| File name: | xls |
| Full analysis: | https://app.any.run/tasks/2bb0c4cf-4946-4635-92e8-eab78b608ce0 |
| Verdict: | Malicious activity |
| Analysis date: | August 28, 2024, 16:30:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
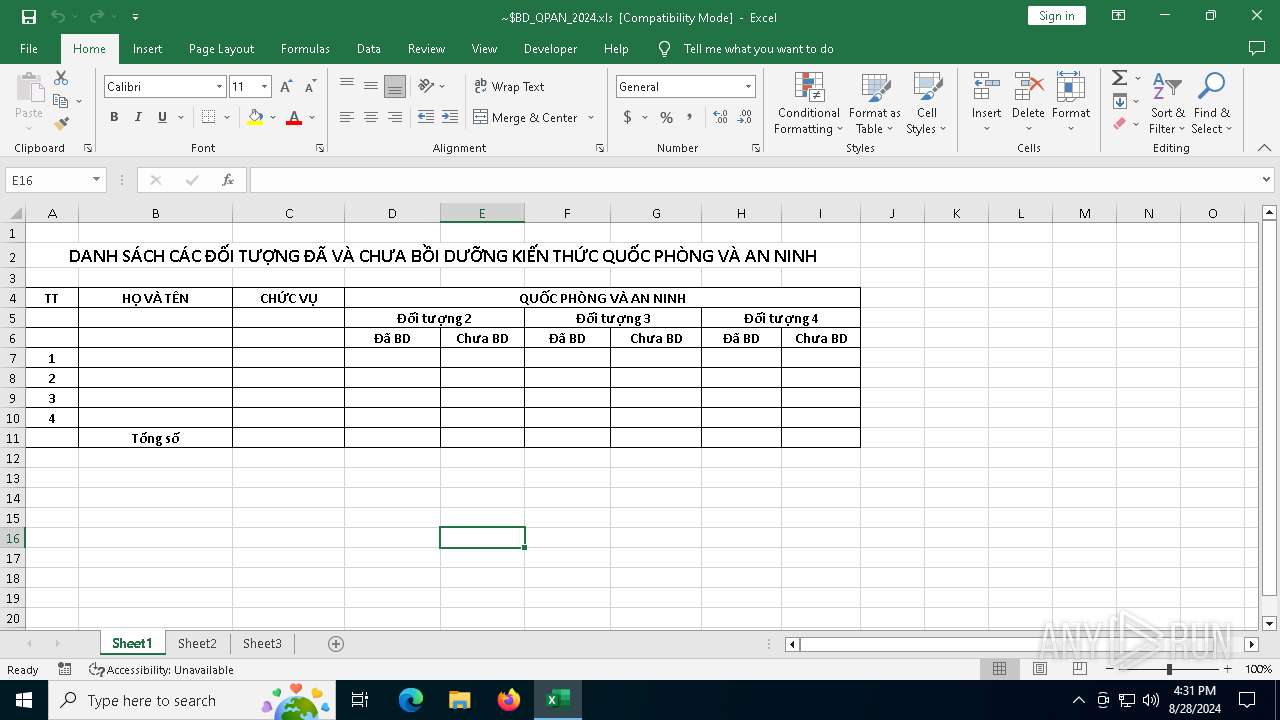
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Author: Windows User, Last Saved By: Windows User, Name of Creating Application: Microsoft Excel, Create Time/Date: Tue Apr 2 07:57:44 2024, Last Saved Time/Date: Tue Apr 2 07:58:03 2024, Security: 0 |
| MD5: | 7B5646374BE4AA1252CADFE59A37A900 |
| SHA1: | 33DE5A0F75142E99165DF146643E3E5ADF49673B |
| SHA256: | BA0CCD90AB208C591033A10806A81244047458A68856093687E0D5B739BC28A7 |
| SSDEEP: | 12288:U/fCiCqVTSsu1AU3/i4Ia2YZzb3RdZblNPO5StYJaKBsMm9:0fC3K/uOxy/pddZqXMks |
MALICIOUS
Detects the decoding of a binary file from Base64 (SCRIPT)
- EXCEL.EXE (PID: 6836)
Checks whether a specified folder exists (SCRIPT)
- EXCEL.EXE (PID: 6836)
Uses sleep, probably for evasion (MACROS)
- EXCEL.EXE (PID: 6836)
Starts CMD.EXE for commands execution
- EXCEL.EXE (PID: 6836)
Microsoft Office executes commands via PowerShell or Cmd
- EXCEL.EXE (PID: 6836)
Unusual execution from MS Office
- EXCEL.EXE (PID: 6836)
Changes the autorun value in the registry
- gpresult.exe (PID: 4100)
SUSPICIOUS
Creates FileSystem object to access computer's file system (SCRIPT)
- EXCEL.EXE (PID: 6836)
Checks whether a specific file exists (SCRIPT)
- EXCEL.EXE (PID: 6836)
Sets XML DOM element text (SCRIPT)
- splwow64.exe (PID: 2028)
Writes binary data to a Stream object (SCRIPT)
- EXCEL.EXE (PID: 6836)
Accesses current user name via WMI (SCRIPT)
- EXCEL.EXE (PID: 6836)
Runs shell command (SCRIPT)
- EXCEL.EXE (PID: 6836)
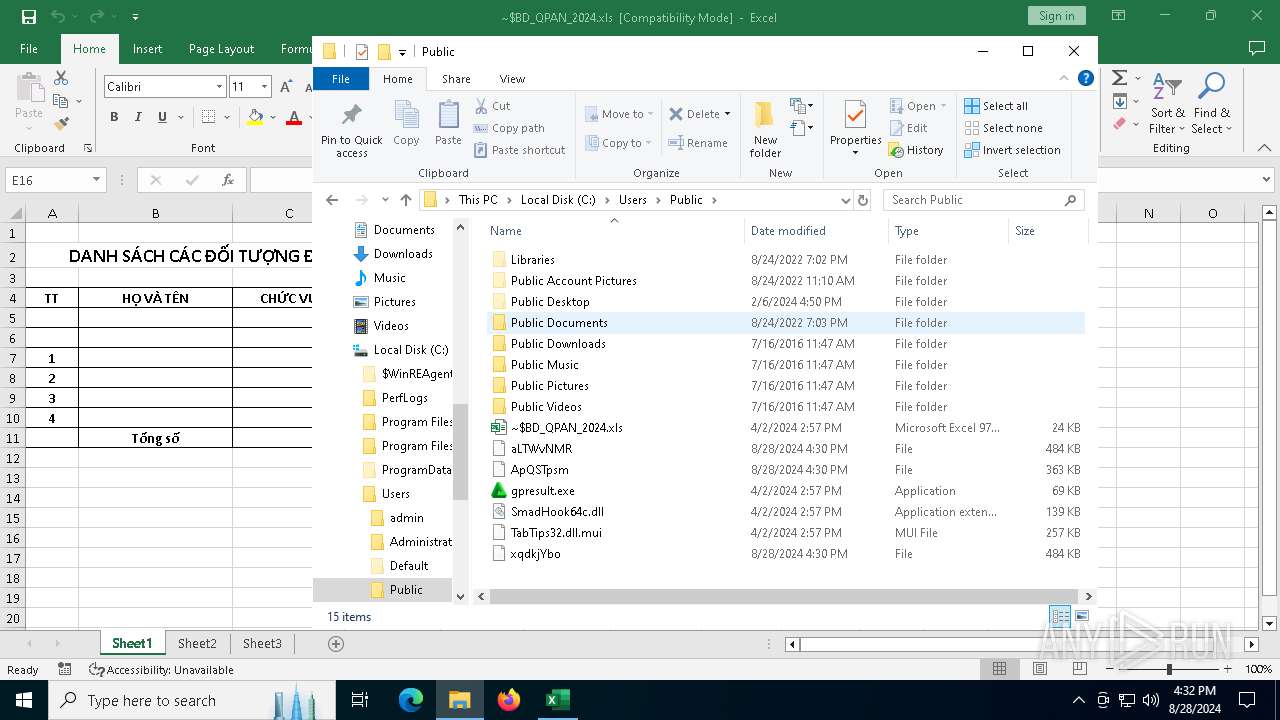
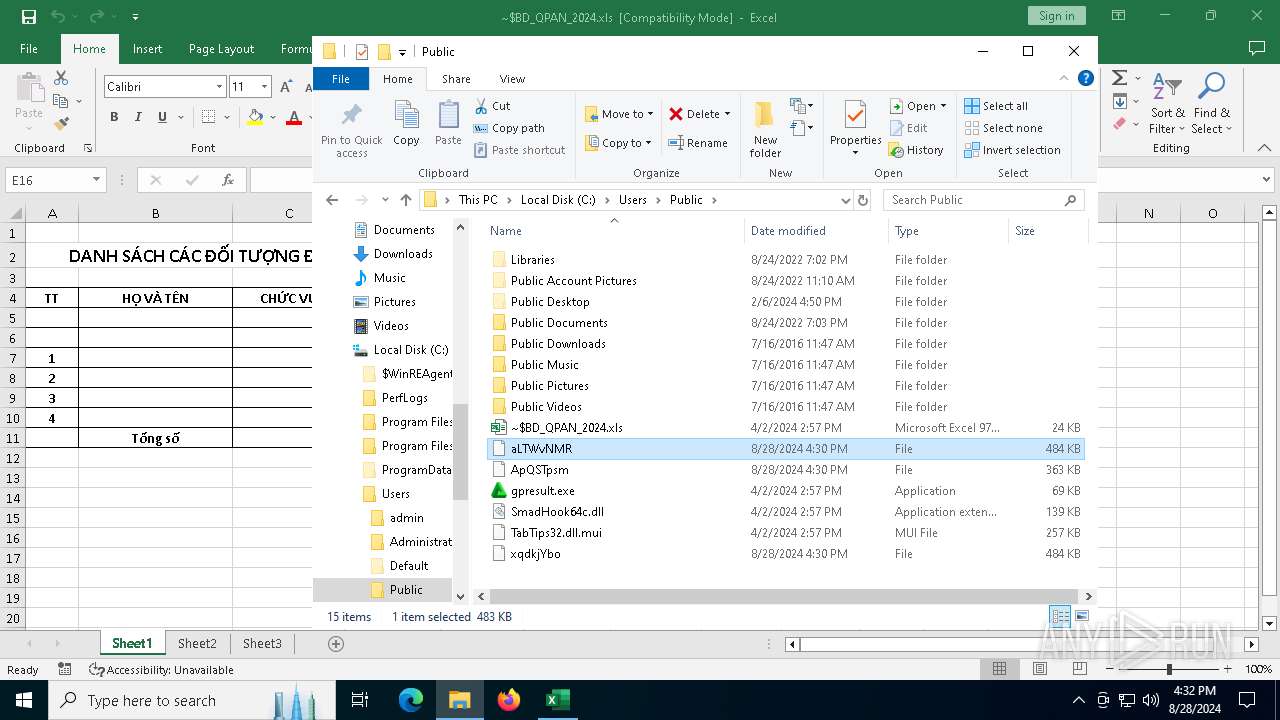
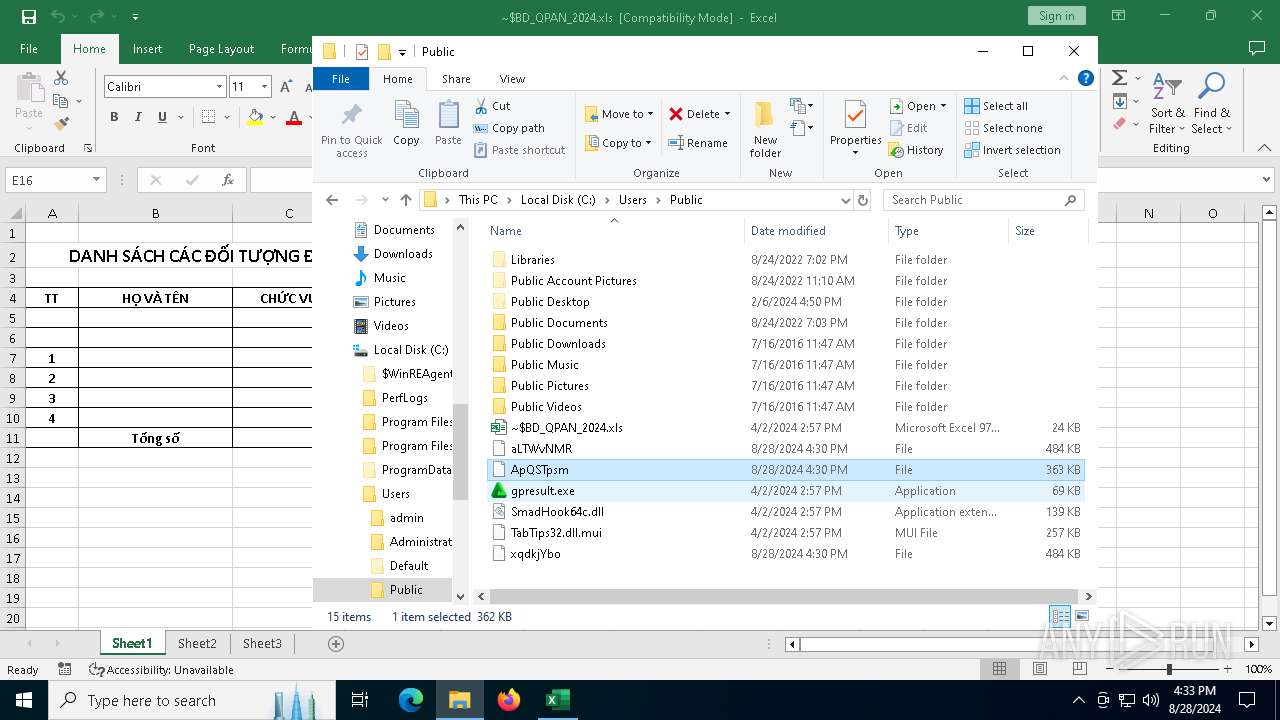
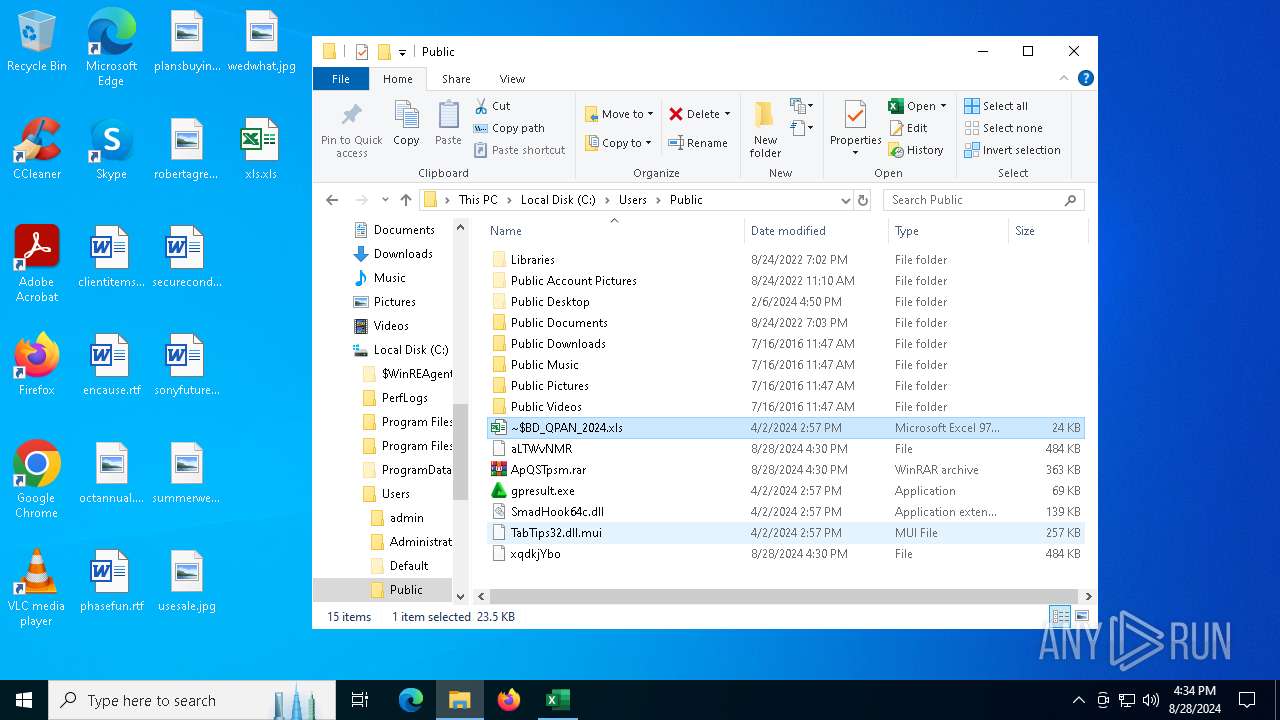
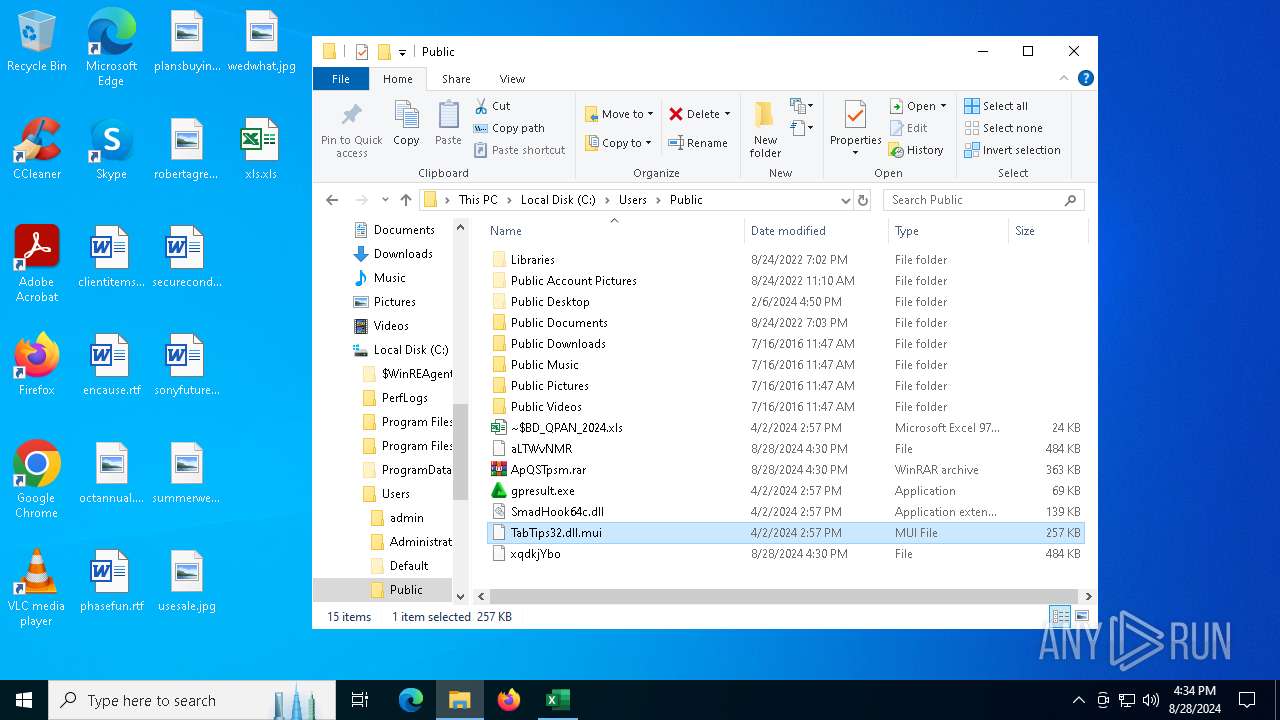
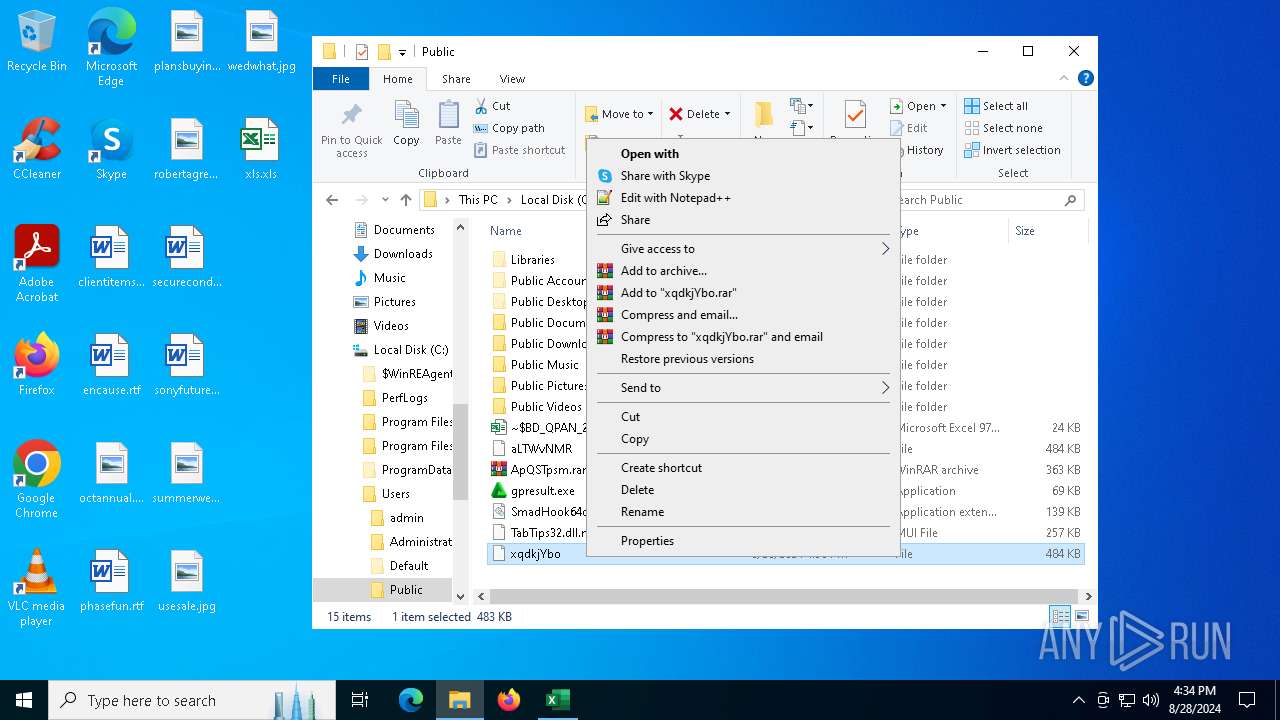
Likely accesses (executes) a file from the Public directory
- cmd.exe (PID: 7100)
- ftp.exe (PID: 4576)
- cmd.exe (PID: 1840)
- findstr.exe (PID: 5172)
- certutil.exe (PID: 2576)
- expand.exe (PID: 4084)
- cmd.exe (PID: 2492)
- gpresult.exe (PID: 4100)
- cmd.exe (PID: 4708)
- notepad++.exe (PID: 892)
- notepad++.exe (PID: 7084)
- notepad++.exe (PID: 304)
- WinRAR.exe (PID: 3104)
- EXCEL.EXE (PID: 6412)
Detected use of alternative data streams (AltDS)
- EXCEL.EXE (PID: 6836)
Starts CMD.EXE for commands execution
- ftp.exe (PID: 4576)
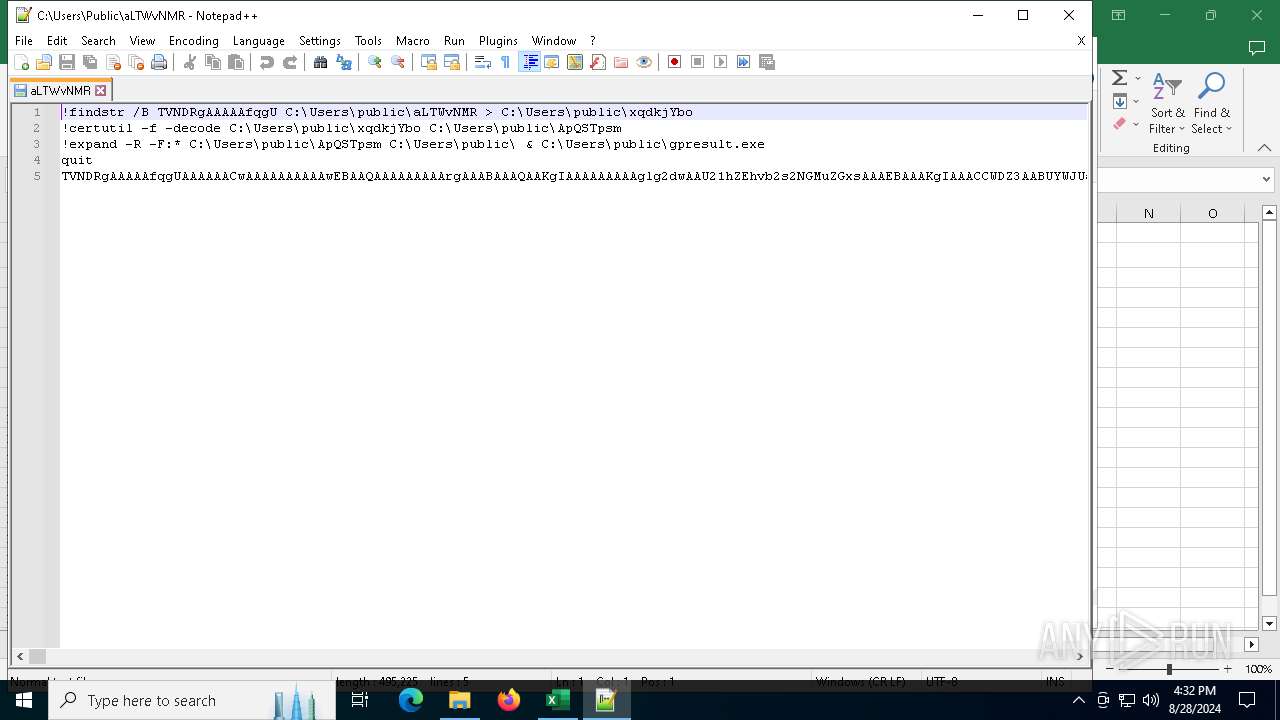
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1840)
Decoding a file from Base64 using CertUtil
- cmd.exe (PID: 4708)
Drops the executable file immediately after the start
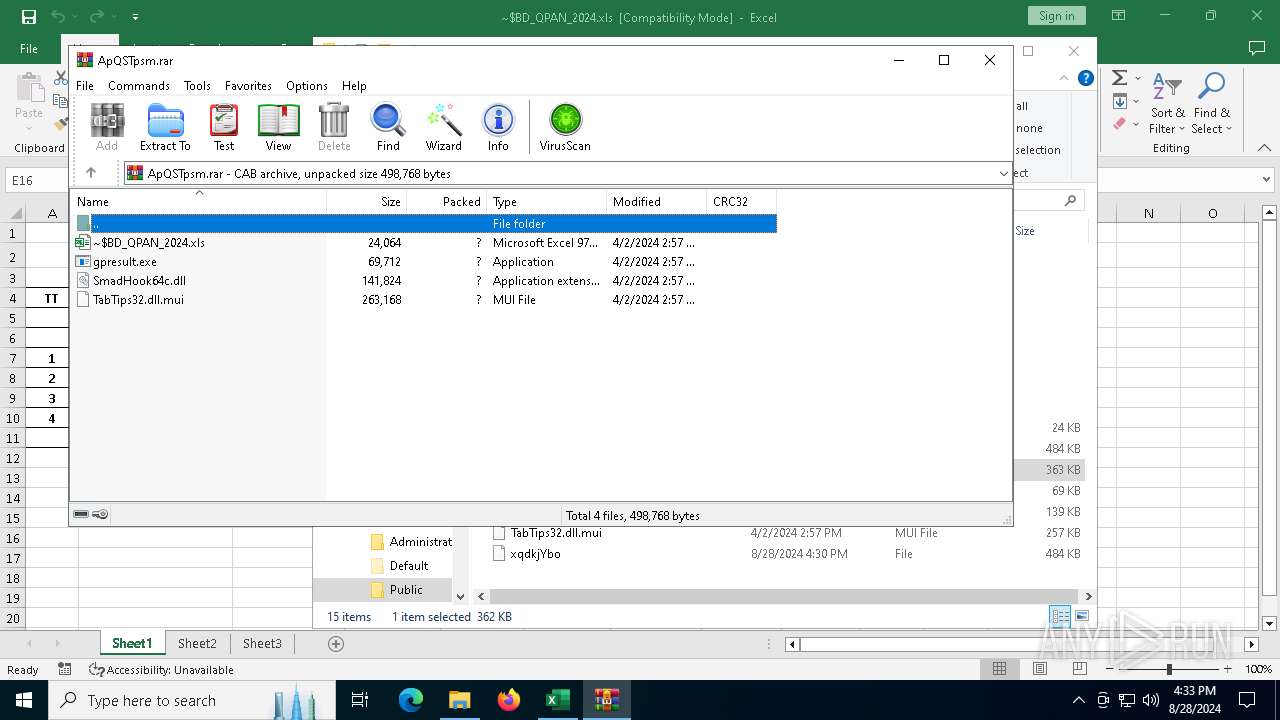
- expand.exe (PID: 4084)
Unpacks CAB file
- expand.exe (PID: 4084)
Executable content was dropped or overwritten
- expand.exe (PID: 4084)
Reads security settings of Internet Explorer
- gpresult.exe (PID: 4100)
Checks Windows Trust Settings
- gpresult.exe (PID: 4100)
INFO
Reads security settings of Internet Explorer
- splwow64.exe (PID: 2028)
Checks supported languages
- expand.exe (PID: 4084)
- gpresult.exe (PID: 4100)
Reads the machine GUID from the registry
- expand.exe (PID: 4084)
- gpresult.exe (PID: 4100)
Reads the computer name
- gpresult.exe (PID: 4100)
Checks proxy server information
- gpresult.exe (PID: 4100)
- slui.exe (PID: 1640)
Manual execution by a user
- WinRAR.exe (PID: 3104)
- notepad++.exe (PID: 7084)
- EXCEL.EXE (PID: 6412)
- notepad++.exe (PID: 304)
- notepad++.exe (PID: 892)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 1044)
Reads the software policy settings
- slui.exe (PID: 1640)
- gpresult.exe (PID: 4100)
- slui.exe (PID: 2720)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (48) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (alternate) (39.2) |
EXIF
FlashPix
| Author: | Windows User |
|---|---|
| LastModifiedBy: | Windows User |
| Software: | Microsoft Excel |
| CreateDate: | 2024:04:02 07:57:44 |
| ModifyDate: | 2024:04:02 07:58:03 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| AppVersion: | 12 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
| CompObjUserTypeLen: | 38 |
| CompObjUserType: | Microsoft Office Excel 2003 Worksheet |
Total processes
167
Monitored processes
22
Malicious processes
1
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 304 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\Public\xqdkjYbo" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Version: 7.91 Modules
| |||||||||||||||
| 892 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\Public\aLTWvNMR" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 1044 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1640 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1840 | C:\WINDOWS\system32\cmd.exe /C findstr /B TVNDRgAAAAAfqgU C:\Users\public\aLTWvNMR > C:\Users\public\xqdkjYbo | C:\Windows\System32\cmd.exe | — | ftp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2028 | C:\WINDOWS\splwow64.exe 8192 | C:\Windows\splwow64.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Print driver host for applications Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2492 | C:\WINDOWS\system32\cmd.exe /C expand -R -F:* C:\Users\public\ApQSTpsm C:\Users\public\ & C:\Users\public\gpresult.exe | C:\Windows\System32\cmd.exe | — | ftp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2576 | certutil -f -decode C:\Users\public\xqdkjYbo C:\Users\public\ApQSTpsm | C:\Windows\System32\certutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CertUtil.exe Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2720 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
23 347
Read events
22 977
Write events
335
Delete events
35
Modification events
| (PID) Process: | (6836) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 1 |
Value: 01D014000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (6836) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\EXCEL\6836 |
| Operation: | write | Name: | 0 |
Value: 0B0E10831229BEEE2AE04FAE8A39CD19573652230046CB9E9DAAFAACBEED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511B435D2120965007800630065006C002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6836) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (6836) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (6836) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (6836) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (6836) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (6836) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (6836) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (6836) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
4
Suspicious files
28
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6836 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:C0D146BA3B93175D1B731C475BBBCCCF | SHA256:1638B0A5DB681F052940D52D307D764838887F6ED8D22F3EBA7BFC0BC96DB653 | |||
| 2576 | certutil.exe | C:\Users\Public\ApQSTpsm | compressed | |
MD5:0FC5D8AD07F09925CBA62CC2DB649FC6 | SHA256:50F12BD0F8DB55785361716B8070EB59A866D3EC4468396FDE57FAA72AE96B8A | |||
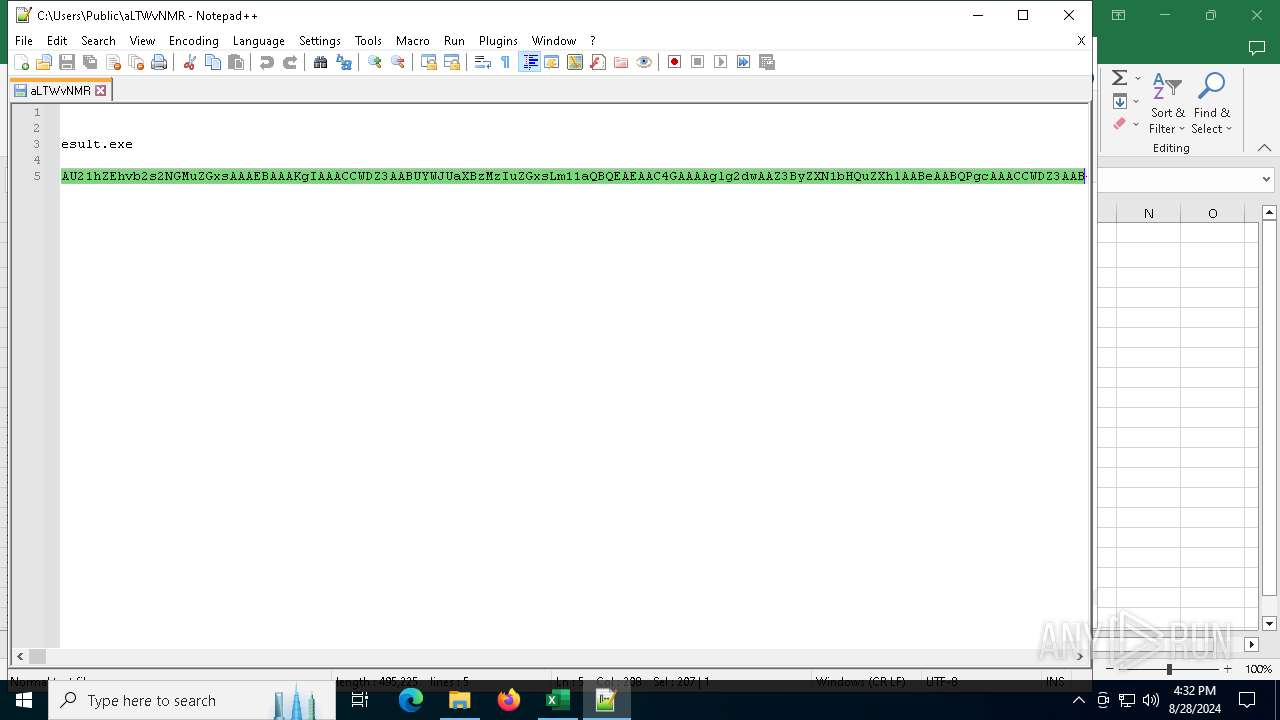
| 6836 | EXCEL.EXE | C:\Users\Public\aLTWvNMR | text | |
MD5:CBE5A16940898C76D2B7F8CCCACF3D3C | SHA256:B23D126F4EC33B5D5AA32B4D4BEB5B8E4CE3AAEC831019372FDB2DF5B85F33E4 | |||
| 6836 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:E3D6EDDE2A55818149026FE2BDEB8A2F | SHA256:652BD662D7944B4177CA4F8496D4A196CDA9B0C6C6FA7989B1BF972F42B898B6 | |||
| 6836 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\C79BA243-4B5A-4FEA-BD99-3C46FE77920E | xml | |
MD5:B0D3255F45FAF89B45B9CF57025ECCB7 | SHA256:36B813B3F0BA1593D2F2070DC6585BFC92C0419DFC8687C62B6A9F46B7308D95 | |||
| 6836 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\xls.xls.LNK | lnk | |
MD5:D751328EC9BC33C55DE81081BB96B7A4 | SHA256:EFEB0204C2C8698DAD9EF8A9936B854C9D0C6895332605C61BBEDA1D1E901D6F | |||
| 6836 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | ini | |
MD5:1298689D566F727EBE32EED73A8ADB3F | SHA256:71E0A3E979BCE581420FE19C40A325AD0B93BE56C0989D7C57A6D8861ED17221 | |||
| 4084 | expand.exe | C:\Users\Public\TabTips32.dll.mui | binary | |
MD5:D9B7163C6E90F89881F08830F0B3C5CB | SHA256:CF19EF7547419EE3BDB41465C0D73534A26C14D79C3979C8962D1C5FEB33BEC9 | |||
| 6836 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\UsageMetricsStore\FileActivityStoreV3\Excel\ASkwMDAwMDAwMC0wMDAwLTAwMDAtMDAwMC0wMDAwMDAwMDAwMDBfTnVsbAA.S | binary | |
MD5:6E06927D27158231305384E17292005E | SHA256:474204BBC77F54B1D0CAC5F15165B73EFBEDD78A7AC9DB3B804864958070390C | |||
| 4084 | expand.exe | C:\Users\Public\SmadHook64c.dll | executable | |
MD5:56D73E0861A5771D1BB3998178955BB8 | SHA256:370A231A9AF2A1E48B12E5EC0AF54B345AA0B4A1E3080280A2580D53E39AD838 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
66
DNS requests
31
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1828 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6836 | EXCEL.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7088 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7088 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
812 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6052 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6428 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6052 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6836 | EXCEL.EXE | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
6836 | EXCEL.EXE | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6836 | EXCEL.EXE | 52.111.231.13:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2120 | MoUsoCoreWorker.exe | 52.167.249.196:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
office-update.iaahnpmqyu.workers.dev |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] DNS Query to Cloudflare Worker App |
2256 | svchost.exe | Misc activity | ET INFO Observed DNS Query to Cloudflare workers.dev Domain |
4100 | gpresult.exe | Misc activity | ET INFO Observed Cloudflare workers.dev Domain in TLS SNI |
4100 | gpresult.exe | Misc activity | ET INFO Observed Cloudflare workers.dev Domain in TLS SNI |
4100 | gpresult.exe | Misc activity | ET INFO Observed Cloudflare workers.dev Domain in TLS SNI |
4100 | gpresult.exe | Misc activity | ET INFO Observed Cloudflare workers.dev Domain in TLS SNI |
4100 | gpresult.exe | Misc activity | ET INFO Observed Cloudflare workers.dev Domain in TLS SNI |
4100 | gpresult.exe | Misc activity | ET INFO Observed Cloudflare workers.dev Domain in TLS SNI |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|