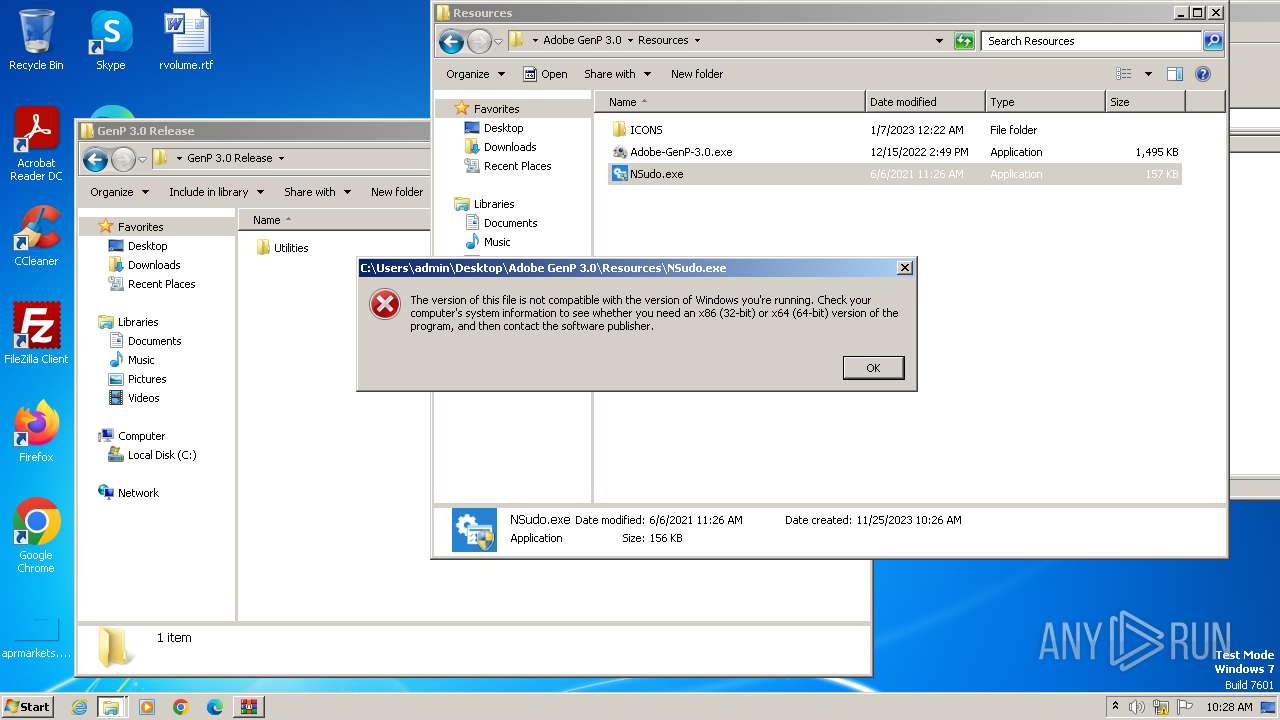
| download: | /70f083qqmkmgRoYwsRtkjhAR7XGci0lgOSr2ylaNf8ou6H75Fp9JXGEygrD24WuWFBm4bHllYVsrZcKICZ_m4-4jxTGCDwfkdlF-LhHqQuoSLJmD8cFkHWgBqQdGUNU6A1AxOUhC0VNby0nTFwq53SnkyZVdZiCXeN6GyddKFwhF/ipp9gj15xzty1uw/GenP+3.0+Release.zip |
| Full analysis: | https://app.any.run/tasks/474da6cf-9f5d-49c6-8f3a-0e6a110a2592 |
| Verdict: | Malicious activity |
| Analysis date: | November 25, 2023, 10:26:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | F78A9965B1EF6FB2ED878D3E9A4C2AF3 |
| SHA1: | 0B0C502A5079B2357E0D330427DEB4D5B24EF071 |
| SHA256: | BA734CEA2D9B594B4028E94F7A396F0380FBDDE68DF026B5BD26D00A3F067C81 |
| SSDEEP: | 98304:0lRgEGmPg0ipktIzHh38s8ofc3Br9eLJkouhNv1TFARiNx:0jgzmPg0ipDLms8eMJ9eLRsv1q8f |
MALICIOUS
Starts Visual C# compiler
- sdiagnhost.exe (PID: 3052)
Drops the executable file immediately after the start
- csc.exe (PID: 3972)
- csc.exe (PID: 3608)
- csc.exe (PID: 3512)
SUSPICIOUS
Process drops legitimate windows executable
- msdt.exe (PID: 3756)
Probably uses Microsoft diagnostics tool to execute malicious payload
- pcwrun.exe (PID: 3000)
Reads settings of System Certificates
- msdt.exe (PID: 3756)
Reads the Internet Settings
- sdiagnhost.exe (PID: 3052)
- msdt.exe (PID: 3756)
Uses .NET C# to load dll
- sdiagnhost.exe (PID: 3052)
Uses RUNDLL32.EXE to load library
- msdt.exe (PID: 3756)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 888)
- msdt.exe (PID: 3756)
Manual execution by a user
- pcwrun.exe (PID: 3000)
- taskmgr.exe (PID: 4012)
Create files in a temporary directory
- msdt.exe (PID: 3756)
- pcwrun.exe (PID: 3000)
- sdiagnhost.exe (PID: 3052)
- csc.exe (PID: 3972)
- cvtres.exe (PID: 4000)
- csc.exe (PID: 3512)
- cvtres.exe (PID: 3456)
- csc.exe (PID: 3608)
- cvtres.exe (PID: 3644)
Reads security settings of Internet Explorer
- msdt.exe (PID: 3756)
- sdiagnhost.exe (PID: 3052)
Checks supported languages
- csc.exe (PID: 3972)
- cvtres.exe (PID: 4000)
- csc.exe (PID: 3512)
- cvtres.exe (PID: 3456)
- cvtres.exe (PID: 3644)
- csc.exe (PID: 3608)
Reads the machine GUID from the registry
- csc.exe (PID: 3972)
- cvtres.exe (PID: 4000)
- csc.exe (PID: 3512)
- cvtres.exe (PID: 3456)
- csc.exe (PID: 3608)
- cvtres.exe (PID: 3644)
Creates files or folders in the user directory
- msdt.exe (PID: 3756)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2023:01:07 00:22:38 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
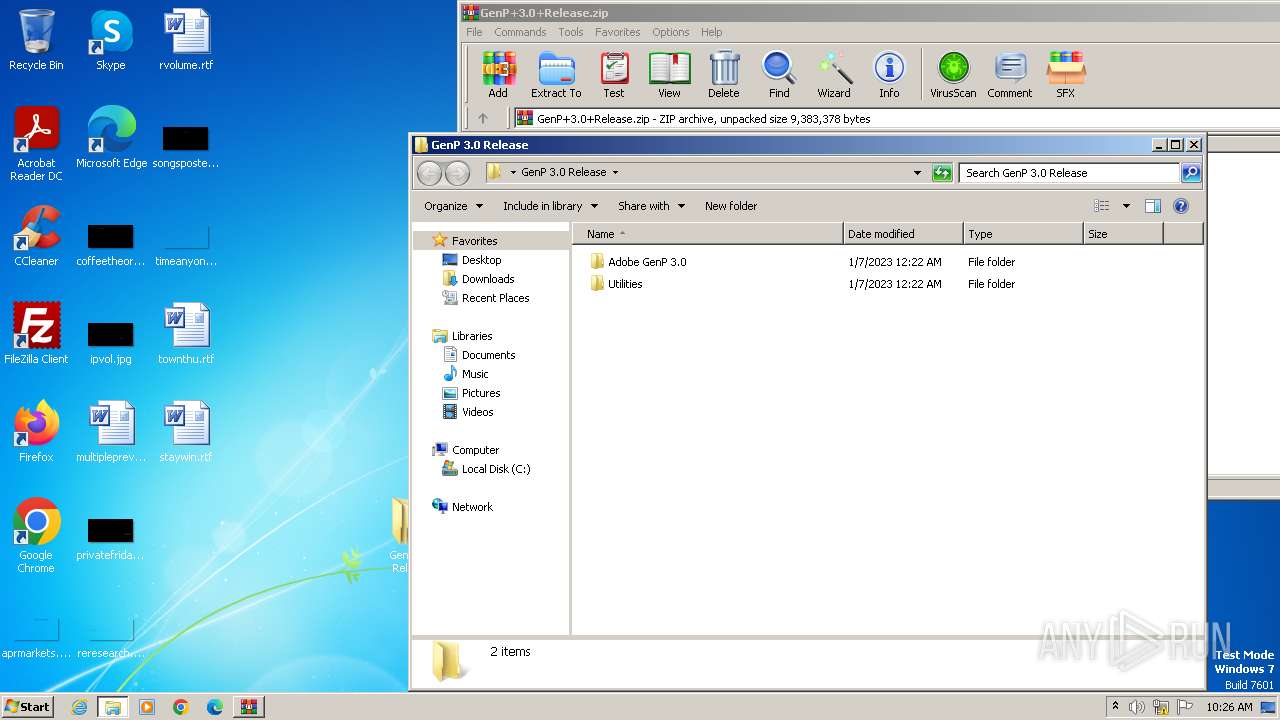
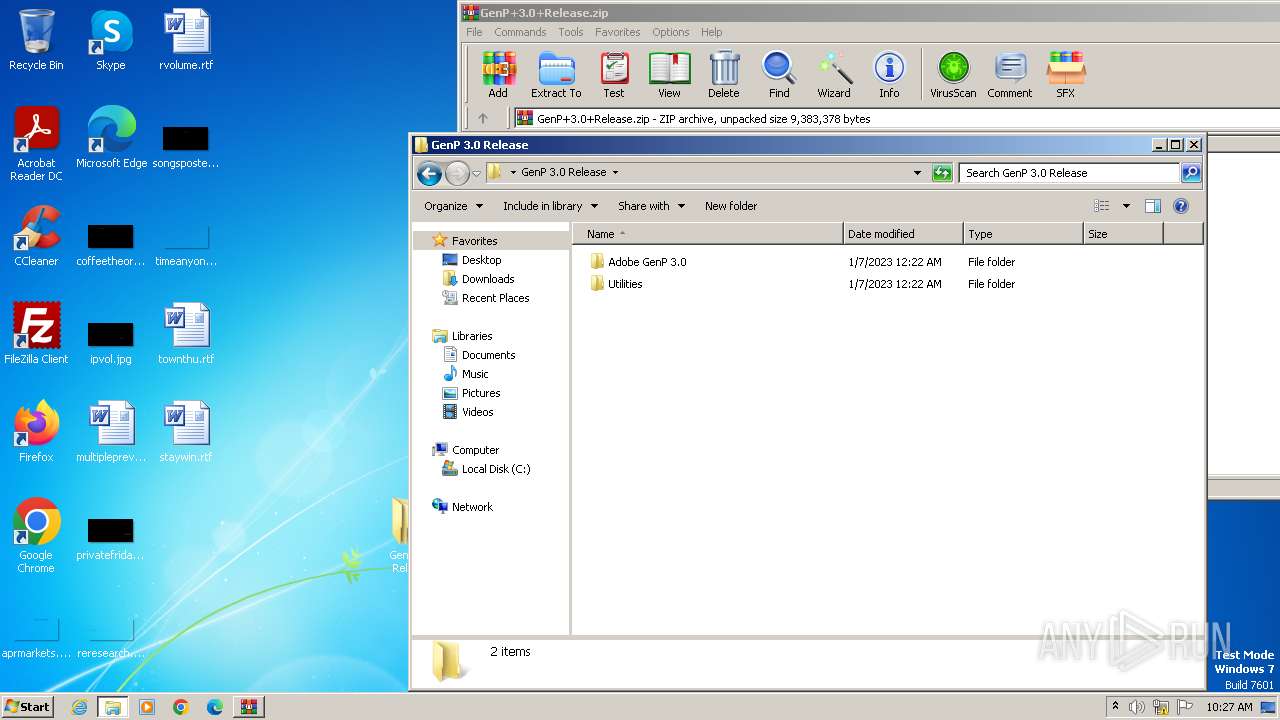
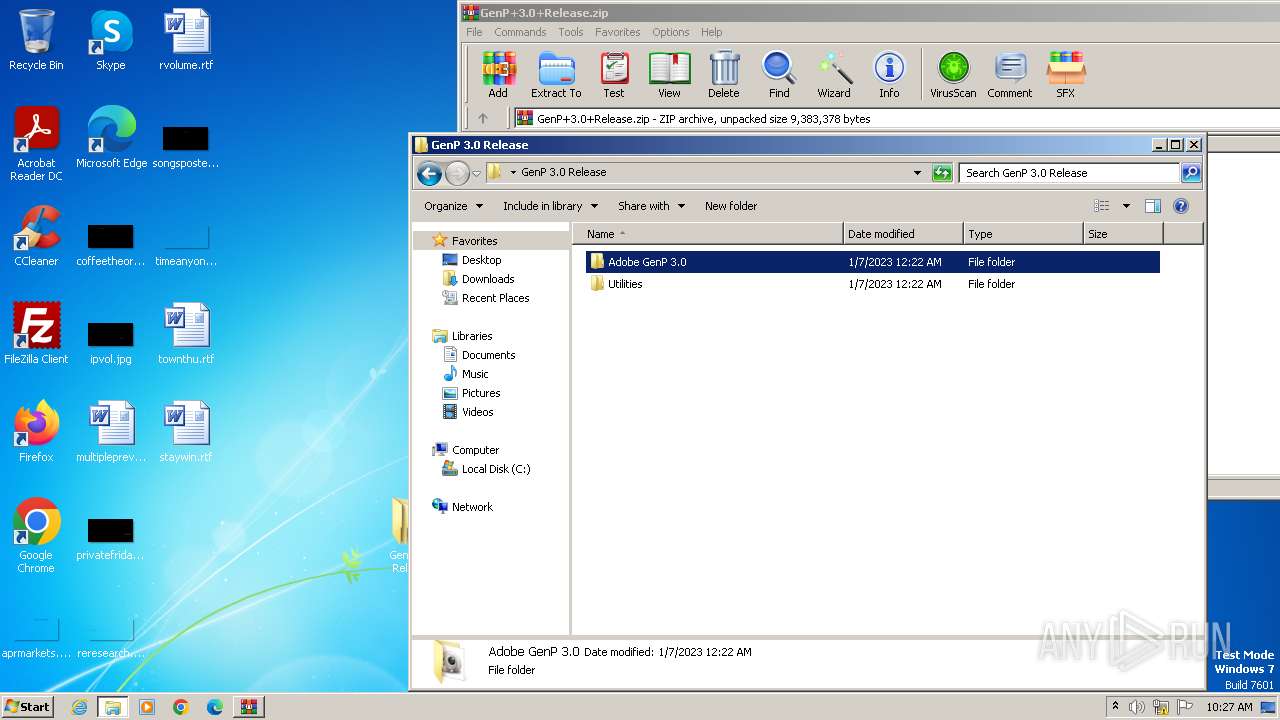
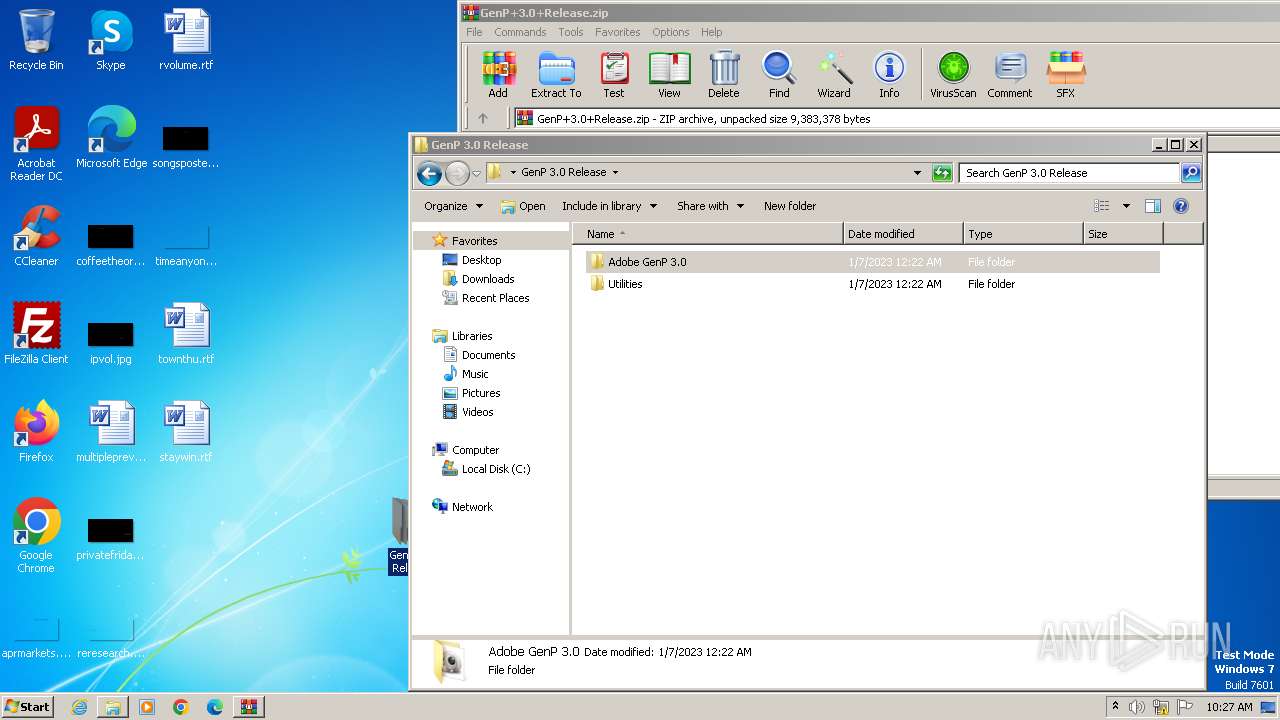
| ZipFileName: | GenP 3.0 Release/Adobe GenP 3.0/ |
Total processes
52
Monitored processes
12
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 888 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\GenP+3.0+Release.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
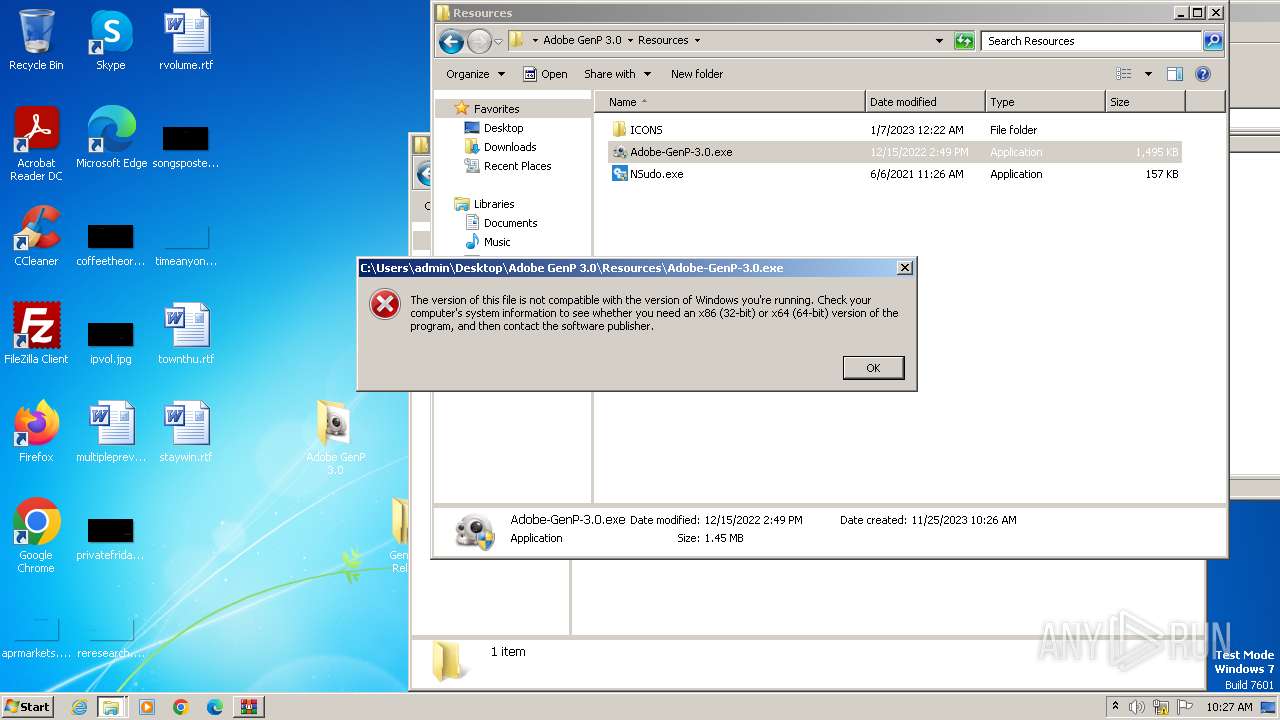
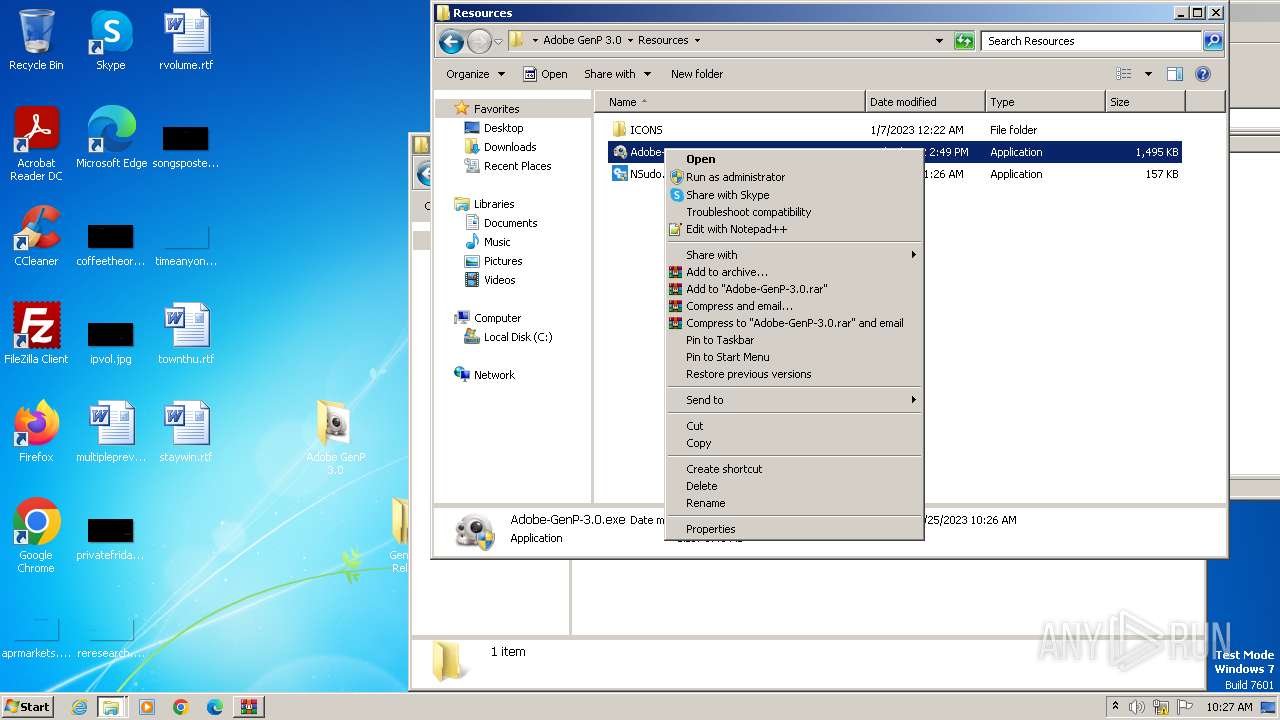
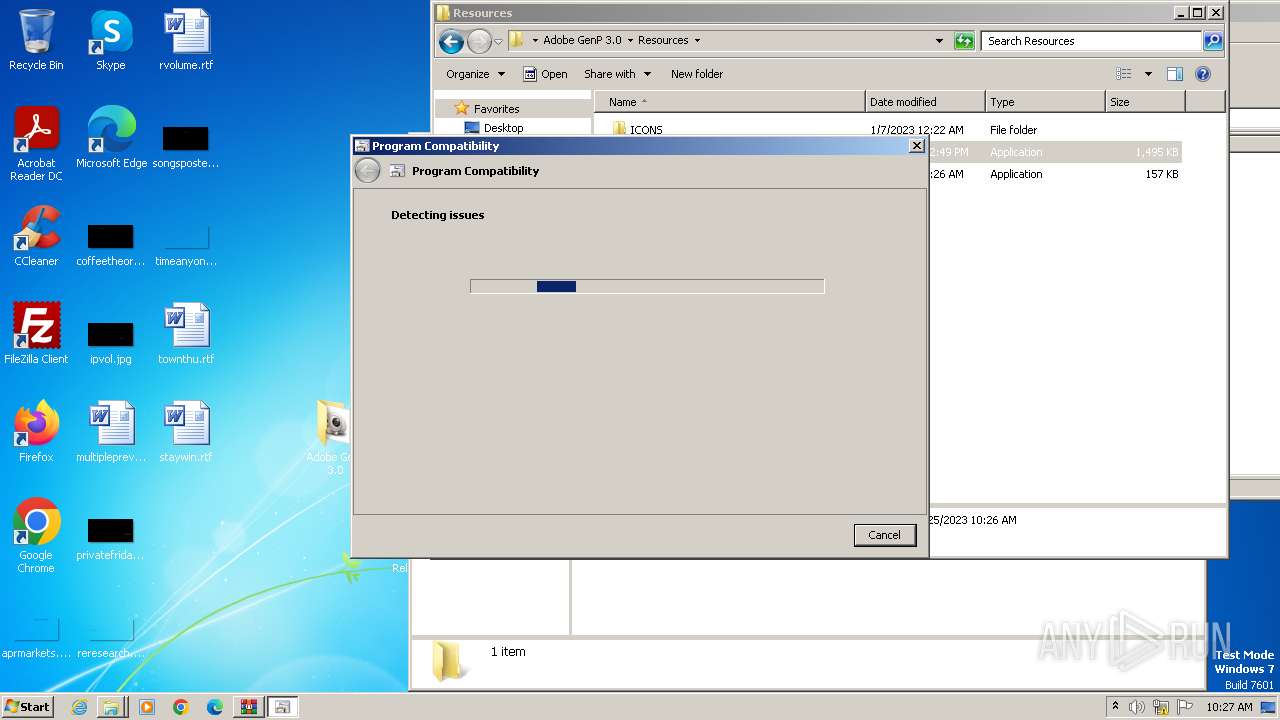
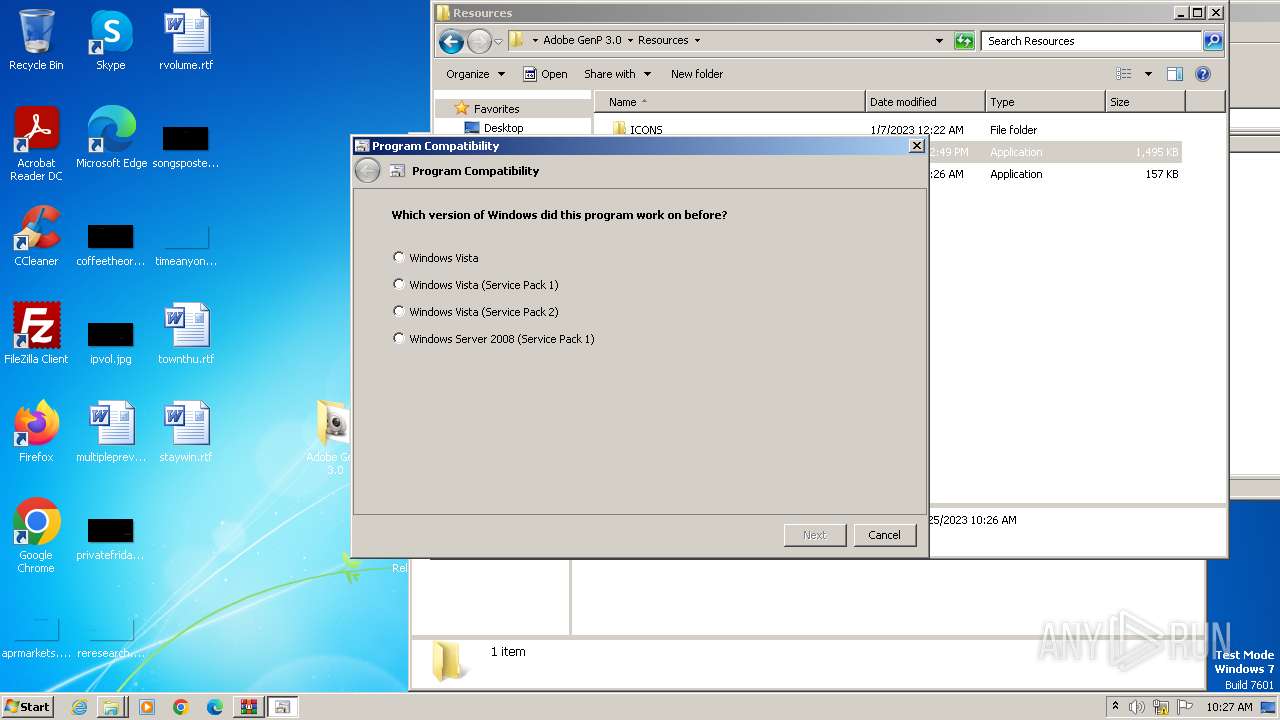
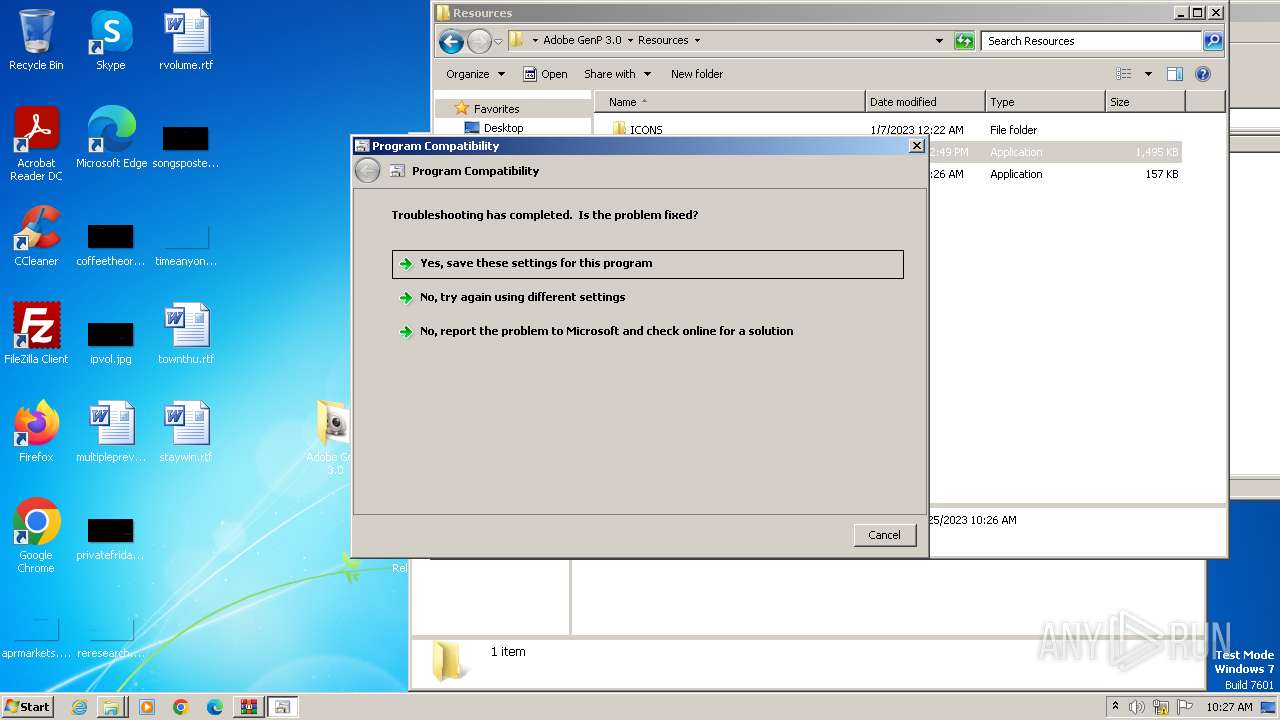
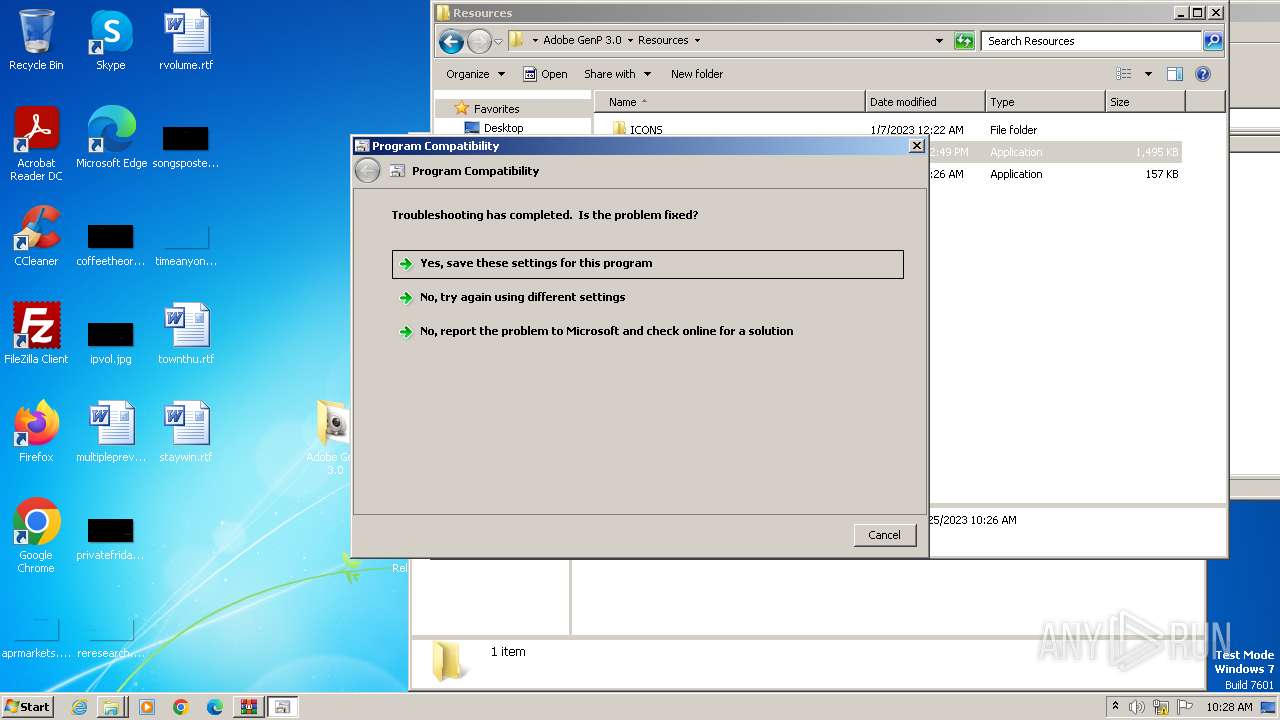
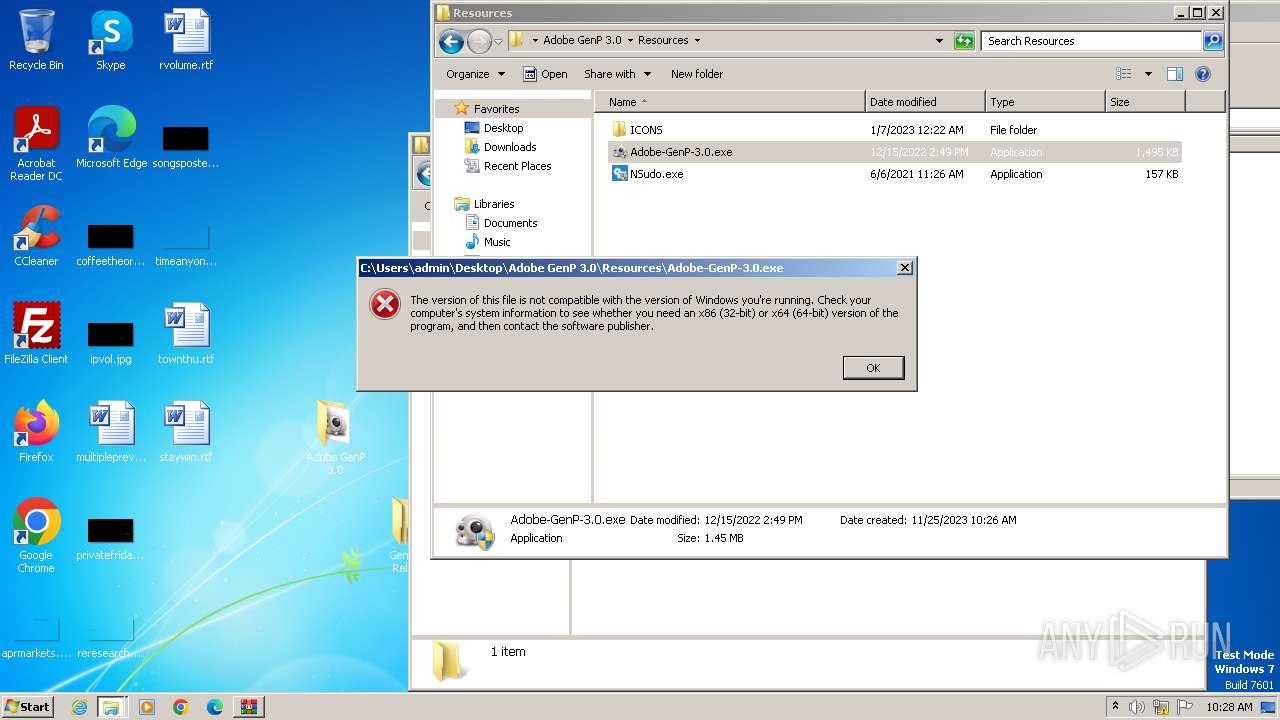
| 3000 | C:\Windows\system32\pcwrun.exe "C:\Users\admin\Desktop\Adobe GenP 3.0\Resources\Adobe-GenP-3.0.exe" | C:\Windows\System32\pcwrun.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Program Compatibility Troubleshooter Invoker Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3052 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Scripted Diagnostics Native Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3340 | "C:\Windows\System32\rundll32.exe" C:\Windows\system32\pcwutl.dll,CreateAndRunTask -path "C:\Users\admin\Desktop\Adobe GenP 3.0\Resources\Adobe-GenP-3.0.exe" | C:\Windows\System32\rundll32.exe | — | msdt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3456 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESB05D.tmp" "c:\Users\admin\AppData\Local\Temp\CSCB04C.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.5003 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 3512 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\66afxqyj.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | sdiagnhost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.5483 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 3608 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\ifvaeu4q.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | sdiagnhost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.5483 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 3644 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESB0DA.tmp" "c:\Users\admin\AppData\Local\Temp\CSCB0D9.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.5003 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 3756 | C:\Windows\System32\msdt.exe -path C:\Windows\diagnostics\index\PCWDiagnostic.xml -af C:\Users\admin\AppData\Local\Temp\PCWAC26.xml /skip TRUE | C:\Windows\System32\msdt.exe | — | pcwrun.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Diagnostics Troubleshooting Wizard Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3972 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\ll2cisl0.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | sdiagnhost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.5483 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
Total events
6 650
Read events
6 610
Write events
39
Delete events
1
Modification events
| (PID) Process: | (888) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (888) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (888) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (888) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (888) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (888) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (888) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (888) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3756) msdt.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3052) sdiagnhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
10
Suspicious files
15
Text files
37
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
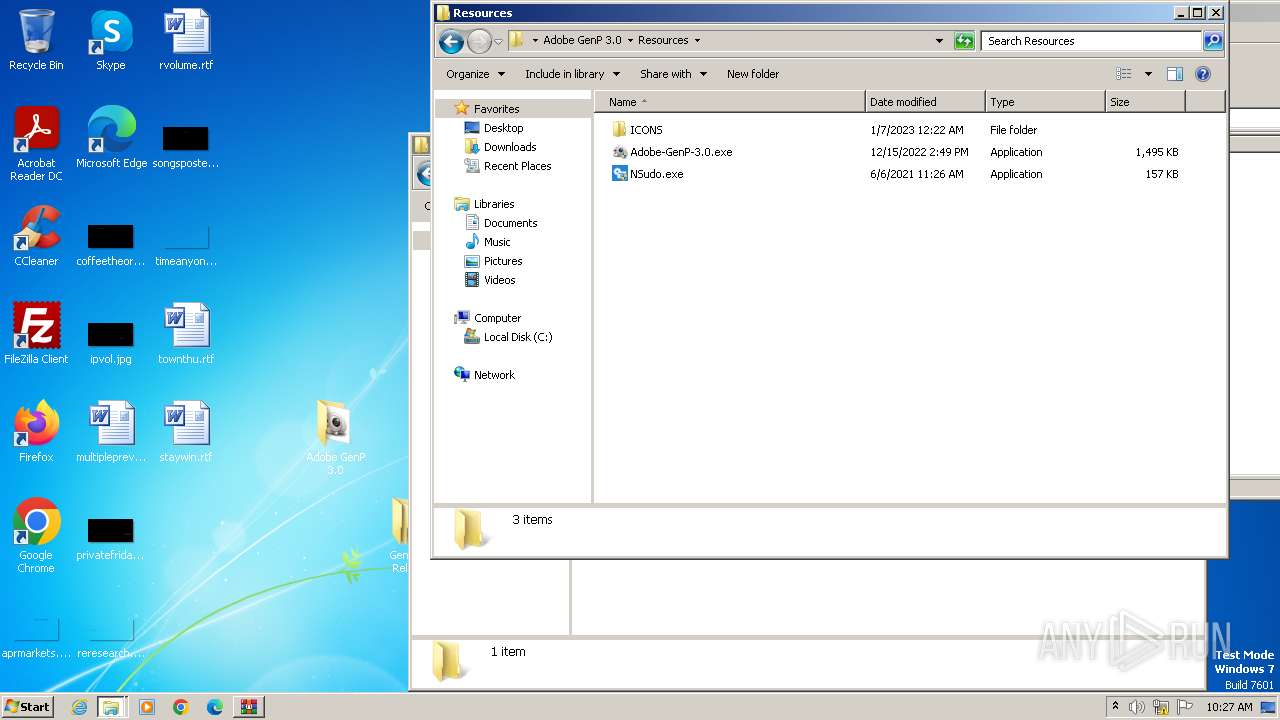
| 888 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa888.49081\GenP 3.0 Release\Adobe GenP 3.0\Resources\NSudo.exe | executable | |
MD5:7AACFD85B8DFF0AA6867BEDE82CFD147 | SHA256:871E4F28FE39BCAD8D295AE46E148BE458778C0195ED660B7DB18EB595D00BD8 | |||
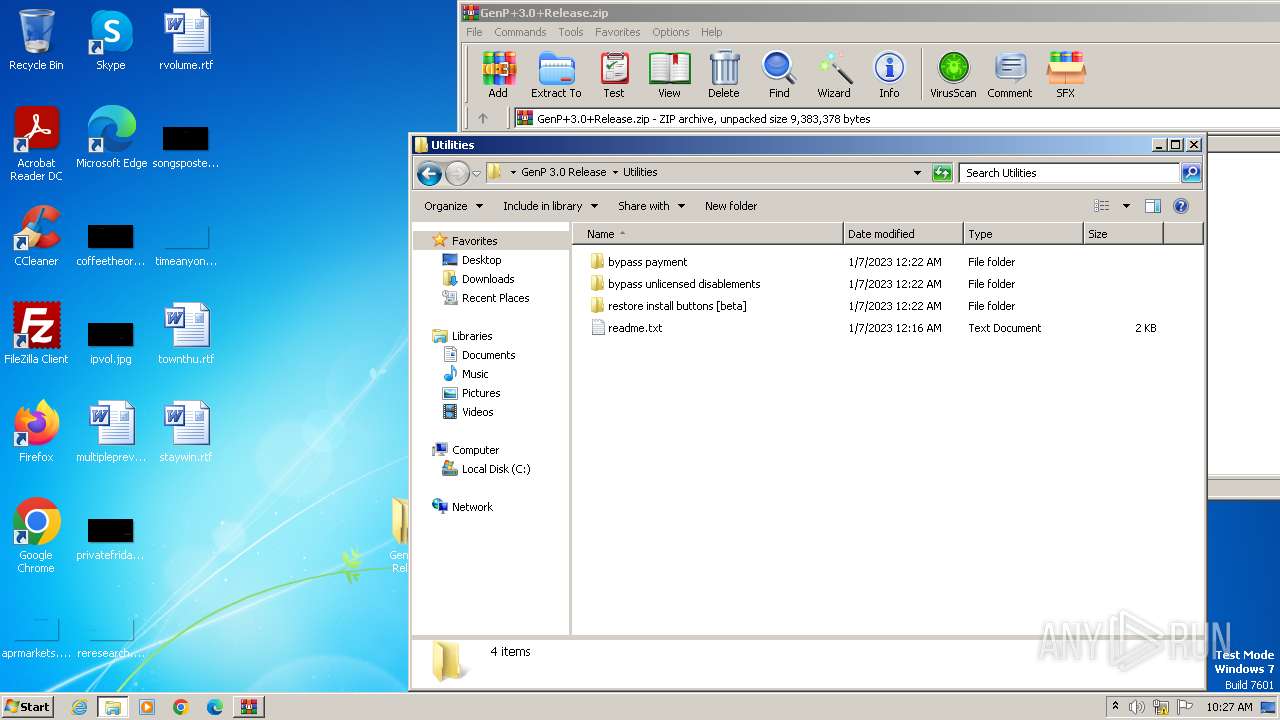
| 888 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa888.49081\GenP 3.0 Release\Utilities\bypass payment\Resource\import.ps1 | text | |
MD5:DFEA6576CCC0FC7E2BAC188EF68E612A | SHA256:12E9A9B1B6F6720E4A0BCB7F8D8D5FE605AFFBD2A56BC6552A96BB29F4439F49 | |||
| 888 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa888.49081\GenP 3.0 Release\Utilities\bypass payment\readme.txt | text | |
MD5:E5FA616E8F245AA019E30F9F948E55B6 | SHA256:0E6C836D4ABFF6C50C7362CB4E885F4EB10210017B451A2C243A94D11B67D421 | |||
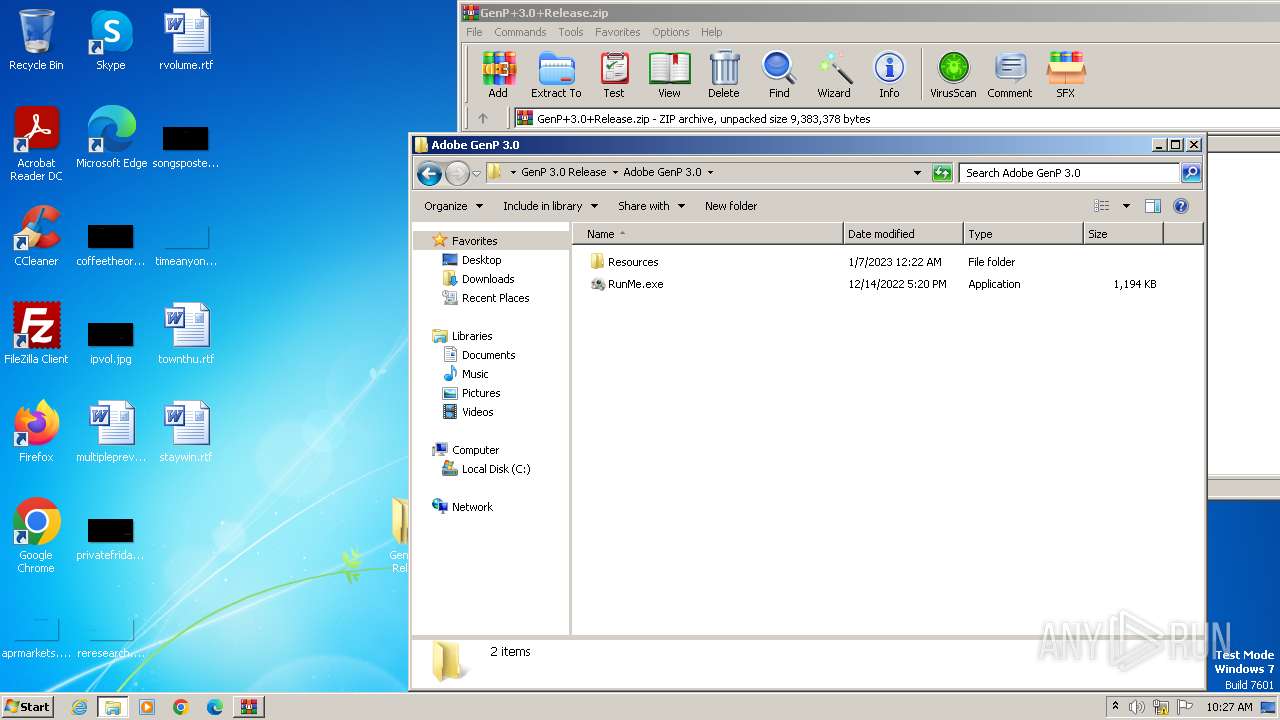
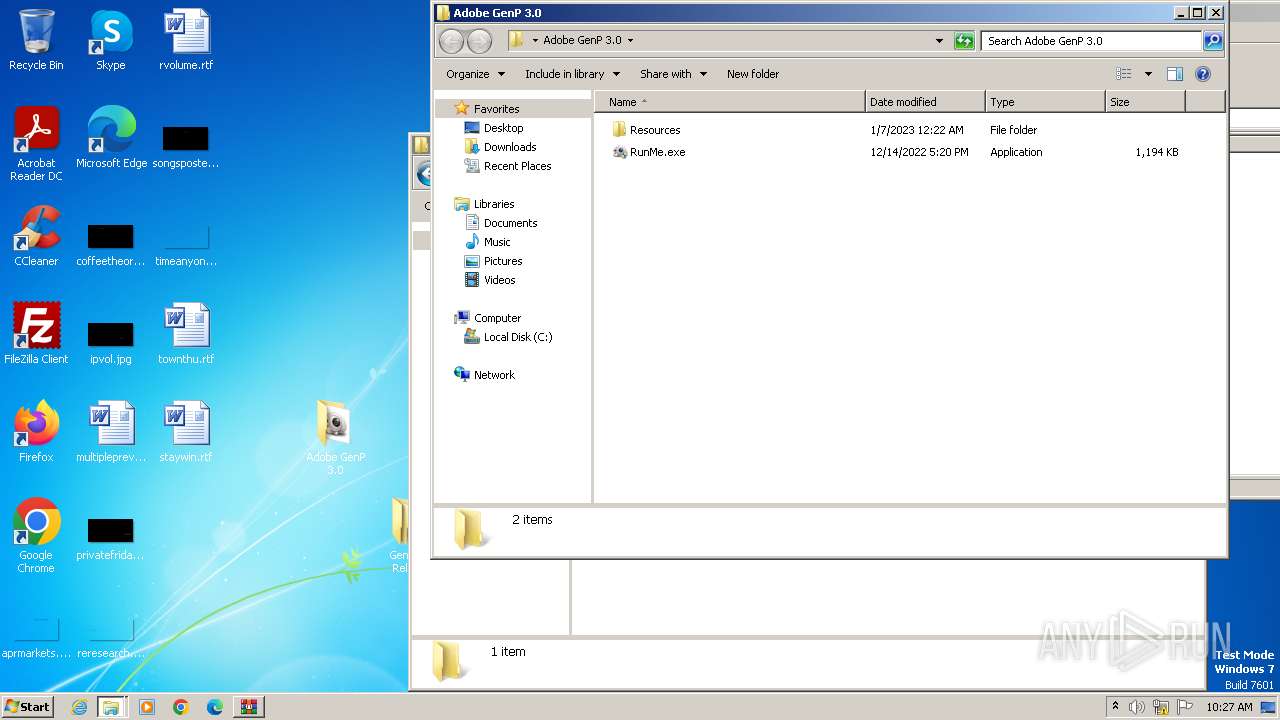
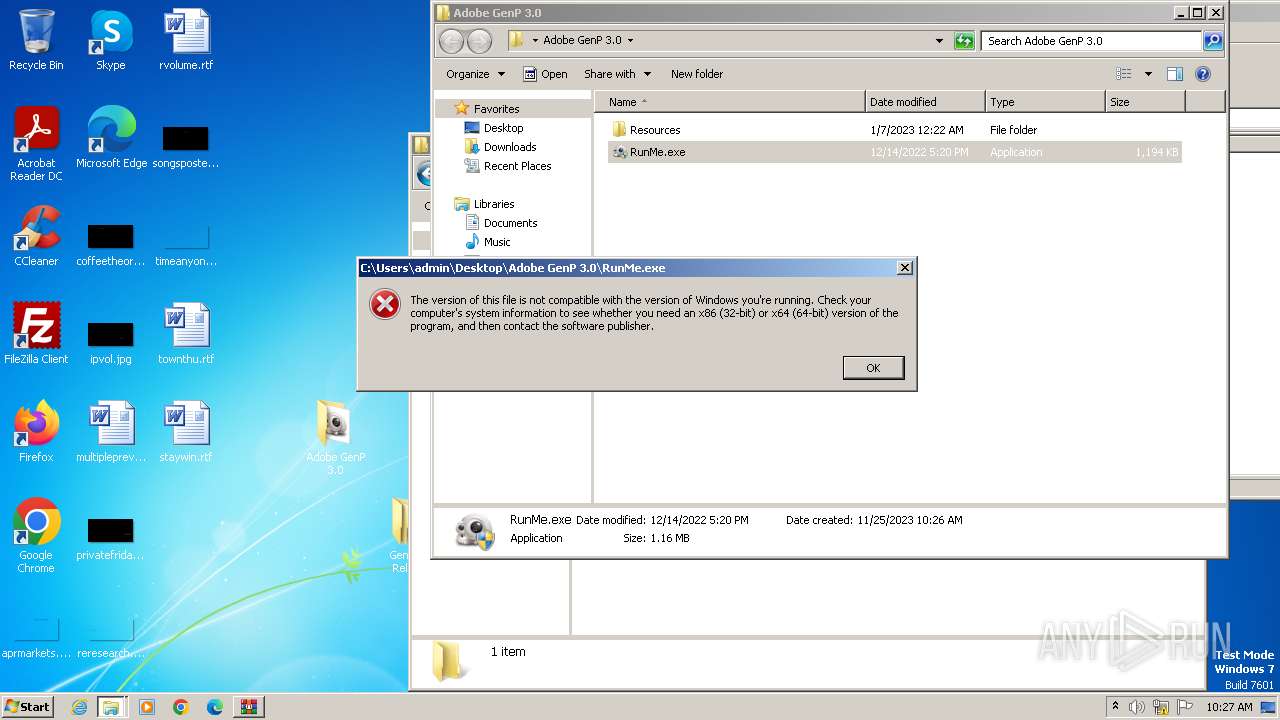
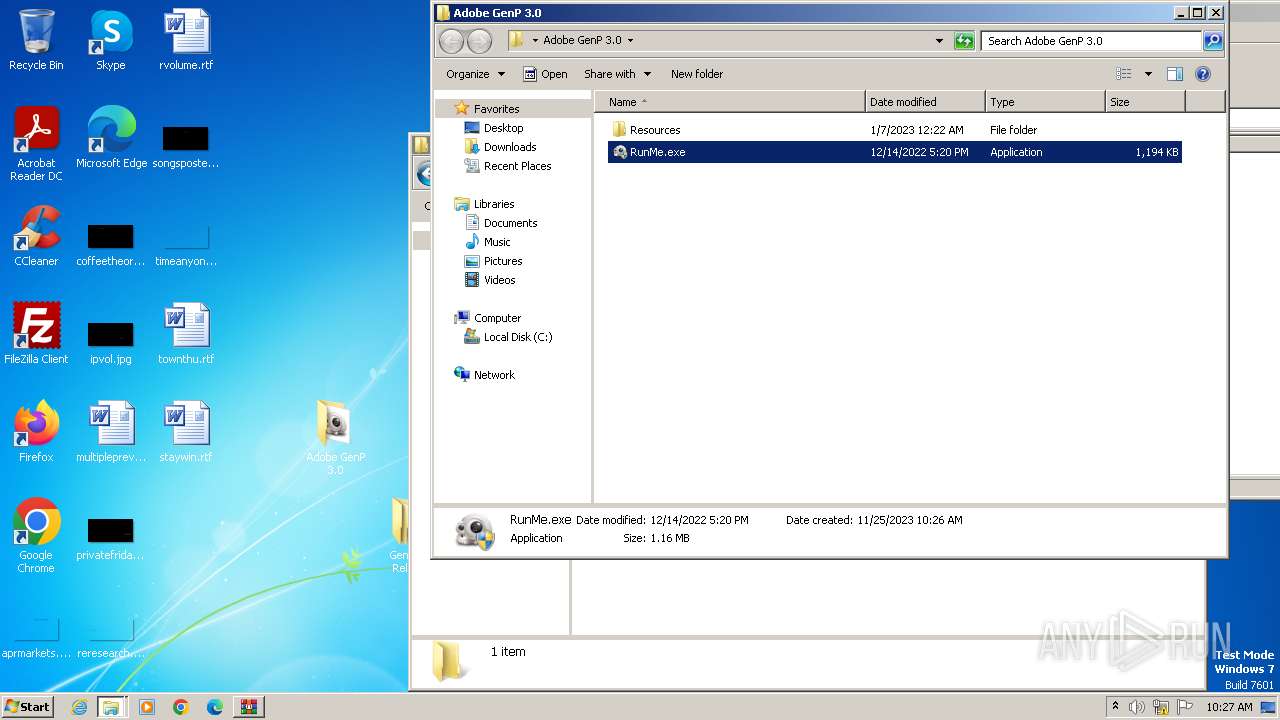
| 888 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa888.49081\GenP 3.0 Release\Adobe GenP 3.0\RunMe.exe | executable | |
MD5:A41EF7D298A96FF2E0B51D255D554568 | SHA256:2063B7289BB34B2E732970437B183B9D112CD3A4E5DB9B13BF5BD0F485856C27 | |||
| 888 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa888.49081\GenP 3.0 Release\Utilities\bypass payment\Resource\module.ps1 | text | |
MD5:F793A64C786EB54630806118368D415A | SHA256:190FA9CAB2F8C76DE77A1EBAC3554F17671487C1A5DA134E49AEE576AC3ECB60 | |||
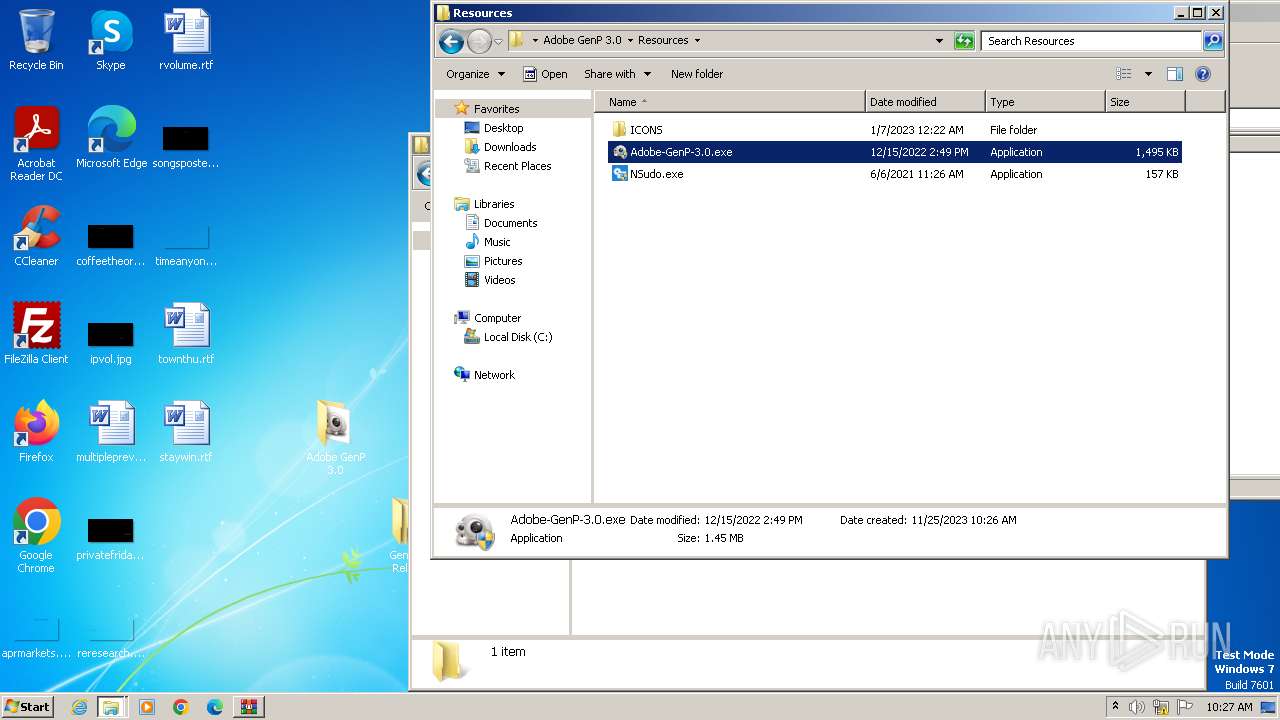
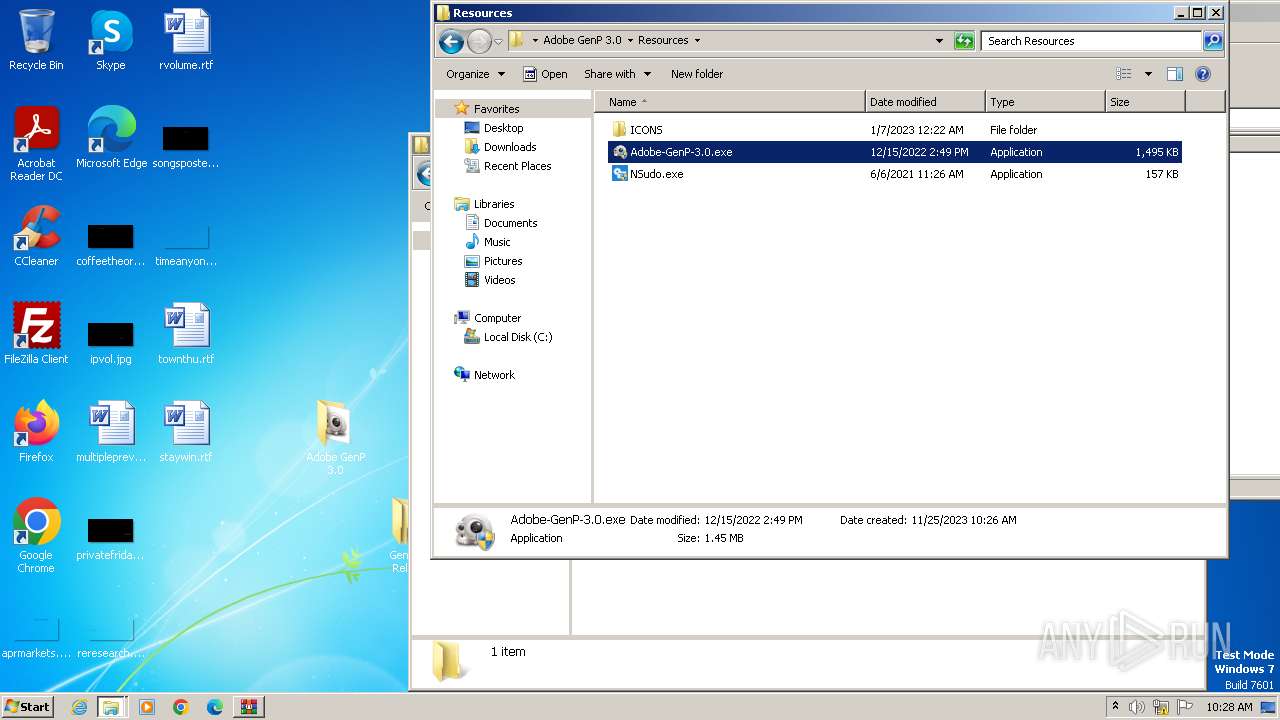
| 888 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa888.49081\GenP 3.0 Release\Adobe GenP 3.0\Resources\Adobe-GenP-3.0.exe | executable | |
MD5:ED76BDAFD8D0AEB9429DD3B09D506C1A | SHA256:DD0927DB589AA8EBD7B81988DE635CECFC55DA14821F2A3284AF2809C16169BE | |||
| 888 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa888.49081\GenP 3.0 Release\Utilities\bypass payment\Resource\portable.ps1 | text | |
MD5:0ABF702B10BDDDC9B9795347B6684D20 | SHA256:9D415506811C8951D97E805E4E530D792FCC11FF3F8FB7AD2A2D157E110BAB3B | |||
| 888 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa888.49081\GenP 3.0 Release\Utilities\bypass payment\Patch.bat | text | |
MD5:17242BB383F1F5A2362A0BECD66A591D | SHA256:C574D4BA81A60BCCF241530040A3015CEBF55A3724B92B5472288FB15813C02C | |||
| 888 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa888.49081\GenP 3.0 Release\Utilities\bypass unlicensed disablements\Patch.bat | text | |
MD5:17242BB383F1F5A2362A0BECD66A591D | SHA256:C574D4BA81A60BCCF241530040A3015CEBF55A3724B92B5472288FB15813C02C | |||
| 888 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa888.49081\GenP 3.0 Release\Adobe GenP 3.0\Resources\ICONS\Cure.bmp | image | |
MD5:079F2E0FBBE5CF57A8D9C5B9F2CAA26E | SHA256:F8431728CDD9BFB09F1EAF062E966356EA26F15D39C504943847928BF5A4A980 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Threats
Process | Message |
|---|---|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|