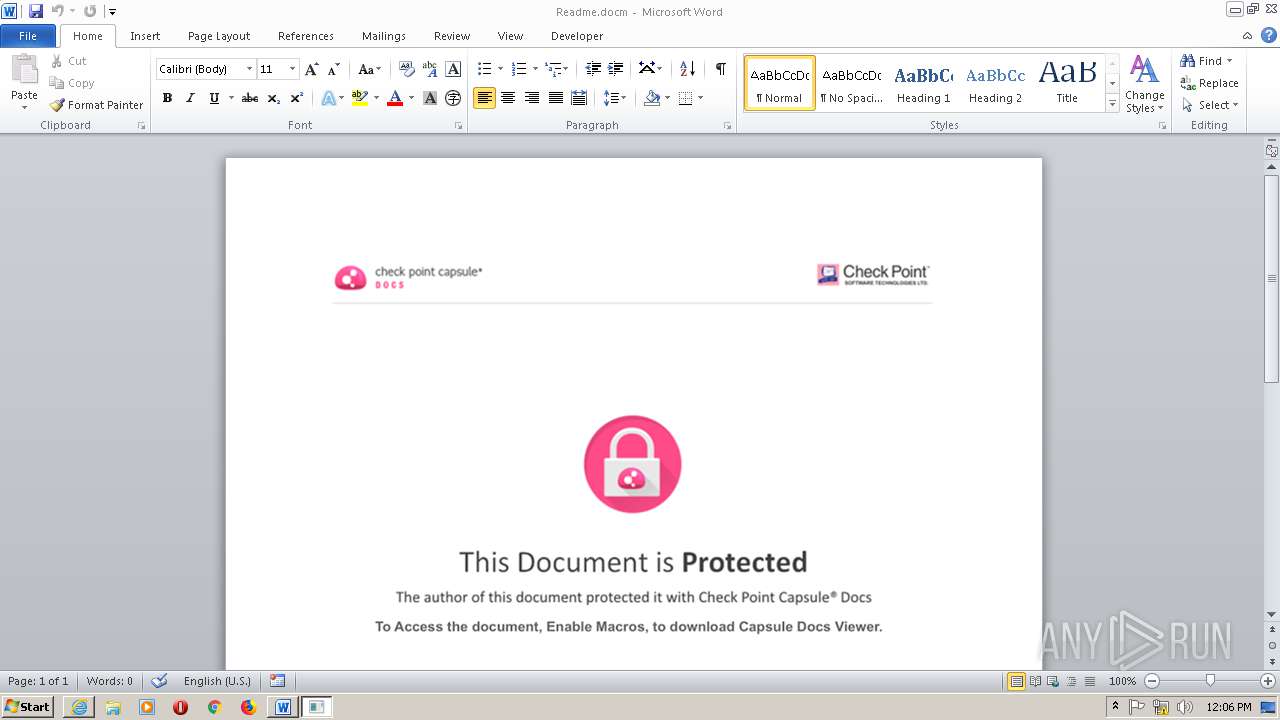
| File name: | Readme.docm |
| Full analysis: | https://app.any.run/tasks/5106658d-2b8d-483f-a46d-43675af81078 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | January 29, 2020, 12:03:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 0729C3C9390DD4A1C8FCD62E2A6D5B9D |
| SHA1: | 0877D65353D6FBF7E4077D333DEC99D1F6B206B2 |
| SHA256: | BBCBCF0F04CF0178A3E1B34AC35771BD3928420A7D835675BEE8BA3D04BEB3E5 |
| SSDEEP: | 6144:eLFMRO4KXYr0I2RJMypOdV7/bhdA9TbbxioBJYobdtv9BP+FFFFFFFFFFFFa9:eFEO4KXbI0qyUdp/bhdA9l7Sobdtv9Z9 |
MALICIOUS
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 564)
Application was dropped or rewritten from another process
- capsule.exe (PID: 1780)
- capsule.exe (PID: 2804)
- CPDS.exe (PID: 2412)
- capsule.exe (PID: 2240)
- Setup.exe (PID: 192)
- vstor_redist.exe (PID: 2020)
- vstor40_x64.exe (PID: 2100)
- install.exe (PID: 2428)
- FilesInUse.exe (PID: 3356)
- Install.exe (PID: 2616)
- Launcher.exe (PID: 2344)
- vc90sp1redist_x86.exe (PID: 2388)
- install.exe (PID: 3032)
- vc110redist_x86.exe (PID: 776)
- vc110redist_x86.exe (PID: 2572)
- vc120redist_x86.exe (PID: 3028)
- vc120redist_x86.exe (PID: 2936)
- FilesInUse.exe (PID: 3364)
- FilesInUse.exe (PID: 3372)
Requests a remote executable file from MS Office
- WINWORD.EXE (PID: 564)
Downloads executable files from IP
- WINWORD.EXE (PID: 564)
Changes the autorun value in the registry
- CPDS.exe (PID: 2412)
- rundll32.exe (PID: 1192)
- Install.exe (PID: 2616)
- vc110redist_x86.exe (PID: 776)
UAC/LUA settings modification
- rundll32.exe (PID: 1192)
Loads dropped or rewritten executable
- rundll32.exe (PID: 1192)
- Setup.exe (PID: 192)
- install.exe (PID: 2428)
- FilesInUse.exe (PID: 3356)
- rundll32.exe (PID: 1184)
- install.exe (PID: 3032)
- vc110redist_x86.exe (PID: 2572)
- vc120redist_x86.exe (PID: 2936)
- FilesInUse.exe (PID: 3372)
- FilesInUse.exe (PID: 3364)
- lmclientconsole.exe (PID: 3852)
Loads the Task Scheduler COM API
- ngen.exe (PID: 3280)
- ngen.exe (PID: 4004)
- ngen.exe (PID: 3100)
- ngen.exe (PID: 3600)
- ngen.exe (PID: 4060)
- ngen.exe (PID: 3444)
- ngen.exe (PID: 3848)
- ngen.exe (PID: 4064)
- ngen.exe (PID: 2524)
- ngen.exe (PID: 3932)
- ngen.exe (PID: 3324)
- ngen.exe (PID: 3568)
- ngen.exe (PID: 3620)
- ngen.exe (PID: 3088)
- ngen.exe (PID: 3140)
- ngen.exe (PID: 3204)
- ngen.exe (PID: 3408)
- ngen.exe (PID: 3572)
- ngen.exe (PID: 3864)
- ngen.exe (PID: 3076)
- ngen.exe (PID: 3356)
- ngen.exe (PID: 3584)
- ngen.exe (PID: 3856)
- ngen.exe (PID: 3500)
- ngen.exe (PID: 3776)
- ngen.exe (PID: 3564)
- ngen.exe (PID: 3148)
- ngen.exe (PID: 3460)
- ngen.exe (PID: 3772)
- ngen.exe (PID: 2308)
- ngen.exe (PID: 3716)
- ngen.exe (PID: 3648)
- ngen.exe (PID: 3500)
- ngen.exe (PID: 3912)
Changes settings of System certificates
- Launcher.exe (PID: 2344)
SUSPICIOUS
Creates files in the Windows directory
- capsule.exe (PID: 2804)
- msiexec.exe (PID: 2680)
- ngen.exe (PID: 3280)
- ngen.exe (PID: 4004)
- ngen.exe (PID: 3444)
- ngen.exe (PID: 3600)
- ngen.exe (PID: 4060)
- ngen.exe (PID: 3848)
- ngen.exe (PID: 3100)
- ngen.exe (PID: 2524)
- ngen.exe (PID: 4064)
- ngen.exe (PID: 3324)
- ngen.exe (PID: 3932)
- ngen.exe (PID: 3620)
- ngen.exe (PID: 3568)
- ngen.exe (PID: 3088)
- ngen.exe (PID: 3912)
- ngen.exe (PID: 3572)
- ngen.exe (PID: 3408)
- ngen.exe (PID: 3076)
- ngen.exe (PID: 3864)
- ngen.exe (PID: 3856)
- ngen.exe (PID: 3500)
- ngen.exe (PID: 3356)
- ngen.exe (PID: 3584)
- ngen.exe (PID: 3776)
- ngen.exe (PID: 3564)
- ngen.exe (PID: 3460)
- ngen.exe (PID: 2308)
- ngen.exe (PID: 3148)
- ngen.exe (PID: 3772)
- ngen.exe (PID: 3716)
- ngen.exe (PID: 3648)
- ngen.exe (PID: 3500)
- mscorsvw.exe (PID: 3996)
- ngen.exe (PID: 3204)
- ngen.exe (PID: 3140)
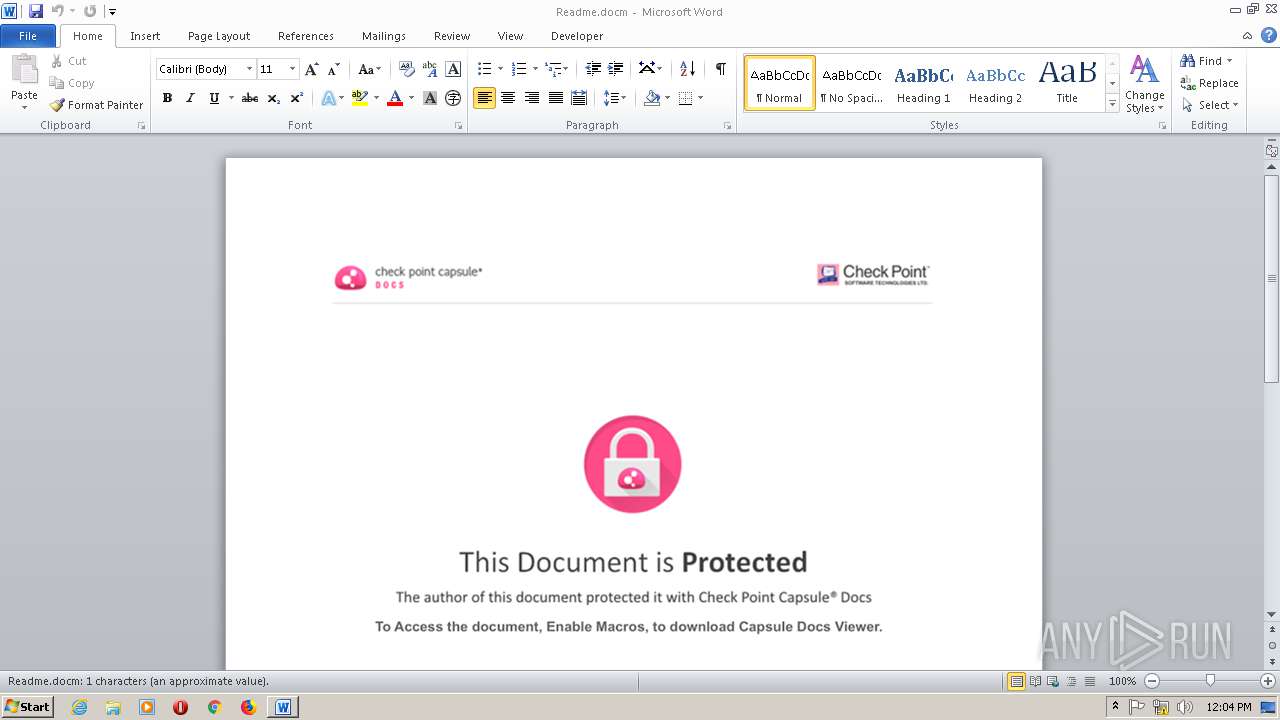
Creates files like Ransomware instruction
- WINWORD.EXE (PID: 564)
Creates files in the program directory
- CPDS.exe (PID: 2412)
- vc110redist_x86.exe (PID: 776)
- Install.exe (PID: 2616)
- lmclientconsole.exe (PID: 3852)
Executable content was dropped or overwritten
- CPDS.exe (PID: 2412)
- capsule.exe (PID: 2804)
- rundll32.exe (PID: 1192)
- vstor_redist.exe (PID: 2020)
- vstor40_x64.exe (PID: 2100)
- msiexec.exe (PID: 2680)
- Install.exe (PID: 2616)
- vc90sp1redist_x86.exe (PID: 2388)
- vc110redist_x86.exe (PID: 776)
- vc120redist_x86.exe (PID: 2936)
- vc120redist_x86.exe (PID: 3028)
- vc110redist_x86.exe (PID: 2572)
Reads Internet Cache Settings
- WINWORD.EXE (PID: 564)
Executed via WMI
- cmd.exe (PID: 2716)
Starts Internet Explorer
- capsule.exe (PID: 2804)
- cmd.exe (PID: 1620)
Uses RUNDLL32.EXE to load library
- capsule.exe (PID: 2804)
- runonce.exe (PID: 1468)
Starts CMD.EXE for commands execution
- rundll32.exe (PID: 1192)
Reads the machine GUID from the registry
- msiexec.exe (PID: 2680)
- MsiExec.exe (PID: 1396)
- explorer.exe (PID: 3924)
Reads default file associations for system extensions
- msiexec.exe (PID: 2680)
Modifies the open verb of a shell class
- msiexec.exe (PID: 2680)
Creates COM task schedule object
- msiexec.exe (PID: 2680)
Executed as Windows Service
- mscorsvw.exe (PID: 3996)
Removes files from Windows directory
- msiexec.exe (PID: 2680)
Adds / modifies Windows certificates
- Launcher.exe (PID: 2344)
Searches for installed software
- vc110redist_x86.exe (PID: 2572)
- vc110redist_x86.exe (PID: 776)
- Install.exe (PID: 2616)
Creates a software uninstall entry
- vc110redist_x86.exe (PID: 776)
- Install.exe (PID: 2616)
Application launched itself
- vc110redist_x86.exe (PID: 776)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 564)
- iexplore.exe (PID: 2740)
- IEXPLORE.EXE (PID: 2840)
Reads the machine GUID from the registry
- WINWORD.EXE (PID: 564)
- iexplore.exe (PID: 2740)
- iexplore.exe (PID: 1488)
Reads Internet Cache Settings
- iexplore.exe (PID: 2740)
- iexplore.exe (PID: 1488)
Reads internet explorer settings
- IEXPLORE.EXE (PID: 1856)
- IEXPLORE.EXE (PID: 2840)
Reads settings of System Certificates
- iexplore.exe (PID: 2740)
- Setup.exe (PID: 192)
- IEXPLORE.EXE (PID: 2840)
- msiexec.exe (PID: 2680)
- IEXPLORE.EXE (PID: 1856)
- iexplore.exe (PID: 1488)
Changes internet zones settings
- iexplore.exe (PID: 2740)
- iexplore.exe (PID: 1488)
Changes settings of System certificates
- IEXPLORE.EXE (PID: 1856)
Creates files in the program directory
- msiexec.exe (PID: 2680)
Loads dropped or rewritten executable
- msiexec.exe (PID: 2680)
- MsiExec.exe (PID: 844)
- MsiExec.exe (PID: 1816)
- MsiExec.exe (PID: 3220)
Application launched itself
- msiexec.exe (PID: 2680)
Creates a software uninstall entry
- msiexec.exe (PID: 2680)
Dropped object may contain Bitcoin addresses
- mscorsvw.exe (PID: 3996)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 564)
Manual execution by user
- runonce.exe (PID: 1068)
- IMEKLMG.EXE (PID: 1504)
- IMEKLMG.EXE (PID: 384)
- runonce.exe (PID: 2136)
- lmclientconsole.exe (PID: 3852)
- explorer.exe (PID: 3924)
- taskmgr.exe (PID: 3976)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x14506c9d |
| ZipCompressedSize: | 438 |
| ZipUncompressedSize: | 1613 |
| ZipFileName: | [Content_Types].xml |
XML
| Template: | Normal.dotm |
|---|---|
| TotalEditTime: | 1 minute |
| Pages: | 1 |
| Words: | - |
| Characters: | 1 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 1 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 14 |
| LastModifiedBy: | analyst |
| RevisionNumber: | 5 |
| CreateDate: | 2018:02:08 16:03:00Z |
| ModifyDate: | 2018:02:08 16:08:00Z |
XMP
| Creator: | analyst |
|---|
Total processes
236
Monitored processes
85
Malicious processes
14
Suspicious processes
42
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 192 | c:\f0d4efd43dab2c5064\Setup.exe /q /norestart /log "C:\Users\admin\AppData\Local\Temp\{CCEDD726-478B-47A5-8EBC-F508FB0460BC}\vstor_redist.log" | c:\f0d4efd43dab2c5064\Setup.exe | — | vstor_redist.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Setup Installer Exit code: 1073807364 Version: 10.0.50903.0 built by: VSTO_Rel Modules
| |||||||||||||||
| 384 | "C:\Program Files\Common Files\Microsoft Shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\Microsoft Shared\IME14\SHARED\IMEKLMG.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 564 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\Readme.docm" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 1073807364 Version: 14.0.5123.5000 Modules
| |||||||||||||||
| 776 | "C:\Users\admin\AppData\Local\Temp\{CCEDD726-478B-47A5-8EBC-F508FB0460BC}\vc110redist_x86.exe" /q /norestart /l "C:\Users\admin\AppData\Local\Temp\{CCEDD726-478B-47A5-8EBC-F508FB0460BC}\vc110redist_x86.log" | C:\Users\admin\AppData\Local\Temp\{CCEDD726-478B-47A5-8EBC-F508FB0460BC}\vc110redist_x86.exe | Install.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2012 Redistributable (x86) - 11.0.61030 Exit code: 0 Version: 11.0.61030.0 Modules
| |||||||||||||||
| 844 | c:\Windows\syswow64\MsiExec.exe -Embedding 522217A1C0140F81714386745C7E24B2 | c:\Windows\syswow64\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 1073807364 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1068 | C:\Windows\system32\runonce.exe /Explorer | C:\Windows\system32\runonce.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1184 | "C:\Windows\System32\rundll32.exe" C:\Users\admin\AppData\Roaming\2094653670c\f2897a.dll,CVMKJV | C:\Windows\SysWOW64\rundll32.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1192 | C:\Windows\system32\rundll32.exe C:\Windows\Temp\_.exe,CVMKJV | C:\Windows\SysWOW64\rundll32.exe | capsule.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 1073807364 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1396 | c:\Windows\system32\MsiExec.exe -Embedding 35DF57C54D86C4D04503A0B27196FC25 E Global\MSI0000 | c:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 1073807364 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1408 | c:\Windows\syswow64\MsiExec.exe -Embedding 148B7A7251245424B68EDBAAE9A36E39 M Global\MSI0000 | c:\Windows\syswow64\MsiExec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 1073807364 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
10 577
Read events
6 634
Write events
3 691
Delete events
252
Modification events
| (PID) Process: | (564) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | k6! |
Value: 6B36210034020000010000000000000000000000 | |||
| (PID) Process: | (564) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (564) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (564) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (564) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (564) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (564) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (564) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (564) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (564) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
Executable files
397
Suspicious files
42
Text files
536
Unknown types
20
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 564 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR664B.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 564 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\Readme.docm.LNK | lnk | |
MD5:— | SHA256:— | |||
| 564 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\capsule.exe | executable | |
MD5:— | SHA256:— | |||
| 2412 | CPDS.exe | C:\Users\admin\AppData\Local\Temp\{CCEDD726-478B-47A5-8EBC-F508FB0460BC}\Launcher.exe | executable | |
MD5:— | SHA256:— | |||
| 2804 | capsule.exe | C:\Windows\Temp\CPDS.exe | executable | |
MD5:— | SHA256:— | |||
| 564 | WINWORD.EXE | C:\Users\admin\Desktop\~$Readme.docm | pgc | |
MD5:— | SHA256:— | |||
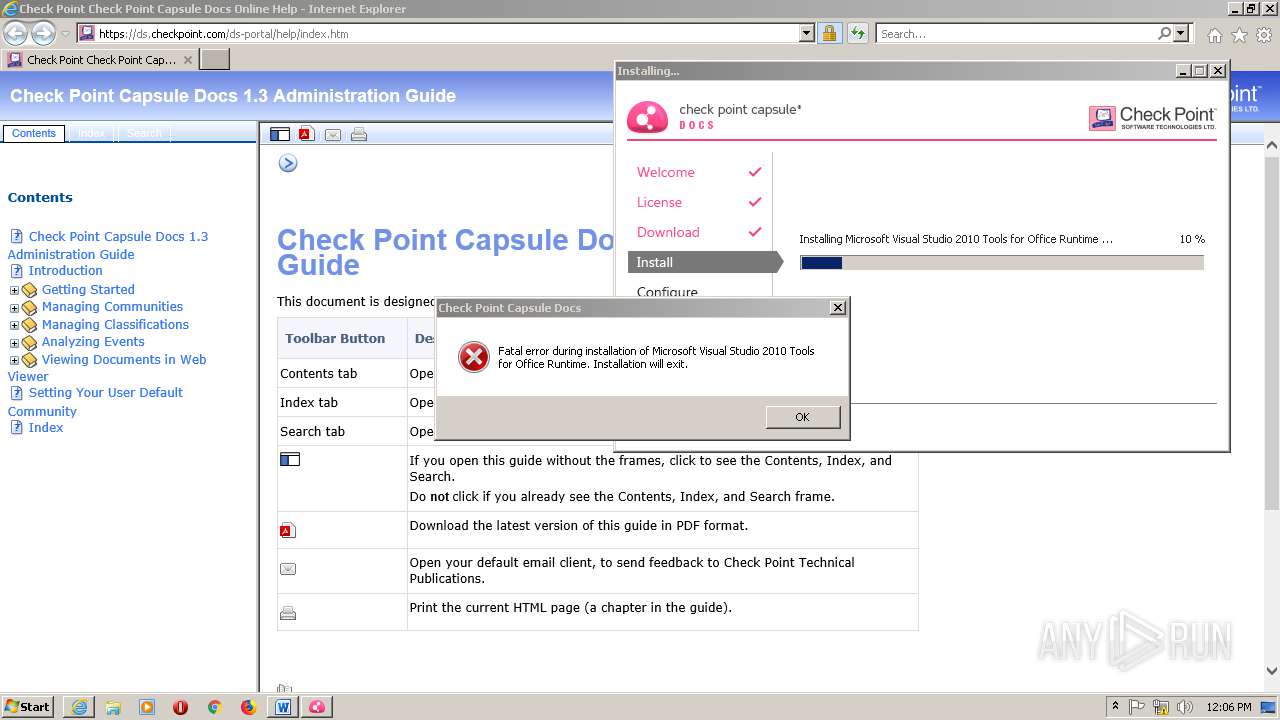
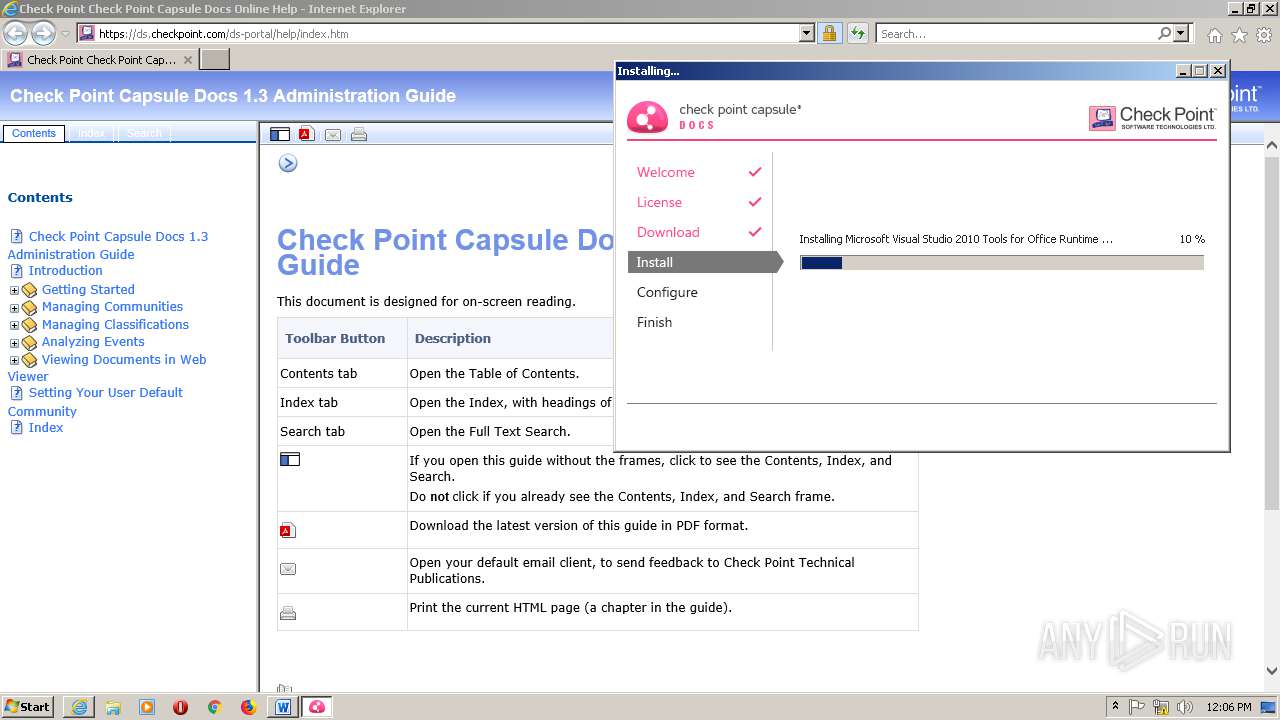
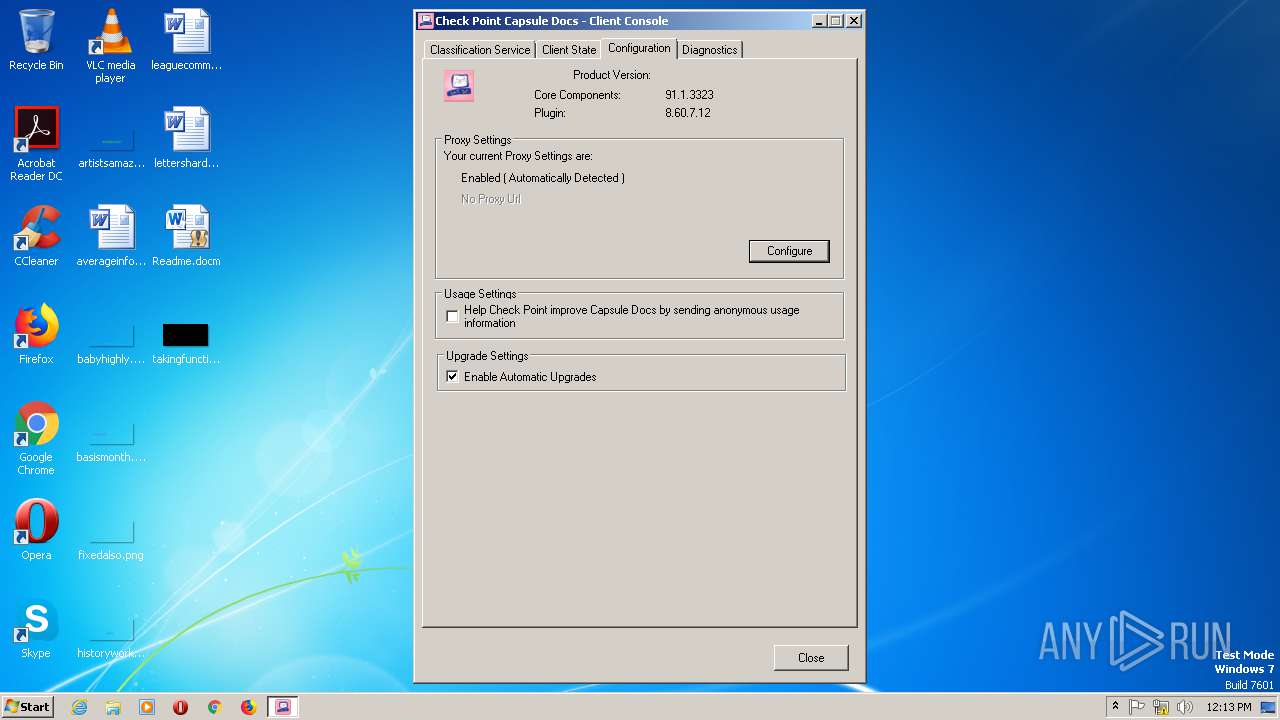
| 2412 | CPDS.exe | C:\Users\admin\AppData\Local\Temp\{CCEDD726-478B-47A5-8EBC-F508FB0460BC}\CapsuleDocsTutorial.doc | document | |
MD5:— | SHA256:— | |||
| 564 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 2412 | CPDS.exe | C:\Users\admin\AppData\Local\Temp\{CCEDD726-478B-47A5-8EBC-F508FB0460BC}\License.txt | text | |
MD5:— | SHA256:— | |||
| 2412 | CPDS.exe | C:\Program Files (x86)\CheckPoint\Document Security\Install\Install.xml | xml | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
74
TCP/UDP connections
56
DNS requests
28
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 104.82.231.81:80 | http://sc1.checkpoint.com/docsec/Integration/91.1.3323/3rdParty/vstor_redist.exe | NL | — | — | whitelisted |
1856 | IEXPLORE.EXE | GET | 200 | 209.87.211.175:443 | https://ds.checkpoint.com/ds-portal/help/docsstylesheet.css | US | text | 2.85 Kb | unknown |
1856 | IEXPLORE.EXE | GET | 200 | 209.87.211.175:443 | https://ds.checkpoint.com/ds-portal/help/heading.htm | US | html | 1.19 Kb | unknown |
1856 | IEXPLORE.EXE | GET | 200 | 209.87.211.175:443 | https://ds.checkpoint.com/ds-portal/help/toc.htm | US | html | 3.01 Kb | unknown |
1856 | IEXPLORE.EXE | GET | 200 | 209.87.211.175:443 | https://ds.checkpoint.com/ds-portal/help/stylesheet.css | US | text | 22.8 Kb | unknown |
1856 | IEXPLORE.EXE | GET | 200 | 209.87.211.175:443 | https://ds.checkpoint.com/ds-portal/help/index.html | US | html | 8.14 Kb | unknown |
1856 | IEXPLORE.EXE | GET | 200 | 209.87.211.175:443 | https://ds.checkpoint.com/ds-portal/help/index.htm | US | html | 1.45 Kb | unknown |
1856 | IEXPLORE.EXE | GET | 200 | 209.87.211.175:443 | https://ds.checkpoint.com/ds-portal/help/banner_center.png | US | image | 222 b | unknown |
1856 | IEXPLORE.EXE | GET | 200 | 209.87.211.175:443 | https://ds.checkpoint.com/ds-portal/help/toolbar_bg.jpg | US | image | 401 b | unknown |
1856 | IEXPLORE.EXE | GET | 200 | 209.87.211.175:443 | https://ds.checkpoint.com/ds-portal/help/checkpoint_utils.js | US | text | 146 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2740 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
1192 | rundll32.exe | 172.217.22.4:80 | www.google.com | Google Inc. | US | whitelisted |
2740 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2840 | IEXPLORE.EXE | 138.197.31.21:80 | fediafedia.com | Digital Ocean, Inc. | US | unknown |
1488 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2840 | IEXPLORE.EXE | 209.197.3.24:80 | code.jquery.com | Highwinds Network Group, Inc. | US | malicious |
2840 | IEXPLORE.EXE | 172.217.22.110:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
2740 | iexplore.exe | 204.79.197.203:443 | www.msn.com | Microsoft Corporation | US | malicious |
2740 | iexplore.exe | 13.92.246.37:443 | query.prod.cms.msn.com | Microsoft Corporation | US | whitelisted |
776 | vc110redist_x86.exe | 95.101.72.17:80 | crl.microsoft.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
sc1.checkpoint.com |
| whitelisted |
ds.checkpoint.com |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.google.com |
| malicious |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
fediafedia.com |
| malicious |
code.jquery.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
564 | WINWORD.EXE | A Network Trojan was detected | ET INFO Executable Download from dotted-quad Host |
564 | WINWORD.EXE | Misc activity | ET INFO Packed Executable Download |
564 | WINWORD.EXE | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
564 | WINWORD.EXE | Potentially Bad Traffic | ET INFO SUSPICIOUS Dotted Quad Host MZ Response |
564 | WINWORD.EXE | Misc activity | ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging) |
— | — | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
5 ETPRO signatures available at the full report