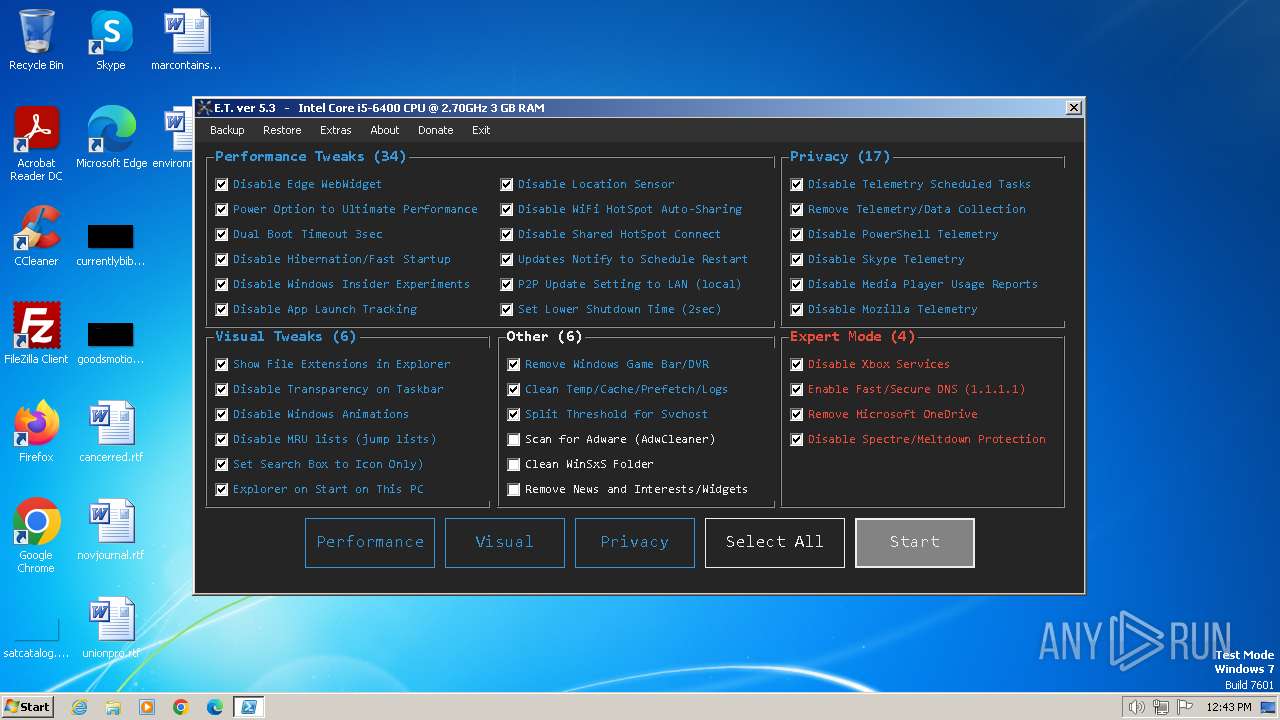
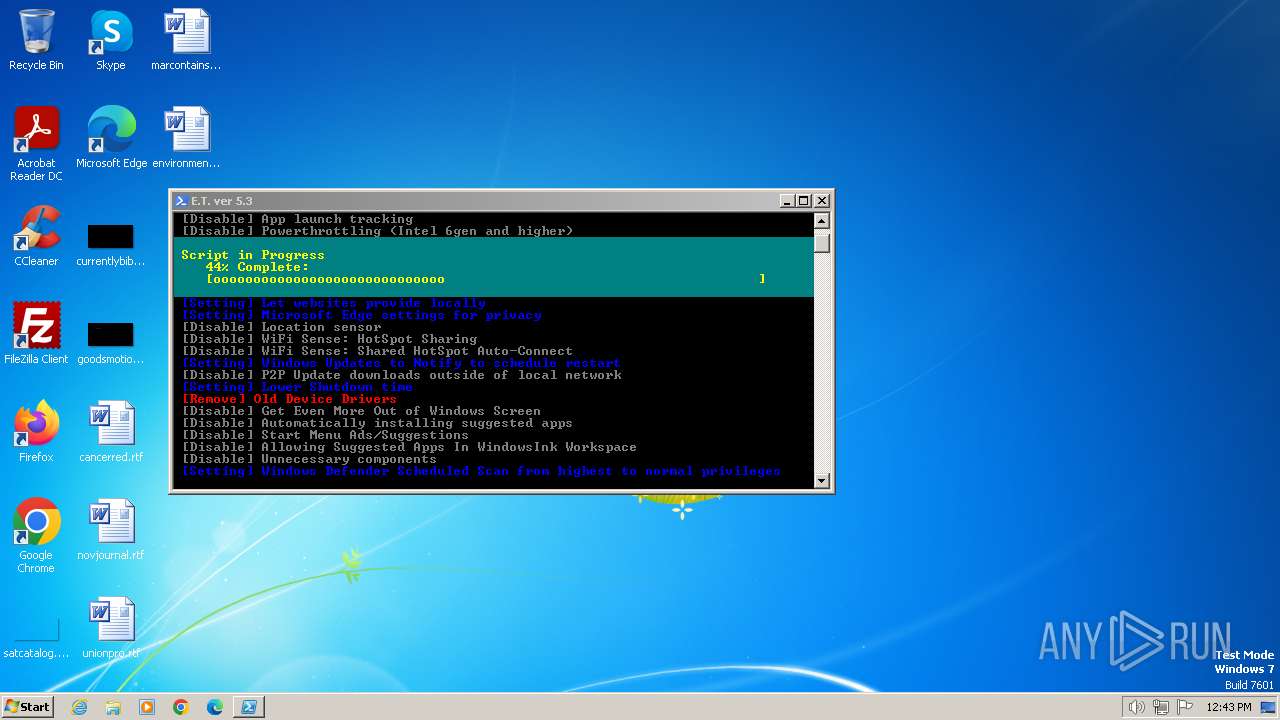
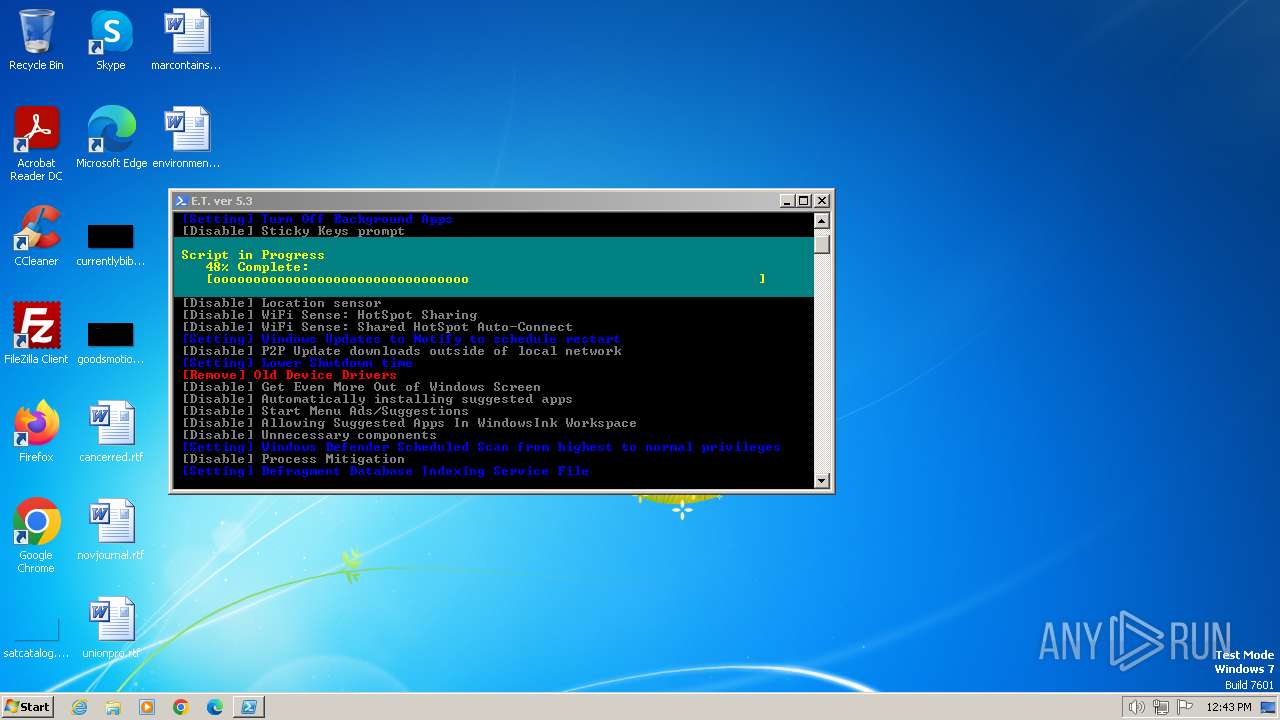
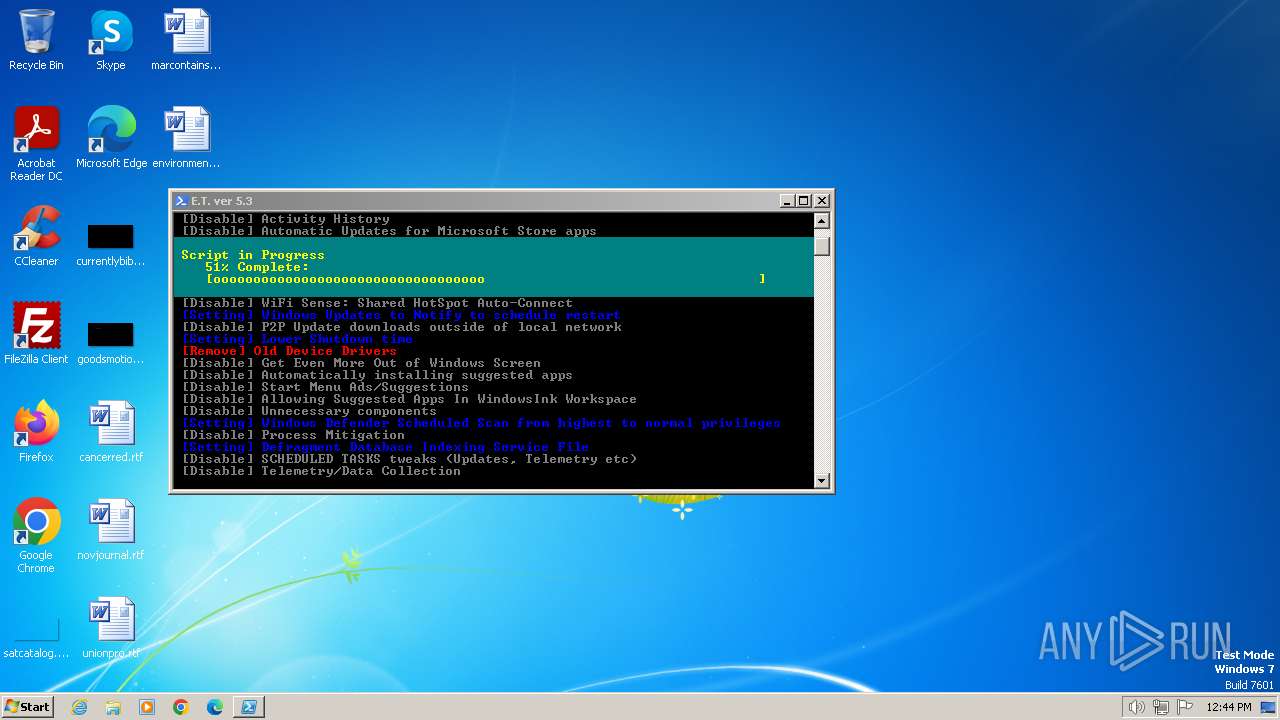
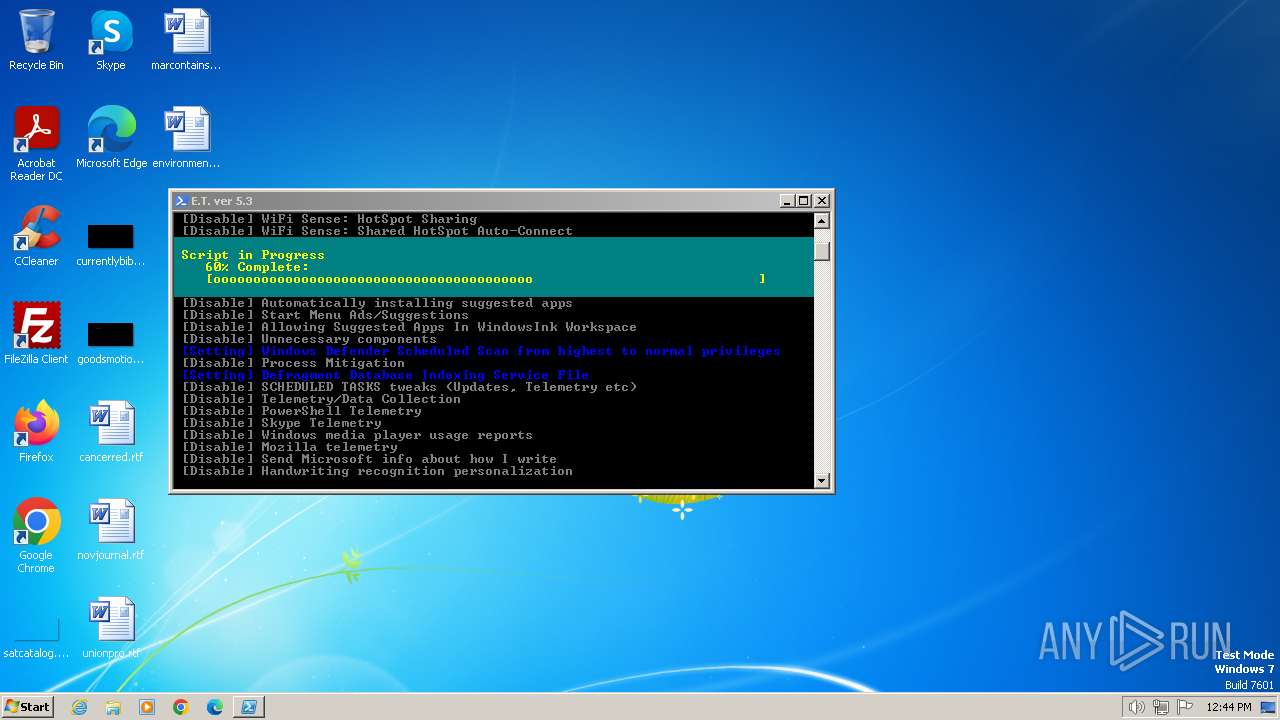
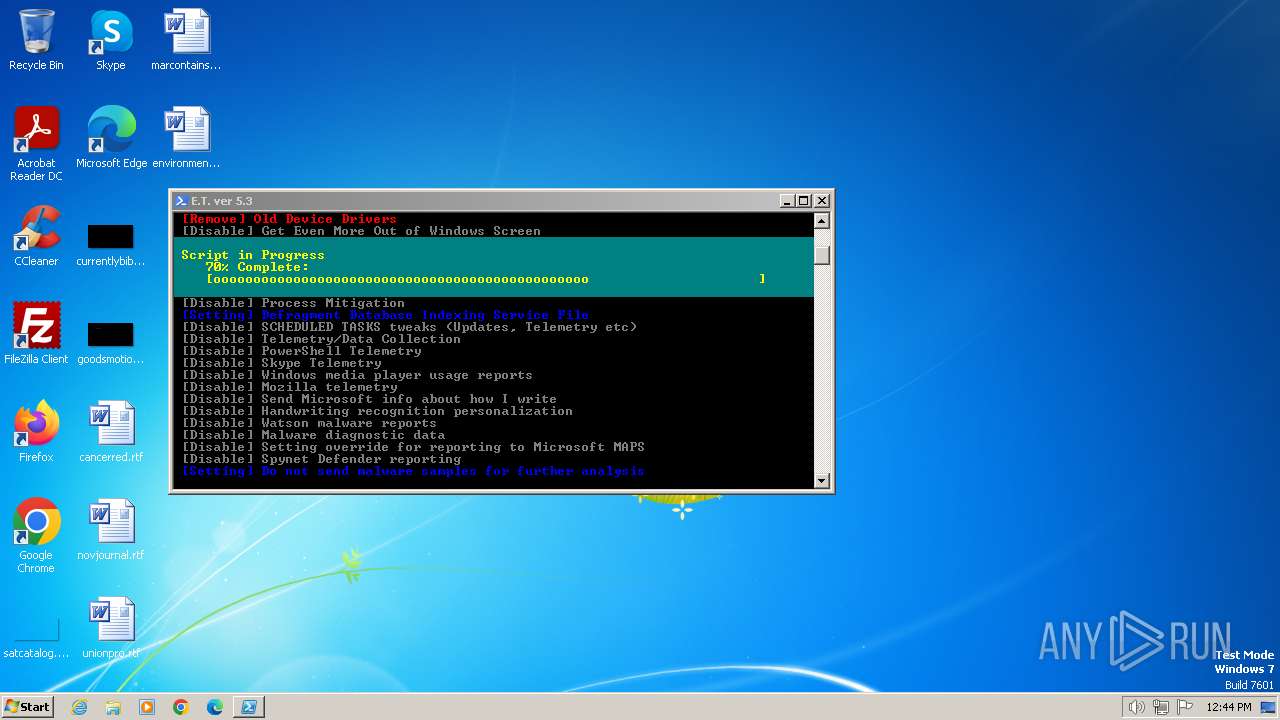
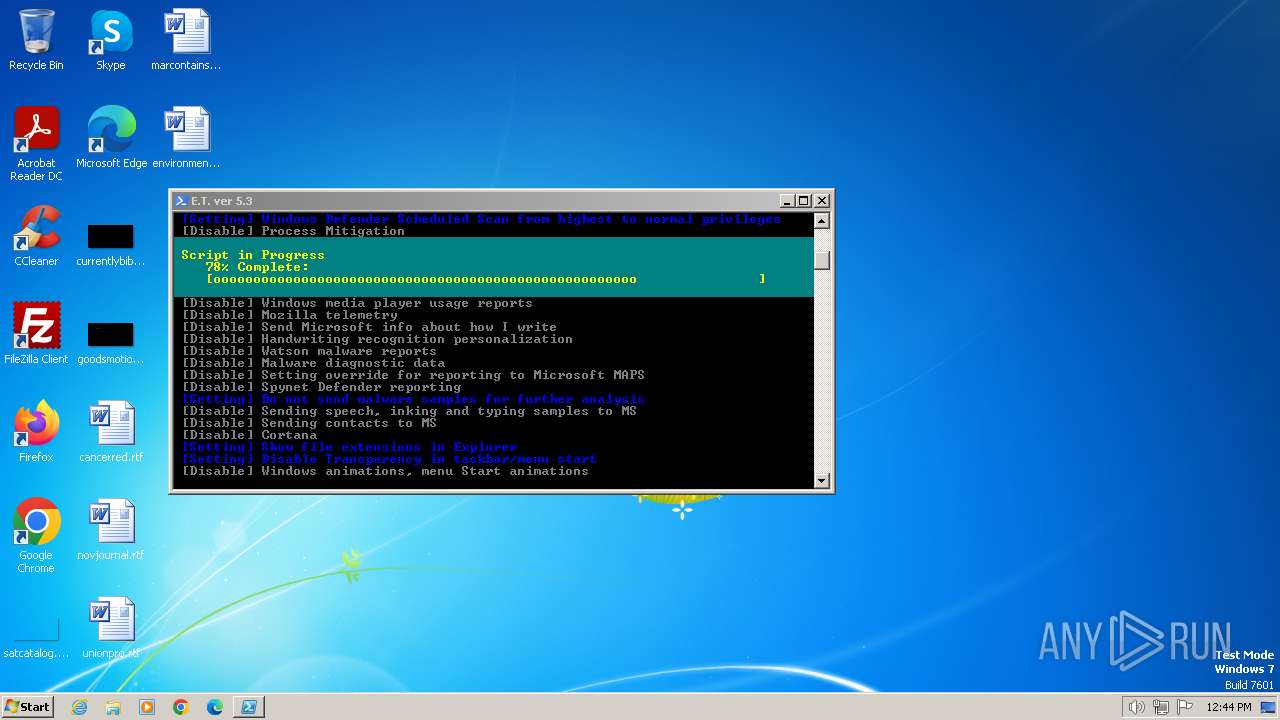
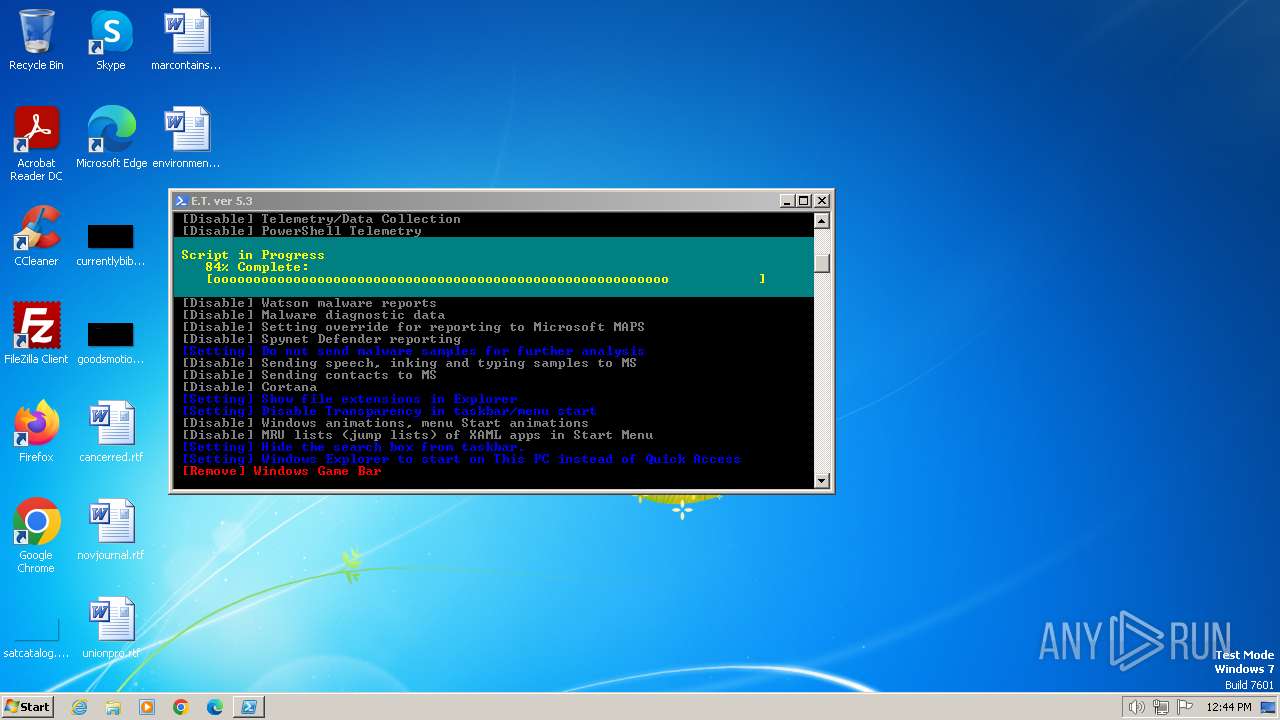
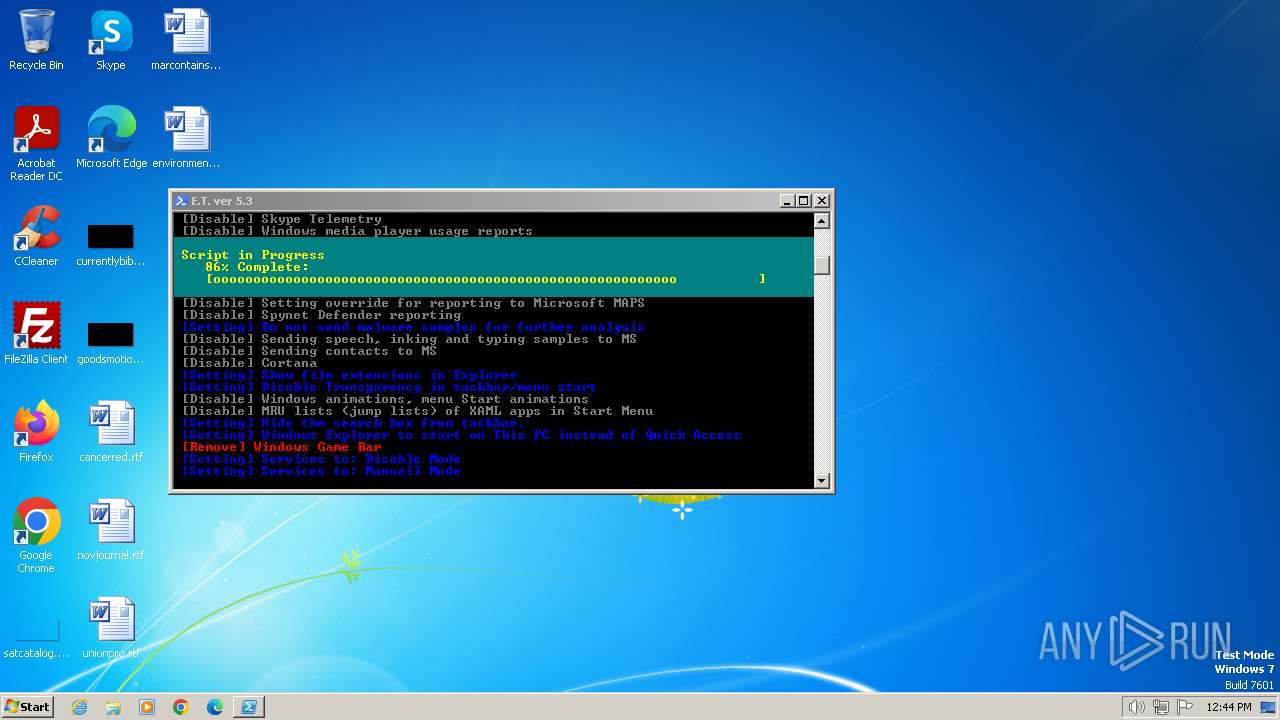
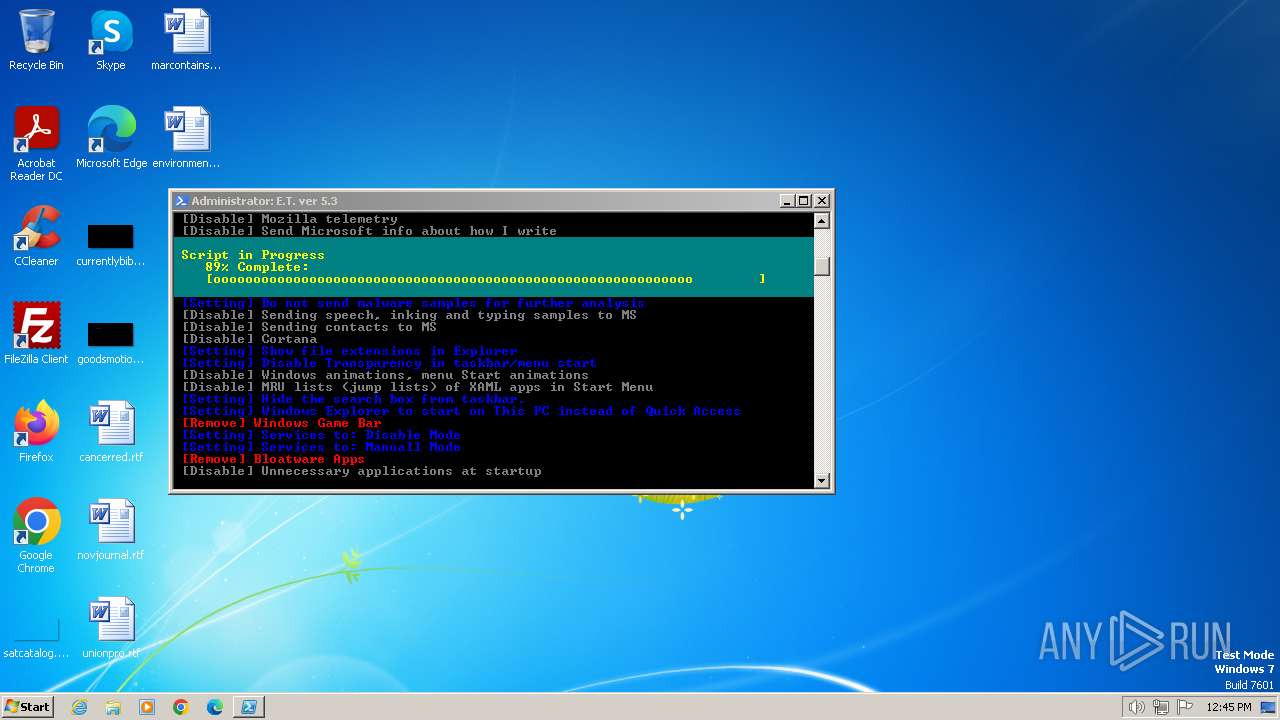
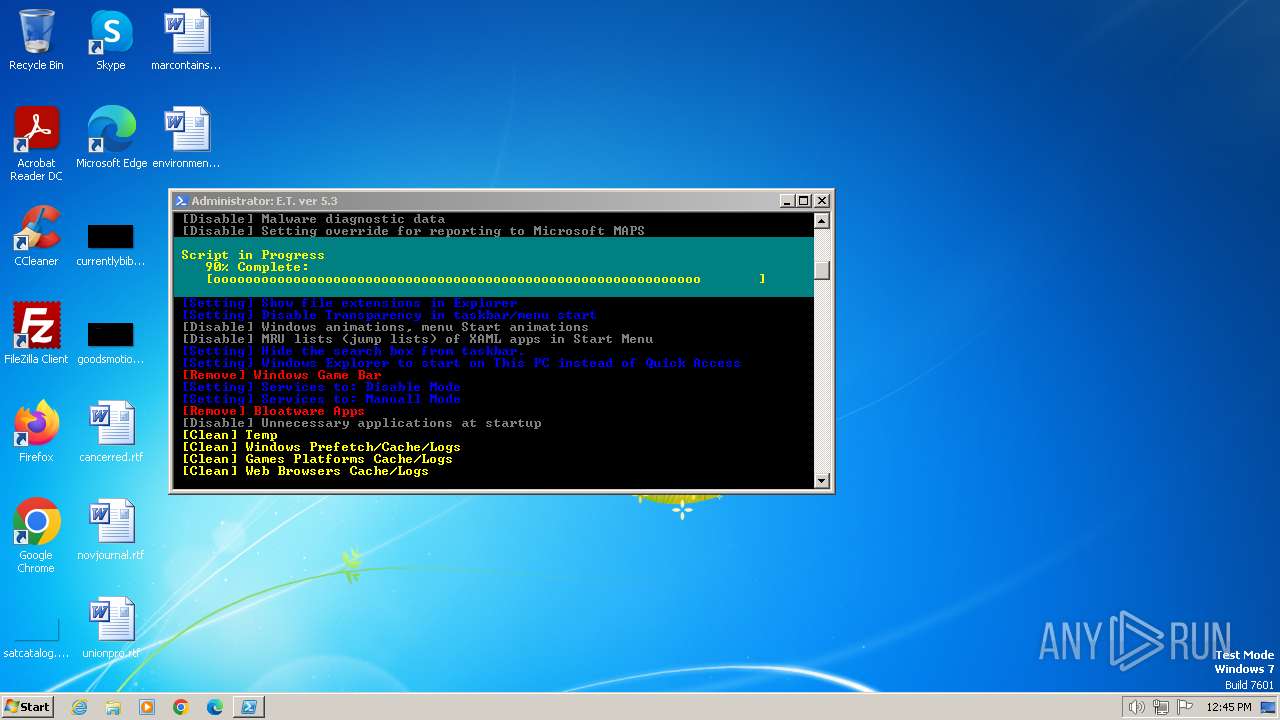
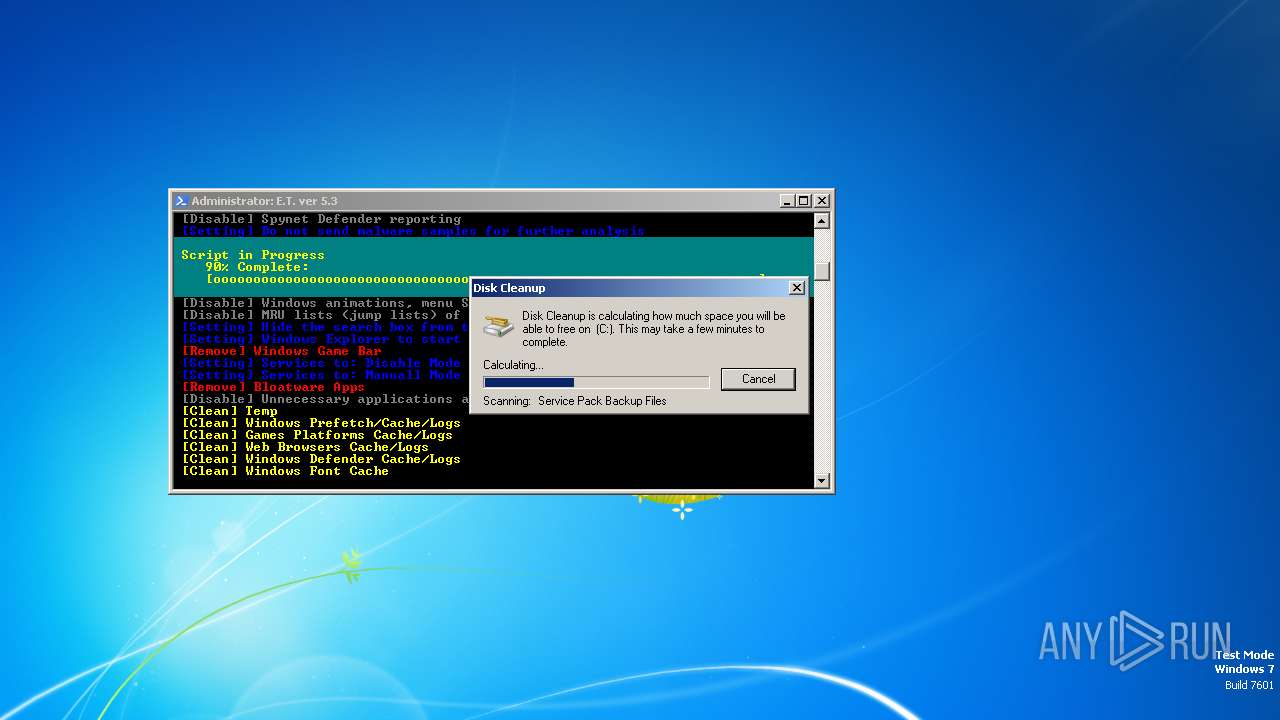
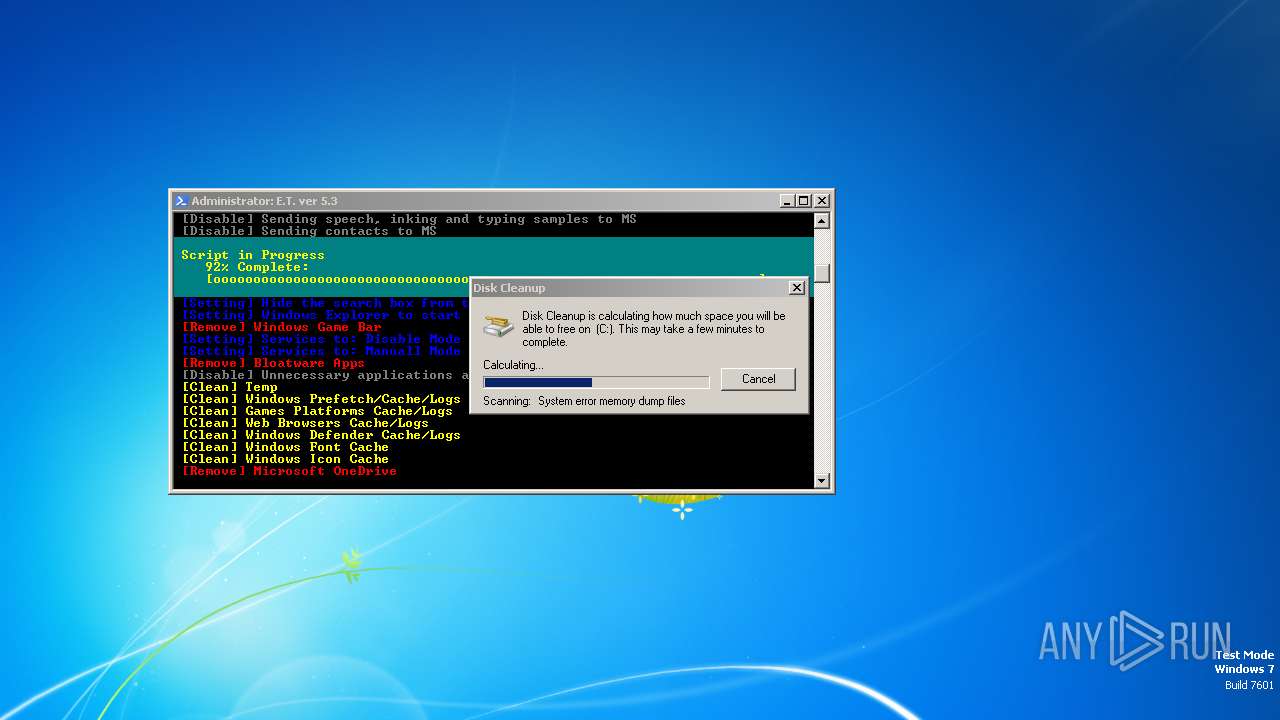
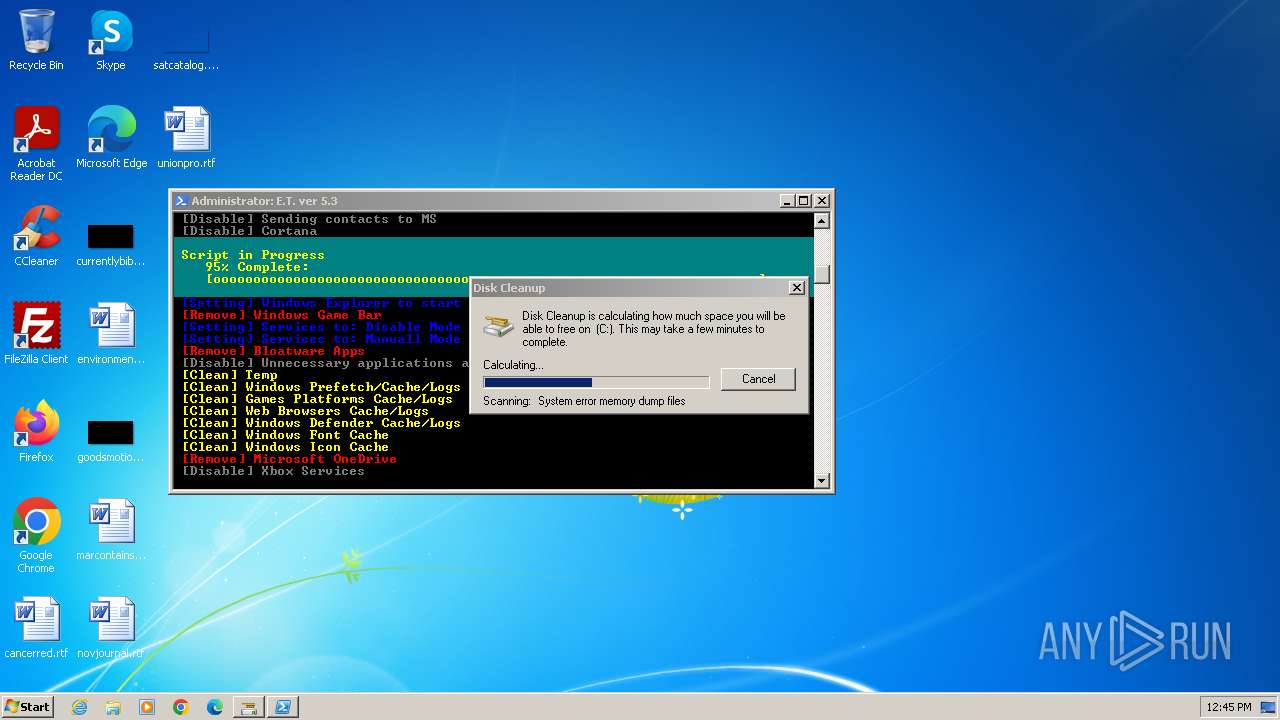
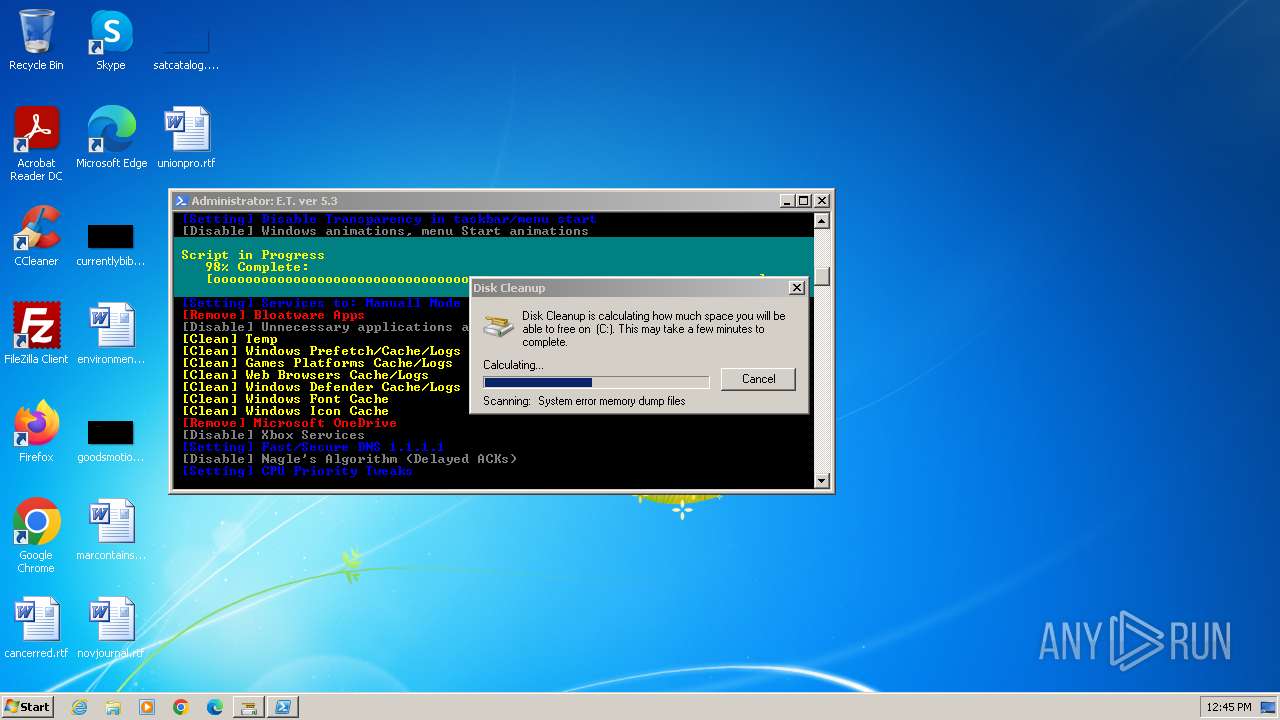
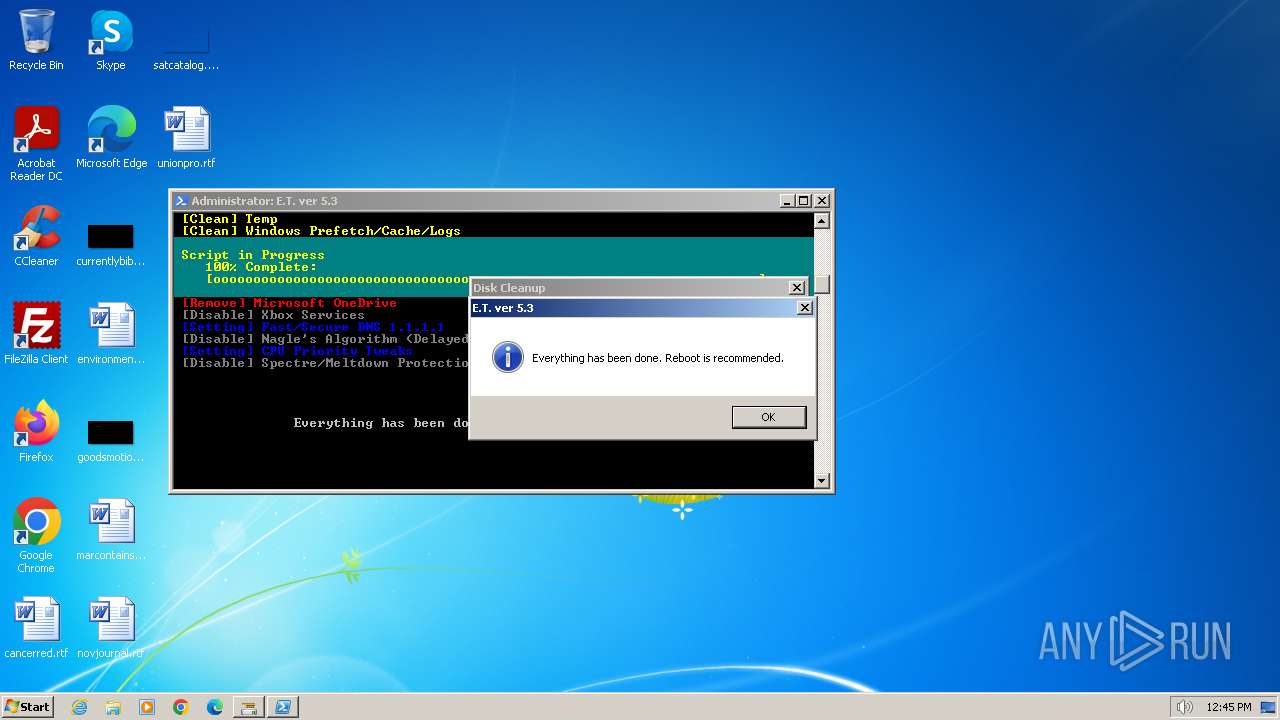
| download: | /semazurek/ET-Optimizer/releases/download/5.3/ET-Optimizer.exe |
| Full analysis: | https://app.any.run/tasks/7f02c6bd-35db-49c8-bf44-c545dbaa50c5 |
| Verdict: | Malicious activity |
| Analysis date: | January 04, 2024, 12:42:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 9FC9B0D5F4D2797FEA101559666BD50B |
| SHA1: | A7251A0E99F5C1C4BB0B7AE959C26F30CC528EF6 |
| SHA256: | BAB5BB681F4AD2965040860950003FE619D4760E0A5CC311BAC7926D524AC11A |
| SSDEEP: | 192:blRcsCghYlLCRcMs+7wk/s4C5Y9lGnx3p5ayHU52FjB61B85YcKV1:Hug6L/J+EkHkYTqbpB61BkYcKV1 |
MALICIOUS
Starts Visual C# compiler
- powershell.exe (PID: 668)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 2396)
- cmd.exe (PID: 3008)
- cmd.exe (PID: 3240)
- cmd.exe (PID: 1220)
- cmd.exe (PID: 968)
- cmd.exe (PID: 3204)
- cmd.exe (PID: 3144)
- cmd.exe (PID: 3264)
- cmd.exe (PID: 3308)
- cmd.exe (PID: 3356)
- cmd.exe (PID: 3428)
- cmd.exe (PID: 3532)
- cmd.exe (PID: 3452)
- cmd.exe (PID: 3528)
- cmd.exe (PID: 3824)
- cmd.exe (PID: 3692)
- cmd.exe (PID: 2092)
- cmd.exe (PID: 3772)
- cmd.exe (PID: 332)
- cmd.exe (PID: 2784)
- cmd.exe (PID: 2044)
- cmd.exe (PID: 2020)
- cmd.exe (PID: 3644)
- cmd.exe (PID: 1504)
- cmd.exe (PID: 3764)
- cmd.exe (PID: 2076)
- cmd.exe (PID: 2016)
- cmd.exe (PID: 2308)
- cmd.exe (PID: 1748)
- cmd.exe (PID: 2292)
- cmd.exe (PID: 2324)
- cmd.exe (PID: 1808)
- cmd.exe (PID: 392)
- cmd.exe (PID: 1728)
- cmd.exe (PID: 2688)
- cmd.exe (PID: 2316)
- cmd.exe (PID: 2624)
- cmd.exe (PID: 1600)
- cmd.exe (PID: 2396)
- cmd.exe (PID: 1992)
- cmd.exe (PID: 1380)
Starts NET.EXE for service management
- net.exe (PID: 2848)
- net.exe (PID: 2300)
- powershell.exe (PID: 668)
- net.exe (PID: 3316)
- cmd.exe (PID: 3192)
- net.exe (PID: 3204)
- cmd.exe (PID: 2264)
- net.exe (PID: 1504)
- cmd.exe (PID: 1344)
- net.exe (PID: 1044)
- cmd.exe (PID: 2868)
Steals credentials from Web Browsers
- cmd.exe (PID: 2652)
- cmd.exe (PID: 3148)
Actions looks like stealing of personal data
- cmd.exe (PID: 2828)
- cmd.exe (PID: 3308)
- cmd.exe (PID: 3216)
- cmd.exe (PID: 2128)
- cmd.exe (PID: 3908)
- cmd.exe (PID: 2664)
- cmd.exe (PID: 3980)
- cmd.exe (PID: 3728)
- cmd.exe (PID: 3532)
- cmd.exe (PID: 3296)
- cmd.exe (PID: 2512)
- SearchIndexer.exe (PID: 3068)
- cmd.exe (PID: 3736)
- cmd.exe (PID: 2620)
- cmd.exe (PID: 3876)
- cmd.exe (PID: 796)
- cmd.exe (PID: 2440)
- cmd.exe (PID: 2792)
- cmd.exe (PID: 3304)
- cmd.exe (PID: 1656)
The DLL Hijacking
- DismHost.exe (PID: 3720)
SUSPICIOUS
Reads the Internet Settings
- ET-Optimizer.exe (PID: 2084)
- powershell.exe (PID: 668)
- WMIC.exe (PID: 2312)
- WMIC.exe (PID: 2752)
- cleanmgr.exe (PID: 2816)
- WMIC.exe (PID: 3860)
- WMIC.exe (PID: 1976)
Request a resource from the Internet using PowerShell's cmdlet
- ET-Optimizer.exe (PID: 2084)
Possibly malicious use of IEX has been detected
- ET-Optimizer.exe (PID: 2084)
Starts POWERSHELL.EXE for commands execution
- ET-Optimizer.exe (PID: 2084)
- powershell.exe (PID: 668)
The process executes Powershell scripts
- ET-Optimizer.exe (PID: 2084)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 668)
Starts application with an unusual extension
- powershell.exe (PID: 668)
Using 'findstr.exe' to search for text patterns in files and output
- powershell.exe (PID: 668)
Uses WMIC.EXE to obtain service application data
- powershell.exe (PID: 668)
Searches for installed software
- dllhost.exe (PID: 2444)
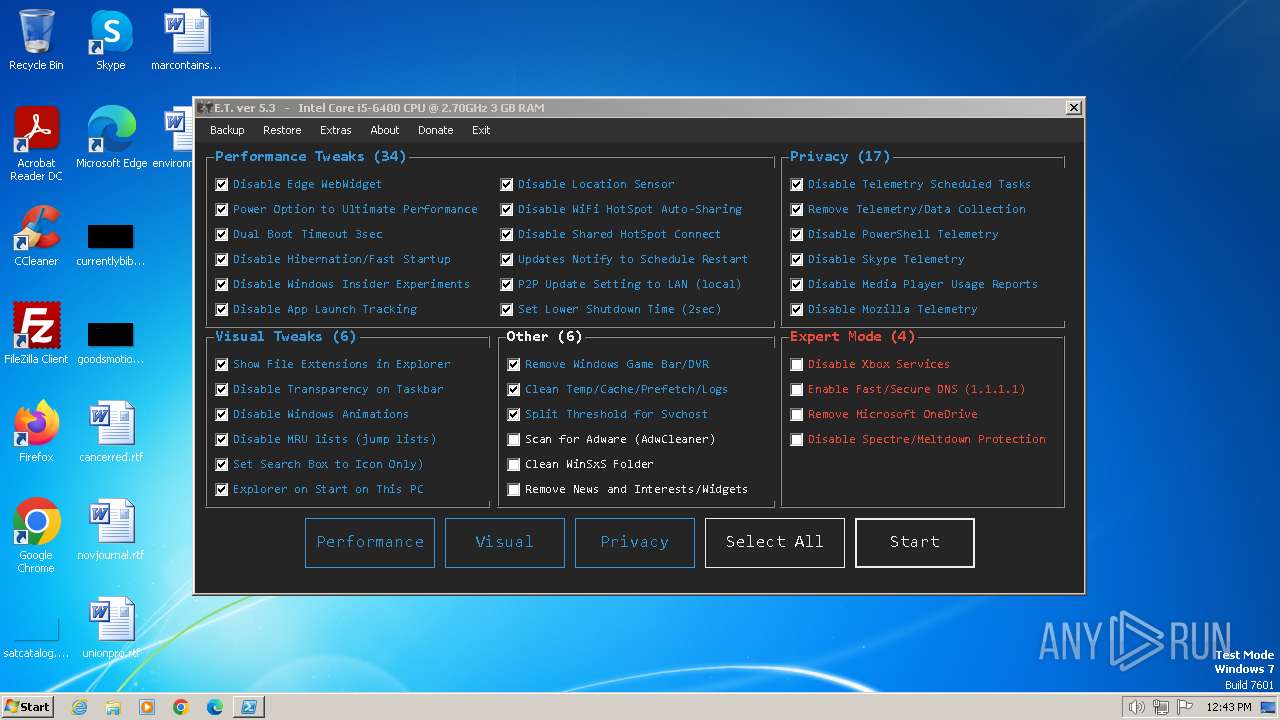
Uses powercfg.exe to modify the power settings
- cmd.exe (PID: 1192)
- cmd.exe (PID: 2368)
- powershell.exe (PID: 668)
- cmd.exe (PID: 2516)
- cmd.exe (PID: 2844)
- cmd.exe (PID: 884)
Uses WMIC.EXE to obtain computer system information
- powershell.exe (PID: 668)
Found strings related to reading or modifying Windows Defender settings
- powershell.exe (PID: 668)
Uses .NET C# to load dll
- powershell.exe (PID: 668)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 668)
Creates or modifies Windows services
- reg.exe (PID: 3308)
Starts SC.EXE for service management
- cmd.exe (PID: 3820)
- cmd.exe (PID: 3992)
- cmd.exe (PID: 2444)
- cmd.exe (PID: 3288)
- cmd.exe (PID: 3648)
- cmd.exe (PID: 3848)
- cmd.exe (PID: 3820)
- cmd.exe (PID: 3284)
- cmd.exe (PID: 2164)
- cmd.exe (PID: 2020)
- cmd.exe (PID: 3940)
- cmd.exe (PID: 2836)
- cmd.exe (PID: 1740)
- cmd.exe (PID: 3360)
- cmd.exe (PID: 3692)
- cmd.exe (PID: 2988)
- cmd.exe (PID: 1220)
- cmd.exe (PID: 2204)
- cmd.exe (PID: 3260)
- cmd.exe (PID: 2076)
- cmd.exe (PID: 4032)
- cmd.exe (PID: 116)
- cmd.exe (PID: 3884)
- cmd.exe (PID: 980)
- cmd.exe (PID: 1044)
- cmd.exe (PID: 3644)
- cmd.exe (PID: 3028)
- cmd.exe (PID: 2184)
- cmd.exe (PID: 392)
- cmd.exe (PID: 4052)
- cmd.exe (PID: 2940)
- cmd.exe (PID: 2296)
- cmd.exe (PID: 2688)
- cmd.exe (PID: 3608)
- cmd.exe (PID: 2424)
- cmd.exe (PID: 2808)
- cmd.exe (PID: 2316)
- cmd.exe (PID: 1528)
- cmd.exe (PID: 2396)
- cmd.exe (PID: 3728)
- cmd.exe (PID: 2792)
- cmd.exe (PID: 2788)
- cmd.exe (PID: 2628)
- cmd.exe (PID: 2032)
- cmd.exe (PID: 4072)
- cmd.exe (PID: 2884)
- cmd.exe (PID: 3936)
- cmd.exe (PID: 3144)
- cmd.exe (PID: 2236)
- cmd.exe (PID: 952)
- cmd.exe (PID: 3624)
- cmd.exe (PID: 1196)
- cmd.exe (PID: 2380)
- cmd.exe (PID: 2984)
- cmd.exe (PID: 2284)
- cmd.exe (PID: 900)
- cmd.exe (PID: 2300)
- cmd.exe (PID: 2920)
- cmd.exe (PID: 2532)
- cmd.exe (PID: 2360)
- cmd.exe (PID: 2444)
- cmd.exe (PID: 2860)
- cmd.exe (PID: 3284)
- cmd.exe (PID: 3872)
- cmd.exe (PID: 3368)
- cmd.exe (PID: 1544)
- cmd.exe (PID: 3992)
- cmd.exe (PID: 3940)
- cmd.exe (PID: 2536)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3512)
- cmd.exe (PID: 3752)
- powershell.exe (PID: 668)
- cmd.exe (PID: 2072)
Uses REG/REGEDIT.EXE to modify registry
- powershell.exe (PID: 668)
- cmd.exe (PID: 1472)
- cmd.exe (PID: 3868)
- cmd.exe (PID: 3824)
- cmd.exe (PID: 2372)
- cmd.exe (PID: 3504)
- cmd.exe (PID: 2836)
- cmd.exe (PID: 2448)
- cmd.exe (PID: 3084)
- cmd.exe (PID: 1028)
- cmd.exe (PID: 1424)
- cmd.exe (PID: 2368)
- cmd.exe (PID: 4020)
- cmd.exe (PID: 3004)
- cmd.exe (PID: 2268)
- cmd.exe (PID: 1544)
- cmd.exe (PID: 3752)
- cmd.exe (PID: 3460)
- cmd.exe (PID: 2108)
- cmd.exe (PID: 3332)
- cmd.exe (PID: 1308)
- cmd.exe (PID: 2072)
- cmd.exe (PID: 3212)
- cmd.exe (PID: 2024)
- cmd.exe (PID: 3092)
- cmd.exe (PID: 3032)
- cmd.exe (PID: 2688)
- cmd.exe (PID: 2384)
- cmd.exe (PID: 2040)
- cmd.exe (PID: 2332)
- cmd.exe (PID: 3040)
- cmd.exe (PID: 2068)
- cmd.exe (PID: 3608)
- cmd.exe (PID: 2112)
- cmd.exe (PID: 3260)
- cmd.exe (PID: 1216)
- cmd.exe (PID: 4004)
- cmd.exe (PID: 4028)
- cmd.exe (PID: 2972)
- cmd.exe (PID: 2496)
- cmd.exe (PID: 2440)
- cmd.exe (PID: 3944)
- cmd.exe (PID: 1056)
- cmd.exe (PID: 2156)
- cmd.exe (PID: 1772)
- cmd.exe (PID: 332)
Process uses IPCONFIG to clear DNS cache
- powershell.exe (PID: 668)
Suspicious use of NETSH.EXE
- powershell.exe (PID: 668)
Uses WMIC.EXE to obtain CPU information
- powershell.exe (PID: 668)
INFO
Drops the executable file immediately after the start
- ET-Optimizer.exe (PID: 2084)
- csc.exe (PID: 696)
- cleanmgr.exe (PID: 2816)
Checks supported languages
- ET-Optimizer.exe (PID: 2084)
- csc.exe (PID: 696)
- cvtres.exe (PID: 2128)
- chcp.com (PID: 188)
- DismHost.exe (PID: 3720)
- PresentationFontCache.exe (PID: 3164)
- wmpnscfg.exe (PID: 2512)
- wmpnscfg.exe (PID: 2664)
Reads the machine GUID from the registry
- ET-Optimizer.exe (PID: 2084)
- cvtres.exe (PID: 2128)
- csc.exe (PID: 696)
- DismHost.exe (PID: 3720)
- PresentationFontCache.exe (PID: 3164)
Reads the computer name
- ET-Optimizer.exe (PID: 2084)
- DismHost.exe (PID: 3720)
- PresentationFontCache.exe (PID: 3164)
- wmpnscfg.exe (PID: 2512)
- wmpnscfg.exe (PID: 2664)
Create files in a temporary directory
- csc.exe (PID: 696)
- cvtres.exe (PID: 2128)
- esentutl.exe (PID: 2548)
- cleanmgr.exe (PID: 2816)
Executes as Windows Service
- VSSVC.exe (PID: 2640)
- SearchIndexer.exe (PID: 3068)
- PresentationFontCache.exe (PID: 3164)
Creates files in the program directory
- powershell.exe (PID: 668)
- SearchIndexer.exe (PID: 3068)
Unusual connection from system programs
- powershell.exe (PID: 668)
The Powershell connects to the Internet
- powershell.exe (PID: 668)
Changes appearance of the Explorer extensions
- reg.exe (PID: 3544)
Application launched itself
- powershell.exe (PID: 668)
Reads Microsoft Office registry keys
- cleanmgr.exe (PID: 2816)
Creates files or folders in the user directory
- cleanmgr.exe (PID: 2816)
Process drops legitimate windows executable
- cleanmgr.exe (PID: 2816)
Reads the Internet Settings
- explorer.exe (PID: 3956)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2079:01:04 05:17:05+01:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 3584 |
| InitializedDataSize: | 9728 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2c1e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | ConsoleApp1 |
| FileVersion: | 1.0.0.0 |
| InternalName: | ET-Optimizer.exe |
| LegalCopyright: | Copyright © 2023 |
| LegalTrademarks: | - |
| OriginalFileName: | ET-Optimizer.exe |
| ProductName: | ConsoleApp1 |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
911
Monitored processes
867
Malicious processes
18
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Windows\system32\cmd.exe" /c sc stop AdobeARMservice | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1062 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 120 | "C:\Windows\system32\reg.exe" add HKLM\Software\Microsoft\VSCommon\15.0\SQM /v OptIn /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 120 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Command "Get-AppxPackage -allusers *XING* | Remove-AppxPackage" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 120 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Command "Get-AppxPackage -allusers *HPQuickTouch* | Remove-AppxPackage" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 120 | "C:\Windows\system32\cmd.exe" /c Del %WinDir%\System32\SleepStudy\*.etl /F /Q | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 128 | "C:\Windows\system32\reg.exe" add HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\ContentDeliveryManager /v SubscribedContent-338387Enabled /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 128 | "C:\Windows\system32\cmd.exe" /c Del %AppData%\Origin\Logs /F /Q /S | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 148 | schtasks /Change /TN GoogleUpdateTaskMachineUA /Disable | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 188 | "C:\Windows\system32\chcp.com" 65001 | C:\Windows\System32\chcp.com | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 188 | schtasks /Change /TN MicrosoftEdgeUpdateTaskMachineCore /Disable | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
86 940
Read events
86 186
Write events
522
Delete events
232
Modification events
| (PID) Process: | (2084) ET-Optimizer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2084) ET-Optimizer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2084) ET-Optimizer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2084) ET-Optimizer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (668) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (668) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (668) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (668) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (668) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2444) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP\Clients |
| Operation: | write | Name: | {09F7EDC5-294E-4180-AF6A-FB0E6A0E9513} |
Value: \\?\Volume{e1a82db4-a9f0-11e7-b142-806e6f6e6963}\:(C%3A) | |||
Executable files
32
Suspicious files
234
Text files
68
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2444 | dllhost.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 668 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\N7QFMSOTKV9B136CYCP4.temp | binary | |
MD5:F500255BDC0DD45A0934243E38529D10 | SHA256:AD4304402753CEF71770C63692428001309617BDA00D87E229D197721D29496E | |||
| 2444 | dllhost.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{fff42233-3f73-413b-9f45-08363091dd8d}_OnDiskSnapshotProp | binary | |
MD5:D7803E8DB4919A72A87F5DA815443067 | SHA256:08EA8D294E05E23D5E3D7ED4313CA2B2259A9F8D489BBB9DD90A1CBD34B25E13 | |||
| 668 | powershell.exe | C:\Users\admin\AppData\Local\Temp\1g4t1fmv\1g4t1fmv.cmdline | text | |
MD5:E042B13C742D71238B21C076BDA0C4B2 | SHA256:41DA8896C592D1A136BE8214862EE7295E38C85AC6B357B2DD0042D6626CAA9D | |||
| 2128 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES1C1F.tmp | binary | |
MD5:50B4C1AD727D7E0B3C662DC420F0C78C | SHA256:9F2857BF1456CE1D34D1493C7840FB5CEC43E54127AD54C5D02B6B33E9D0A261 | |||
| 668 | powershell.exe | C:\Users\admin\AppData\Local\Temp\1g4t1fmv\1g4t1fmv.0.cs | text | |
MD5:D2DD7B143C5631AA598407BBE81EF5DB | SHA256:B3CCD5D9083909C89F8201C421434EC38280C051597B5414559C1DF7FCF31CFE | |||
| 668 | powershell.exe | C:\Users\admin\AppData\Local\Temp\rniupbzq.e3r.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 696 | csc.exe | C:\Users\admin\AppData\Local\Temp\1g4t1fmv\CSCF37759C72484472BBCEA3CBF5D3ACE3.TMP | binary | |
MD5:5464F5E271776E2F93EBE53B13B12980 | SHA256:97937E889BD08120936976F8D51C9BEFD8DA3DB767D1CBFF4E041CA8B4CF5A68 | |||
| 668 | powershell.exe | C:\ProgramData\ET\chck2.lbool | text | |
MD5:3C98E042B3F054AEB08C9C98E01903A2 | SHA256:5663B002B47D49F7FC46FED1B3EAA48B25E2E7BE6FA8B1E8D60DD251055AA729 | |||
| 668 | powershell.exe | C:\ProgramData\ET\chck6.lbool | text | |
MD5:3C98E042B3F054AEB08C9C98E01903A2 | SHA256:5663B002B47D49F7FC46FED1B3EAA48B25E2E7BE6FA8B1E8D60DD251055AA729 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
668 | powershell.exe | 185.199.109.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
raw.githubusercontent.com |
| shared |
Threats
Process | Message |
|---|---|
cleanmgr.exe | PID=2816 The requested provider was not found in the Provider Store. - CDISMProviderStore::Internal_GetProvider(hr:0x80004005) |
cleanmgr.exe | PID=2816 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
cleanmgr.exe | PID=2816 Connecting to the provider located at C:\Windows\System32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |
cleanmgr.exe | PID=2816 Loading Provider from location C:\Windows\System32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
cleanmgr.exe | PID=2816 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
cleanmgr.exe | PID=2816 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
cleanmgr.exe | PID=2816 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
cleanmgr.exe | PID=2816 Getting Provider OSServices - CDISMProviderStore::GetProvider |
cleanmgr.exe | PID=2816 Failed to get an OSServices provider. Must be running in local store. Falling back to checking alongside the log provider for wdscore.dll. - CDISMLogger::FindWdsCore(hr:0x80004005) |
DismHost.exe | PID=3720 Disconnecting Provider: DISMLogger - CDISMProviderStore::Internal_DisconnectProvider |