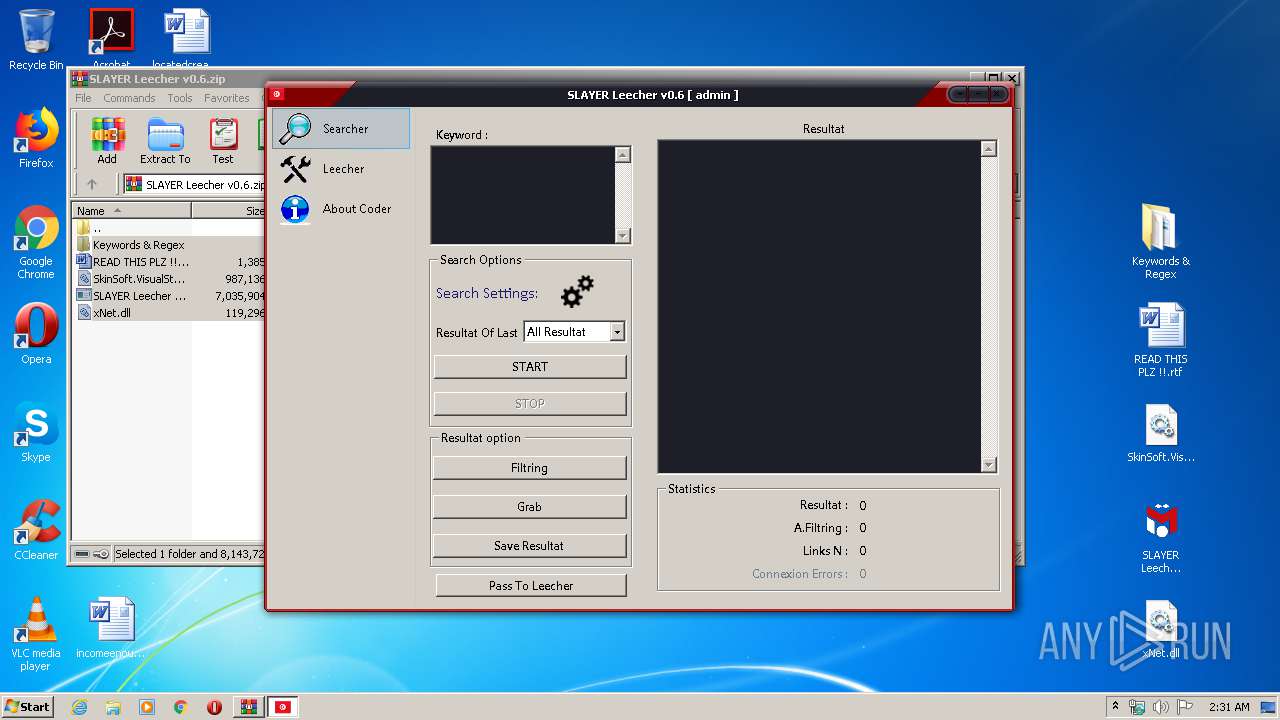
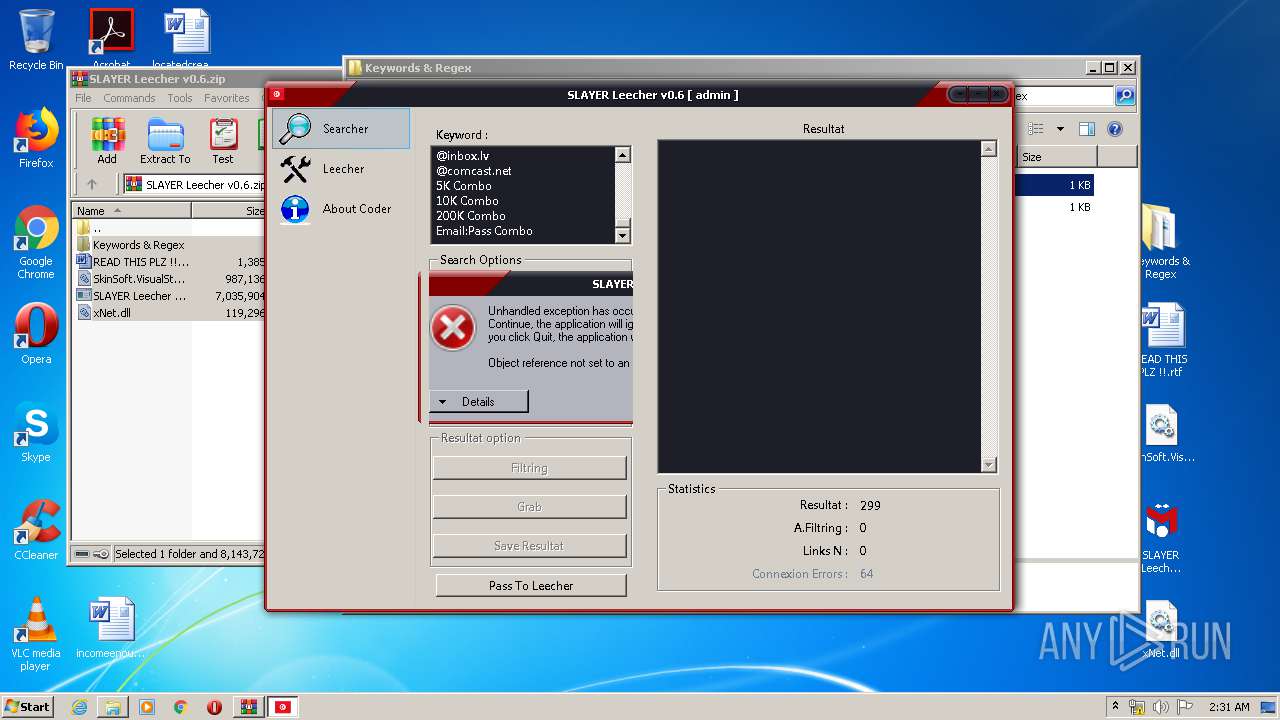
| File name: | SLAYER Leecher v0.6.zip |
| Full analysis: | https://app.any.run/tasks/414e34c3-796d-4494-845f-b0b8306eb3ec |
| Verdict: | Malicious activity |
| Analysis date: | April 12, 2020, 01:30:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | A03646560ED643E4778DDB42856C293B |
| SHA1: | 4D7D9464D036E1FFEF97C6171FE0CB4318F4D8CB |
| SHA256: | BA4AD2BCBFF9362B84CAD8E3C3A9A3D0174A5DBB7FC79B97D75322D0F05FCBFE |
| SSDEEP: | 196608:i/gyf/cSkc3cdsIIf65fOs7BXIDPs7eXFvdQnlHB3:izHcS2vfz7Bi1X7u |
MALICIOUS
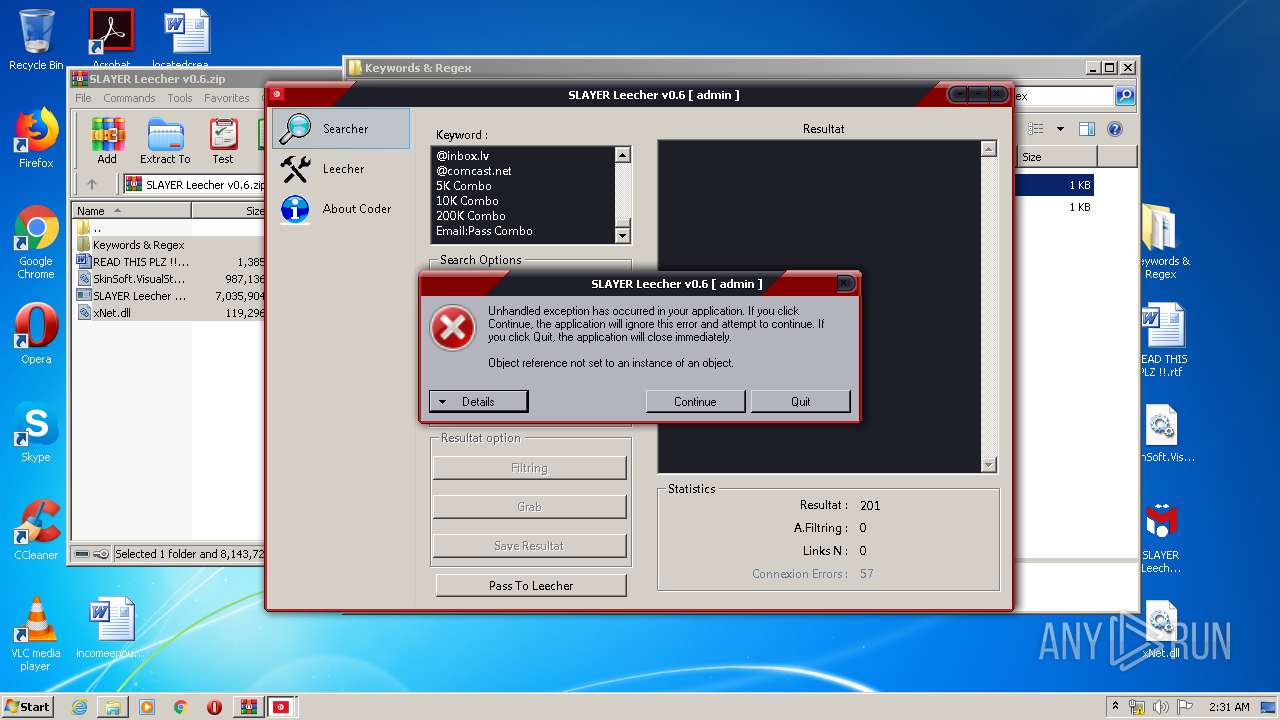
Loads dropped or rewritten executable
- SLAYER Leecher v0.6.exe (PID: 924)
- SearchProtocolHost.exe (PID: 744)
Application was dropped or rewritten from another process
- SLAYER Leecher v0.6.exe (PID: 924)
SUSPICIOUS
Executable content was dropped or overwritten
- SLAYER Leecher v0.6.exe (PID: 924)
Reads Environment values
- SLAYER Leecher v0.6.exe (PID: 924)
INFO
Manual execution by user
- NOTEPAD.EXE (PID: 376)
- SLAYER Leecher v0.6.exe (PID: 924)
Reads settings of System Certificates
- SLAYER Leecher v0.6.exe (PID: 924)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .kmz | | | Google Earth saved working session (60) |
|---|---|---|
| .zip | | | ZIP compressed archive (40) |
EXIF
ZIP
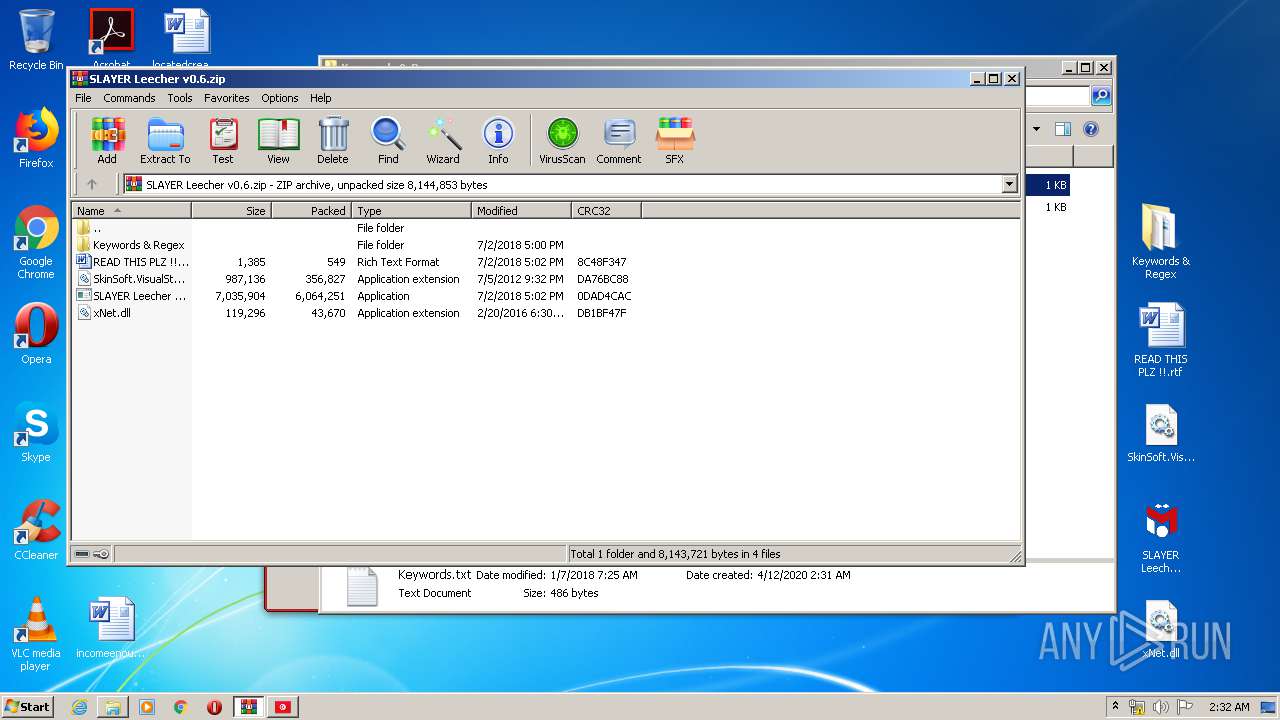
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2012:07:05 13:32:12 |
| ZipCRC: | 0xda76bc88 |
| ZipCompressedSize: | 356827 |
| ZipUncompressedSize: | 987136 |
| ZipFileName: | SkinSoft.VisualStyler.dll |
Total processes
37
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
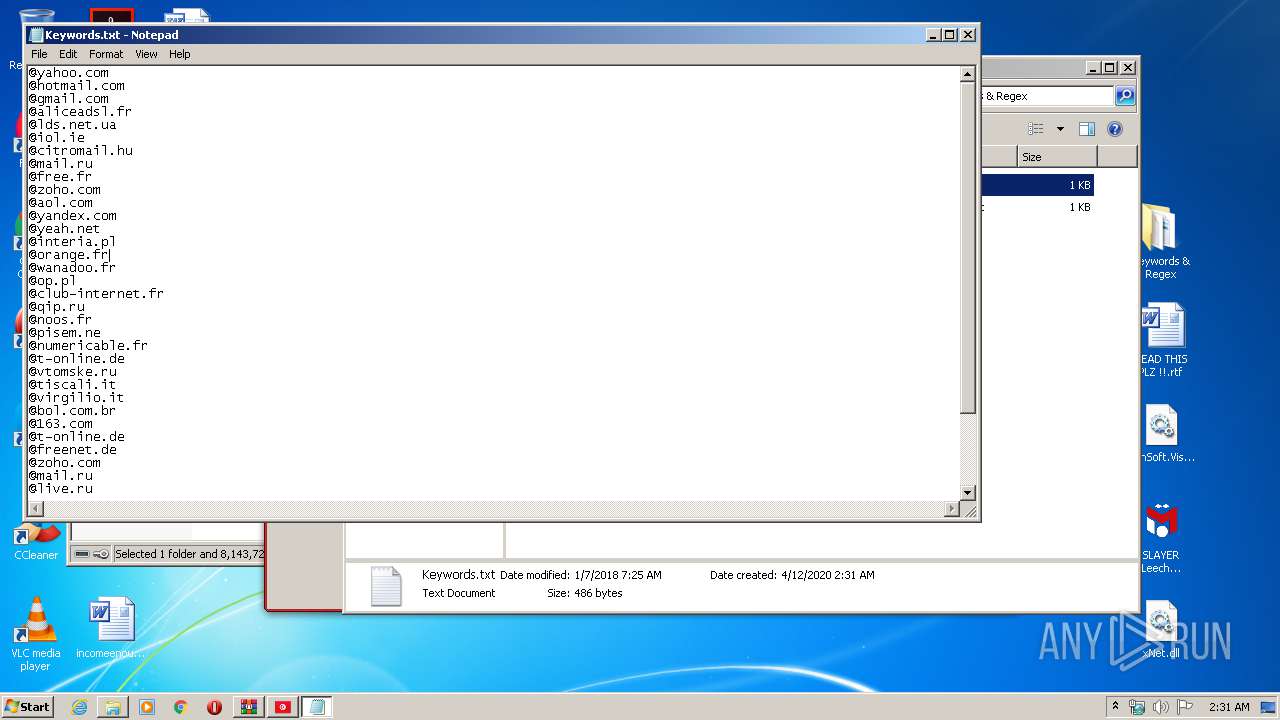
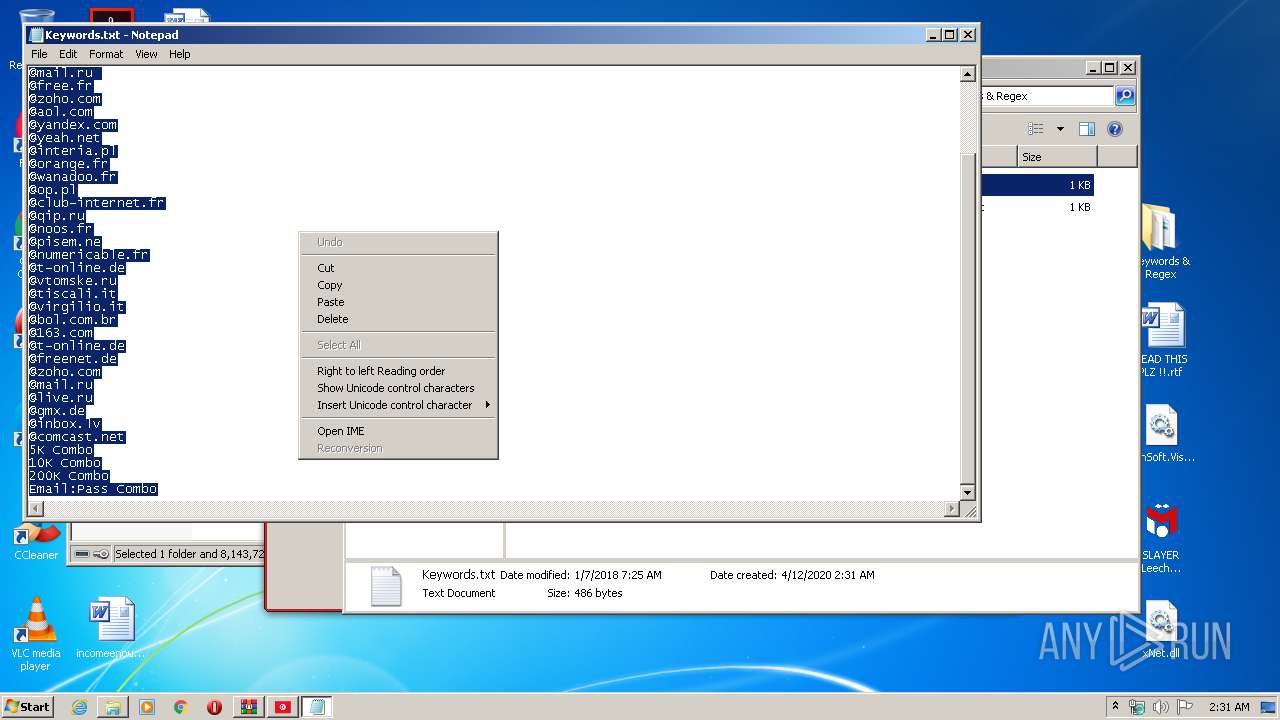
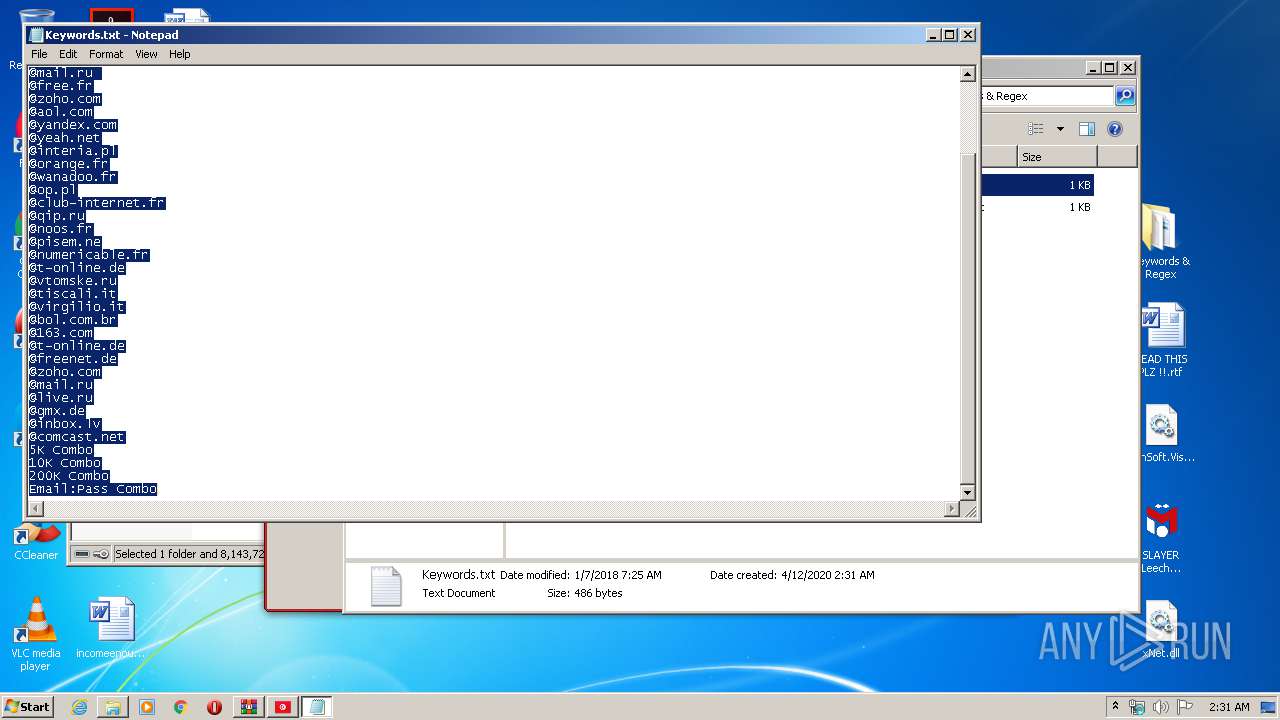
| 376 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Keywords & Regex\Keywords.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 744 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
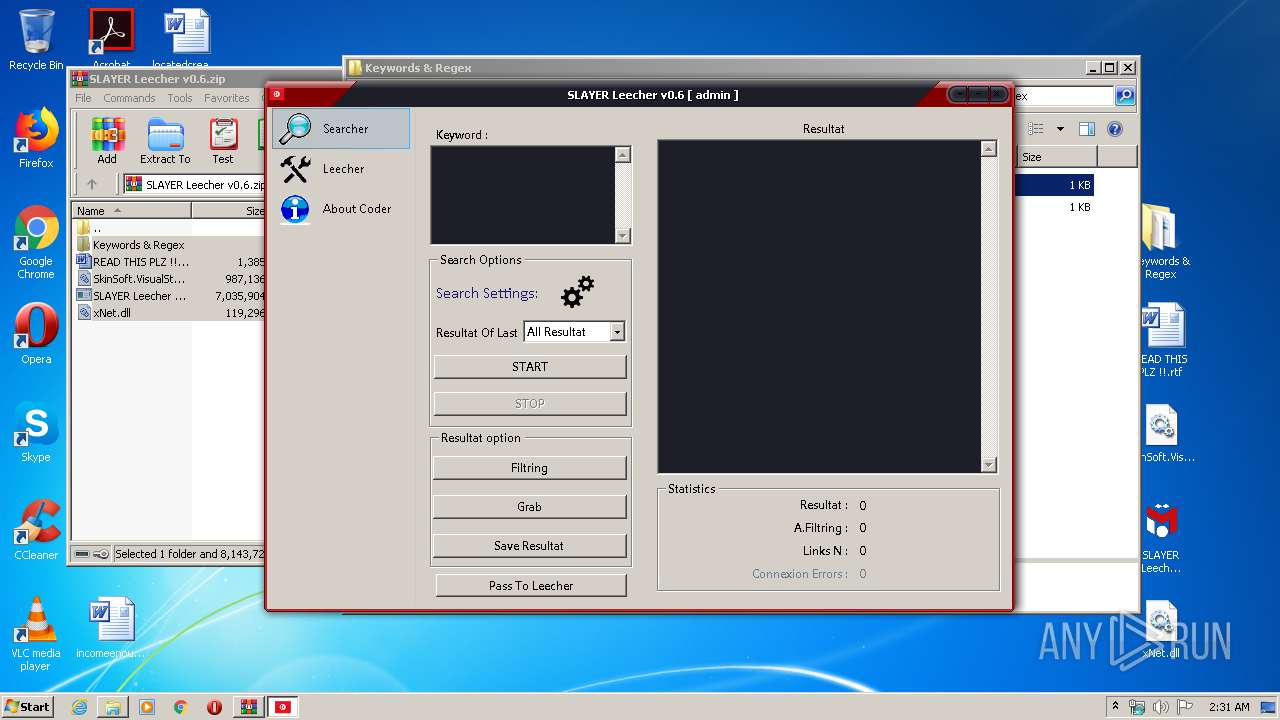
| 924 | "C:\Users\admin\Desktop\SLAYER Leecher v0.6.exe" | C:\Users\admin\Desktop\SLAYER Leecher v0.6.exe | explorer.exe | ||||||||||||
User: admin Company: Iheb Briki Integrity Level: MEDIUM Description: SLAYER Leecher Exit code: 0 Version: 0.4.1 Modules
| |||||||||||||||
| 3640 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\SLAYER Leecher v0.6.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
863
Read events
812
Write events
51
Delete events
0
Modification events
| (PID) Process: | (3640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3640) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SLAYER Leecher v0.6.zip | |||
| (PID) Process: | (3640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (744) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (744) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3640 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3640.39604\SkinSoft.VisualStyler.dll | — | |
MD5:— | SHA256:— | |||
| 3640 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3640.39604\SLAYER Leecher v0.6.exe | — | |
MD5:— | SHA256:— | |||
| 3640 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3640.39604\xNet.dll | — | |
MD5:— | SHA256:— | |||
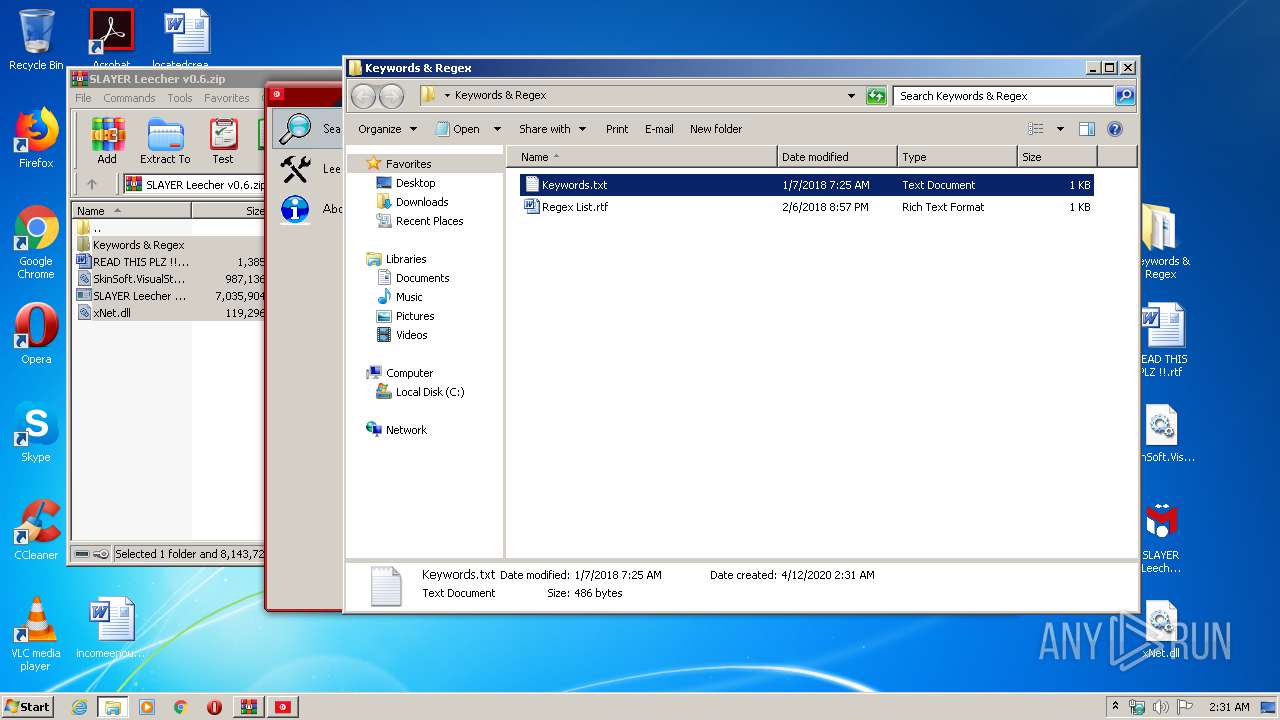
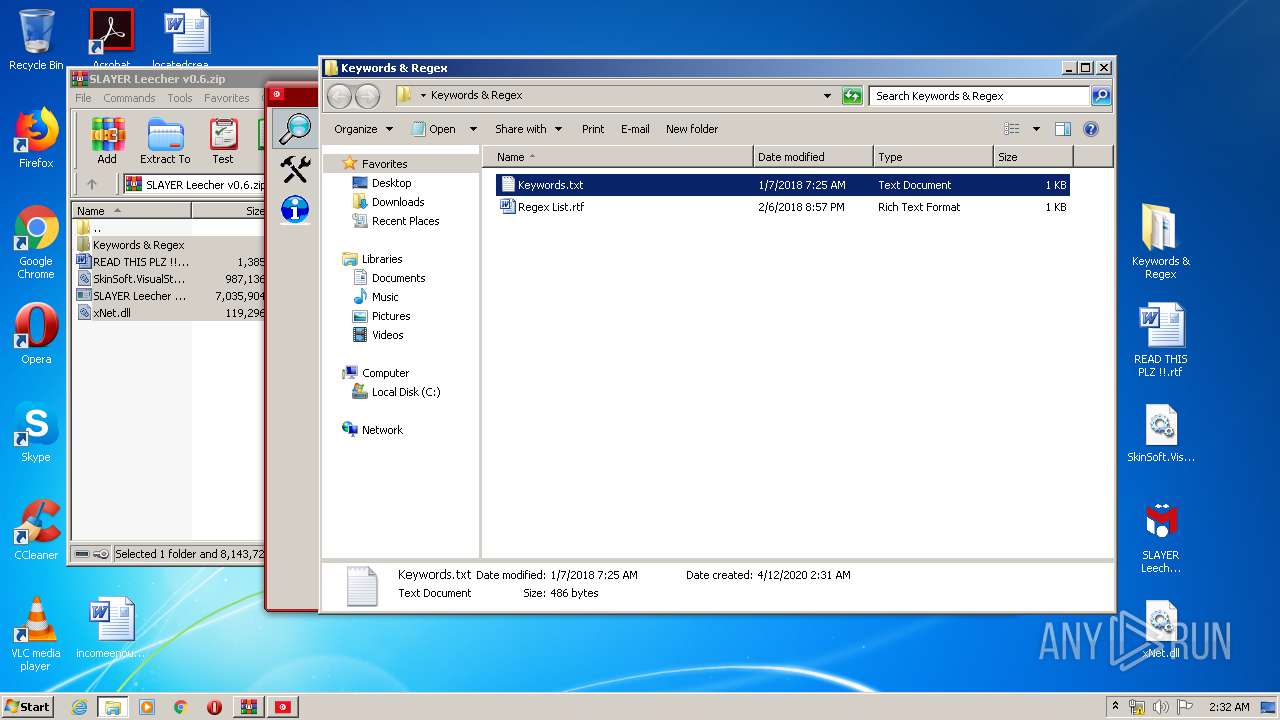
| 3640 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3640.39604\Keywords & Regex\Keywords.txt | — | |
MD5:— | SHA256:— | |||
| 3640 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3640.39604\Keywords & Regex\Regex List.rtf | — | |
MD5:— | SHA256:— | |||
| 3640 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3640.39604\READ THIS PLZ !!.rtf | — | |
MD5:— | SHA256:— | |||
| 924 | SLAYER Leecher v0.6.exe | C:\Users\admin\AppData\Local\SkinSoft\VisualStyler\2.3.5.0\x86\ssapihook.dll | executable | |
MD5:D7F644C06B4CDE60651D02AED6B4174D | SHA256:A99EA2F5759B34859B484AFA3A58CE82A7F3BF792886A6C838DB852D517D9C0D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
104
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
924 | SLAYER Leecher v0.6.exe | GET | 302 | 172.217.16.131:80 | http://www.google.tn/search?q=%0A@hotmail.com&num=100&tbs=qdr:all&ei=-d2PUqnoIOyp7AbP2IGoBQ&start=50&sa=N&biw=1366&bih=604 | US | html | 461 b | whitelisted |
924 | SLAYER Leecher v0.6.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/search?q=%0A@iol.ie&start=55 | US | html | 37.8 Kb | whitelisted |
924 | SLAYER Leecher v0.6.exe | GET | 429 | 172.217.22.36:80 | http://www.google.com/sorry/index?continue=http://www.google.fr/search%3Fq%3D%40yahoo.com%26num%3D100%26tbs%3Dqdr:all%26ei%3D-d2PUqnoIOyp7AbP2IGoBQ%26start%3D50%26sa%3DN%26biw%3D1366%26bih%3D604&q=EgRUESRLGIDfyfQFIhkA8aeDS91Ah_YfdxozOfD3bqqXp_oFI8I4MgFy | US | html | 3.09 Kb | malicious |
924 | SLAYER Leecher v0.6.exe | GET | 302 | 172.217.23.99:80 | http://www.google.ru/search?q=%0A@lds.net.ua&num=100&tbs=qdr:all&ei=-d2PUqnoIOyp7AbP2IGoBQ&start=50&sa=N&biw=1366&bih=604 | US | html | 460 b | whitelisted |
924 | SLAYER Leecher v0.6.exe | GET | 429 | 172.217.22.36:80 | http://www.google.com/sorry/index?continue=http://www.google.ru/search%3Fq%3D%250A%40lds.net.ua%26num%3D100%26tbs%3Dqdr:all%26ei%3D-d2PUqnoIOyp7AbP2IGoBQ%26start%3D50%26sa%3DN%26biw%3D1366%26bih%3D604&q=EgRUESRLGIbfyfQFIhkA8aeDS-oOJz_7IgmO7xqDYxAXZw0HpqFlMgFy | US | html | 3.10 Kb | malicious |
924 | SLAYER Leecher v0.6.exe | GET | 302 | 172.217.16.131:80 | http://www.google.tn/search?q=%0A@iol.ie&num=100&tbs=qdr:all&ei=-d2PUqnoIOyp7AbP2IGoBQ&start=50&sa=N&biw=1366&bih=604 | US | html | 456 b | whitelisted |
924 | SLAYER Leecher v0.6.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/search?q=%0A@gmail.com&start=55 | US | html | 38.0 Kb | whitelisted |
924 | SLAYER Leecher v0.6.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/search?q=%0A@lds.net.ua&start=55 | US | html | 38.0 Kb | whitelisted |
924 | SLAYER Leecher v0.6.exe | GET | 302 | 172.217.22.3:80 | http://www.google.fr/search?q=@yahoo.com&num=100&tbs=qdr:all&ei=-d2PUqnoIOyp7AbP2IGoBQ&start=50&sa=N&biw=1366&bih=604 | US | html | 454 b | whitelisted |
924 | SLAYER Leecher v0.6.exe | GET | 429 | 172.217.22.36:80 | http://www.google.com/sorry/index?continue=http://www.google.tn/search%3Fq%3D%250A%40aliceadsl.fr%26num%3D100%26tbs%3Dqdr:all%26ei%3D-d2PUqnoIOyp7AbP2IGoBQ%26start%3D50%26sa%3DN%26biw%3D1366%26bih%3D604&q=EgRUESRLGIbfyfQFIhkA8aeDS6oUH-QsgkL1A5ElE5MMec7ETI29MgFy | US | html | 3.11 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
924 | SLAYER Leecher v0.6.exe | 5.255.255.5:443 | yandex.ru | YANDEX LLC | RU | whitelisted |
924 | SLAYER Leecher v0.6.exe | 172.217.22.36:443 | www.google.com | Google Inc. | US | whitelisted |
924 | SLAYER Leecher v0.6.exe | 79.125.108.55:443 | duckduckgo.com | Amazon.com, Inc. | IE | unknown |
924 | SLAYER Leecher v0.6.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
924 | SLAYER Leecher v0.6.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
924 | SLAYER Leecher v0.6.exe | 172.217.22.67:80 | www.google.ac | Google Inc. | US | whitelisted |
924 | SLAYER Leecher v0.6.exe | 172.217.16.131:80 | www.google.tn | Google Inc. | US | whitelisted |
924 | SLAYER Leecher v0.6.exe | 172.217.22.3:80 | www.google.fr | Google Inc. | US | whitelisted |
924 | SLAYER Leecher v0.6.exe | 172.217.23.99:80 | www.google.ru | Google Inc. | US | whitelisted |
924 | SLAYER Leecher v0.6.exe | 172.217.22.36:80 | www.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| malicious |
www.google.com |
| malicious |
yandex.ru |
| whitelisted |
www.bing.com |
| whitelisted |
duckduckgo.com |
| whitelisted |
www.google.fr |
| whitelisted |
www.google.tn |
| whitelisted |
www.google.ac |
| whitelisted |
www.google.ru |
| whitelisted |