| File name: | bb4a41175e286cf4c48c519a0ad3add906300ba4726d7fed23e30b3a0934c14d |
| Full analysis: | https://app.any.run/tasks/230c577a-ae78-44f4-b8ee-9285bf13c37f |
| Verdict: | Malicious activity |
| Analysis date: | June 12, 2024, 20:45:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64, for MS Windows |
| MD5: | A0DB2AA180714362B1FED093CBE75BD1 |
| SHA1: | CE7B39E4B3282DF6A337E7163C99067CD44748E8 |
| SHA256: | BB4A41175E286CF4C48C519A0AD3ADD906300BA4726D7FED23E30B3A0934C14D |
| SSDEEP: | 98304:deQM6Xivj4haVAv+X1aOhHdit+FfYBgF6LBievaZSCvS7T4P2LBfeodd5uDwUZiw:cG2c |
MALICIOUS
Drops the executable file immediately after the start
- bb4a41175e286cf4c48c519a0ad3add906300ba4726d7fed23e30b3a0934c14d.exe (PID: 6428)
SUSPICIOUS
No suspicious indicators.INFO
Checks supported languages
- bb4a41175e286cf4c48c519a0ad3add906300ba4726d7fed23e30b3a0934c14d.exe (PID: 6428)
Reads the computer name
- bb4a41175e286cf4c48c519a0ad3add906300ba4726d7fed23e30b3a0934c14d.exe (PID: 6428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 3 |
| CodeSize: | 2704384 |
| InitializedDataSize: | 272896 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6d860 |
| OSVersion: | 6.1 |
| ImageVersion: | 1 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows command line |
Total processes
116
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6428 | "C:\Users\admin\Desktop\bb4a41175e286cf4c48c519a0ad3add906300ba4726d7fed23e30b3a0934c14d.exe" | C:\Users\admin\Desktop\bb4a41175e286cf4c48c519a0ad3add906300ba4726d7fed23e30b3a0934c14d.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6436 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | bb4a41175e286cf4c48c519a0ad3add906300ba4726d7fed23e30b3a0934c14d.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 897
Read events
1 651
Write events
246
Delete events
0
Modification events
| (PID) Process: | (6428) bb4a41175e286cf4c48c519a0ad3add906300ba4726d7fed23e30b3a0934c14d.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-462 |
Value: Afghanistan Standard Time | |||
| (PID) Process: | (6428) bb4a41175e286cf4c48c519a0ad3add906300ba4726d7fed23e30b3a0934c14d.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-461 |
Value: Afghanistan Daylight Time | |||
| (PID) Process: | (6428) bb4a41175e286cf4c48c519a0ad3add906300ba4726d7fed23e30b3a0934c14d.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-222 |
Value: Alaskan Standard Time | |||
| (PID) Process: | (6428) bb4a41175e286cf4c48c519a0ad3add906300ba4726d7fed23e30b3a0934c14d.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-221 |
Value: Alaskan Daylight Time | |||
| (PID) Process: | (6428) bb4a41175e286cf4c48c519a0ad3add906300ba4726d7fed23e30b3a0934c14d.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-2392 |
Value: Aleutian Standard Time | |||
| (PID) Process: | (6428) bb4a41175e286cf4c48c519a0ad3add906300ba4726d7fed23e30b3a0934c14d.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-2391 |
Value: Aleutian Daylight Time | |||
| (PID) Process: | (6428) bb4a41175e286cf4c48c519a0ad3add906300ba4726d7fed23e30b3a0934c14d.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-2162 |
Value: Altai Standard Time | |||
| (PID) Process: | (6428) bb4a41175e286cf4c48c519a0ad3add906300ba4726d7fed23e30b3a0934c14d.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-2161 |
Value: Altai Daylight Time | |||
| (PID) Process: | (6428) bb4a41175e286cf4c48c519a0ad3add906300ba4726d7fed23e30b3a0934c14d.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-392 |
Value: Arab Standard Time | |||
| (PID) Process: | (6428) bb4a41175e286cf4c48c519a0ad3add906300ba4726d7fed23e30b3a0934c14d.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-391 |
Value: Arab Daylight Time | |||
Executable files
0
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6428 | bb4a41175e286cf4c48c519a0ad3add906300ba4726d7fed23e30b3a0934c14d.exe | C:\Users\admin\Desktop\app.log | text | |
MD5:E6256D47A672F268DFF2C20267FAD019 | SHA256:E33F2B1BE4F93D612546790D70CD651949A459A934C5EEC98F2F1E4E3D57BB4A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
22
DNS requests
27
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5140 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5944 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1744 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1744 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5944 | RUXIMICS.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
— | — | POST | 200 | 20.42.73.26:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | — | 9 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1744 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5140 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1744 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
— | — | 239.255.255.250:1900 | — | — | — | unknown |
5944 | RUXIMICS.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
5140 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
5944 | RUXIMICS.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
5140 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
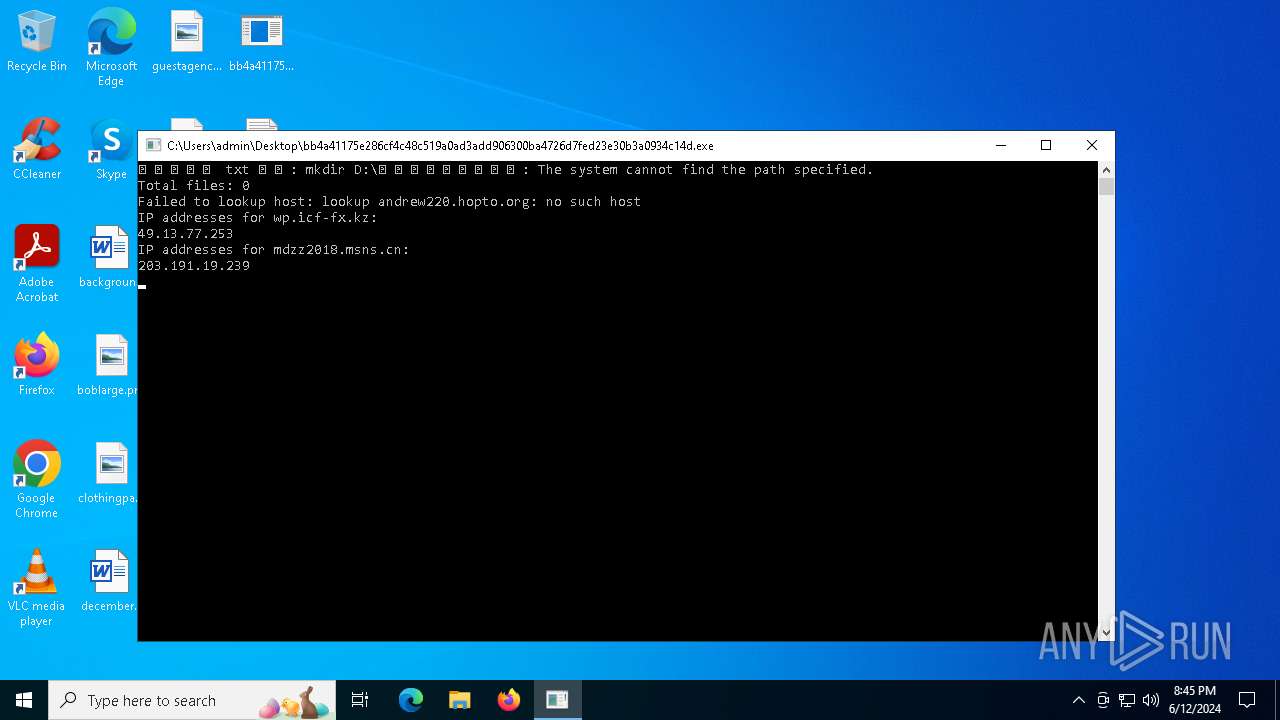
andrew220.hopto.org |
| unknown |
wp.icf-fx.kz |
| unknown |
mdzz2018.msns.cn |
| unknown |
mdzz2023.msns.cn |
| unknown |
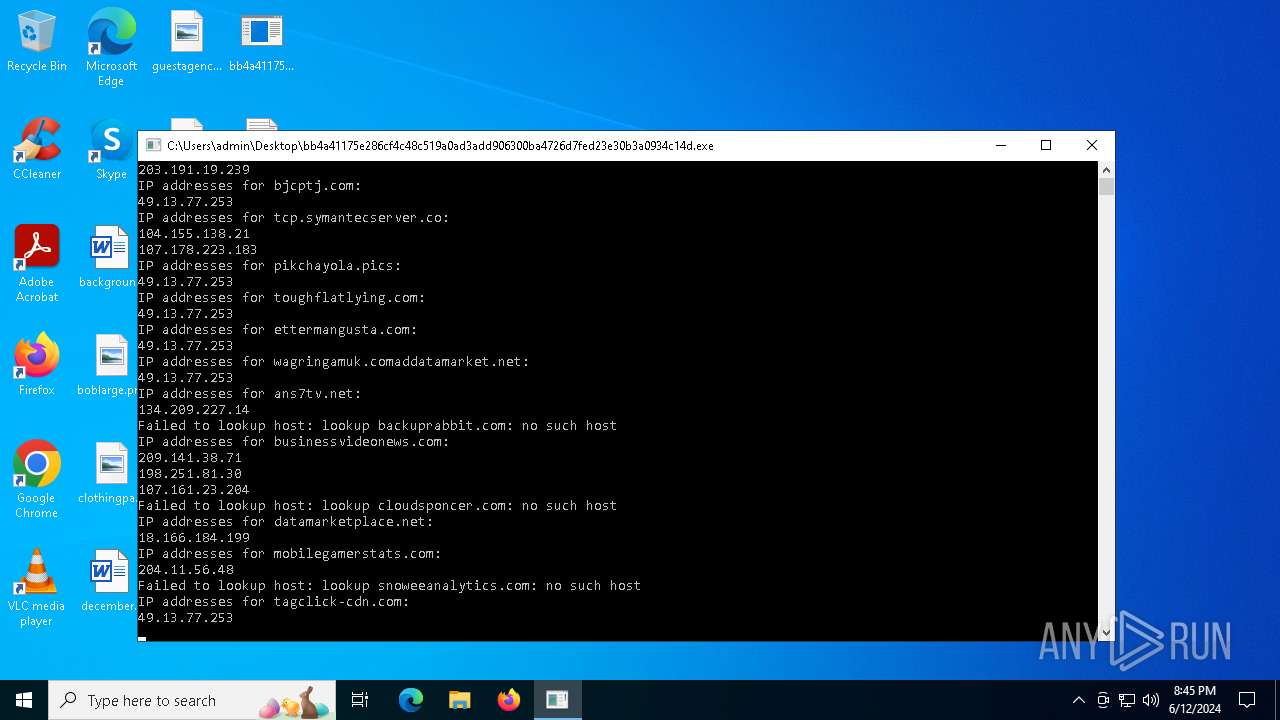
bjcptj.com |
| unknown |
tcp.symantecserver.co |
| malicious |
pikchayola.pics |
| unknown |
toughflatlying.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2184 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.hopto .org |
2184 | svchost.exe | Domain Observed Used for C2 Detected | ET MOBILE_MALWARE Trojan/iOS Operation Triangulation CnC Domain in DNS Lookup |
2184 | svchost.exe | Domain Observed Used for C2 Detected | ET MOBILE_MALWARE Trojan/iOS Operation Triangulation CnC Domain in DNS Lookup |
2184 | svchost.exe | Domain Observed Used for C2 Detected | ET MOBILE_MALWARE Trojan/iOS Operation Triangulation CnC Domain in DNS Lookup |
2184 | svchost.exe | Domain Observed Used for C2 Detected | ET MOBILE_MALWARE Trojan/iOS Operation Triangulation CnC Domain in DNS Lookup |
2184 | svchost.exe | Domain Observed Used for C2 Detected | ET MOBILE_MALWARE Trojan/iOS Operation Triangulation CnC Domain in DNS Lookup |
2184 | svchost.exe | Domain Observed Used for C2 Detected | ET MOBILE_MALWARE Trojan/iOS Operation Triangulation CnC Domain in DNS Lookup |
2184 | svchost.exe | Domain Observed Used for C2 Detected | ET MOBILE_MALWARE Trojan/iOS Operation Triangulation CnC Domain in DNS Lookup |
2184 | svchost.exe | Domain Observed Used for C2 Detected | ET MOBILE_MALWARE Trojan/iOS Operation Triangulation CnC Domain in DNS Lookup |
2184 | svchost.exe | Domain Observed Used for C2 Detected | ET MOBILE_MALWARE Trojan/iOS Operation Triangulation CnC Domain in DNS Lookup |