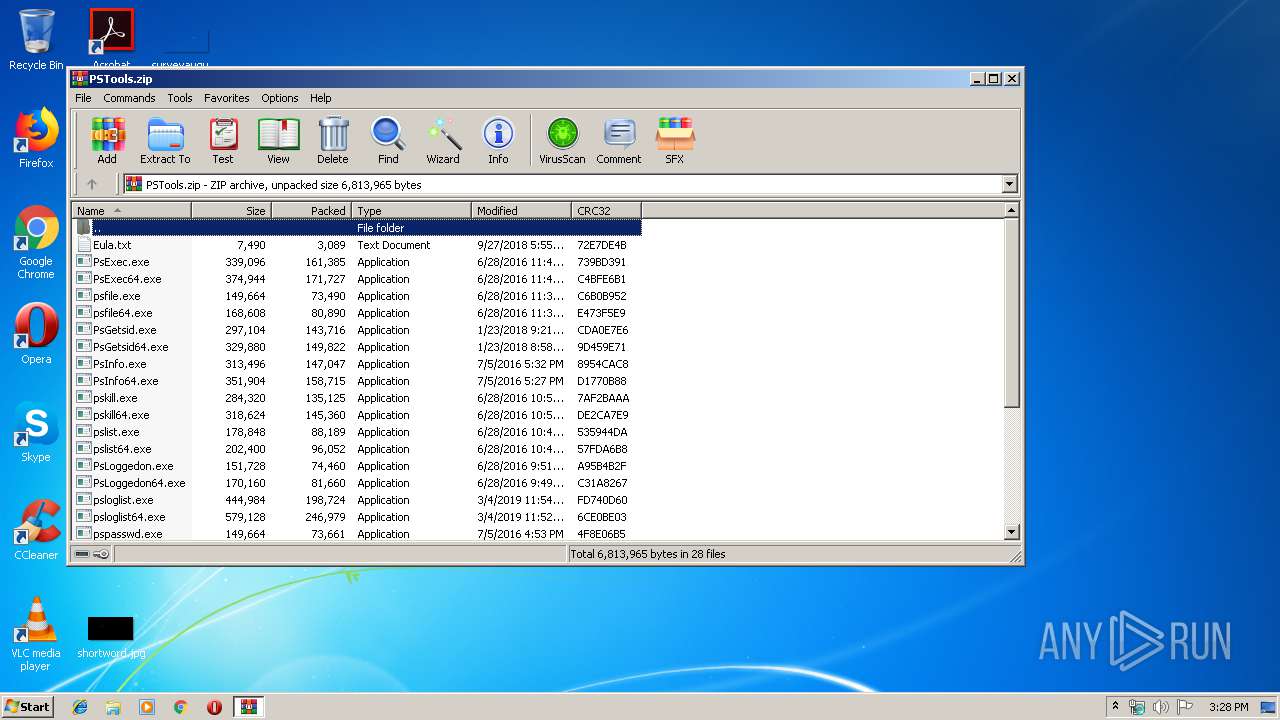
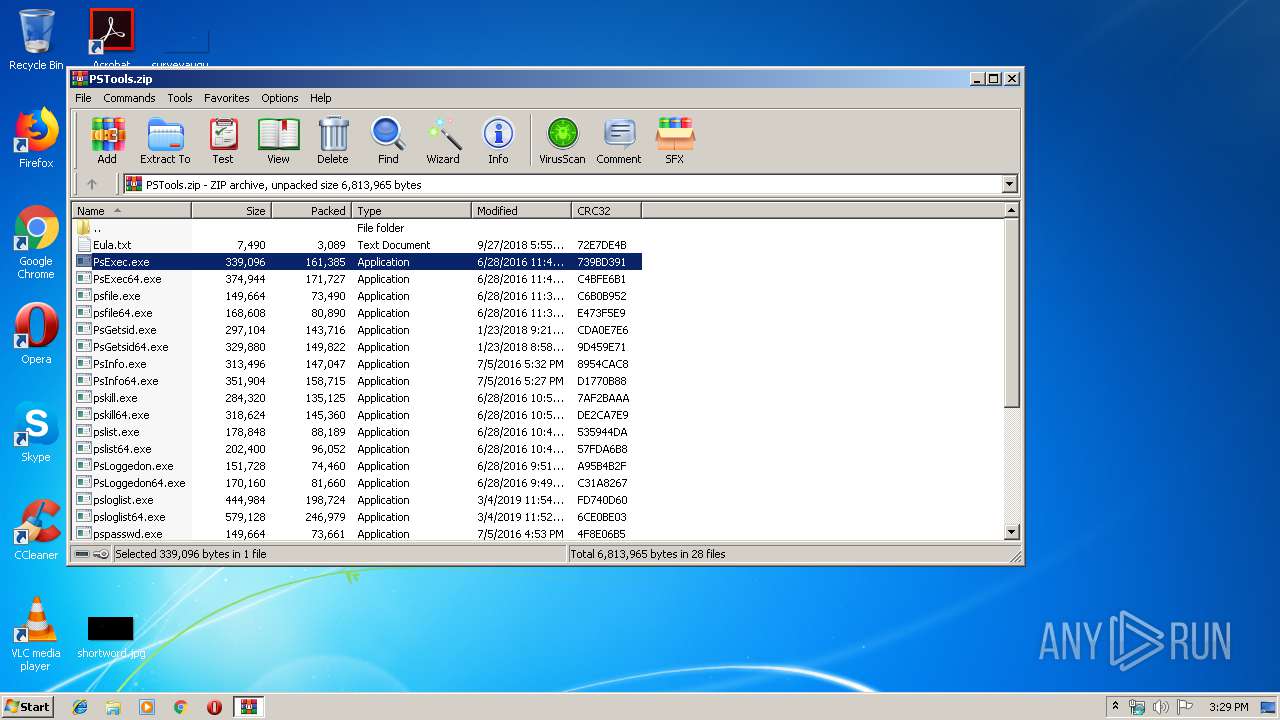
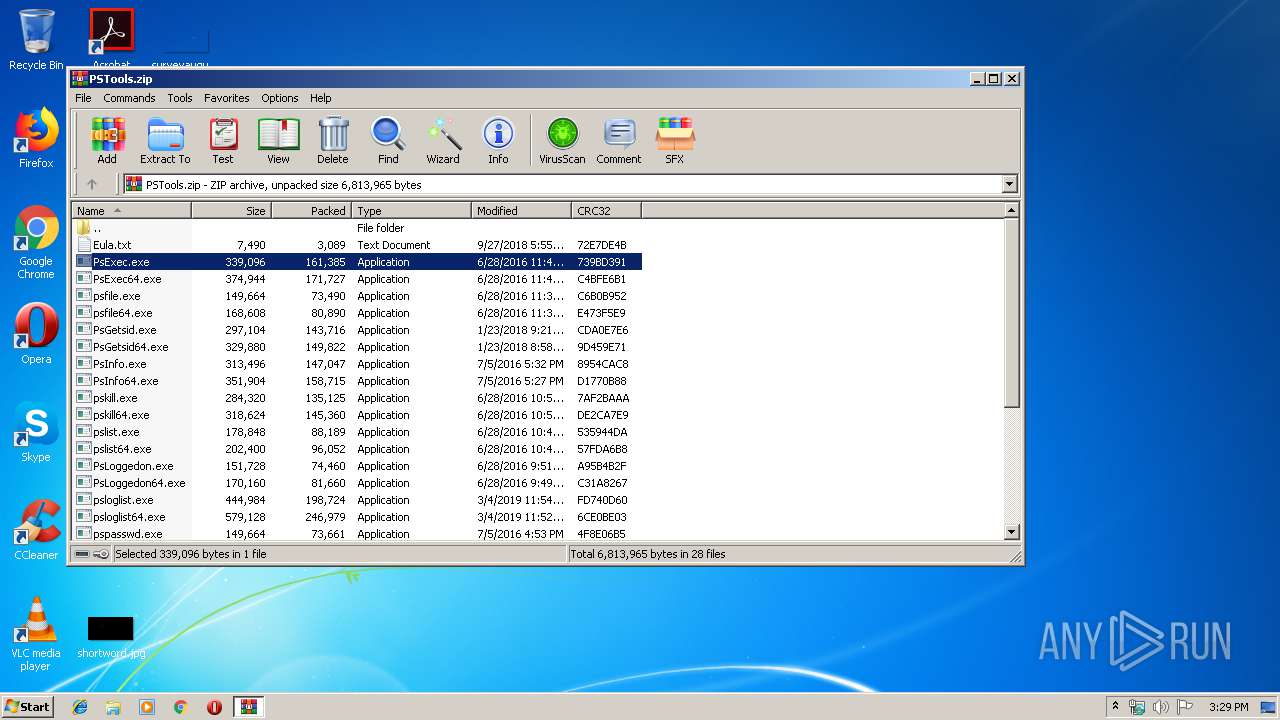
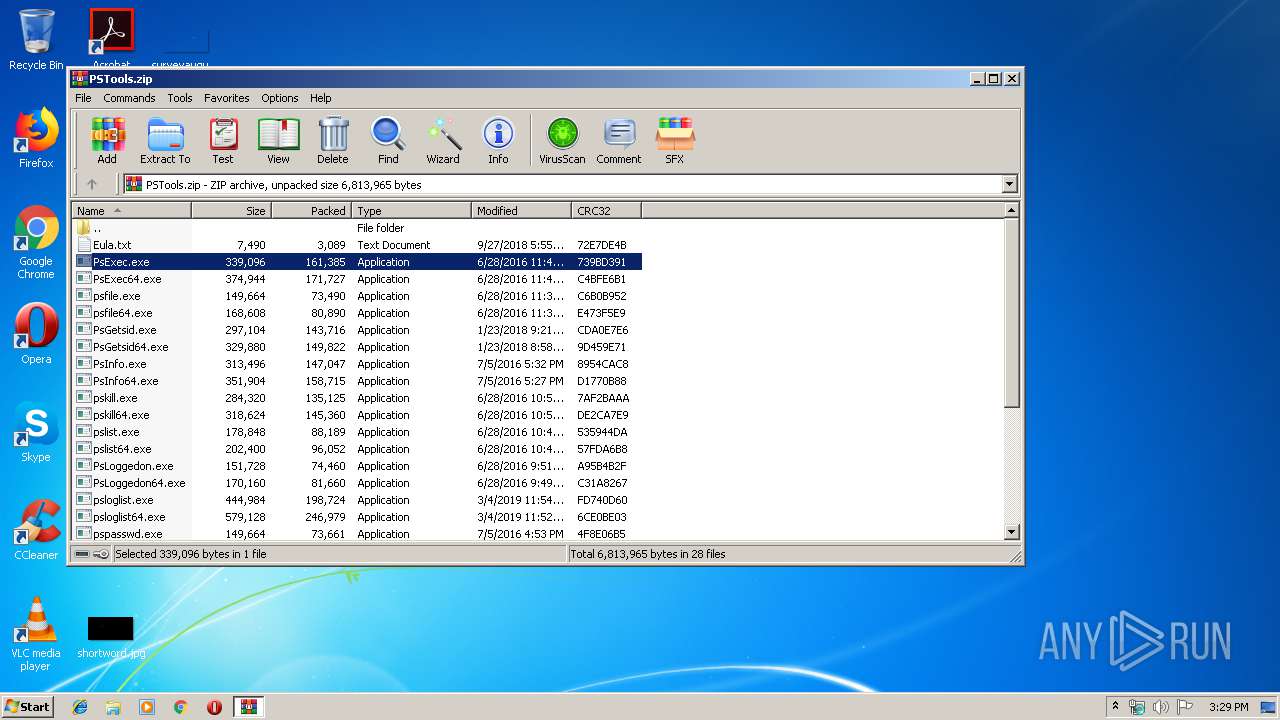
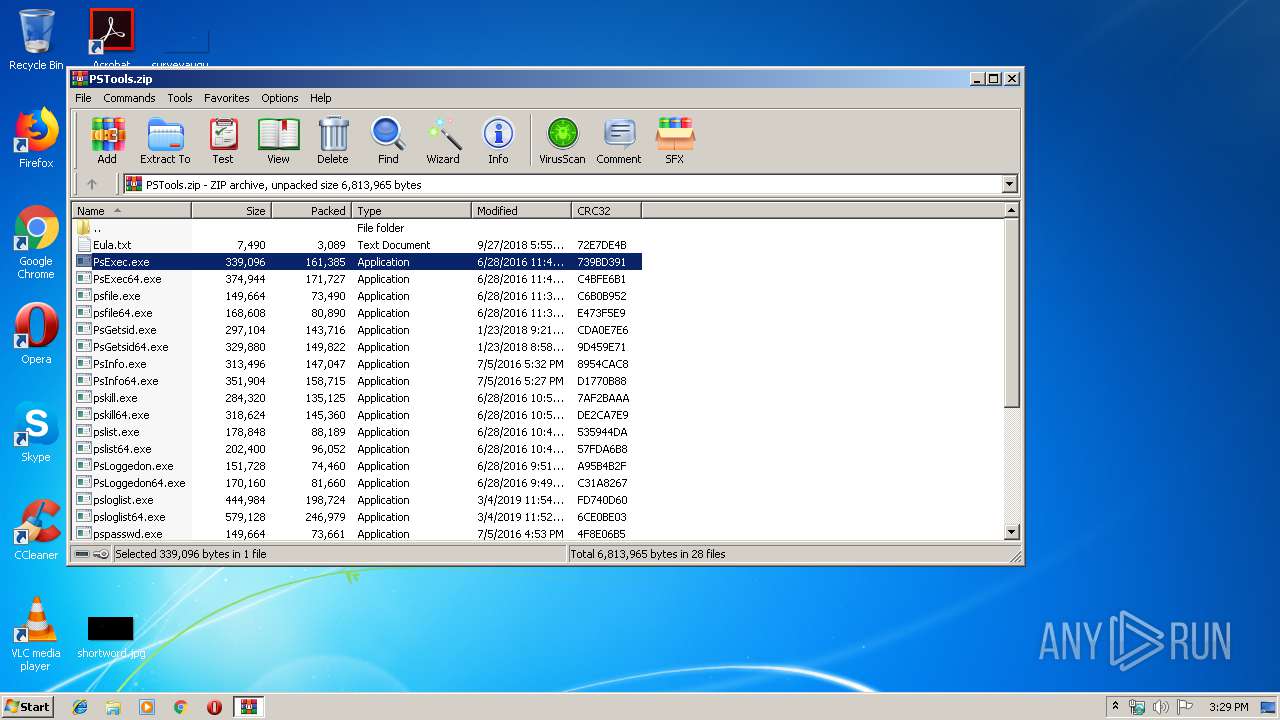
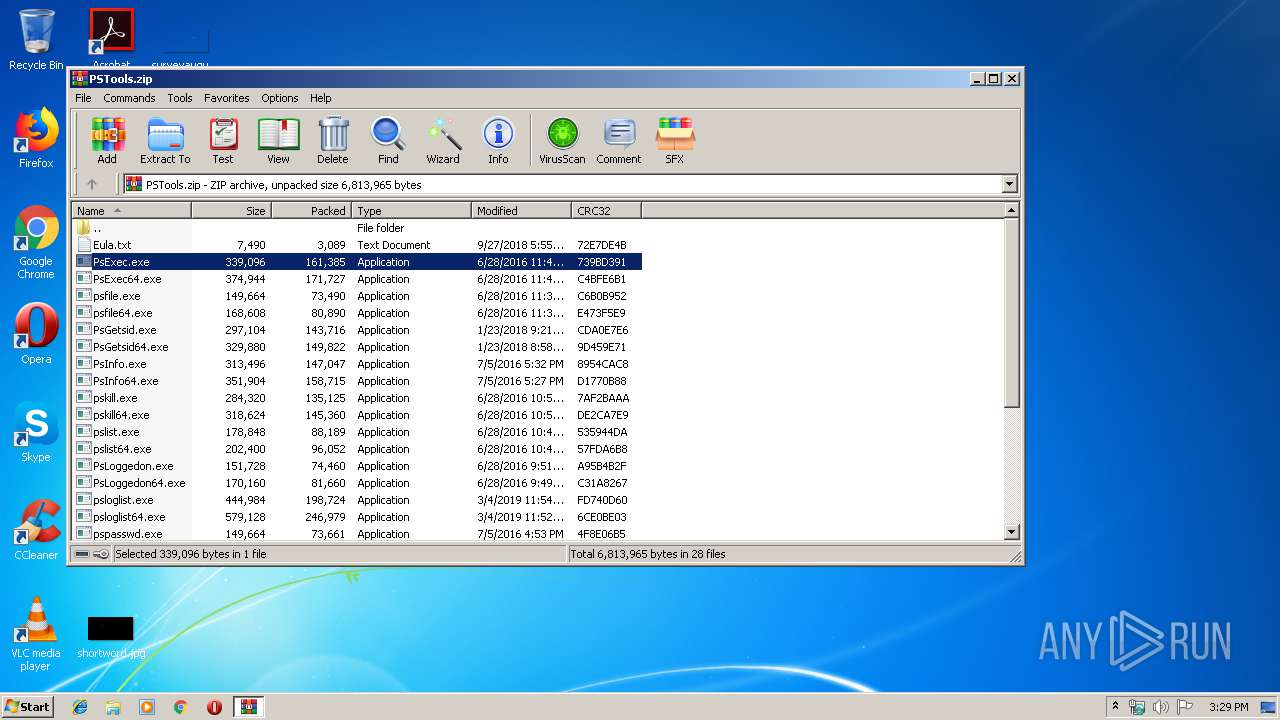
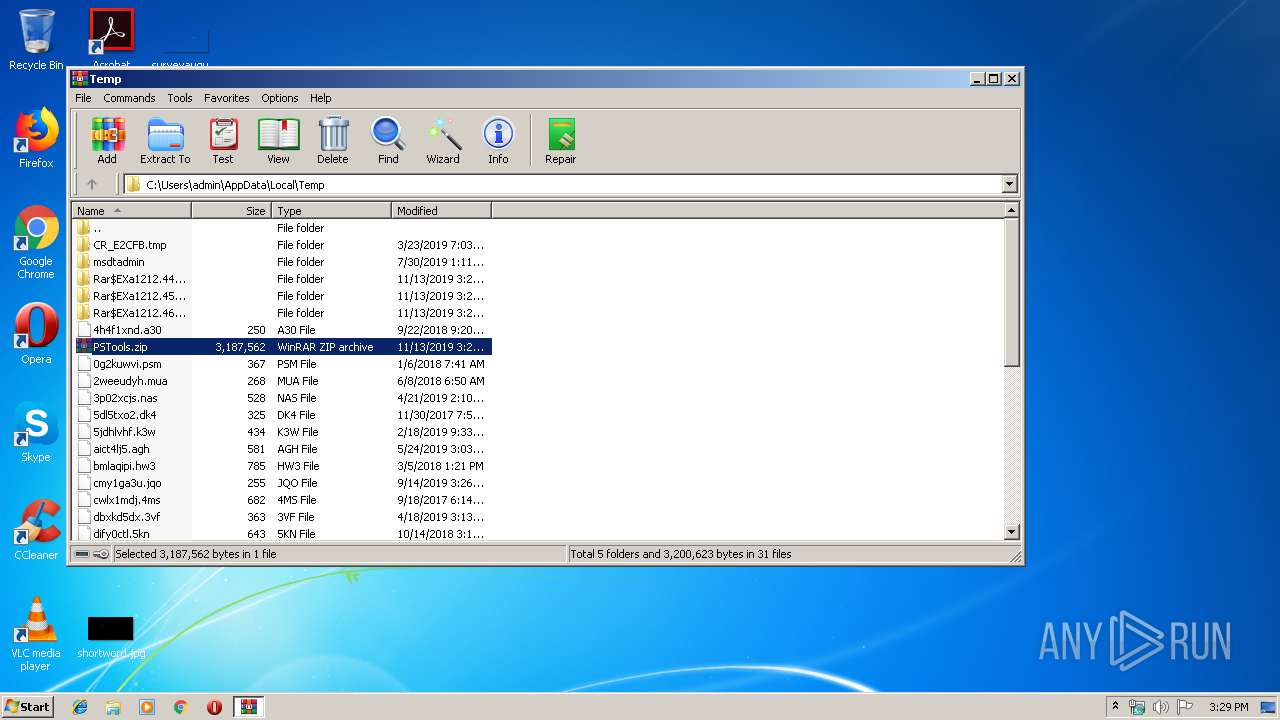
| File name: | PSTools.zip |
| Full analysis: | https://app.any.run/tasks/8e143b36-bbdd-454d-a469-5c51aa5a2d7b |
| Verdict: | Malicious activity |
| Analysis date: | November 13, 2019, 15:28:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 970DD74FCE75C85772DC9451AF8B58AB |
| SHA1: | AD067399BD4A553DA391D8059B95B1BD156FBB0B |
| SHA256: | B9F404D4C7B6BF3A37746C66BCD014E75859D2FCF887B1DB527EC3ED2CCDEB30 |
| SSDEEP: | 98304:2NEY1OfoW3IhXEb1pObL1eD7nn0I8dEoADgh:2KYUgW3IhXEbGu7nN8dEe |
MALICIOUS
Application was dropped or rewritten from another process
- PsExec.exe (PID: 1248)
- PsExec.exe (PID: 2576)
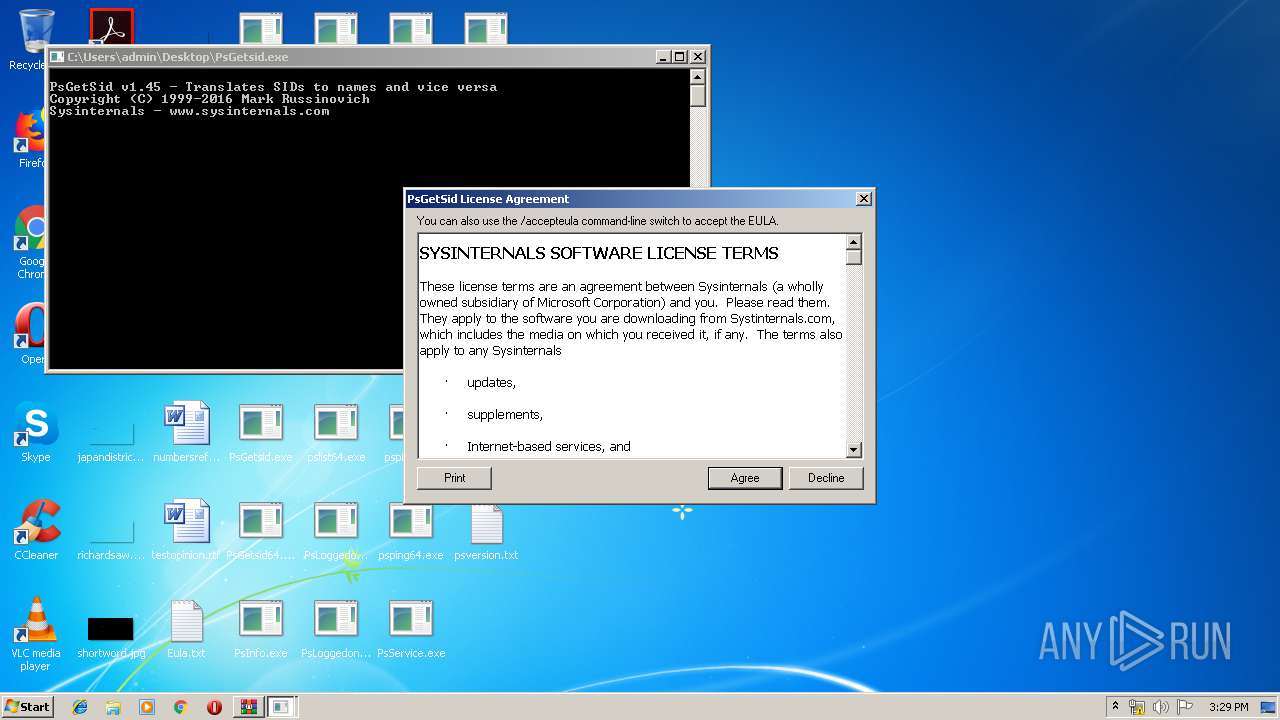
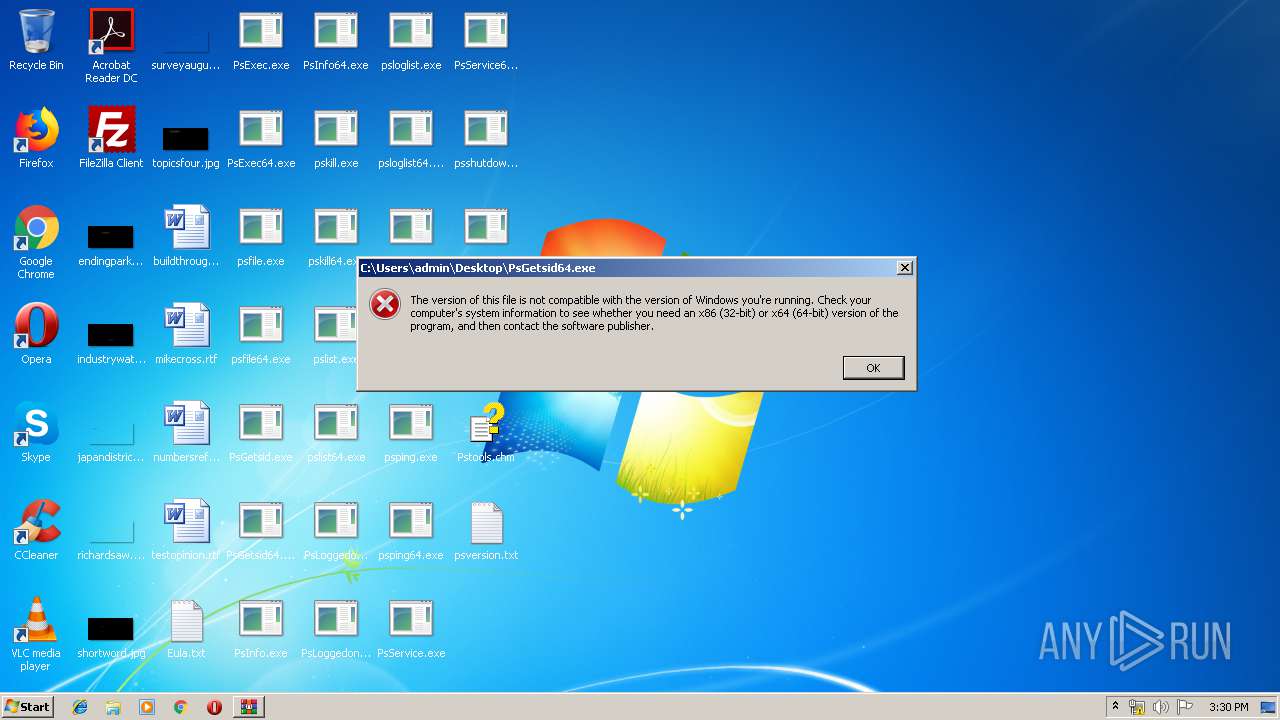
- PsGetsid.exe (PID: 2708)
- PsExec.exe (PID: 1796)
- PsGetsid.exe (PID: 3992)
- PsGetsid.exe (PID: 3136)
- PsGetsid.exe (PID: 2524)
- PsGetsid.exe (PID: 2504)
- PsGetsid.exe (PID: 2752)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1212)
INFO
Manual execution by user
- PsGetsid.exe (PID: 2708)
- PsGetsid.exe (PID: 3136)
- PsGetsid.exe (PID: 3992)
- PsGetsid.exe (PID: 2524)
- PsGetsid.exe (PID: 2752)
- PsGetsid.exe (PID: 2504)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2006:12:04 17:53:09 |
| ZipCRC: | 0xeecdb72d |
| ZipCompressedSize: | 97181 |
| ZipUncompressedSize: | 207664 |
| ZipFileName: | psshutdown.exe |
Total processes
54
Monitored processes
10
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1212 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\PSTools.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
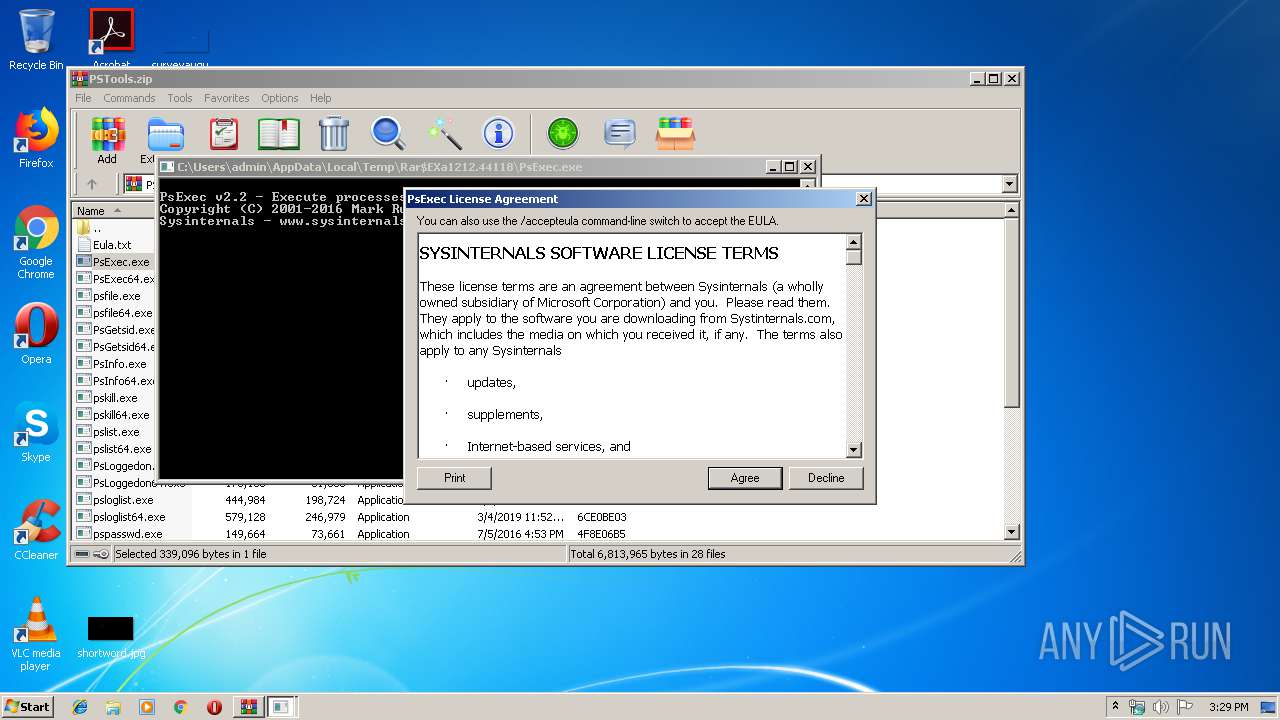
| 1248 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1212.44118\PsExec.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1212.44118\PsExec.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Execute processes remotely Exit code: 4294967295 Version: 2.2 Modules
| |||||||||||||||
| 1796 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1212.46630\PsExec.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1212.46630\PsExec.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Execute processes remotely Exit code: 4294967295 Version: 2.2 Modules
| |||||||||||||||
| 2504 | "C:\Users\admin\Desktop\PsGetsid.exe" | C:\Users\admin\Desktop\PsGetsid.exe | — | explorer.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Translates SIDs to names and vice versa Exit code: 0 Version: 1.45 Modules
| |||||||||||||||
| 2524 | "C:\Users\admin\Desktop\PsGetsid.exe" | C:\Users\admin\Desktop\PsGetsid.exe | — | explorer.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Translates SIDs to names and vice versa Exit code: 0 Version: 1.45 Modules
| |||||||||||||||
| 2576 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1212.45166\PsExec.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1212.45166\PsExec.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Execute processes remotely Exit code: 4294967295 Version: 2.2 Modules
| |||||||||||||||
| 2708 | "C:\Users\admin\Desktop\PsGetsid.exe" | C:\Users\admin\Desktop\PsGetsid.exe | — | explorer.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Translates SIDs to names and vice versa Exit code: 0 Version: 1.45 Modules
| |||||||||||||||
| 2752 | "C:\Users\admin\Desktop\PsGetsid.exe" | C:\Users\admin\Desktop\PsGetsid.exe | — | explorer.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Translates SIDs to names and vice versa Exit code: 0 Version: 1.45 Modules
| |||||||||||||||
| 3136 | "C:\Users\admin\Desktop\PsGetsid.exe" | C:\Users\admin\Desktop\PsGetsid.exe | — | explorer.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Translates SIDs to names and vice versa Exit code: 0 Version: 1.45 Modules
| |||||||||||||||
| 3992 | "C:\Users\admin\Desktop\PsGetsid.exe" | C:\Users\admin\Desktop\PsGetsid.exe | — | explorer.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Translates SIDs to names and vice versa Exit code: 0 Version: 1.45 Modules
| |||||||||||||||
Total events
503
Read events
473
Write events
30
Delete events
0
Modification events
| (PID) Process: | (1212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1212) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\PSTools.zip | |||
| (PID) Process: | (1212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
100
Suspicious files
0
Text files
8
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1212.44118\psshutdown.exe | executable | |
MD5:6AA0305AF2C055AC6C94B5D24F6CEC35 | SHA256:66885C2B1773A6D02C3937E67B94B786FC64AF17A7E8BAD050BE5149092A0117 | |||
| 1212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1212.44118\psfile64.exe | executable | |
MD5:E52AC781C403DABE22DFA16AEF8491BE | SHA256:033B81744E0BD4219A4D698894B8403BB67B525C96049CBFEF34677D4D6FC85C | |||
| 1212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1212.44118\PsExec.exe | executable | |
MD5:27304B246C7D5B4E149124D5F93C5B01 | SHA256:3337E3875B05E0BFBA69AB926532E3F179E8CFBF162EBB60CE58A0281437A7EF | |||
| 1212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1212.44118\pskill.exe | executable | |
MD5:8C1772C2D124E80526642BE3FBD2E8F3 | SHA256:546EC58D0134EA64611E12D7E3A867793E8CB6145AC18745349408A60FC2FABE | |||
| 1212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1212.44118\pslist64.exe | executable | |
MD5:A285919B3737ED691E1D029E36213050 | SHA256:E6901E8423DA3E54BAB25F7C90F60D3979BFA5BB61BCC46059662736253B8C72 | |||
| 1212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1212.44118\psfile.exe | executable | |
MD5:201058594991D79D5D8891DBBEEEE3C6 | SHA256:9D45453285FF3B4A41056317C96866D06481751307D703E3355B18D5EEB092AD | |||
| 1212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1212.44118\PsExec64.exe | executable | |
MD5:9321C107D1F7E336CDA550A2BF049108 | SHA256:AD6B98C01EE849874E4B4502C3D7853196F6044240D3271E4AB3FC6E3C08E9A4 | |||
| 1212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1212.44118\pskill64.exe | executable | |
MD5:26EA3E520CB396587D32A7A01AA564BD | SHA256:75899C5ACE600406503A937EF550AB0BBD0F6E0188B9E93E206BEB1DFC79BB81 | |||
| 1212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1212.44118\pslist.exe | executable | |
MD5:2C23D6223D4AFF81AC137B6989BCE05C | SHA256:9927831E111AC61FD7645BF7EFA1787DB1A3E85B6F64A274CA04B213DC27FD08 | |||
| 1212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1212.44118\pssuspend64.exe | executable | |
MD5:FBE9E863C6E46F75BFABA674E3BA0CDA | SHA256:E93DDD9ED564B7F6532CD5B94CDCE73067D8EBAD8A5CE9373A6F839C7050780F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report