| File name: | GLP_installer_900223150_market.exe |
| Full analysis: | https://app.any.run/tasks/a84e5bcd-81ab-4fbd-a666-1e754571c67b |
| Verdict: | Malicious activity |
| Analysis date: | August 21, 2024, 13:25:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 0AC1FD602F5EC2D2231FE311777791E8 |
| SHA1: | 52CA6CCD121FAF4F3AAD9E7760EE1A519B323D83 |
| SHA256: | BB68113CFABA1DEF162B8A0DF4B1D41B83EA34CE4FD5B23E0A0B75B259B62BFC |
| SSDEEP: | 49152:808OhxtUg9OUi82w6aQp9dgS1GUL38XhCOYc3iJXe9emEPGKOPkQThMYRMnm7LBg:808vdsGaQNgS1C6e6ngKpqM |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates file in the systems drive root
- GLP_installer_900223150_market.exe (PID: 6700)
- TInst.exe (PID: 6512)
- QMEmulatorService.exe (PID: 2480)
Drops the executable file immediately after the start
- GLP_installer_900223150_market.exe (PID: 6700)
- Market.exe (PID: 5656)
- TInst.exe (PID: 6512)
Executable content was dropped or overwritten
- GLP_installer_900223150_market.exe (PID: 6700)
- Market.exe (PID: 5656)
- TInst.exe (PID: 6512)
Reads security settings of Internet Explorer
- GLP_installer_900223150_market.exe (PID: 6700)
- TInst.exe (PID: 6512)
- StartMenuExperienceHost.exe (PID: 3696)
Reads the date of Windows installation
- GLP_installer_900223150_market.exe (PID: 6700)
- StartMenuExperienceHost.exe (PID: 3696)
- SearchApp.exe (PID: 3140)
Process drops legitimate windows executable
- Market.exe (PID: 5656)
- TInst.exe (PID: 6512)
The process drops C-runtime libraries
- Market.exe (PID: 5656)
- TInst.exe (PID: 6512)
The process creates files with name similar to system file names
- Market.exe (PID: 5656)
- TInst.exe (PID: 6512)
Executes as Windows Service
- QMEmulatorService.exe (PID: 2480)
Uses NETSH.EXE to add a firewall rule or allowed programs
- TInst.exe (PID: 6512)
Creates a software uninstall entry
- TInst.exe (PID: 6512)
INFO
Creates files or folders in the user directory
- GLP_installer_900223150_market.exe (PID: 6700)
- TInst.exe (PID: 6512)
Reads the machine GUID from the registry
- GLP_installer_900223150_market.exe (PID: 6700)
- SearchApp.exe (PID: 3140)
Checks supported languages
- GLP_installer_900223150_market.exe (PID: 6700)
- Market.exe (PID: 5656)
- TInst.exe (PID: 6512)
- QMEmulatorService.exe (PID: 2480)
- TextInputHost.exe (PID: 3996)
- StartMenuExperienceHost.exe (PID: 3696)
- SearchApp.exe (PID: 3140)
Create files in a temporary directory
- GLP_installer_900223150_market.exe (PID: 6700)
- TInst.exe (PID: 6512)
Creates files in the program directory
- GLP_installer_900223150_market.exe (PID: 6700)
- TInst.exe (PID: 6512)
- QMEmulatorService.exe (PID: 2480)
Reads the software policy settings
- GLP_installer_900223150_market.exe (PID: 6700)
- TInst.exe (PID: 6512)
- SearchApp.exe (PID: 3140)
Reads the computer name
- GLP_installer_900223150_market.exe (PID: 6700)
- Market.exe (PID: 5656)
- TInst.exe (PID: 6512)
- QMEmulatorService.exe (PID: 2480)
- TextInputHost.exe (PID: 3996)
- StartMenuExperienceHost.exe (PID: 3696)
- SearchApp.exe (PID: 3140)
Dropped object may contain TOR URL's
- Market.exe (PID: 5656)
- TInst.exe (PID: 6512)
Process checks computer location settings
- GLP_installer_900223150_market.exe (PID: 6700)
- StartMenuExperienceHost.exe (PID: 3696)
- SearchApp.exe (PID: 3140)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 5264)
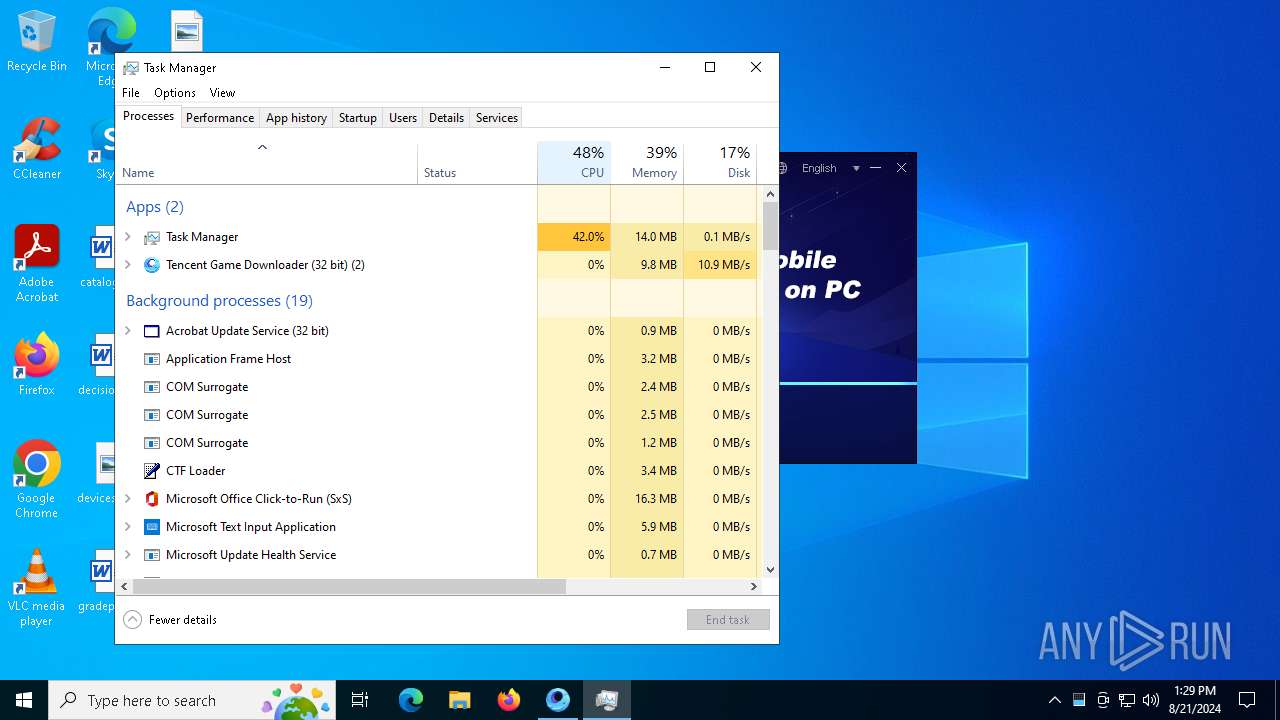
Manual execution by a user
- Taskmgr.exe (PID: 1812)
- Taskmgr.exe (PID: 5264)
Process checks Internet Explorer phishing filters
- SearchApp.exe (PID: 3140)
Checks proxy server information
- SearchApp.exe (PID: 3140)
Reads Environment values
- SearchApp.exe (PID: 3140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (3.6) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (1.6) |
| .exe | | | DOS Executable Generic (1.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:17 02:57:05+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 2604544 |
| InitializedDataSize: | 1211392 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x220be4 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.1 |
| ProductVersionNumber: | 1.0.0.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Tencent |
| FileDescription: | Tencent Game Downloader |
| FileVersion: | 1, 0, 0, 1 |
| InternalName: | TGBDownloader.exe |
| LegalCopyright: | Copyright ? 2020 Tencent. All Rights Reserved. |
| OriginalFileName: | TGBDownloader.exe |
| ProductName: | Tencent Game Downloader |
| ProductVersion: | 1, 0, 0, 1 |
Total processes
175
Monitored processes
28
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 752 | "C:\WINDOWS\system32\Netsh.exe" advfirewall firewall add rule name="bugreport" dir=in program="c:\program files\txgameassistant\appmarket\bugreport.exe" action=allow | C:\Windows\SysWOW64\netsh.exe | — | TInst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1072 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1076 | "C:\WINDOWS\system32\Netsh.exe" advfirewall firewall add rule name="GameDownload" dir=in program="c:\program files\txgameassistant\appmarket\GameDownload.exe" action=allow | C:\Windows\SysWOW64\netsh.exe | — | TInst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1436 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 | |||||||||||||||
| 1784 | "C:\WINDOWS\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca | C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM | |||||||||||||||
| 1812 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1944 | "C:\WINDOWS\system32\Netsh.exe" advfirewall firewall add rule name="TInst" dir=in program="c:\program files\txgameassistant\appmarket\TInst.exe" action=allow | C:\Windows\SysWOW64\netsh.exe | — | TInst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2096 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2132 | "C:\WINDOWS\system32\Netsh.exe" advfirewall firewall add rule name="AppMarket" dir=in program="c:\program files\txgameassistant\appmarket\AppMarket.exe" action=allow | C:\Windows\SysWOW64\netsh.exe | — | TInst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
37 039
Read events
36 907
Write events
128
Delete events
4
Modification events
| (PID) Process: | (6700) GLP_installer_900223150_market.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Tencent\MobileGamePC\Beacon |
| Operation: | write | Name: | Last_Sid_GLP_installer_900223150_market.exe |
Value: D4FDB13E-1C9A-4222-BA7E-2946AF31FF16 | |||
| (PID) Process: | (6700) GLP_installer_900223150_market.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Tencent\MobileGamePC |
| Operation: | write | Name: | TempPath |
Value: C:\Temp\TxGameDownload\Component\ | |||
| (PID) Process: | (6700) GLP_installer_900223150_market.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Tencent\MobileGamePC |
| Operation: | write | Name: | UserLanguage |
Value: en | |||
| (PID) Process: | (6700) GLP_installer_900223150_market.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Tencent\MobileGamePC |
| Operation: | write | Name: | abtestid |
Value: {"Component":"0"} | |||
| (PID) Process: | (6700) GLP_installer_900223150_market.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Tencent\MobileGamePC\GameDownload |
| Operation: | write | Name: | DownloadSpeed |
Value: 0 | |||
| (PID) Process: | (6700) GLP_installer_900223150_market.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Tencent\MobileGamePC |
| Operation: | write | Name: | SupplyId |
Value: 900223150 | |||
| (PID) Process: | (6700) GLP_installer_900223150_market.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Tencent\MobileGamePC |
| Operation: | write | Name: | Region |
Value: DE | |||
| (PID) Process: | (6700) GLP_installer_900223150_market.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Tencent\MobileGamePC\AppMarket |
| Operation: | write | Name: | InstallPath |
Value: C:\Program Files\TxGameAssistant\AppMarket | |||
| (PID) Process: | (6700) GLP_installer_900223150_market.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6700) GLP_installer_900223150_market.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
441
Suspicious files
303
Text files
1 908
Unknown types
35
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6700 | GLP_installer_900223150_market.exe | C:\Temp\TxGameDownload\Component\AppMarket\1d218714941abf910cf39c6d4f265e7d\Market.exe | — | |
MD5:— | SHA256:— | |||
| 5656 | Market.exe | C:\Temp\TxGameDownload\Component\AppMarket\1d218714941abf910cf39c6d4f265e7d\Setup\api-ms-win-core-file-l1-2-0.dll | executable | |
MD5:EC4F2CB68DCF7E96516EB284003BE8BB | SHA256:3816BBB7DD76D8FC6A7B83A0ED2F61B23DD5FC0843D3308EE077CB725D5C9088 | |||
| 5656 | Market.exe | C:\Temp\TxGameDownload\Component\AppMarket\1d218714941abf910cf39c6d4f265e7d\Setup\api-ms-win-core-file-l1-2-1.dll | executable | |
MD5:A32230B9BFDB8813E94D095222AAFA11 | SHA256:7068D2B8AEA252294E6B5C3BF3630475D0A91E11877F11A04E8ED1F91196410F | |||
| 5656 | Market.exe | C:\Temp\TxGameDownload\Component\AppMarket\1d218714941abf910cf39c6d4f265e7d\Setup\api-ms-win-core-errorhandling-l1-1-0.dll | executable | |
MD5:9D74D89F2679C0C5DDB35A1EF30BD182 | SHA256:E207FFC6FEF144E5D393E79DE75F8F20D223F1AC33A011EEB822D30FA2031046 | |||
| 5656 | Market.exe | C:\Temp\TxGameDownload\Component\AppMarket\1d218714941abf910cf39c6d4f265e7d\Setup\api-ms-win-core-handle-l1-1-0.dll | executable | |
MD5:6A35A52D536E34BA060A19D06B1DAC80 | SHA256:A369EF130749BF8CD9F67055179E6F537F200C060AF47493D49473912A95021E | |||
| 5656 | Market.exe | C:\Temp\TxGameDownload\Component\AppMarket\1d218714941abf910cf39c6d4f265e7d\Setup\api-ms-win-core-libraryloader-l1-1-0.dll | executable | |
MD5:E33F52E89DFC376EAF7AA655F260CA76 | SHA256:0BD03E89A539AAA3100E2F7D9A058964730320E55AEE1F85BE8FD243EEA7017A | |||
| 5656 | Market.exe | C:\Temp\TxGameDownload\Component\AppMarket\1d218714941abf910cf39c6d4f265e7d\Setup\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:64978E199A7239D2C911876447A7F05B | SHA256:92B947F1D6236F86ED7E105CFF19E23C13D1968861426511B775905E1D26B47A | |||
| 5656 | Market.exe | C:\Temp\TxGameDownload\Component\AppMarket\1d218714941abf910cf39c6d4f265e7d\Setup\AECommonDll.dll | executable | |
MD5:B58C94617DF43430D2342A66EAA0A554 | SHA256:74C2288B4FF073C5C947F96B0C79A01C587981A8B9440290A9FF33AA14F06E6D | |||
| 5656 | Market.exe | C:\Temp\TxGameDownload\Component\AppMarket\1d218714941abf910cf39c6d4f265e7d\Setup\AowGame.xml | text | |
MD5:5FD0B9F7612369BCA18996D8AAA9F62C | SHA256:9937ADDC0F2EEA66EF456A53B21F93E8AE2732CB83F3E0E08E94E763F0150537 | |||
| 6700 | GLP_installer_900223150_market.exe | C:\Users\admin\AppData\Local\Tencent\TxGameAssistant\TGBDownloader\dr.dll | executable | |
MD5:2814ACBD607BA47BDBCDF6AC3076EE95 | SHA256:5904A7E4D97EEAC939662C3638A0E145F64FF3DD0198F895C4BF0337595C6A67 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
64
DNS requests
29
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6472 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1104 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
7148 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7040 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3140 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3916 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3144 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
6700 | GLP_installer_900223150_market.exe | 157.255.4.39:443 | master.etl.desktop.qq.com | China Unicom Guangdong IP network | CN | unknown |
6700 | GLP_installer_900223150_market.exe | 101.33.47.68:8081 | oth.eve.mdt.qq.com | Tencent Building, Kejizhongyi Avenue | SG | unknown |
3916 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6700 | GLP_installer_900223150_market.exe | 49.51.129.71:443 | unifiedaccess.gameloop.com | Tencent Building, Kejizhongyi Avenue | DE | unknown |
6700 | GLP_installer_900223150_market.exe | 43.175.151.207:443 | down.gameloop.com | — | SG | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
master.etl.desktop.qq.com |
| whitelisted |
oth.eve.mdt.qq.com |
| whitelisted |
unifiedaccess.gameloop.com |
| unknown |
down.gameloop.com |
| unknown |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |