| File name: | Transaction Error Payments skype.com |
| Full analysis: | https://app.any.run/tasks/a172943a-187a-4da6-892f-dbf28a07ce63 |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2024, 15:13:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | EEA902810F2A087672DAFD9CEAC2B479 |
| SHA1: | 9DBCEE36364CAD1752197A17CED603DB119B49C8 |
| SHA256: | BA1C87A8C55358752053C44CF5AA20D7409DD7F27400D7F4608682A038A0721B |
| SSDEEP: | 98304:dbrLIBtkeqDCgvEudxXgo5UZEGlJn/b7FlBdwu9YOoBogq3ZA4svICbHLG5zJPUg:I |
MALICIOUS
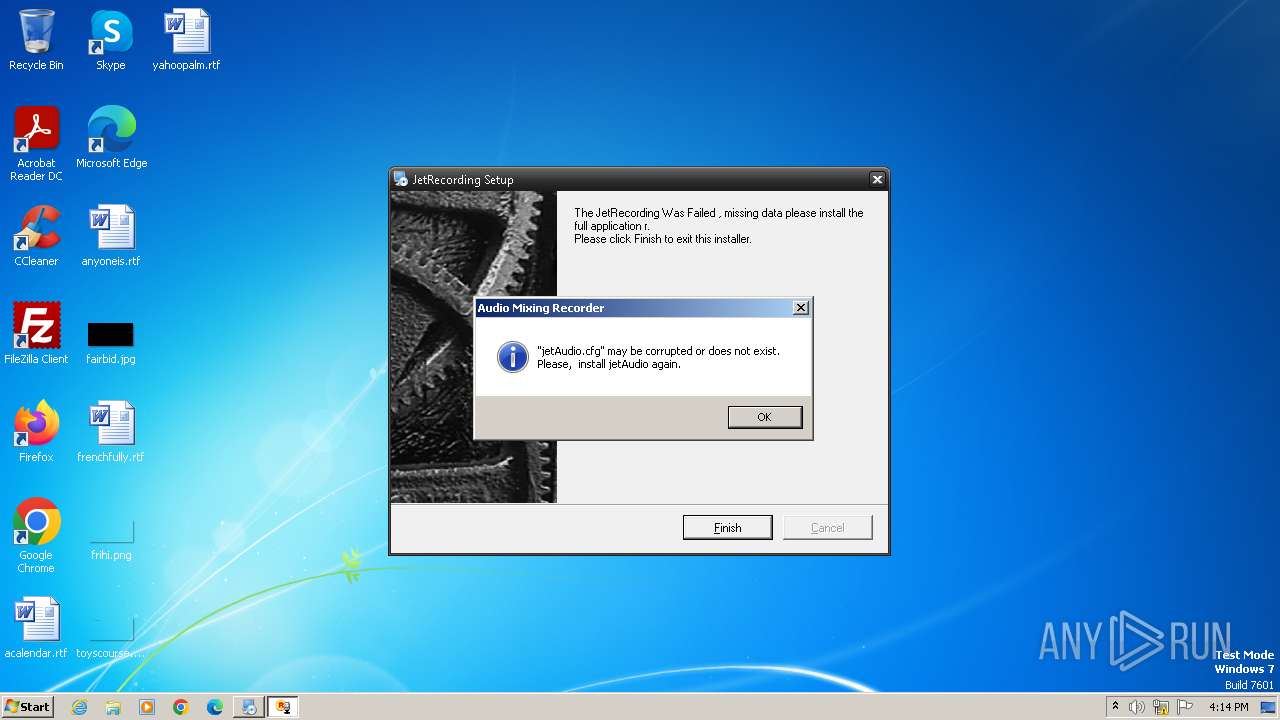
Drops the executable file immediately after the start
- irsetup.exe (PID: 4008)
- a172943a-187a-4da6-892f-dbf28a07ce63.exe (PID: 3976)
- JetRecorder.exe (PID: 4068)
Changes the autorun value in the registry
- reg.exe (PID: 4084)
SUSPICIOUS
Reads security settings of Internet Explorer
- a172943a-187a-4da6-892f-dbf28a07ce63.exe (PID: 3976)
Reads the Internet Settings
- a172943a-187a-4da6-892f-dbf28a07ce63.exe (PID: 3976)
Reads the Windows owner or organization settings
- irsetup.exe (PID: 4008)
Executable content was dropped or overwritten
- irsetup.exe (PID: 4008)
- a172943a-187a-4da6-892f-dbf28a07ce63.exe (PID: 3976)
- JetRecorder.exe (PID: 4068)
The process executes via Task Scheduler
- reg.exe (PID: 4084)
INFO
Checks supported languages
- a172943a-187a-4da6-892f-dbf28a07ce63.exe (PID: 3976)
- irsetup.exe (PID: 4008)
- JetRecorder.exe (PID: 4068)
Reads the computer name
- a172943a-187a-4da6-892f-dbf28a07ce63.exe (PID: 3976)
- irsetup.exe (PID: 4008)
- JetRecorder.exe (PID: 4068)
Create files in a temporary directory
- irsetup.exe (PID: 4008)
- JetRecorder.exe (PID: 4068)
- a172943a-187a-4da6-892f-dbf28a07ce63.exe (PID: 3976)
Creates files or folders in the user directory
- JetRecorder.exe (PID: 4068)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (17.7) |
|---|---|---|
| .scr | | | Windows screen saver (7.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.7) |
| .exe | | | Win32 Executable (generic) (2.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:08:28 18:19:38+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 23552 |
| InitializedDataSize: | 48640 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2ce1 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 9.6.0.1 |
| ProductVersionNumber: | 9.6.0.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Private build |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | Created with Setup Factory |
| FileDescription: | Setup Application |
| FileVersion: | 9.6.0.1 |
| InternalName: | suf_launch |
| LegalCopyright: | Setup Engine Copyright © 2004-2023 Indigo Rose Corporation |
| LegalTrademarks: | Setup Factory is a trademark of Indigo Rose Corporation. |
| OriginalFileName: | suf_launch.exe |
| ProductName: | Setup Factory Runtime |
| ProductVersion: | 9.6.0.1 |
Total processes
36
Monitored processes
4
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3976 | "C:\Users\admin\AppData\Local\Temp\a172943a-187a-4da6-892f-dbf28a07ce63.exe" | C:\Users\admin\AppData\Local\Temp\a172943a-187a-4da6-892f-dbf28a07ce63.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Setup Application Exit code: 0 Version: 9.6.0.1 Modules
| |||||||||||||||
| 4008 | "C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\irsetup.exe" __IRAOFF:4229178 "__IRAFN:C:\Users\admin\AppData\Local\Temp\a172943a-187a-4da6-892f-dbf28a07ce63.exe" "__IRCT:2" "__IRTSS:0" "__IRSID:S-1-5-21-1302019708-1500728564-335382590-1000" | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\irsetup.exe | a172943a-187a-4da6-892f-dbf28a07ce63.exe | ||||||||||||
User: admin Company: Indigo Rose Corporation Integrity Level: MEDIUM Description: Setup Application Exit code: 0 Version: 9.6.0.1 Modules
| |||||||||||||||
| 4068 | C:\Users\admin\AppData\Local\Temp\JetRecorder.exe | C:\Users\admin\AppData\Local\Temp\JetRecorder.exe | irsetup.exe | ||||||||||||
User: admin Company: COWON America, Inc. Integrity Level: MEDIUM Description: JetRecorder Exit code: 0 Version: 1, 0, 2, 4511 Modules
| |||||||||||||||
| 4084 | C:\Windows\system32\REG.EXE ADD "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /V "SysCheck" /t REG_SZ /F /D "schtasks /run /tn SysCheck" | C:\Windows\System32\reg.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 177
Read events
3 168
Write events
9
Delete events
0
Modification events
| (PID) Process: | (3976) a172943a-187a-4da6-892f-dbf28a07ce63.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3976) a172943a-187a-4da6-892f-dbf28a07ce63.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3976) a172943a-187a-4da6-892f-dbf28a07ce63.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3976) a172943a-187a-4da6-892f-dbf28a07ce63.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4084) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | SysCheck |
Value: schtasks /run /tn SysCheck | |||
Executable files
6
Suspicious files
2
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3976 | a172943a-187a-4da6-892f-dbf28a07ce63.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\lua5.1.dll | executable | |
MD5:C333AF59FA9F0B12D1CD9F6BBA111E3A | SHA256:FAD540071986C59EC40102C9CA9518A0DDCE80CF39EB2FD476BB1A7A03D6EB34 | |||
| 4008 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\IRIMG1.JPG | image | |
MD5:874E3E604857F429A7E5075F42478063 | SHA256:8F837FF1E644F32FD2B7E70EC5CE1FD32C58DA0A169E172B5FB464EE775C6F8C | |||
| 3976 | a172943a-187a-4da6-892f-dbf28a07ce63.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\irsetup.exe | executable | |
MD5:3FC1DB5CB5BA580147D3502E982152A1 | SHA256:5E3237A155864BFDD6290A3D195E53CE3CBF522FD1FEB318CE3C5D94B57B49A9 | |||
| 4008 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\IRIMG3.JPG | image | |
MD5:5DC2D6C2CDB0BD1447DC42810344FA1E | SHA256:ECA7064B09FA0B62582A795965B3D980E299293A4D5052D7925B40002EA9000B | |||
| 4008 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\IRIMG2.JPG | image | |
MD5:E3F04B9A2CB90768D26E29915A44C32D | SHA256:EC6FF19E6F85D0A9EDFE25CC8206AEC67E5243C884E73BB82AFA4BBC03F83CB3 | |||
| 4008 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\JetCfg.dll | executable | |
MD5:412D5CF1707378AD960F5C14093EC57D | SHA256:933E0D5AEE41C8DC845D4DD53E11532F2FC065EA631C863EFAD683B6F2FBD9AA | |||
| 4008 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\txinst.txt | text | |
MD5:D7E746EE6FECCE39DC0B3B1F284F0254 | SHA256:263C707C9C42909509EB454DE6D774C98BB45820335EF48E452C2BB8292B6EAE | |||
| 4008 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\irsetup.skin | executable | |
MD5:04915D39840C9406D1E9347C0EAFD7B7 | SHA256:CC26D305824288A1C43C1C35CF8F456C5B19EFFAA39475F5179D372C4A06EEF5 | |||
| 4008 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\irsetup.dat | binary | |
MD5:189927ECE66A5DF690CE5B8934FB0046 | SHA256:4C3B51519CD741D29DD2A12D0015DACDC3ED921CED8A22542F1E23F5D54DFCFD | |||
| 4068 | JetRecorder.exe | C:\Users\admin\AppData\Local\Temp\log.old | binary | |
MD5:28EF021214018475DA3D1AC10E490764 | SHA256:3F0C88FCFA44E7B451A747F090D6F69664B3BE2934907B8E1D1DABEC6F08D719 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |