| File name: | sfx.exe |
| Full analysis: | https://app.any.run/tasks/97903ac4-ce4f-4d22-933b-0a5d4824b485 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2018, 14:06:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, RAR self-extracting archive |
| MD5: | 531D4AEBE7811A13EC620771A6748C40 |
| SHA1: | 301AFED380BEE985DD6F33761FC5E0BA00CAEB28 |
| SHA256: | BBB0E793550BD5758A31DCD7C489ECC7A6C33D9D1872440330DA68AB5D657906 |
| SSDEEP: | 98304:jKDoMPf6SP4TQHJiWXRr+tLBAqFVaTfXlT/vTeWbu8lLwf:jaUSzHJiqEVAqFG/N/L/DLA |
MALICIOUS
Application was dropped or rewritten from another process
- setupAll.exe (PID: 3560)
- setupAll.exe (PID: 2296)
- setupUSB.exe (PID: 2600)
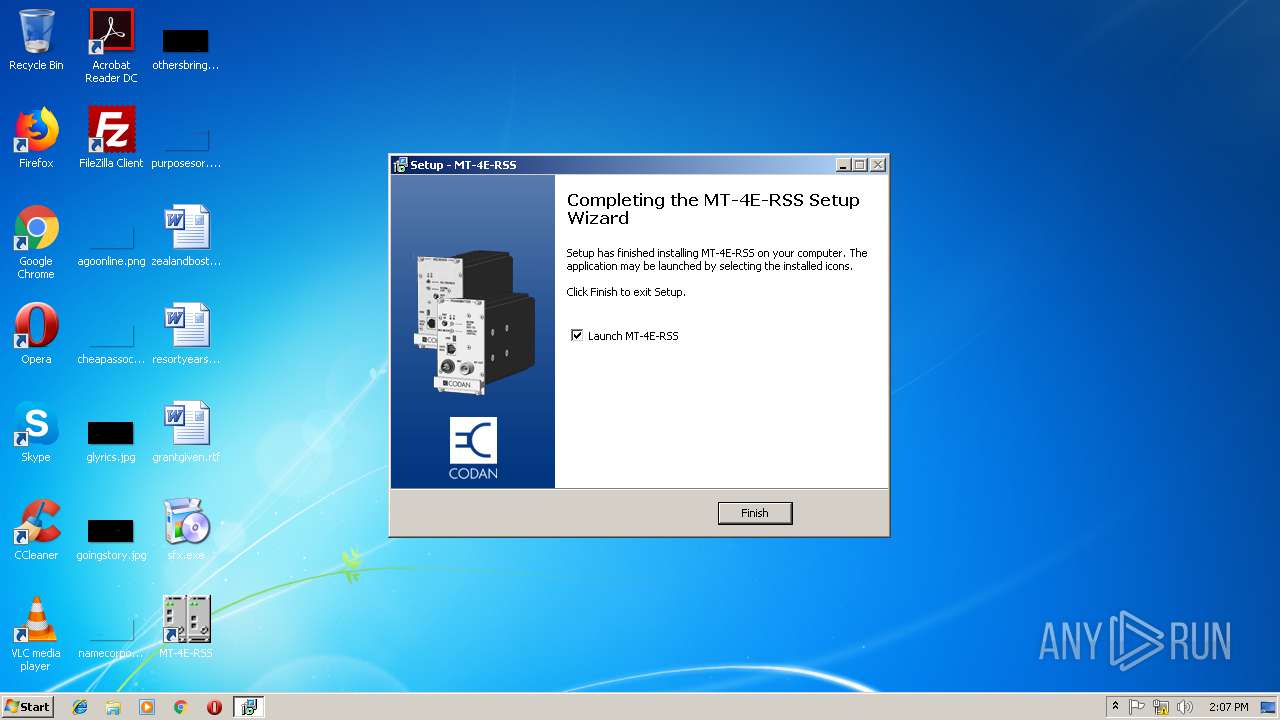
- MT-4E-RSS.exe (PID: 1812)
Loads dropped or rewritten executable
- setupUSB.exe (PID: 2600)
- regsvr32.exe (PID: 1048)
- MT-4E-RSS.exe (PID: 1812)
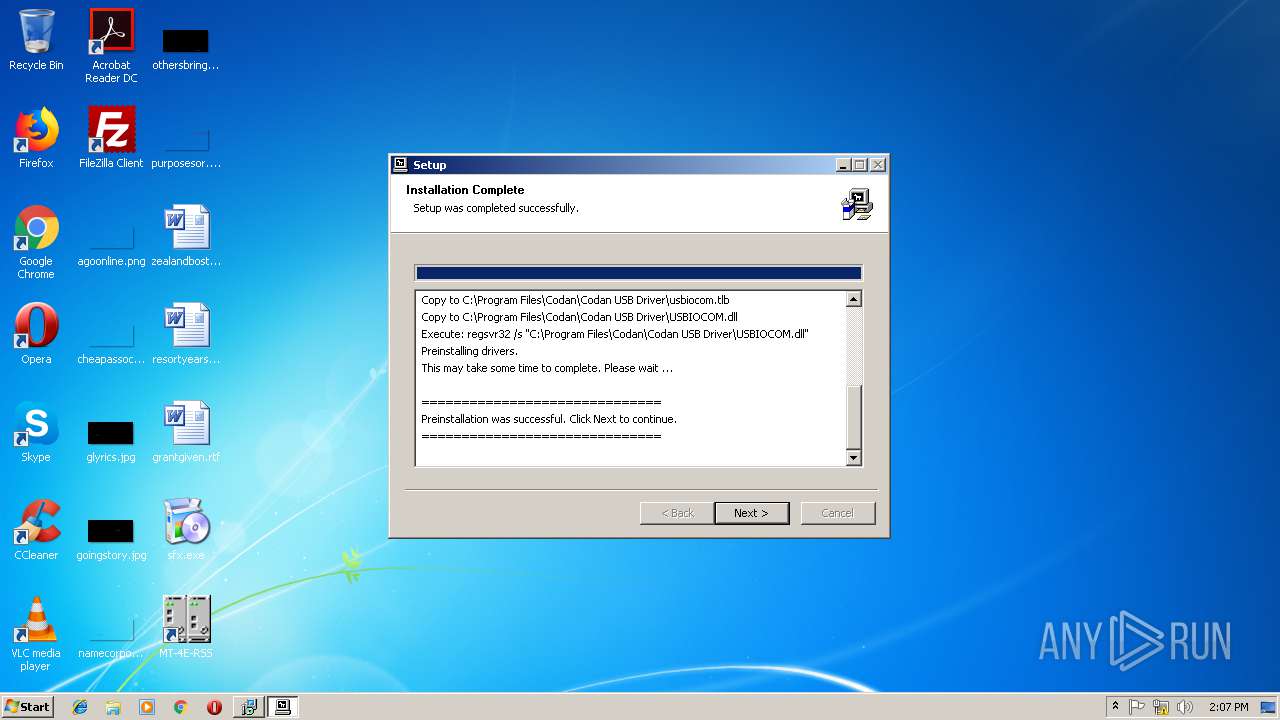
Registers / Runs the DLL via REGSVR32.EXE
- setupUSB.exe (PID: 2600)
SUSPICIOUS
Executable content was dropped or overwritten
- setupAll.exe (PID: 2296)
- setupAll.exe (PID: 3560)
- sfx.exe (PID: 3772)
- setupAll.tmp (PID: 2700)
- setupUSB.exe (PID: 2600)
- DrvInst.exe (PID: 2272)
Creates files in the user directory
- setupAll.tmp (PID: 2700)
Creates files in the Windows directory
- setupUSB.exe (PID: 2600)
- DrvInst.exe (PID: 2272)
Creates a software uninstall entry
- setupUSB.exe (PID: 2600)
Creates files in the program directory
- setupUSB.exe (PID: 2600)
Creates files in the driver directory
- DrvInst.exe (PID: 2272)
Removes files from Windows directory
- DrvInst.exe (PID: 2272)
Uses RUNDLL32.EXE to load library
- DrvInst.exe (PID: 2272)
Searches for installed software
- DrvInst.exe (PID: 2272)
Creates COM task schedule object
- regsvr32.exe (PID: 1048)
INFO
Application was dropped or rewritten from another process
- setupAll.tmp (PID: 2608)
- setupAll.tmp (PID: 2700)
Loads dropped or rewritten executable
- setupAll.tmp (PID: 2700)
Creates files in the program directory
- setupAll.tmp (PID: 2700)
Creates a software uninstall entry
- setupAll.tmp (PID: 2700)
Changes settings of System certificates
- DrvInst.exe (PID: 2272)
Low-level read access rights to disk partition
- vssvc.exe (PID: 3716)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2014:12:02 11:07:30+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 165376 |
| InitializedDataSize: | 64512 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1d5db |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 02-Dec-2014 10:07:30 |
| Detected languages: |
|
| Debug artifacts: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000E8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 02-Dec-2014 10:07:30 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0002859A | 0x00028600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.72265 |
.rdata | 0x0002A000 | 0x00004FD3 | 0x00005000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.38632 |
.data | 0x0002F000 | 0x00021428 | 0x00001600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.46654 |
.rsrc | 0x00051000 | 0x000095B0 | 0x00009600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.79957 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.24822 | 1738 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 4.34688 | 744 | Latin 1 / Western European | Process Default Language | RT_ICON |
3 | 4.08356 | 296 | Latin 1 / Western European | Process Default Language | RT_ICON |
4 | 6.5129 | 3752 | Latin 1 / Western European | Process Default Language | RT_ICON |
5 | 6.72198 | 2216 | Latin 1 / Western European | Process Default Language | RT_ICON |
6 | 5.61913 | 1384 | Latin 1 / Western European | Process Default Language | RT_ICON |
7 | 3.1586 | 482 | Latin 1 / Western European | English - United States | RT_STRING |
8 | 3.11685 | 460 | Latin 1 / Western European | English - United States | RT_STRING |
9 | 3.15447 | 494 | Latin 1 / Western European | English - United States | RT_STRING |
10 | 2.99727 | 326 | Latin 1 / Western European | English - United States | RT_STRING |
Imports
ADVAPI32.dll |
COMCTL32.dll |
COMDLG32.dll |
GDI32.dll |
KERNEL32.dll |
OLEAUT32.dll |
SHELL32.dll |
SHLWAPI.dll |
USER32.dll |
ole32.dll |
Total processes
47
Monitored processes
12
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1048 | regsvr32 /s "C:\Program Files\Codan\Codan USB Driver\USBIOCOM.dll" | C:\Windows\system32\regsvr32.exe | — | setupUSB.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
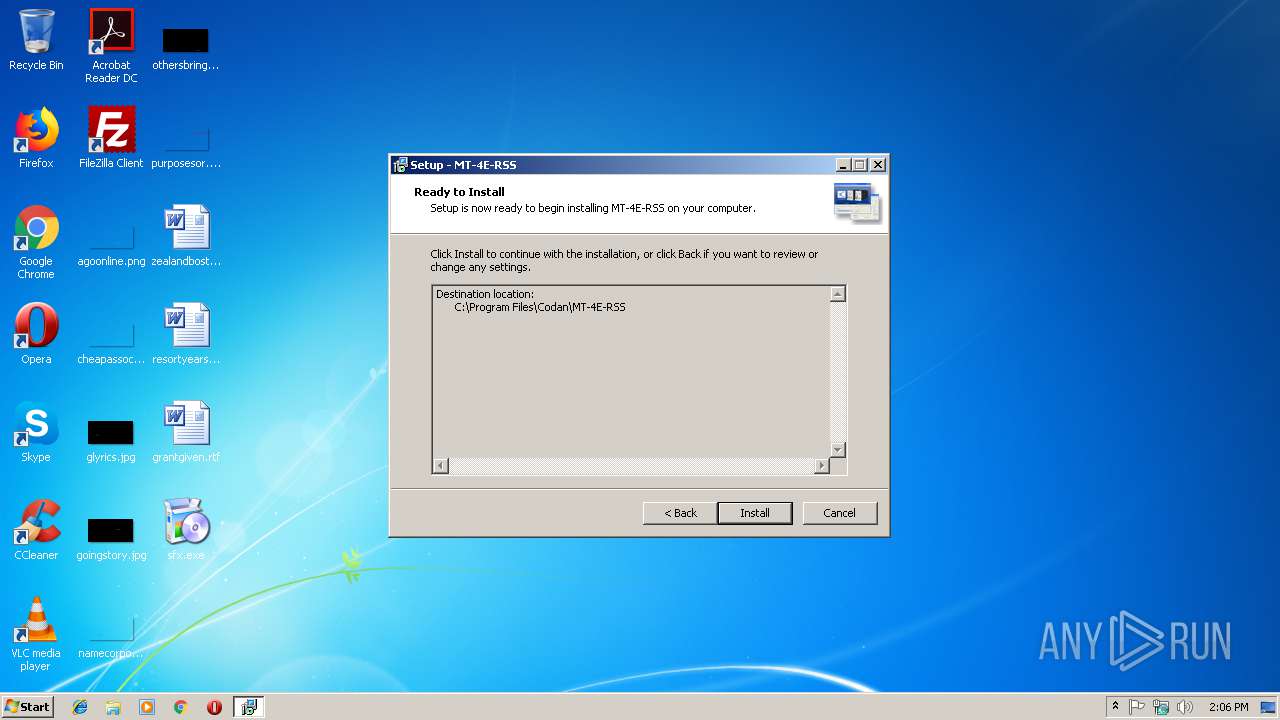
| 1812 | "C:\Program Files\Codan\MT-4E-RSS\MT-4E-RSS.exe" | C:\Program Files\Codan\MT-4E-RSS\MT-4E-RSS.exe | — | setupAll.tmp | |||||||||||
User: admin Company: Codan Radio Communications Integrity Level: MEDIUM Description: MT-4E RSS Exit code: 0 Version: 1.7.7.0 Modules
| |||||||||||||||
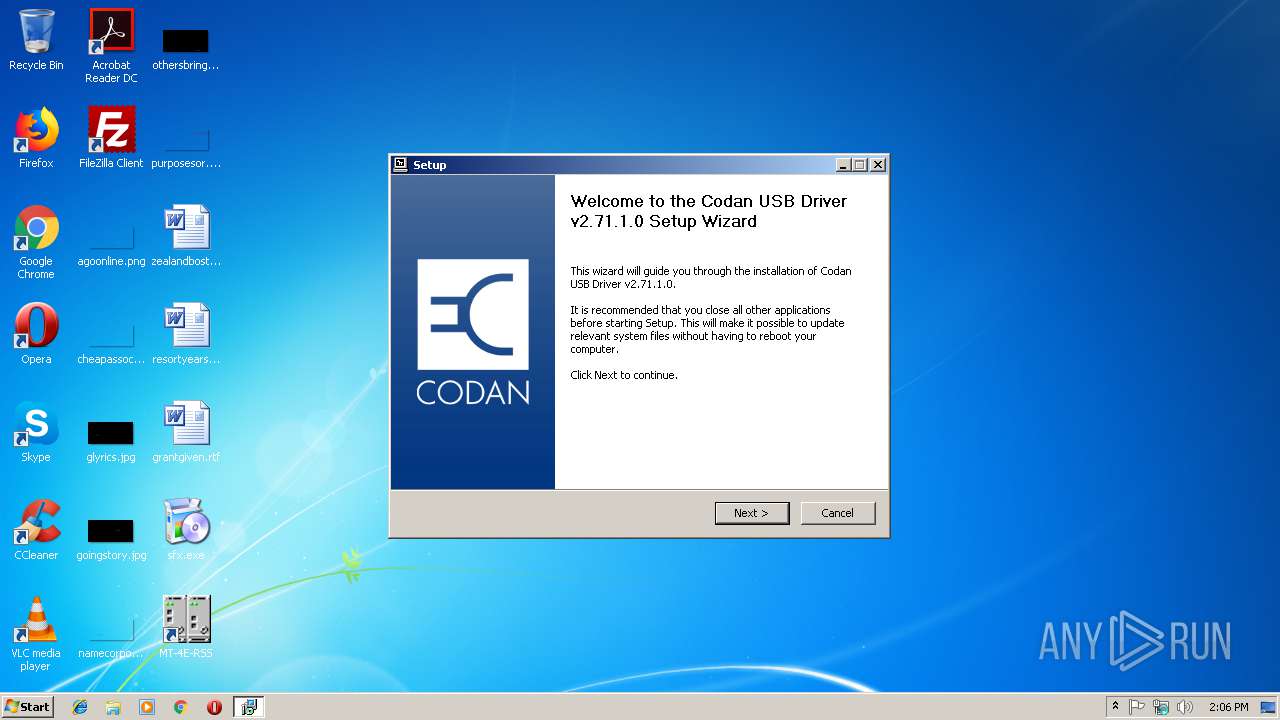
| 2272 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{67e871a3-381a-1b9b-4d28-377ca9e1780e}\codanusb.inf" "0" "6a15d52f7" "000002D0" "WinSta0\Default" "000003A8" "208" "C:\Program Files\Codan\Codan USB Driver" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
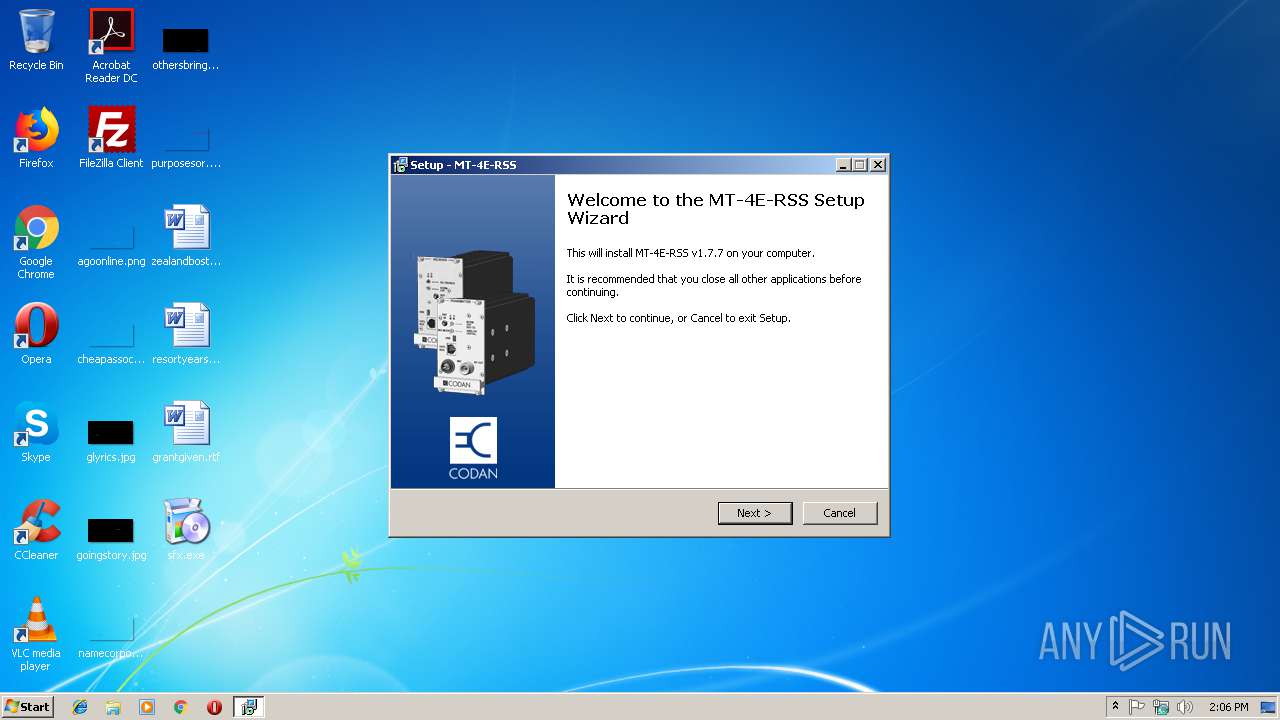
| 2296 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\setupAll.exe" /SPAWNWND=$10152 /NOTIFYWND=$10146 | C:\Users\admin\AppData\Local\Temp\RarSFX0\setupAll.exe | setupAll.tmp | ||||||||||||
User: admin Company: Codan Radio Communications Integrity Level: HIGH Description: MT-4E-RSS Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 2336 | rundll32.exe C:\Windows\system32\pnpui.dll,InstallSecurityPromptRunDllW 20 Global\{6b9e9027-3780-4c35-78a2-0c2198374116} Global\{0219e9e4-f70e-17a8-bc42-5a7318bd313e} C:\Windows\System32\DriverStore\Temp\{3991c3eb-a874-4758-346c-487f3385ea21}\codanusb.inf C:\Windows\System32\DriverStore\Temp\{3991c3eb-a874-4758-346c-487f3385ea21}\codanusb.cat | C:\Windows\system32\rundll32.exe | — | DrvInst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
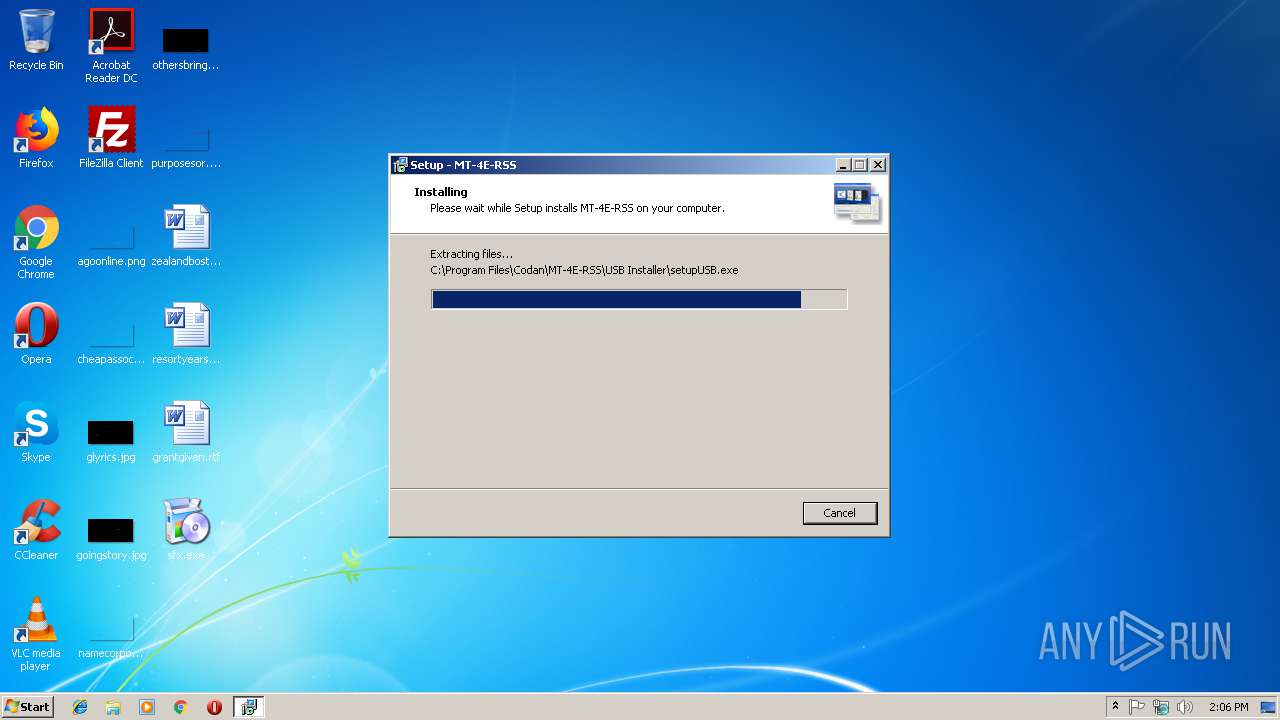
| 2600 | "C:\Program Files\Codan\MT-4E-RSS\USB Installer\setupUSB.exe" | C:\Program Files\Codan\MT-4E-RSS\USB Installer\setupUSB.exe | setupAll.tmp | ||||||||||||
User: admin Integrity Level: HIGH Description: PnP Driver Installer Exit code: 0 Version: 1.7.0.0 Modules
| |||||||||||||||
| 2608 | "C:\Users\admin\AppData\Local\Temp\is-GVV77.tmp\setupAll.tmp" /SL5="$10146,3487278,56832,C:\Users\admin\AppData\Local\Temp\RarSFX0\setupAll.exe" | C:\Users\admin\AppData\Local\Temp\is-GVV77.tmp\setupAll.tmp | — | setupAll.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 2680 | DrvInst.exe "1" "200" "STORAGE\VolumeSnapshot\HarddiskVolumeSnapshot18" "" "" "6792c44eb" "00000000" "000005E4" "000005EC" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2700 | "C:\Users\admin\AppData\Local\Temp\is-VUEB8.tmp\setupAll.tmp" /SL5="$20154,3487278,56832,C:\Users\admin\AppData\Local\Temp\RarSFX0\setupAll.exe" /SPAWNWND=$10152 /NOTIFYWND=$10146 | C:\Users\admin\AppData\Local\Temp\is-VUEB8.tmp\setupAll.tmp | setupAll.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 3560 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\setupAll.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\setupAll.exe | sfx.exe | ||||||||||||
User: admin Company: Codan Radio Communications Integrity Level: MEDIUM Description: MT-4E-RSS Setup Exit code: 0 Version: Modules
| |||||||||||||||
Total events
1 373
Read events
1 089
Write events
278
Delete events
6
Modification events
| (PID) Process: | (3772) sfx.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3772) sfx.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2700) setupAll.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 8C0A000038E0EBE46C8DD401 | |||
| (PID) Process: | (2700) setupAll.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: BDB9E418BEDF6C7EF960A617C84AA367885D69E4A0FA66B80A63437FC4AE5F51 | |||
| (PID) Process: | (2700) setupAll.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2700) setupAll.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\Codan\MT-4E-RSS\MT-4E-RSS.exe | |||
| (PID) Process: | (2700) setupAll.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 199E468347C429950C58C33CEC6B7DFEC4E3ABACB6FC3850248CF09714EC404C | |||
| (PID) Process: | (2700) setupAll.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs |
| Operation: | write | Name: | C:\Program Files\Codan\MT-4E-RSS\USB Installer\codanusb.cat |
Value: 1 | |||
| (PID) Process: | (2700) setupAll.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs |
| Operation: | write | Name: | C:\Program Files\Codan\MT-4E-RSS\USB Installer\codanusb.inf |
Value: 1 | |||
| (PID) Process: | (2700) setupAll.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs |
| Operation: | write | Name: | C:\Program Files\Codan\MT-4E-RSS\USB Installer\codanusb.sys |
Value: 1 | |||
Executable files
30
Suspicious files
18
Text files
270
Unknown types
531
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2700 | setupAll.tmp | C:\Program Files\Codan\MT-4E-RSS\is-CHV1D.tmp | — | |
MD5:— | SHA256:— | |||
| 2700 | setupAll.tmp | C:\Program Files\Codan\MT-4E-RSS\is-3HJAG.tmp | — | |
MD5:— | SHA256:— | |||
| 2700 | setupAll.tmp | C:\Program Files\Codan\MT-4E-RSS\is-U2DE4.tmp | — | |
MD5:— | SHA256:— | |||
| 2700 | setupAll.tmp | C:\Program Files\Codan\MT-4E-RSS\is-NHVFH.tmp | — | |
MD5:— | SHA256:— | |||
| 2700 | setupAll.tmp | C:\Program Files\Codan\MT-4E-RSS\is-I0F2R.tmp | — | |
MD5:— | SHA256:— | |||
| 2700 | setupAll.tmp | C:\Program Files\Codan\MT-4E-RSS\is-30G0J.tmp | — | |
MD5:— | SHA256:— | |||
| 2700 | setupAll.tmp | C:\Program Files\Codan\MT-4E-RSS\USB Installer\is-RRR7L.tmp | — | |
MD5:— | SHA256:— | |||
| 2700 | setupAll.tmp | C:\Program Files\Codan\MT-4E-RSS\USB Installer\is-86S65.tmp | — | |
MD5:— | SHA256:— | |||
| 2700 | setupAll.tmp | C:\Program Files\Codan\MT-4E-RSS\USB Installer\is-ECL6T.tmp | — | |
MD5:— | SHA256:— | |||
| 2700 | setupAll.tmp | C:\Program Files\Codan\MT-4E-RSS\USB Installer\is-O2VJT.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report