| URL: | https://www.iobit.com/appgoto.php?name=asc&ver=16.4.0.225&lan=&to=update&idata=eyJhc2MiOjEsImRiIjoxLCJpbWYiOjEwLCJpdSI6MTAsInNkIjoxLCJpc3UiOjEwfQ%3D%3D&usr=2&instd=295&litype=free&expd=0&insur=sd_defrag |
| Full analysis: | https://app.any.run/tasks/e3738e03-36d6-4d3b-8422-8bea0d3d1ca7 |
| Verdict: | Malicious activity |
| Analysis date: | March 28, 2024, 15:23:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 8E49EE39B340AD9828121B0E57F0B780 |
| SHA1: | 1B923F9F38448DDB97BDF6FE62E5173ED27E86EA |
| SHA256: | BA749ADFF0D95D917C38B7F3312D4507FCD3ED618F17CE99D18CD56E8AE614A6 |
| SSDEEP: | 6:2OLgPBIZ9/P6Euhp4Hy8rCdGmNGMq5cVPNm:2eZ9X6EufKy8rCdxs5um |
MALICIOUS
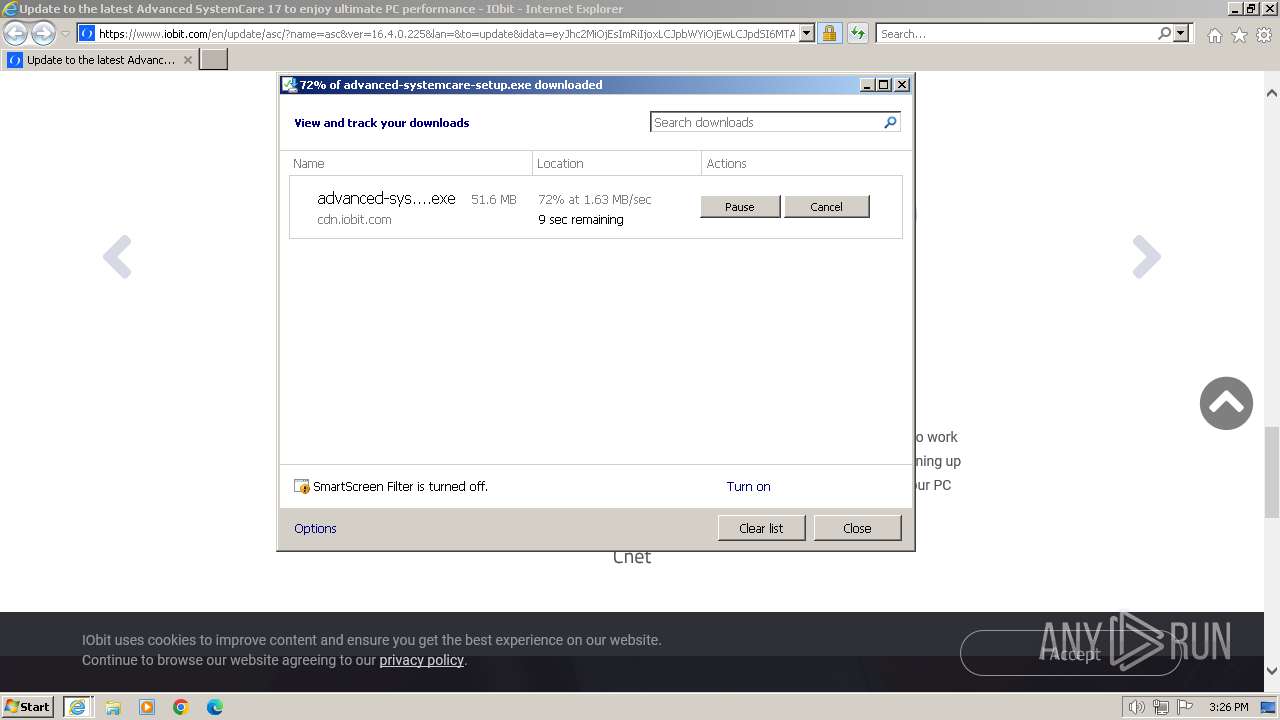
Drops the executable file immediately after the start
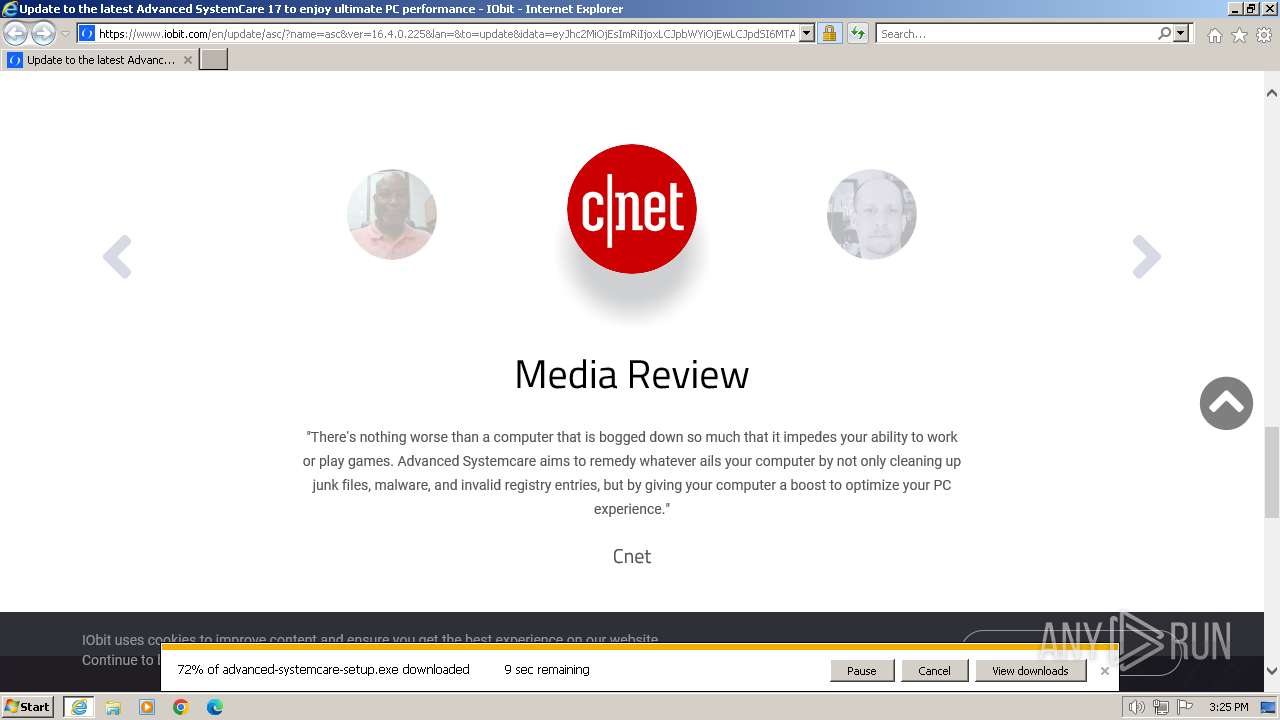
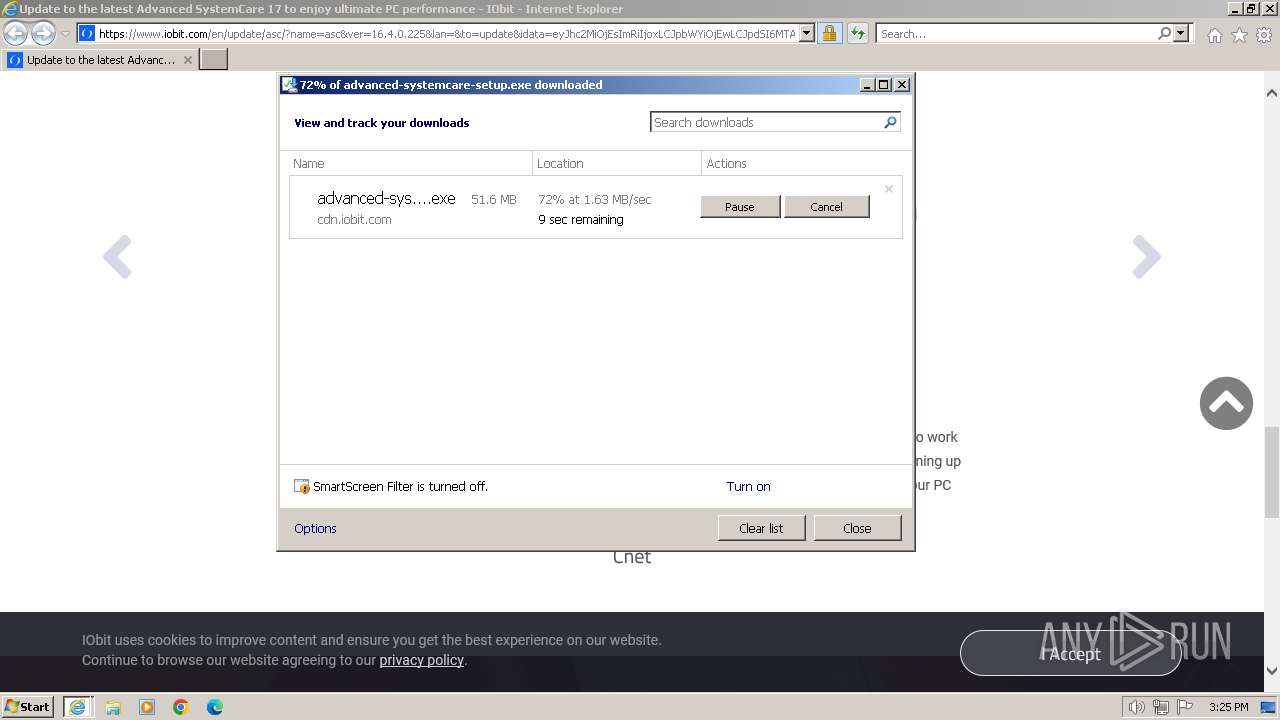
- advanced-systemcare-setup.exe (PID: 3336)
- advanced-systemcare-setup.exe (PID: 584)
- advanced-systemcare-setup.tmp (PID: 2028)
- advanced-systemcare-setup.exe (PID: 3156)
- ASCInit.exe (PID: 1192)
- advanced-systemcare-setup.tmp (PID: 3096)
- Monitor.exe (PID: 3556)
Creates a writable file in the system directory
- smBootTimebase.exe (PID: 4028)
Steals credentials from Web Browsers
- smBootTimebase.exe (PID: 4028)
- PPUninstaller.exe (PID: 2260)
Actions looks like stealing of personal data
- smBootTimebase.exe (PID: 4028)
- ASCService.exe (PID: 3772)
- PPUninstaller.exe (PID: 2260)
Registers / Runs the DLL via REGSVR32.EXE
- ASCInit.exe (PID: 1192)
Changes the autorun value in the registry
- ASCInit.exe (PID: 1192)
SUSPICIOUS
Reads the Windows owner or organization settings
- advanced-systemcare-setup.tmp (PID: 2028)
- advanced-systemcare-setup.tmp (PID: 3096)
- smBootTime.exe (PID: 3072)
- smBootTime.exe (PID: 900)
Reads the Internet Settings
- advanced-systemcare-setup.tmp (PID: 2028)
- advanced-systemcare-setup.tmp (PID: 3096)
- ASCInit.exe (PID: 1192)
- Setup.exe (PID: 1316)
Reads security settings of Internet Explorer
- advanced-systemcare-setup.tmp (PID: 2028)
- advanced-systemcare-setup.tmp (PID: 3096)
- ASCInit.exe (PID: 1192)
- Setup.exe (PID: 1316)
Process drops SQLite DLL files
- advanced-systemcare-setup.tmp (PID: 3096)
Searches for installed software
- advanced-systemcare-setup.tmp (PID: 3096)
- smBootTimebase.exe (PID: 4028)
- PrivacyShield.exe (PID: 3200)
- UninstallInfo.exe (PID: 3892)
- ASCService.exe (PID: 3772)
- smBootTime.exe (PID: 3072)
- PPUninstaller.exe (PID: 2260)
- smBootTime.exe (PID: 900)
- Setup.exe (PID: 1316)
- BrowserProtect.exe (PID: 2160)
Executes as Windows Service
- ASCService.exe (PID: 3772)
Starts CMD.EXE for commands execution
- ASCInit.exe (PID: 1192)
Starts SC.EXE for service management
- cmd.exe (PID: 292)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 3916)
Reads the date of Windows installation
- ASCInit.exe (PID: 1192)
- PPUninstaller.exe (PID: 2260)
Application launched itself
- RealTimeProtector.exe (PID: 3584)
INFO
Drops the executable file immediately after the start
- iexplore.exe (PID: 1556)
Application launched itself
- iexplore.exe (PID: 2120)
- msedge.exe (PID: 2164)
- msedge.exe (PID: 2332)
The process uses the downloaded file
- iexplore.exe (PID: 2120)
Checks supported languages
- advanced-systemcare-setup.exe (PID: 3336)
- advanced-systemcare-setup.tmp (PID: 4080)
- advanced-systemcare-setup.exe (PID: 584)
- advanced-systemcare-setup.tmp (PID: 2028)
- Setup.exe (PID: 1316)
- advanced-systemcare-setup.tmp (PID: 3096)
- advanced-systemcare-setup.exe (PID: 3156)
- ASCUpgrade.exe (PID: 3016)
- LocalLang.exe (PID: 3880)
- ASCInit.exe (PID: 1192)
- ASCService.exe (PID: 3772)
- ASCUpgrade.exe (PID: 3024)
- smBootTimebase.exe (PID: 4028)
- UninstallInfo.exe (PID: 3892)
- BrowserCleaner.exe (PID: 3428)
- PrivacyShield.exe (PID: 3200)
- PPUninstaller.exe (PID: 2260)
- RealTimeProtector.exe (PID: 3584)
- RealTimeProtector.exe (PID: 2968)
- smBootTime.exe (PID: 3072)
- DiskDefrag.exe (PID: 2888)
- RealTimeProtector.exe (PID: 3796)
- smBootTime.exe (PID: 900)
- BrowserProtect.exe (PID: 2160)
- ASC.exe (PID: 3676)
Reads the computer name
- advanced-systemcare-setup.tmp (PID: 4080)
- advanced-systemcare-setup.tmp (PID: 2028)
- Setup.exe (PID: 1316)
- advanced-systemcare-setup.tmp (PID: 3096)
- ASCUpgrade.exe (PID: 3016)
- ASCService.exe (PID: 3772)
- ASCInit.exe (PID: 1192)
- ASCUpgrade.exe (PID: 3024)
- smBootTimebase.exe (PID: 4028)
- UninstallInfo.exe (PID: 3892)
- PrivacyShield.exe (PID: 3200)
- RealTimeProtector.exe (PID: 3584)
- PPUninstaller.exe (PID: 2260)
- smBootTime.exe (PID: 3072)
- RealTimeProtector.exe (PID: 2968)
- smBootTime.exe (PID: 900)
- RealTimeProtector.exe (PID: 3796)
- BrowserProtect.exe (PID: 2160)
- ASC.exe (PID: 3676)
Create files in a temporary directory
- advanced-systemcare-setup.exe (PID: 3336)
- advanced-systemcare-setup.exe (PID: 584)
- advanced-systemcare-setup.tmp (PID: 2028)
- advanced-systemcare-setup.exe (PID: 3156)
- Setup.exe (PID: 1316)
- advanced-systemcare-setup.tmp (PID: 3096)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2120)
Creates files or folders in the user directory
- advanced-systemcare-setup.tmp (PID: 2028)
- Setup.exe (PID: 1316)
- advanced-systemcare-setup.tmp (PID: 3096)
- ASCInit.exe (PID: 1192)
- ASCService.exe (PID: 3772)
- BrowserCleaner.exe (PID: 3428)
- UninstallInfo.exe (PID: 3892)
- PPUninstaller.exe (PID: 2260)
Creates files in the program directory
- Setup.exe (PID: 1316)
- ASCInit.exe (PID: 1192)
- advanced-systemcare-setup.tmp (PID: 3096)
- smBootTimebase.exe (PID: 4028)
- ASCService.exe (PID: 3772)
- UninstallInfo.exe (PID: 3892)
- PrivacyShield.exe (PID: 3200)
- smBootTime.exe (PID: 3072)
- BrowserProtect.exe (PID: 2160)
- ASC.exe (PID: 3676)
Dropped object may contain TOR URL's
- advanced-systemcare-setup.tmp (PID: 3096)
Creates a software uninstall entry
- advanced-systemcare-setup.tmp (PID: 3096)
Reads the machine GUID from the registry
- smBootTimebase.exe (PID: 4028)
- ASCInit.exe (PID: 1192)
- PPUninstaller.exe (PID: 2260)
Reads Environment values
- ASCInit.exe (PID: 1192)
Manual execution by a user
- msedge.exe (PID: 2332)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
104
Monitored processes
58
Malicious processes
10
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | "C:\Windows\System32\cmd.exe" /c SC description AdvancedSystemCareService17 "Advanced SystemCare Service" | C:\Windows\System32\cmd.exe | — | ASCInit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 584 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\advanced-systemcare-setup.exe" /SPAWNWND=$D01E2 /NOTIFYWND=$1C0164 | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\advanced-systemcare-setup.exe | advanced-systemcare-setup.tmp | ||||||||||||
User: admin Company: IObit Integrity Level: HIGH Description: Advanced SystemCare Exit code: 0 Version: 17.3.0.204 Modules
| |||||||||||||||
| 584 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1456 --field-trial-handle=1472,i,824996902456420871,6367661493885491088,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 109.0.1518.115 | |||||||||||||||
| 848 | "C:\Program Files\IObit\Advanced SystemCare\ASCFeature.exe" /u http://stats.iobit.com/active_month.php /a asc17 /p iobit /v 17.3.0.204 /t 1 /d 7 | C:\Program Files\IObit\Advanced SystemCare\ASCFeature.exe | — | ASC.exe | |||||||||||
User: admin Company: IObit Integrity Level: HIGH Description: IObit ASCFeature Exit code: 0 Version: 15.0.0.3 | |||||||||||||||
| 900 | "C:\Program Files\IObit\Advanced SystemCare\smBootTime.exe" /start | C:\Program Files\IObit\Advanced SystemCare\smBootTime.exe | ASCService.exe | ||||||||||||
User: admin Company: IObit Integrity Level: HIGH Description: Startup Boot Time Exit code: 0 Version: 16.0.0.44 Modules
| |||||||||||||||
| 1192 | "C:\Program Files\IObit\Advanced SystemCare\ASCInit.exe" /install /CreateTaskBar /Installer=true /insur= | C:\Program Files\IObit\Advanced SystemCare\ASCInit.exe | advanced-systemcare-setup.tmp | ||||||||||||
User: admin Company: IObit Integrity Level: HIGH Description: Advanced SystemCare Initialization Exit code: 0 Version: 14.0.0.170 Modules
| |||||||||||||||
| 1316 | "C:\Users\admin\AppData\Local\Temp\is-M9A8N.tmp\Installer\Setup.exe" /InnoSetup "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\advanced-systemcare-setup.exe" | C:\Users\admin\AppData\Local\Temp\is-M9A8N.tmp\Installer\Setup.exe | advanced-systemcare-setup.tmp | ||||||||||||
User: admin Company: IObit Integrity Level: HIGH Description: Advanced SystemCare Installer Exit code: 0 Version: 17.0.0.84 Modules
| |||||||||||||||
| 1408 | "C:\Program Files\IObit\Advanced SystemCare\ProductStat3.exe" /statcom /stflag 363 /appid "asc17" /pd "asc" /url "http://stats.iobit.com/usage_v2.php?action=insert" /user 0 /insur "other" /type 1 /pr "iobit" /ver "17.3.0.204" | C:\Program Files\IObit\Advanced SystemCare\ProductStat3.exe | — | ASC.exe | |||||||||||
User: admin Company: IObit Integrity Level: HIGH Description: IObit stat Component Exit code: 0 Version: 3.0.0.6398 | |||||||||||||||
| 1556 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2120 CREDAT:267543 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1596 | "C:\Program Files\IObit\Advanced SystemCare\ActionCenterDownloader.exe" /Product=ASC17 "/Config=http://update.iobit.com/infofiles/installer/Freeware-asc.upt" "iTop VPN Installer B" "iTop Data Recovery Installer" "Driver Booster Installer" | C:\Program Files\IObit\Advanced SystemCare\ActionCenterDownloader.exe | — | Setup.exe | |||||||||||
User: admin Company: IObit Integrity Level: HIGH Description: IObit Downloader Version: 16.0.16.139 | |||||||||||||||
Total events
89 295
Read events
88 703
Write events
547
Delete events
45
Modification events
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31097123 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 103322046 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31097124 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
286
Suspicious files
79
Text files
596
Unknown types
89
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\75CA58072B9926F763A91F0CC2798706_B5D3A17E5BEDD2EDA793611A0A74E1E8 | binary | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_B5D3A17E5BEDD2EDA793611A0A74E1E8 | binary | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D03E46CD585BBE111C712E6577BC5F07_B0E62F3370DEB32FD1A99D49E8486B4C | binary | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D03E46CD585BBE111C712E6577BC5F07_B0E62F3370DEB32FD1A99D49E8486B4C | binary | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\62RRP814.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
66
TCP/UDP connections
91
DNS requests
67
Threats
37
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3092 | iexplore.exe | GET | 304 | 217.20.56.98:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7f30423e8f7249ff | unknown | — | — | unknown |
3092 | iexplore.exe | GET | 200 | 18.165.185.182:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | unknown | — | — | unknown |
3092 | iexplore.exe | GET | 200 | 18.165.184.219:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | — | — | unknown |
3092 | iexplore.exe | GET | 304 | 217.20.56.98:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5259f1aa84763c8c | unknown | — | — | unknown |
3092 | iexplore.exe | GET | 200 | 18.165.184.219:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEjgLnWaIozse2b%2BczaaODg8%3D | unknown | — | — | unknown |
3092 | iexplore.exe | GET | 200 | 18.165.189.160:80 | http://ocsp.r2m01.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBShdVEFnSEQ0gG5CBtzM48cPMe9XwQUgbgOY4qJEhjl%2Bjs7UJWf5uWQE4UCEAMpJs%2BO%2FhUI93RIOUqmQvI%3D | unknown | — | — | unknown |
3092 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | unknown |
3092 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDpjUVCgnd2whD%2FCYt5X90R | unknown | — | — | unknown |
3092 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | — | — | unknown |
3092 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEHbOEmPcnJ2%2BEsGo2UIm5Ag%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3092 | iexplore.exe | 52.55.134.231:443 | www.iobit.com | AMAZON-AES | US | unknown |
3092 | iexplore.exe | 217.20.56.98:80 | ctldl.windowsupdate.com | — | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3092 | iexplore.exe | 18.165.185.182:80 | o.ss2.us | — | US | unknown |
3092 | iexplore.exe | 18.165.184.219:80 | ocsp.rootg2.amazontrust.com | — | US | unknown |
3092 | iexplore.exe | 18.165.189.160:80 | ocsp.r2m01.amazontrust.com | — | US | unknown |
3092 | iexplore.exe | 142.250.185.72:443 | www.googletagmanager.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.iobit.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.r2m01.amazontrust.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
codes.iobit.com |
| whitelisted |
kit.fontawesome.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1316 | Setup.exe | Potentially Bad Traffic | ET HUNTING Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
1316 | Setup.exe | Potentially Bad Traffic | ET HUNTING Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
1316 | Setup.exe | Potentially Bad Traffic | ET HUNTING Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
1316 | Setup.exe | Potentially Bad Traffic | ET HUNTING Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
1316 | Setup.exe | Potentially Bad Traffic | ET HUNTING Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
1316 | Setup.exe | Potentially Bad Traffic | ET HUNTING Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
1316 | Setup.exe | Potentially Bad Traffic | ET HUNTING Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
1316 | Setup.exe | Potentially Bad Traffic | ET HUNTING Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
1316 | Setup.exe | Potentially Bad Traffic | ET HUNTING Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
— | — | Potentially Bad Traffic | ET HUNTING Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
Process | Message |
|---|---|
Setup.exe | ********** FLanguageName: English |
Setup.exe | CheckDiskSpace: 1 |
Setup.exe | LoadUserConfig: 1 |
Setup.exe | CheckDiskSpace: 5 |
Setup.exe | GetDownloadPath: 2 |
Setup.exe | CheckDiskSpace: 3 |
Setup.exe | CheckDiskSpace: 5 |
Setup.exe | CheckDiskSpace: 5 |
Setup.exe | CheckDiskSpace: 4 |
Setup.exe | CheckDiskSpace: 2 |