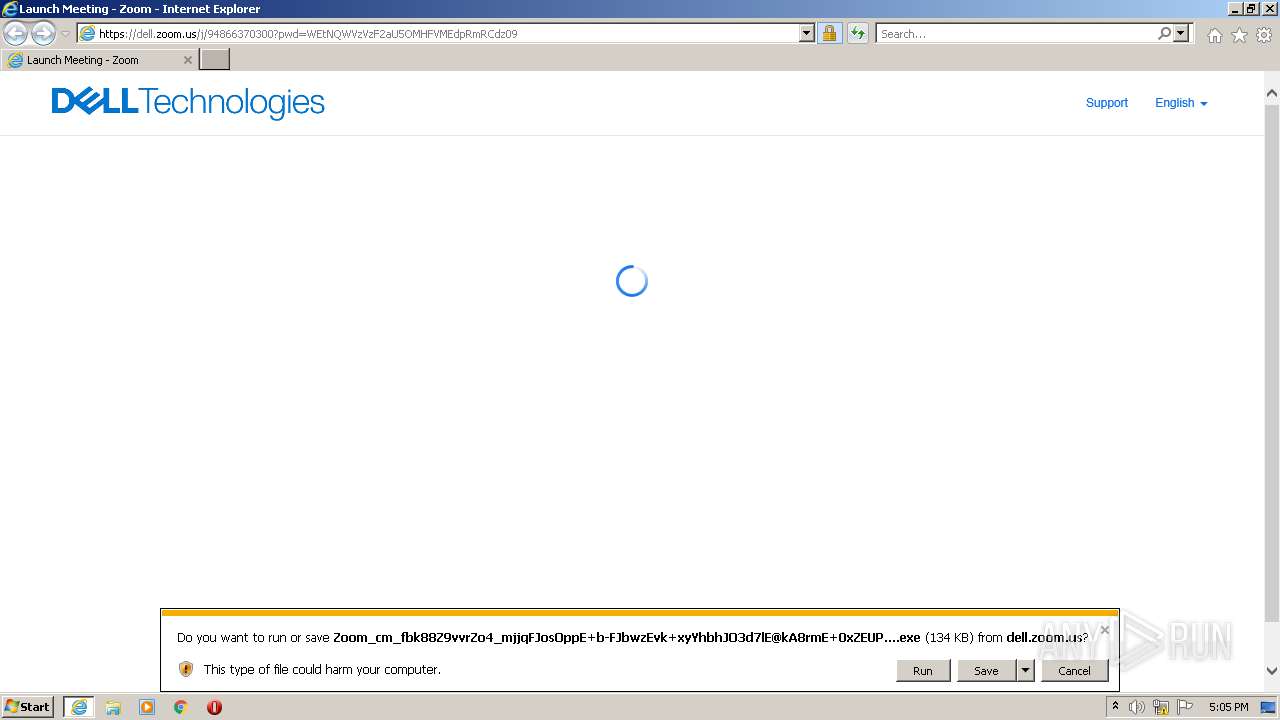
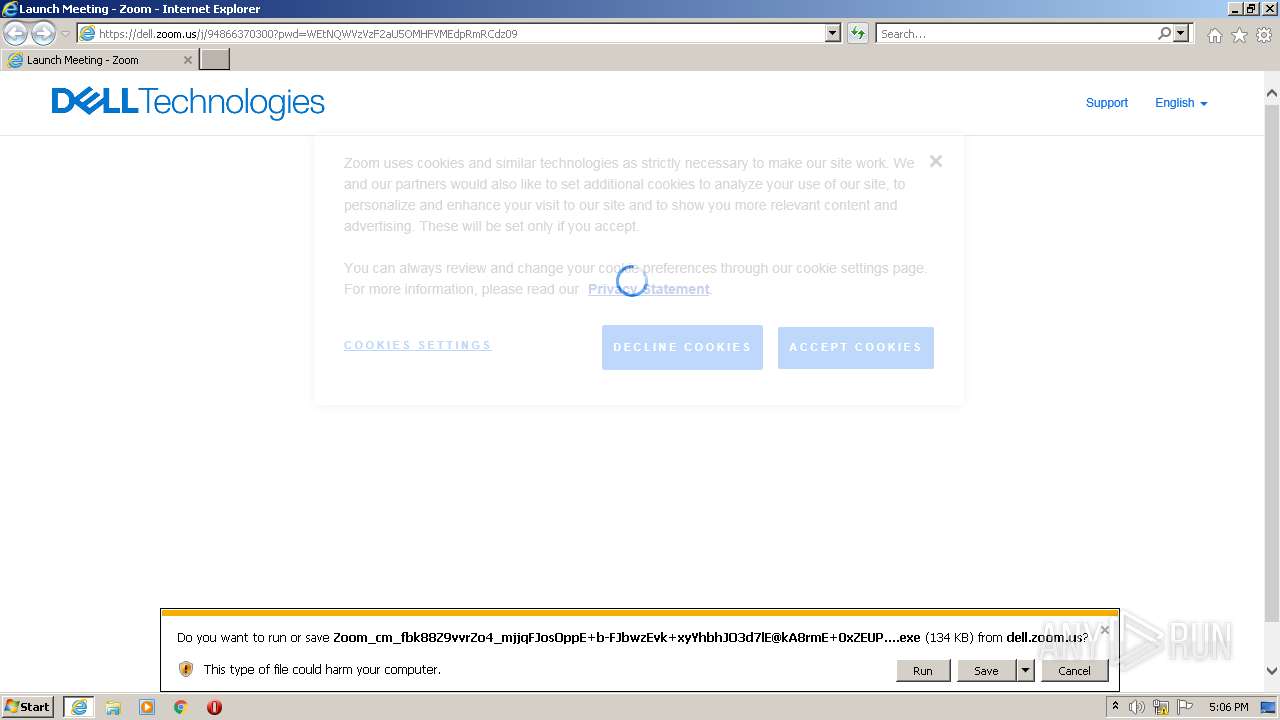
| URL: | https://dell.zoom.us/j/94866370300?pwd=WEtNQWVzVzF2aU5OMHFVMEdpRmRCdz09 |
| Full analysis: | https://app.any.run/tasks/51ccab72-d22e-41fb-b5a1-1ea5ec4c7955 |
| Verdict: | Malicious activity |
| Analysis date: | April 01, 2023, 16:05:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 41D2ED077103298719117AE99A52D09D |
| SHA1: | 7B301C765383C433D9E445084DD325A2225C0A82 |
| SHA256: | BA1FC1627C918ABA95E73DF9F7B4D7EAEAED170F109CD1C184304CD9902A5DFB |
| SSDEEP: | 3:N8YIQNzTTWhVVNBfnazfryj9cn:2YD/TOTazfuj+n |
MALICIOUS
Application was dropped or rewritten from another process
- Zoom_cm_fbk88Z9vvrZo4_mjjqFJosOppE+b-FJbwzEvk+xyYhbhJO3d7lE@kA8rmE+0xZEUPkaG_k152805ddd477a952_.exe (PID: 3504)
- Installer.exe (PID: 2964)
- Zoom.exe (PID: 1020)
- Installer.exe (PID: 1704)
- zm2C47.tmp (PID: 2416)
- Zoom.exe (PID: 2624)
SUSPICIOUS
Reads the Internet Settings
- Zoom_cm_fbk88Z9vvrZo4_mjjqFJosOppE+b-FJbwzEvk+xyYhbhJO3d7lE@kA8rmE+0xZEUPkaG_k152805ddd477a952_.exe (PID: 3504)
- Installer.exe (PID: 2964)
- Zoom.exe (PID: 1020)
- Zoom.exe (PID: 2624)
Reads security settings of Internet Explorer
- Zoom_cm_fbk88Z9vvrZo4_mjjqFJosOppE+b-FJbwzEvk+xyYhbhJO3d7lE@kA8rmE+0xZEUPkaG_k152805ddd477a952_.exe (PID: 3504)
- Installer.exe (PID: 2964)
- Zoom.exe (PID: 2624)
- Zoom.exe (PID: 1020)
Reads settings of System Certificates
- Zoom_cm_fbk88Z9vvrZo4_mjjqFJosOppE+b-FJbwzEvk+xyYhbhJO3d7lE@kA8rmE+0xZEUPkaG_k152805ddd477a952_.exe (PID: 3504)
- Installer.exe (PID: 2964)
- Zoom.exe (PID: 1020)
- Zoom.exe (PID: 2624)
Checks Windows Trust Settings
- Zoom_cm_fbk88Z9vvrZo4_mjjqFJosOppE+b-FJbwzEvk+xyYhbhJO3d7lE@kA8rmE+0xZEUPkaG_k152805ddd477a952_.exe (PID: 3504)
- Zoom.exe (PID: 1020)
- Installer.exe (PID: 2964)
- Zoom.exe (PID: 2624)
Executable content was dropped or overwritten
- Zoom_cm_fbk88Z9vvrZo4_mjjqFJosOppE+b-FJbwzEvk+xyYhbhJO3d7lE@kA8rmE+0xZEUPkaG_k152805ddd477a952_.exe (PID: 3504)
- Installer.exe (PID: 2964)
- Zoom.exe (PID: 1020)
Adds/modifies Windows certificates
- iexplore.exe (PID: 2824)
The process creates files with name similar to system file names
- Installer.exe (PID: 2964)
Starts application with an unusual extension
- Zoom_cm_fbk88Z9vvrZo4_mjjqFJosOppE+b-FJbwzEvk+xyYhbhJO3d7lE@kA8rmE+0xZEUPkaG_k152805ddd477a952_.exe (PID: 3504)
Application launched itself
- Installer.exe (PID: 2964)
- Zoom.exe (PID: 1020)
Starts itself from another location
- Zoom_cm_fbk88Z9vvrZo4_mjjqFJosOppE+b-FJbwzEvk+xyYhbhJO3d7lE@kA8rmE+0xZEUPkaG_k152805ddd477a952_.exe (PID: 3504)
INFO
Executable content was dropped or overwritten
- iexplore.exe (PID: 2824)
- iexplore.exe (PID: 3220)
Application launched itself
- iexplore.exe (PID: 2824)
Create files in a temporary directory
- iexplore.exe (PID: 2824)
- Zoom_cm_fbk88Z9vvrZo4_mjjqFJosOppE+b-FJbwzEvk+xyYhbhJO3d7lE@kA8rmE+0xZEUPkaG_k152805ddd477a952_.exe (PID: 3504)
- Zoom.exe (PID: 1020)
The process uses the downloaded file
- iexplore.exe (PID: 2824)
- Zoom_cm_fbk88Z9vvrZo4_mjjqFJosOppE+b-FJbwzEvk+xyYhbhJO3d7lE@kA8rmE+0xZEUPkaG_k152805ddd477a952_.exe (PID: 3504)
Creates files or folders in the user directory
- Zoom_cm_fbk88Z9vvrZo4_mjjqFJosOppE+b-FJbwzEvk+xyYhbhJO3d7lE@kA8rmE+0xZEUPkaG_k152805ddd477a952_.exe (PID: 3504)
- Zoom.exe (PID: 2624)
- Installer.exe (PID: 2964)
- Zoom.exe (PID: 1020)
Reads the computer name
- Zoom_cm_fbk88Z9vvrZo4_mjjqFJosOppE+b-FJbwzEvk+xyYhbhJO3d7lE@kA8rmE+0xZEUPkaG_k152805ddd477a952_.exe (PID: 3504)
- Installer.exe (PID: 2964)
- Installer.exe (PID: 1704)
- Zoom.exe (PID: 1020)
- Zoom.exe (PID: 2624)
- wmpnscfg.exe (PID: 3840)
Checks proxy server information
- Zoom_cm_fbk88Z9vvrZo4_mjjqFJosOppE+b-FJbwzEvk+xyYhbhJO3d7lE@kA8rmE+0xZEUPkaG_k152805ddd477a952_.exe (PID: 3504)
Checks supported languages
- Zoom_cm_fbk88Z9vvrZo4_mjjqFJosOppE+b-FJbwzEvk+xyYhbhJO3d7lE@kA8rmE+0xZEUPkaG_k152805ddd477a952_.exe (PID: 3504)
- Installer.exe (PID: 2964)
- Installer.exe (PID: 1704)
- Zoom.exe (PID: 1020)
- zm2C47.tmp (PID: 2416)
- Zoom.exe (PID: 2624)
- wmpnscfg.exe (PID: 3840)
Reads the machine GUID from the registry
- Zoom_cm_fbk88Z9vvrZo4_mjjqFJosOppE+b-FJbwzEvk+xyYhbhJO3d7lE@kA8rmE+0xZEUPkaG_k152805ddd477a952_.exe (PID: 3504)
- Installer.exe (PID: 2964)
- Zoom.exe (PID: 1020)
- Zoom.exe (PID: 2624)
- wmpnscfg.exe (PID: 3840)
The process checks LSA protection
- Zoom_cm_fbk88Z9vvrZo4_mjjqFJosOppE+b-FJbwzEvk+xyYhbhJO3d7lE@kA8rmE+0xZEUPkaG_k152805ddd477a952_.exe (PID: 3504)
- Installer.exe (PID: 2964)
- Zoom.exe (PID: 1020)
- Zoom.exe (PID: 2624)
- wmpnscfg.exe (PID: 3840)
Process checks computer location settings
- Zoom.exe (PID: 1020)
Manual execution by a user
- wmpnscfg.exe (PID: 3840)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
48
Monitored processes
9
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1020 | "C:\Users\admin\AppData\Roaming\Zoom\bin\Zoom.exe" "--url=zoommtg://win.launch?h.domain=dell.zoom.us&h.path=join&confid=dXNzPTdGUG8tRjUyR2tKeTh5Ym82aWZEYU8tV2ZfaEF6VE9seklpeUp5WDAyUGRNWk5BRTFXMTFadXVHQkhVSjFSRGR6SWVxSjc5VmRIOXVFYV90UElWZmhGaGcubllqalZqd0V6TWRYSkx4cyZ0aWQ9YWQ1ZDBhNjc2YWY1NDEwZDk3YTEyMzFjNWE2ZGQ3ZjQ%3D&mcv=0.92.11227.0929&stype=0&zc=0&browser=msie&action=join&confno=94866370300&pwd=WEtNQWVzVzF2aU5OMHFVMEdpRmRCdz09" | C:\Users\admin\AppData\Roaming\Zoom\bin\Zoom.exe | Zoom_cm_fbk88Z9vvrZo4_mjjqFJosOppE+b-FJbwzEvk+xyYhbhJO3d7lE@kA8rmE+0xZEUPkaG_k152805ddd477a952_.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Meetings Exit code: 0 Version: 5,14,0,13888 Modules
| |||||||||||||||
| 1704 | "C:\Users\admin\AppData\Roaming\Zoom\ZoomDownload\Installer.exe" /addfwexception --bin_home="C:\Users\admin\AppData\Roaming\Zoom\bin" | C:\Users\admin\AppData\Roaming\Zoom\ZoomDownload\Installer.exe | Installer.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: HIGH Description: Zoom Installer Exit code: 0 Version: 5,14,0,13888 Modules
| |||||||||||||||
| 2416 | "C:\Users\admin\AppData\Local\Temp\zm2C47.tmp" -DAF8C715436E44649F1312698287E6A5=C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Zoom_cm_fbk88Z9vvrZo4_mjjqFJosOppE+b-FJbwzEvk+xyYhbhJO3d7lE@kA8rmE+0xZEUPkaG_k152805ddd477a952_.exe | C:\Users\admin\AppData\Local\Temp\zm2C47.tmp | — | Zoom_cm_fbk88Z9vvrZo4_mjjqFJosOppE+b-FJbwzEvk+xyYhbhJO3d7lE@kA8rmE+0xZEUPkaG_k152805ddd477a952_.exe | |||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Opener Exit code: 0 Version: 5,10,3,4851 Modules
| |||||||||||||||
| 2624 | "C:\Users\admin\AppData\Roaming\Zoom\bin\Zoom.exe" --action=join --runaszvideo=TRUE | C:\Users\admin\AppData\Roaming\Zoom\bin\Zoom.exe | Zoom.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Meetings Exit code: 0 Version: 5,14,0,13888 Modules
| |||||||||||||||
| 2824 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://dell.zoom.us/j/94866370300?pwd=WEtNQWVzVzF2aU5OMHFVMEdpRmRCdz09" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2964 | "C:\Users\admin\AppData\Roaming\Zoom\ZoomDownload\Installer.exe" ZInstaller --conf.mode=silent --ipc_wnd=66066 | C:\Users\admin\AppData\Roaming\Zoom\ZoomDownload\Installer.exe | Zoom_cm_fbk88Z9vvrZo4_mjjqFJosOppE+b-FJbwzEvk+xyYhbhJO3d7lE@kA8rmE+0xZEUPkaG_k152805ddd477a952_.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Installer Exit code: 0 Version: 5,14,0,13888 Modules
| |||||||||||||||
| 3220 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2824 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3504 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Zoom_cm_fbk88Z9vvrZo4_mjjqFJosOppE+b-FJbwzEvk+xyYhbhJO3d7lE@kA8rmE+0xZEUPkaG_k152805ddd477a952_.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Zoom_cm_fbk88Z9vvrZo4_mjjqFJosOppE+b-FJbwzEvk+xyYhbhJO3d7lE@kA8rmE+0xZEUPkaG_k152805ddd477a952_.exe | iexplore.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Opener Exit code: 0 Version: 5,10,3,4851 Modules
| |||||||||||||||
| 3840 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
92 192
Read events
91 740
Write events
426
Delete events
26
Modification events
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2824) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
390
Suspicious files
294
Text files
132
Unknown types
20
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3220 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | der | |
MD5:— | SHA256:— | |||
| 3220 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3220 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\2JKI8PXD.txt | text | |
MD5:— | SHA256:— | |||
| 3220 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\94866370300[1].htm | html | |
MD5:— | SHA256:— | |||
| 3220 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\80237EE4964FC9C409AAF55BF996A292_FB287BEB63DB9E8D59A799779773B97C | binary | |
MD5:— | SHA256:— | |||
| 3220 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\SR1HV4GN.txt | text | |
MD5:— | SHA256:— | |||
| 3220 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\V68BFH8T.txt | text | |
MD5:— | SHA256:— | |||
| 3220 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:— | SHA256:— | |||
| 3220 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\8DOR32H2.txt | text | |
MD5:— | SHA256:— | |||
| 3220 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\BF776OK6.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
53
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3220 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAhflMAthXvozBT%2FU%2B2iPio%3D | US | der | 471 b | whitelisted |
3220 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
2824 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2824 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | der | 471 b | whitelisted |
3220 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | US | der | 471 b | whitelisted |
3220 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSnxLiz3Fu1WB6n1%2FE6xWn1b0jXiQQUdIWAwGbH3zfez70pN6oDHb7tzRcCEAbCsehAv%2FkAxBfkV5KvfLI%3D | US | der | 471 b | whitelisted |
2824 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
2824 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
3220 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?884ff7ffd71a194f | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3220 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
2824 | iexplore.exe | 204.79.197.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3220 | iexplore.exe | 18.66.147.121:443 | static.ada.support | AMAZON-02 | US | suspicious |
3220 | iexplore.exe | 34.98.108.207:443 | cdn.solvvy.com | GOOGLE | US | unknown |
3220 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3220 | iexplore.exe | 18.66.130.242:443 | st3.zoom.us | AMAZON-02 | US | unknown |
3220 | iexplore.exe | 54.235.192.240:443 | log-gateway.zoom.us | AMAZON-AES | US | unknown |
3220 | iexplore.exe | 104.19.187.97:443 | cdn.cookielaw.org | CLOUDFLARENET | — | whitelisted |
3220 | iexplore.exe | 104.18.43.158:443 | geolocation.onetrust.com | CLOUDFLARENET | — | shared |
2824 | iexplore.exe | 13.107.21.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dell.zoom.us |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
static.ada.support |
| whitelisted |
cdn.solvvy.com |
| shared |
st3.zoom.us |
| whitelisted |
st1.zoom.us |
| whitelisted |
log-gateway.zoom.us |
| unknown |
Threats
Process | Message |
|---|---|
Installer.exe | [ProductPathHelper::RecursiveRemoveDirA] Path is: |
Installer.exe | |
Installer.exe | [ProductPathHelper::RecursiveRemoveDirA] Path is: |
Installer.exe | C:\Users\admin\AppData\Roaming\Zoom\zoom_install_src |
Installer.exe | |
Installer.exe | C:\Users\admin\AppData\Roaming\Zoom\zoom_install_src |
Installer.exe | C:\Users\admin\AppData\Roaming\Zoom\tmp_bin |
Installer.exe | [ProductPathHelper::RecursiveRemoveDirA] Path is: |
Installer.exe | C:\Users\admin\AppData\Roaming\Zoom\tmp_uninstall |
Installer.exe | |