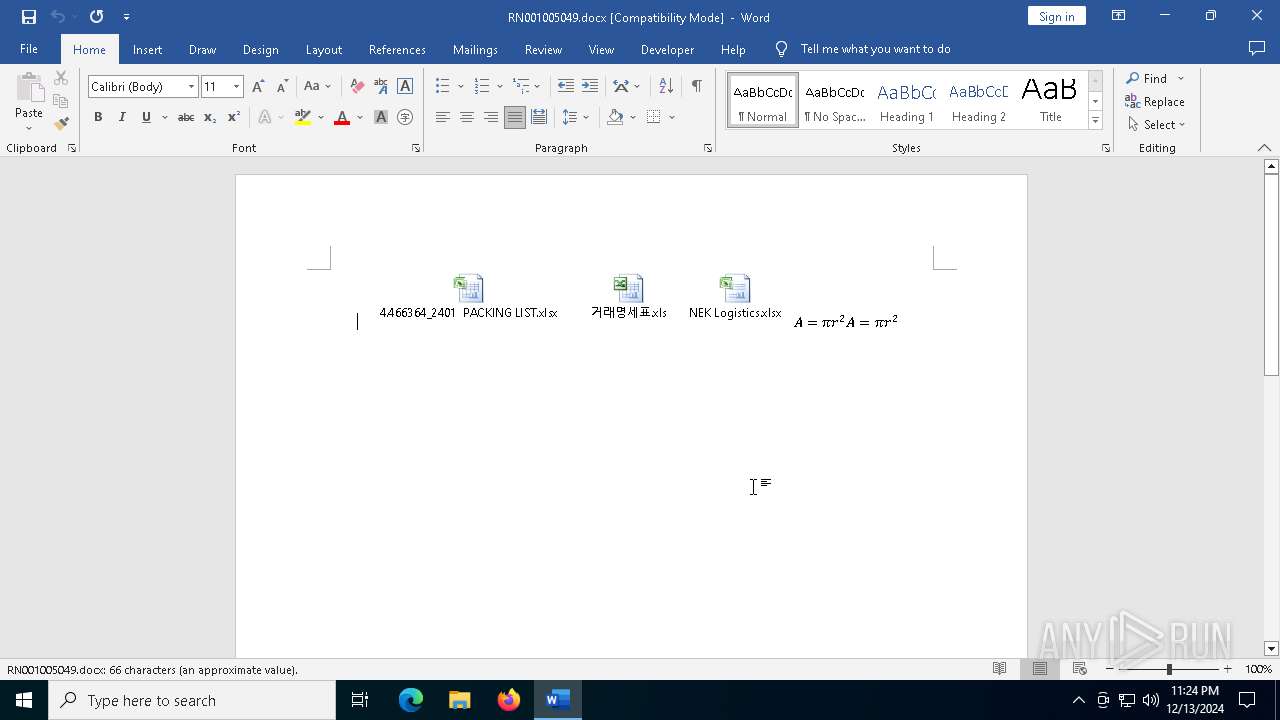
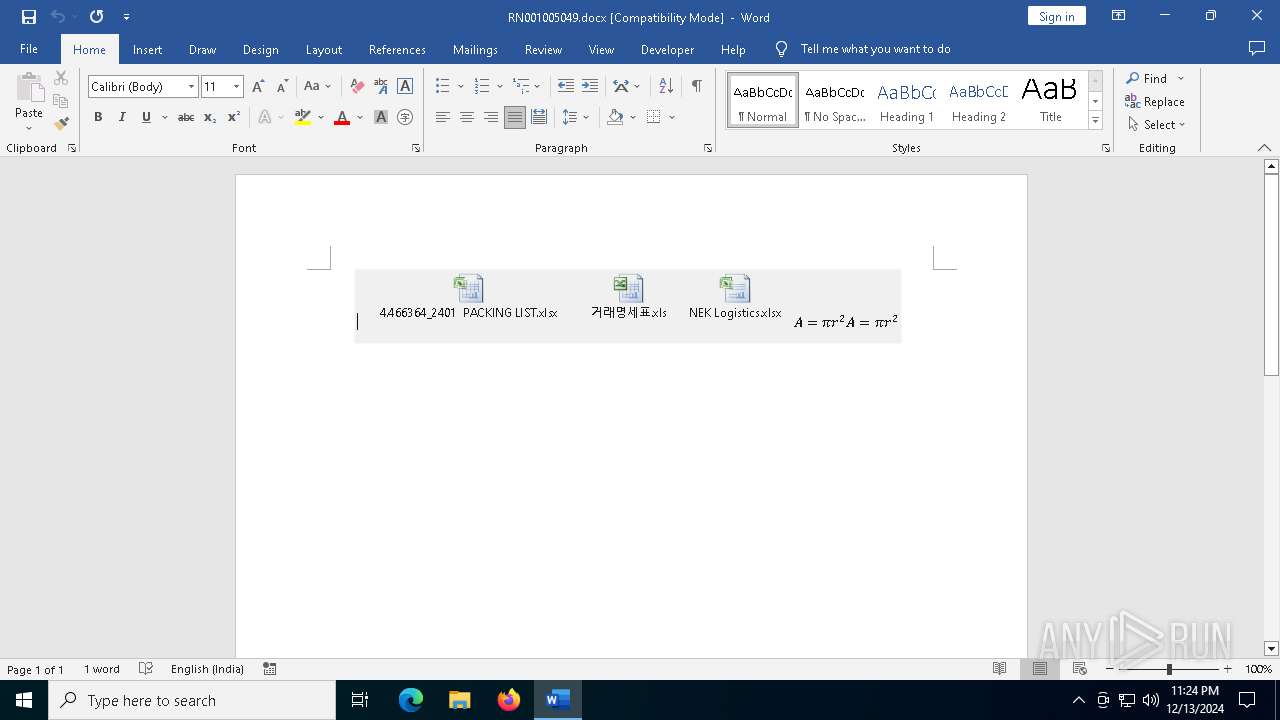
| File name: | RN001005049.docx |
| Full analysis: | https://app.any.run/tasks/ffbd30ad-f938-4aff-9ac5-4d743d3afbab |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 23:23:32 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | A5E111B3672DBC700CFC9225CFD78C5A |
| SHA1: | 754AFE5A81533F115F09DDB6F898F4B77D912DFA |
| SHA256: | BA03071326DC6D63A637E360C3846C7407D30FAF91EA38DD4D4B26056469EF4C |
| SSDEEP: | 1536:KKkedifD/2fXCP0Urf5kHvRdklYgGIJl0/DrnG4zthlyoq/UfpWT7:nx08C8UrfMRdCvKW4zthgoq/eWT7 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Connects to the server without a host name
- WINWORD.EXE (PID: 3040)
INFO
Sends debugging messages
- WINWORD.EXE (PID: 3040)
The process uses the downloaded file
- WINWORD.EXE (PID: 3040)
Drops encrypted VBS script (Microsoft Script Encoder)
- WINWORD.EXE (PID: 3040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:12:12 17:20:16 |
| ZipCRC: | 0x7fcf3406 |
| ZipCompressedSize: | 365 |
| ZipUncompressedSize: | 1460 |
| ZipFileName: | [Content_Types].xml |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | 91974 |
| Description: | - |
XML
| Keywords: | - |
|---|---|
| LastModifiedBy: | 91974 |
| RevisionNumber: | 2 |
| CreateDate: | 2024:12:12 10:40:00Z |
| ModifyDate: | 2024:12:12 10:41:00Z |
| Template: | Normal.dotm |
| TotalEditTime: | 1 minute |
| Pages: | 1 |
| Words: | 12 |
| Characters: | 71 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| Company: | Grizli777 |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 82 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 12 |
Total processes
130
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3040 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n C:\Users\admin\AppData\Local\Temp\RN001005049.docx /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 4540 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "66E1AFDF-FF8E-4922-BC7B-2429E147FA13" "9105BA00-CCF0-4E4D-990B-B348BFAA92F9" "3040" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
Total events
13 113
Read events
12 928
Write events
164
Delete events
21
Modification events
| (PID) Process: | (3040) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (3040) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\3040 |
| Operation: | write | Name: | 0 |
Value: 0B0E10D5F3333899112341A128465608832ED3230046AAD89EC9E0B6D3ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511E017D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (3040) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (3040) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (3040) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (3040) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (3040) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (3040) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (3040) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (3040) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
14
Suspicious files
137
Text files
37
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3040 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:47C8D438FCC31507C3BE6066D1A7111F | SHA256:738CAEAD3C1B3B74F4F3500D6DEA73CF3C2251F8EB2F06516EF5AA5729BA2D01 | |||
| 3040 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:BB68CC87D75A9C21FB64276AE8D37C45 | SHA256:42B98A2E9A5E4F628FF7067009891B53538ADE5D63E86FCDBD265B92481609E3 | |||
| 3040 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:02311CF2DE0E4FFFA8D90C94B4A3D5A7 | SHA256:5A2A60873F24E547C7C4A3746DBE5C9E4F822677958A7CDCDAF6F1C9D8E950A7 | |||
| 3040 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:CC3EC4A7489D02D2BED8B55FCE7AB36F | SHA256:5CB9280F5B658E42F78419572473ADC1DDE11F22114DF5D7735A8D0F972D997D | |||
| 3040 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 3040 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:66DCB47C02BD7CE40D3F1E2AC22596B2 | SHA256:80B8D62E6C7F8A79922B4CC4A83862B01DDBF627D731C99AB939A8EA18DF6CA9 | |||
| 3040 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\ResourceInfoCache\07fc2a8c43a1d1f16572d21e959a4847e306edae.temp | binary | |
MD5:53157862BB5244ED0084F4BBE4A62A21 | SHA256:09E555BE37CD1427F0B46367A6EE91F717C9CAB6070AB5C9096092FEF450505D | |||
| 3040 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\5C7112ED-2F4E-4772-83FC-DCE715E8BF8E | xml | |
MD5:24F34855AEAB5BEF969F186561257D2B | SHA256:25ED2778CE9E72DAD1C10482993C957DF61CABCF18750668482EACADB740B865 | |||
| 3040 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\87063374136EEC47E933C8519BBDFF7F | binary | |
MD5:EC8AD116B8A2C7A84562946FB93A7DAA | SHA256:34E9140675AA2C972F1B80EFA2AD4BDC13A1A4E4B4FB91321618BBFF03EAB2C8 | |||
| 3040 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\87063374136EEC47E933C8519BBDFF7F | binary | |
MD5:6946168CA4B9693D0E60A6C33D4F1429 | SHA256:3FB9D03A8B35D14CE651E8C312AAA956C3FF78761F37E621D64692A98B0622F6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
92
DNS requests
35
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6256 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6580 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6580 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3040 | WINWORD.EXE | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
3040 | WINWORD.EXE | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEHdj953KEba36aTSnQ7XHnA%3D | unknown | — | — | whitelisted |
3040 | WINWORD.EXE | HEAD | 200 | 87.106.188.164:80 | http://87.106.188.164/2322/ecc/verynicepeoplesthinkingeverythinggoodforentiretimeperfect________withgreatnicecakewhicheatsweetkissingtobefine____verygoodpeoplesaroundtheworldwithnicepeoples.doc | unknown | — | — | unknown |
3040 | WINWORD.EXE | HEAD | 200 | 87.106.188.164:80 | http://87.106.188.164/2322/ecc/verynicepeoplesthinkingeverythinggoodforentiretimeperfect________withgreatnicecakewhicheatsweetkissingtobefine____verygoodpeoplesaroundtheworldwithnicepeoples.doc | unknown | — | — | unknown |
3040 | WINWORD.EXE | GET | 200 | 87.106.188.164:80 | http://87.106.188.164/2322/ecc/verynicepeoplesthinkingeverythinggoodforentiretimeperfect________withgreatnicecakewhicheatsweetkissingtobefine____verygoodpeoplesaroundtheworldwithnicepeoples.doc | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
132 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
132 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
— | — | 104.126.37.171:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3040 | WINWORD.EXE | Potentially Bad Traffic | ET INFO Dotted Quad Host DOC Request |
3040 | WINWORD.EXE | Potentially Bad Traffic | ET INFO Dotted Quad Host DOC Request |
3040 | WINWORD.EXE | Potentially Bad Traffic | ET HUNTING Microsoft Office User-Agent Requesting A Doc File |
3040 | WINWORD.EXE | Potentially Bad Traffic | ET INFO Dotted Quad Host DOC Request |
3040 | WINWORD.EXE | Misc activity | ET USER_AGENTS Microsoft Office Existence Discovery User-Agent |
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|