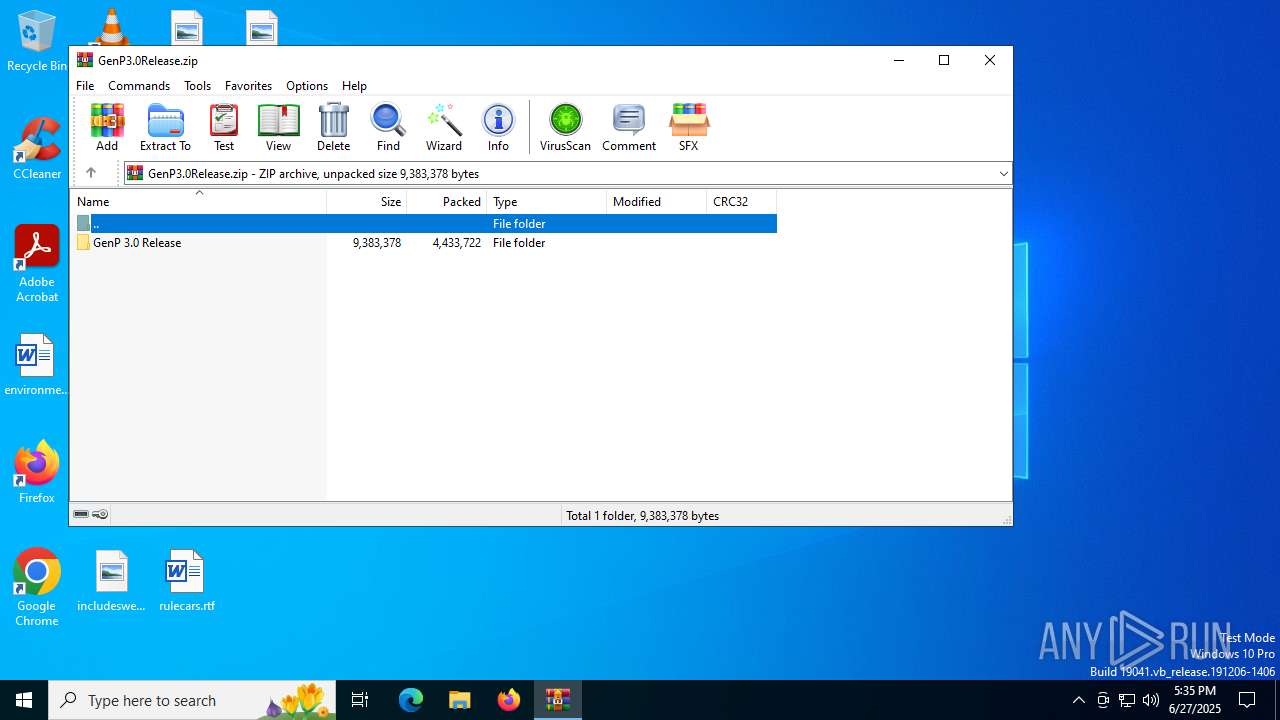
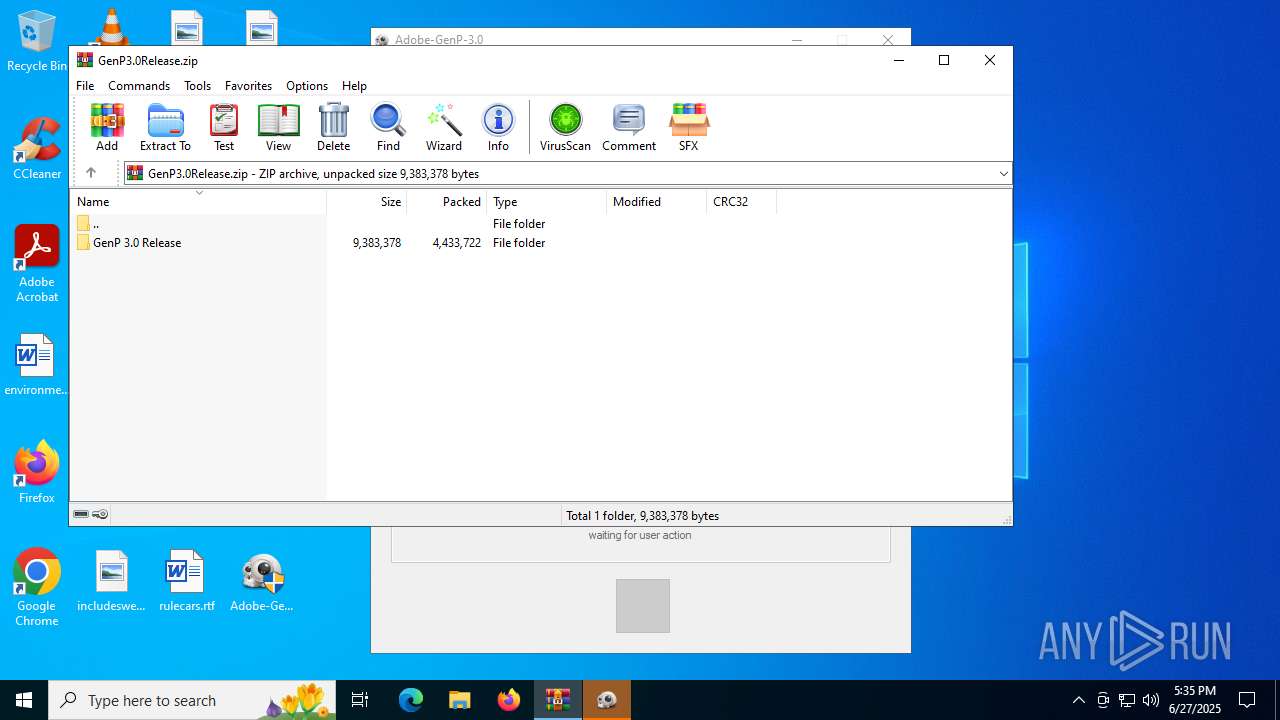
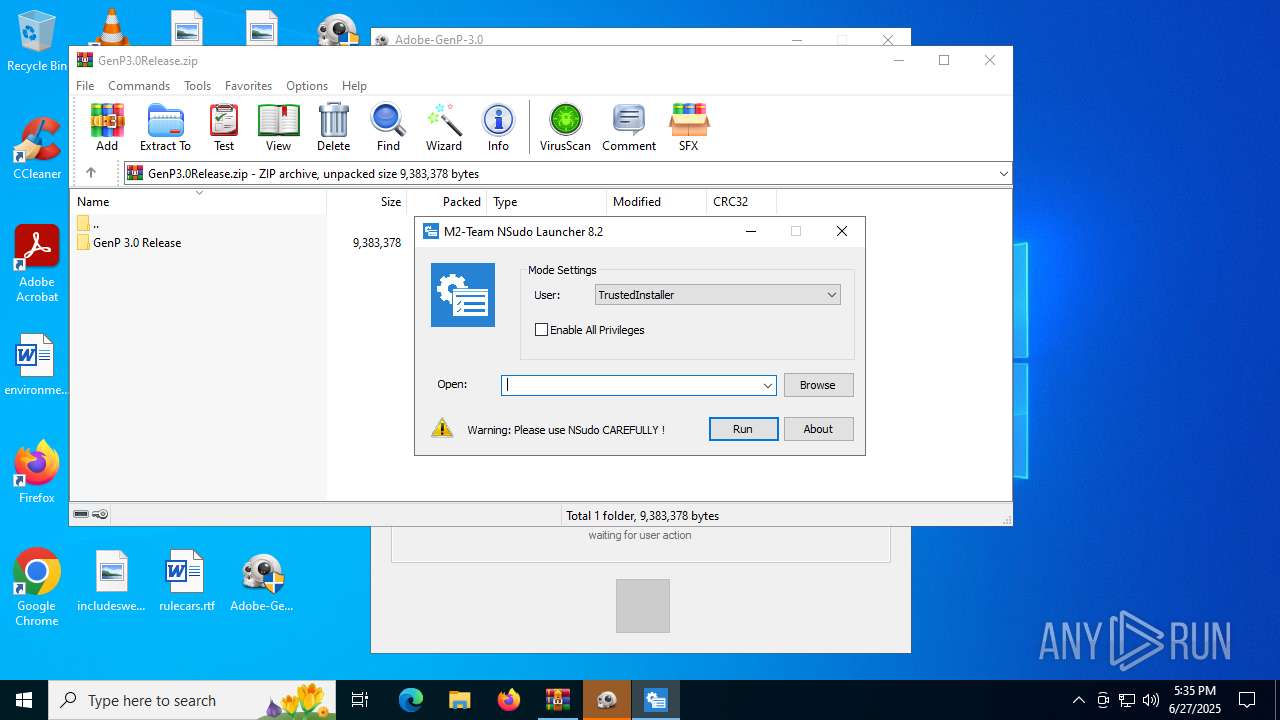
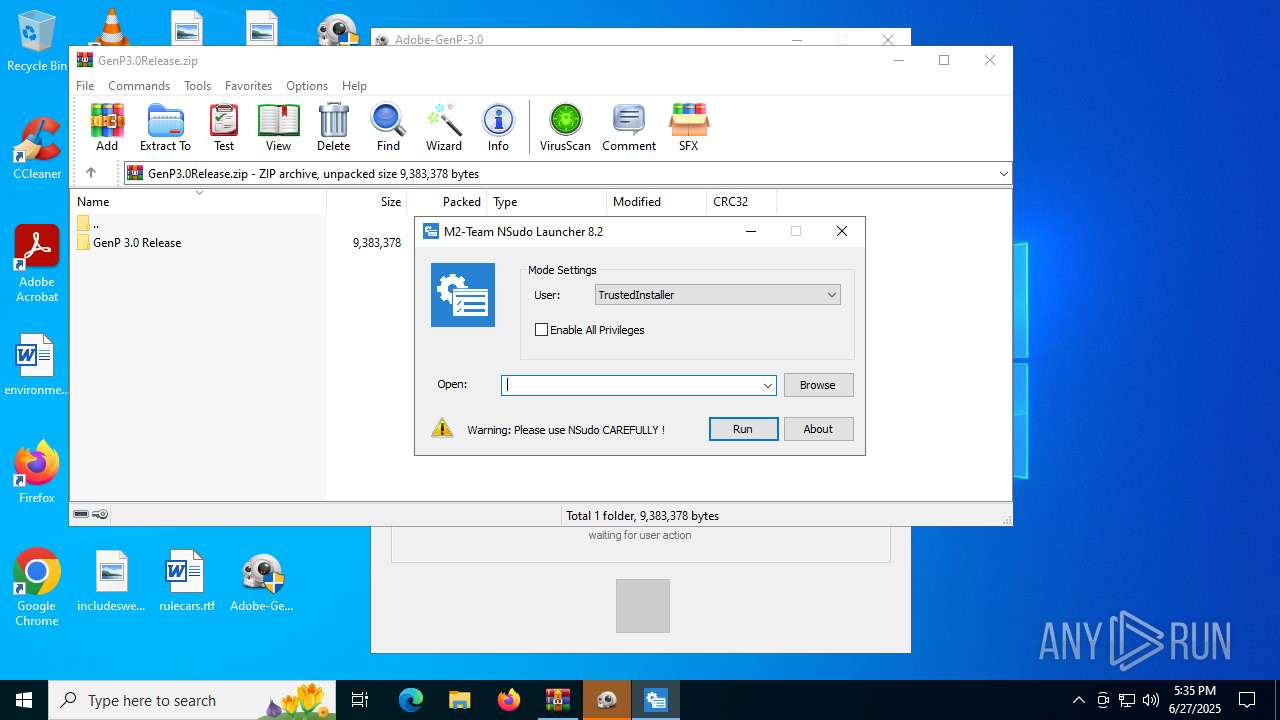
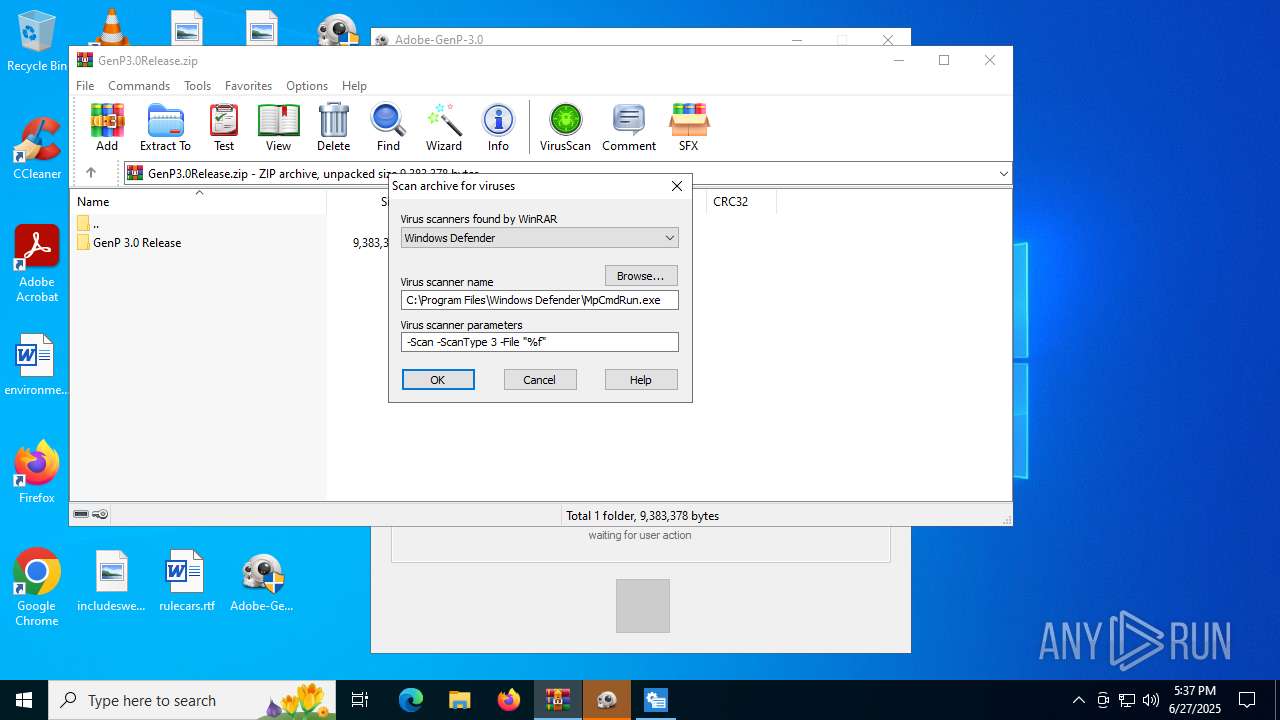
| File name: | GenP3.0Release.zip |
| Full analysis: | https://app.any.run/tasks/c49615d8-80f4-4583-86d6-0a0b7803978f |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2025, 17:35:18 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | F78A9965B1EF6FB2ED878D3E9A4C2AF3 |
| SHA1: | 0B0C502A5079B2357E0D330427DEB4D5B24EF071 |
| SHA256: | BA734CEA2D9B594B4028E94F7A396F0380FBDDE68DF026B5BD26D00A3F067C81 |
| SSDEEP: | 98304:0lRgEGmPg0ipktIzHh38s8ofc3Br9eLJkouhNv1TFARiNx:0jgzmPg0ipDLms8eMJ9eLRsv1q8f |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6428)
Changes powershell execution policy (RemoteSigned)
- cmd.exe (PID: 4820)
Bypass execution policy to execute commands
- powershell.exe (PID: 2780)
- powershell.exe (PID: 4112)
- powershell.exe (PID: 2212)
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 4112)
SUSPICIOUS
Executing commands from a ".bat" file
- mshta.exe (PID: 3668)
- WinRAR.exe (PID: 6428)
Runs shell command (SCRIPT)
- mshta.exe (PID: 3668)
Starts NET.EXE to display or manage information about active sessions
- cmd.exe (PID: 2732)
- cmd.exe (PID: 4820)
- net.exe (PID: 4800)
- net.exe (PID: 3620)
The process executes Powershell scripts
- cmd.exe (PID: 4820)
- powershell.exe (PID: 4112)
Starts CMD.EXE for commands execution
- mshta.exe (PID: 3668)
- WinRAR.exe (PID: 6428)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4820)
- powershell.exe (PID: 4112)
Checks a user's role membership (POWERSHELL)
- powershell.exe (PID: 4112)
Application launched itself
- powershell.exe (PID: 4112)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 4112)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6428)
There is functionality for taking screenshot (YARA)
- Adobe-GenP-3.0.exe (PID: 4444)
INFO
Checks supported languages
- mode.com (PID: 3932)
- mode.com (PID: 4916)
- Adobe-GenP-3.0.exe (PID: 4444)
- RunMe.exe (PID: 6128)
- NSudo.exe (PID: 2124)
- MpCmdRun.exe (PID: 5564)
Checks proxy server information
- mshta.exe (PID: 3668)
- slui.exe (PID: 5284)
Reads Internet Explorer settings
- mshta.exe (PID: 3668)
Starts MODE.COM to configure console settings
- mode.com (PID: 4916)
- mode.com (PID: 3932)
Manual execution by a user
- cmd.exe (PID: 2732)
- Adobe-GenP-3.0.exe (PID: 2432)
- Adobe-GenP-3.0.exe (PID: 4444)
- RunMe.exe (PID: 6128)
- RunMe.exe (PID: 7136)
- NSudo.exe (PID: 1700)
- NSudo.exe (PID: 2124)
- powershell.exe (PID: 4112)
- powershell.exe (PID: 2780)
Reads mouse settings
- Adobe-GenP-3.0.exe (PID: 4444)
- RunMe.exe (PID: 6128)
Reads the computer name
- Adobe-GenP-3.0.exe (PID: 4444)
- NSudo.exe (PID: 2124)
- MpCmdRun.exe (PID: 5564)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6428)
Reads the software policy settings
- slui.exe (PID: 5284)
The sample compiled with english language support
- WinRAR.exe (PID: 6428)
The process uses AutoIt
- Adobe-GenP-3.0.exe (PID: 4444)
Create files in a temporary directory
- MpCmdRun.exe (PID: 5564)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2023:01:07 00:22:38 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | GenP 3.0 Release/Adobe GenP 3.0/ |
Total processes
166
Monitored processes
29
Malicious processes
2
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1328 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1652 | C:\WINDOWS\system32\net1 session | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1700 | "C:\Users\admin\Desktop\NSudo.exe" | C:\Users\admin\Desktop\NSudo.exe | — | explorer.exe | |||||||||||
User: admin Company: M2-Team Integrity Level: MEDIUM Description: NSudo Launcher Exit code: 3221226540 Version: 8.2.0.0 Modules
| |||||||||||||||
| 2124 | "C:\Users\admin\Desktop\NSudo.exe" | C:\Users\admin\Desktop\NSudo.exe | explorer.exe | ||||||||||||
User: admin Company: M2-Team Integrity Level: HIGH Description: NSudo Launcher Version: 8.2.0.0 Modules
| |||||||||||||||
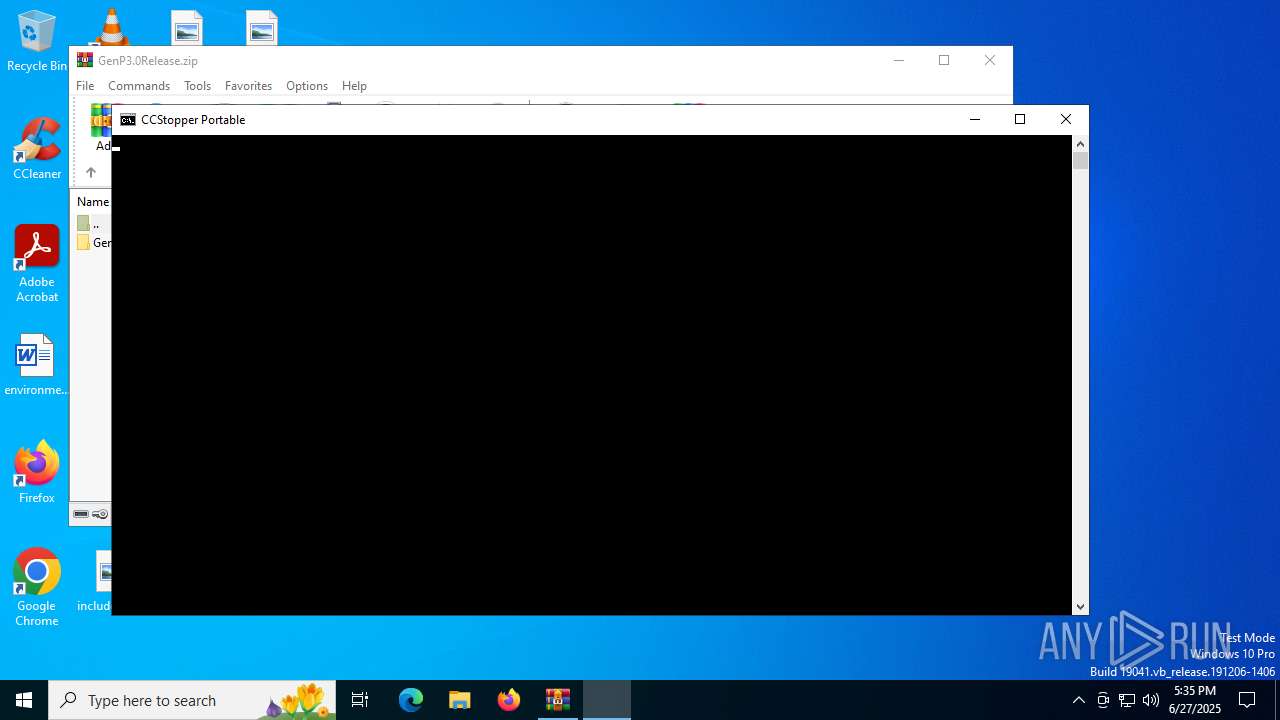
| 2212 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -ExecutionPolicy Bypass -File "C:\Users\admin\Desktop\import.ps1" " Hosts Block - CCStopper Portable Module" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2432 | "C:\Users\admin\Desktop\Adobe-GenP-3.0.exe" | C:\Users\admin\Desktop\Adobe-GenP-3.0.exe | — | explorer.exe | |||||||||||
User: admin Company: 2.0.0 Integrity Level: MEDIUM Description: Adobe-GenP-3.0 Exit code: 3221226540 Version: 2.0.0.0 Modules
| |||||||||||||||
| 2732 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\Patch.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2780 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\Desktop\import.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3620 | net session | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3668 | mshta vbscript:CreateObject("Shell.Application").ShellExecute("cmd","/c C:\Users\admin\Desktop\Patch.bat ::","","runas",1)(window.close) | C:\Windows\System32\mshta.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
23 505
Read events
23 491
Write events
14
Delete events
0
Modification events
| (PID) Process: | (6428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\GenP3.0Release.zip | |||
| (PID) Process: | (6428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3668) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3668) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
5
Suspicious files
10
Text files
24
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3780 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_544d1ux0.gpd.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4112 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_efc14zdp.1qp.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2780 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_j24zkmqn.qxf.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2780 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\4VWPDZBTE4GBN3IS9ZA6.temp | binary | |
MD5:7E1BE7913AAF01DEE6D89055C93B99CC | SHA256:00DBA3E06A95F48DB54E05124A2779CC6D946AA7822922BED10944834A67A4B7 | |||
| 2212 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:683A811ECE83D90B486B0900AC463B86 | SHA256:7C5A8CF366BA63FAD34BC1606125FD0FDCF039B150EDF83E3264E94BC4529C67 | |||
| 4112 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\PTNA2SVOK1OJK2OXPYMA.temp | binary | |
MD5:C8EFE8A8C1D596DBD15C966107FABFAE | SHA256:902B93660E233D90A1B7C6F1997C3AD602F79FEAD3CC46A9D927BF6167FE3DC3 | |||
| 4112 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_mtc5ur1u.o0p.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2780 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF178618.TMP | binary | |
MD5:C8EFE8A8C1D596DBD15C966107FABFAE | SHA256:902B93660E233D90A1B7C6F1997C3AD602F79FEAD3CC46A9D927BF6167FE3DC3 | |||
| 2780 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_b2kvtcly.gce.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2212 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\4JS09VKHGLKITXKRIKEW.temp | binary | |
MD5:683A811ECE83D90B486B0900AC463B86 | SHA256:7C5A8CF366BA63FAD34BC1606125FD0FDCF039B150EDF83E3264E94BC4529C67 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
19
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6404 | RUXIMICS.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6404 | RUXIMICS.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
1268 | svchost.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6404 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6404 | RUXIMICS.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6404 | RUXIMICS.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |