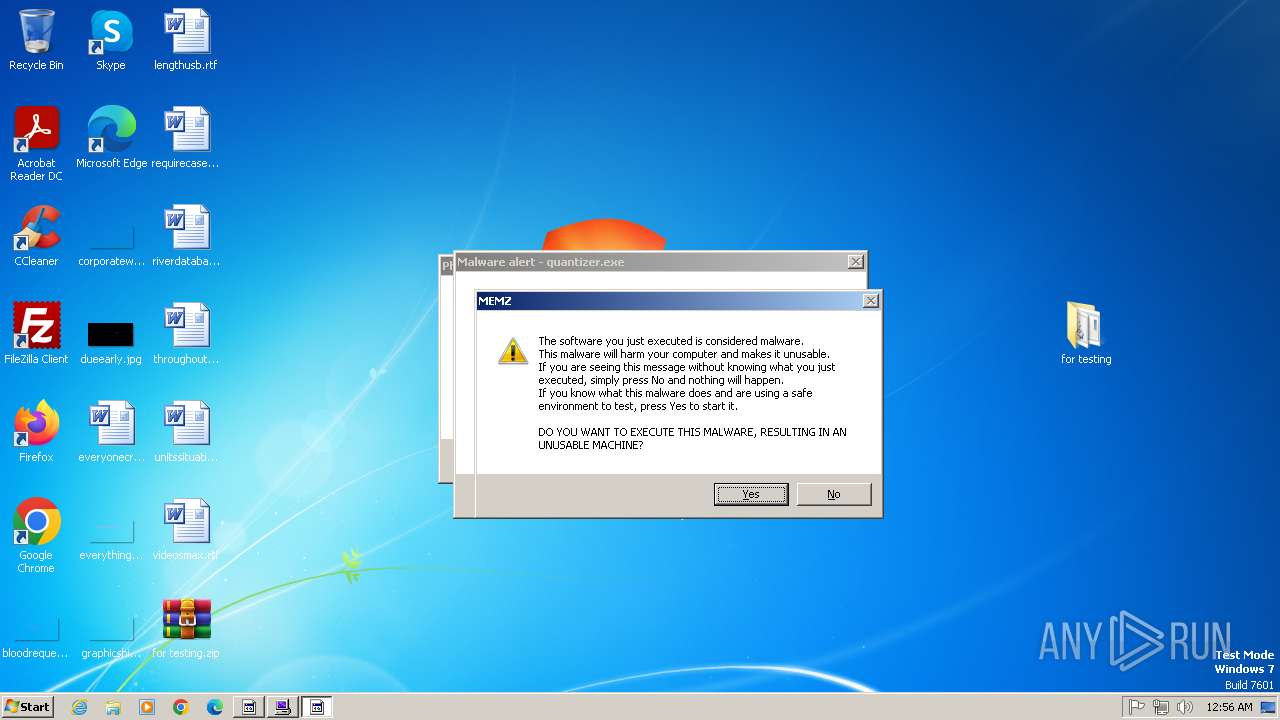
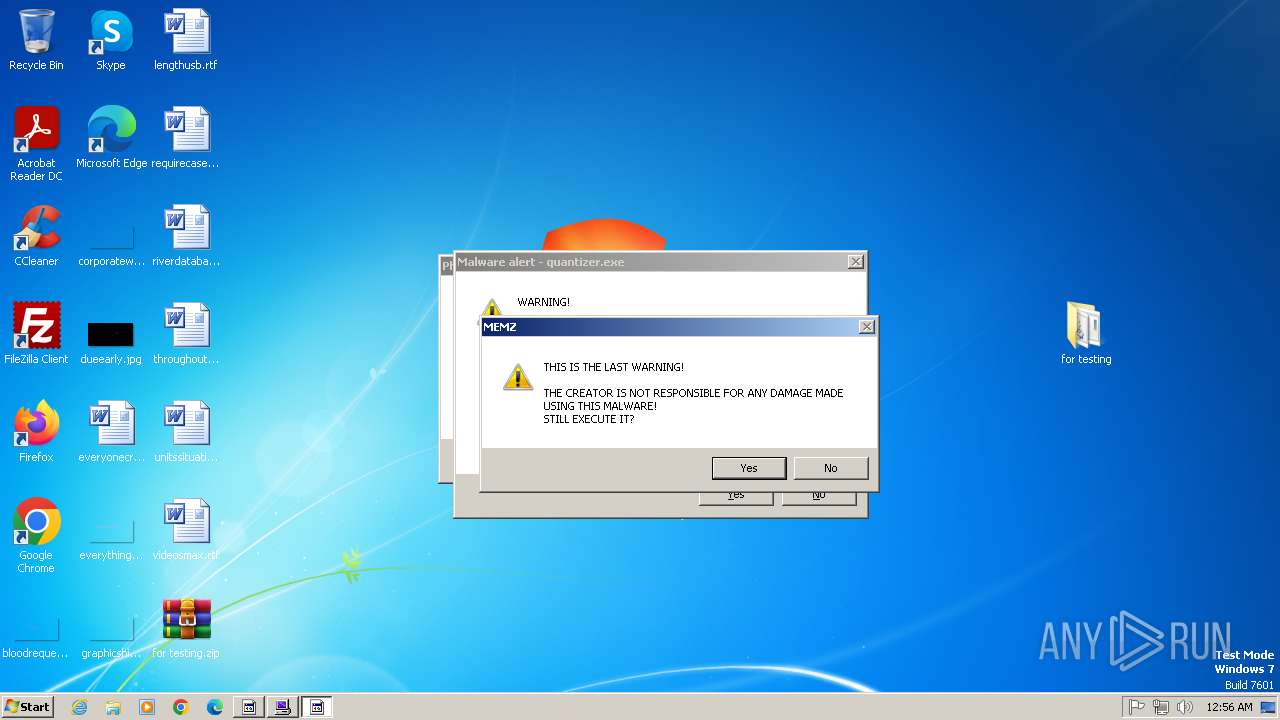
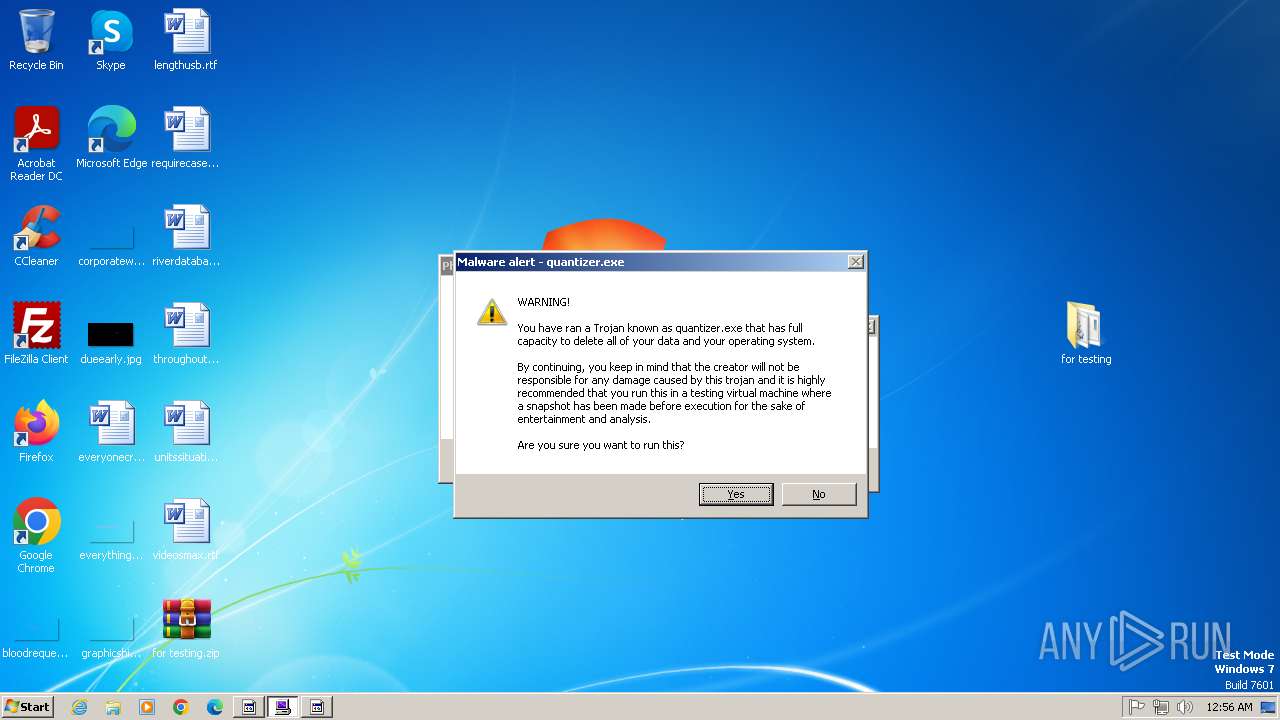
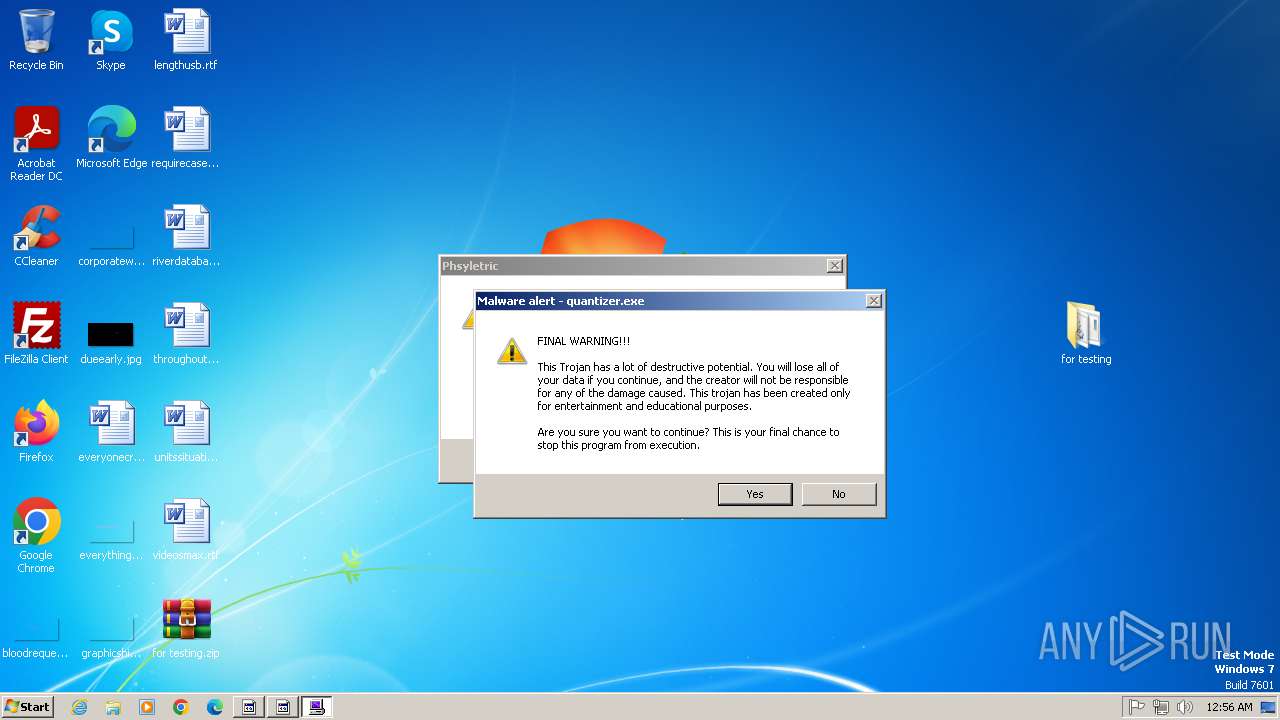
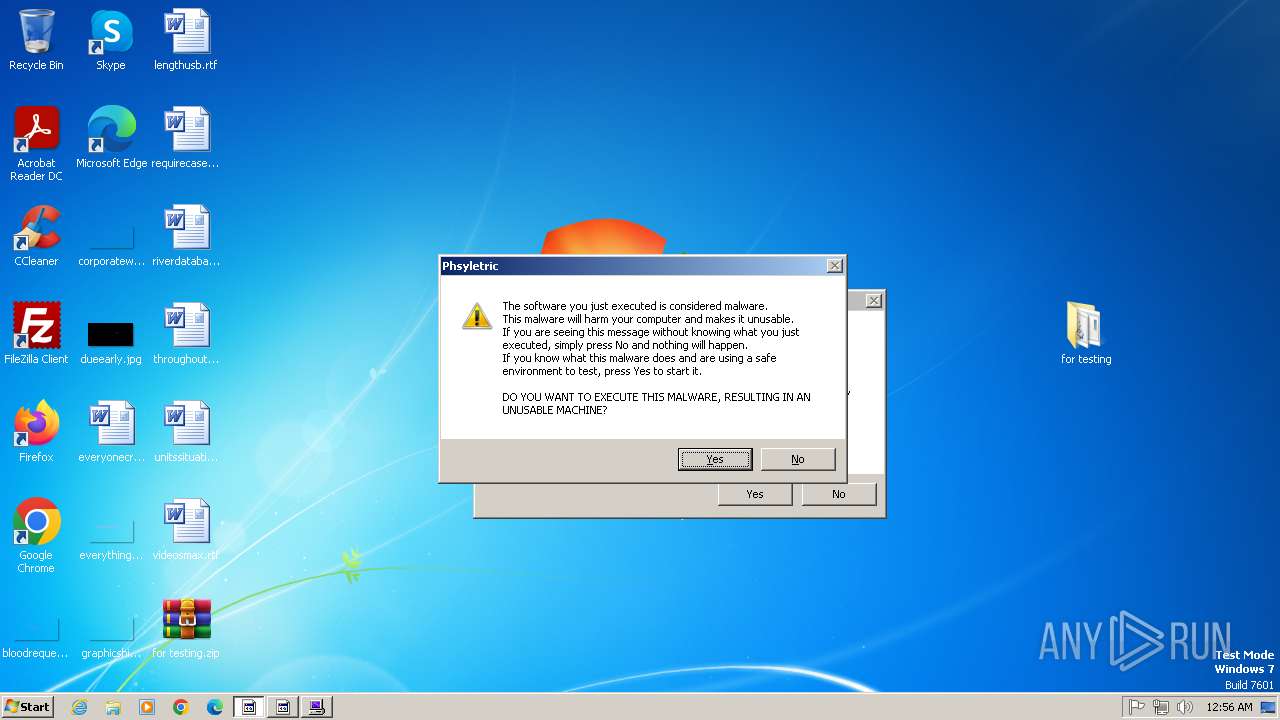
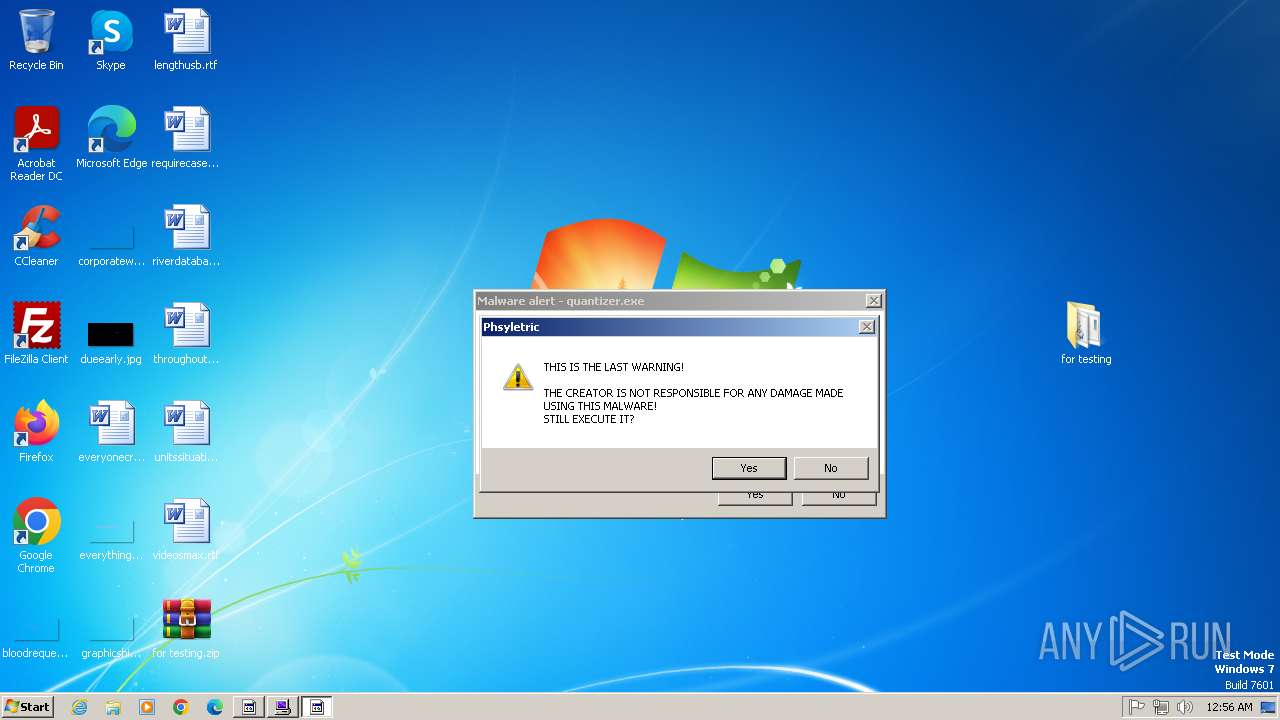
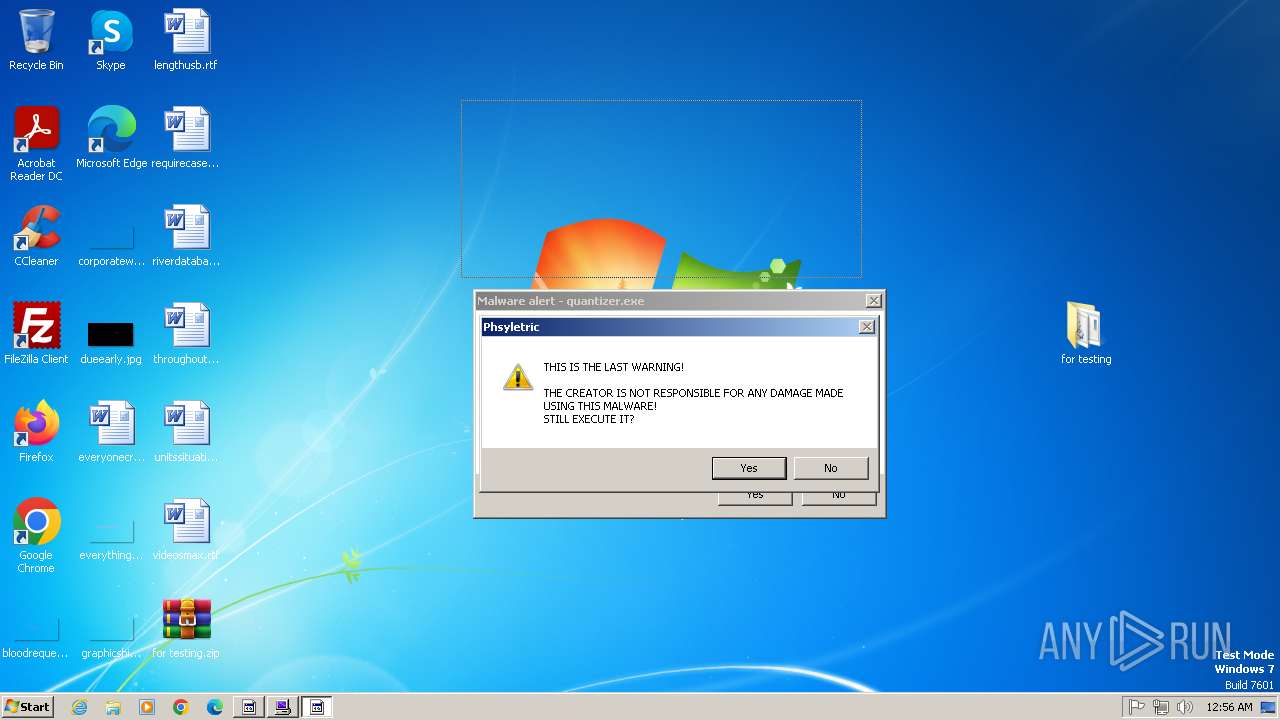
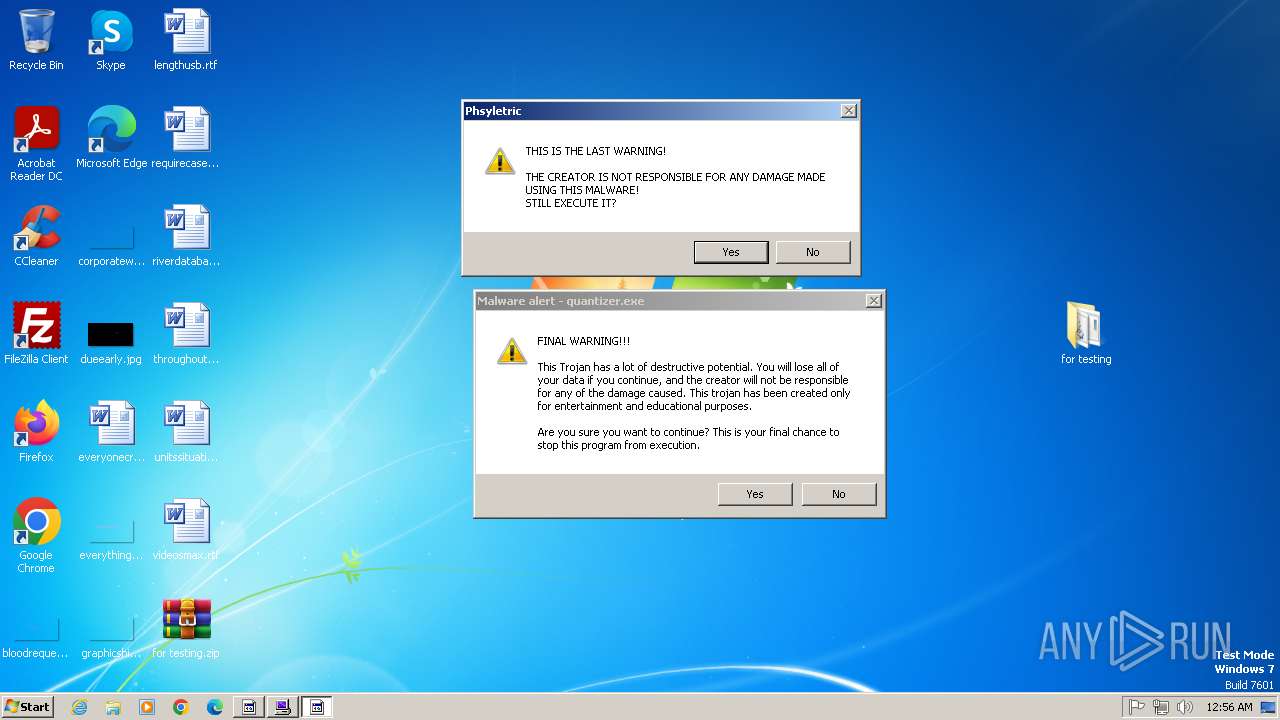
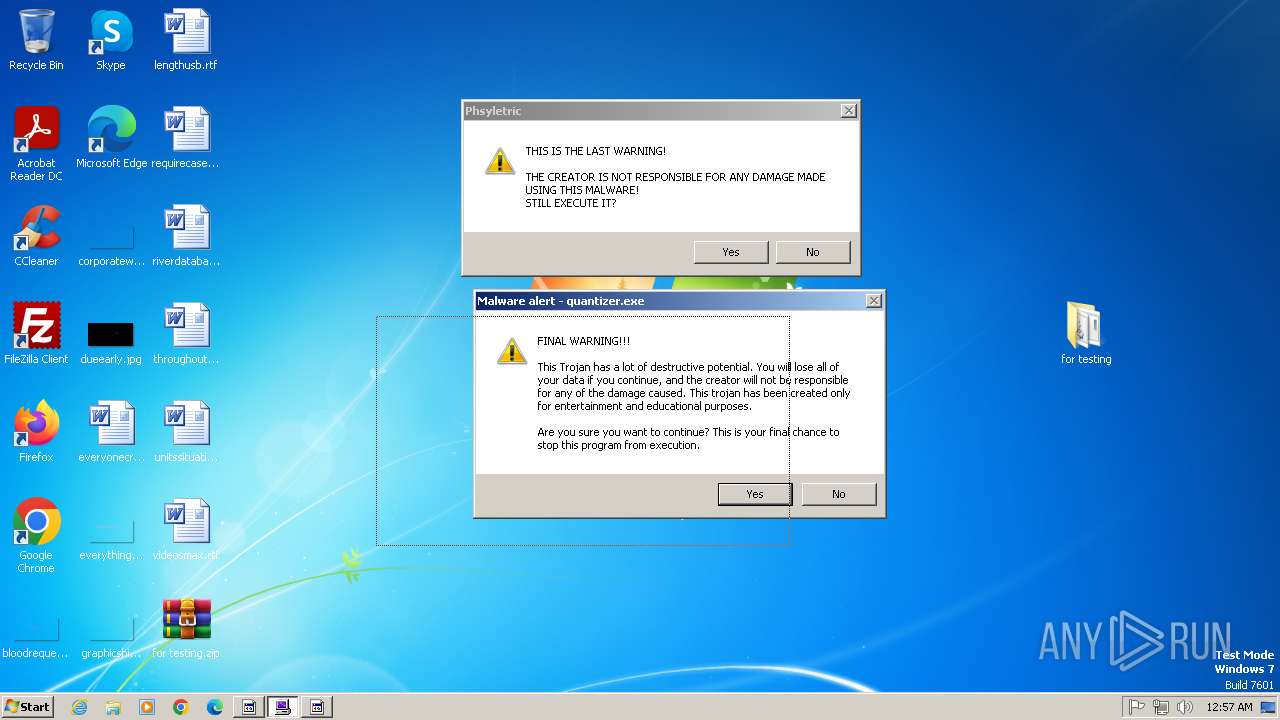
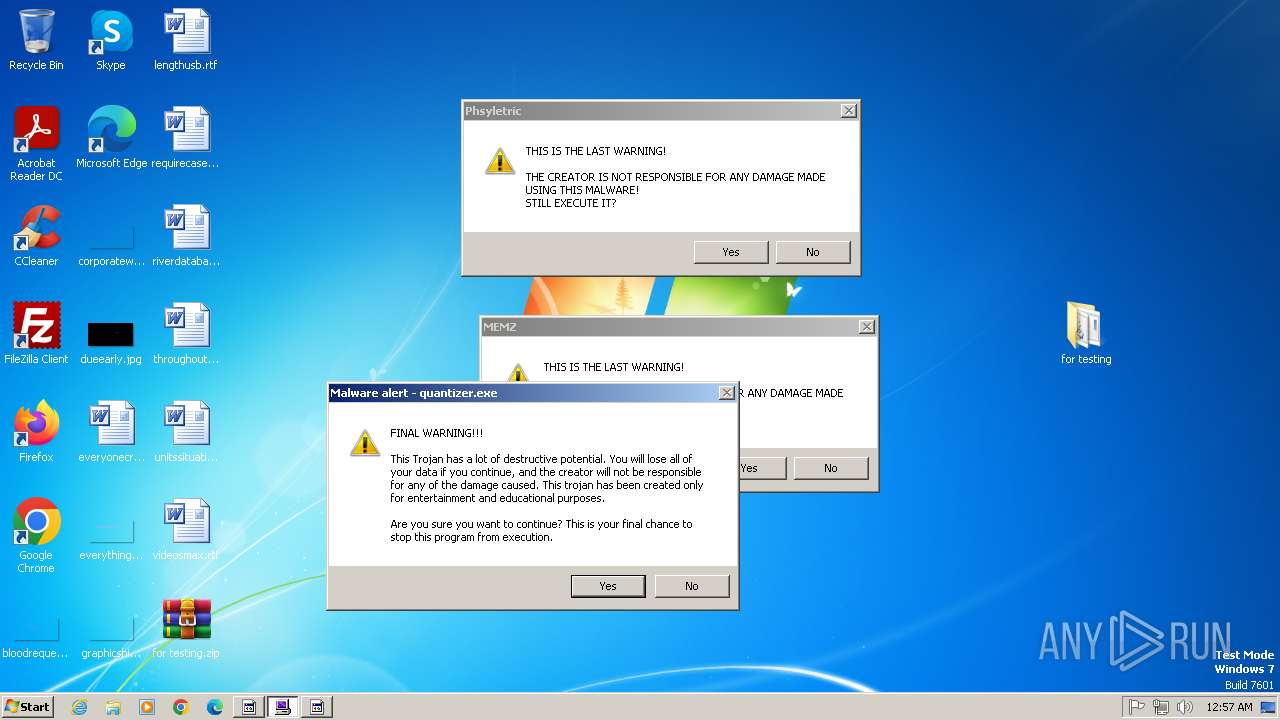
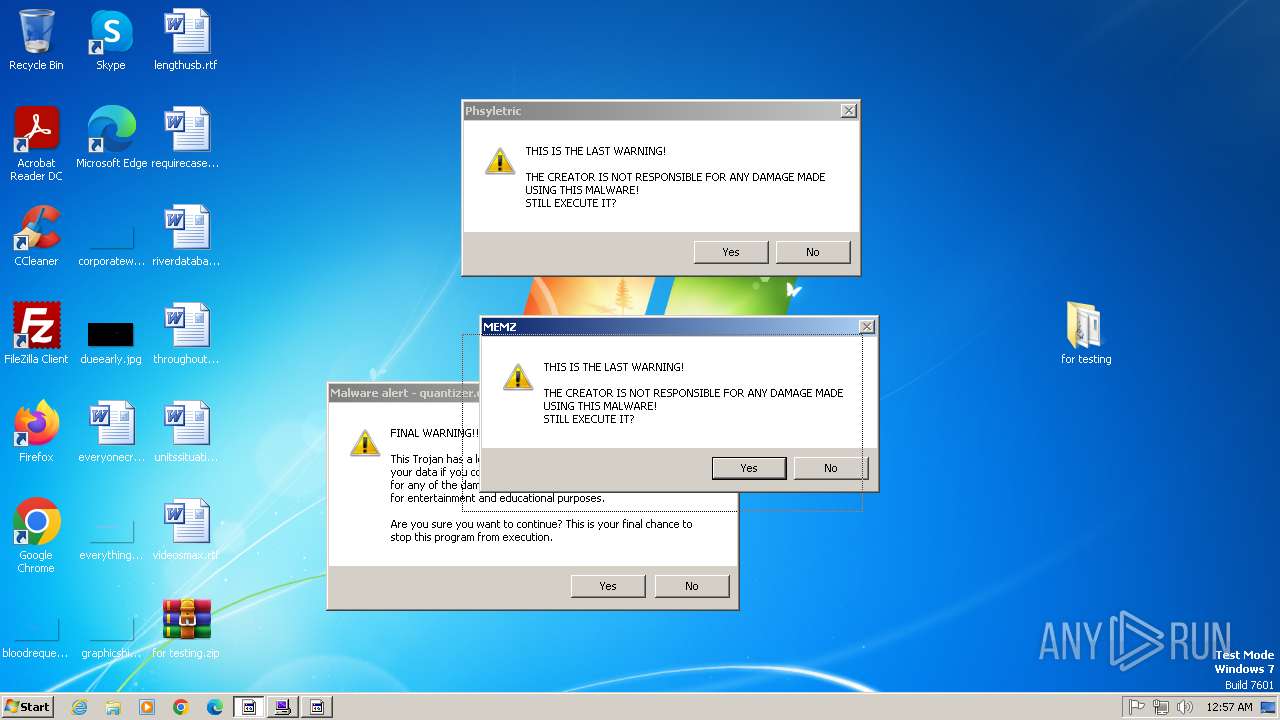
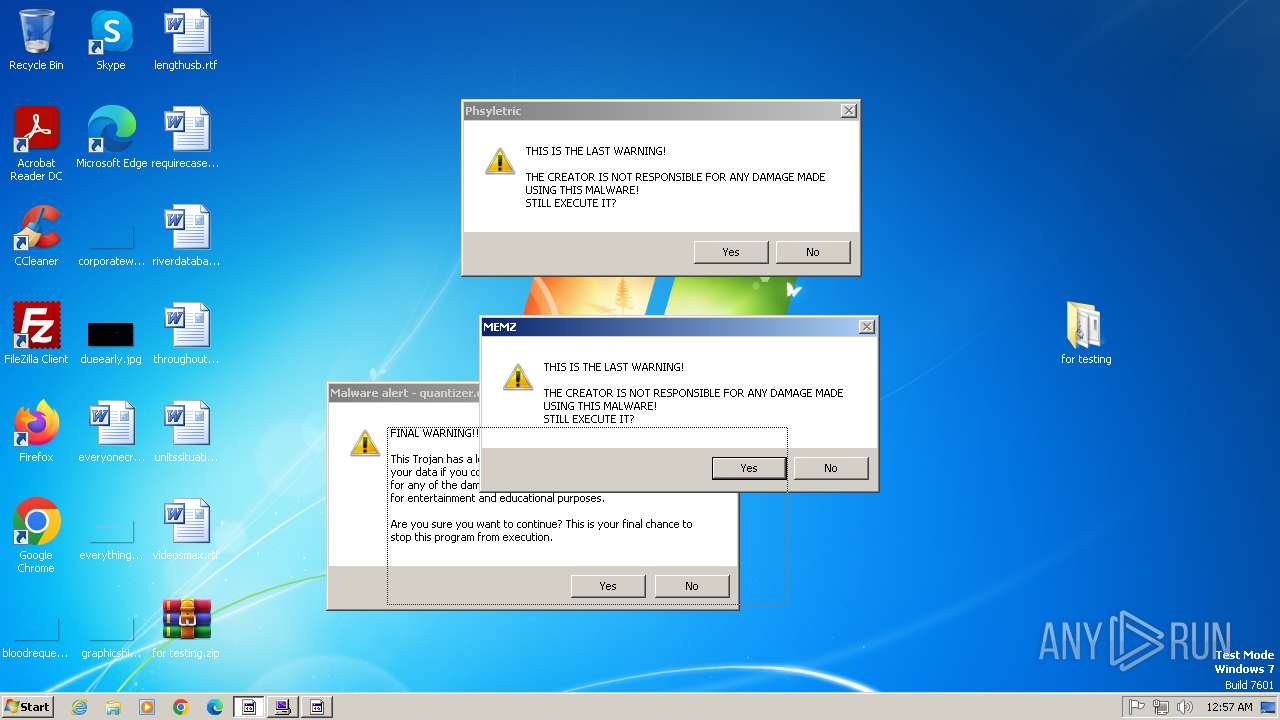
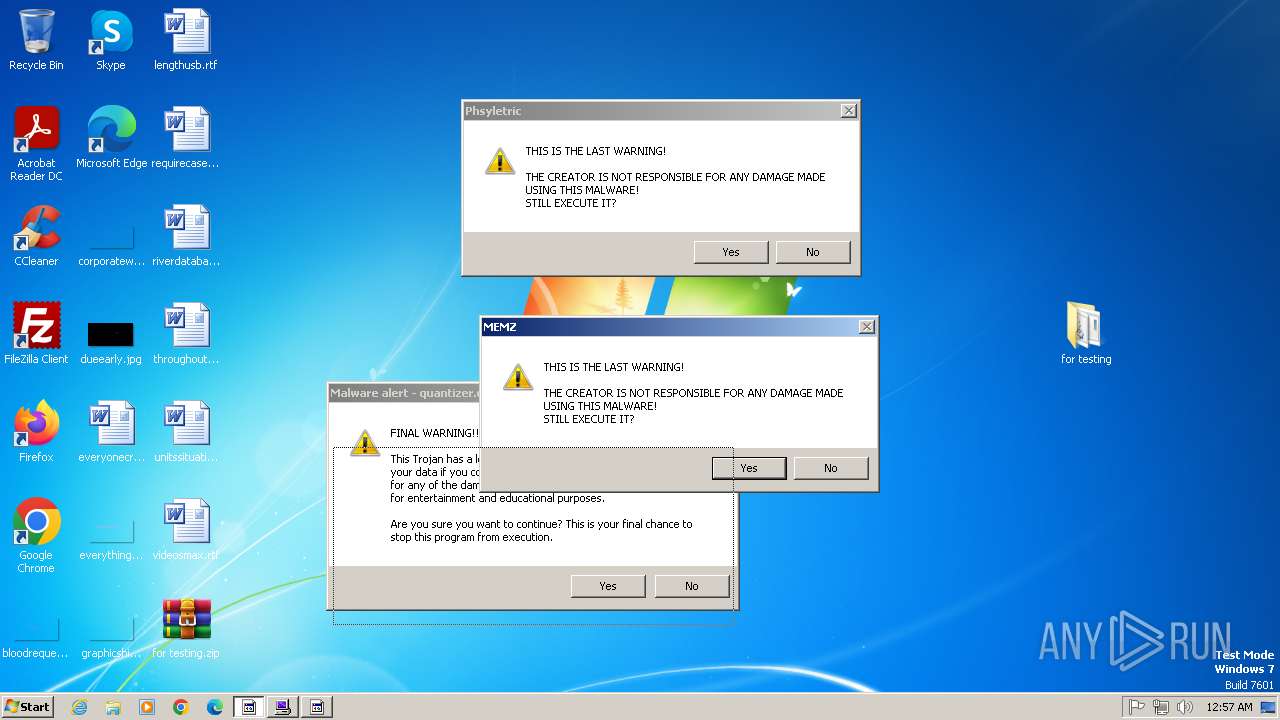
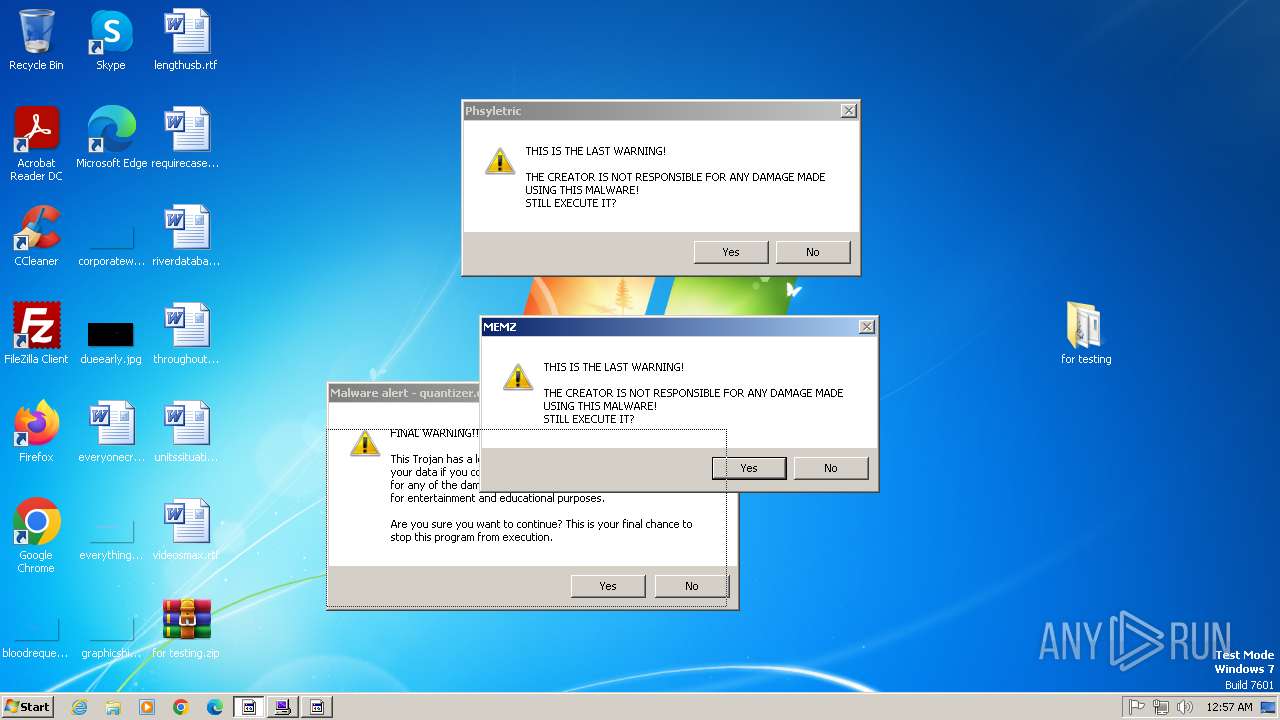
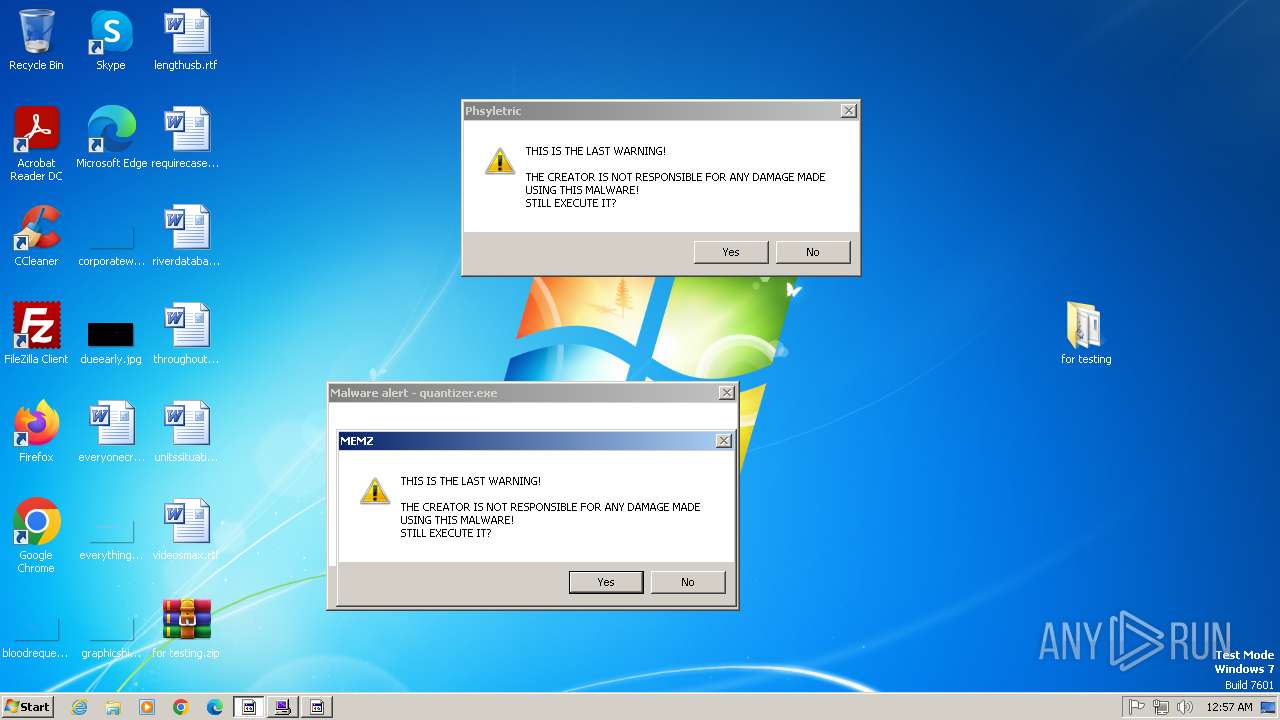
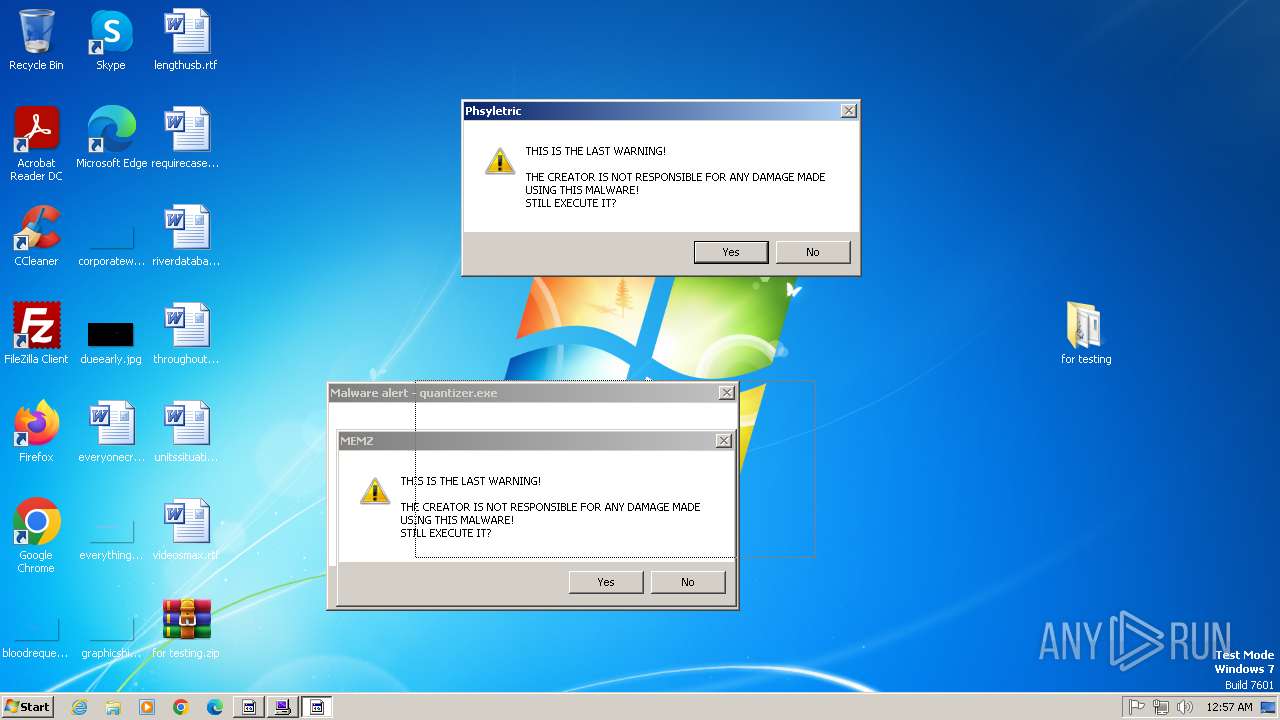
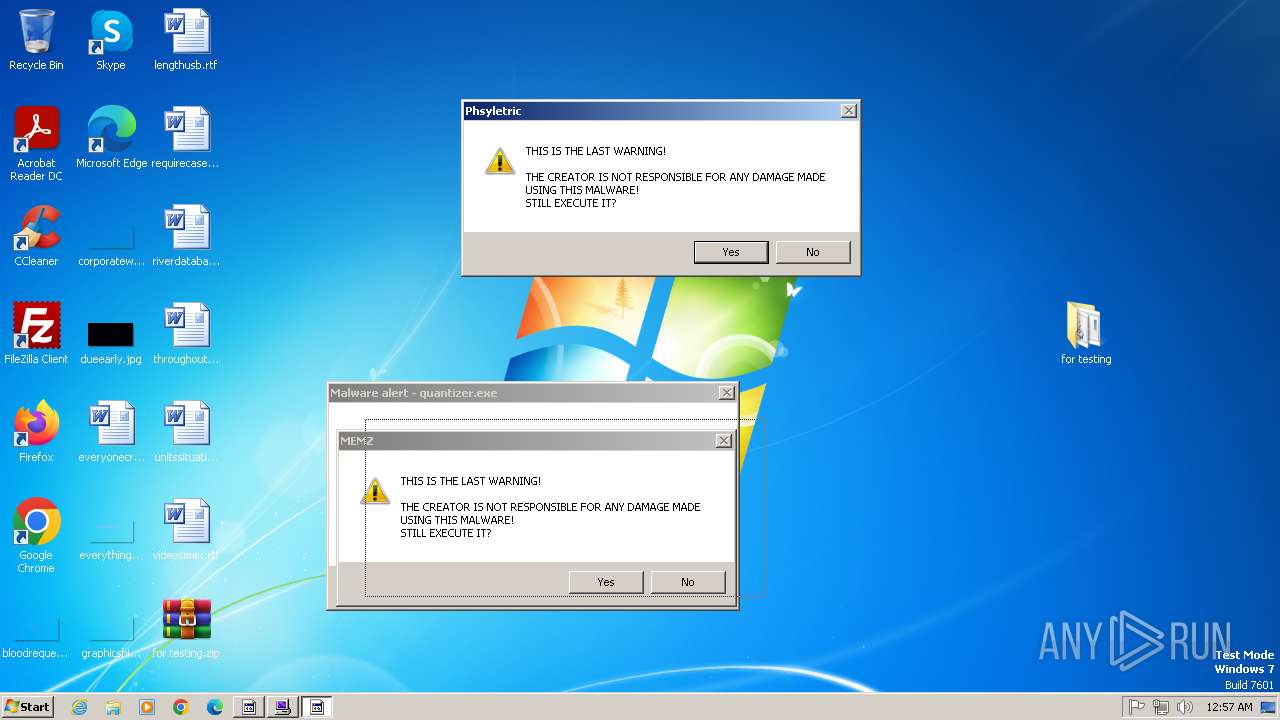
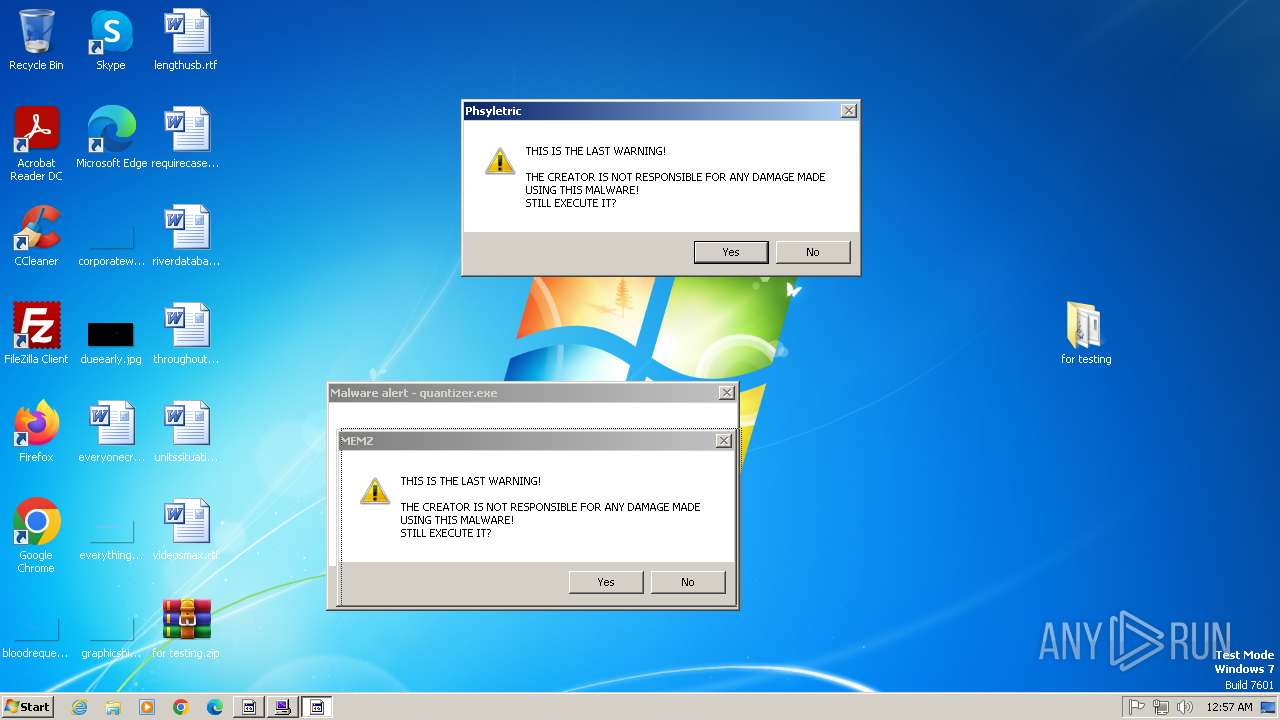
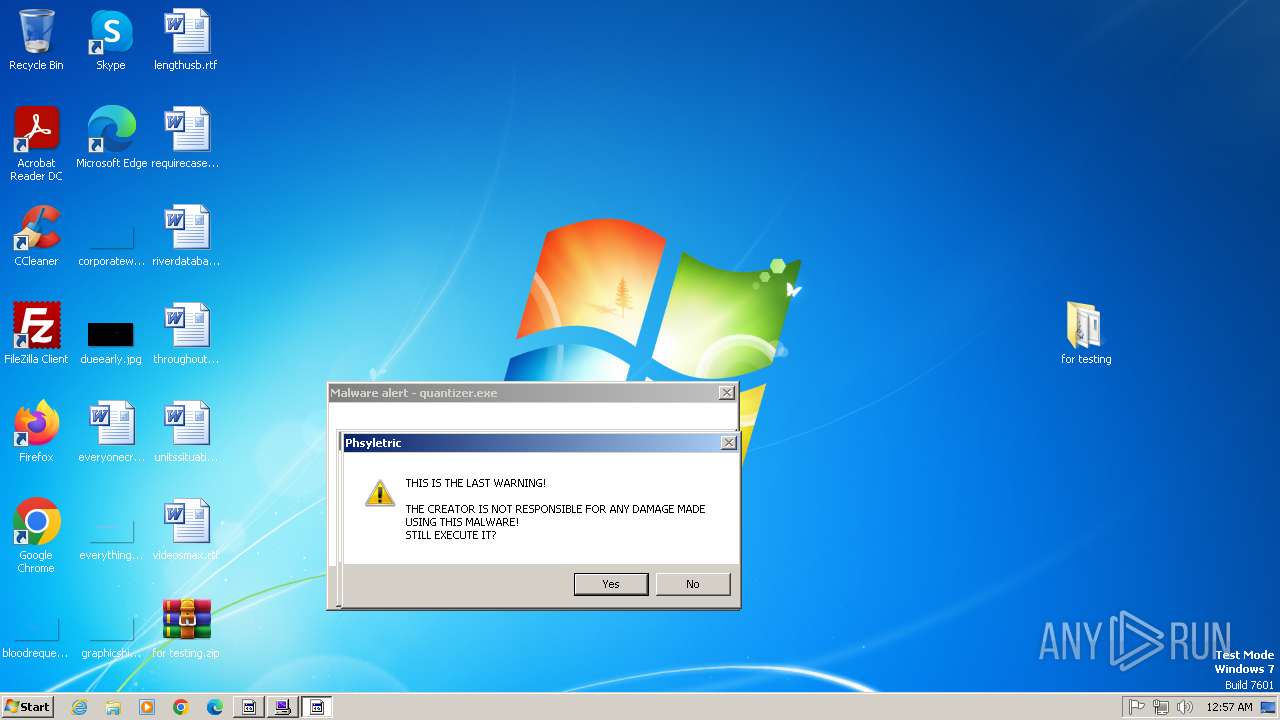
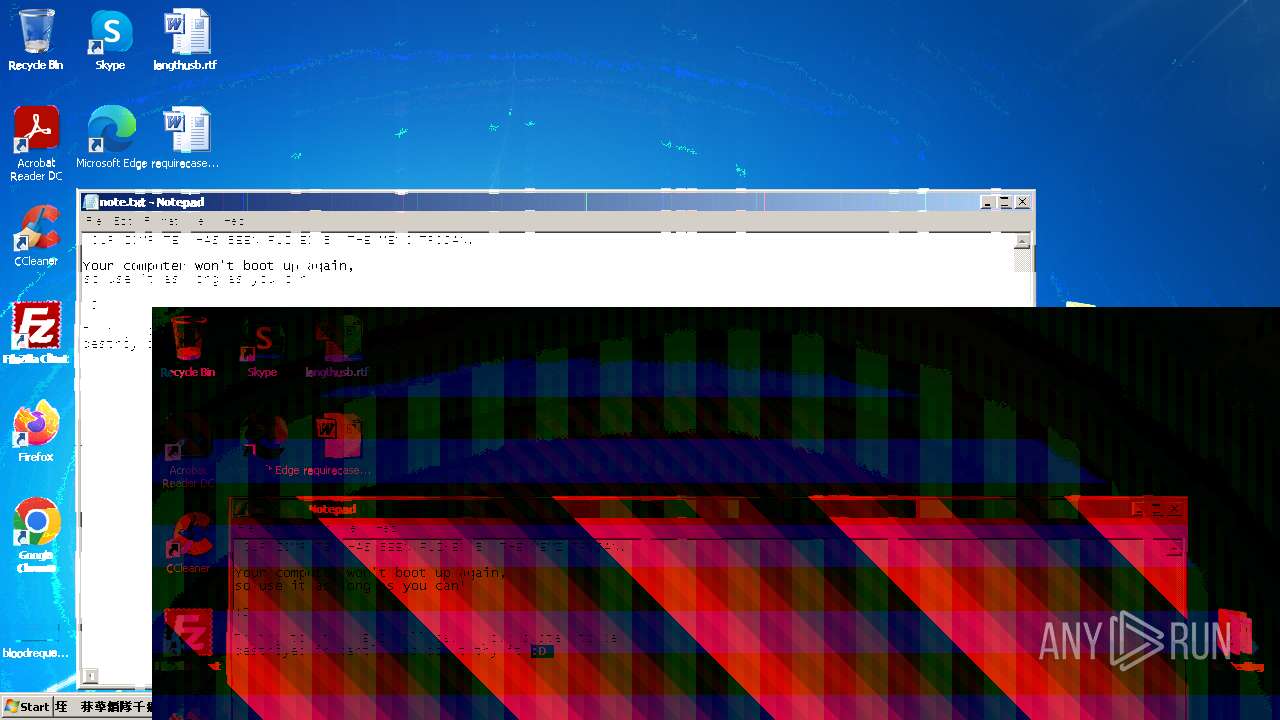
| File name: | for testing.zip |
| Full analysis: | https://app.any.run/tasks/9f12c6e7-2409-4b03-9e76-de71242542e9 |
| Verdict: | Malicious activity |
| Analysis date: | May 27, 2025, 23:56:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract, compression method=deflate |
| MD5: | 68EC8DD3E945B1506DC42AB2B5D59384 |
| SHA1: | FF1507B08F59C6E858C27BFC58C006CE313D6175 |
| SHA256: | BA49309462459D7957E469B7DED546BC939002B7F9D27BE3E45B157373DEF292 |
| SSDEEP: | 6144:7U1afzTKFQ4QmtMitJCzX/FcyQXVDG2EvMDMKZDi5iriWPB9tvb:7oafzT7TmtPe/NaDG2EvMDQMGWPNvb |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2448)
Gets a file object corresponding to the file in a specified path (SCRIPT)
- cscript.exe (PID: 1888)
Uses base64 encoding (SCRIPT)
- cscript.exe (PID: 1888)
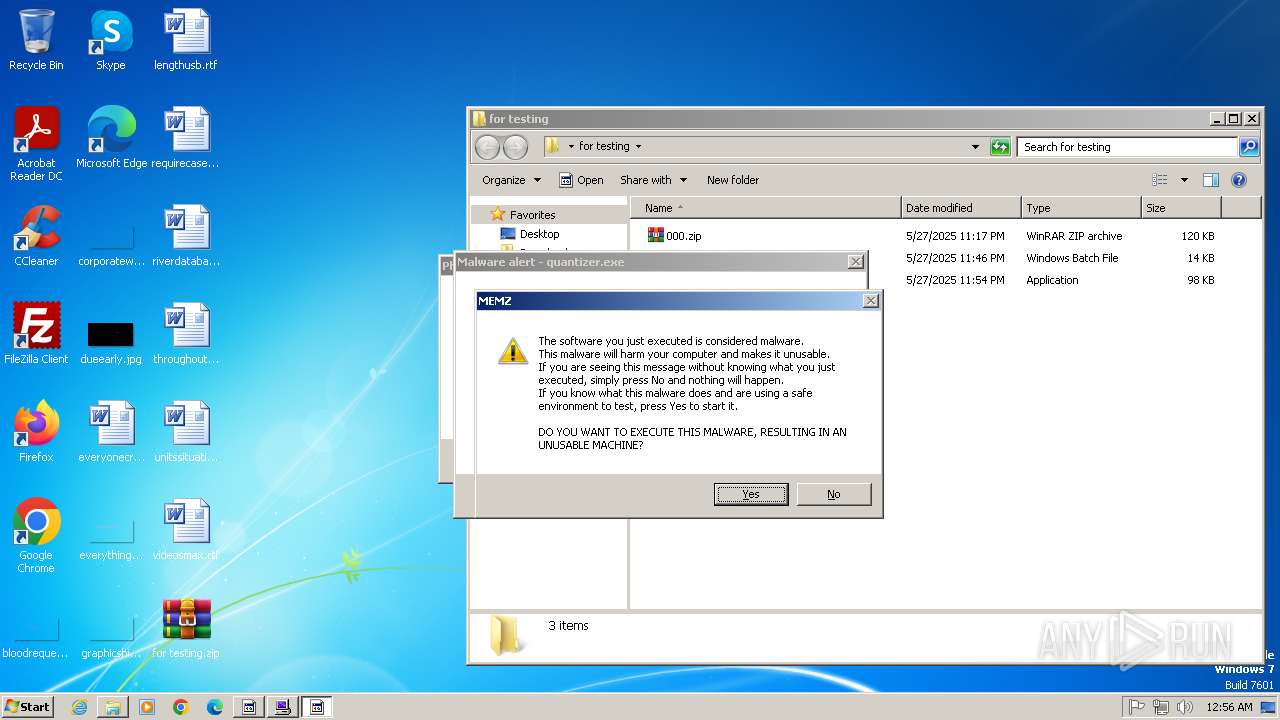
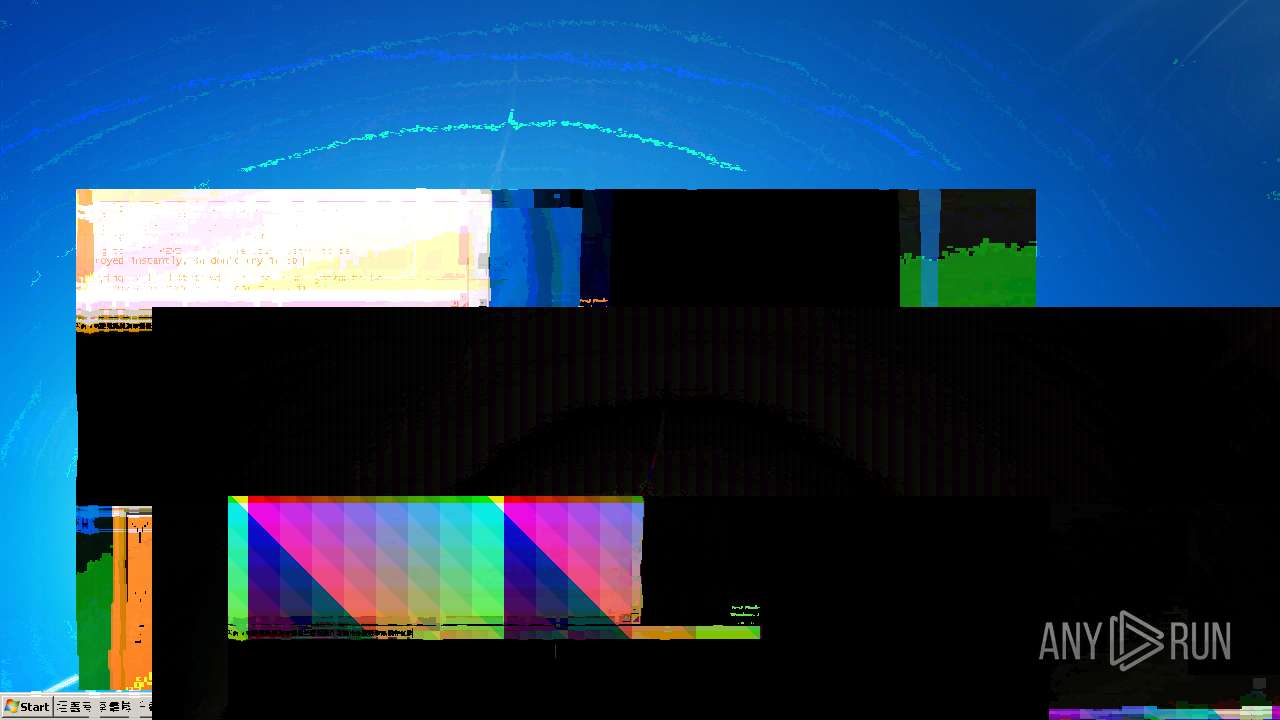
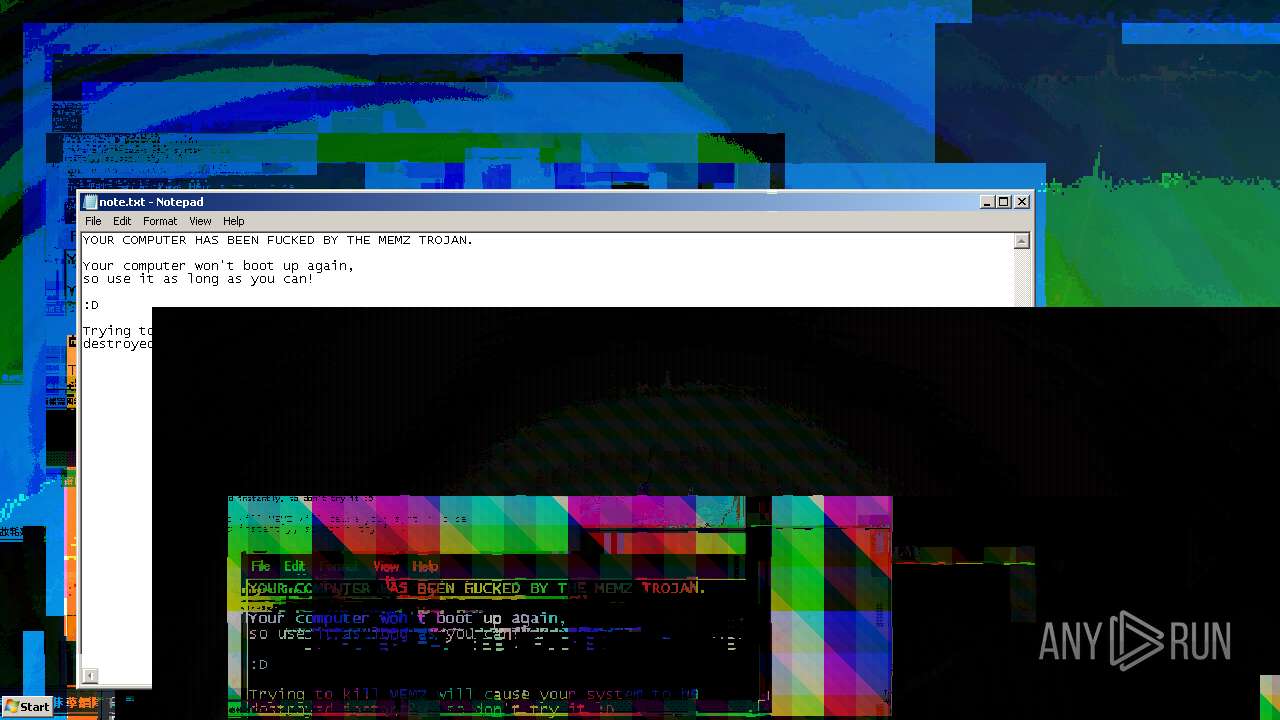
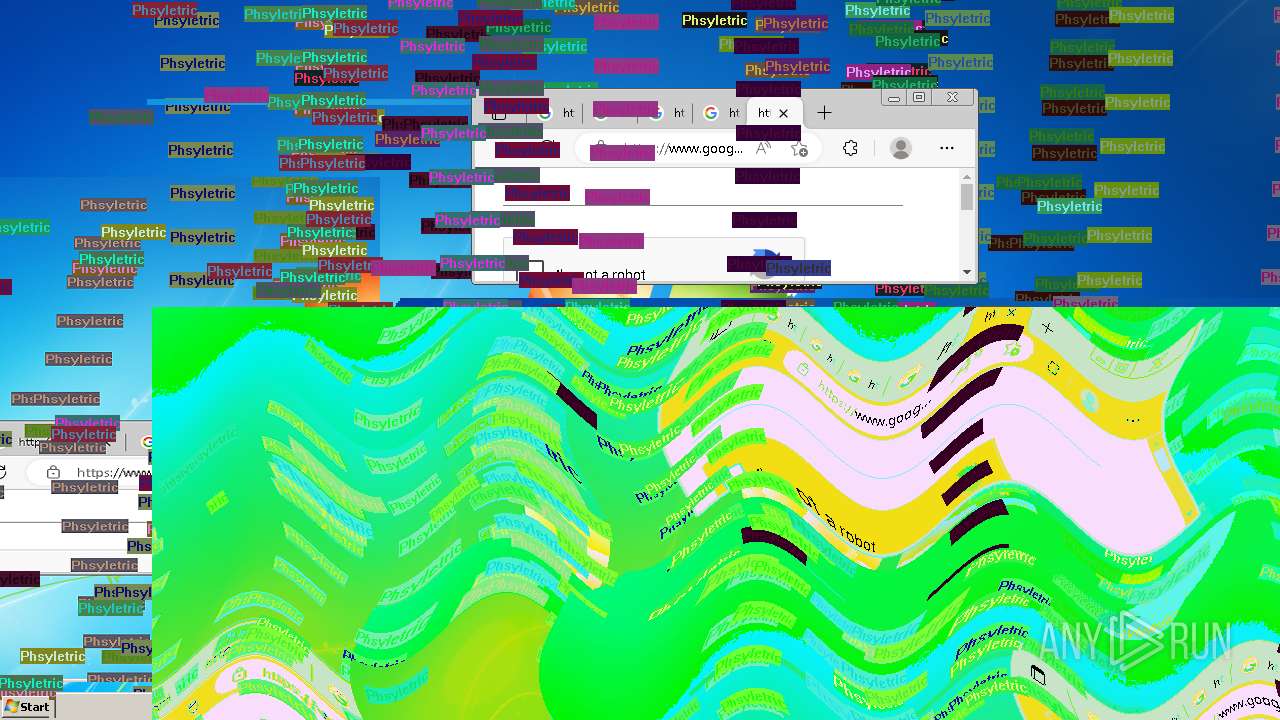
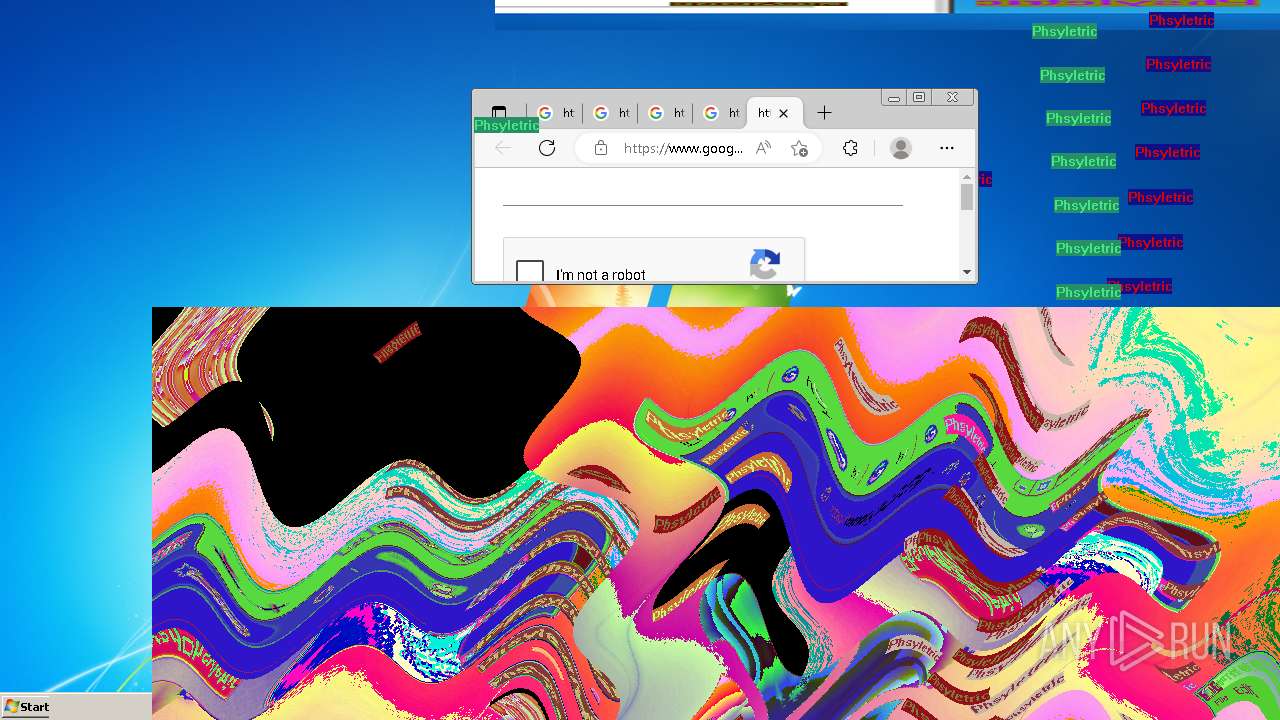
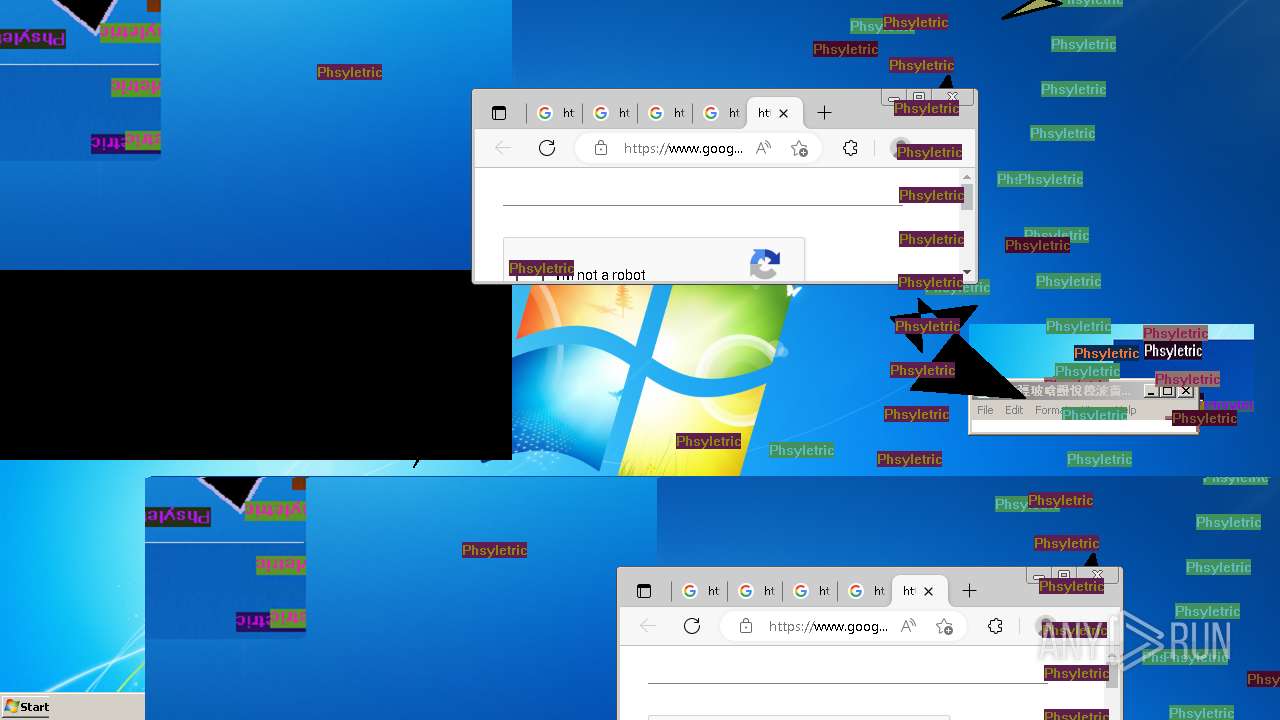
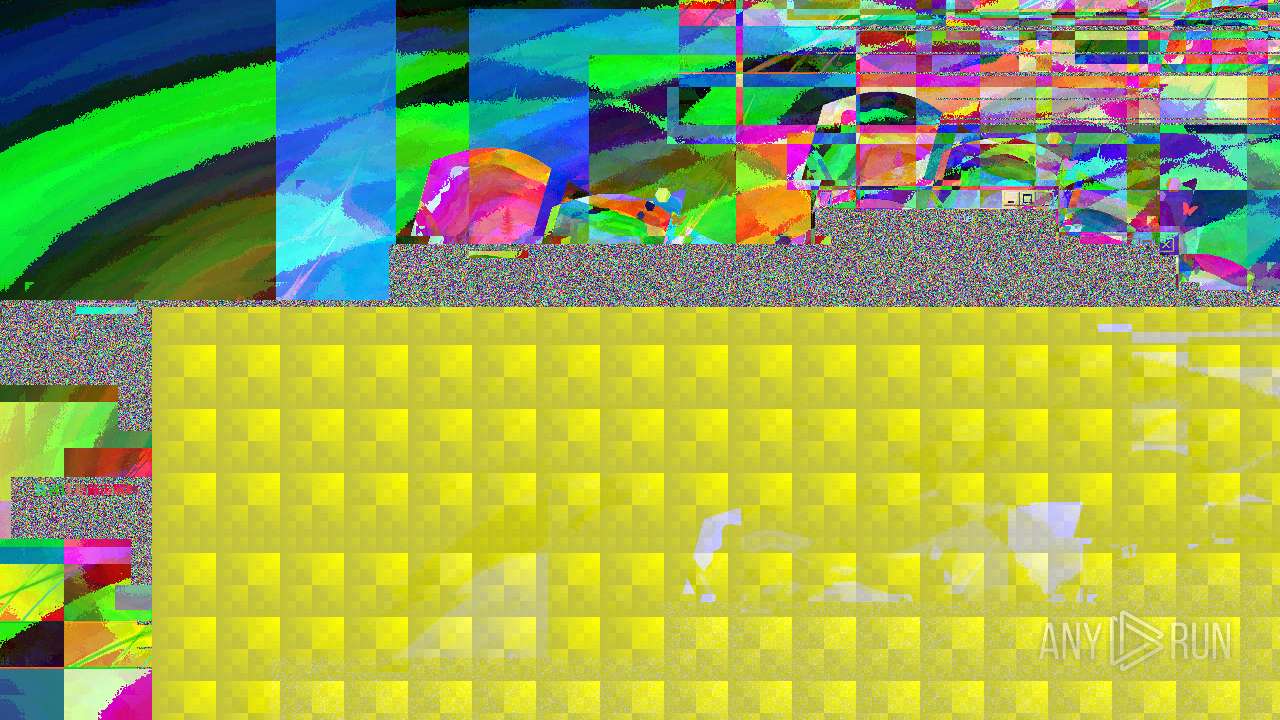
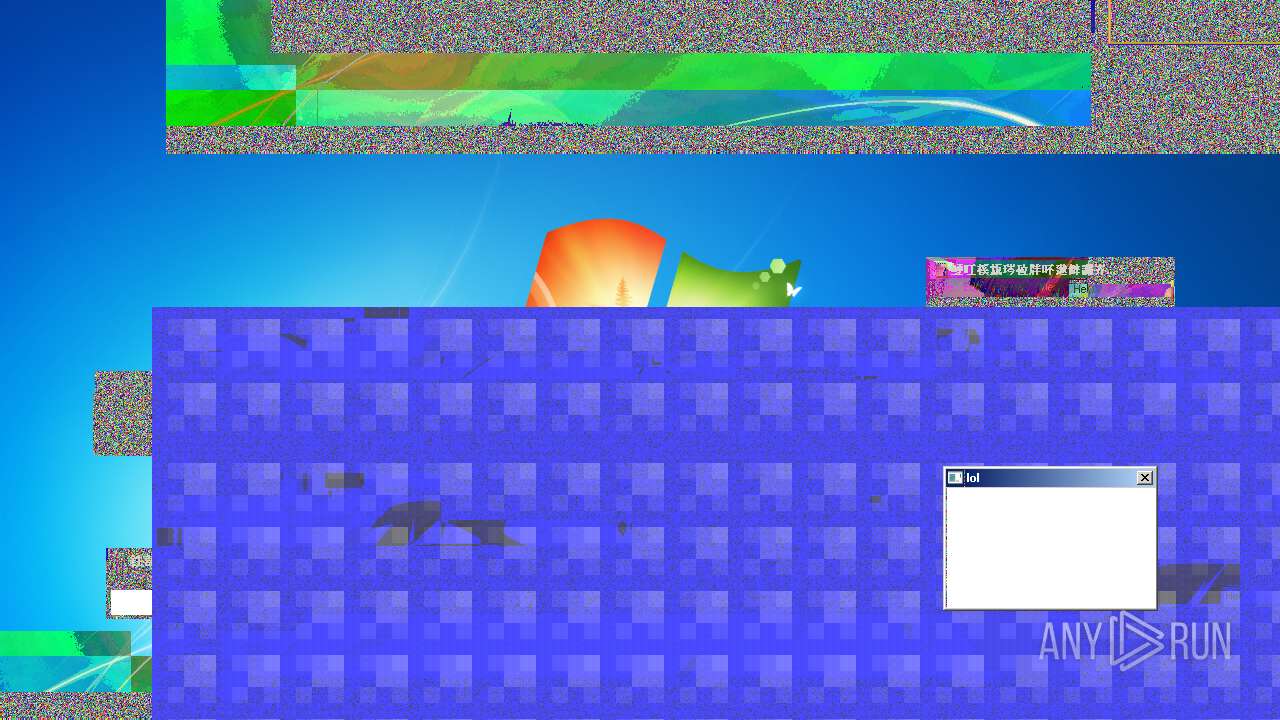
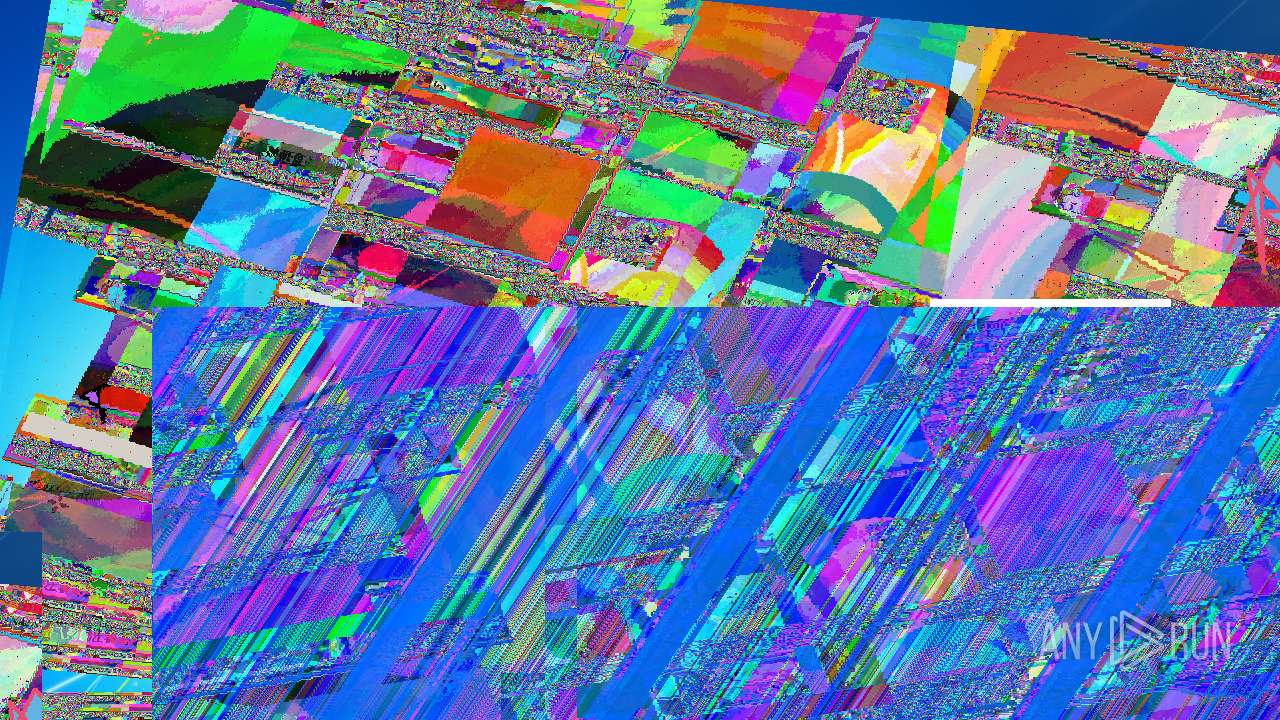
MEMZ has been detected (YARA)
- MEMZ.exe (PID: 2096)
- MEMZ.exe (PID: 3636)
- MEMZ.exe (PID: 3224)
- MEMZ.exe (PID: 3000)
- MEMZ.exe (PID: 3712)
- MEMZ.exe (PID: 3656)
- MEMZ.exe (PID: 3776)
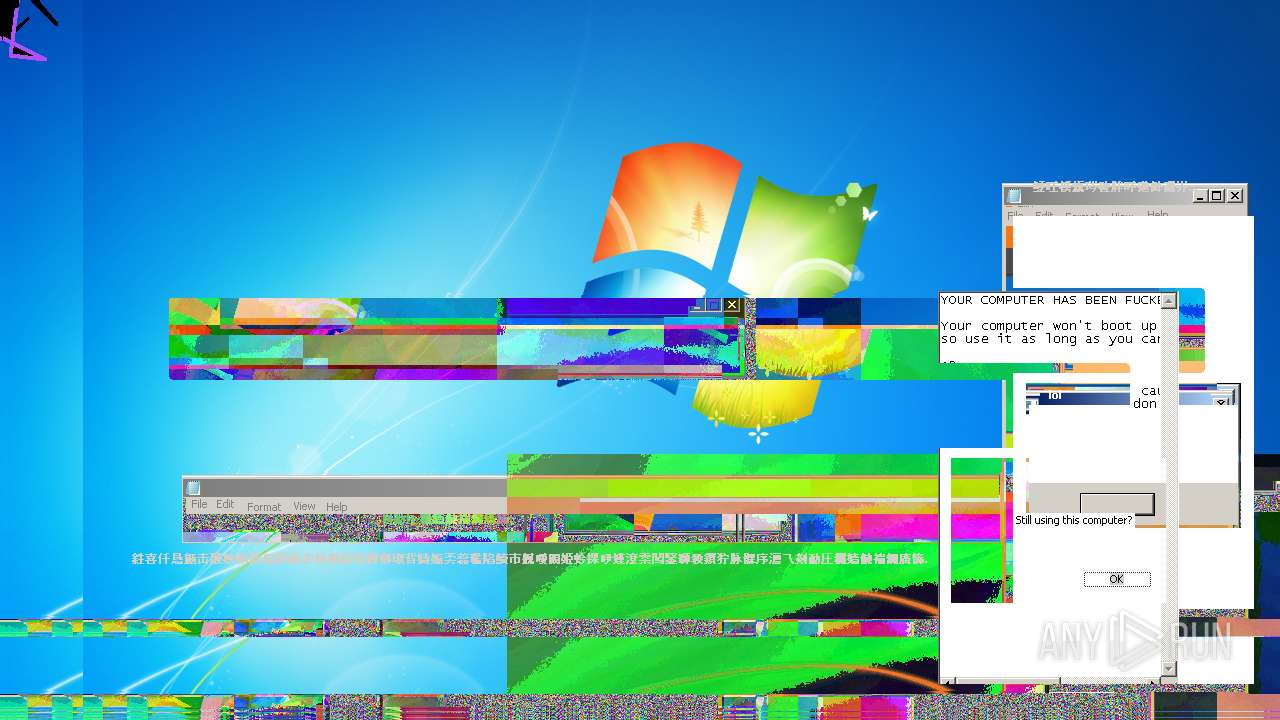
Disables task manager
- 一一一一一一一一一一一一一一一一.exe (PID: 3096)
SUSPICIOUS
The process executes JS scripts
- cmd.exe (PID: 1864)
Sets XML DOM element text (SCRIPT)
- cscript.exe (PID: 1888)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 1888)
Creates XML DOM element (SCRIPT)
- cscript.exe (PID: 1888)
Script creates XML DOM node (SCRIPT)
- cscript.exe (PID: 1888)
Saves data to a binary file (SCRIPT)
- cscript.exe (PID: 1888)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- cscript.exe (PID: 1888)
Writes binary data to a Stream object (SCRIPT)
- cscript.exe (PID: 1888)
Creates a Folder object (SCRIPT)
- cscript.exe (PID: 1888)
Executable content was dropped or overwritten
- cscript.exe (PID: 1888)
- quantizer.exe (PID: 1500)
Reads the Internet Settings
- cscript.exe (PID: 1888)
- cmd.exe (PID: 1864)
- MEMZ.exe (PID: 2096)
- MEMZ.exe (PID: 3656)
There is functionality for taking screenshot (YARA)
- Phsyletric.exe (PID: 2416)
- 一一一一一一一一一一一一一一一一.exe (PID: 3096)
- MEMZ.exe (PID: 2096)
- MEMZ.exe (PID: 3224)
- MEMZ.exe (PID: 3636)
- MEMZ.exe (PID: 3656)
- MEMZ.exe (PID: 3776)
- MEMZ.exe (PID: 3000)
- MEMZ.exe (PID: 3712)
Starts itself from another location
- quantizer.exe (PID: 1500)
Application launched itself
- MEMZ.exe (PID: 2096)
Creates file in the systems drive root
- MEMZ.exe (PID: 3656)
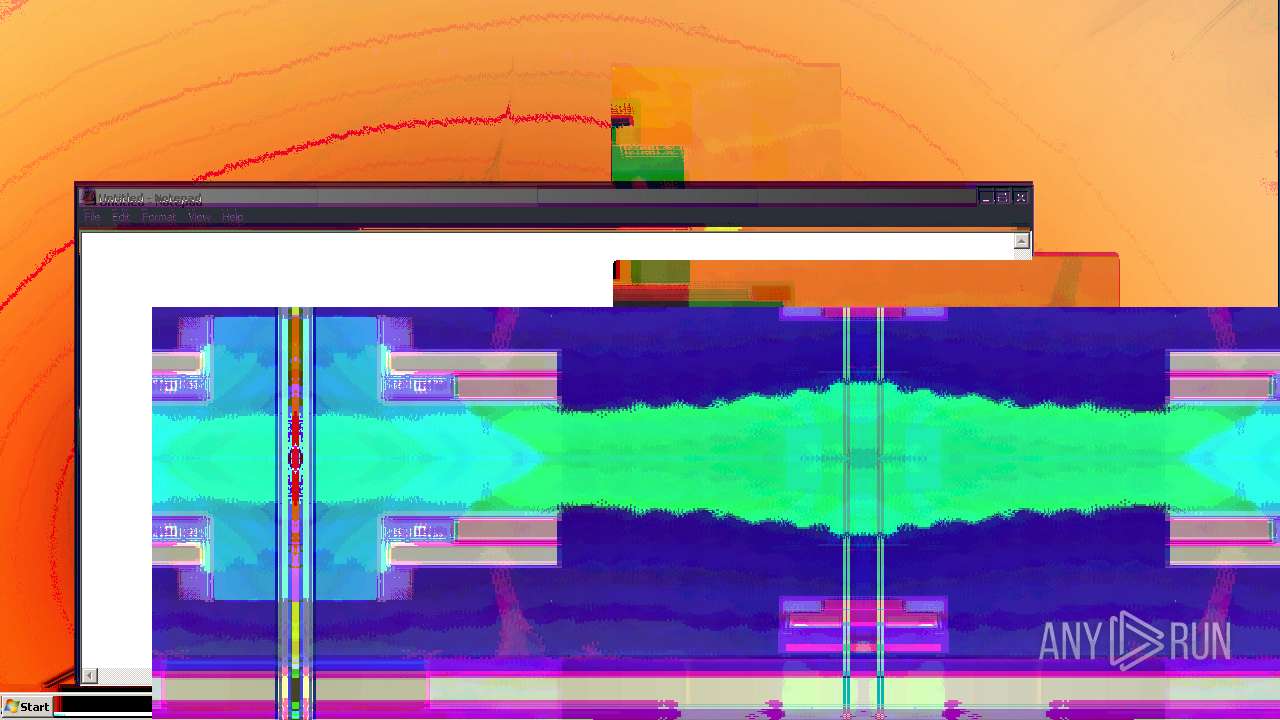
- notepad.exe (PID: 3136)
Reads security settings of Internet Explorer
- MEMZ.exe (PID: 3656)
- MEMZ.exe (PID: 2096)
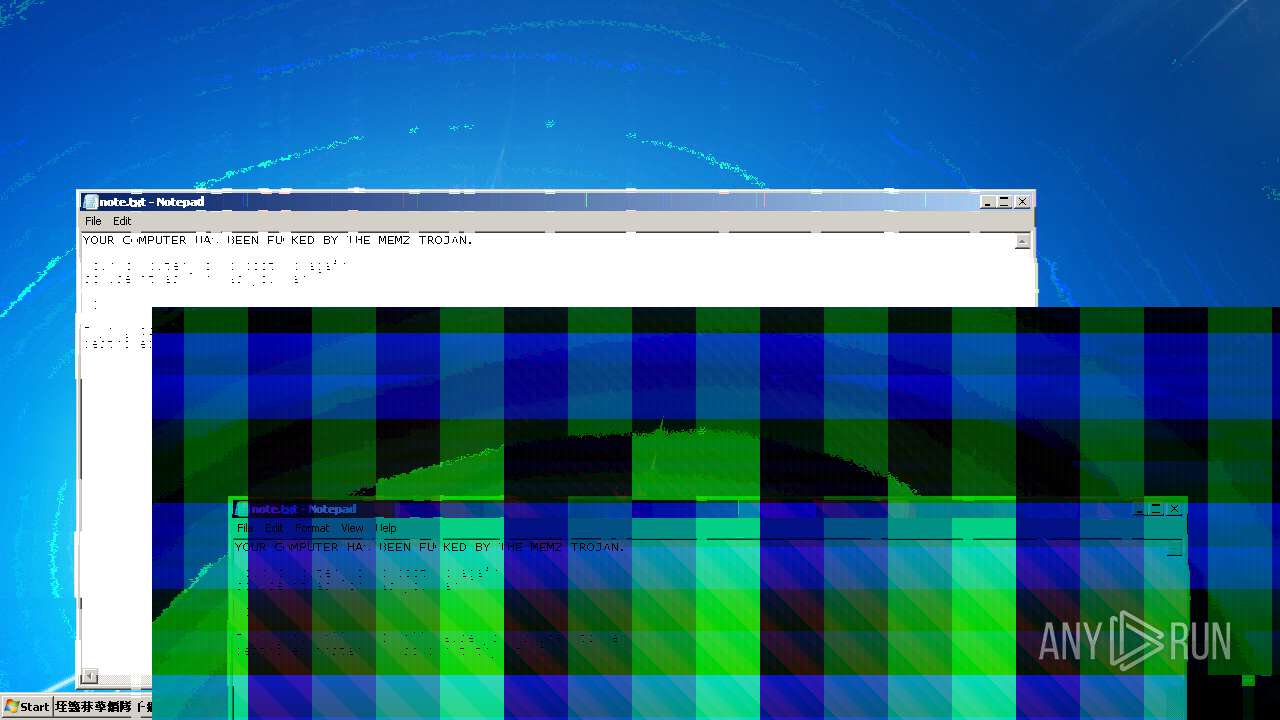
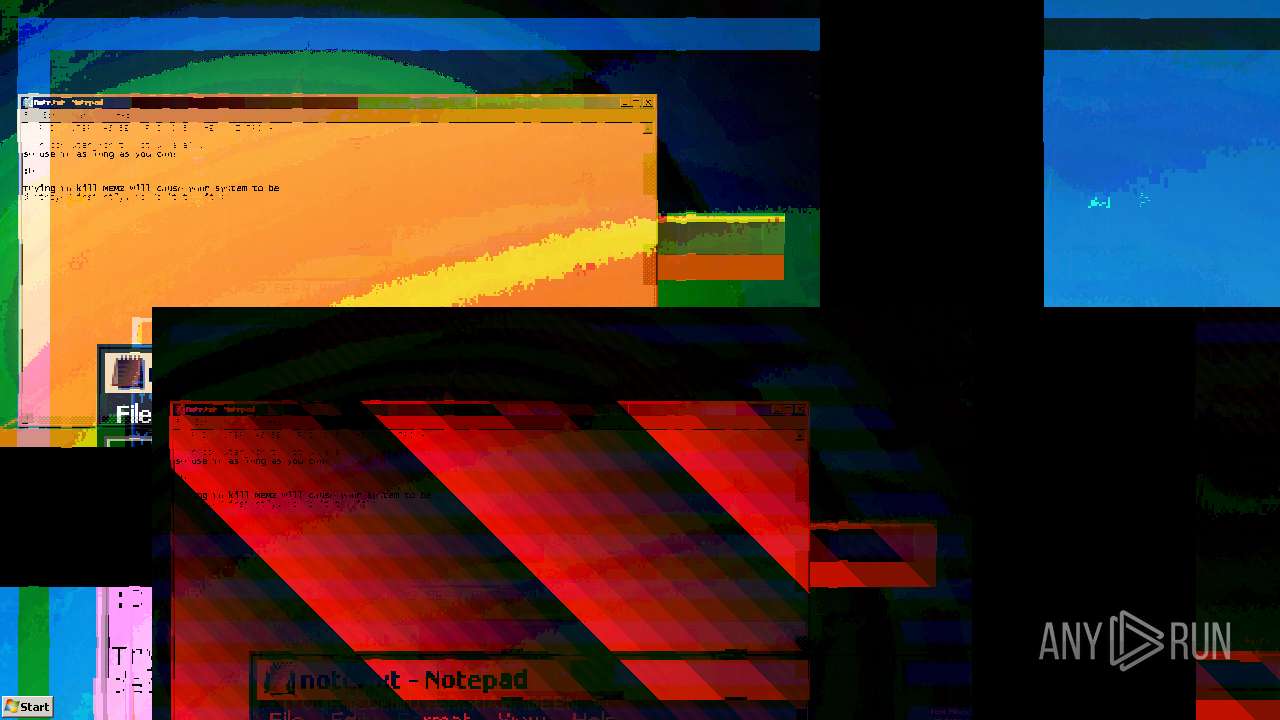
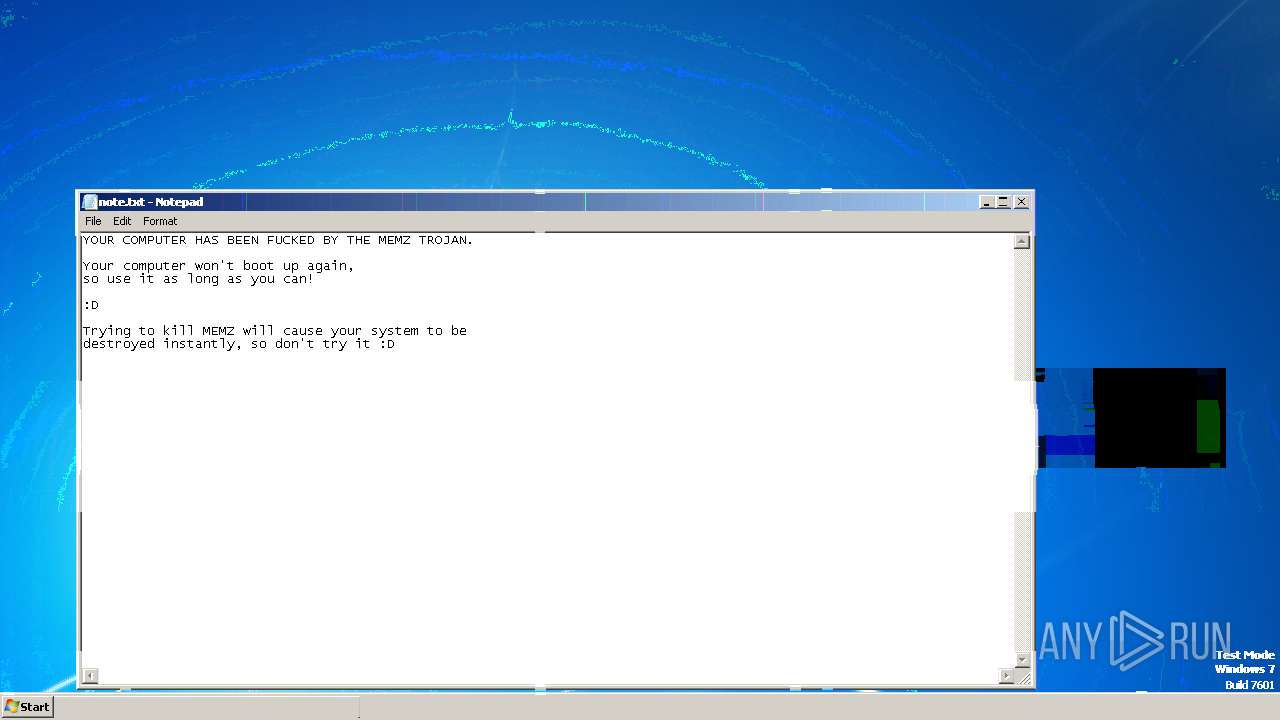
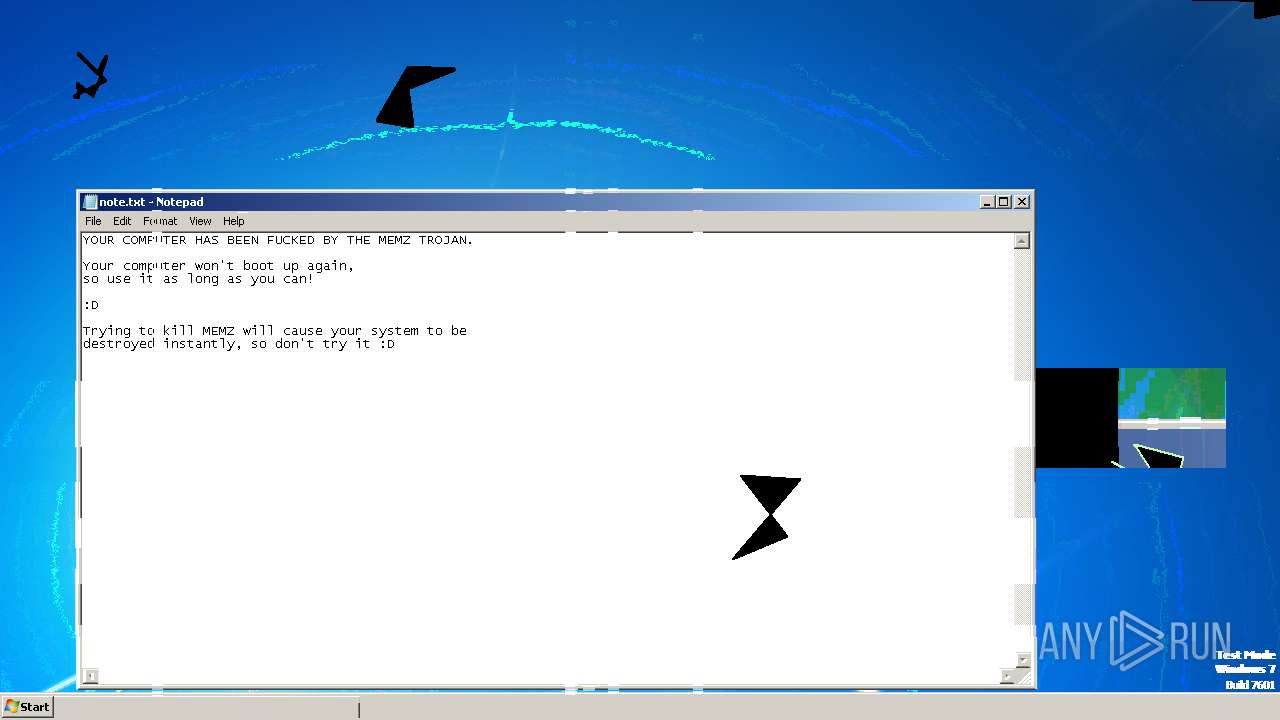
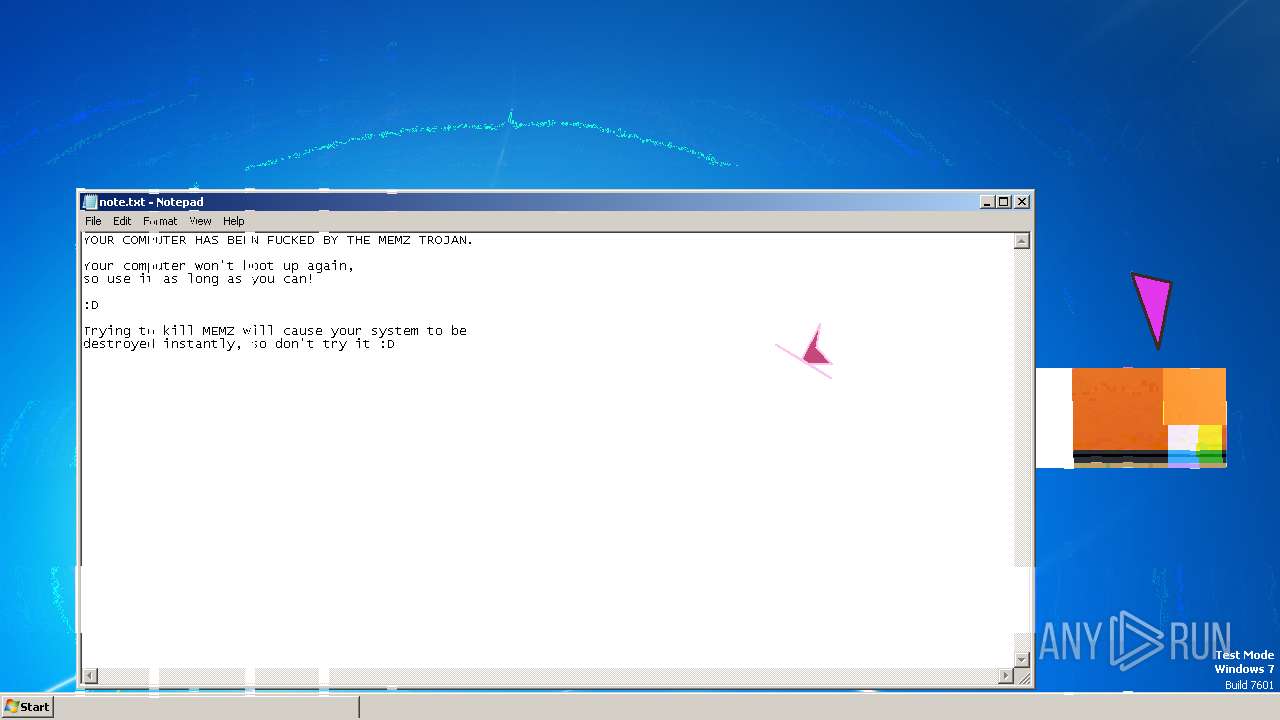
Start notepad (likely ransomware note)
- MEMZ.exe (PID: 3656)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2448)
Manual execution by a user
- cmd.exe (PID: 1864)
- Phsyletric.exe (PID: 1000)
- Phsyletric.exe (PID: 2416)
- quantizer.exe (PID: 1500)
- quantizer.exe (PID: 2384)
- msedge.exe (PID: 912)
Reads security settings of Internet Explorer
- cscript.exe (PID: 1888)
Creates files or folders in the user directory
- cscript.exe (PID: 1888)
Checks supported languages
- Phsyletric.exe (PID: 2416)
- quantizer.exe (PID: 1500)
- 一一一一一一一一一一一一一一一一.exe (PID: 3096)
- MEMZ.exe (PID: 2096)
- MEMZ.exe (PID: 3224)
- MEMZ.exe (PID: 3636)
- MEMZ.exe (PID: 3776)
- MEMZ.exe (PID: 3000)
- MEMZ.exe (PID: 3712)
- MEMZ.exe (PID: 3656)
Create files in a temporary directory
- quantizer.exe (PID: 1500)
Reads the computer name
- Phsyletric.exe (PID: 2416)
- MEMZ.exe (PID: 2096)
- 一一一一一一一一一一一一一一一一.exe (PID: 3096)
- MEMZ.exe (PID: 3656)
Reads the machine GUID from the registry
- MEMZ.exe (PID: 3656)
Application launched itself
- msedge.exe (PID: 3264)
- msedge.exe (PID: 2984)
- msedge.exe (PID: 912)
- msedge.exe (PID: 1768)
- msedge.exe (PID: 2328)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 45 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:27 23:54:38 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 2 |
| ZipUncompressedSize: | - |
| ZipFileName: | for testing/ |
Total processes
95
Monitored processes
54
Malicious processes
10
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 184 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=19 --mojo-platform-channel-handle=3932 --field-trial-handle=1360,i,3594101637935057206,18080221346021653775,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 320 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=3368 --field-trial-handle=1360,i,3594101637935057206,18080221346021653775,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 524 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=2452 --field-trial-handle=1360,i,3594101637935057206,18080221346021653775,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 656 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=2844 --field-trial-handle=1360,i,3594101637935057206,18080221346021653775,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 856 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=22 --mojo-platform-channel-handle=3880 --field-trial-handle=1360,i,3594101637935057206,18080221346021653775,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 912 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --flag-switches-begin --enable-features=msMicrosoftRootStoreUsed --flag-switches-end --do-not-de-elevate http://google.co.ck/search?q=how+to+send+a+virus+to+my+friend | C:\Program Files\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 944 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1292 --field-trial-handle=1360,i,3594101637935057206,18080221346021653775,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1000 | "C:\Users\admin\Desktop\for testing\Phsyletric.exe" | C:\Users\admin\Desktop\for testing\Phsyletric.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1156 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=13 --mojo-platform-channel-handle=4352 --field-trial-handle=1360,i,3594101637935057206,18080221346021653775,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1396 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=18 --mojo-platform-channel-handle=3440 --field-trial-handle=1360,i,3594101637935057206,18080221346021653775,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
11 923
Read events
11 720
Write events
196
Delete events
7
Modification events
| (PID) Process: | (2448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2448) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\for testing.zip | |||
| (PID) Process: | (2448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
4
Suspicious files
83
Text files
28
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2416 | Phsyletric.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 3656 | MEMZ.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 4068 | msedge.exe | — | ||
MD5:— | SHA256:— | |||
| 1864 | cmd.exe | C:\Users\admin\Desktop\for testing\x | text | |
MD5:CFC1E7E18B9F9B70310C88F922E59B29 | SHA256:3DCF309E134AE67CAED27FA52782267C90646B405C4A9594041B284733B8E346 | |||
| 3264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 2448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2448.913\for testing\000.zip | compressed | |
MD5:D113BD83E59586DD8F1843BDB9B98EE0 | SHA256:9D3FE04D88C401178165F7FBDF307AC0FB690CC5FEF8B70EE7F380307D4748F8 | |||
| 912 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF194740.TMP | — | |
MD5:— | SHA256:— | |||
| 912 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1864 | cmd.exe | C:\Users\admin\Desktop\for testing\x.js | text | |
MD5:D94C93F882CF030ED9D66CC35796731D | SHA256:F7941E6BE49D757B46B9D6FB5ECB15392EC36A64E8906692D2EEB2BA9FC67CB6 | |||
| 2448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2448.913\for testing\MEMZ-Destructive.bat | text | |
MD5:508CCEBEBAEFB2FB833BF8E7FEBFA209 | SHA256:17B1F1E3F6235008152F64BA8B8B4AF4ABBBEB0150DB3EF32EABF04EE3BDC5F4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
43
DNS requests
35
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3680 | msedge.exe | GET | 302 | 172.217.16.196:80 | http://google.co.ck/search?q=how+to+send+a+virus+to+my+friend | unknown | — | — | whitelisted |
3680 | msedge.exe | GET | 302 | 172.217.16.196:80 | http://google.co.ck/search?q=my+computer+is+doing+weird+things+wtf+is+happenin+plz+halp | unknown | — | — | whitelisted |
3680 | msedge.exe | GET | 302 | 172.217.16.196:80 | http://google.co.ck/search?q=the+memz+are+real | unknown | — | — | whitelisted |
3680 | msedge.exe | GET | 302 | 172.217.16.196:80 | http://google.co.ck/search?q=my+computer+is+doing+weird+things+wtf+is+happenin+plz+halp | unknown | — | — | whitelisted |
— | — | GET | 302 | 172.217.16.196:80 | http://google.co.ck/search?q=how+2+remove+a+virus | unknown | — | — | whitelisted |
3680 | msedge.exe | GET | 302 | 172.217.16.196:80 | http://google.co.ck/search?q=dank+memz | unknown | — | — | whitelisted |
— | — | GET | 302 | 172.217.16.196:80 | http://google.co.ck/search?q=how+to+remove+memz+trojan+virus | unknown | — | — | whitelisted |
— | — | GET | 302 | 172.217.16.196:80 | http://google.co.ck/search?q=how+to+create+your+own+ransomware | unknown | — | — | whitelisted |
— | — | GET | 302 | 172.217.16.196:80 | http://google.co.ck/search?q=facebook+hacking+tool+free+download+no+virus+working+2016 | unknown | — | — | whitelisted |
— | — | GET | 302 | 172.217.16.196:80 | http://google.co.ck/search?q=the+memz+are+real | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3680 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3680 | msedge.exe | 172.217.16.196:80 | google.co.ck | GOOGLE | US | whitelisted |
912 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3680 | msedge.exe | 216.58.206.36:443 | www.google.com | GOOGLE | US | whitelisted |
3680 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3680 | msedge.exe | 2.16.204.141:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
google.co.ck |
| whitelisted |
www.google.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
msedge.exe | [0528/005840.950:ERROR:exception_handler_server.cc(527)] ConnectNamedPipe: The pipe is being closed. (0xE8)
|
msedge.exe | [0528/005857.037:ERROR:exception_handler_server.cc(527)] ConnectNamedPipe: The pipe is being closed. (0xE8)
|
msedge.exe | [0528/005912.291:ERROR:exception_handler_server.cc(527)] ConnectNamedPipe: The pipe is being closed. (0xE8)
|