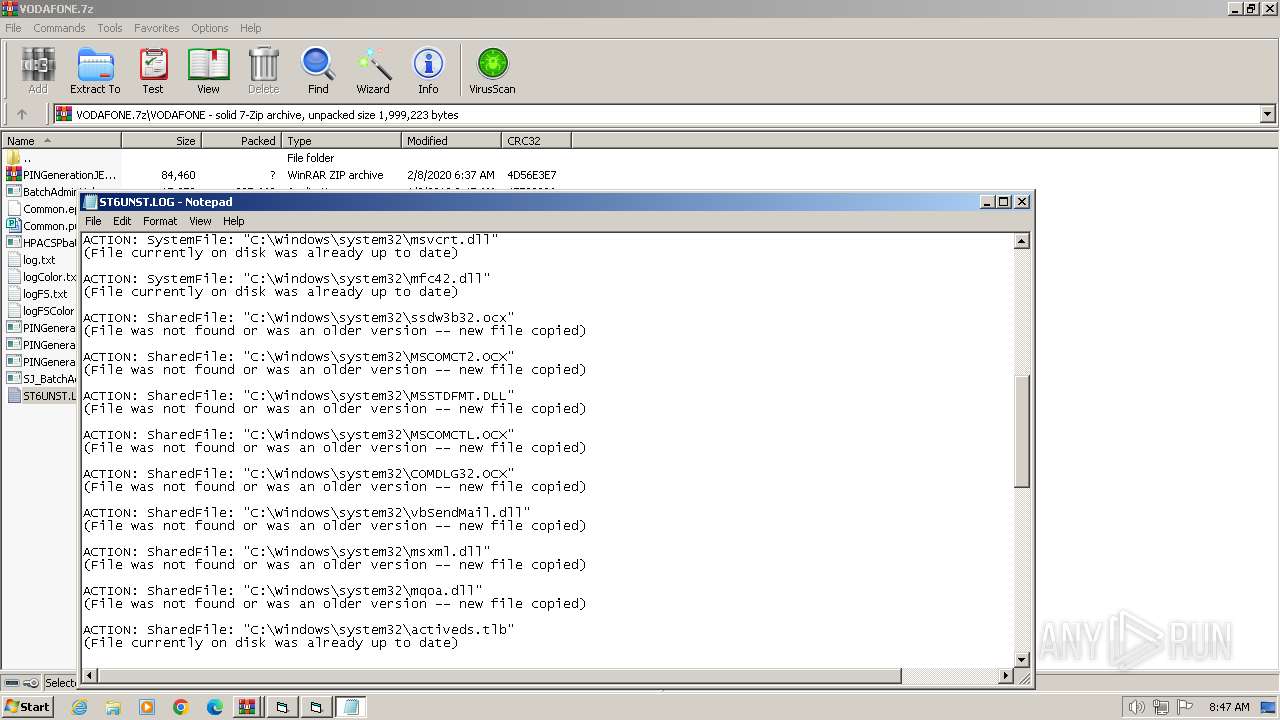
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1392)
SUSPICIOUS
Connects to unusual port
- PINGenerationJEDI_30June2018.exe (PID: 2556)
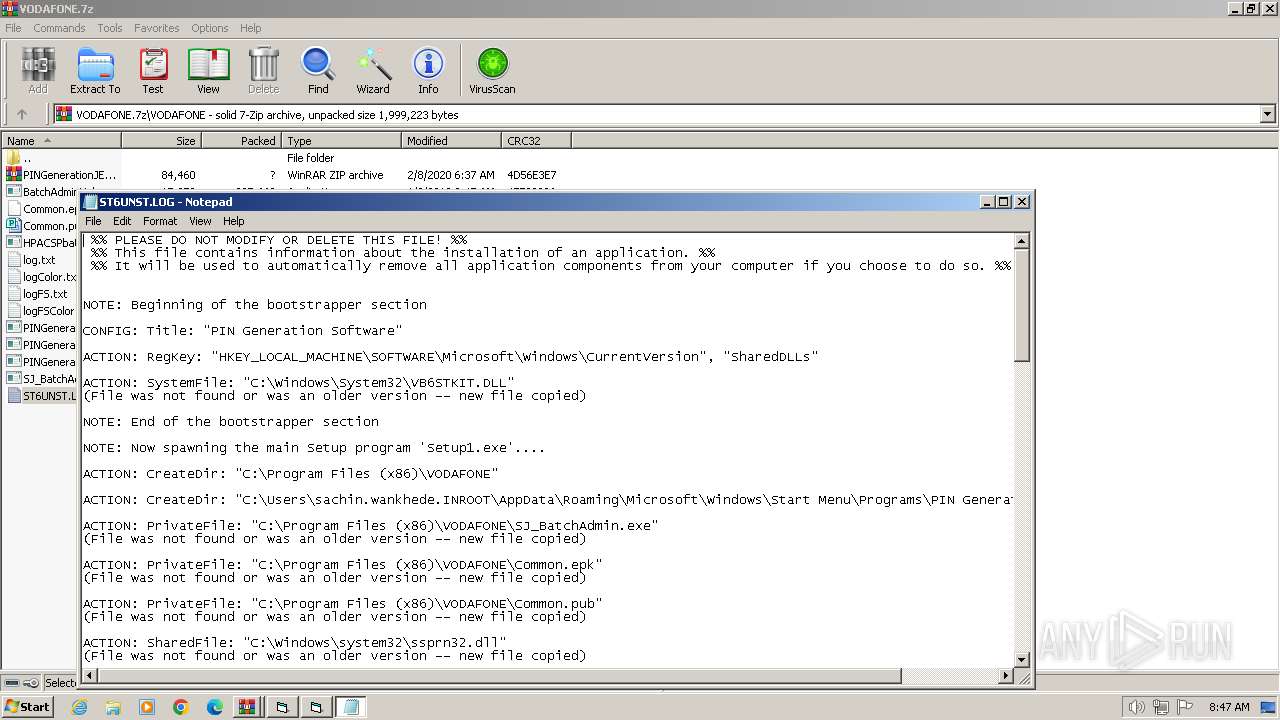
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 1392)
Searches for installed software
- MSPUB.EXE (PID: 3580)
Application launched itself
- WinRAR.exe (PID: 1392)
INFO
Reads the computer name
- PINGenerationJEDI_TLS.EXE (PID: 2032)
- PINGeneration.exe (PID: 3012)
- PINGenerationJEDI_30June2018.exe (PID: 2556)
- MSPUB.EXE (PID: 3580)
- wmpnscfg.exe (PID: 3740)
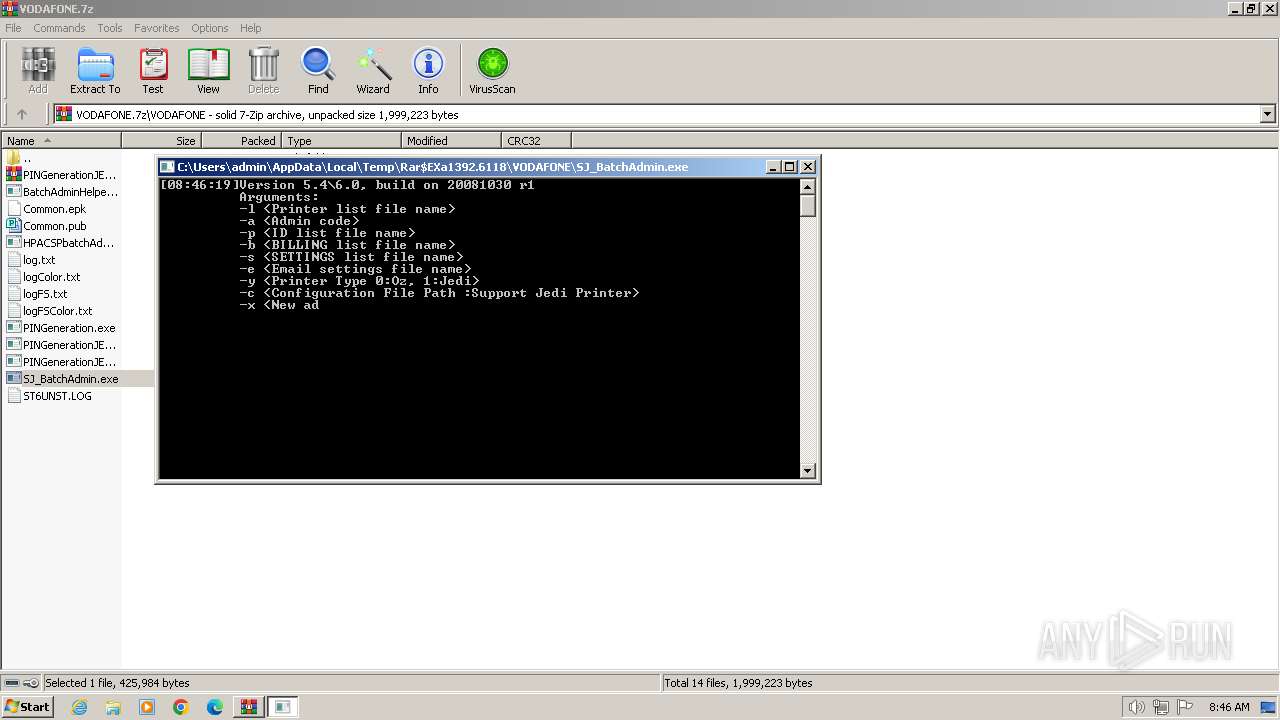
Checks supported languages
- SJ_BatchAdmin.exe (PID: 584)
- PINGenerationJEDI_TLS.EXE (PID: 2032)
- PINGenerationJEDI_30June2018.exe (PID: 2556)
- PINGeneration.exe (PID: 3012)
- MSPUB.EXE (PID: 3580)
- HPACSPbatchAdmin.exe (PID: 2764)
- BatchAdminHelper.exe (PID: 3644)
- wmpnscfg.exe (PID: 3740)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1392)
Reads the machine GUID from the registry
- PINGenerationJEDI_TLS.EXE (PID: 2032)
- PINGeneration.exe (PID: 3012)
- MSPUB.EXE (PID: 3580)
- PINGenerationJEDI_30June2018.exe (PID: 2556)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 1392)
- MSPUB.EXE (PID: 3580)
Reads Environment values
- MSPUB.EXE (PID: 3580)
Creates files or folders in the user directory
- MSPUB.EXE (PID: 3580)
Process checks computer location settings
- MSPUB.EXE (PID: 3580)
Manual execution by a user
- wmpnscfg.exe (PID: 3740)
Create files in a temporary directory
- MSPUB.EXE (PID: 3580)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
51
Monitored processes
13
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 584 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1392.6118\VODAFONE\SJ_BatchAdmin.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1392.6118\VODAFONE\SJ_BatchAdmin.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1392 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\VODAFONE.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2032 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1392.6306\VODAFONE\PINGenerationJEDI_TLS.EXE" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1392.6306\VODAFONE\PINGenerationJEDI_TLS.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Kaps IT Solutions Pvt. Ltd Integrity Level: MEDIUM Description: Version 1.0 Exit code: 0 Version: 8.00 Modules
| |||||||||||||||
| 2136 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa1392.12803\PINGenerationJEDI_TLS.zip | C:\Program Files\WinRAR\WinRAR.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2556 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1392.7185\VODAFONE\PINGenerationJEDI_30June2018.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1392.7185\VODAFONE\PINGenerationJEDI_30June2018.exe | WinRAR.exe | ||||||||||||
User: admin Company: Kaps IT Solutions Pvt. Ltd Integrity Level: MEDIUM Description: Version 1.0 Exit code: 0 Version: 7.00.0003 Modules
| |||||||||||||||
| 2764 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1392.8098\VODAFONE\HPACSPbatchAdmin.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1392.8098\VODAFONE\HPACSPbatchAdmin.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3012 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1392.7737\VODAFONE\PINGeneration.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1392.7737\VODAFONE\PINGeneration.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Kaps IT Solutions Pvt. Ltd Integrity Level: MEDIUM Description: Version 1.0 Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 3580 | "C:\Program Files\Microsoft Office\Office14\MSPUB.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa1392.8343\Common.pub | C:\Program Files\Microsoft Office\Office14\MSPUB.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Publisher Exit code: 0 Version: 14.0.6026.1000 Modules
| |||||||||||||||
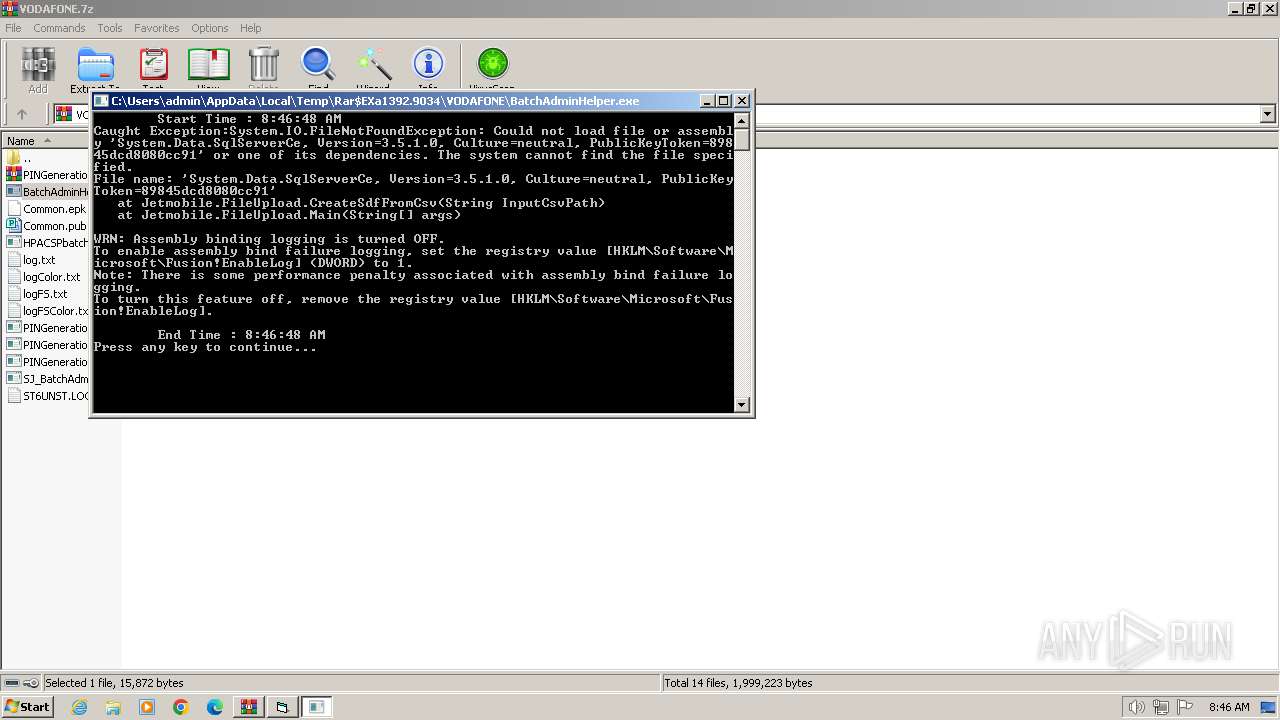
| 3644 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1392.9034\VODAFONE\BatchAdminHelper.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1392.9034\VODAFONE\BatchAdminHelper.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Intime Integrity Level: MEDIUM Description: BatchAdminHelper Exit code: 1 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3740 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 050
Read events
4 971
Write events
74
Delete events
5
Modification events
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
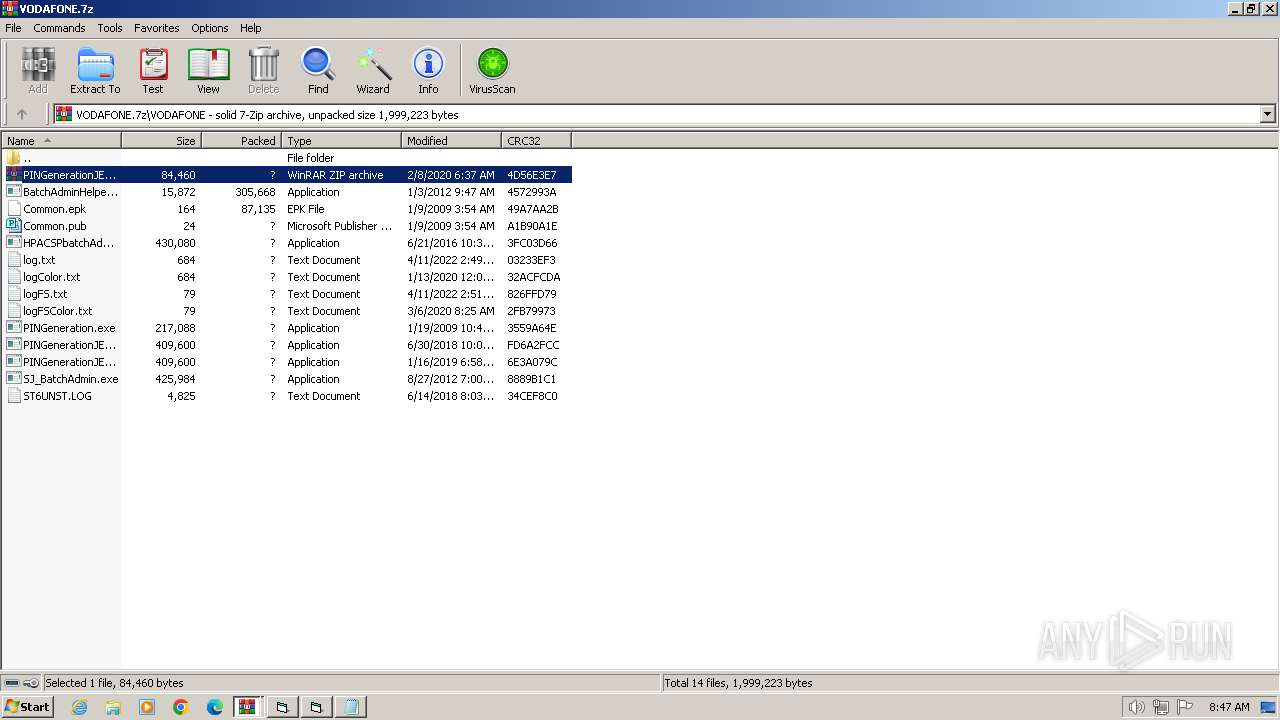
Executable files
36
Suspicious files
29
Text files
34
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1392.6118\VODAFONE\logFSColor.txt | text | |
MD5:CC4B4E23AE8C4338957D01B001E6B45F | SHA256:E30439F533A8F4A825D1D3A9D977EE122A9A2D3BDD0D2D5D2B0408D2D240BB51 | |||
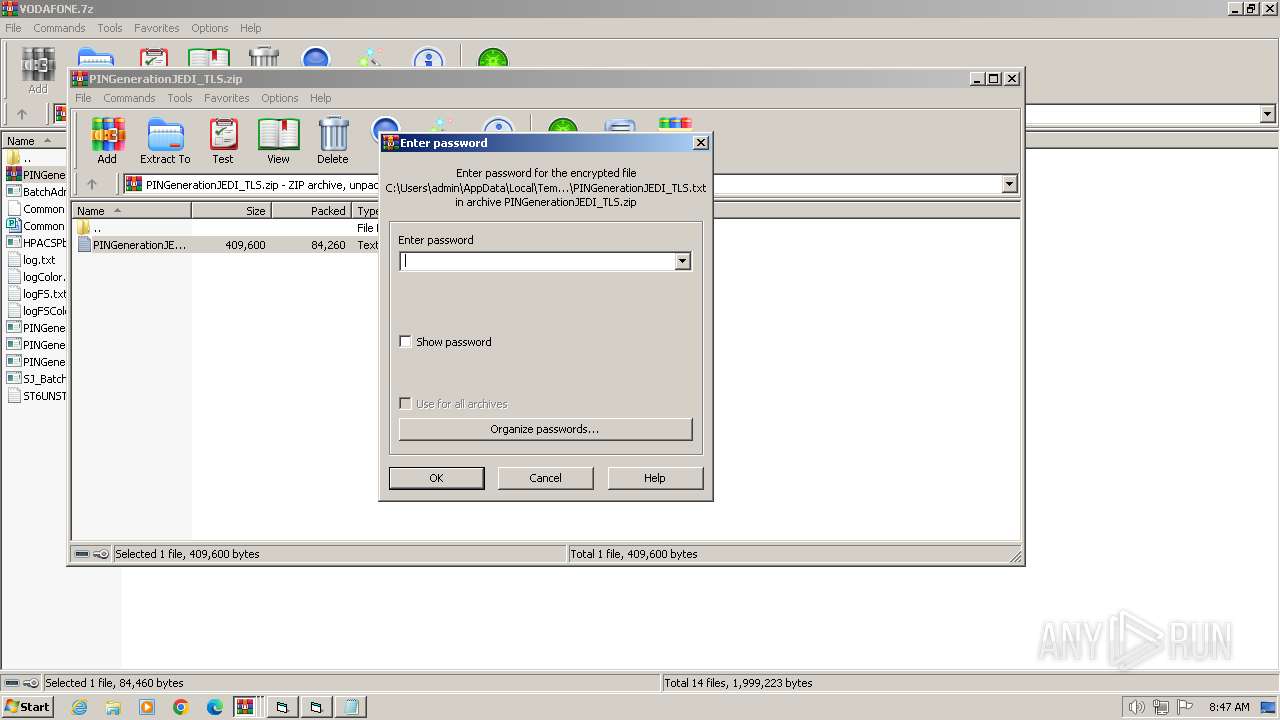
| 1392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1392.6118\VODAFONE\PINGenerationJEDI_TLS.zip | compressed | |
MD5:607CC0A493621CAA41DD3D4865D1EF7B | SHA256:B17A7F95B14FEF59D9B81DFAFBF50B07EE9EBA17DBFD37414FD55FE47C9EF609 | |||
| 1392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1392.6118\VODAFONE\BatchAdminHelper.exe | executable | |
MD5:2D4F9E79F70299CC954C863B246E649B | SHA256:93FF7F333E3AEFCD3A388DD2C1C7ED9F1C811BB9D830D3646894589DDF9808AF | |||
| 1392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1392.6118\VODAFONE\Common.pub | binary | |
MD5:9180B8EEA52F770160EC3B14B628E123 | SHA256:D2737498C9B66605F630B8C159882B4A230D9735302314809D2377882F726CA0 | |||
| 1392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1392.6118\VODAFONE\PINGenerationJEDI_30June2018.exe | executable | |
MD5:BFD6D795DD3ACA8C5D12797088B5092C | SHA256:794B6F7633746E89DD03B85ADB551AE62B1AF742930BE06FFC6A604CA8BA9953 | |||
| 1392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1392.6118\VODAFONE\PINGeneration.exe | executable | |
MD5:ABC148A85E7ACACC483FEFF9B81A96D9 | SHA256:D67A95FC0BAD2FA8620EB69974DC7EBE810A8036DE7601CB33D97AED875CD873 | |||
| 1392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1392.6118\VODAFONE\SJ_BatchAdmin.exe | executable | |
MD5:42EED41578F74B7E661A726D444A3D44 | SHA256:70C853F9AA528FF51CD9A68B4FC5FFF1BA127D36E428B0BD10C1C8A987DEFC9A | |||
| 1392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1392.6306\VODAFONE\Common.epk | binary | |
MD5:B362AFB15D0F551BD03EB15D6A81ACDE | SHA256:5CEEB110FED9967E23015CA87B9CAEEE3060BDFFDC3305EF14C6B48E27B402A1 | |||
| 1392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1392.6118\VODAFONE\HPACSPbatchAdmin.exe | executable | |
MD5:BE9DA637F1C76B02740CBA4A40504D04 | SHA256:03E46D0F2A56A545B5B758759E34FE21FF6C68CD2A98C87E2035D9BB9B339C17 | |||
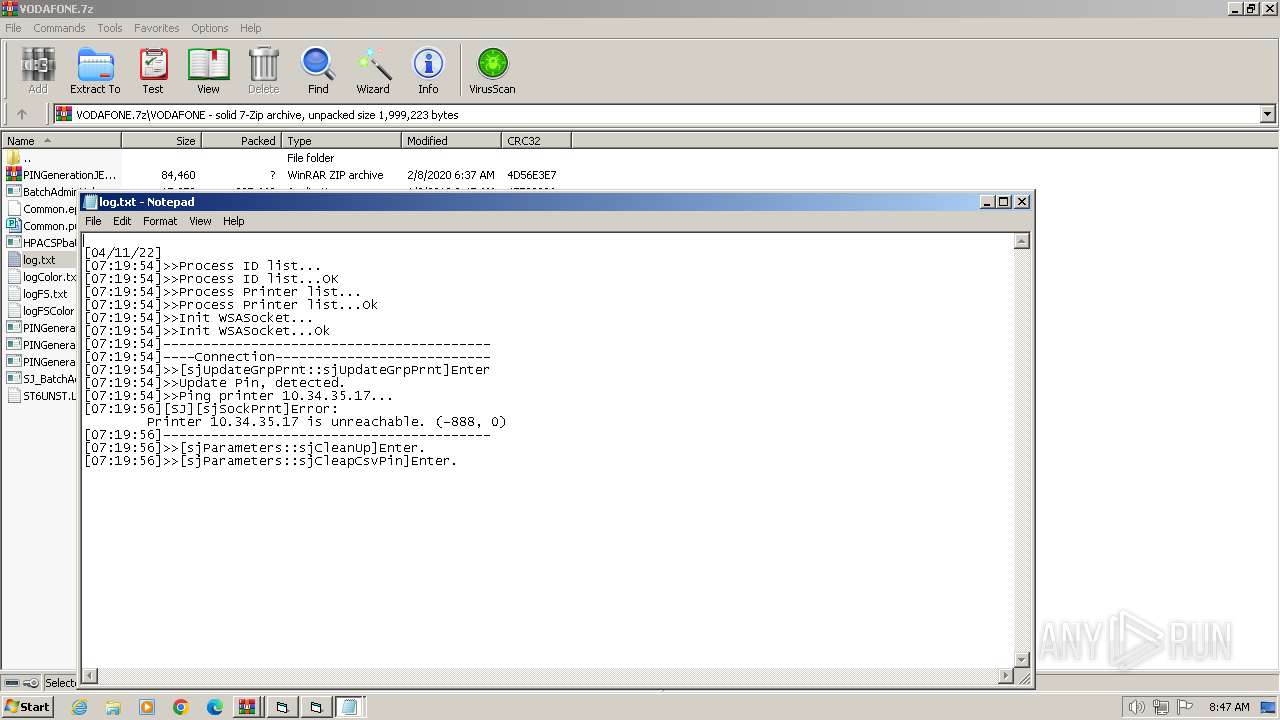
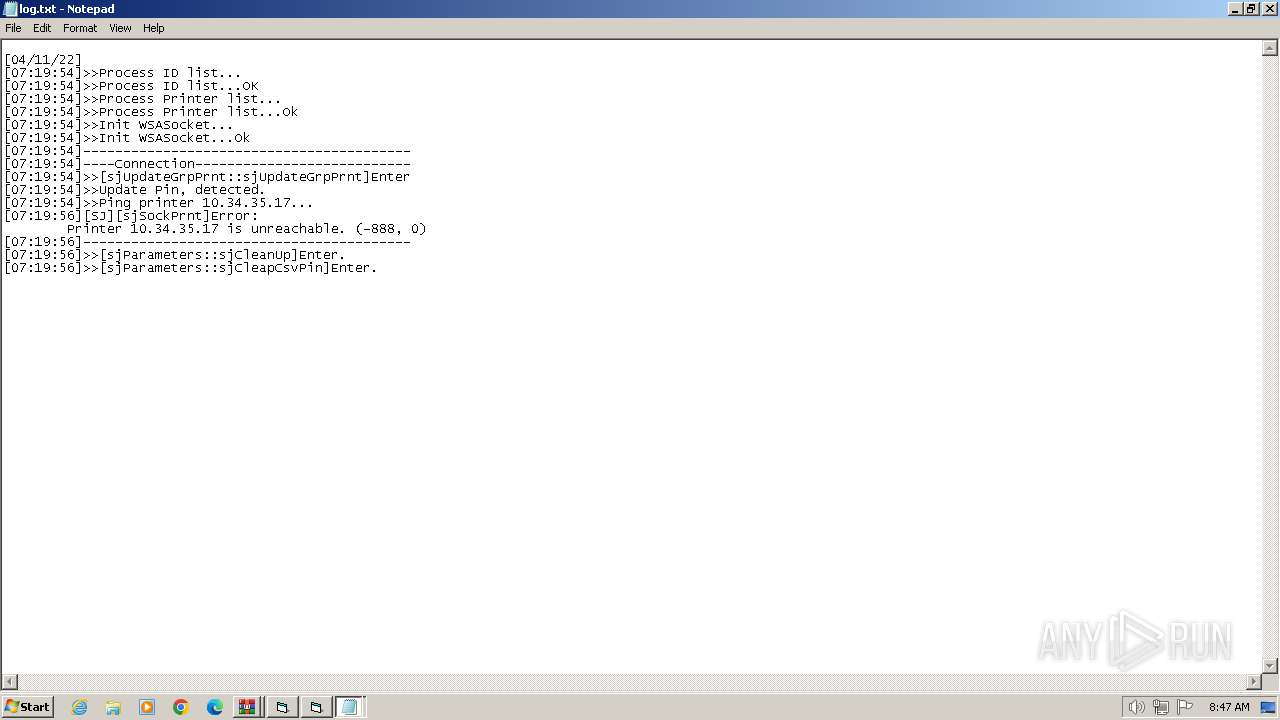
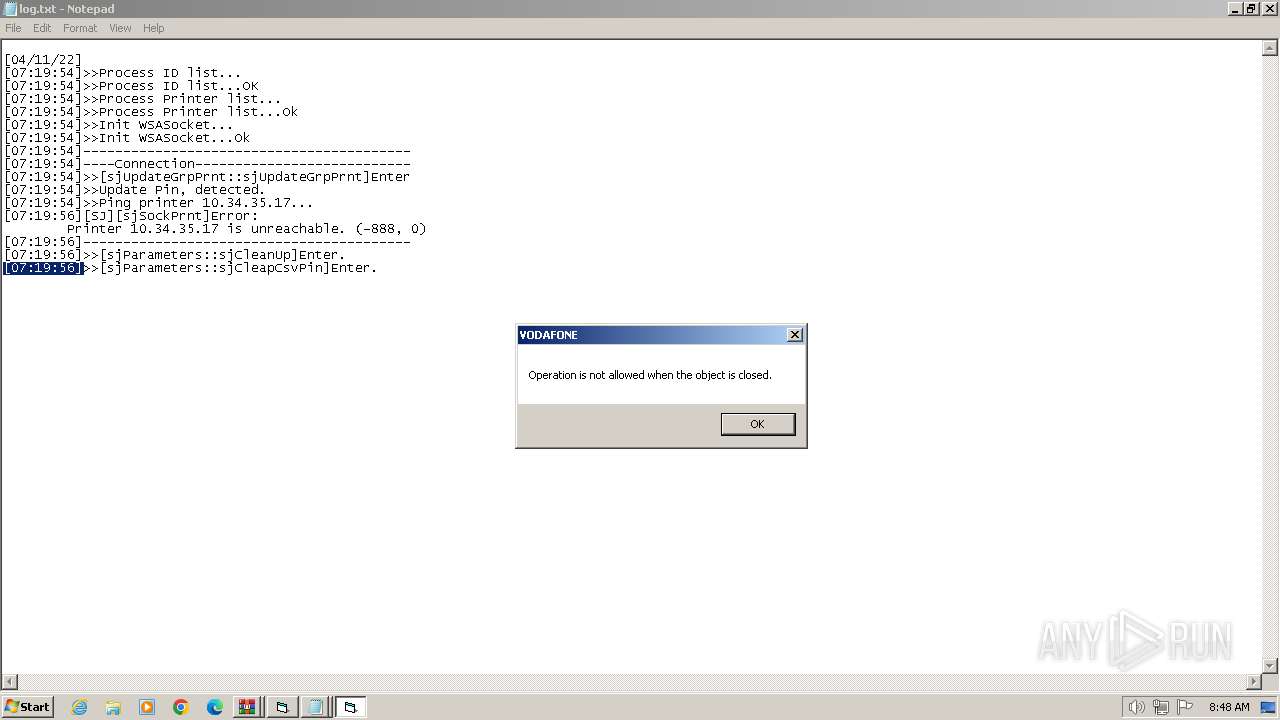
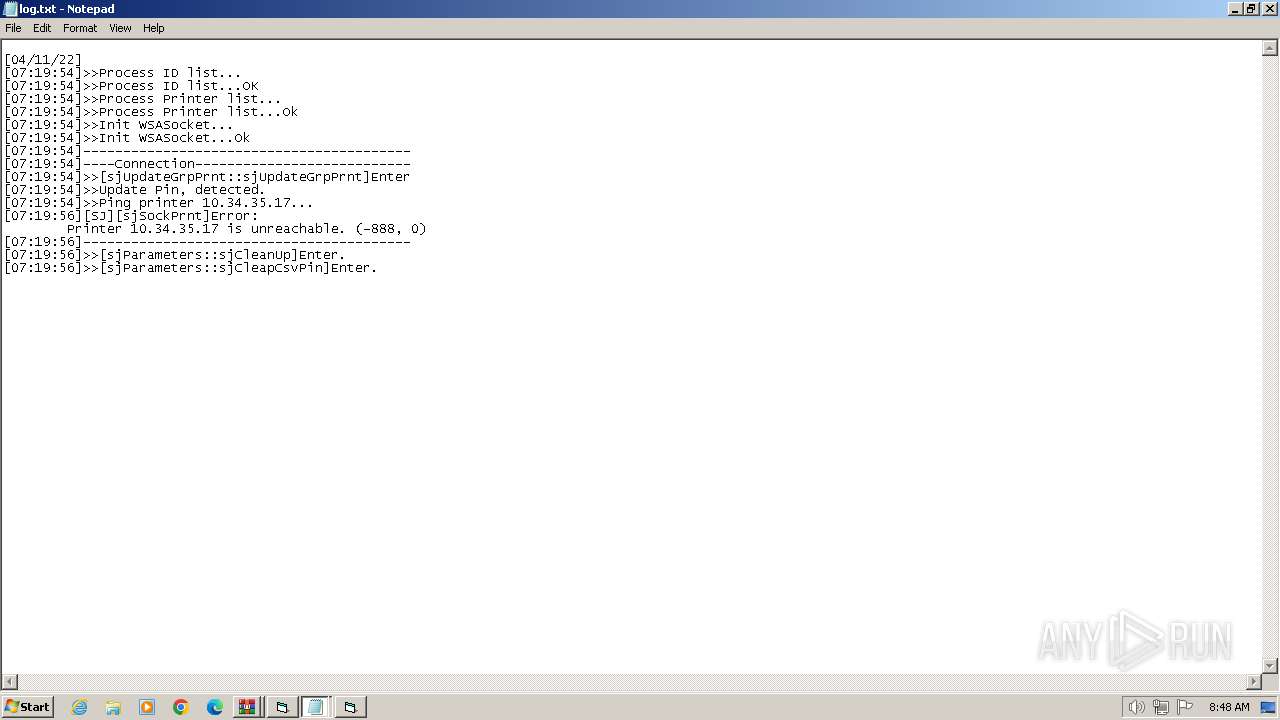
| 1392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1392.6306\VODAFONE\log.txt | text | |
MD5:EB076D12F7C362958C381D1ED3A87C7D | SHA256:067CC7B30CE282F3C6242FC40E67324101A5FFAFFD89C2093C179269F86B52A5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
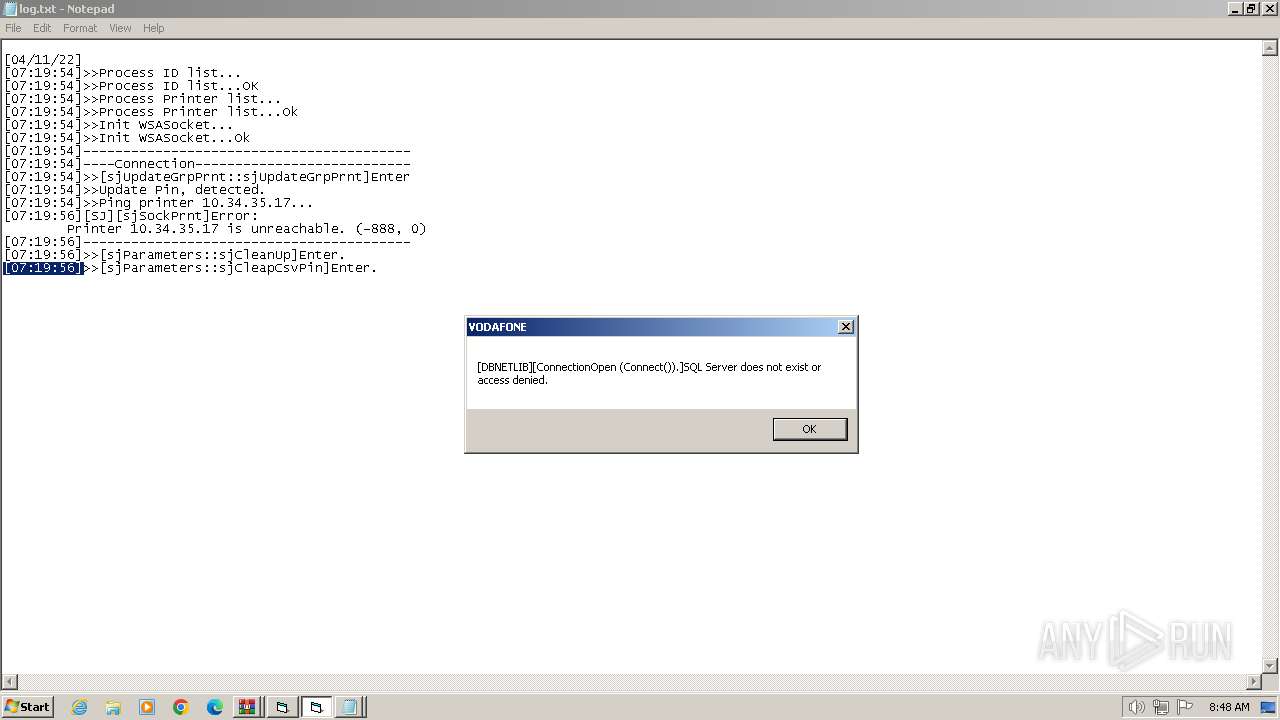
2556 | PINGenerationJEDI_30June2018.exe | 10.94.105.183:1433 | — | — | — | unknown |