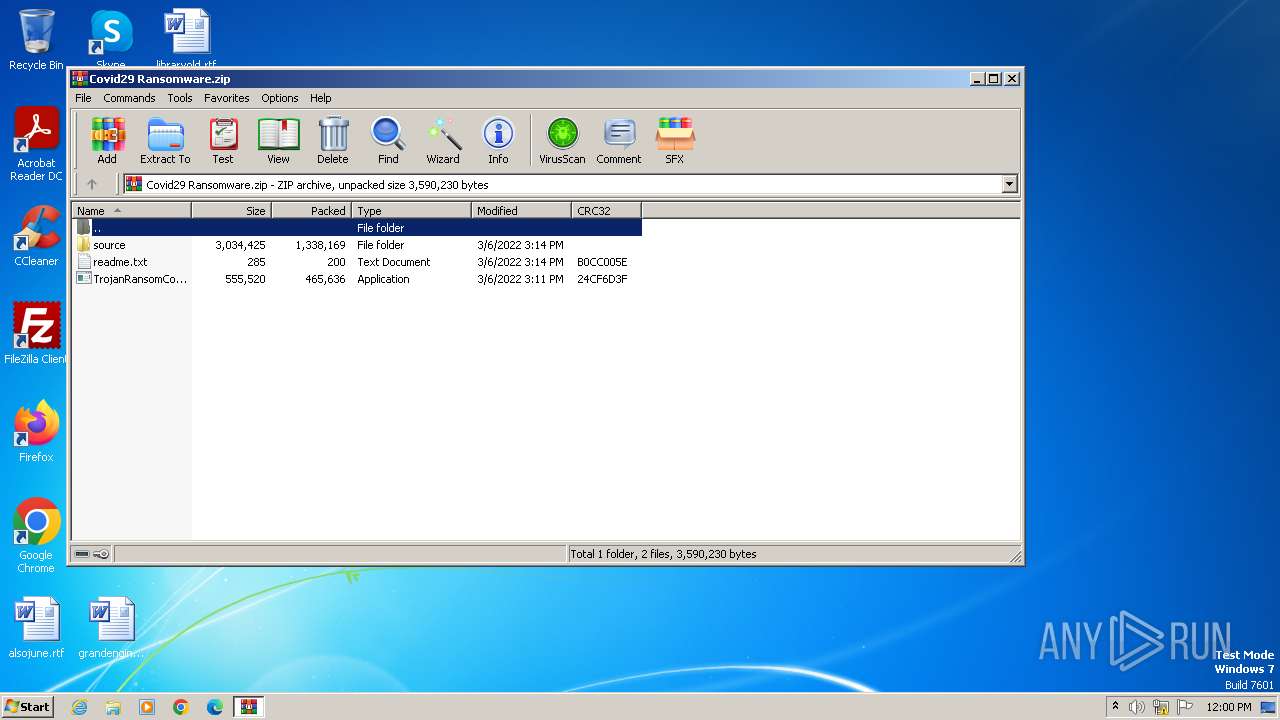
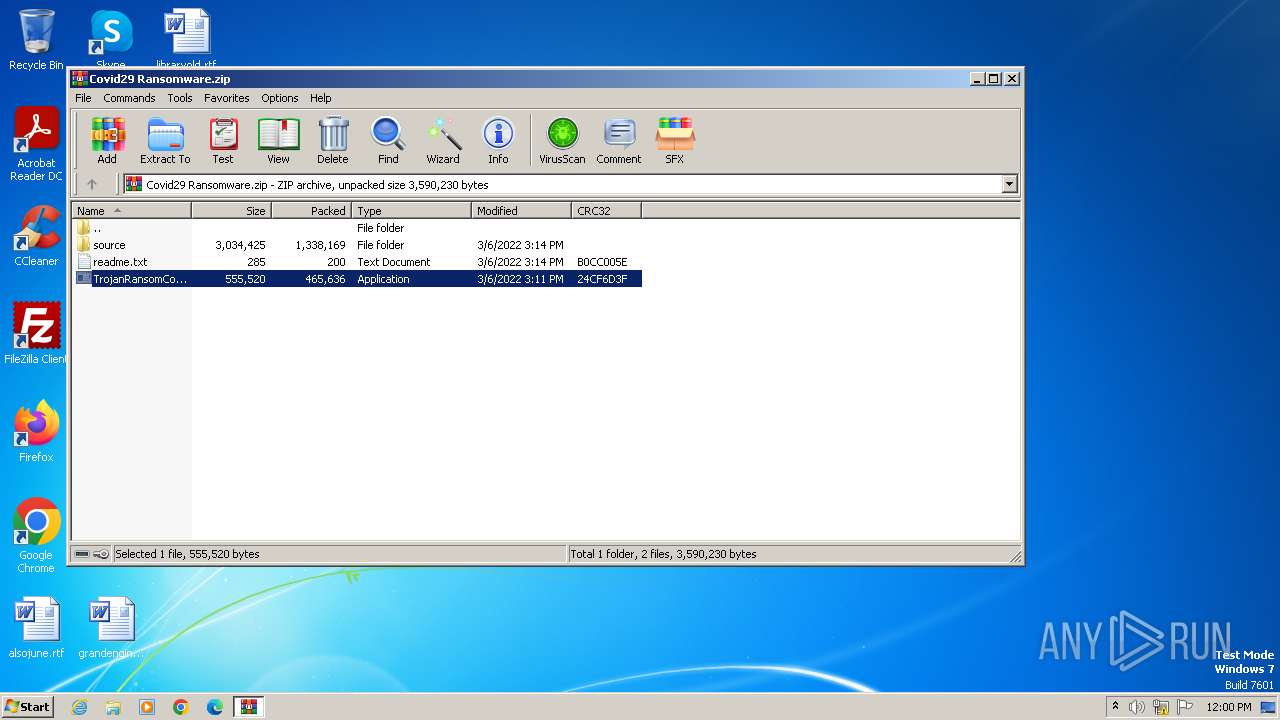
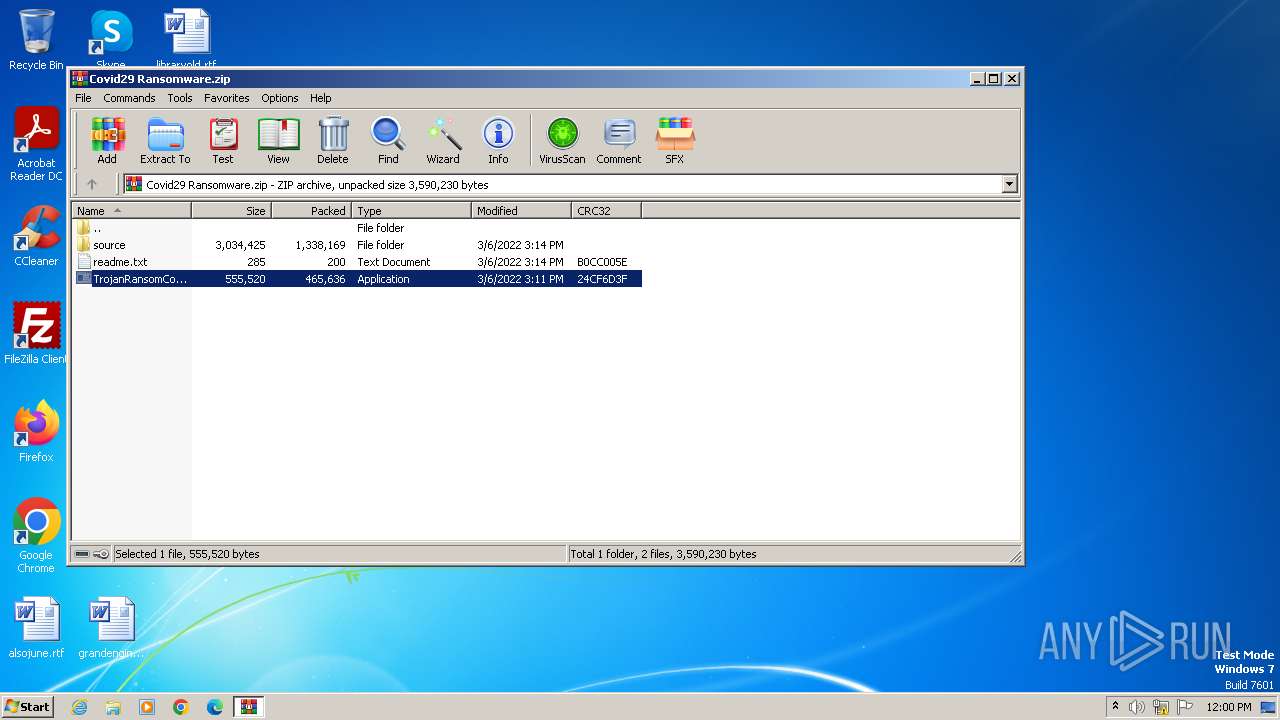
| File name: | Covid29 Ransomware.zip |
| Full analysis: | https://app.any.run/tasks/e983ca32-432d-4826-84f3-b85547afb8b4 |
| Verdict: | Malicious activity |
| Analysis date: | May 26, 2024, 11:00:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 272D3E458250ACD2EA839EB24B427CE5 |
| SHA1: | FAE7194DA5C969F2D8220ED9250AA1DE7BF56609 |
| SHA256: | BBB5C6B4F85C81A323D11D34629776E99CA40E983C5CE0D0A3D540ADDB1C2FE3 |
| SSDEEP: | 49152:dSrGy+kXRl9cIXjRG8OzbgFSXACZ4UL238tvVZkKNDN0AaFlkUSan:OZlyIzRXOfZv4UrtvVZRW6i |
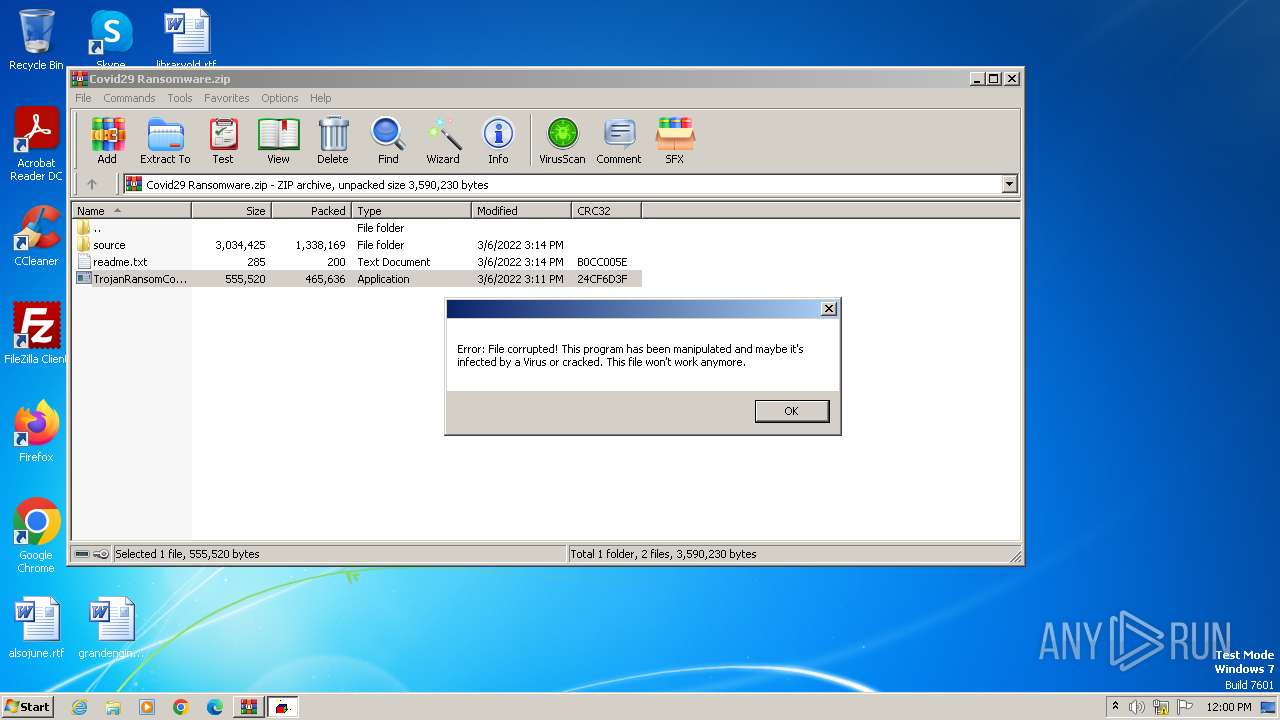
MALICIOUS
Drops the executable file immediately after the start
- TrojanRansomCovid29.exe (PID: 2108)
- WinRAR.exe (PID: 3976)
- cmd.exe (PID: 752)
- Cov29Cry.exe (PID: 1060)
UAC/LUA settings modification
- reg.exe (PID: 316)
Disables the LogOff the Start menu
- reg.exe (PID: 1580)
Actions looks like stealing of personal data
- svchost.exe (PID: 2008)
Deletes shadow copies
- cmd.exe (PID: 2348)
- cmd.exe (PID: 2684)
Create files in the Startup directory
- svchost.exe (PID: 2008)
Using BCDEDIT.EXE to modify recovery options
- cmd.exe (PID: 2324)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3976)
- TrojanRansomCovid29.exe (PID: 2108)
- svchost.exe (PID: 2008)
- Cov29Cry.exe (PID: 1060)
Reads the Internet Settings
- TrojanRansomCovid29.exe (PID: 2108)
- cmd.exe (PID: 752)
- svchost.exe (PID: 2008)
- Cov29Cry.exe (PID: 1060)
- WMIC.exe (PID: 1520)
Executable content was dropped or overwritten
- TrojanRansomCovid29.exe (PID: 2108)
- cmd.exe (PID: 752)
- Cov29Cry.exe (PID: 1060)
Executing commands from a ".bat" file
- TrojanRansomCovid29.exe (PID: 2108)
Starts CMD.EXE for commands execution
- TrojanRansomCovid29.exe (PID: 2108)
- svchost.exe (PID: 2008)
The process executes VB scripts
- cmd.exe (PID: 752)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 752)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 752)
The executable file from the user directory is run by the CMD process
- Cov29Cry.exe (PID: 1060)
- mbr.exe (PID: 764)
- Cov29LockScreen.exe (PID: 2456)
The system shut down or reboot
- cmd.exe (PID: 752)
The process creates files with name similar to system file names
- Cov29Cry.exe (PID: 1060)
Executes as Windows Service
- VSSVC.exe (PID: 736)
- wbengine.exe (PID: 2428)
- vds.exe (PID: 2816)
Starts itself from another location
- Cov29Cry.exe (PID: 1060)
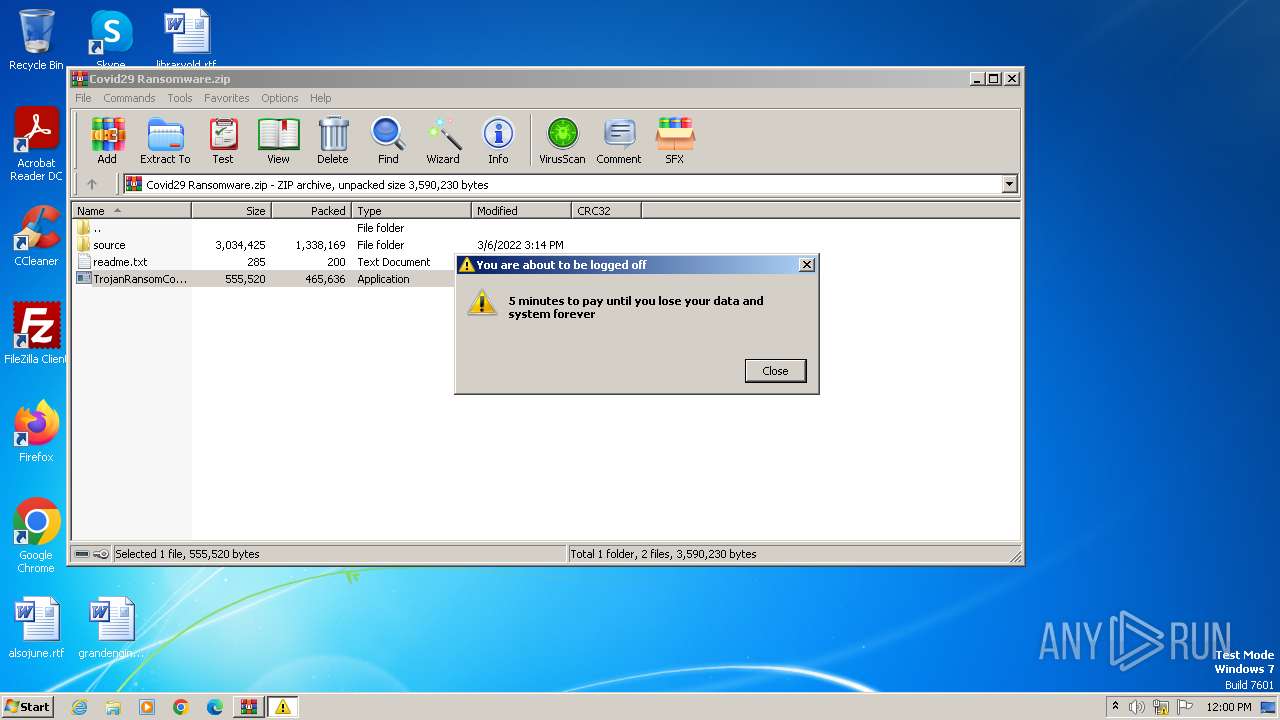
Start notepad (likely ransomware note)
- svchost.exe (PID: 2008)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 752)
INFO
Drops a (possible) Coronavirus decoy
- WinRAR.exe (PID: 3976)
- TrojanRansomCovid29.exe (PID: 2108)
- svchost.exe (PID: 2008)
Checks supported languages
- TrojanRansomCovid29.exe (PID: 2108)
- Cov29Cry.exe (PID: 1060)
- mbr.exe (PID: 764)
- svchost.exe (PID: 2008)
- Cov29LockScreen.exe (PID: 2456)
Reads the computer name
- TrojanRansomCovid29.exe (PID: 2108)
- Cov29Cry.exe (PID: 1060)
- svchost.exe (PID: 2008)
Create files in a temporary directory
- TrojanRansomCovid29.exe (PID: 2108)
- svchost.exe (PID: 2008)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3976)
Creates files or folders in the user directory
- Cov29Cry.exe (PID: 1060)
- svchost.exe (PID: 2008)
Reads the machine GUID from the registry
- svchost.exe (PID: 2008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2022:03:06 16:11:02 |
| ZipCRC: | 0x24cf6d3f |
| ZipCompressedSize: | 465636 |
| ZipUncompressedSize: | 555520 |
| ZipFileName: | TrojanRansomCovid29.exe |
Total processes
77
Monitored processes
33
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 312 | reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v ConsentPromptBehaviorAdmin /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 316 | reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 692 | ping localhost -n 9 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 736 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 752 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\4CDA.tmp\TrojanRansomCovid29.bat" " | C:\Windows\System32\cmd.exe | TrojanRansomCovid29.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 764 | mbr.exe | C:\Users\admin\AppData\Local\Temp\4CDA.tmp\mbr.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1060 | Cov29Cry.exe | C:\Users\admin\AppData\Local\Temp\4CDA.tmp\Cov29Cry.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 1 Version: 0.0.0.0 Modules
| |||||||||||||||
| 1112 | reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System /v DisableTaskMgr /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1520 | wmic shadowcopy delete | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1580 | reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer /v NoLogoff /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
15 542
Read events
15 470
Write events
72
Delete events
0
Modification events
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Covid29 Ransomware.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
14
Suspicious files
1
Text files
130
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3976.5177\source\Bat To Exe Converter\help.chm | chm | |
MD5:FFA8C49B21B077B0DC4B51A1F6F9A753 | SHA256:00037BFC41AFACF262AFDA160E17D3CCA33606276324E99BBD93AD1207E9A7C0 | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3976.5177\TrojanRansomCovid29.exe | executable | |
MD5:9F0563F2FAAF6B9A0F7B3CF058AC80B6 | SHA256:A8054338891DB7231F9885CA0D3BC90A651C63878FF603EDE5C3EFAFA7E25254 | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3976.5177\source\Cov29LockScreen.exe | executable | |
MD5:F724C6DA46DC54E6737DB821F9B62D77 | SHA256:6CDE4A9F109AE5473703C4F5962F43024D71D2138CBD889223283E7B71E5911C | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3976.5177\readme.txt | text | |
MD5:F4F557DB9C615C87E524802AF8A9992F | SHA256:17976E8A6952B0123B729B50B3AD981CBE97083DB9DE66A37EB6F8DECC39B76E | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3976.5177\source\Cov29Cry\AdvancedOptions.PNG | image | |
MD5:C5F0F9AB684461C635F551D045E6CAA5 | SHA256:6C9EB2DA924DF69BCEE50C50F51A67C66321EAF1F453E4C864F037D31E08CF93 | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3976.5177\source\Bat To Exe Converter\Bat_To_Exe_Converter.exe | executable | |
MD5:76D5900A4ADF4C1F2AB8DBFD0A450C4A | SHA256:7ADC1F7FF040628A600F99465BD70E71AD83FECFE60B0F1DADC84B5D262FF350 | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3976.5177\source\Cov29Cry\Cov29Cry.exe.death | executable | |
MD5:8BCD083E16AF6C15E14520D5A0BD7E6A | SHA256:B4F78FF66DC3F5F8DDD694166E6B596D533830792F9B5F1634D3F5F17D6A884A | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3976.5177\source\Bat To Exe Converter\settings.ini | ini | |
MD5:D3BE6C4EDEA45F5A9A766DD235E4C23A | SHA256:236D6136A9EA4241FACB7C459BF0BAD6D1FA572D436E6E73C44884D6126E5AB4 | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3976.5177\source\Cov29Cry\Chaos Ransomware Builder v4.exe | executable | |
MD5:8B855E56E41A6E10D28522A20C1E0341 | SHA256:F2665F89BA53ABD3DEB81988C0D5194992214053E77FC89B98B64A31A7504D77 | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3976.5177\source\Cov29Cry\covid29-is-here.txt | text | |
MD5:0A9F7B91E7C6BEAC740C17951E7FEECB | SHA256:BE6D0B63A86A838D3252CE3EF015029499AF4E9F0F8A0E04062F096368B58B8A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |