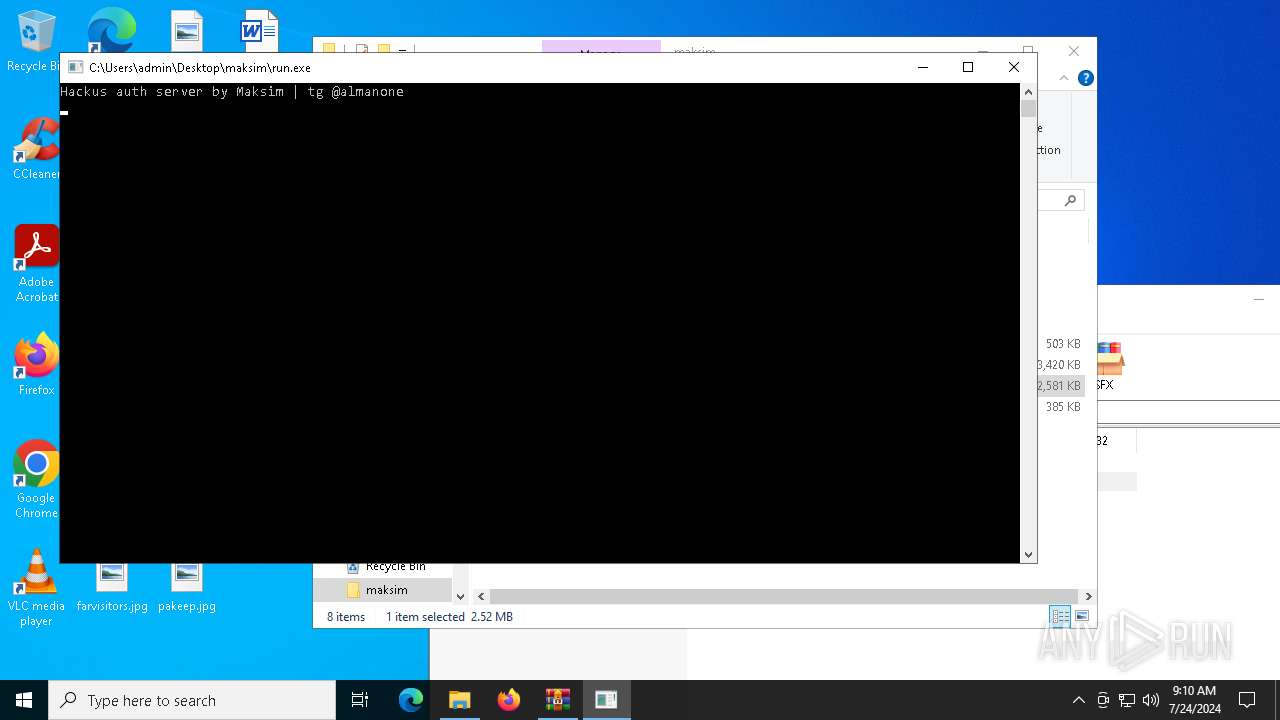
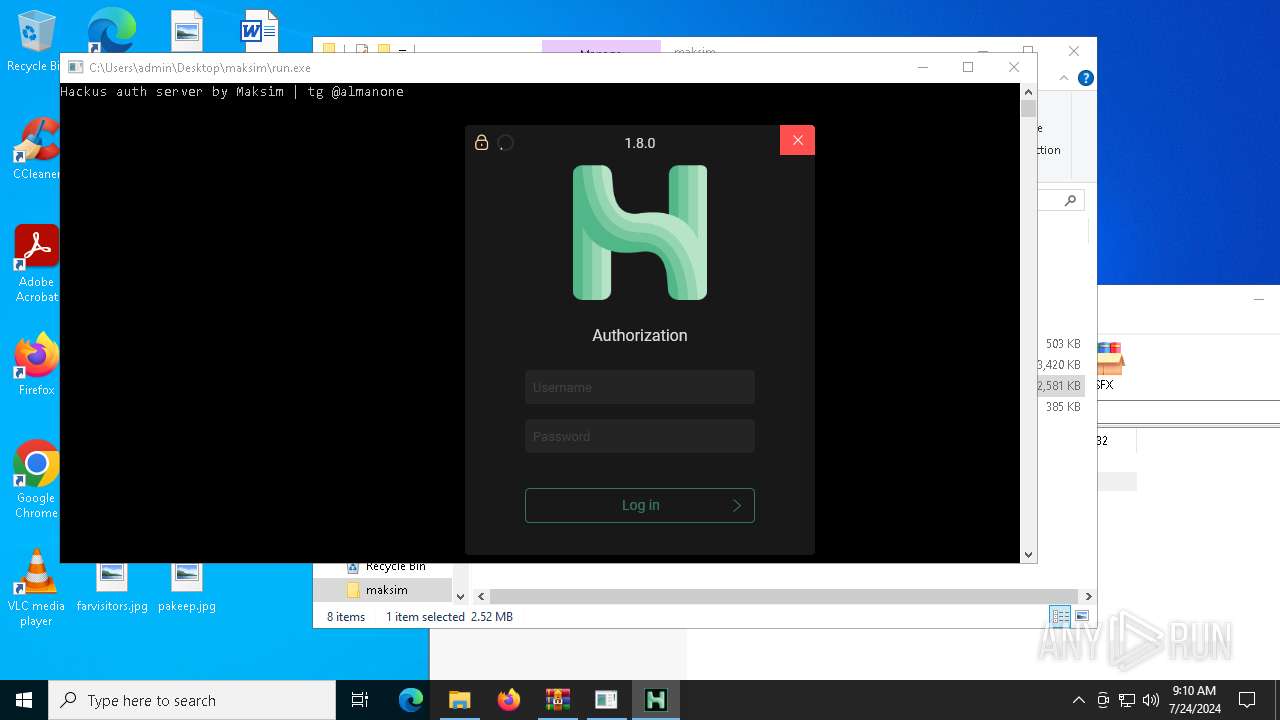
| File name: | maksim.rar |
| Full analysis: | https://app.any.run/tasks/9b5189b7-97f7-4e89-9784-e5aa0ccdaf3e |
| Verdict: | Malicious activity |
| Analysis date: | July 24, 2024, 09:09:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | DA2D42D05FB1C41F66301E9E75DA03F2 |
| SHA1: | 48BCAFBD5664CEE47D8B9B69F108BEF6C654F31B |
| SHA256: | BA4F98080FCDFDC17B5C3063B2878CA8BFB51DFEC83FF13ECC8C75A498992BA3 |
| SSDEEP: | 98304:QXFjELUDrgH4Je8otRtEVgNl5v7Rboh6/q3goNeRdwgT8kkPmSwzj0uv1iVeIi/5:8XvtInl1x7R08mFEbiW7 |
MALICIOUS
Modifies hosts file to block updates
- run.exe (PID: 6444)
SUSPICIOUS
Reads security settings of Internet Explorer
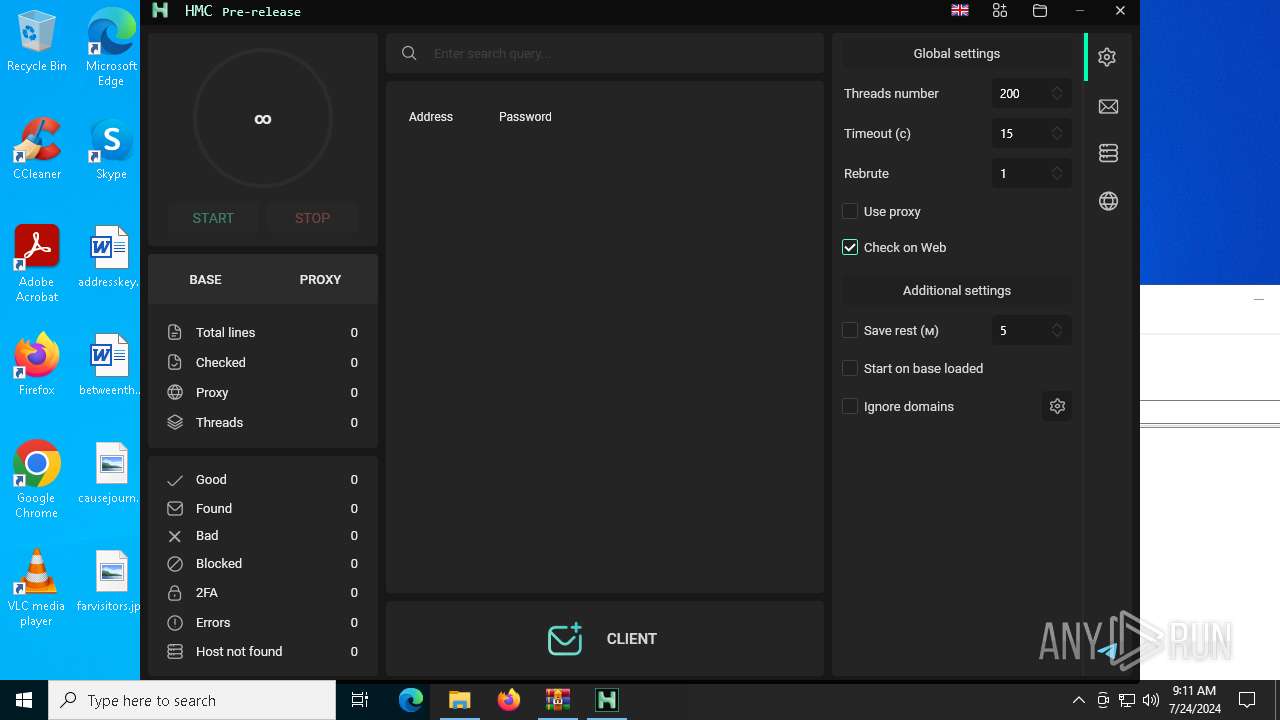
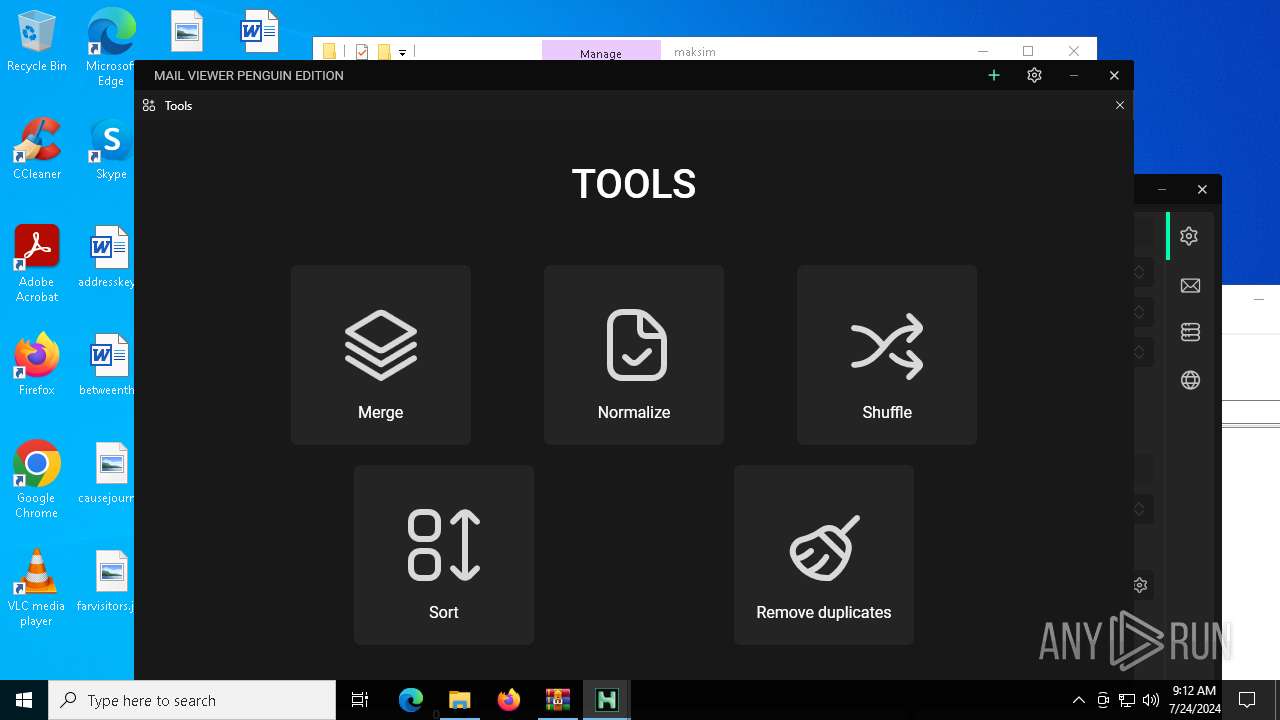
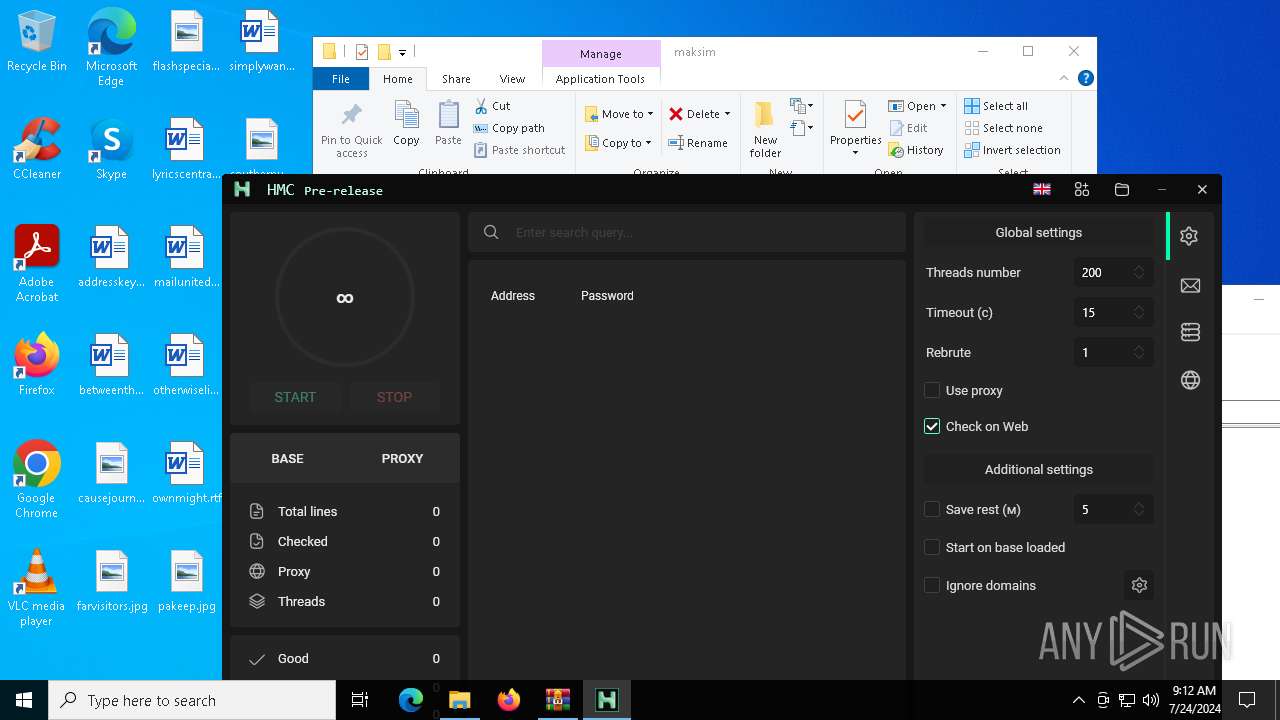
- HMC 1.8.0.exe (PID: 5672)
Creates files in the driver directory
- run.exe (PID: 6444)
INFO
Checks supported languages
- run.exe (PID: 6444)
- HMC 1.8.0.exe (PID: 5672)
- TextInputHost.exe (PID: 2884)
Reads the computer name
- HMC 1.8.0.exe (PID: 5672)
- TextInputHost.exe (PID: 2884)
Reads the machine GUID from the registry
- HMC 1.8.0.exe (PID: 5672)
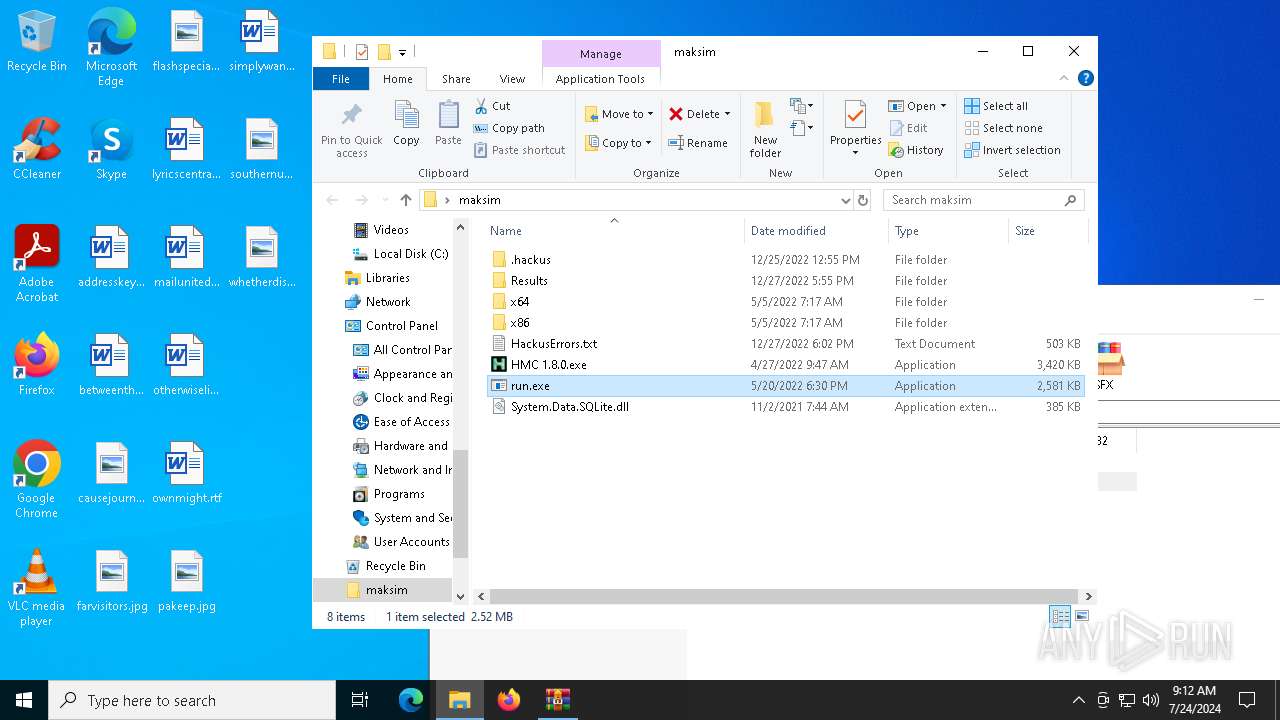
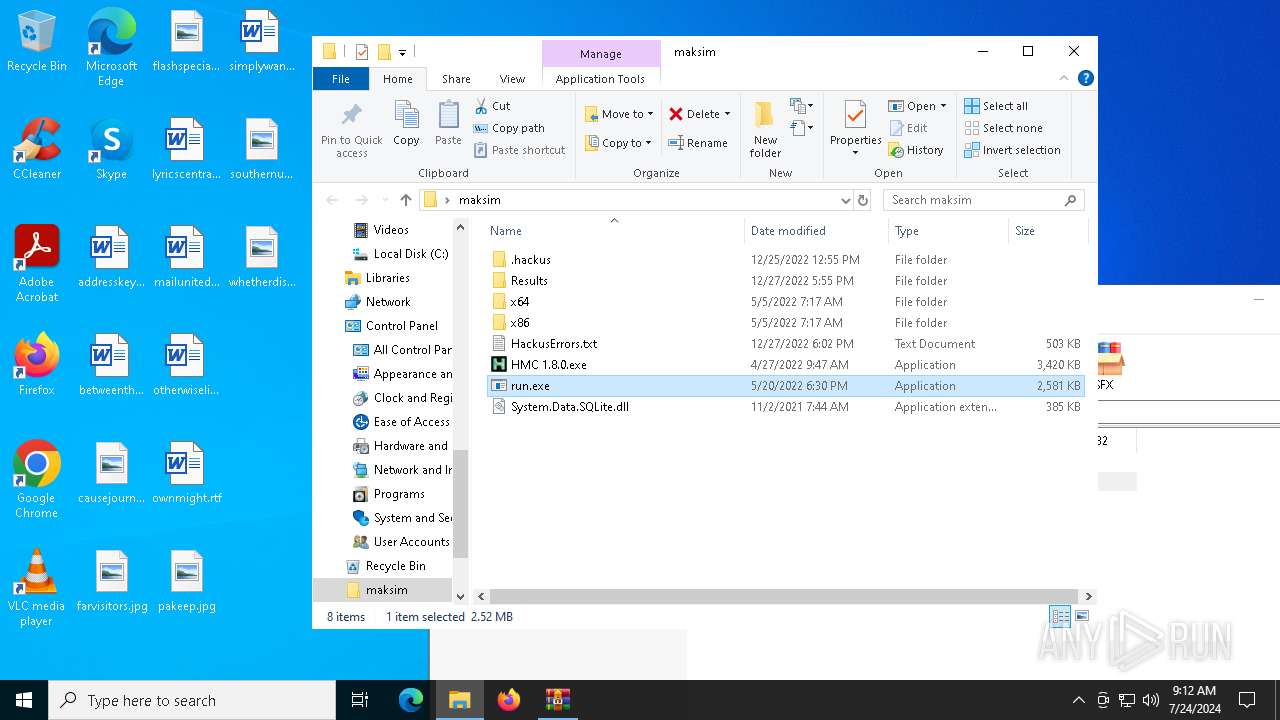
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1108)
Manual execution by a user
- run.exe (PID: 6444)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1108)
Create files in a temporary directory
- HMC 1.8.0.exe (PID: 5672)
Reads the software policy settings
- slui.exe (PID: 6820)
- HMC 1.8.0.exe (PID: 5672)
Checks proxy server information
- slui.exe (PID: 6820)
Reads Environment values
- HMC 1.8.0.exe (PID: 5672)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
140
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1108 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\maksim.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2588 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | run.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 2884 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 4656 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
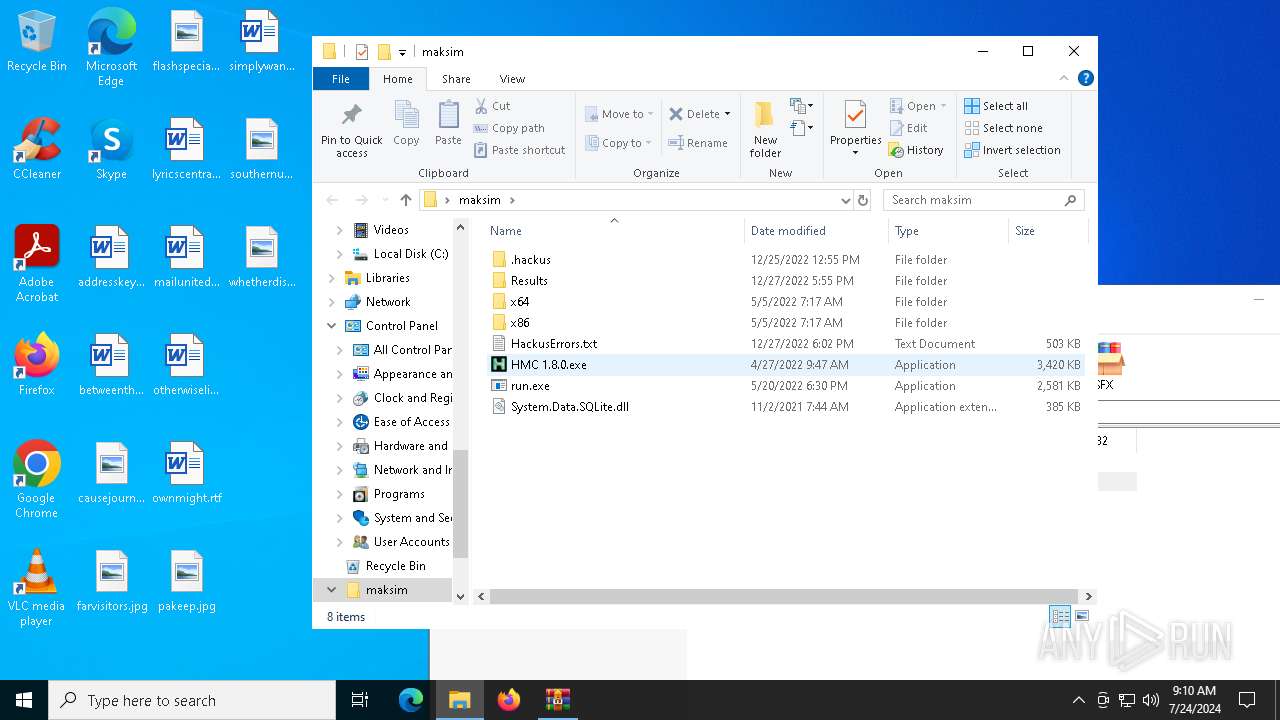
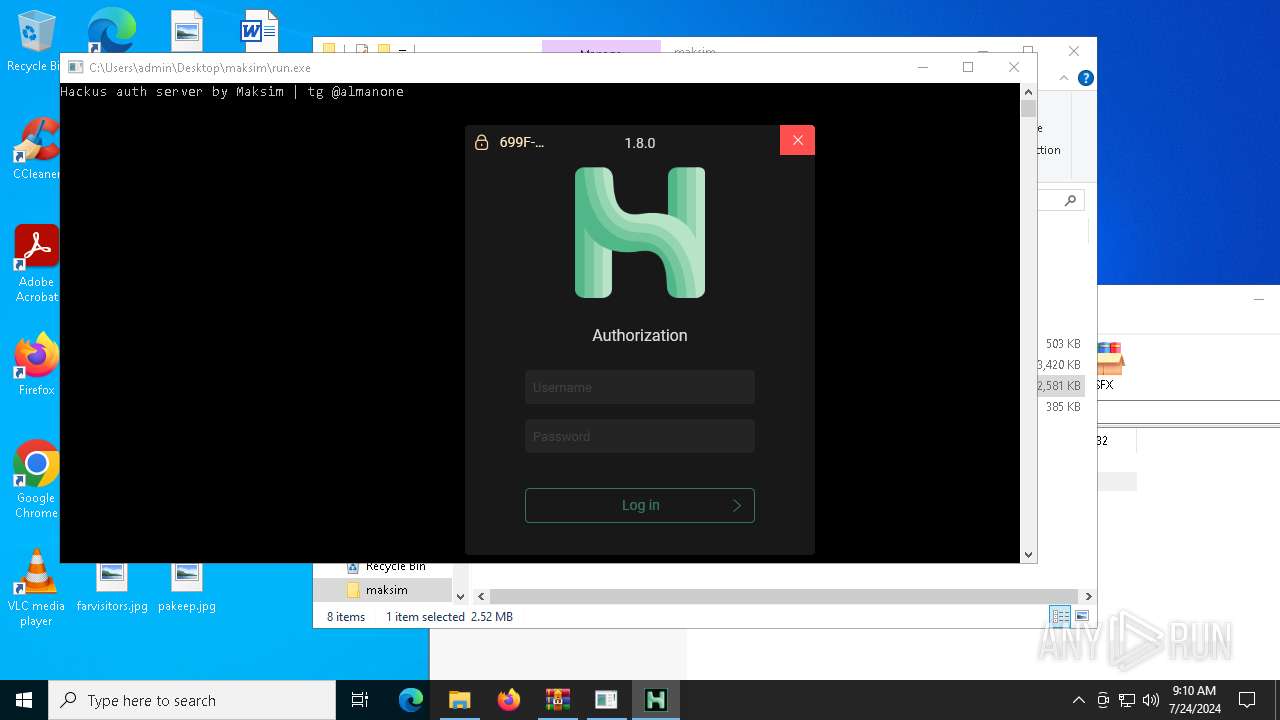
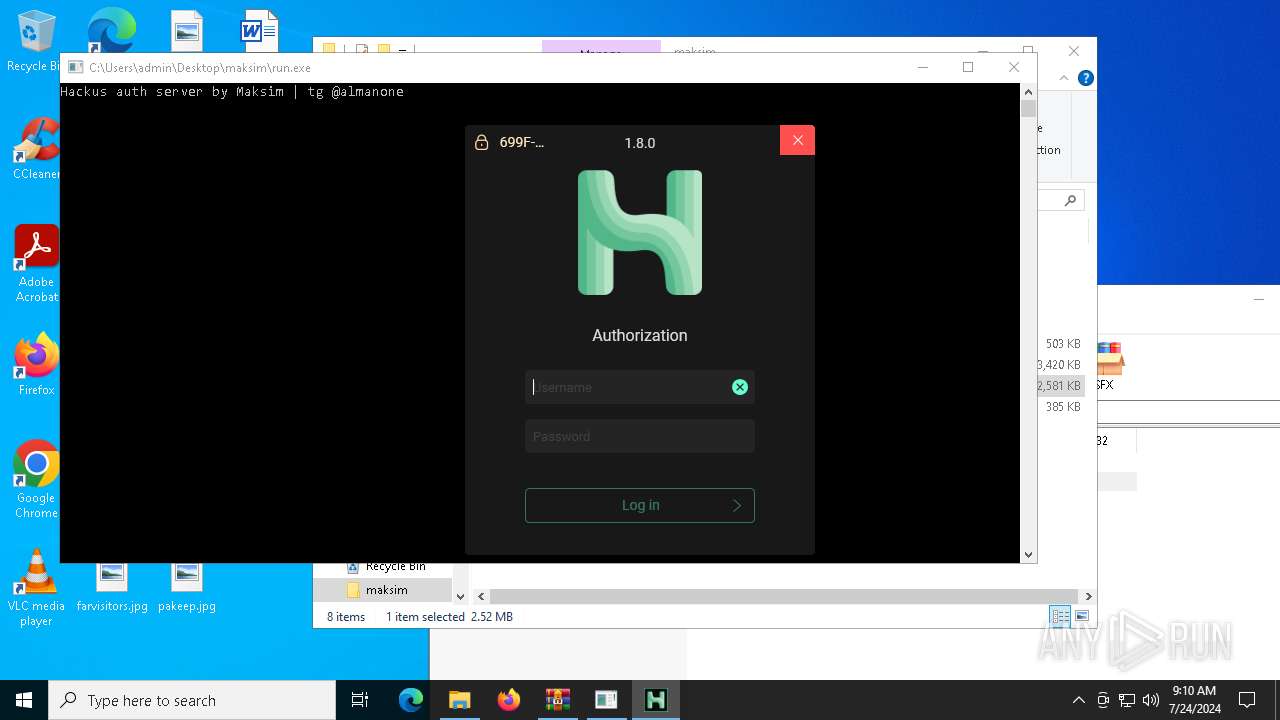
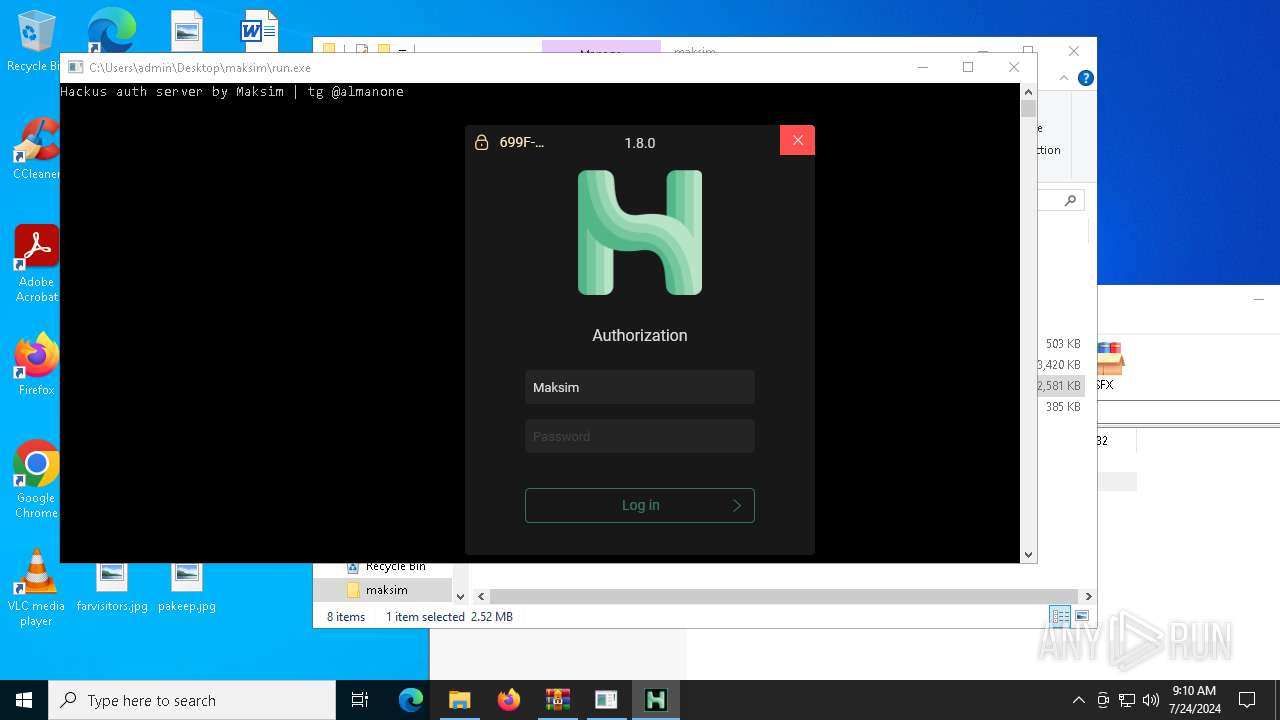
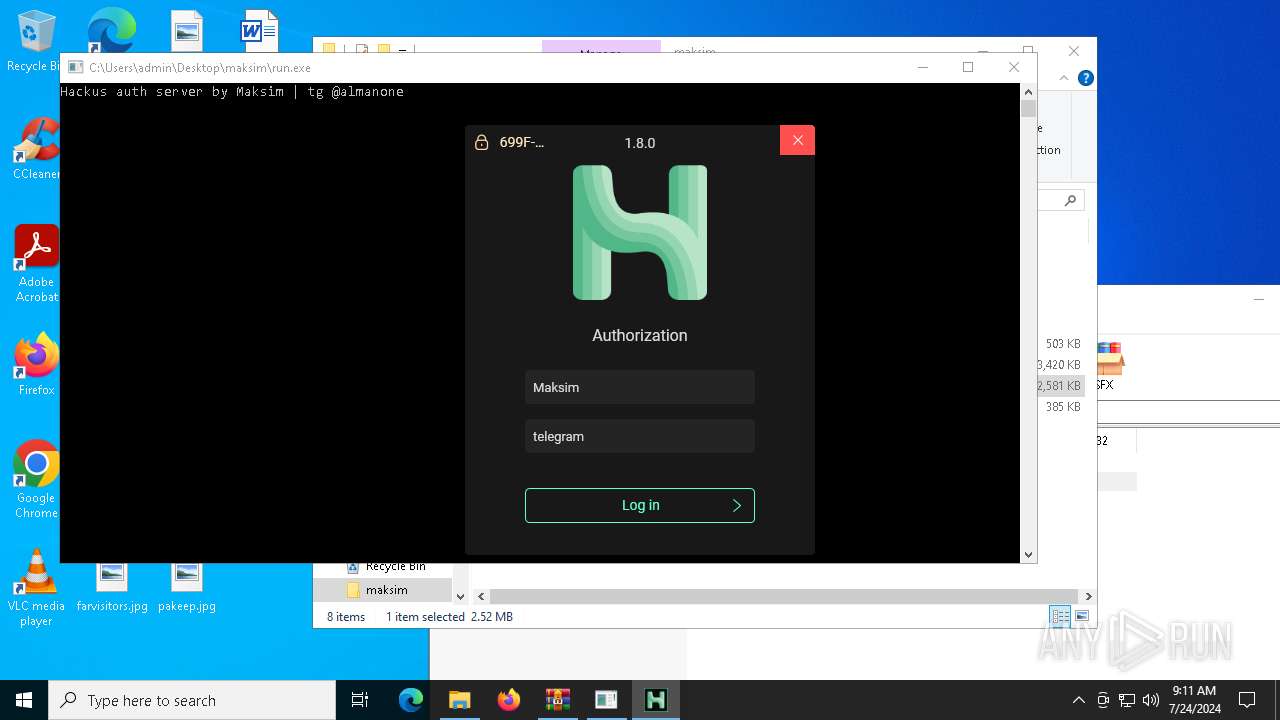
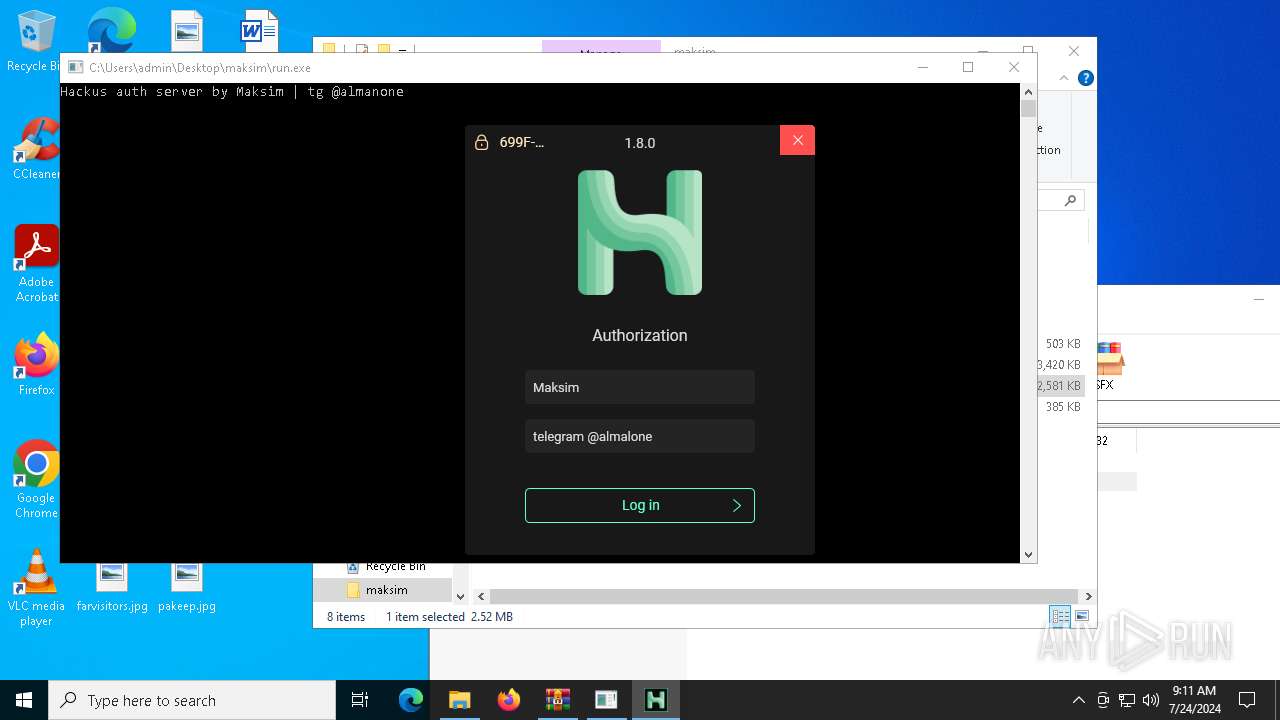
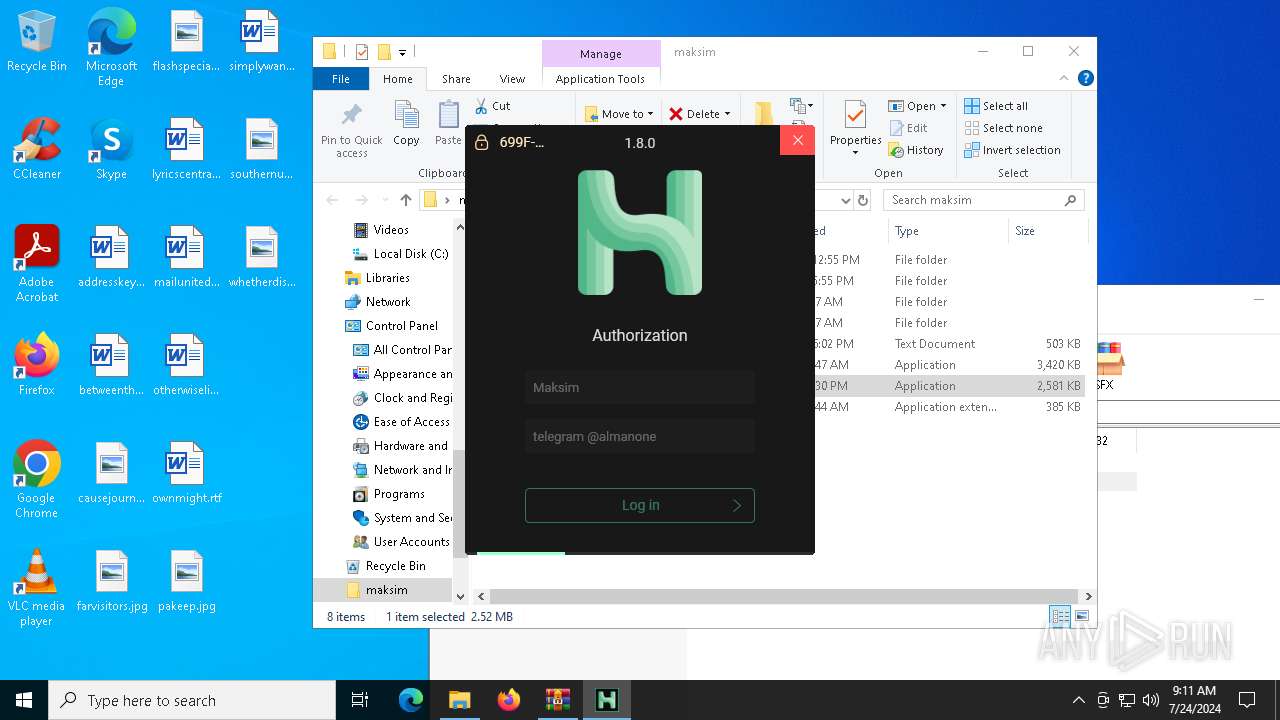
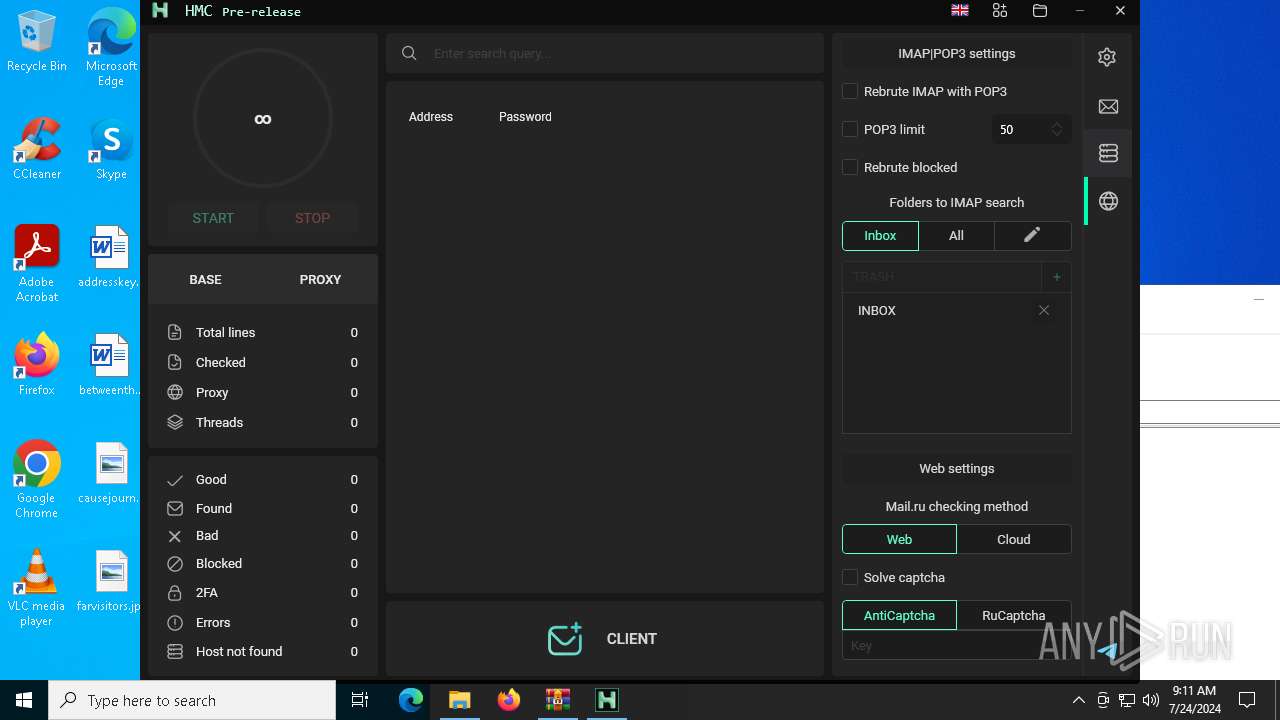
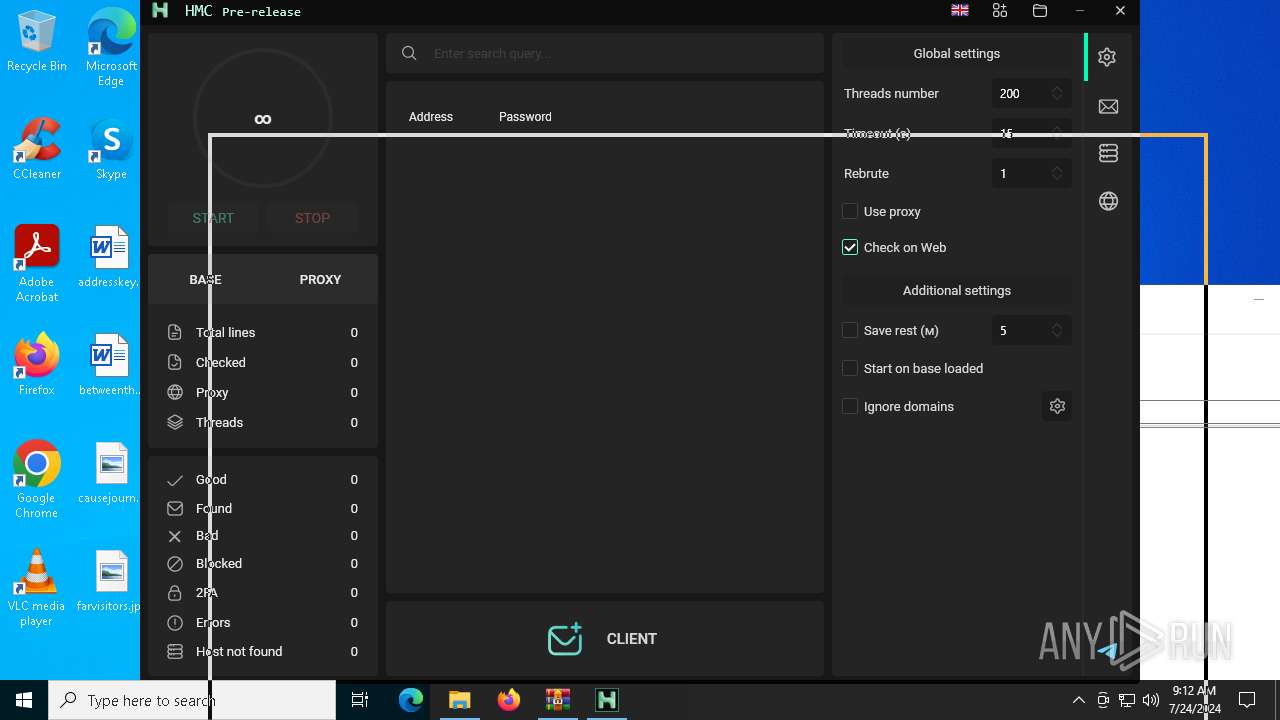
| 5672 | "./HMC 1.8.0.exe" | C:\Users\admin\Desktop\maksim\HMC 1.8.0.exe | — | run.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Hackus Mail Checker Reforged Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
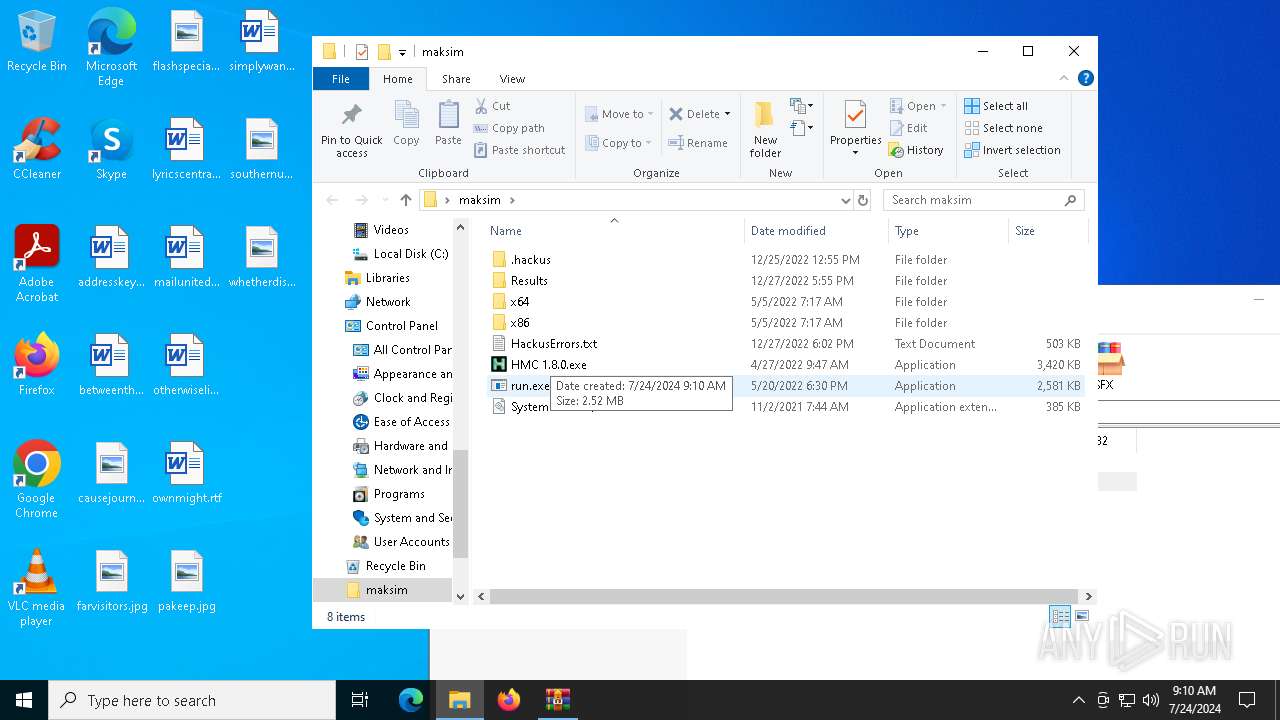
| 6444 | "C:\Users\admin\Desktop\maksim\run.exe" | C:\Users\admin\Desktop\maksim\run.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 6820 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 793
Read events
1 787
Write events
6
Delete events
0
Modification events
| (PID) Process: | (1108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (1108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\maksim.rar | |||
| (PID) Process: | (1108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
5
Suspicious files
1
Text files
62
Unknown types
0
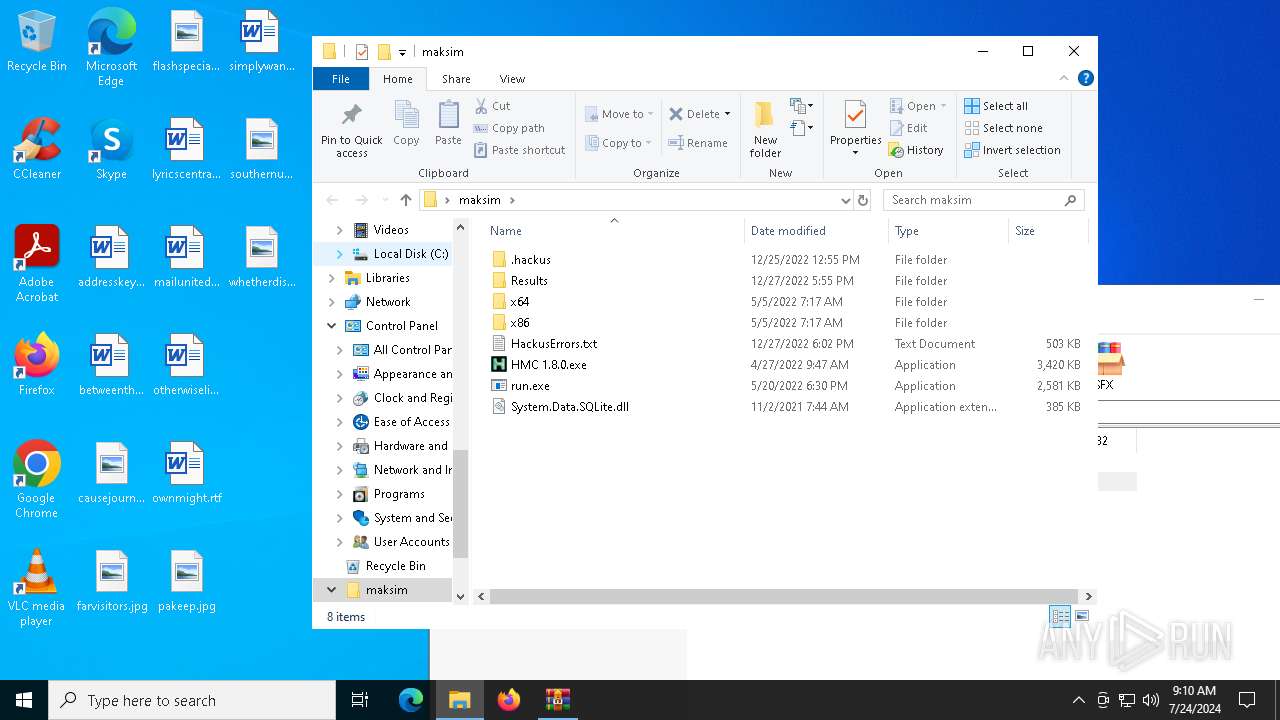
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
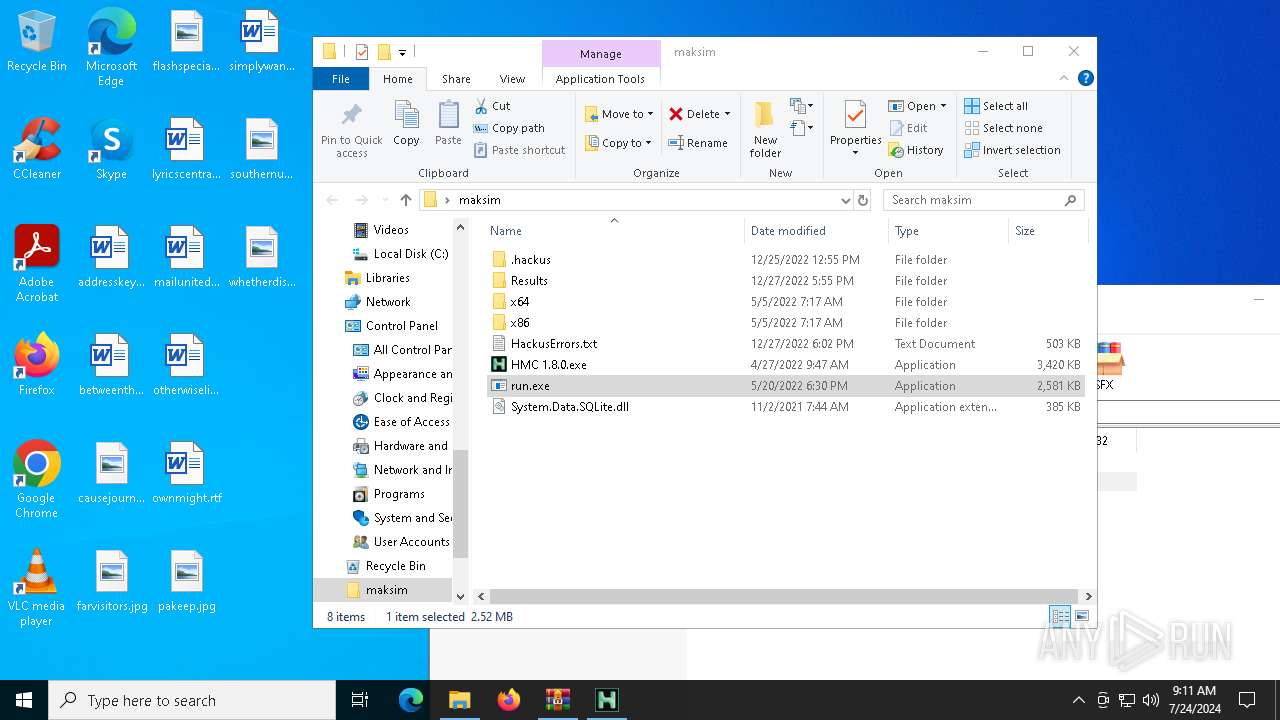
| 1108 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1108.1198\maksim\.hackus\Configuration.cfg | — | |
MD5:— | SHA256:— | |||
| 1108 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1108.1198\maksim\HMC 1.8.0.exe | executable | |
MD5:37974F0FE30D3A228ADCB38DE7D9A02A | SHA256:471D56F4F0EC0D6FF60A0266C77F9FAA51EF42096E0EC0F8D6AEB1F242B78E6A | |||
| 1108 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1108.1198\maksim\HackusErrors.txt | text | |
MD5:8D6DC990844364AB08EE0D86026C9867 | SHA256:D5AC8478BAFF3472658A99AD519BC1B143772F0DC9180B83465E3524FC909F6C | |||
| 1108 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1108.1198\maksim\Results\25.12.2022 14.20 — 84K_PRIVATE_UKRAINE\TwoFactor.txt | text | |
MD5:5D121D7CDF3351570DF98285727FA4C1 | SHA256:72D170E529D272029F747EB257D42A6F2116AAEA05CE4FD3B20891B3292A60D1 | |||
| 1108 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1108.1198\maksim\Results\25.12.2022 14.20 — 84K_PRIVATE_UKRAINE\Blocked.txt | text | |
MD5:F1AC3B553B3857DDF80775AE1143F02E | SHA256:0E290710FAD6EDF918F77921086B8359E21EC796262FE72D44738D9813DC409B | |||
| 1108 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1108.1198\maksim\Results\25.12.2022 14.20 — 84K_PRIVATE_UKRAINE\Bad.txt | text | |
MD5:32EB8D013392AB7AA3DE0848FBB3AD6E | SHA256:025553D46DE9A26AE035C00F148F58CC9B0B91D73E1E92AF848E075B9DD2DBB1 | |||
| 1108 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1108.1198\maksim\Results\25.12.2022 14.20 — 84K_PRIVATE_UKRAINE\Error.txt | text | |
MD5:66C9DC9F8770B5AF3A297E869181F59B | SHA256:A8CC9D5A2F290FCE313F9A011AE9A3708F066D016117ECCE293F64826ABC43D9 | |||
| 1108 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1108.1198\maksim\Results\25.12.2022 14.18 — 16.7K_PRIVATE_MYR_Gaming Combo\HostNotFound.txt | text | |
MD5:B642524CCB32E808925C5BCD2FF9EE53 | SHA256:2349CE782A3E2CFD3A35894F1ABFC22DC692C590CF88E9908706E24E936A466B | |||
| 1108 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1108.1198\maksim\Results\25.12.2022 14.22 — 26.7K_PRIVATE_Yahoo_shoping\Blocked.txt | text | |
MD5:1797FC78DEB52263E930EA467E1AA785 | SHA256:4763723576DDDEE39F57804505D41508672854FE51095CE7FED799F39E3B66C3 | |||
| 1108 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1108.1198\maksim\Results\25.12.2022 14.20 — 84K_PRIVATE_UKRAINE\Ok.txt | text | |
MD5:0F85C1E8C708DD842AD0FE773136B89B | SHA256:FC1DD79FC52EAB507A42EED353C1430FFBC6A8D6937C64C8D293CED4C8BD61A2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
46
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
916 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3148 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1468 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6012 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3044 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3360 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 92.123.104.41:443 | — | Akamai International B.V. | DE | unknown |
4204 | svchost.exe | 4.209.32.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
784 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6012 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |