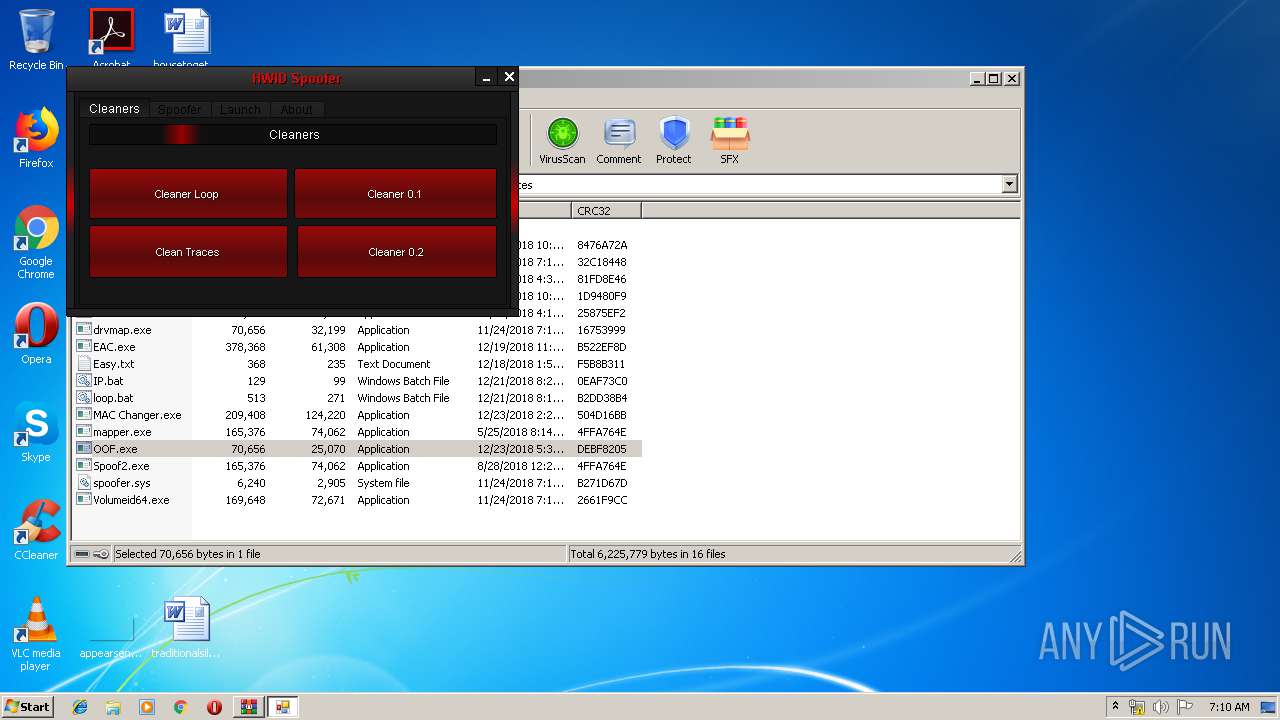
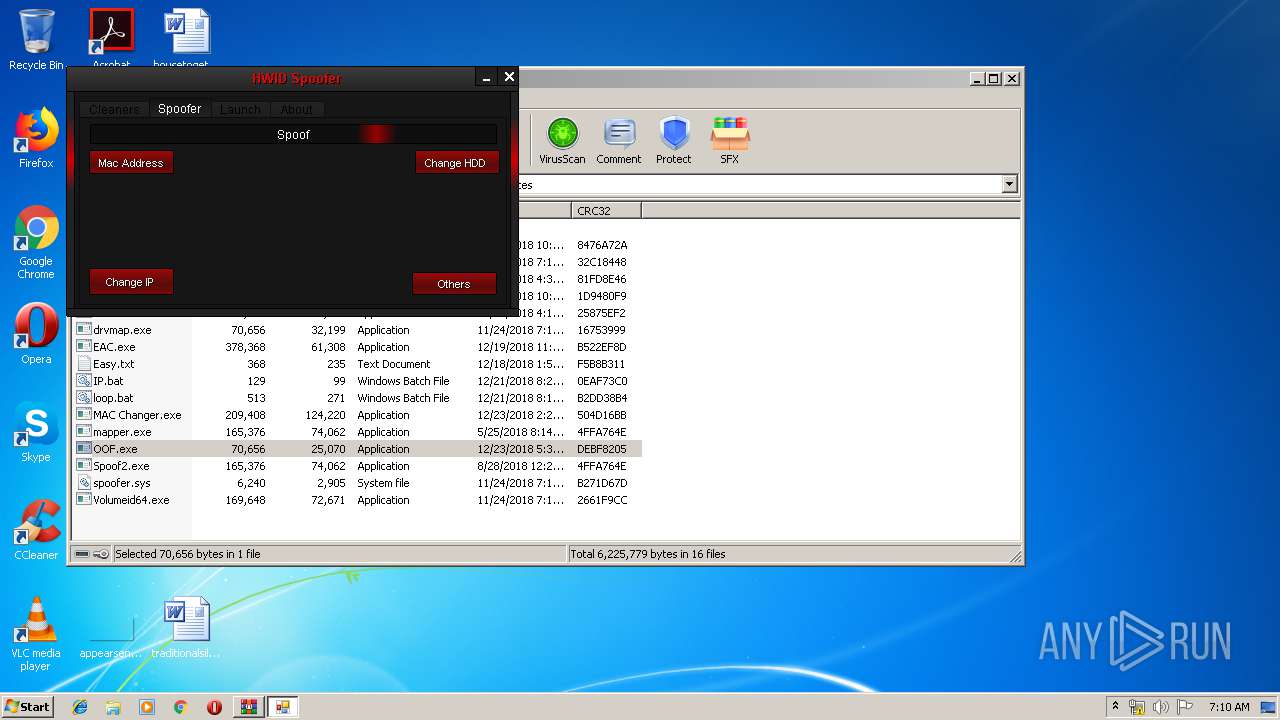
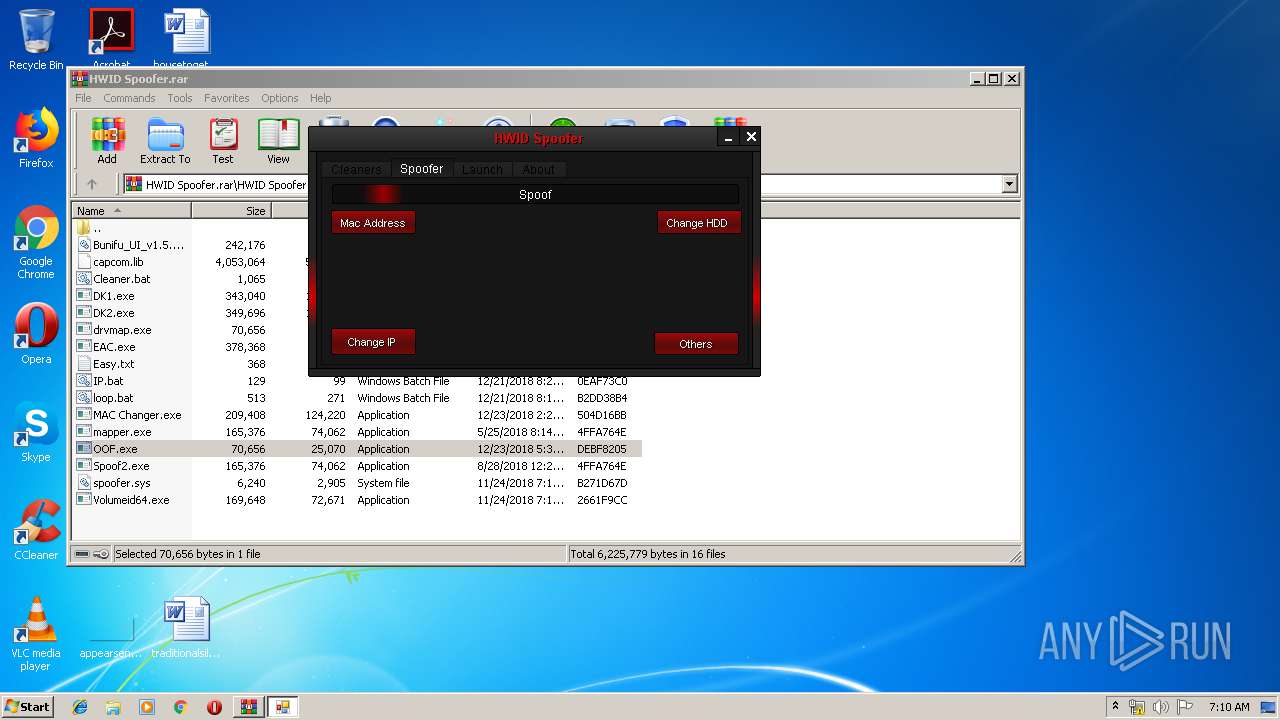
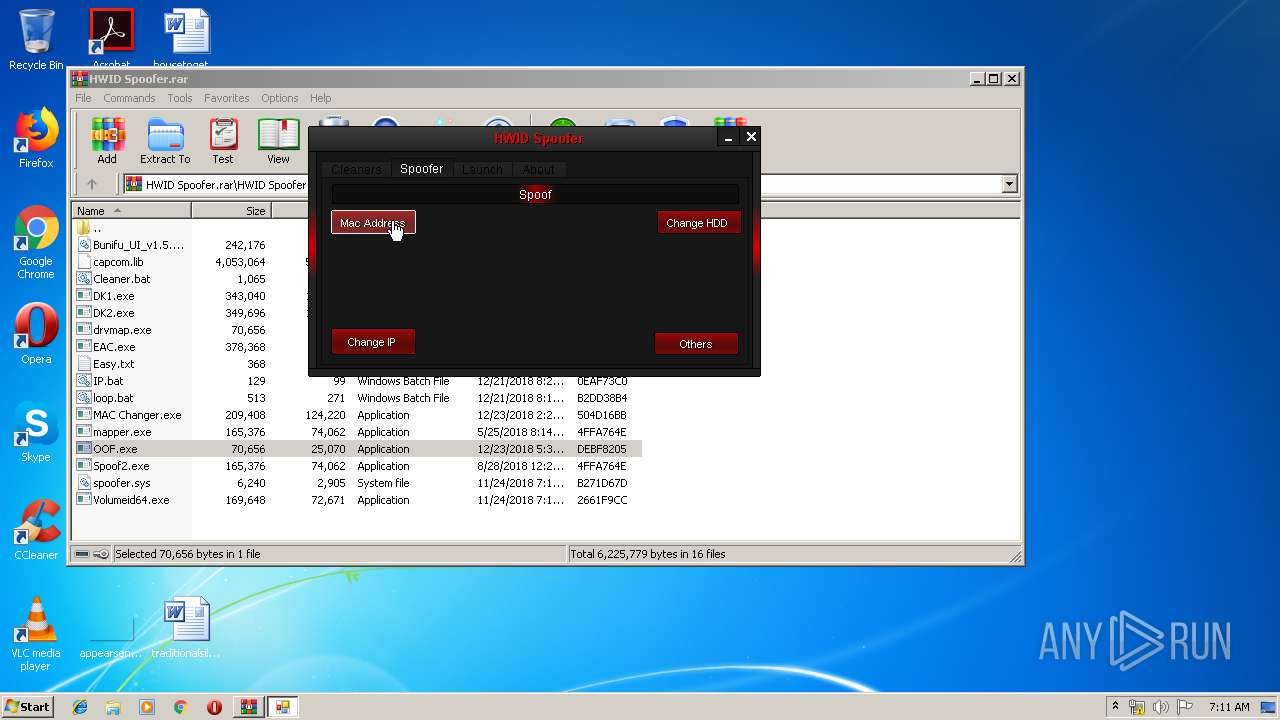
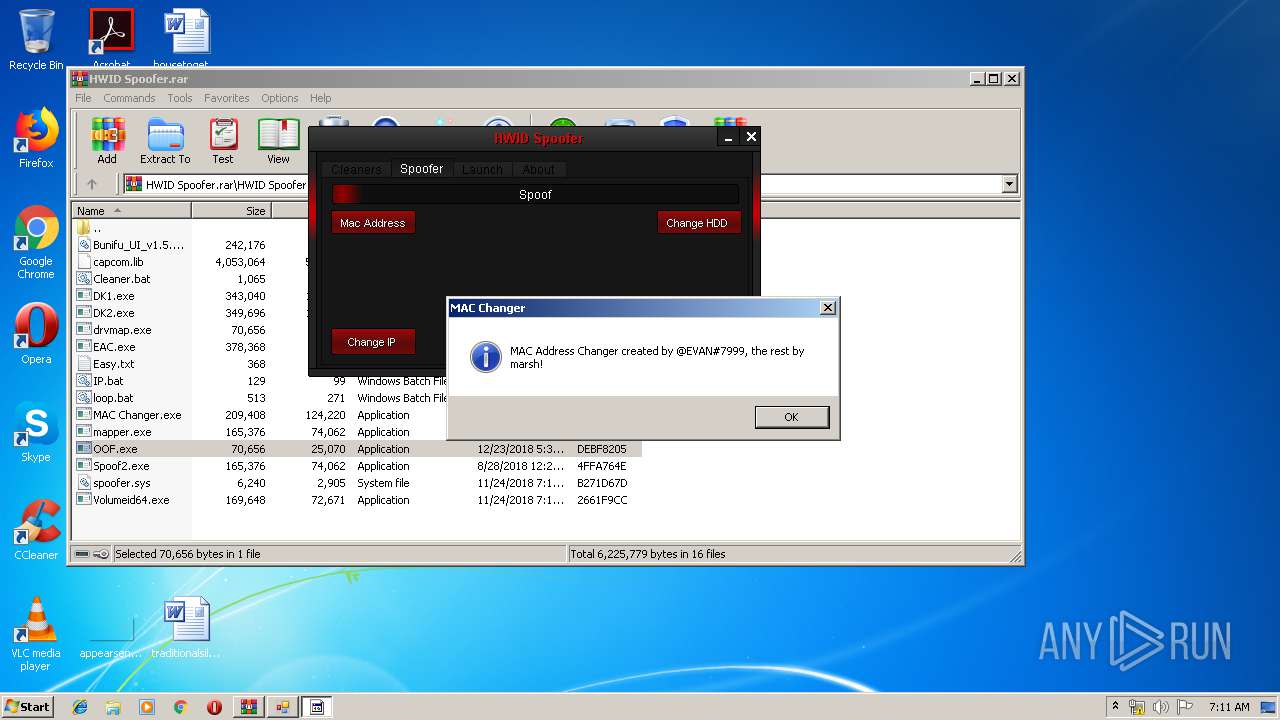
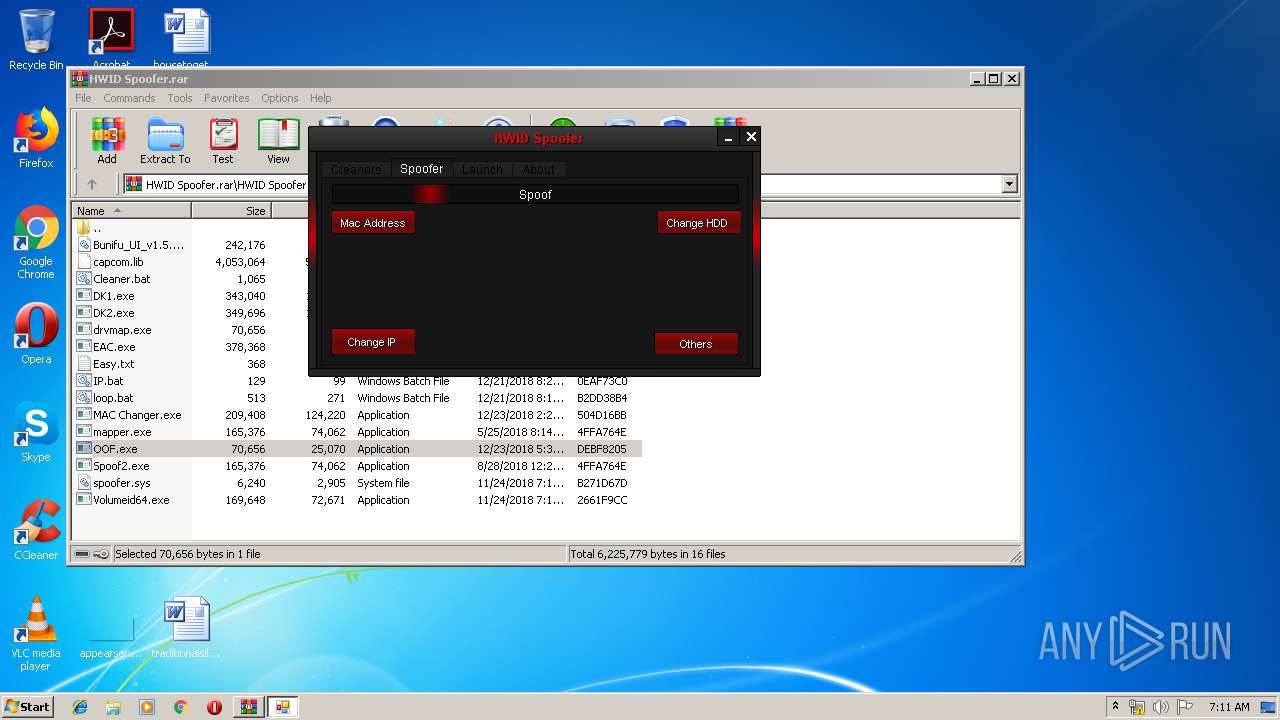
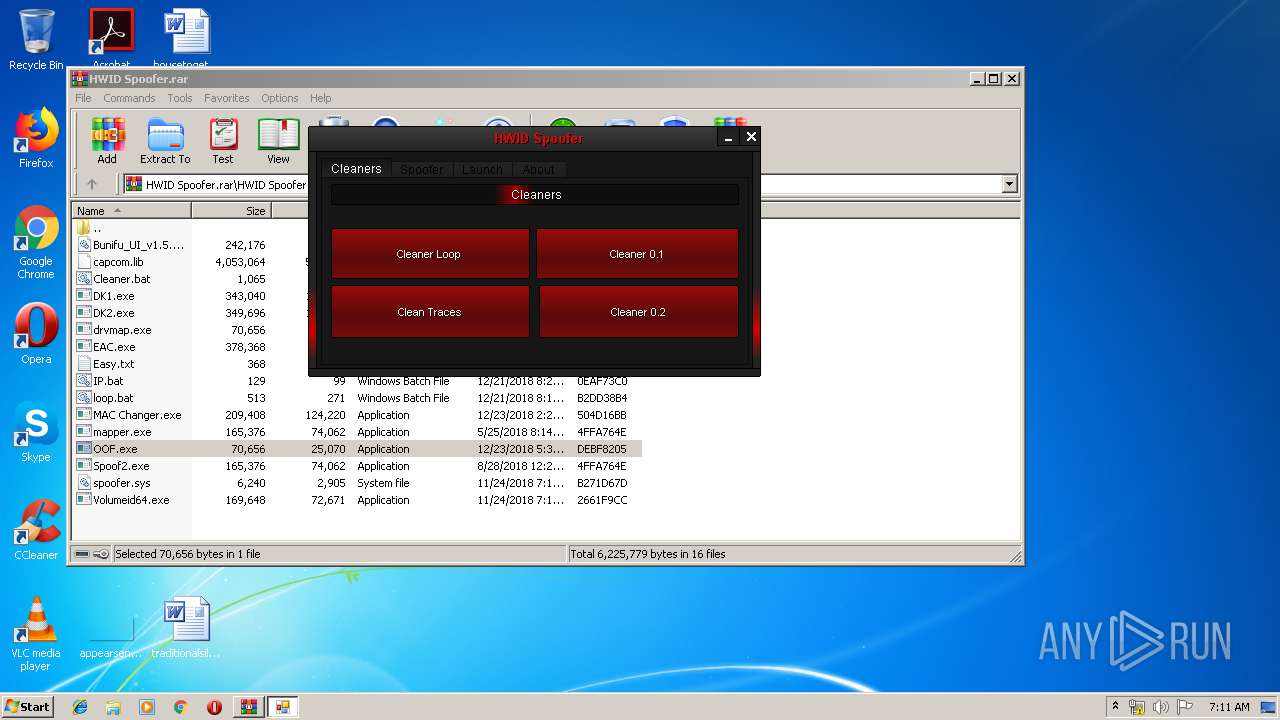
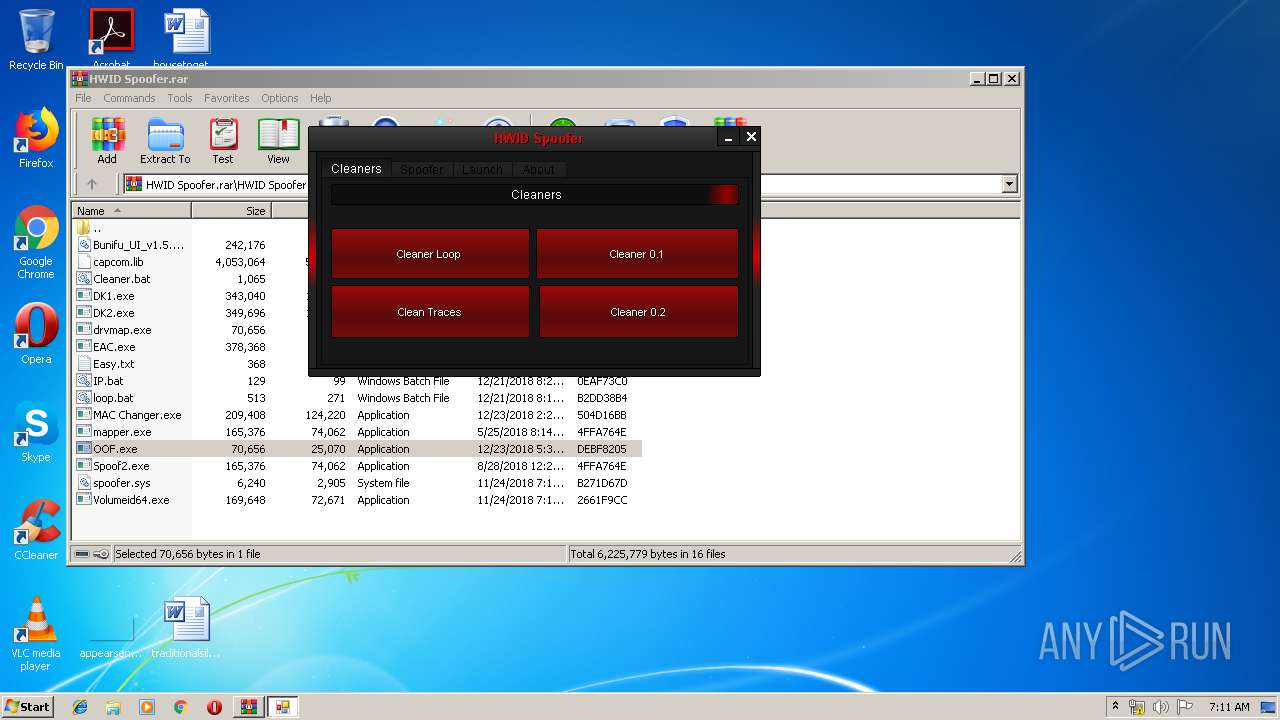
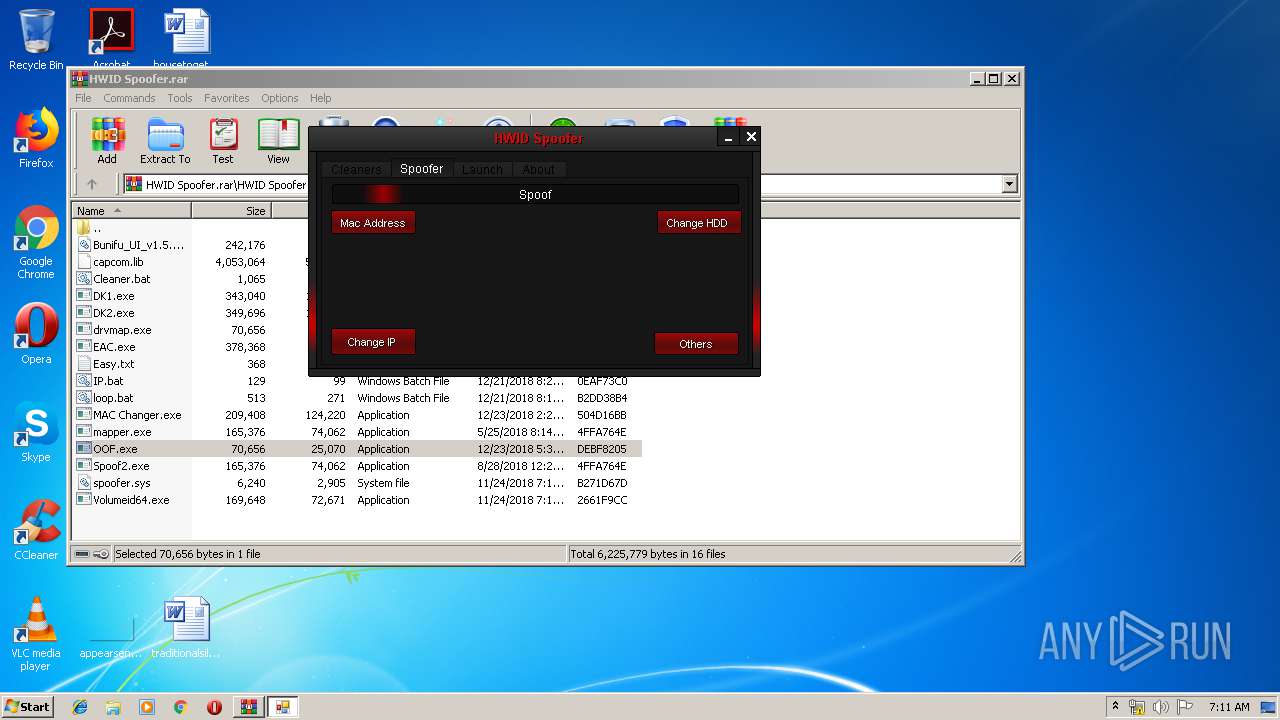
| File name: | HWID Spoofer.rar |
| Full analysis: | https://app.any.run/tasks/dac61a2e-98c7-4d61-b89e-3f588fc265ea |
| Verdict: | Suspicious activity |
| Analysis date: | June 30, 2019, 06:10:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 87B831401529F395A4F5117EB7F0C637 |
| SHA1: | B7A6ABF24A0C2292B76999A447253F0EF2E006B3 |
| SHA256: | BAAE3127ACF477FAFA20BCBF3F3D6D63C73CB541236844841708136BEA574D4E |
| SSDEEP: | 24576:EfX/EzLtwSE3SEZs+VuJFtBqmtGJrGyhxGnY33Lr6XnQqW7gV+gkiWx8V8NBWL8p:WiBEZJojtGMyhxn3/QV+gxWx8V8N4L8p |
MALICIOUS
Application was dropped or rewritten from another process
- MAC Changer.exe (PID: 3616)
- OOF.exe (PID: 2548)
- MAC Changer.exe (PID: 3892)
Loads dropped or rewritten executable
- MAC Changer.exe (PID: 3616)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1812)
Starts CMD.EXE for commands execution
- MAC Changer.exe (PID: 3616)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 3512)
- cmd.exe (PID: 3624)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 1812)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
48
Monitored processes
10
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 388 | netsh interface set interface Wi-Fi disabled | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1812 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\HWID Spoofer.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2548 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.5493\HWID Spoofer\OOF.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.5493\HWID Spoofer\OOF.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: WindowsApp1 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2732 | netsh interface set interface Wi-Fi enabled | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
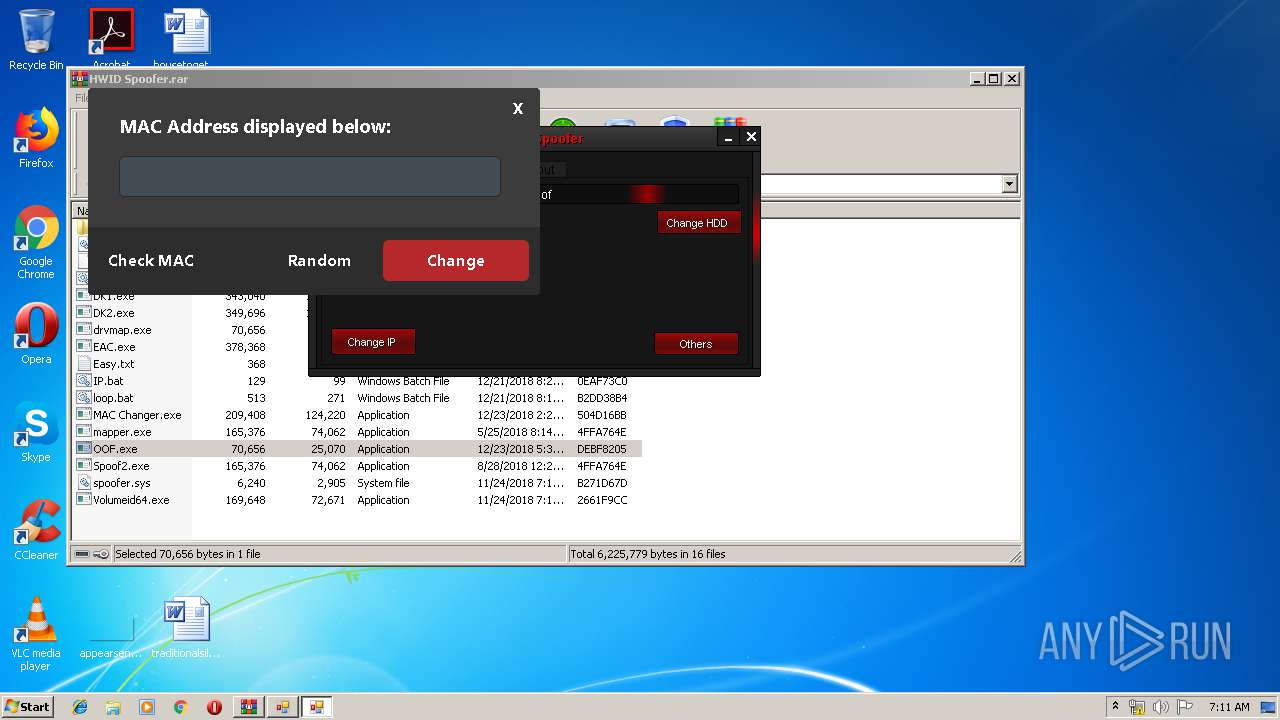
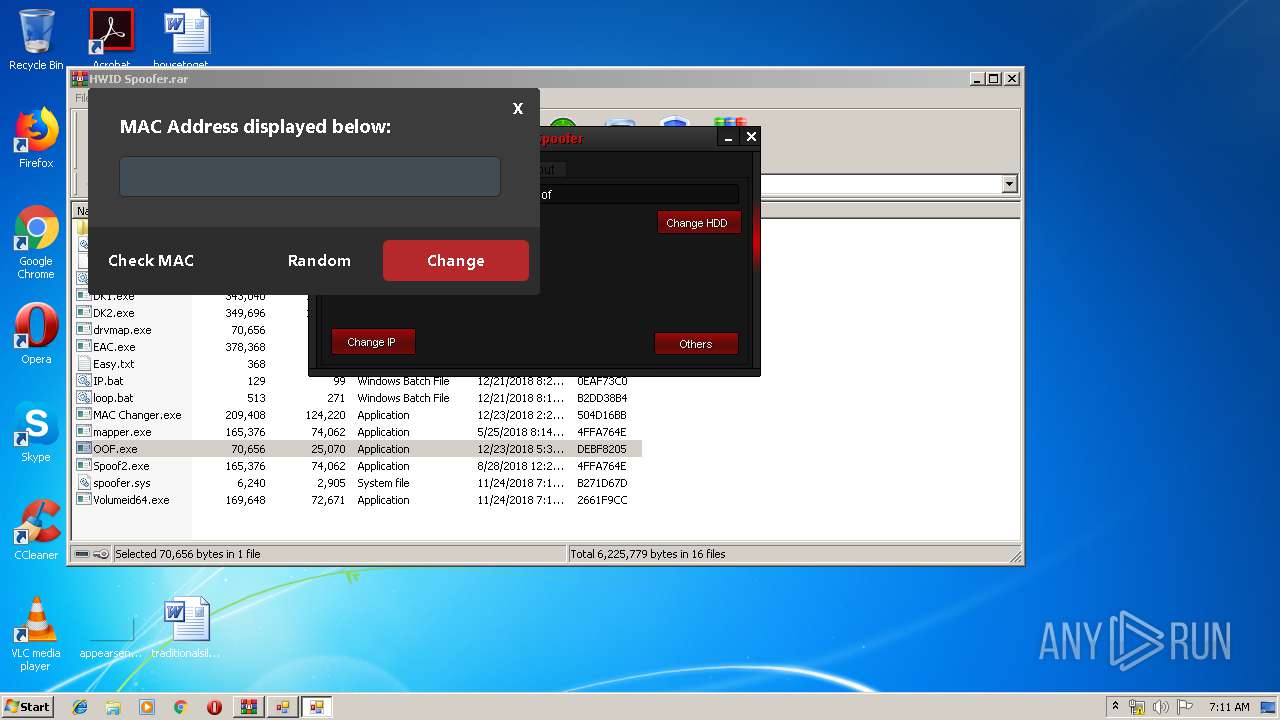
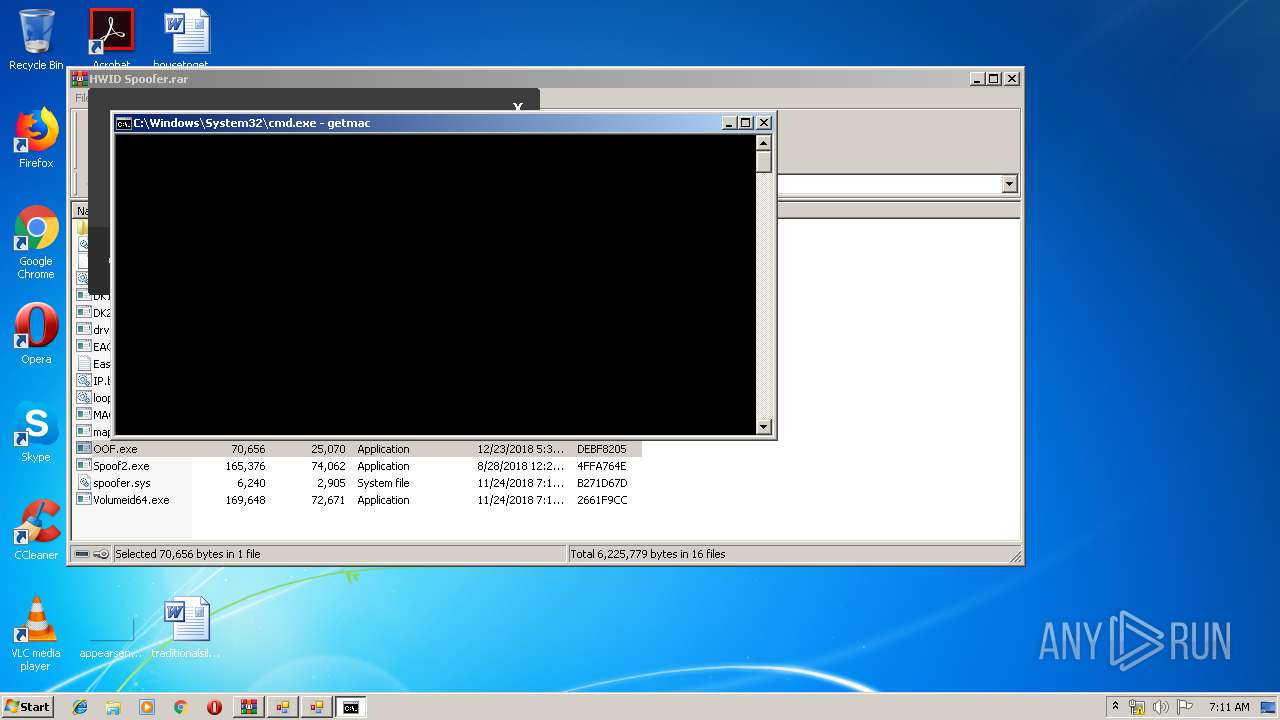
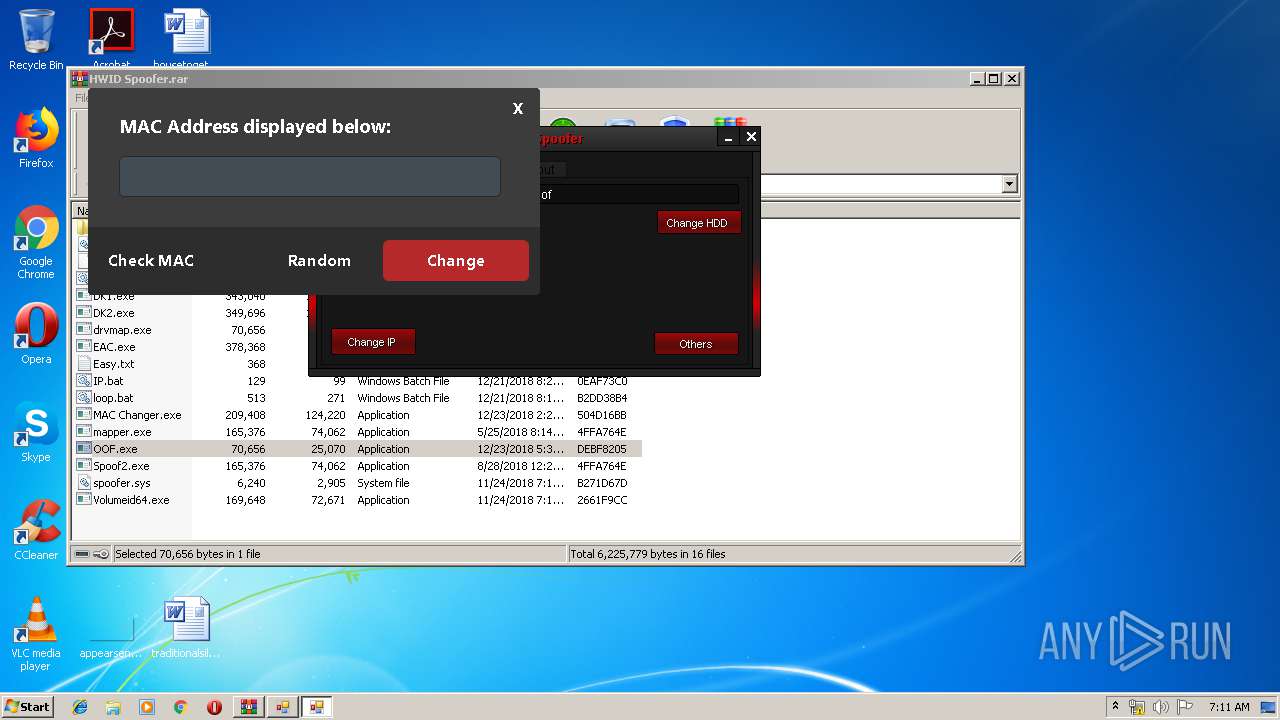
| 2912 | getmac | C:\Windows\system32\getmac.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Displays NIC MAC information Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3192 | "C:\Windows\System32\cmd.exe" /k getmac | C:\Windows\System32\cmd.exe | — | MAC Changer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 3221225786 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3512 | "C:\Windows\System32\cmd.exe" /c netsh interface set interface Wi-Fi disabled | C:\Windows\System32\cmd.exe | — | MAC Changer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3616 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.5493\HWID Spoofer\MAC Changer.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.5493\HWID Spoofer\MAC Changer.exe | OOF.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: WindowsFormsApp1 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3624 | "C:\Windows\System32\cmd.exe" /c netsh interface set interface Wi-Fi enabled | C:\Windows\System32\cmd.exe | — | MAC Changer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3892 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.5493\HWID Spoofer\MAC Changer.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.5493\HWID Spoofer\MAC Changer.exe | — | OOF.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: WindowsFormsApp1 Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
1 046
Read events
904
Write events
142
Delete events
0
Modification events
| (PID) Process: | (1812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1812) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\HWID Spoofer.rar | |||
| (PID) Process: | (1812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1812) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
| (PID) Process: | (1812) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
Executable files
11
Suspicious files
0
Text files
4
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.5493\HWID Spoofer\Cleaner.bat | text | |
MD5:— | SHA256:— | |||
| 1812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.5493\HWID Spoofer\drvmap.exe | executable | |
MD5:— | SHA256:— | |||
| 1812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.5493\HWID Spoofer\capcom.lib | obj | |
MD5:— | SHA256:— | |||
| 1812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.5493\HWID Spoofer\Easy.txt | text | |
MD5:— | SHA256:— | |||
| 1812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.5493\HWID Spoofer\EAC.exe | executable | |
MD5:— | SHA256:— | |||
| 1812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.5493\HWID Spoofer\MAC Changer.exe | executable | |
MD5:— | SHA256:— | |||
| 1812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.5493\HWID Spoofer\loop.bat | text | |
MD5:— | SHA256:— | |||
| 1812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.5493\HWID Spoofer\IP.bat | text | |
MD5:— | SHA256:— | |||
| 1812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.5493\HWID Spoofer\Bunifu_UI_v1.5.3.dll | executable | |
MD5:2ECB51AB00C5F340380ECF849291DBCF | SHA256:F1B3E0F2750A9103E46A6A4A34F1CF9D17779725F98042CC2475EC66484801CF | |||
| 1812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1812.5493\HWID Spoofer\DK2.exe | executable | |
MD5:BB36D4578CE201DC932AB6BBC079875C | SHA256:4C831252AA6F193C4474BA74F352BEE7D00099DFAF5AC6E98AB1253E21999B4A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report