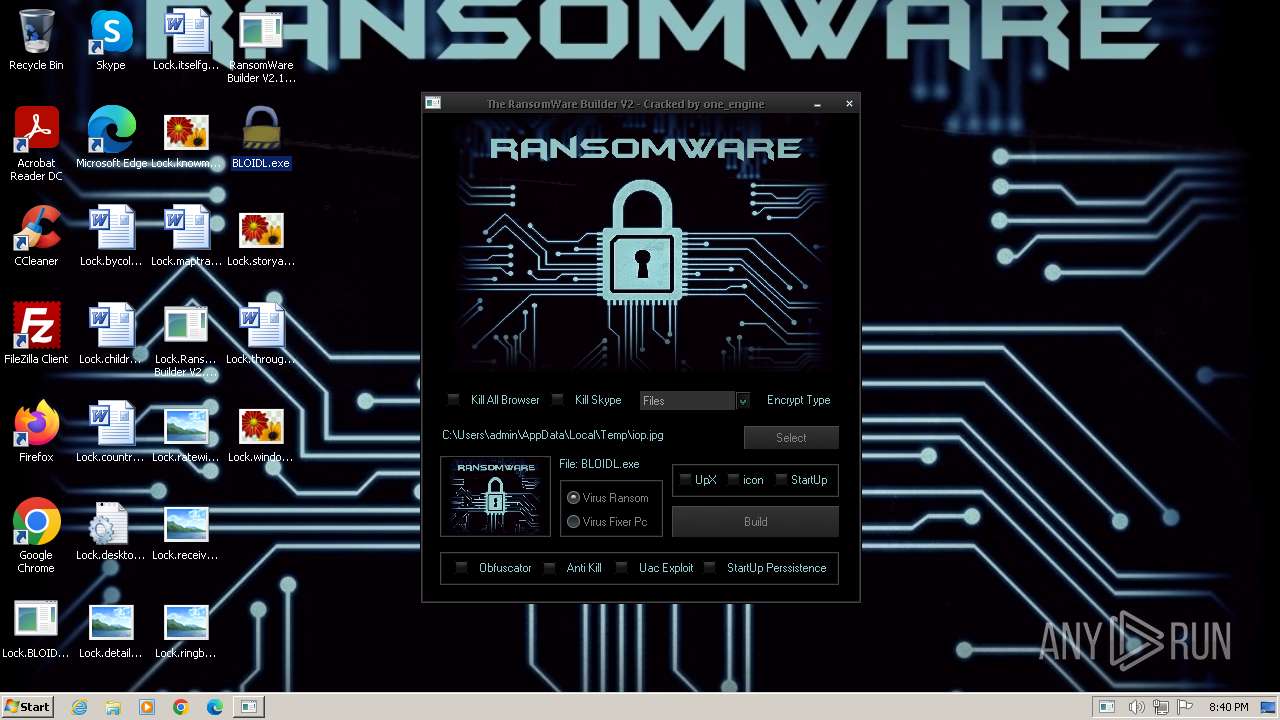
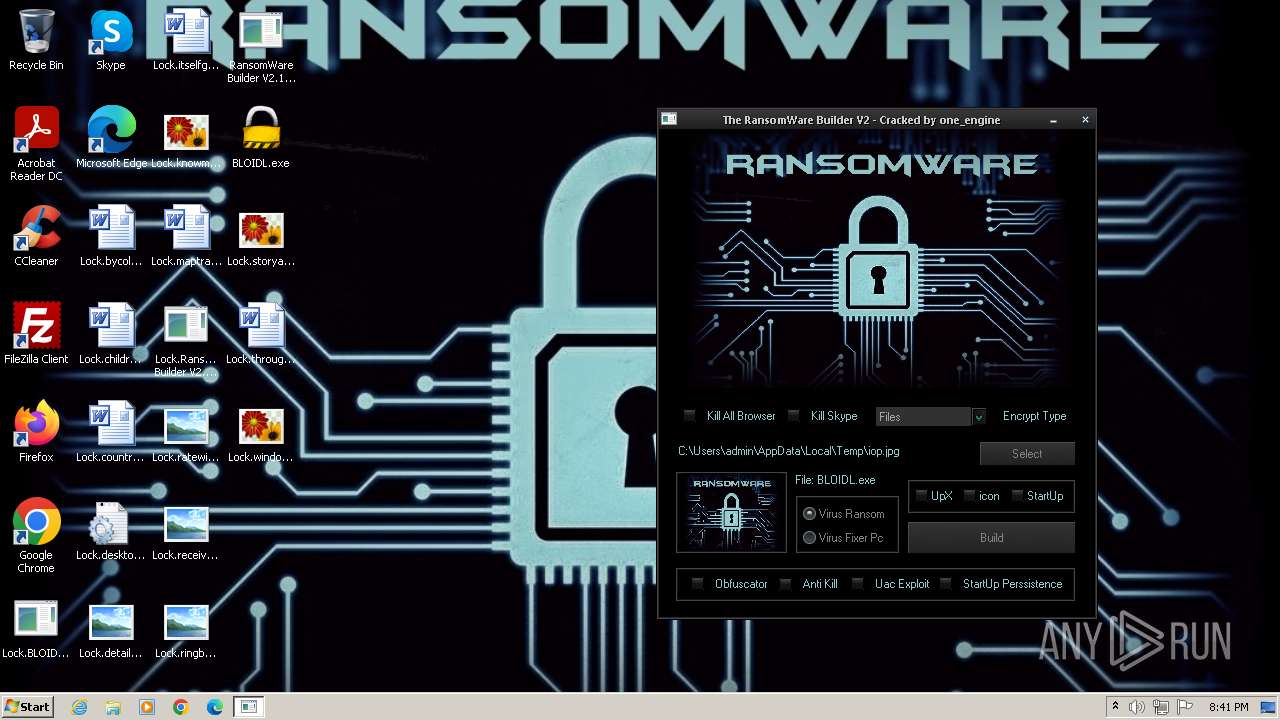
| File name: | RansomWare Builder V2.1_O - Cracked.exe |
| Full analysis: | https://app.any.run/tasks/edd46cf6-7dc0-4f9f-96c1-a0b9b9922704 |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2024, 20:40:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 43A2C7BA0ECD3A1B8FF0B82A0E82296D |
| SHA1: | 9B106AA440085D1CF76889A186A4C0ECE9F86B06 |
| SHA256: | BB623A98F1D61F13D2DE4DEE55B14F97956E8306AA66D945AAB0B00538B95900 |
| SSDEEP: | 98304:w8sjkaDkbFqE0DtuJFsEG/SxFEQGr7wgiMgaUP/XEXw5d1OFQg:yj3aqE0tubjTPgiFaUHEXgaFj |
MALICIOUS
Drops the executable file immediately after the start
- RansomWare Builder V2.1_O - Cracked.exe (PID: 984)
- Include.exe (PID: 1824)
- Aut2exe.exe (PID: 2880)
SUSPICIOUS
Reads the Internet Settings
- RansomWare Builder V2.1_O - Cracked.exe (PID: 984)
Executable content was dropped or overwritten
- RansomWare Builder V2.1_O - Cracked.exe (PID: 984)
- Include.exe (PID: 1824)
- Aut2exe.exe (PID: 2880)
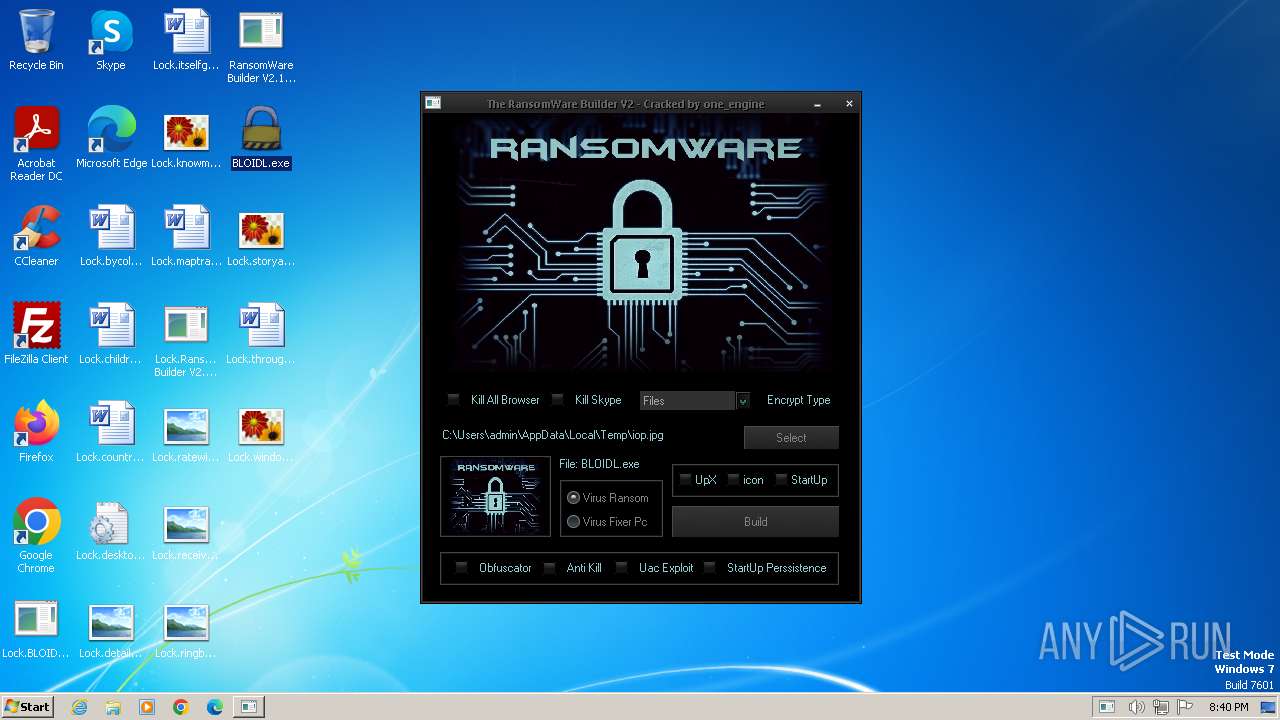
Changes the desktop background image
- BLOIDL.exe (PID: 3016)
Write to the desktop.ini file (may be used to cloak folders)
- BLOIDL.exe (PID: 3016)
INFO
Create files in a temporary directory
- RansomWare Builder V2.1_O - Cracked.exe (PID: 984)
- Include.exe (PID: 1824)
- Aut2exe.exe (PID: 2880)
- BLOIDL.exe (PID: 3016)
Checks supported languages
- RansomWare Builder V2.1_O - Cracked.exe (PID: 984)
- Include.exe (PID: 1824)
- Aut2exe.exe (PID: 2880)
- BLOIDL.exe (PID: 3016)
Reads mouse settings
- RansomWare Builder V2.1_O - Cracked.exe (PID: 984)
- BLOIDL.exe (PID: 3016)
Reads the computer name
- RansomWare Builder V2.1_O - Cracked.exe (PID: 984)
- Include.exe (PID: 1824)
- Aut2exe.exe (PID: 2880)
- BLOIDL.exe (PID: 3016)
Reads the machine GUID from the registry
- RansomWare Builder V2.1_O - Cracked.exe (PID: 984)
- BLOIDL.exe (PID: 3016)
Reads Microsoft Office registry keys
- RansomWare Builder V2.1_O - Cracked.exe (PID: 984)
Manual execution by a user
- BLOIDL.exe (PID: 3016)
Creates files or folders in the user directory
- BLOIDL.exe (PID: 3016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:02:21 13:51:45+01:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 581120 |
| InitializedDataSize: | 3921408 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x27f4a |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
Total processes
42
Monitored processes
4
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 984 | "C:\Users\admin\Desktop\RansomWare Builder V2.1_O - Cracked.exe" | C:\Users\admin\Desktop\RansomWare Builder V2.1_O - Cracked.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1824 | "C:\Users\admin\AppData\Local\Temp\Include.exe" | C:\Users\admin\AppData\Local\Temp\Include.exe | RansomWare Builder V2.1_O - Cracked.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2880 | C:\Users\admin\AppData\Local\Temp\Aut2exe.exe /in C:\Users\admin\AppData\Local\Temp/Serv.au3 /out C:\Users\admin\AppData\Local\Temp/BLOIDL.exe /icon C:\Users\admin\AppData\Local\Temp\8x1.ico /comp 2 /nopack /Unicode | C:\Users\admin\AppData\Local\Temp\Aut2exe.exe | RansomWare Builder V2.1_O - Cracked.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: Aut2Exe Exit code: 0 Version: 3, 3, 8, 1 Modules
| |||||||||||||||
| 3016 | "C:\Users\admin\Desktop\BLOIDL.exe" | C:\Users\admin\Desktop\BLOIDL.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 3, 3, 8, 1 Modules
| |||||||||||||||
Total events
3 896
Read events
3 678
Write events
217
Delete events
1
Modification events
| (PID) Process: | (984) RansomWare Builder V2.1_O - Cracked.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (984) RansomWare Builder V2.1_O - Cracked.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (984) RansomWare Builder V2.1_O - Cracked.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (984) RansomWare Builder V2.1_O - Cracked.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (984) RansomWare Builder V2.1_O - Cracked.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (984) RansomWare Builder V2.1_O - Cracked.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0100000006000000000000000B00000002000000070000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (984) RansomWare Builder V2.1_O - Cracked.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (984) RansomWare Builder V2.1_O - Cracked.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 070000000100000006000000000000000B000000020000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (984) RansomWare Builder V2.1_O - Cracked.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\82\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | Mode |
Value: 6 | |||
| (PID) Process: | (984) RansomWare Builder V2.1_O - Cracked.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\82\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | LogicalViewMode |
Value: 2 | |||
Executable files
14
Suspicious files
61
Text files
164
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 984 | RansomWare Builder V2.1_O - Cracked.exe | C:\Users\admin\AppData\Local\Temp\aut9AB8.tmp | binary | |
MD5:E35517D16231710681CDAFC2BE786479 | SHA256:29F30C79B076AA20775A35EB75F89339CEEF417F43D74B8AA1F66D052A31E96C | |||
| 984 | RansomWare Builder V2.1_O - Cracked.exe | C:\Users\admin\AppData\Local\Temp\aut9BD6.tmp | executable | |
MD5:9843D4CB1FF9E4B22053392784734539 | SHA256:3EB756620D1E11B28E4E86ABBFA977754A40610BA6B3EB020AB0411F54890F50 | |||
| 984 | RansomWare Builder V2.1_O - Cracked.exe | C:\Users\admin\AppData\Local\Temp\aut9AE8.tmp | image | |
MD5:19A588347DE928200A06957F290B1B69 | SHA256:D1E84A6B637BA81F38889A8FEEBC6EE6B6A656AEAD2B62B4853FF3A1917AB404 | |||
| 984 | RansomWare Builder V2.1_O - Cracked.exe | C:\Users\admin\AppData\Local\Temp\Aut2exe.exe | executable | |
MD5:33AEC29A31022484B53BA9EE6B10F5F6 | SHA256:DDEF833E1D31151235EB996BD33BC70E24B01B05386B3FD3FD4AC06F96C8BC7B | |||
| 984 | RansomWare Builder V2.1_O - Cracked.exe | C:\Users\admin\AppData\Local\Temp\iop.jpg | image | |
MD5:19A588347DE928200A06957F290B1B69 | SHA256:D1E84A6B637BA81F38889A8FEEBC6EE6B6A656AEAD2B62B4853FF3A1917AB404 | |||
| 984 | RansomWare Builder V2.1_O - Cracked.exe | C:\Users\admin\AppData\Local\Temp\AutoItSC.bin | executable | |
MD5:3EDCF50443AF194BF5131B0F35E3671D | SHA256:8378A324A838EF0AB3CEED73B8840D7B948C2607A35820A4D968894E1DFA2355 | |||
| 984 | RansomWare Builder V2.1_O - Cracked.exe | C:\Users\admin\AppData\Local\Temp\aut9B47.tmp | binary | |
MD5:B48C30193542846286C56629D412B852 | SHA256:9CC0AA4EFB10444FBAB2D74F8C54B6F5041C3691AA9702CB69F18E2F813E76C5 | |||
| 984 | RansomWare Builder V2.1_O - Cracked.exe | C:\Users\admin\AppData\Local\Temp\aut9BA6.tmp | executable | |
MD5:308F709A8F01371A6DD088A793E65A5F | SHA256:C0F9FAFFDF14AB2C853880457BE19A237B10F8986755F184ECFE21670076CB35 | |||
| 984 | RansomWare Builder V2.1_O - Cracked.exe | C:\Users\admin\AppData\Local\Temp\Include.exe | executable | |
MD5:9843D4CB1FF9E4B22053392784734539 | SHA256:3EB756620D1E11B28E4E86ABBFA977754A40610BA6B3EB020AB0411F54890F50 | |||
| 984 | RansomWare Builder V2.1_O - Cracked.exe | C:\Users\admin\AppData\Local\Temp\upx.exe | executable | |
MD5:308F709A8F01371A6DD088A793E65A5F | SHA256:C0F9FAFFDF14AB2C853880457BE19A237B10F8986755F184ECFE21670076CB35 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |