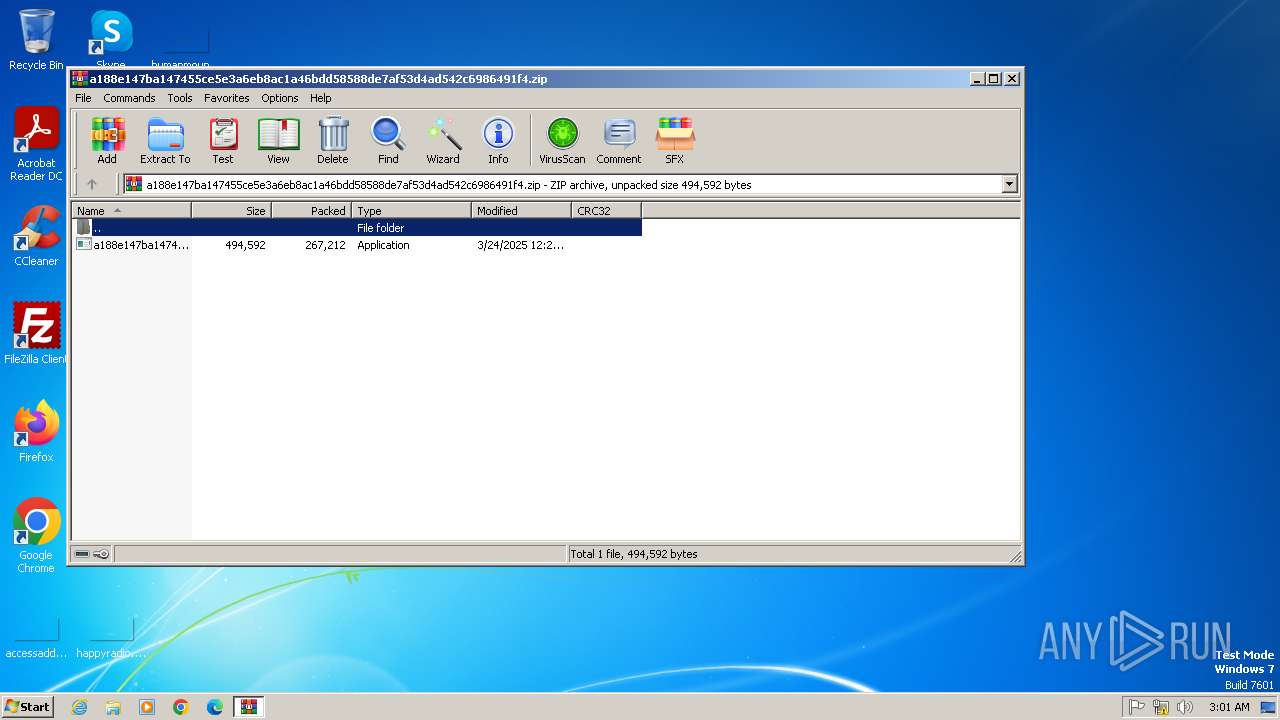
| File name: | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.zip |
| Full analysis: | https://app.any.run/tasks/d24fa274-6fa9-47f5-80f4-9b11de87b0ab |
| Verdict: | Malicious activity |
| Analysis date: | March 25, 2025, 03:01:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
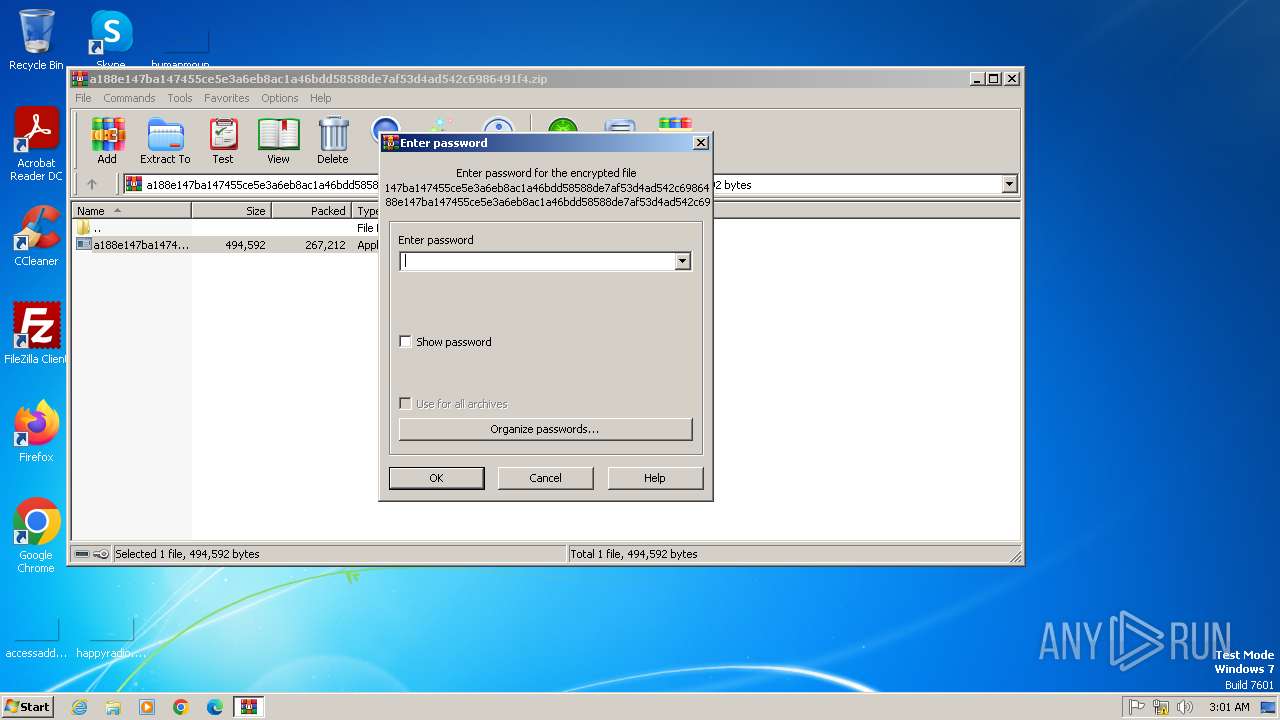
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | AEE3997DA91D1FB190EA04385516A83E |
| SHA1: | F92FCAFFEB19EE18B6B07E5923456F2910C025D7 |
| SHA256: | B9F5694BF18F1DD1EB951CA155BF594CA389EC54675A823C25DC9E6F5D6B2E0B |
| SSDEEP: | 12288:+iEzjLRRWtGEOlutfMWCX/bBdtrWOZv7fHtBY1S0:+i6LRRWtHgutkWCPbBdtrWizfNG1S0 |
MALICIOUS
Changes the autorun value in the registry
- a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe (PID: 2000)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 1760)
Deletes shadow copies
- cmd.exe (PID: 1484)
Using BCDEDIT.EXE to modify recovery options
- cmd.exe (PID: 1484)
SUSPICIOUS
Executable content was dropped or overwritten
- a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe (PID: 2000)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2060)
- a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe (PID: 2000)
The process executes via Task Scheduler
- a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe (PID: 2564)
Starts CMD.EXE for commands execution
- a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe (PID: 2000)
Reads the Internet Settings
- a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe (PID: 2000)
- WMIC.exe (PID: 1596)
Checks for external IP
- a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe (PID: 2000)
There is functionality for capture public ip (YARA)
- a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe (PID: 2000)
Potential Corporate Privacy Violation
- a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe (PID: 2000)
Connects to the server without a host name
- a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe (PID: 2000)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2060)
Reads the computer name
- a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe (PID: 2000)
Reads the machine GUID from the registry
- a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe (PID: 2000)
Checks supported languages
- a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe (PID: 2000)
- a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe (PID: 2564)
Create files in a temporary directory
- a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe (PID: 2000)
Autorun file from Task Scheduler
- cmd.exe (PID: 1760)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:03:24 00:27:34 |
| ZipCRC: | 0xe62883a2 |
| ZipCompressedSize: | 267212 |
| ZipUncompressedSize: | 494592 |
| ZipFileName: | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe |
Total processes
46
Monitored processes
12
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | wbadmin DELETE SYSTEMSTATEBACKUP | C:\Windows\System32\wbadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Command Line Interface for Microsoft® BLB Backup Exit code: 4294967293 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1472 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1484 | "C:\Windows\System32\cmd.exe" /C wmic SHADOWCOPY DELETE & wbadmin DELETE SYSTEMSTATEBACKUP & bcdedit.exe / set{ default } bootstatuspolicy ignoreallfailures & bcdedit.exe / set{ default } recoveryenabled No | C:\Windows\System32\cmd.exe | — | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1596 | wmic SHADOWCOPY DELETE | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 2147749908 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1760 | "C:\Windows\System32\cmd.exe" /C schtasks /Create /SC MINUTE /TN "Mouse Application" /TR "C:\Users\admin\AppData\Local\Temp\Rar$EXb2060.483\a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe" /f | C:\Windows\System32\cmd.exe | — | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1844 | bcdedit.exe / set{ default } bootstatuspolicy ignoreallfailures | C:\Windows\System32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Boot Configuration Data Editor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2000 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2060.483\a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2060.483\a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2060 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2212 | schtasks /Create /SC MINUTE /TN "Mouse Application" /TR "C:\Users\admin\AppData\Local\Temp\Rar$EXb2060.483\a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe" /f | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2304 | bcdedit.exe / set{ default } recoveryenabled No | C:\Windows\System32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Boot Configuration Data Editor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
3 101
Read events
3 060
Write events
41
Delete events
0
Modification events
| (PID) Process: | (2060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2060) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.zip | |||
| (PID) Process: | (2060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
2
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2060.483\a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | executable | |
MD5:3265B2B0AFC6D2AD0BDD55AF8EDB9B37 | SHA256:A188E147BA147455CE5E3A6EB8AC1A46BDD58588DE7AF53D4AD542C6986491F4 | |||
| 2000 | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2060.483\tor-lib.dll | executable | |
MD5:DC7E564809D6C2A2F3457C3C9B91F22B | SHA256:9969C1E4CF32D1FE6140D6FABF63B6B093A6C6FF7045A187B14175D46CFB74A0 | |||
| 2000 | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2060.483\a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.log | text | |
MD5:25346E0B5CE73319D079051CC0077305 | SHA256:72C3334F9A7C8CF7E8F12FF2CF1806CAC16614892E5699C016A85E1FD25056AF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
11
DNS requests
2
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2000 | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | GET | — | 204.13.164.118:80 | http://204.13.164.118/tor/status-vote/current/consensus | unknown | — | — | unknown |
2000 | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | GET | — | 193.23.244.244:80 | http://193.23.244.244/tor/server/fp/752bc361622e9bc2dbf395235431a2befbe79135 | unknown | — | — | unknown |
2000 | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | GET | — | 216.218.219.41:80 | http://216.218.219.41/tor/server/fp/40e7d6ce5085e4cdda31d51a29d1457eb53f12ad | unknown | — | — | unknown |
2000 | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | GET | 200 | 172.67.74.152:80 | http://api.ipify.org/ | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
2000 | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | 172.67.74.152:80 | api.ipify.org | CLOUDFLARENET | US | shared |
2000 | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | 204.13.164.118:80 | — | RISEUP | US | unknown |
2000 | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | 178.254.45.235:443 | — | EVANZO e-commerce GmbH | DE | unknown |
2000 | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | 193.23.244.244:80 | — | Chaos Computer Club e.V. | DE | unknown |
2000 | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | 204.8.96.102:443 | — | — | US | unknown |
2000 | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | 216.218.219.41:80 | — | HURRICANE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
api.ipify.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2000 | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External IP Lookup by HTTP (api .ipify .org) |
2000 | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup api.ipify.org |
2000 | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |
2000 | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 414 |
1080 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
2000 | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | Potential Corporate Privacy Violation | ET INFO TOR Consensus Data Requested |
2000 | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 268 |
2000 | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | Potential Corporate Privacy Violation | ET P2P Tor Get Server Request |
2000 | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 337 |
2000 | a188e147ba147455ce5e3a6eb8ac1a46bdd58588de7af53d4ad542c6986491f4.exe | Misc Attack | ET TOR Known Tor Exit Node Traffic group 77 |