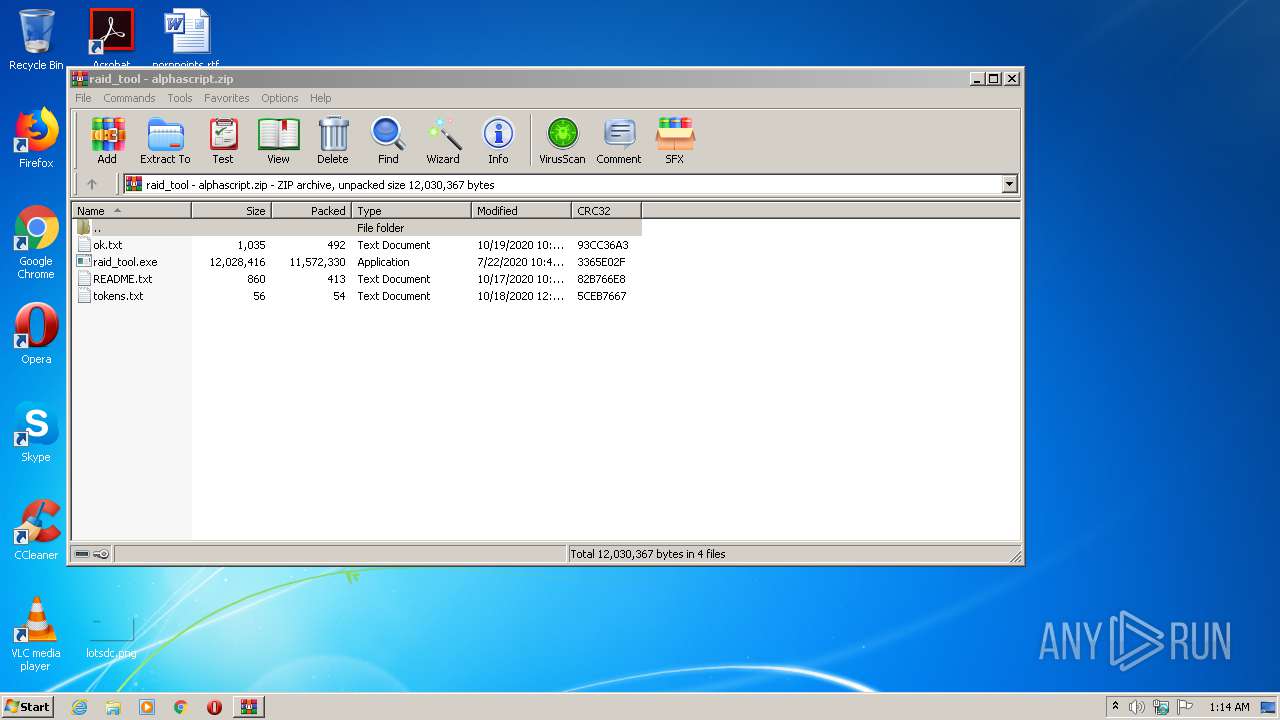
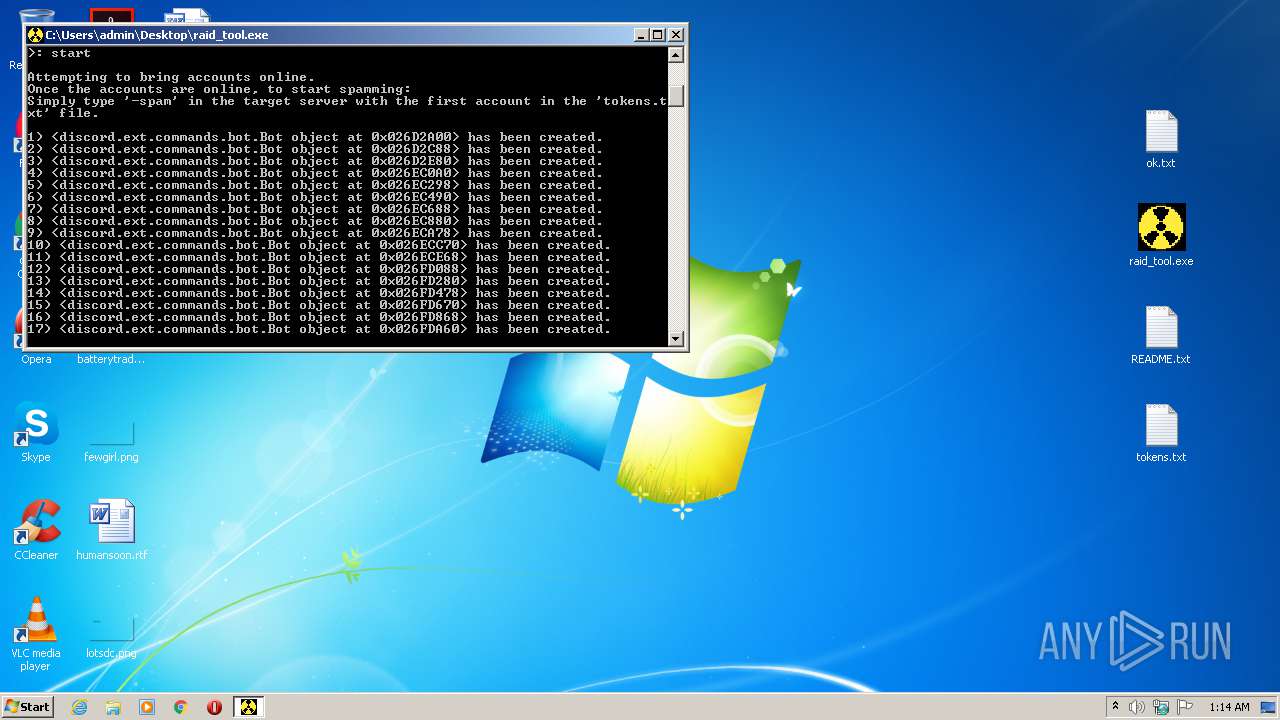
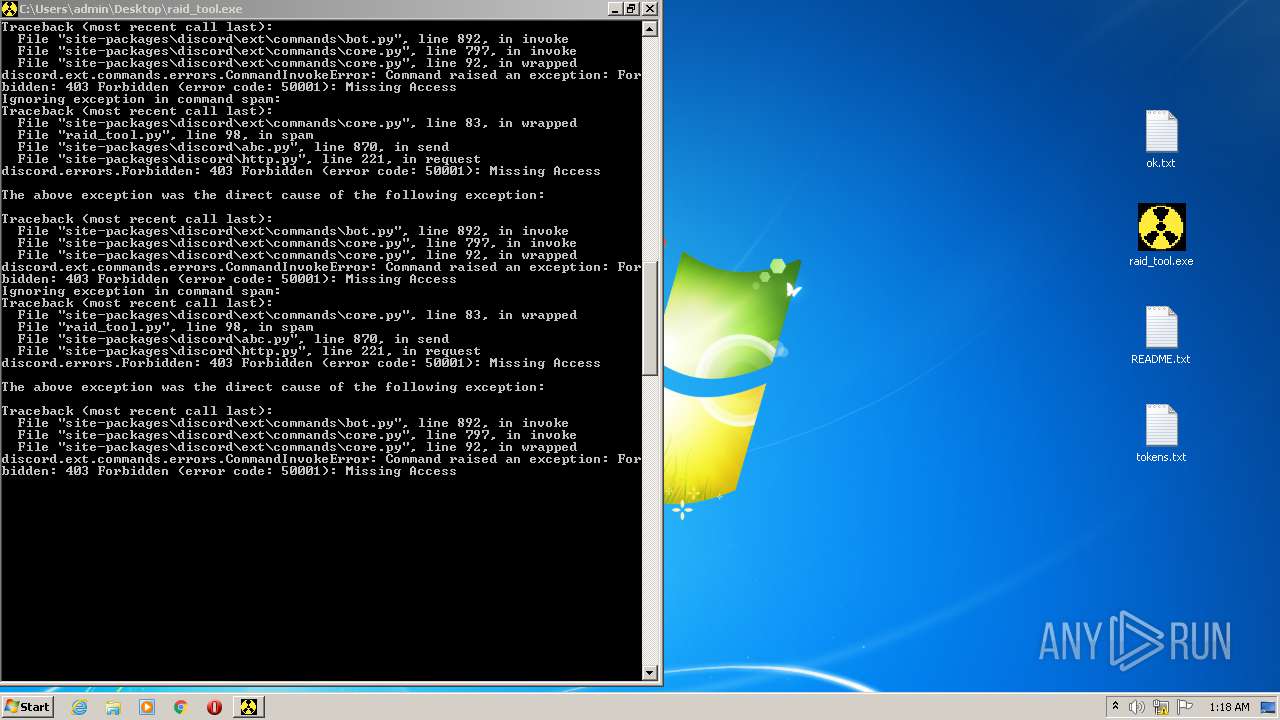
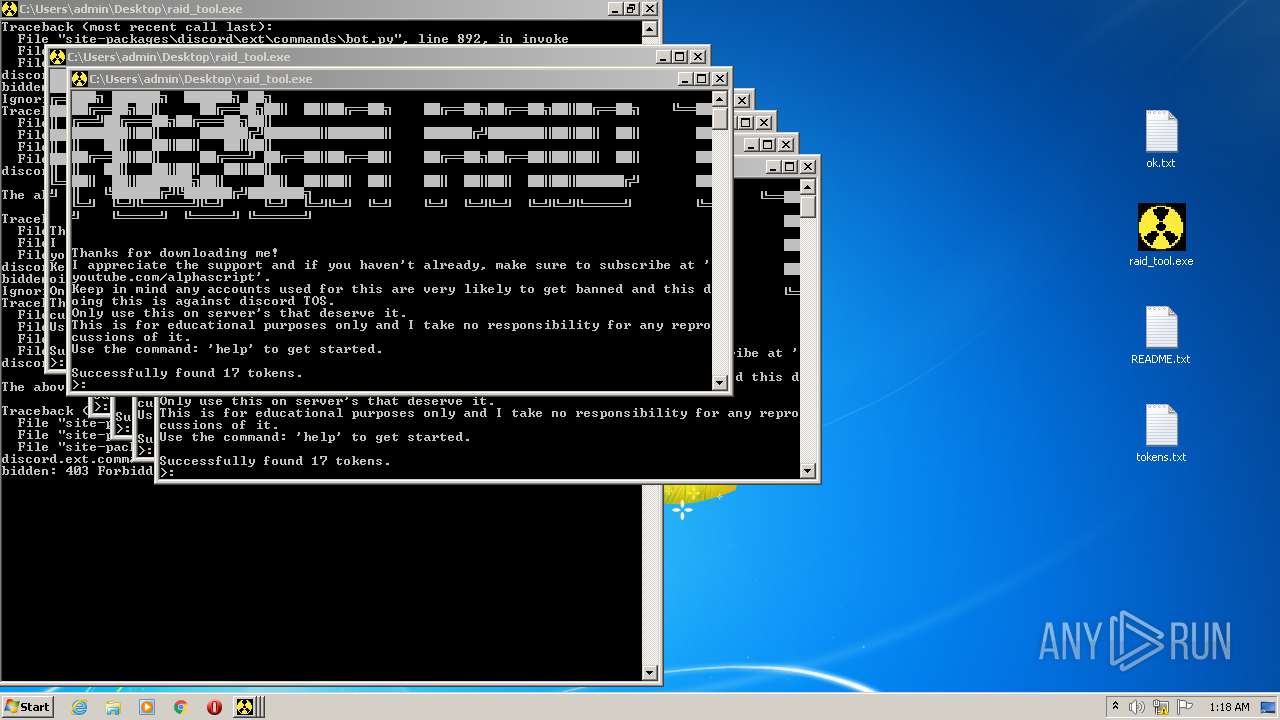
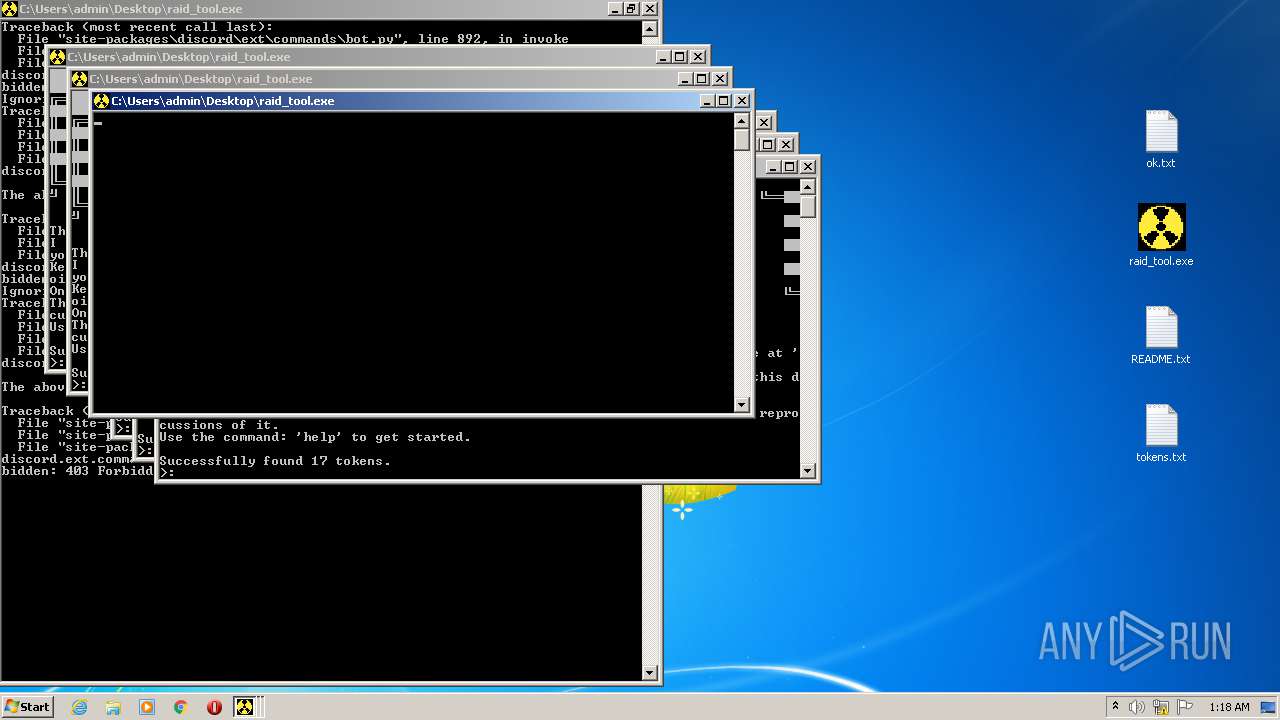
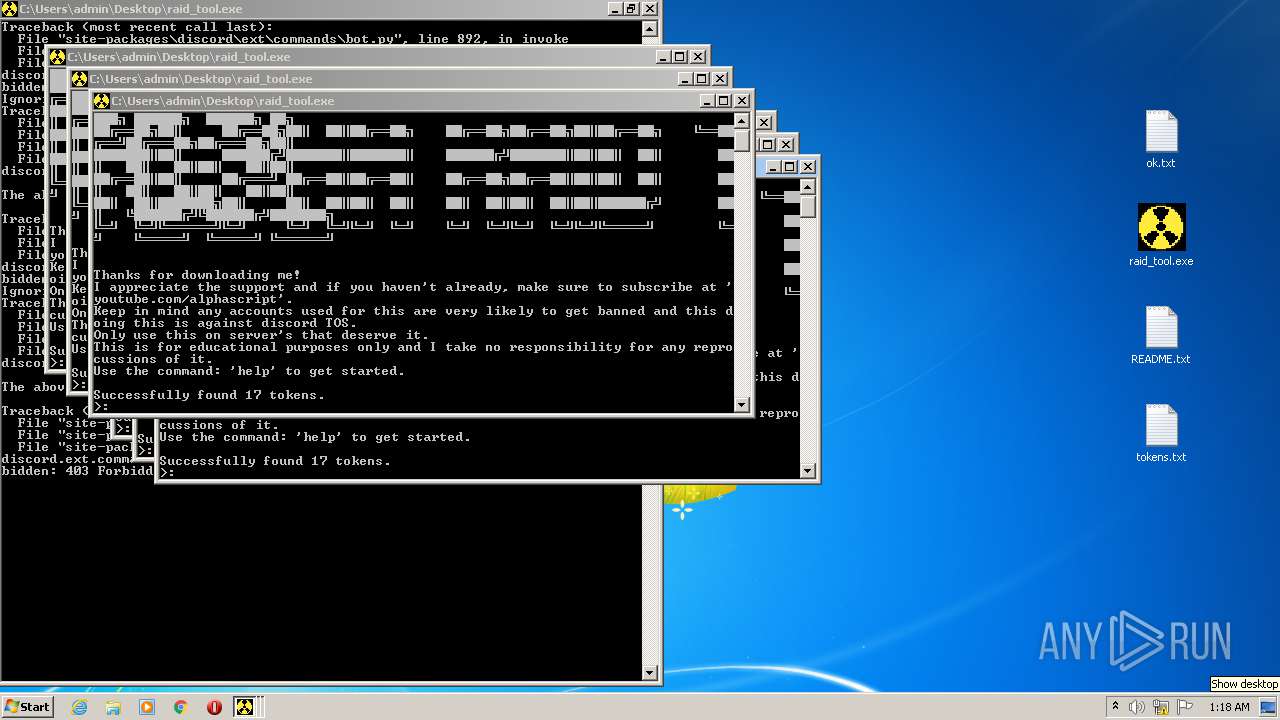
| File name: | raid_tool - alphascript.zip |
| Full analysis: | https://app.any.run/tasks/72d61d65-95ea-4b32-9f70-2fc92928b4de |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2020, 00:13:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 3E061CDB0DEA5EE253DBBDBAB76F4423 |
| SHA1: | 3871E331356B869F1F1ADD16F02B977EA97D9CB1 |
| SHA256: | BA4563BF28A50601E88C1F412D359B94F407E8A49E23CEB651D81445E9C56320 |
| SSDEEP: | 196608:egzE5VUziCh92ESzIYsbO1m8v26jrkNDRHcthJZ409aXKNdSF88C0YwAfcjrZIVS:dz/0nzIfi1m8u6QHcthbtE2V0Y9kxjGY |
MALICIOUS
Application was dropped or rewritten from another process
- raid_tool.exe (PID: 2824)
- raid_tool.exe (PID: 3000)
- raid_tool.exe (PID: 3544)
- raid_tool.exe (PID: 2580)
- raid_tool.exe (PID: 2240)
- raid_tool.exe (PID: 3256)
- raid_tool.exe (PID: 1272)
- raid_tool.exe (PID: 1820)
- raid_tool.exe (PID: 2524)
- raid_tool.exe (PID: 952)
- raid_tool.exe (PID: 3768)
- raid_tool.exe (PID: 2388)
- raid_tool.exe (PID: 3208)
- raid_tool.exe (PID: 3212)
- raid_tool.exe (PID: 3100)
- raid_tool.exe (PID: 1928)
- raid_tool.exe (PID: 1704)
- raid_tool.exe (PID: 2760)
- raid_tool.exe (PID: 2844)
- raid_tool.exe (PID: 2180)
- raid_tool.exe (PID: 2352)
- raid_tool.exe (PID: 4064)
Loads dropped or rewritten executable
- raid_tool.exe (PID: 2824)
- raid_tool.exe (PID: 3208)
- raid_tool.exe (PID: 3212)
- raid_tool.exe (PID: 3100)
- raid_tool.exe (PID: 1704)
- raid_tool.exe (PID: 2844)
- raid_tool.exe (PID: 2760)
- raid_tool.exe (PID: 2352)
- raid_tool.exe (PID: 1928)
- raid_tool.exe (PID: 2180)
SUSPICIOUS
Application launched itself
- raid_tool.exe (PID: 3000)
- raid_tool.exe (PID: 3544)
- raid_tool.exe (PID: 1272)
- raid_tool.exe (PID: 2580)
- raid_tool.exe (PID: 3256)
- raid_tool.exe (PID: 3768)
- raid_tool.exe (PID: 2524)
- raid_tool.exe (PID: 2240)
- raid_tool.exe (PID: 4064)
- raid_tool.exe (PID: 952)
Executable content was dropped or overwritten
- raid_tool.exe (PID: 3000)
- raid_tool.exe (PID: 1272)
- raid_tool.exe (PID: 2580)
- raid_tool.exe (PID: 3544)
- raid_tool.exe (PID: 3256)
- raid_tool.exe (PID: 3768)
- raid_tool.exe (PID: 1820)
- raid_tool.exe (PID: 2240)
- raid_tool.exe (PID: 2388)
- raid_tool.exe (PID: 952)
- raid_tool.exe (PID: 2524)
- raid_tool.exe (PID: 4064)
Loads Python modules
- raid_tool.exe (PID: 2824)
- raid_tool.exe (PID: 3212)
- raid_tool.exe (PID: 3208)
- raid_tool.exe (PID: 3100)
- raid_tool.exe (PID: 1928)
- raid_tool.exe (PID: 2844)
- raid_tool.exe (PID: 1704)
- raid_tool.exe (PID: 2760)
- raid_tool.exe (PID: 2352)
- raid_tool.exe (PID: 2180)
INFO
Manual execution by user
- NOTEPAD.EXE (PID: 3672)
- NOTEPAD.EXE (PID: 3736)
- raid_tool.exe (PID: 3000)
- raid_tool.exe (PID: 1272)
- raid_tool.exe (PID: 2580)
- raid_tool.exe (PID: 2240)
- raid_tool.exe (PID: 3544)
- raid_tool.exe (PID: 3256)
- raid_tool.exe (PID: 1820)
- raid_tool.exe (PID: 952)
- raid_tool.exe (PID: 2524)
- raid_tool.exe (PID: 3768)
- raid_tool.exe (PID: 2388)
- raid_tool.exe (PID: 4064)
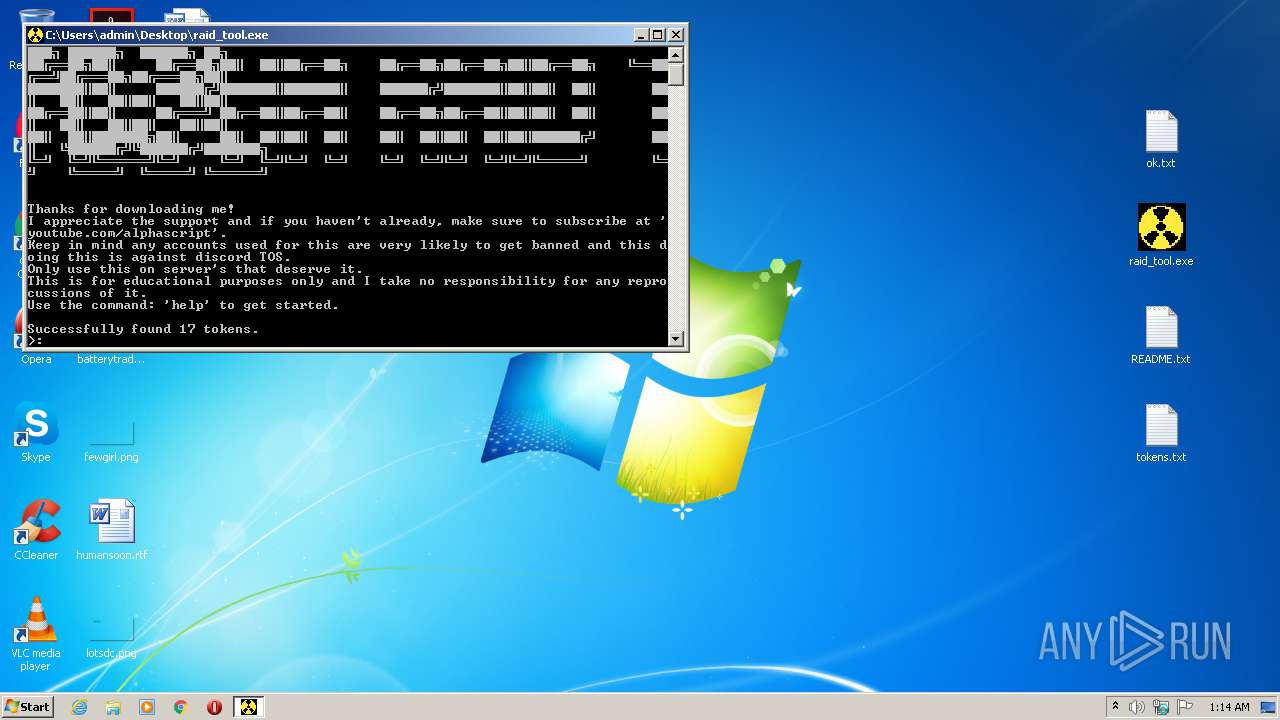
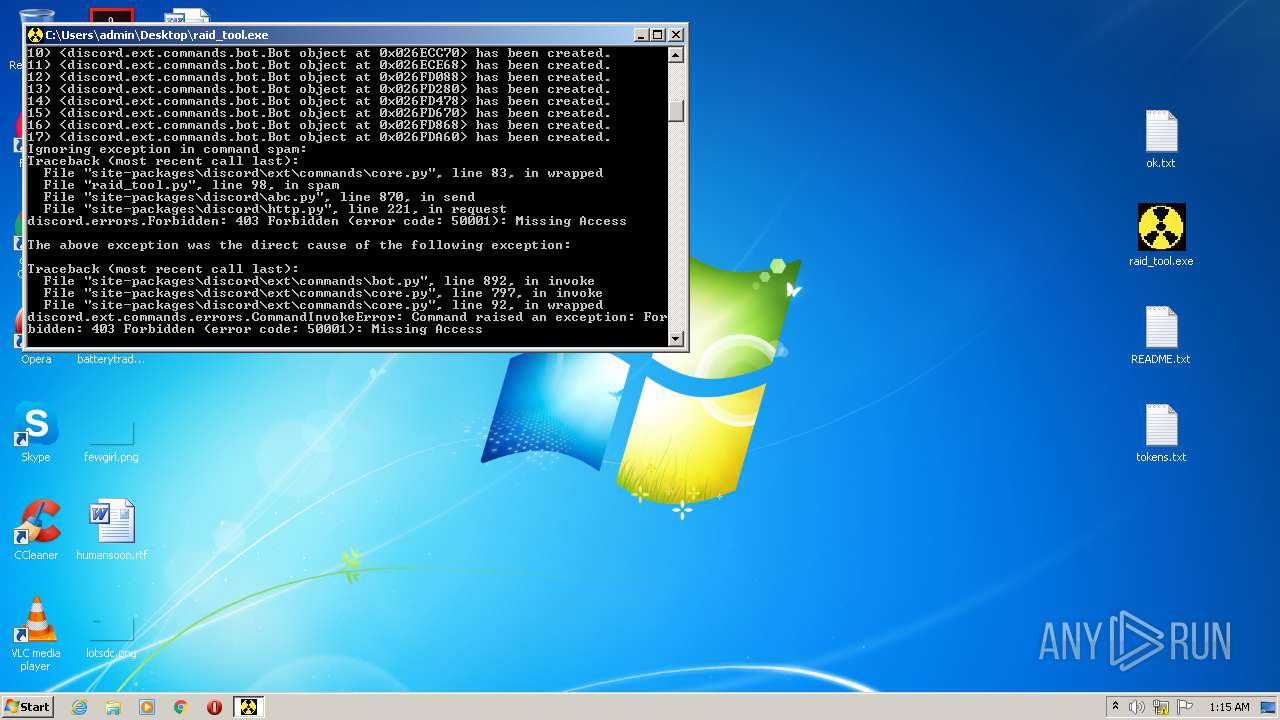
Dropped object may contain Bitcoin addresses
- raid_tool.exe (PID: 3000)
- raid_tool.exe (PID: 3544)
- raid_tool.exe (PID: 3256)
- raid_tool.exe (PID: 1820)
- raid_tool.exe (PID: 2388)
- raid_tool.exe (PID: 2240)
- raid_tool.exe (PID: 1272)
- raid_tool.exe (PID: 2580)
- raid_tool.exe (PID: 952)
- raid_tool.exe (PID: 3768)
- raid_tool.exe (PID: 2524)
- raid_tool.exe (PID: 4064)
Reads settings of System Certificates
- raid_tool.exe (PID: 2824)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:07:22 17:41:08 |
| ZipCRC: | 0x3365e02f |
| ZipCompressedSize: | 11572330 |
| ZipUncompressedSize: | 12028416 |
| ZipFileName: | raid_tool.exe |
Total processes
72
Monitored processes
25
Malicious processes
19
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 952 | "C:\Users\admin\Desktop\raid_tool.exe" | C:\Users\admin\Desktop\raid_tool.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1272 | "C:\Users\admin\Desktop\raid_tool.exe" | C:\Users\admin\Desktop\raid_tool.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1704 | "C:\Users\admin\Desktop\raid_tool.exe" | C:\Users\admin\Desktop\raid_tool.exe | — | raid_tool.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1820 | "C:\Users\admin\Desktop\raid_tool.exe" | C:\Users\admin\Desktop\raid_tool.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225786 Modules
| |||||||||||||||
| 1928 | "C:\Users\admin\Desktop\raid_tool.exe" | C:\Users\admin\Desktop\raid_tool.exe | — | raid_tool.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2180 | "C:\Users\admin\Desktop\raid_tool.exe" | C:\Users\admin\Desktop\raid_tool.exe | — | raid_tool.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2240 | "C:\Users\admin\Desktop\raid_tool.exe" | C:\Users\admin\Desktop\raid_tool.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2352 | "C:\Users\admin\Desktop\raid_tool.exe" | C:\Users\admin\Desktop\raid_tool.exe | — | raid_tool.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2388 | "C:\Users\admin\Desktop\raid_tool.exe" | C:\Users\admin\Desktop\raid_tool.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225786 Modules
| |||||||||||||||
| 2524 | "C:\Users\admin\Desktop\raid_tool.exe" | C:\Users\admin\Desktop\raid_tool.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
3 055
Read events
3 030
Write events
25
Delete events
0
Modification events
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\raid_tool - alphascript.zip | |||
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
408
Suspicious files
36
Text files
9 655
Unknown types
20
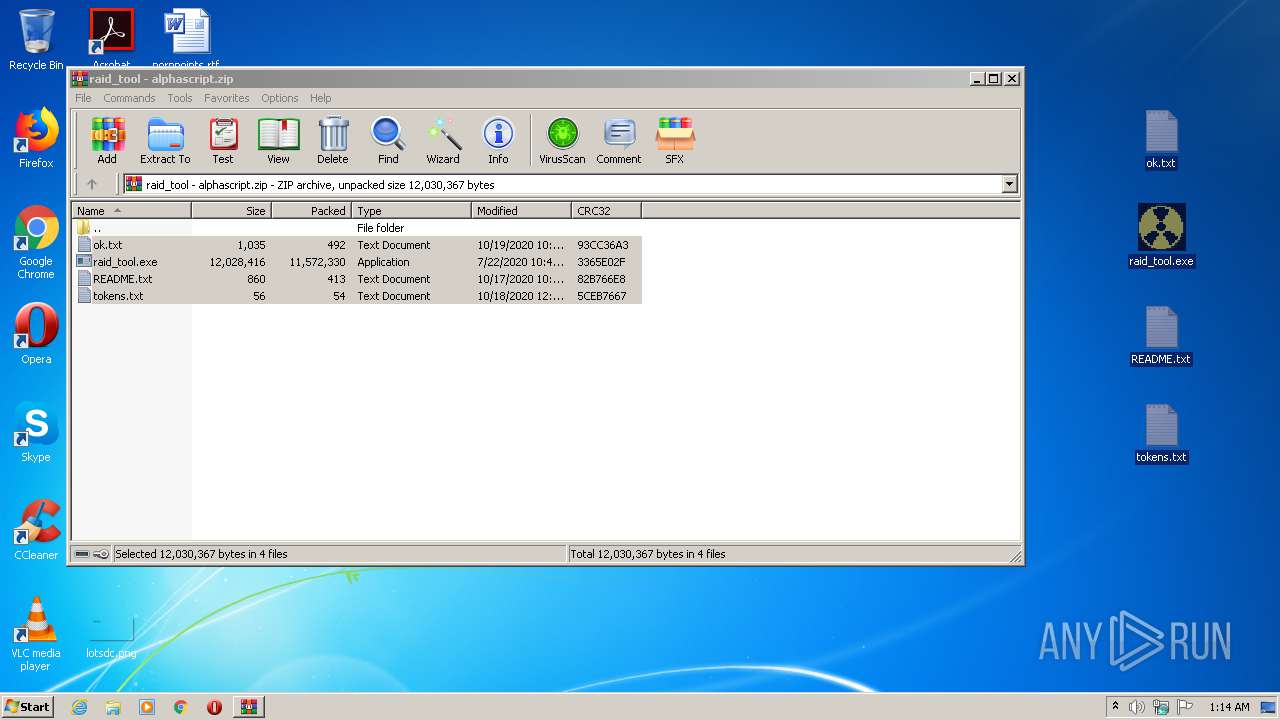
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3316.18774\raid_tool.exe | — | |
MD5:— | SHA256:— | |||
| 3316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3316.18774\README.txt | — | |
MD5:— | SHA256:— | |||
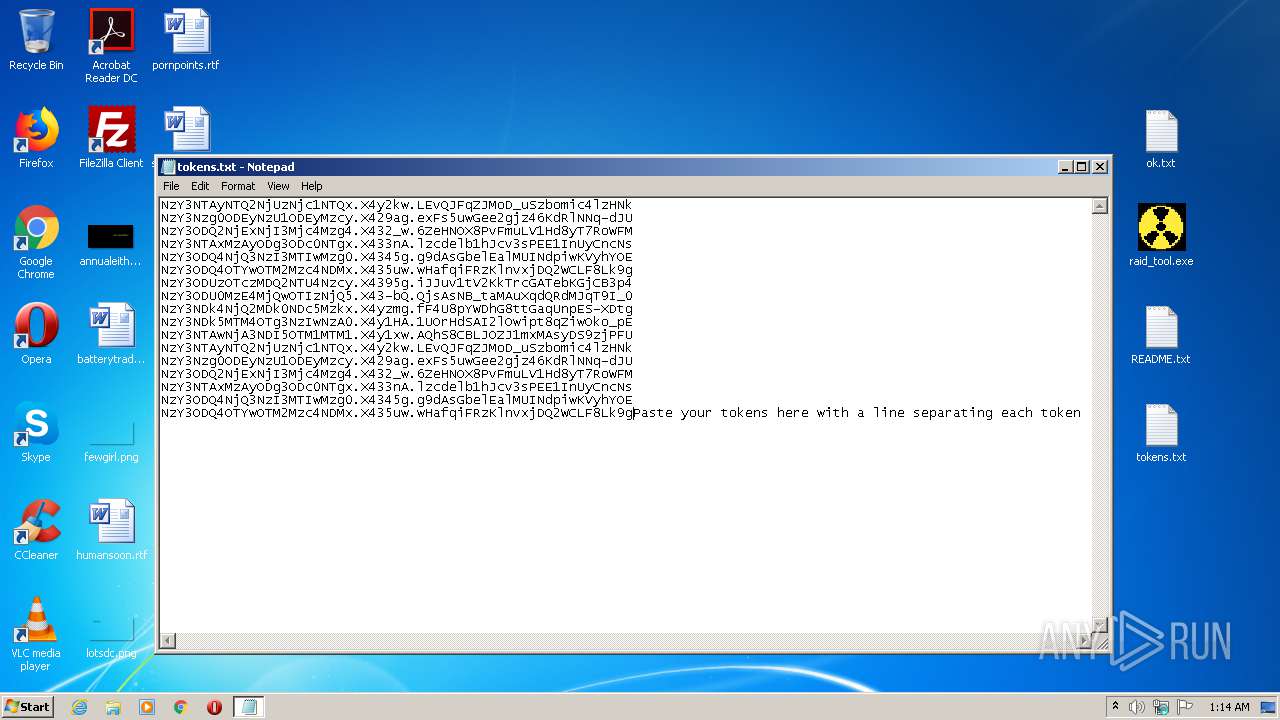
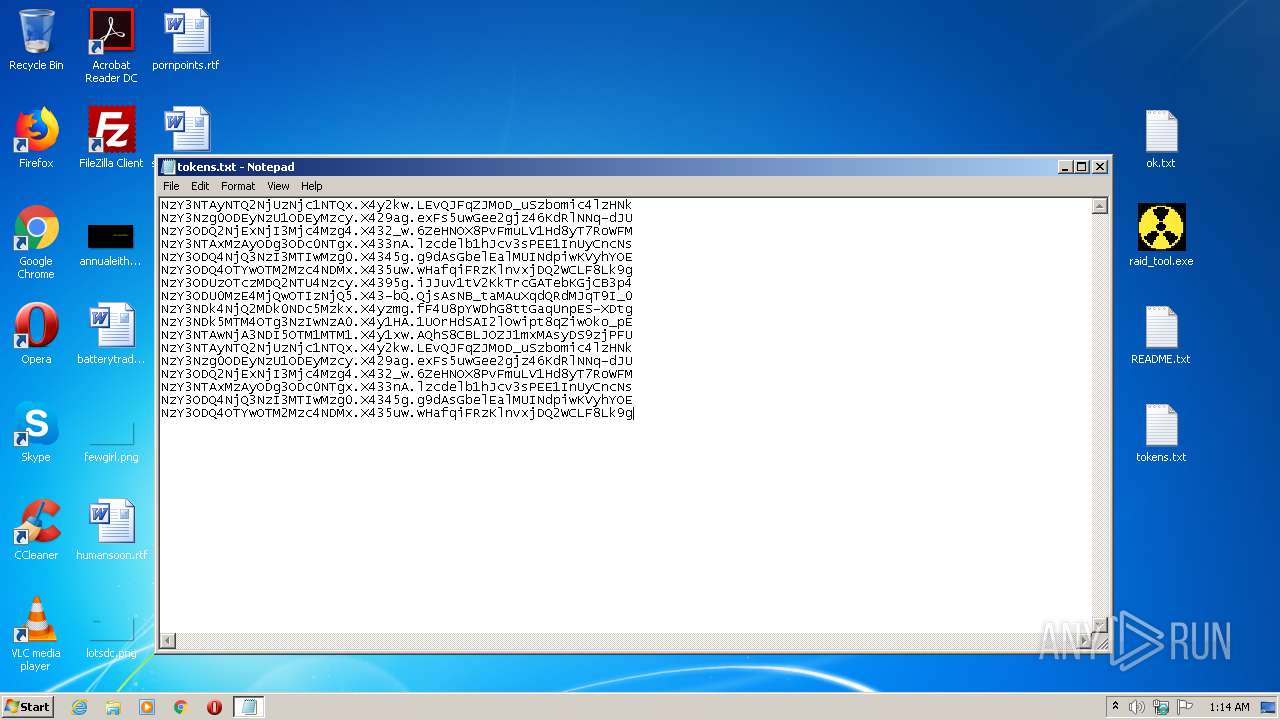
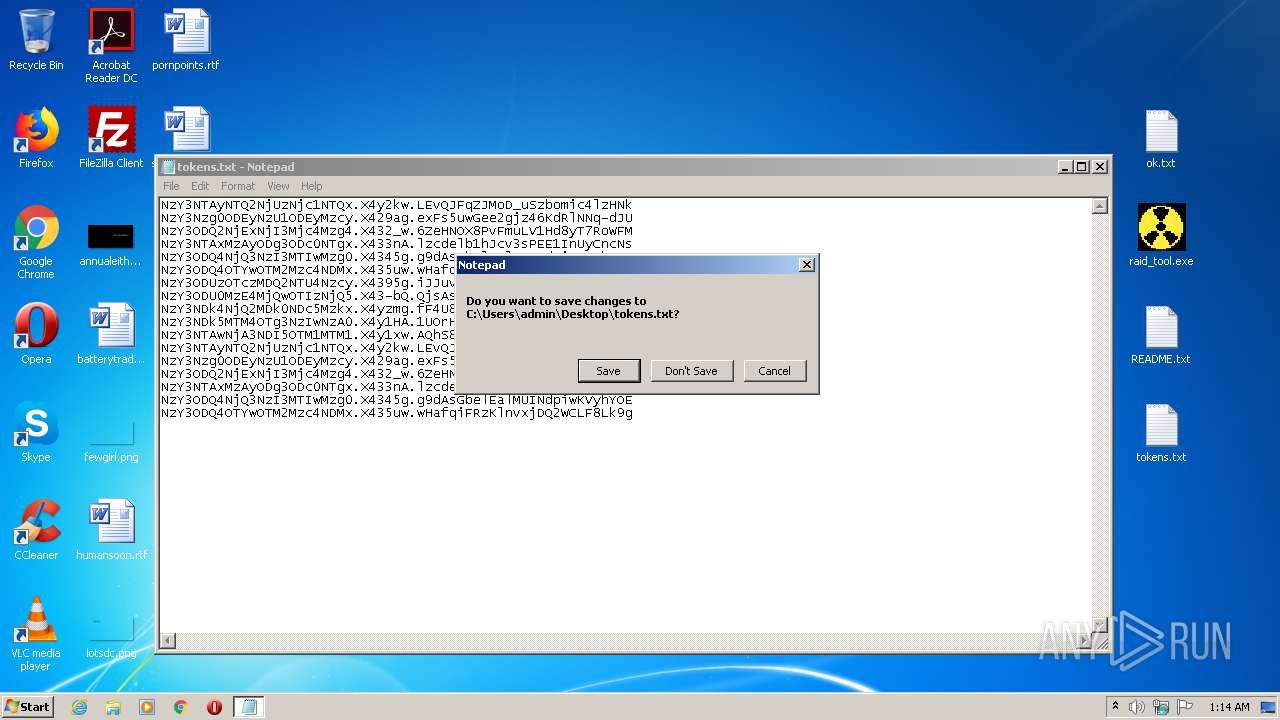
| 3316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3316.18774\tokens.txt | — | |
MD5:— | SHA256:— | |||
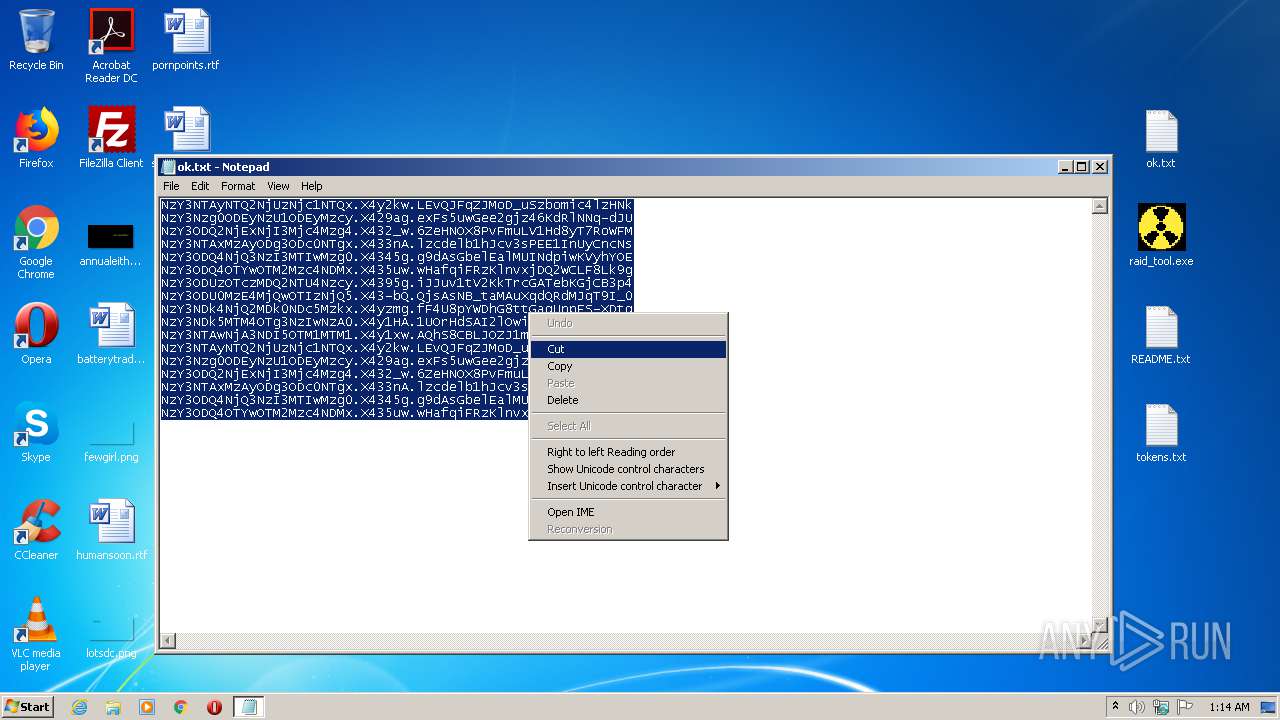
| 3316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3316.18774\ok.txt | — | |
MD5:— | SHA256:— | |||
| 3736 | NOTEPAD.EXE | C:\Users\admin\Desktop\tokens.txt | text | |
MD5:— | SHA256:— | |||
| 3000 | raid_tool.exe | C:\Users\admin\AppData\Local\Temp\_MEI30002\_cffi_backend.cp38-win32.pyd | executable | |
MD5:012DB6C90D38DB71D0647659217CA286 | SHA256:4207E3276411F75A6680EAE28D7D5ED7F6CAD946B1DE7B724440F44593267414 | |||
| 3000 | raid_tool.exe | C:\Users\admin\AppData\Local\Temp\_MEI30002\_hashlib.pyd | executable | |
MD5:05362ADD80824B06014645A7951337D8 | SHA256:20B3A3D3350B3D4D57911ECFDB15F77512A6E73C3BF72B410724F81C79A5B1AF | |||
| 3000 | raid_tool.exe | C:\Users\admin\AppData\Local\Temp\_MEI30002\VCRUNTIME140.dll | executable | |
MD5:4C360F78DE1F5BAAA5F110E65FAC94B4 | SHA256:AD1B0992B890BFE88EF52D0A830873ACC0AECC9BD6E4FC22397DBCCF4D2B4E37 | |||
| 3000 | raid_tool.exe | C:\Users\admin\AppData\Local\Temp\_MEI30002\_bz2.pyd | executable | |
MD5:0F75C236C4CCFEA1B16F132F6C139236 | SHA256:5DC26DCBF58CC7F5BFDEC0BADD5240D6724DB3E34010AAF35A31876FE4057158 | |||
| 3000 | raid_tool.exe | C:\Users\admin\AppData\Local\Temp\_MEI30002\_lzma.pyd | executable | |
MD5:54F12E2385A77D825AE4D41A4AC515FE | SHA256:08DE18FBA635822F3BB89C9429F175E3680B7261546430BA9E2ED09BB31F5218 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
34
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2824 | raid_tool.exe | 162.159.133.233:443 | discordapp.com | Cloudflare Inc | — | shared |
2824 | raid_tool.exe | 162.159.134.234:443 | gateway.discord.gg | Cloudflare Inc | — | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
discordapp.com |
| whitelisted |
gateway.discord.gg |
| whitelisted |