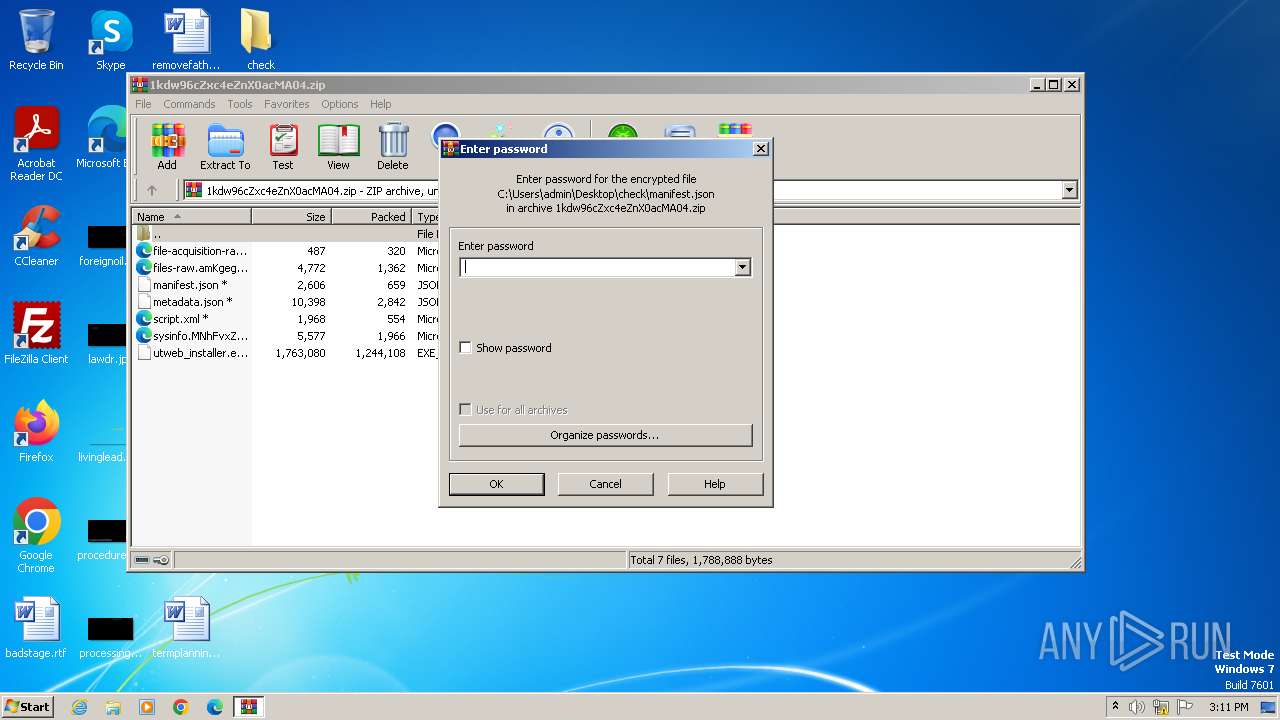
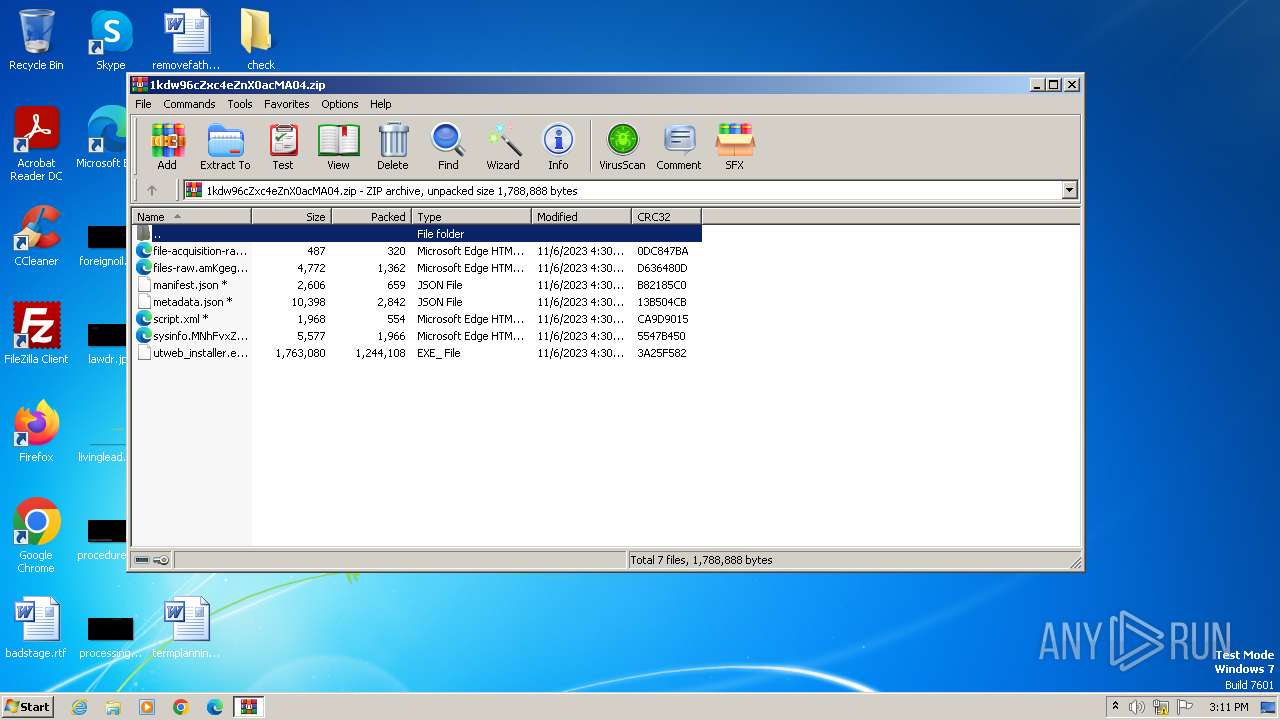
| File name: | 1kdw96cZxc4eZnX0acMA04.zip |
| Full analysis: | https://app.any.run/tasks/ff7f41e7-122f-4846-a49f-9a087561b679 |
| Verdict: | Malicious activity |
| Analysis date: | November 10, 2023, 15:11:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 63A19C8EF5107DC0B34EEBC8FA7912B8 |
| SHA1: | 067035F4B2E449FC44D96D1864A9EC02E77F361C |
| SHA256: | BB09F073FBAFA23224DB87C8087CB2DFC7E4569217E13198CF679880CF483CBE |
| SSDEEP: | 49152:wCNVd9XpGvVxqkYs3yQTQ30OHWd3itWFSAORC0L7QJVrpOEHBk2vSAFQDnWTXLo+:wCnd3G9IkYxQUXHWd3QO9p3a2vSAyDnO |
MALICIOUS
Drops the executable file immediately after the start
- utweb_installer.exe (PID: 3904)
- utweb_installer.tmp (PID: 3916)
- utweb_installer.exe (PID: 3676)
- utweb_installer.exe (PID: 3380)
- utweb.exe (PID: 1924)
SUSPICIOUS
Reads the Windows owner or organization settings
- utweb_installer.tmp (PID: 3916)
Reads settings of System Certificates
- utweb_installer.tmp (PID: 3916)
- utweb.exe (PID: 1924)
- helper.exe (PID: 2468)
Reads the Internet Settings
- utweb_installer.tmp (PID: 3916)
- utweb_installer.exe (PID: 3676)
- utweb.exe (PID: 1924)
- saBSI.exe (PID: 1816)
The process creates files with name similar to system file names
- utweb_installer.exe (PID: 3676)
Malware-specific behavior (creating "System.dll" in Temp)
- utweb_installer.exe (PID: 3676)
Process drops legitimate windows executable
- utweb_installer.exe (PID: 3676)
Reads security settings of Internet Explorer
- saBSI.exe (PID: 1816)
- utweb.exe (PID: 1924)
Checks Windows Trust Settings
- saBSI.exe (PID: 1816)
- utweb.exe (PID: 1924)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3448)
Checks supported languages
- utweb_installer.exe (PID: 3904)
- utweb_installer.tmp (PID: 3916)
- wmpnscfg.exe (PID: 4016)
- saBSI.exe (PID: 1816)
- utweb_installer.exe (PID: 3676)
- utweb.exe (PID: 1924)
- utweb_installer.exe (PID: 3380)
- utweb_installer.tmp (PID: 3632)
- helper.exe (PID: 2468)
Create files in a temporary directory
- utweb_installer.exe (PID: 3904)
- utweb_installer.tmp (PID: 3916)
- utweb_installer.exe (PID: 3676)
- utweb_installer.exe (PID: 3380)
Reads the computer name
- utweb_installer.tmp (PID: 3916)
- wmpnscfg.exe (PID: 4016)
- utweb_installer.exe (PID: 3676)
- saBSI.exe (PID: 1816)
- utweb.exe (PID: 1924)
- utweb_installer.tmp (PID: 3632)
- helper.exe (PID: 2468)
Reads the machine GUID from the registry
- utweb_installer.tmp (PID: 3916)
- wmpnscfg.exe (PID: 4016)
- utweb_installer.exe (PID: 3676)
- saBSI.exe (PID: 1816)
- utweb.exe (PID: 1924)
Manual execution by a user
- wmpnscfg.exe (PID: 4016)
- utweb_installer.exe (PID: 3380)
Creates files or folders in the user directory
- utweb_installer.exe (PID: 3676)
- utweb.exe (PID: 1924)
- helper.exe (PID: 2468)
Checks proxy server information
- utweb_installer.exe (PID: 3676)
Creates files in the program directory
- saBSI.exe (PID: 1816)
Application launched itself
- msedge.exe (PID: 2332)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:11:06 09:30:50 |
| ZipCRC: | 0xb82185c0 |
| ZipCompressedSize: | 659 |
| ZipUncompressedSize: | 2606 |
| ZipFileName: | manifest.json |
Total processes
79
Monitored processes
33
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2308 --field-trial-handle=1332,i,15065077765946580247,790556663258160269,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1088 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1388 --field-trial-handle=1332,i,15065077765946580247,790556663258160269,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1616 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4520 --field-trial-handle=1332,i,15065077765946580247,790556663258160269,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
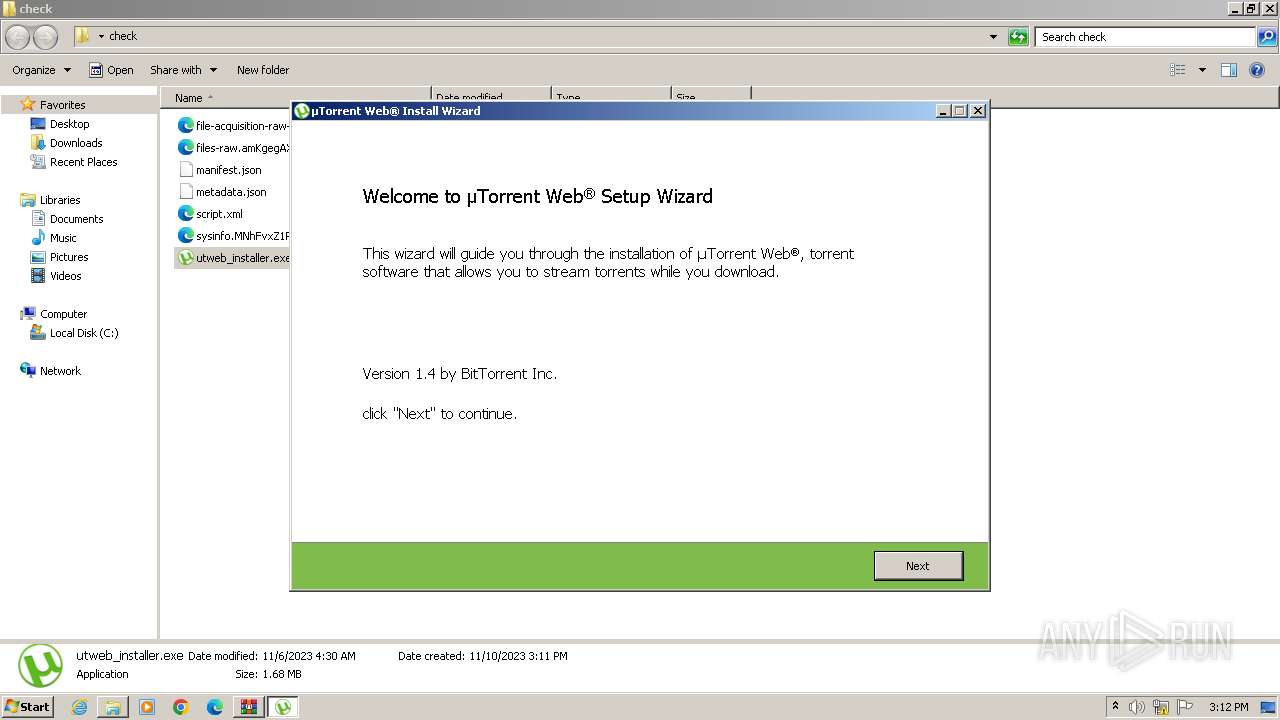
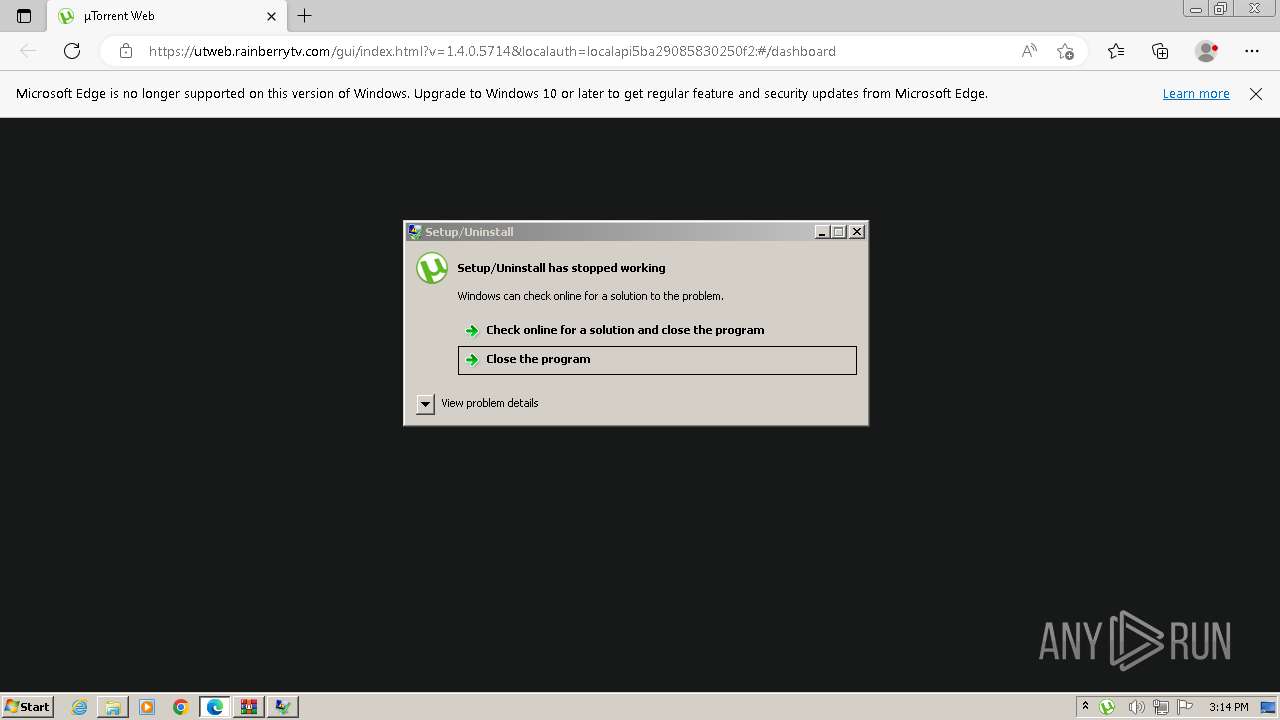
| 1816 | "C:\Users\admin\AppData\Local\Temp\is-5BN9E.tmp\component0_extract\saBSI.exe" /affid 91082 PaidDistribution=true CountryCode=DE | C:\Users\admin\AppData\Local\Temp\is-5BN9E.tmp\component0_extract\saBSI.exe | utweb_installer.tmp | ||||||||||||
User: admin Company: McAfee, LLC Integrity Level: HIGH Description: McAfee WebAdvisor(bootstrap installer) Exit code: 4294967295 Version: 4,1,1,818 Modules
| |||||||||||||||
| 1848 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1216 --field-trial-handle=1332,i,15065077765946580247,790556663258160269,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1924 | "C:\Users\admin\AppData\Roaming\uTorrent Web\utweb.exe" /RUNONSTARTUP | C:\Users\admin\AppData\Roaming\uTorrent Web\utweb.exe | utweb_installer.tmp | ||||||||||||
User: admin Company: Rainberry Inc. Integrity Level: MEDIUM Description: µTorrent Web Exit code: 0 Version: 1.4.0.5714 Modules
| |||||||||||||||
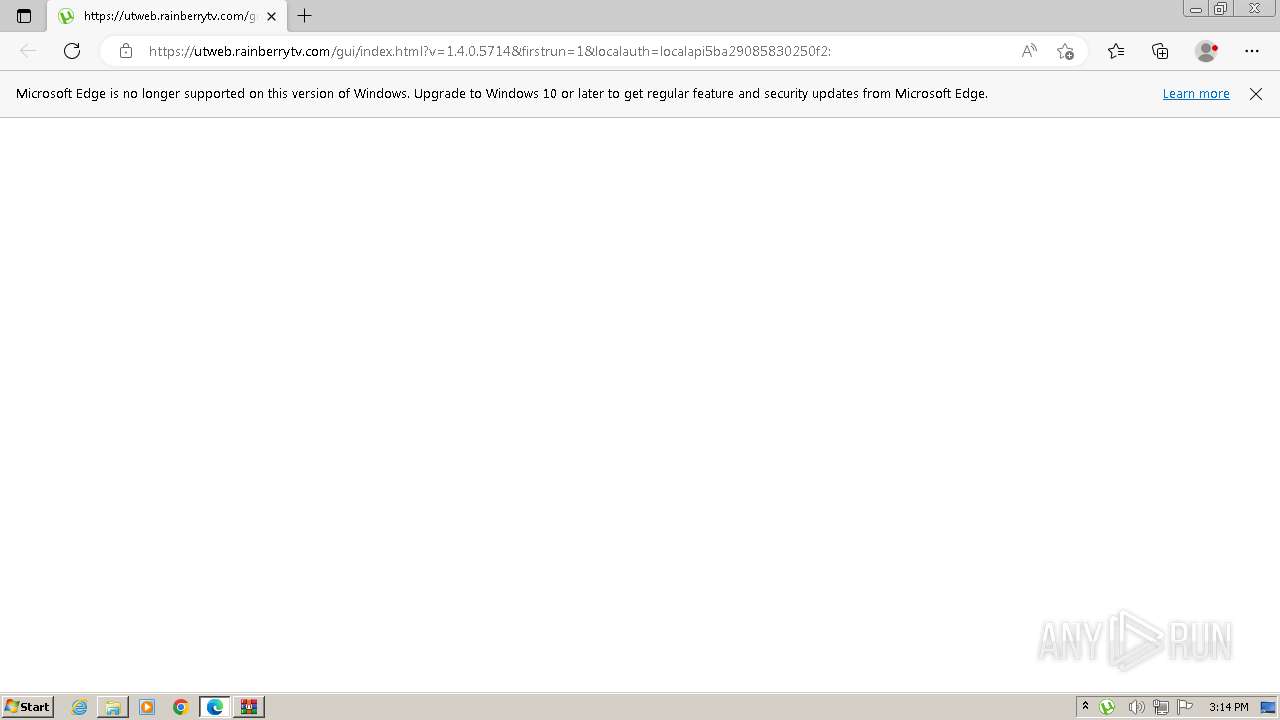
| 2332 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument https://utweb.rainberrytv.com/gui/index.html?v=1.4.0.5714&firstrun=1&localauth=localapi5ba29085830250f2: | C:\Program Files\Microsoft\Edge\Application\msedge.exe | utweb.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2436 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=4032 --field-trial-handle=1332,i,15065077765946580247,790556663258160269,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2452 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3960 --field-trial-handle=1332,i,15065077765946580247,790556663258160269,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2468 | helper/helper.exe 49238 -- ut_web/1.4.0.5714 hval/a69629c6db7fee11a82612a9866c77de | C:\Users\admin\AppData\Roaming\uTorrent Web\helper\helper.exe | utweb.exe | ||||||||||||
User: admin Company: BitTorrent Inc. Integrity Level: MEDIUM Description: µTorrent Helper Exit code: 0 Version: 2.1.6.2679 Modules
| |||||||||||||||
Total events
18 111
Read events
17 995
Write events
105
Delete events
11
Modification events
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 01000000020000000700000000000000060000000C0000000B0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
Executable files
34
Suspicious files
297
Text files
70
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3448 | WinRAR.exe | C:\Users\admin\Desktop\check\manifest.json | binary | |
MD5:ED188E2DC424A00333ED7F5E5E78ABED | SHA256:AB6026278C2674DFC94F91B6F7159CAF9BC018FC505398C8BC6F344C42DEB890 | |||
| 3448 | WinRAR.exe | C:\Users\admin\Desktop\check\script.xml | xml | |
MD5:7B14B831A2F439594EE1B6080D2D8C8A | SHA256:3C742A2AEAE376F0C936618F69EE742C3DE3851D5E7F04BEBA048017FBB87EE7 | |||
| 3904 | utweb_installer.exe | C:\Users\admin\AppData\Local\Temp\is-GGV4Q.tmp\utweb_installer.tmp | executable | |
MD5:EBFFAE50091E056D1A42A81360B41686 | SHA256:B87034BC14479A7A77A1E970215942F41FDF265E6BE6235F7A8DE637B0B6AFA1 | |||
| 3916 | utweb_installer.tmp | C:\Users\admin\AppData\Local\Temp\is-5BN9E.tmp\license.rtf | text | |
MD5:CA9C80605FF244AE36C584FFFFA09435 | SHA256:81C21179CB42FA44D8B7AA07925081B899F0EF5F18AC00FFB75B303309078634 | |||
| 3380 | utweb_installer.exe | C:\Users\admin\AppData\Local\Temp\is-UJF0R.tmp\utweb_installer.tmp | executable | |
MD5:EBFFAE50091E056D1A42A81360B41686 | SHA256:B87034BC14479A7A77A1E970215942F41FDF265E6BE6235F7A8DE637B0B6AFA1 | |||
| 3916 | utweb_installer.tmp | C:\Users\admin\AppData\Local\Temp\is-5BN9E.tmp\is-D6A23.tmp | compressed | |
MD5:CD9C77BC5840AF008799985F397FE1C3 | SHA256:26D7704B540DF18E2BCCD224DF677061FFB9F03CAB5B3C191055A84BF43A9085 | |||
| 3676 | utweb_installer.exe | C:\Users\admin\AppData\Local\Temp\nslC1F4.tmp\UAC.dll | executable | |
MD5:ADB29E6B186DAA765DC750128649B63D | SHA256:2F7F8FC05DC4FD0D5CDA501B47E4433357E887BBFED7292C028D99C73B52DC08 | |||
| 3676 | utweb_installer.exe | C:\Users\admin\AppData\Local\Temp\nslC1F4.tmp\System.dll | executable | |
MD5:CFF85C549D536F651D4FB8387F1976F2 | SHA256:8DC562CDA7217A3A52DB898243DE3E2ED68B80E62DDCB8619545ED0B4E7F65A8 | |||
| 3448 | WinRAR.exe | C:\Users\admin\Desktop\check\utweb_installer.exe_ | executable | |
MD5:3225E1398A194E5EB1B637A7C1D09973 | SHA256:DFB866E36A40B7D6C97C28C680D209CB6F1FE9384882FAA08DA79D3669BF0A6A | |||
| 3448 | WinRAR.exe | C:\Users\admin\Desktop\check\files-raw.amKgegAXa58bgp5VmMqOxX.xml | xml | |
MD5:23B2B89D207BB927685B81300607B603 | SHA256:D34F1D85DDC2BA2141F5452A466886DD258922987AEFD65ACAA37B43FAE53BC5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
311
DNS requests
155
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1924 | utweb.exe | GET | — | 178.79.242.16:80 | http://btinstall-artifacts.bittorrent.com/helper_ui/helper_web_ui.btinstall | unknown | — | — | unknown |
2468 | helper.exe | POST | 200 | 52.22.217.101:80 | http://i-5600.b-2679.helper.bench.utorrent.com/e.php?i=5600 | unknown | binary | 21 b | unknown |
2468 | helper.exe | POST | 200 | 52.22.217.101:80 | http://i-5600.b-2679.helper.bench.utorrent.com/e.php?i=5600 | unknown | binary | 21 b | unknown |
1924 | utweb.exe | POST | 200 | 52.202.150.110:80 | http://i-4103.b-5714.utw.bench.utorrent.com/e?i=4103 | unknown | binary | 21 b | unknown |
3676 | utweb_installer.exe | POST | 200 | 52.45.10.136:80 | http://i-4101.b-5714.utweb.bench.utorrent.com/e?i=4101 | unknown | binary | 21 b | unknown |
2468 | helper.exe | POST | 200 | 52.22.217.101:80 | http://i-5600.b-2679.helper.bench.utorrent.com/e.php?i=5600 | unknown | binary | 21 b | unknown |
2468 | helper.exe | POST | 200 | 52.22.217.101:80 | http://i-5600.b-2679.helper.bench.utorrent.com/e.php?i=5600 | unknown | binary | 21 b | unknown |
2468 | helper.exe | POST | 200 | 52.22.217.101:80 | http://i-5600.b-2679.helper.bench.utorrent.com/e.php?i=5600 | unknown | binary | 21 b | unknown |
2468 | helper.exe | POST | 200 | 52.22.217.101:80 | http://i-5600.b-2679.helper.bench.utorrent.com/e.php?i=5600 | unknown | binary | 21 b | unknown |
1924 | utweb.exe | POST | 200 | 52.0.45.244:80 | http://i-4101.b-10541.utweb_ui.bench.utorrent.com/e?i=4101&e=eyJhY3Rpb24iOiJ2MS4xMDU0MS5kZS51c2VyLnBsYWNlaG9sZGVyLjE2OTk2MjkyNDQ5MjgucGxhY2Vob2xkZXIiLCJhcHBOYW1lIjoidXR3ZWIiLCJhcHBWZXJzaW9uIjoiMS40LjAuNTcxNC4xMDU0MSIsImlzVXR3ZWIiOnRydWUsInR1dG9yaWFsVmlkZW9IYXNoTGlzdCI6WyI4MGIzOWEyZTM3YWEzNTJjZDJmY2JmYmVmN2M0YTZlOWU4Y2ZlNDM4IiwiOWEyM2JlNmM1NWQ1ZjhkMWUyODI2MGU0MDNiYWU1NDEyNDQzNTc5ZSIsIjM4ZTk3MjM0ZmQ2MGM0ZjMwMzQ0ZDlmYWU4MDg5OWE3NWZjZmJmZmUiLCI2MWIzYjg4NTZjNDgzOWVkZjUxZjVjMjM0NjU5OWI2YmVjNTI0MTQ1IiwiNTYyZTI5Yzc4MzZkYWRiY2Y1NWIzZGViZjgzMDYzMjcxNzY5Yzk0ZiJdLCJ1dWlkIjoiYTY5NjI5YzZkYjdmZWUxMWE4MjYxMmE5ODY2Yzc3ZGUiLCJiZW5jaEdlbyI6ImRlIiwidXR3ZWJTYW1wbGVSYXRlIjoxLCJnYUJsb2NrZXJEZXRlY3RlZCI6bnVsbCwibmFtZSI6InQwIiwidHJhY2tpbmdJZCI6IlVBLTg4Njk4MTAyLTEwIiwiY29va2llTmFtZSI6Il9nYSIsImNvb2tpZURvbWFpbiI6InJhaW5iZXJyeXR2LmNvbSIsImNvb2tpZVBhdGgiOiIvIiwiY29va2llRXhwaXJlcyI6NjMwNzIwMDAsImxlZ2FjeUhpc3RvcnlJbXBvcnQiOnRydWUsImFsbG93TGlua2VyIjpmYWxzZSwiYWxsb3dBbmNob3IiOnRydWUsInNhbXBsZVJhdGUiOjEwMCwic2l0ZVNwZWVkU2FtcGxlUmF0ZSI6MSwiYWx3YXlzU2VuZFJlZmVycmVyIjpmYWxzZSwic3RvcmFnZSI6ImNvb2tpZSIsIl9nZSI6dHJ1ZSwiYXBpVmVyc2lvbiI6MSwiY2xpZW50VmVyc2lvbiI6Imo1NiIsIl9nY24iOiJfZ2lkIiwiY2xpZW50SWQiOiIxMTk2Mjk1NDI2LjE2OTk2MjkyNDciLCJfZ2lkIjoiMTA2OTc4MjkxLjE2OTk2MjkyNDciLCJsb2NhdGlvbiI6Imh0dHBzOi8vdXR3ZWIucmFpbmJlcnJ5dHYuY29tL2d1aS9pbmRleC5odG1sP3Y9MS40LjAuNTcxNCIsInNjcmVlblJlc29sdXRpb24iOiIxMjgweDcyMCIsInNjcmVlbkNvbG9ycyI6IjI0LWJpdCIsInZpZXdwb3J0U2l6ZSI6IjEyODB4NTc0IiwiZW5jb2RpbmciOiJVVEYtOCIsImphdmFFbmFibGVkIjpmYWxzZSwibGFuZ3VhZ2UiOiJlbi11cyIsImFkU2Vuc2VJZCI6ODgzNzMzNzM5LCJkaW1lbnNpb24xIjoiMTE5NjI5NTQyNi4xNjk5NjI5MjQ3IiwiZGltZW5zaW9uNiI6MSwidGl0bGUiOiLOvFRvcnJlbnQgV2ViIiwic2NyZWVuTmFtZSI6ImRhc2hib2FyZCIsInBhZ2UiOiIvZGFzaGJvYXJkIiwiZGltZW5zaW9uMiI6MTY5OTYyOTI0NjYxMiwiZGltZW5zaW9uMyI6MCwiZGltZW5zaW9uNyI6ImE2OTYyOWM2ZGI3ZmVlMTFhODI2MTJhOTg2NmM3N2RlIiwiaGl0VHlwZSI6ImV2ZW50IiwiX3RpIjoxNjk5NjI5MjQ3NDQ0LCJfdG8iOjE4LCJfaGMiOjIsIl9qMSI6IiIsIl9qMiI6IiIsIl9zIjoyLCJldmVudENhdGVnb3J5IjoidXNlciIsImV2ZW50QWN0aW9uIjoiZmlyc3RfcnVuIiwiZXZlbnRMYWJlbCI6MTY5OTYyOTI0NDkyOCwiZXZlbnROYW1lIjoidXR3ZWJfdWkiLCJCVUlMRF9OVU1CRVIiOiIxMDU0MSJ9 | unknown | binary | 21 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
868 | svchost.exe | 95.101.148.135:80 | — | Akamai International B.V. | NL | unknown |
868 | svchost.exe | 23.218.208.137:80 | armmf.adobe.com | AKAMAI-AS | DE | unknown |
3916 | utweb_installer.tmp | 65.9.94.46:443 | d3du9emkqnnqkp.cloudfront.net | AMAZON-02 | US | unknown |
3916 | utweb_installer.tmp | 65.9.94.17:443 | dcnlefgcjiudc.cloudfront.net | AMAZON-02 | US | unknown |
3916 | utweb_installer.tmp | 65.9.94.167:443 | d27wm444oowmat.cloudfront.net | AMAZON-02 | US | unknown |
3916 | utweb_installer.tmp | 67.215.238.66:443 | download-lb.utorrent.com | ASN-QUADRANET-GLOBAL | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
armmf.adobe.com |
| whitelisted |
d3du9emkqnnqkp.cloudfront.net |
| unknown |
dcnlefgcjiudc.cloudfront.net |
| unknown |
d27wm444oowmat.cloudfront.net |
| unknown |
download-lb.utorrent.com |
| whitelisted |
i-4101.b-5714.utweb.bench.utorrent.com |
| unknown |
analytics.apis.mcafee.com |
| unknown |
sadownload.mcafee.com |
| whitelisted |
dht.libtorrent.org |
| unknown |
router.bittorrent.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3676 | utweb_installer.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
3676 | utweb_installer.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
1924 | utweb.exe | Potential Corporate Privacy Violation | ET P2P BitTorrent DHT ping request |
1924 | utweb.exe | Potentially Bad Traffic | ET POLICY Executable served from Amazon S3 |
1924 | utweb.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1088 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Global content delivery network (unpkg .com) |
Process | Message |
|---|---|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\is-5BN9E.tmp\component0_extract\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\is-5BN9E.tmp\component0_extract\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\is-5BN9E.tmp\component0_extract\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\is-5BN9E.tmp\component0_extract\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\is-5BN9E.tmp\component0_extract\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\is-5BN9E.tmp\component0_extract\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\is-5BN9E.tmp\component0_extract\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\is-5BN9E.tmp\component0_extract\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|