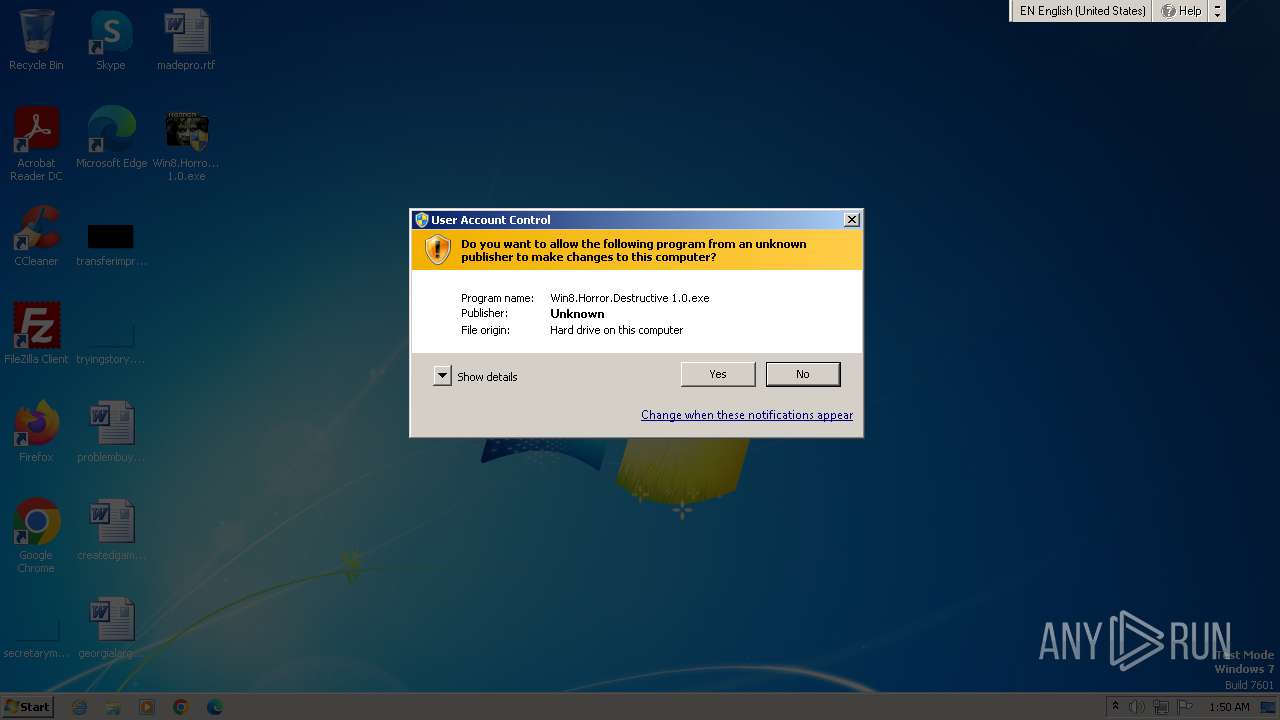
| File name: | Win8.Horror.Destructive 1.0.exe |
| Full analysis: | https://app.any.run/tasks/62799c4b-32c3-4f23-a41e-d673b7c823ed |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2023, 00:50:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 846D847D9B1247C57824D5D2601A7FAF |
| SHA1: | 2119DCCEE1E98AF31FD193CF38BBFD8614F183BB |
| SHA256: | BA8FA2C240EDFC35C3078FCF31B87C0E1AF4404DFC1F52E0D5640EDB061355FC |
| SSDEEP: | 393216:aoFns8VCLkTHRE2DHTwOQVAQZTN79BLaSaumPNC:a474IS2g/VTZPBuRPNC |
MALICIOUS
Drops the executable file immediately after the start
- Win8.Horror.Destructive 1.0.exe (PID: 444)
Application was dropped or rewritten from another process
- TrashMBR.exe (PID: 3352)
- HorrorGui.exe (PID: 300)
SUSPICIOUS
The process executes VB scripts
- Win8.Horror.Destructive 1.0.exe (PID: 444)
- cmd.exe (PID: 2080)
Reads the Internet Settings
- Win8.Horror.Destructive 1.0.exe (PID: 444)
- wscript.exe (PID: 4052)
- cmd.exe (PID: 2080)
- wscript.exe (PID: 2036)
Executing commands from a ".bat" file
- wscript.exe (PID: 4052)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 4052)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2080)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2080)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 2080)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 2080)
The system shut down or reboot
- HorrorGui.exe (PID: 300)
INFO
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3552)
Checks supported languages
- wmpnscfg.exe (PID: 3552)
- Win8.Horror.Destructive 1.0.exe (PID: 444)
- TrashMBR.exe (PID: 3352)
- HorrorGui.exe (PID: 300)
Reads the computer name
- wmpnscfg.exe (PID: 3552)
- Win8.Horror.Destructive 1.0.exe (PID: 444)
Create files in a temporary directory
- Win8.Horror.Destructive 1.0.exe (PID: 444)
The executable file from the user directory is run by the CMD process
- TrashMBR.exe (PID: 3352)
- HorrorGui.exe (PID: 300)
Checks proxy server information
- wscript.exe (PID: 2036)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (35) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (30.9) |
| .scr | | | Windows screen saver (14.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.3) |
| .exe | | | Win32 Executable (generic) (5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:02:01 21:46:09+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 66048 |
| InitializedDataSize: | 12926464 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.6.6.6 |
| ProductVersionNumber: | 6.6.6.6 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug, Pre-release, Private build |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileVersion: | 6.6.6.6 |
| ProductVersion: | 6.6.6.6 |
| ProductName: | Win8.Horror.Destructive |
| InternalName: | Malware |
| FileDescription: | Windows 8 Horror Edition |
| CompanyName: | HorrorTrojans |
| LegalCopyright: | 2012-2021 |
Total processes
65
Monitored processes
23
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | icacls C:\Windows\system32\taskmgr.exe /grant "everyone":F | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 300 | HorrorGui.exe | C:\Users\admin\AppData\Local\Temp\F0D6.tmp\HorrorGui.exe | — | cmd.exe | |||||||||||
User: admin Company: BKHN Integrity Level: HIGH Exit code: 1073807364 Version: 1.00 Modules
| |||||||||||||||
| 444 | "C:\Users\admin\Desktop\Win8.Horror.Destructive 1.0.exe" | C:\Users\admin\Desktop\Win8.Horror.Destructive 1.0.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 556 | takeown /f C:\Windows\system32\logonui.exe | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1192 | icacls C:\Windows\system32\logonui.exe /grant admin:F | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2036 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\F0D6.tmp\music.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2052 | "C:\Users\admin\Desktop\Win8.Horror.Destructive 1.0.exe" | C:\Users\admin\Desktop\Win8.Horror.Destructive 1.0.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2080 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\F0D6.tmp\Horror8.bat" " | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2700 | Shutdown /s /t 00 | C:\Windows\System32\shutdown.exe | — | HorrorGui.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Shutdown and Annotation Tool Exit code: 1073807364 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2948 | taskkill /f /im logonui.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 295
Read events
3 228
Write events
34
Delete events
33
Modification events
| (PID) Process: | (3552) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{6663AE1A-97B9-409A-9314-943840F189D8}\{EAD26FB2-4AC9-4FDB-81A6-EF0873E77922} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3552) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{6663AE1A-97B9-409A-9314-943840F189D8} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3552) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{F86D13E6-4B34-4F5C-9F54-3B9FE833856B} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (444) Win8.Horror.Destructive 1.0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (444) Win8.Horror.Destructive 1.0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (444) Win8.Horror.Destructive 1.0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (444) Win8.Horror.Destructive 1.0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4052) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4052) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4052) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
2
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 444 | Win8.Horror.Destructive 1.0.exe | C:\Users\admin\AppData\Local\Temp\F0D6.tmp\clingclang.wav | — | |
MD5:— | SHA256:— | |||
| 444 | Win8.Horror.Destructive 1.0.exe | C:\Users\admin\AppData\Local\Temp\F0D6.tmp\F0D7.tmp\F0D8.vbs | binary | |
MD5:3BAFC447CF86B66198F84690CB592ADB | SHA256:B96A442ADC718E9E0981B1C3BEA2C8172F6C5B2C8C1FECDA5C311C95728BAFFF | |||
| 444 | Win8.Horror.Destructive 1.0.exe | C:\Users\admin\AppData\Local\Temp\F0D6.tmp\HorrorGui.exe | executable | |
MD5:B2653AA06A2253E8155EB81535B20E6A | SHA256:B4E106E22C4D3E51C87D3D5853298210572AB2834F5E2A0BEAF1DF7D96C57D29 | |||
| 444 | Win8.Horror.Destructive 1.0.exe | C:\Users\admin\AppData\Local\Temp\F0D6.tmp\TrashMBR.exe | executable | |
MD5:87F09F4A202BF9C0ADCF6FED942AA703 | SHA256:ACF8ABE9BD2F61840A247B4796EBEDAD20F69A85DBDF8A4100F5D7D306B064B1 | |||
| 444 | Win8.Horror.Destructive 1.0.exe | C:\Users\admin\AppData\Local\Temp\F0D6.tmp\Horror8.bat | text | |
MD5:36FCF85EC52716F5FD8EA625A11C13C6 | SHA256:3ABA2D676284209730FF20B28A8415A3C41C88F402301B14437040BF2BAEBE0C | |||
| 444 | Win8.Horror.Destructive 1.0.exe | C:\Users\admin\AppData\Local\Temp\F0D6.tmp\music.vbs | text | |
MD5:8B703F9C48EB3724348AF746E7610061 | SHA256:E8CD555C43973E3B2E6FA0E80D602ABC3D7C43A17BC51A6D0BA08E20EA3FEADD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |