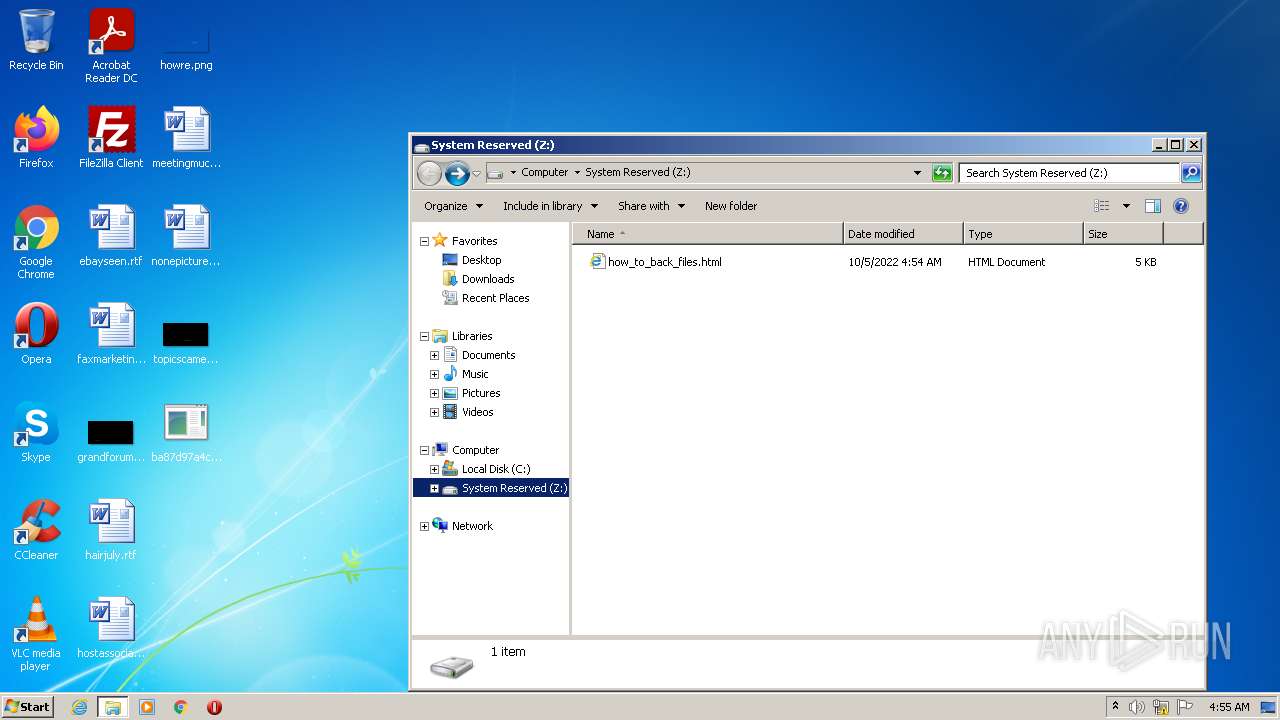
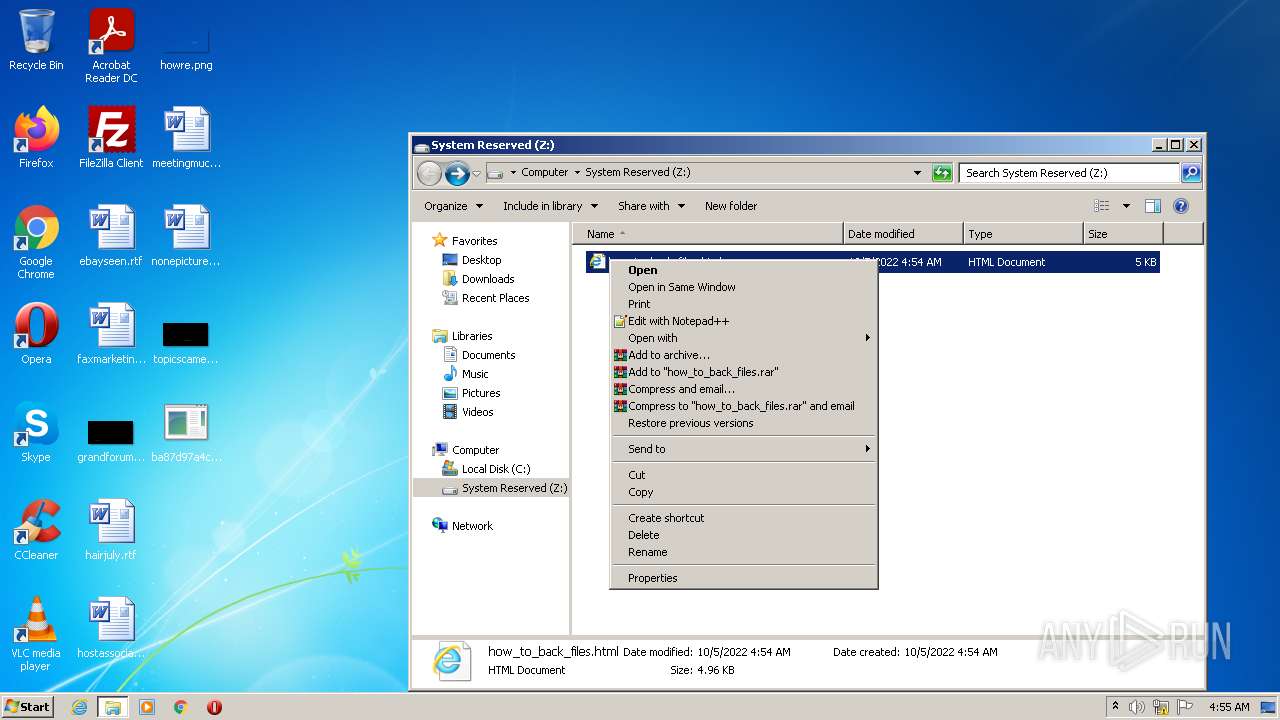
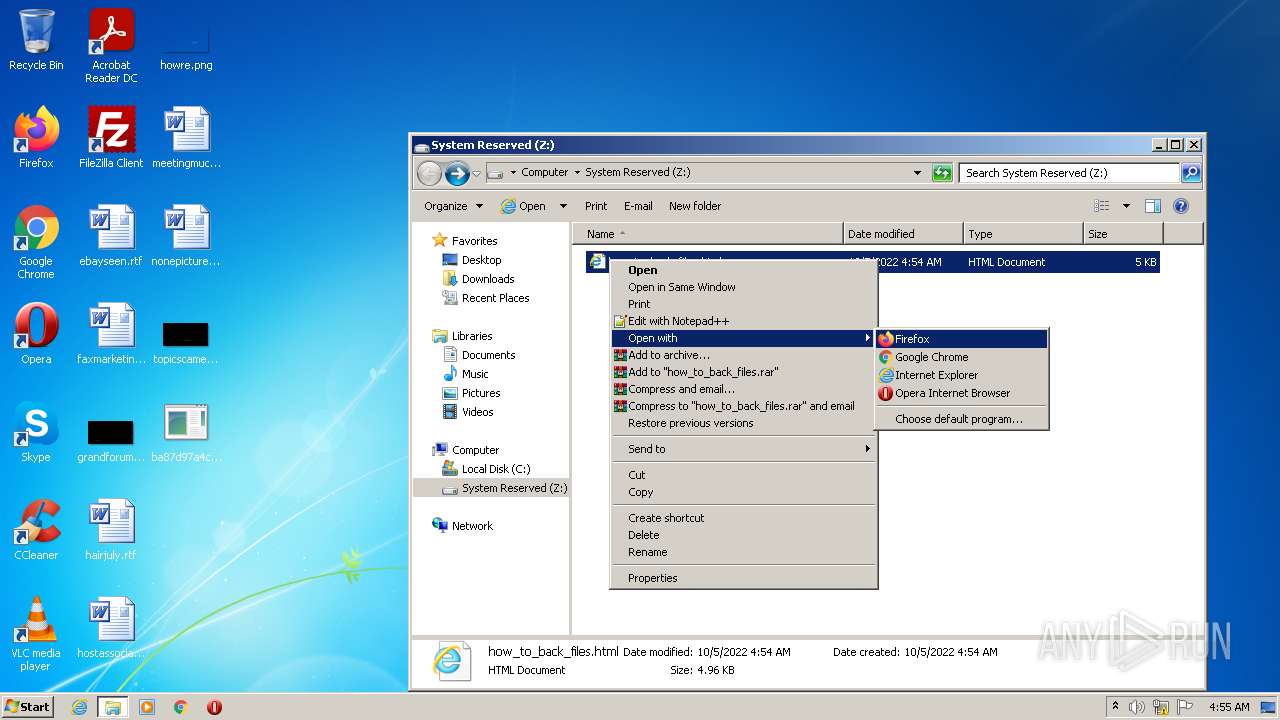
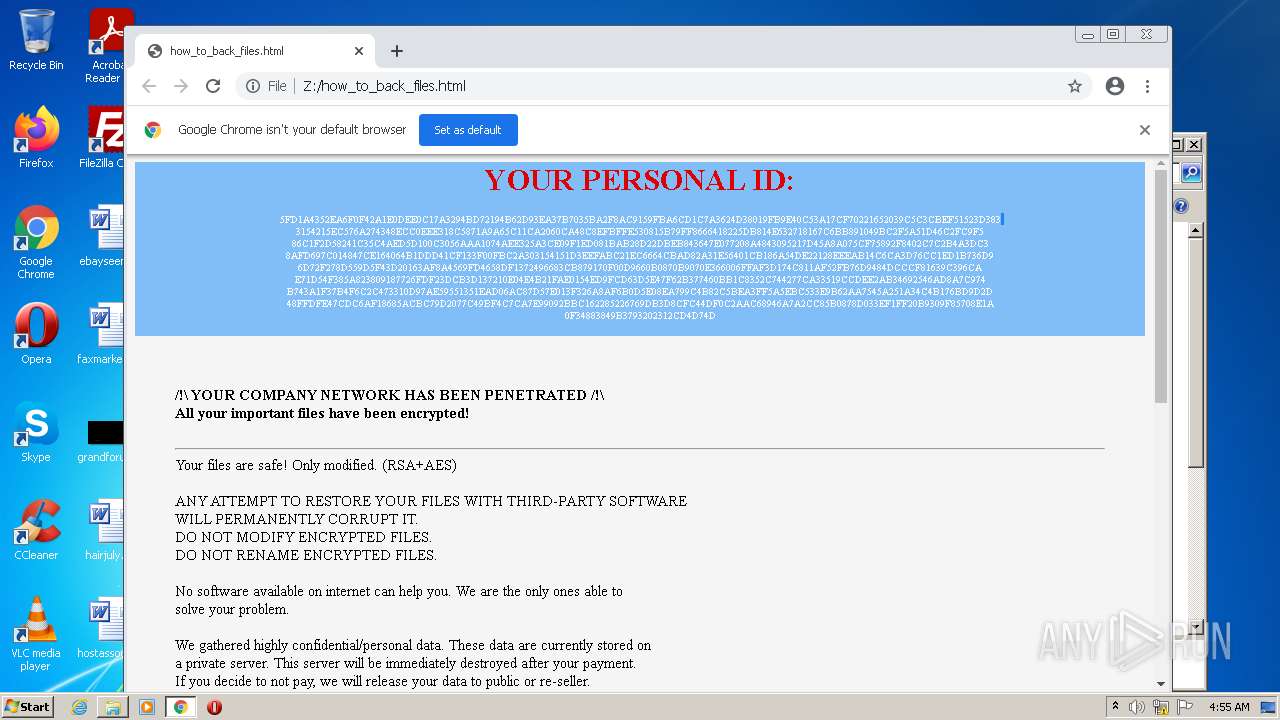
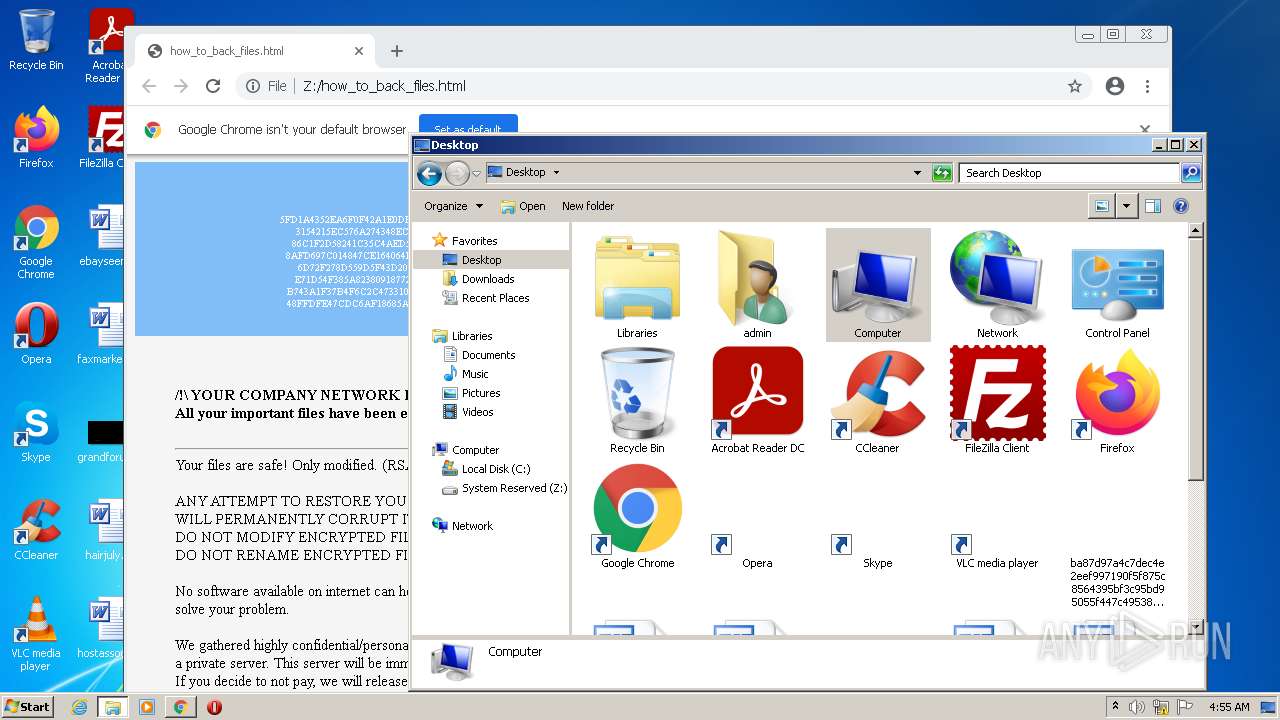
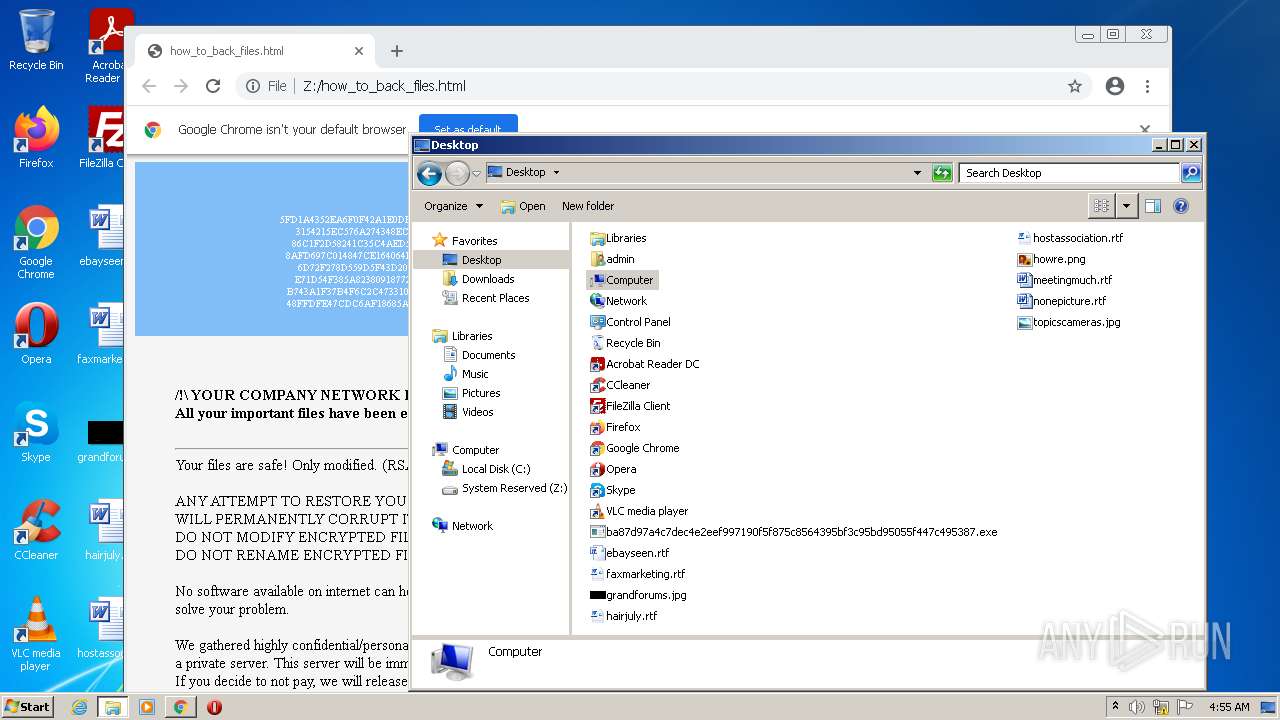
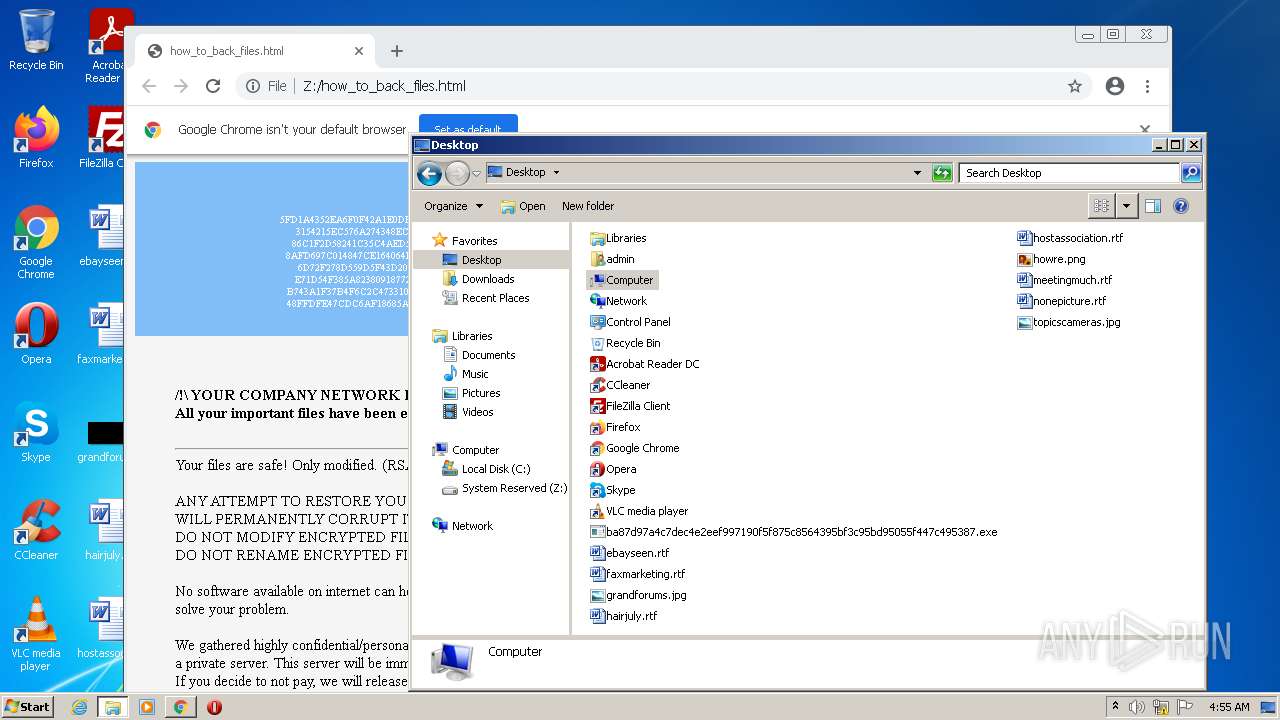
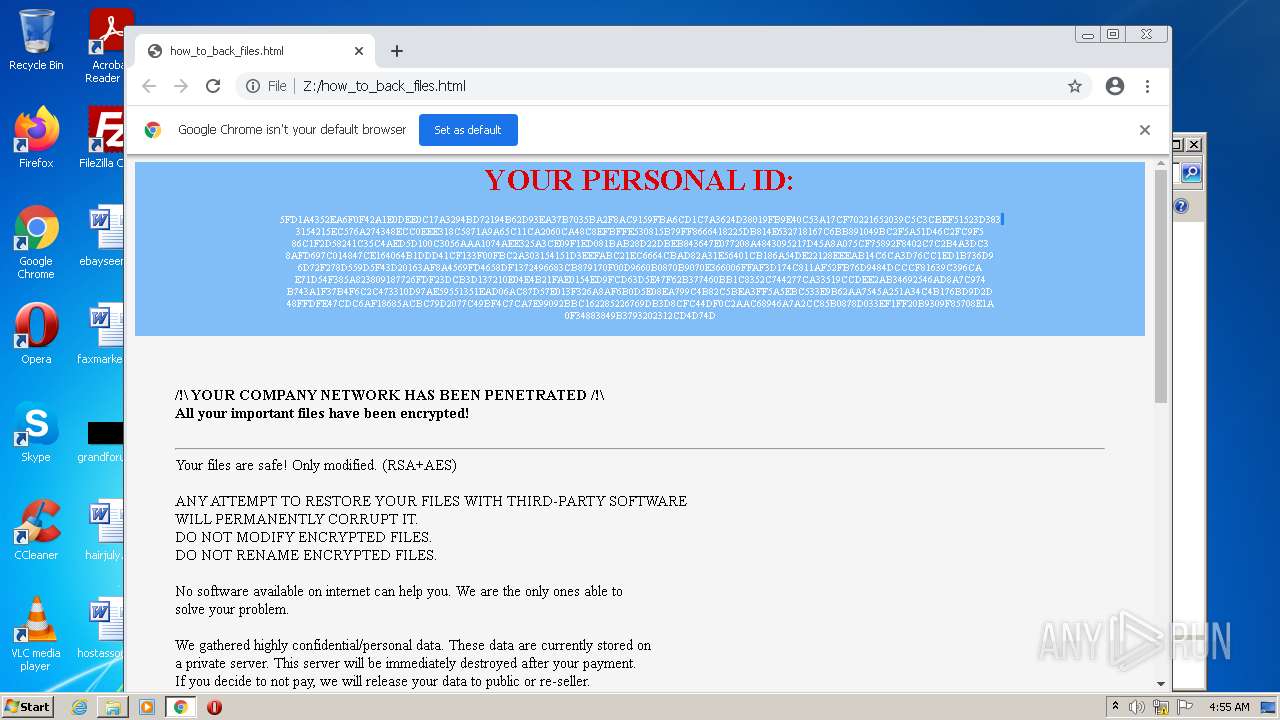
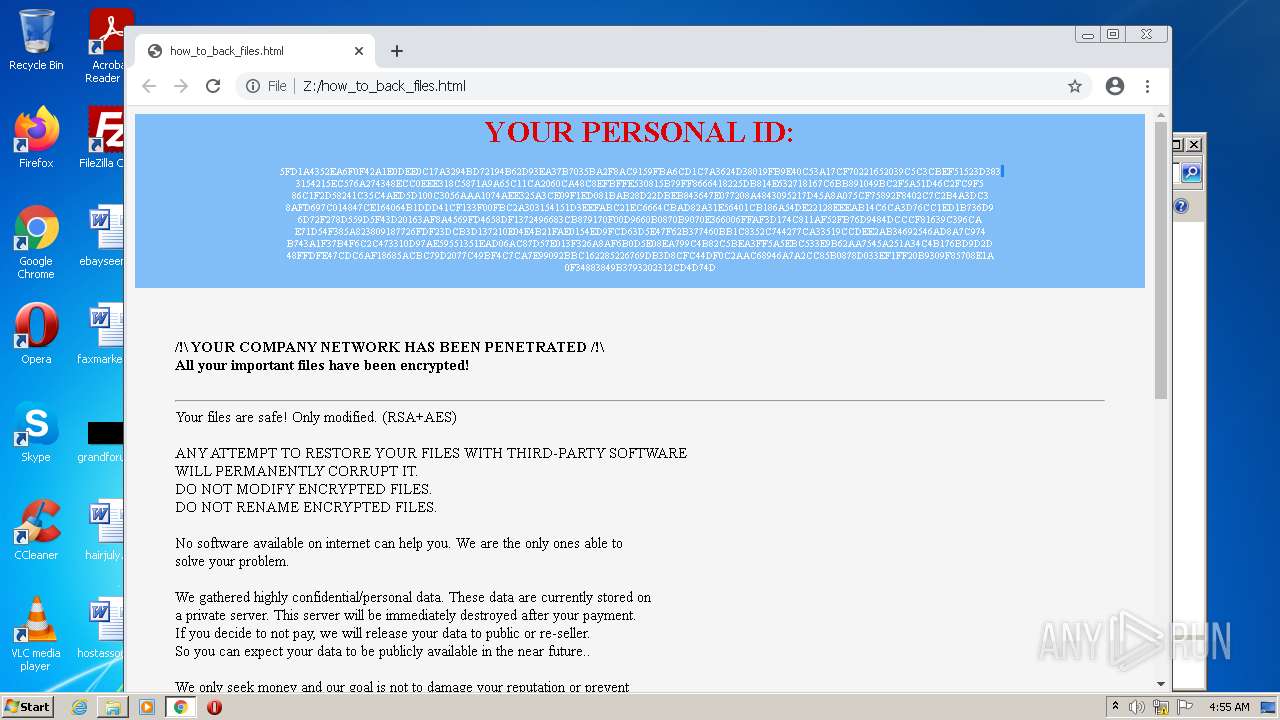
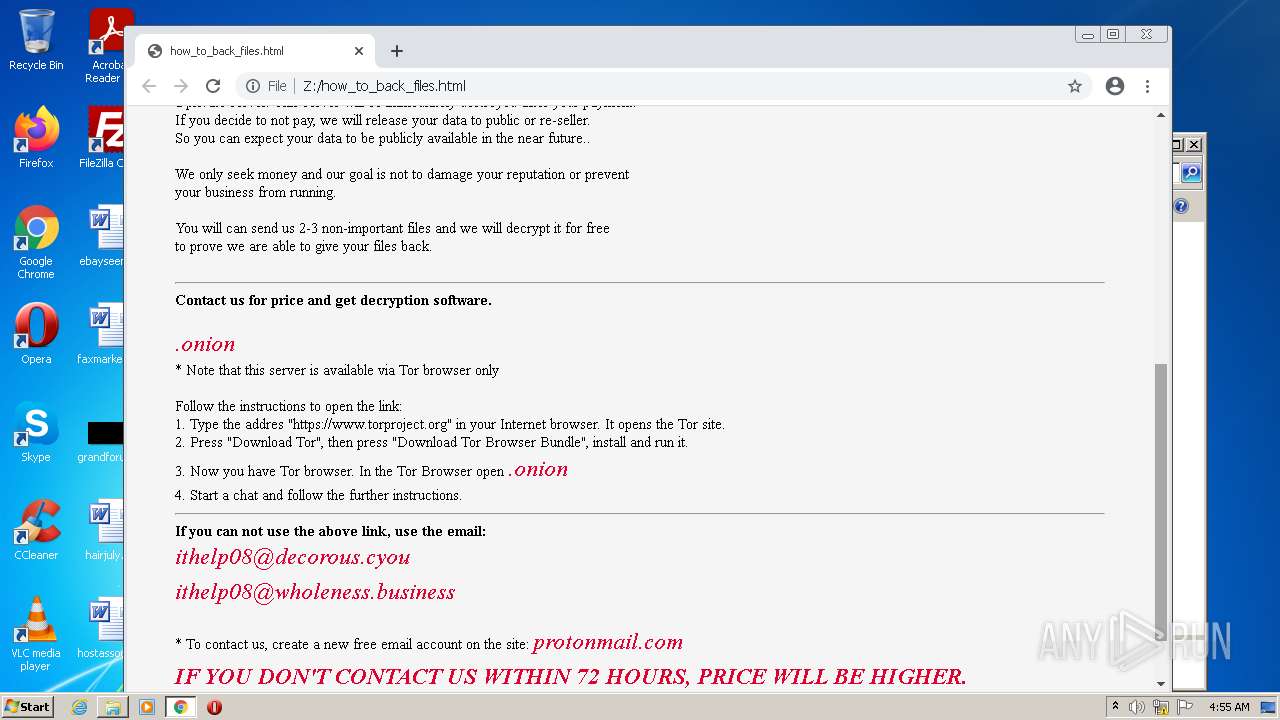
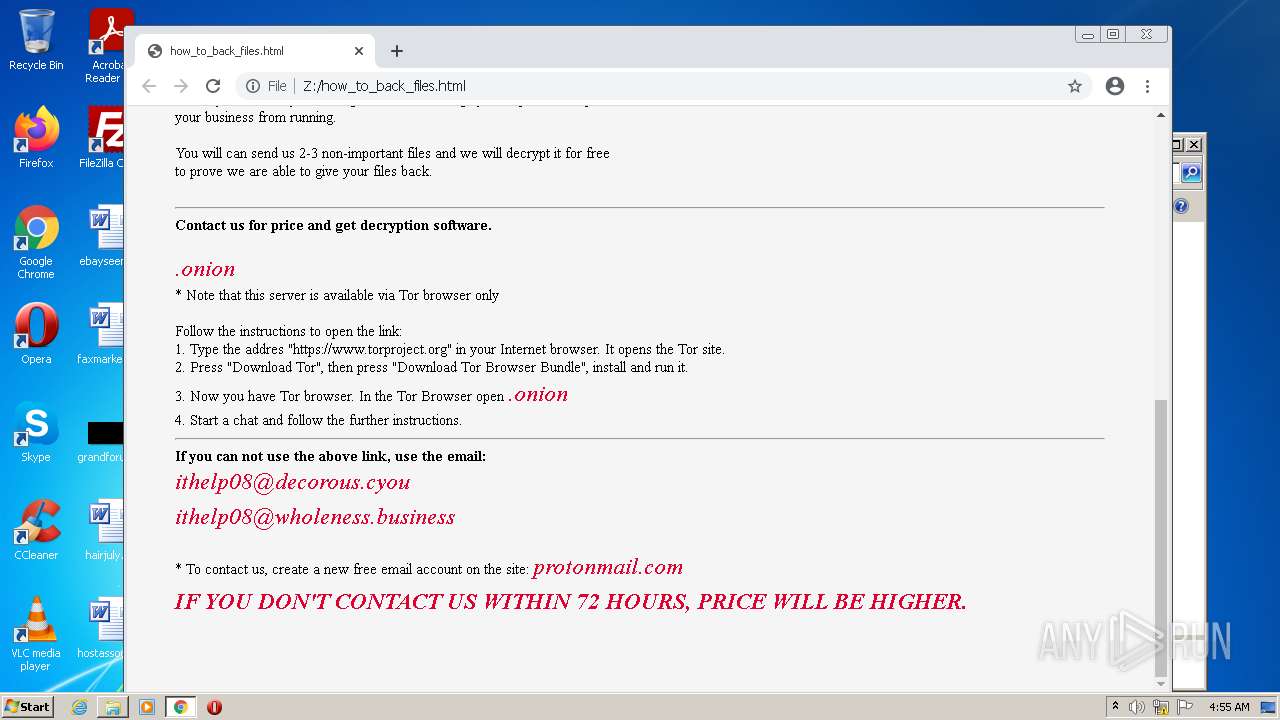
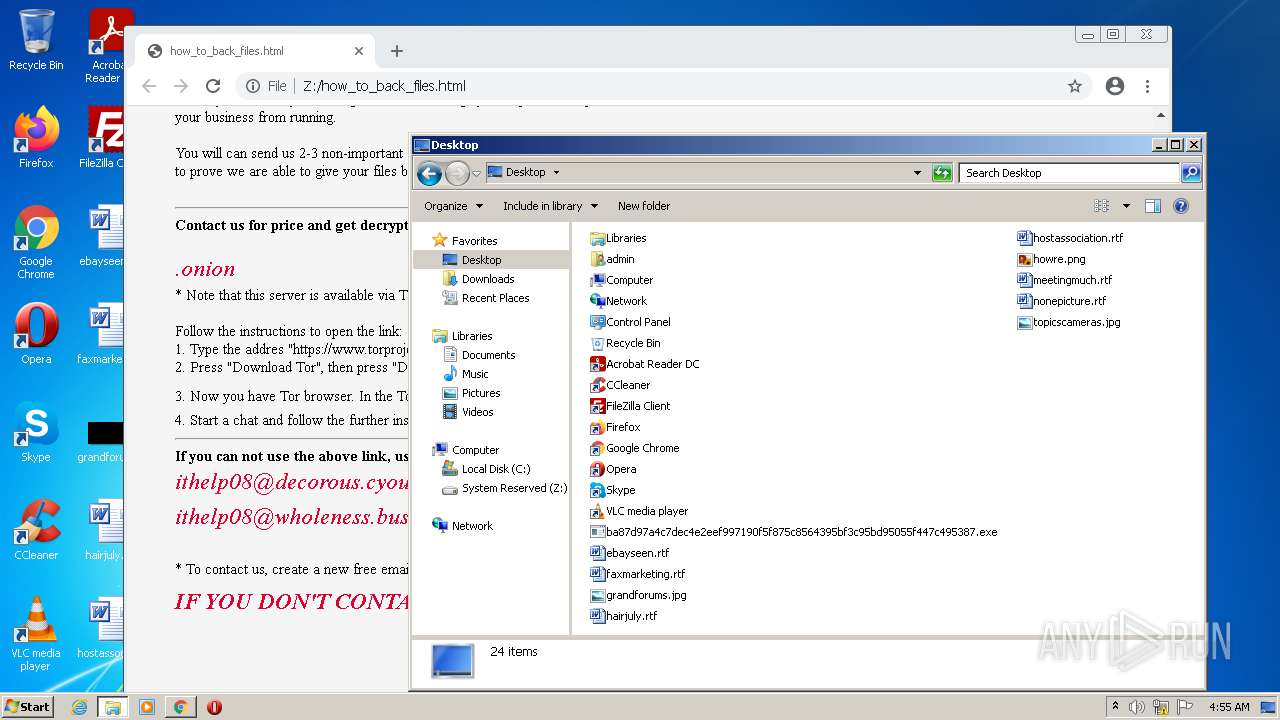
| File name: | ba87d97a4c7dec4e2eef997190f5f875c8564395bf3c95bd95055f447c495387 |
| Full analysis: | https://app.any.run/tasks/ddcfd6de-2f9e-4548-8e45-cc5d714a52fe |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2022, 03:54:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | CFA482B23FA7A59641A6B816D56A3C58 |
| SHA1: | 0CD9753113E29FD460DCDCFFB21F364B3C5A14AA |
| SHA256: | BA87D97A4C7DEC4E2EEF997190F5F875C8564395BF3C95BD95055F447C495387 |
| SSDEEP: | 12288:dQA0FfTcwpBuV2UxqDmuiLZeUaoFi2XZWfGe615HhAZV8DhKD/KeX:Tuf4wTuV2Ux3uIZeUBi2Te6HWMKrKe |
MALICIOUS
UAC/LUA settings modification
- ba87d97a4c7dec4e2eef997190f5f875c8564395bf3c95bd95055f447c495387.exe (PID: 3576)
Known privilege escalation attack
- DllHost.exe (PID: 2304)
Deletes shadow copies
- ba87d97a4c7dec4e2eef997190f5f875c8564395bf3c95bd95055f447c495387.exe (PID: 3576)
Starts BCDEDIT.EXE to disable recovery
- ba87d97a4c7dec4e2eef997190f5f875c8564395bf3c95bd95055f447c495387.exe (PID: 3576)
Loads the Task Scheduler COM API
- ba87d97a4c7dec4e2eef997190f5f875c8564395bf3c95bd95055f447c495387.exe (PID: 3576)
SUSPICIOUS
Checks supported languages
- ba87d97a4c7dec4e2eef997190f5f875c8564395bf3c95bd95055f447c495387.exe (PID: 3576)
- ba87d97a4c7dec4e2eef997190f5f875c8564395bf3c95bd95055f447c495387.exe (PID: 3248)
Creates files in the user directory
- ba87d97a4c7dec4e2eef997190f5f875c8564395bf3c95bd95055f447c495387.exe (PID: 3576)
Reads the computer name
- ba87d97a4c7dec4e2eef997190f5f875c8564395bf3c95bd95055f447c495387.exe (PID: 3248)
- ba87d97a4c7dec4e2eef997190f5f875c8564395bf3c95bd95055f447c495387.exe (PID: 3576)
Executed as Windows Service
- vssvc.exe (PID: 2920)
Creates files in the Windows directory
- wbadmin.exe (PID: 4044)
- wbadmin.exe (PID: 2336)
- wbadmin.exe (PID: 3540)
- wbadmin.exe (PID: 3048)
- wbadmin.exe (PID: 3844)
- wbadmin.exe (PID: 2760)
Removes files from Windows directory
- wbadmin.exe (PID: 3540)
- wbadmin.exe (PID: 3844)
- wbadmin.exe (PID: 2760)
Writes to a desktop.ini file (may be used to cloak folders)
- ba87d97a4c7dec4e2eef997190f5f875c8564395bf3c95bd95055f447c495387.exe (PID: 3576)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2760)
Executed via COM
- DllHost.exe (PID: 2304)
INFO
Checks supported languages
- DllHost.exe (PID: 2304)
- vssadmin.exe (PID: 2664)
- bcdedit.exe (PID: 2460)
- bcdedit.exe (PID: 3828)
- wbadmin.exe (PID: 4044)
- vssvc.exe (PID: 2920)
- vssadmin.exe (PID: 988)
- bcdedit.exe (PID: 3104)
- wmic.exe (PID: 360)
- bcdedit.exe (PID: 2968)
- vssadmin.exe (PID: 2128)
- wbadmin.exe (PID: 3048)
- wbadmin.exe (PID: 3540)
- wmic.exe (PID: 3776)
- bcdedit.exe (PID: 432)
- bcdedit.exe (PID: 280)
- wbadmin.exe (PID: 3844)
- wbadmin.exe (PID: 2760)
- wmic.exe (PID: 2352)
- chrome.exe (PID: 2760)
- chrome.exe (PID: 236)
- chrome.exe (PID: 2108)
- chrome.exe (PID: 1208)
- chrome.exe (PID: 2468)
- chrome.exe (PID: 3600)
- chrome.exe (PID: 1768)
- chrome.exe (PID: 412)
- chrome.exe (PID: 2944)
- chrome.exe (PID: 3340)
- chrome.exe (PID: 316)
- chrome.exe (PID: 3976)
- chrome.exe (PID: 2492)
- wbadmin.exe (PID: 2336)
Reads the computer name
- vssadmin.exe (PID: 2664)
- vssvc.exe (PID: 2920)
- DllHost.exe (PID: 2304)
- wbadmin.exe (PID: 4044)
- wbadmin.exe (PID: 2336)
- vssadmin.exe (PID: 988)
- wmic.exe (PID: 360)
- wbadmin.exe (PID: 3048)
- wbadmin.exe (PID: 3540)
- wmic.exe (PID: 3776)
- vssadmin.exe (PID: 2128)
- wbadmin.exe (PID: 3844)
- wbadmin.exe (PID: 2760)
- wmic.exe (PID: 2352)
- chrome.exe (PID: 2760)
- chrome.exe (PID: 236)
- chrome.exe (PID: 1208)
- chrome.exe (PID: 2944)
- chrome.exe (PID: 412)
- chrome.exe (PID: 2492)
Manual execution by user
- chrome.exe (PID: 2760)
Reads the hosts file
- chrome.exe (PID: 2760)
- chrome.exe (PID: 1208)
Application launched itself
- chrome.exe (PID: 2760)
Reads settings of System Certificates
- chrome.exe (PID: 1208)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2019-Oct-31 06:08:40 |
| Detected languages: |
|
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 144 |
| e_cp: | 3 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | - |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | - |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 272 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 5 |
| TimeDateStamp: | 2019-Oct-31 06:08:40 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 4096 | 469942 | 470016 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.54453 |
.rdata | 475136 | 175538 | 175616 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.69449 |
.data | 651264 | 19304 | 14848 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.77903 |
.rsrc | 671744 | 480 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.70824 |
.reloc | 675840 | 23164 | 23552 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.56882 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.91161 | 381 | UNKNOWN | English - United States | RT_MANIFEST |
Imports
ADVAPI32.dll |
CRYPT32.dll |
IPHLPAPI.DLL |
KERNEL32.dll |
MPR.dll |
NETAPI32.dll |
OLEAUT32.dll |
RstrtMgr.DLL |
SHELL32.dll |
WS2_32.dll |
Total processes
92
Monitored processes
35
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1064,6234371206766742091,7628850936261349308,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1076 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 280 | bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures | C:\Windows\system32\bcdedit.exe | — | ba87d97a4c7dec4e2eef997190f5f875c8564395bf3c95bd95055f447c495387.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 316 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1064,6234371206766742091,7628850936261349308,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3444 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 360 | wmic.exe SHADOWCOPY /nointeractive | C:\Windows\System32\Wbem\wmic.exe | — | ba87d97a4c7dec4e2eef997190f5f875c8564395bf3c95bd95055f447c495387.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 44124 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 412 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1064,6234371206766742091,7628850936261349308,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=2740 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 432 | bcdedit.exe /set {default} recoveryenabled No | C:\Windows\system32\bcdedit.exe | — | ba87d97a4c7dec4e2eef997190f5f875c8564395bf3c95bd95055f447c495387.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 988 | vssadmin.exe Delete Shadows /All /Quiet | C:\Windows\system32\vssadmin.exe | — | ba87d97a4c7dec4e2eef997190f5f875c8564395bf3c95bd95055f447c495387.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1208 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1064,6234371206766742091,7628850936261349308,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1344 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1768 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1064,6234371206766742091,7628850936261349308,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2264 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2108 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=86.0.4240.198 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6d01d988,0x6d01d998,0x6d01d9a4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
17 471
Read events
14 211
Write events
1 680
Delete events
1 580
Modification events
| (PID) Process: | (2304) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2304) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2304) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2304) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3576) ba87d97a4c7dec4e2eef997190f5f875c8564395bf3c95bd95055f447c495387.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (3576) ba87d97a4c7dec4e2eef997190f5f875c8564395bf3c95bd95055f447c495387.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | ConsentPromptBehaviorAdmin |
Value: 0 | |||
| (PID) Process: | (3576) ba87d97a4c7dec4e2eef997190f5f875c8564395bf3c95bd95055f447c495387.exe | Key: | HKEY_CURRENT_USER\Software\MDSLK |
| Operation: | write | Name: | Self |
Value: ba87d97a4c7dec4e2eef997190f5f875c8564395bf3c95bd95055f447c495387.exe | |||
| (PID) Process: | (2460) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\16000009 |
| Operation: | write | Name: | Element |
Value: 00 | |||
| (PID) Process: | (3828) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\250000e0 |
| Operation: | write | Name: | Element |
Value: 0100000000000000 | |||
| (PID) Process: | (2968) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\16000009 |
| Operation: | write | Name: | Element |
Value: 00 | |||
Executable files
1
Suspicious files
458
Text files
146
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4044 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.1.etl | etl | |
MD5:— | SHA256:— | |||
| 2336 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.0.etl | etl | |
MD5:— | SHA256:— | |||
| 2336 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.2.etl | etl | |
MD5:— | SHA256:— | |||
| 3048 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.1.etl | etl | |
MD5:— | SHA256:— | |||
| 3048 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.0.etl | etl | |
MD5:— | SHA256:— | |||
| 4044 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.0.etl | etl | |
MD5:— | SHA256:— | |||
| 3048 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.3.etl | etl | |
MD5:— | SHA256:— | |||
| 3048 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.2.etl | etl | |
MD5:— | SHA256:— | |||
| 3540 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.0.etl | etl | |
MD5:— | SHA256:— | |||
| 2336 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.1.etl | etl | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
16
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1208 | chrome.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | crx | 242 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1208 | chrome.exe | 172.217.17.206:443 | clients2.google.com | GOOGLE | US | whitelisted |
— | — | 192.168.100.2:445 | — | — | — | whitelisted |
1208 | chrome.exe | 216.58.206.193:443 | clients2.googleusercontent.com | GOOGLE | US | whitelisted |
1208 | chrome.exe | 34.104.35.123:80 | edgedl.me.gvt1.com | GOOGLE | US | whitelisted |
1208 | chrome.exe | 142.250.187.163:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
1208 | chrome.exe | 172.217.169.109:443 | accounts.google.com | GOOGLE | US | whitelisted |
1208 | chrome.exe | 142.250.187.131:443 | update.googleapis.com | GOOGLE | US | whitelisted |
— | — | 192.168.100.2:139 | — | — | — | whitelisted |
1208 | chrome.exe | 172.217.20.67:443 | ssl.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
clients2.google.com |
| whitelisted |
accounts.google.com |
| shared |
clients2.googleusercontent.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
edgedl.me.gvt1.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |