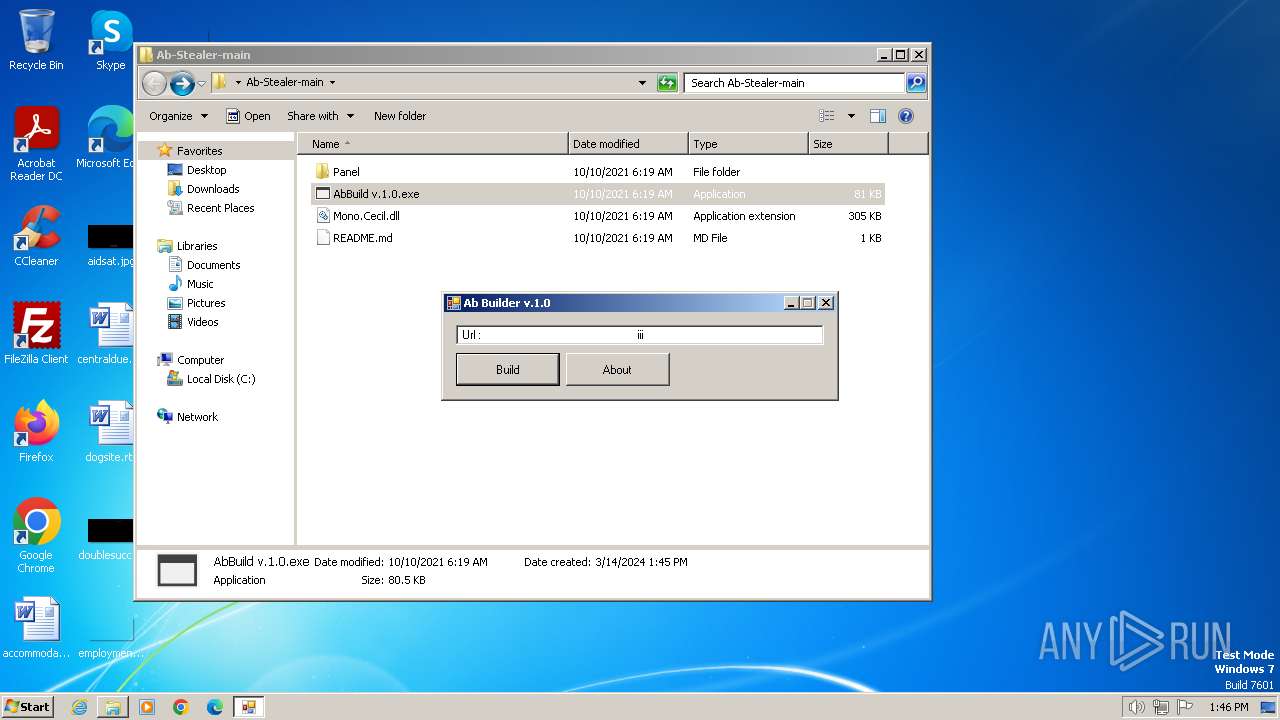
| File name: | AbStealer Builder.7z |
| Full analysis: | https://app.any.run/tasks/745b90ea-9585-4d5b-8d1d-efbd4b9a91d5 |
| Verdict: | Malicious activity |
| Analysis date: | March 14, 2024, 13:44:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | EDD911EB6F5A540B93A1FBC3FA5972BD |
| SHA1: | 722802EBB60ACF876D723E10423A432BC1A2D216 |
| SHA256: | B9D5B9E6591F359BAC9F4983A4FEEB555D3D59F94BA22F6FA5874424EF6A4790 |
| SSDEEP: | 6144:P2KxSQMTRgte0IuKZb9w7kpdbGwuxEH9480OXd3iAG8QqKm7vSgvYA:P9iete5wA3Fuxsn0OZJYmWOR |
MALICIOUS
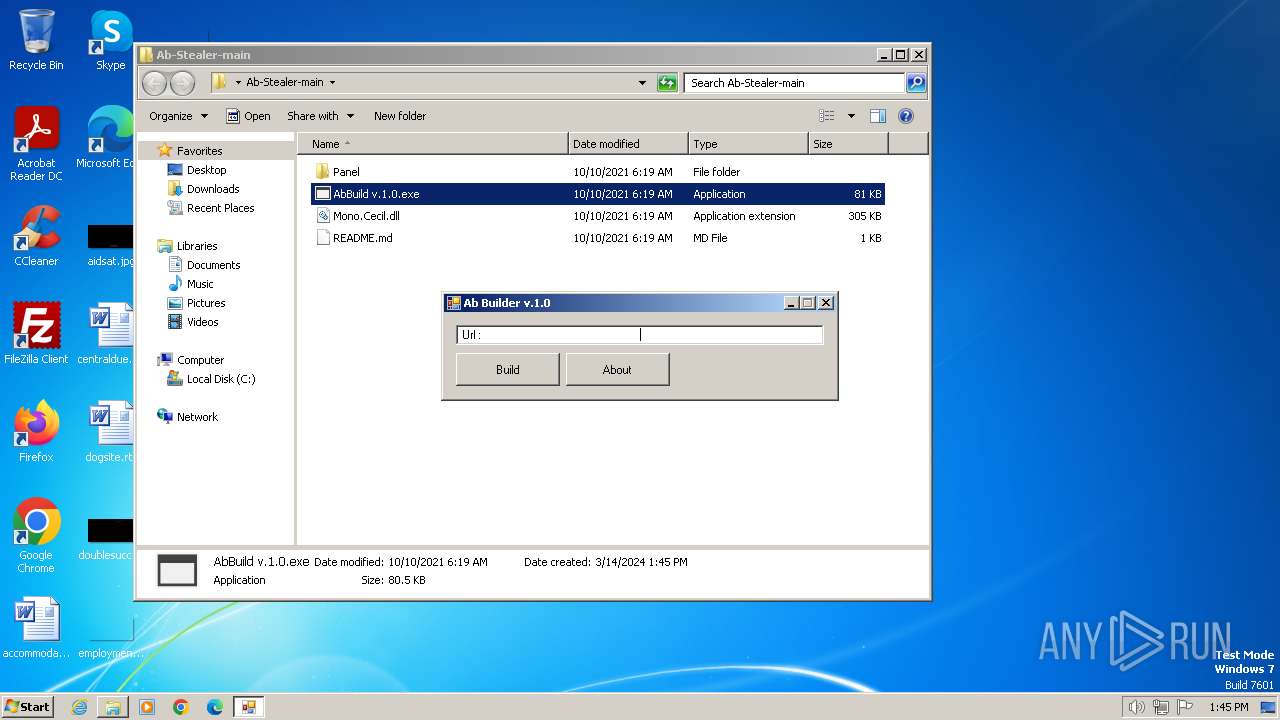
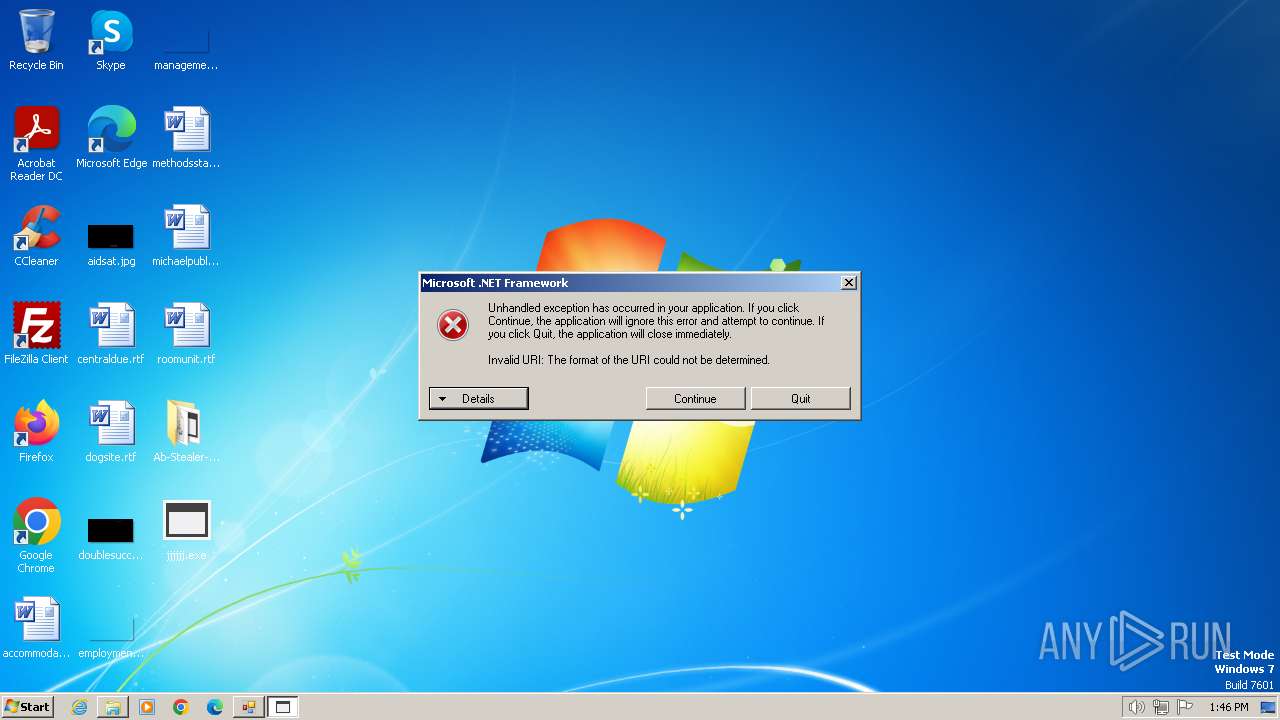
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3656)
- AbBuild v.1.0.exe (PID: 2072)
SUSPICIOUS
Reads the Internet Settings
- AbBuild v.1.0.exe (PID: 2072)
- jjjjjj.exe (PID: 1340)
Executable content was dropped or overwritten
- AbBuild v.1.0.exe (PID: 2072)
Checks for external IP
- jjjjjj.exe (PID: 1340)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3656)
Reads the computer name
- AbBuild v.1.0.exe (PID: 2304)
- AbBuild v.1.0.exe (PID: 2072)
- wmpnscfg.exe (PID: 1768)
- jjjjjj.exe (PID: 1340)
Manual execution by a user
- AbBuild v.1.0.exe (PID: 2304)
- rundll32.exe (PID: 1656)
- AbBuild v.1.0.exe (PID: 2072)
- wmpnscfg.exe (PID: 1768)
- jjjjjj.exe (PID: 1340)
Checks supported languages
- AbBuild v.1.0.exe (PID: 2304)
- AbBuild v.1.0.exe (PID: 2072)
- wmpnscfg.exe (PID: 1768)
- jjjjjj.exe (PID: 1340)
Reads the machine GUID from the registry
- AbBuild v.1.0.exe (PID: 2304)
- AbBuild v.1.0.exe (PID: 2072)
- jjjjjj.exe (PID: 1340)
Reads Environment values
- jjjjjj.exe (PID: 1340)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
45
Monitored processes
6
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1340 | "C:\Users\admin\Desktop\jjjjjj.exe" | C:\Users\admin\Desktop\jjjjjj.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: WindowsApplication710 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
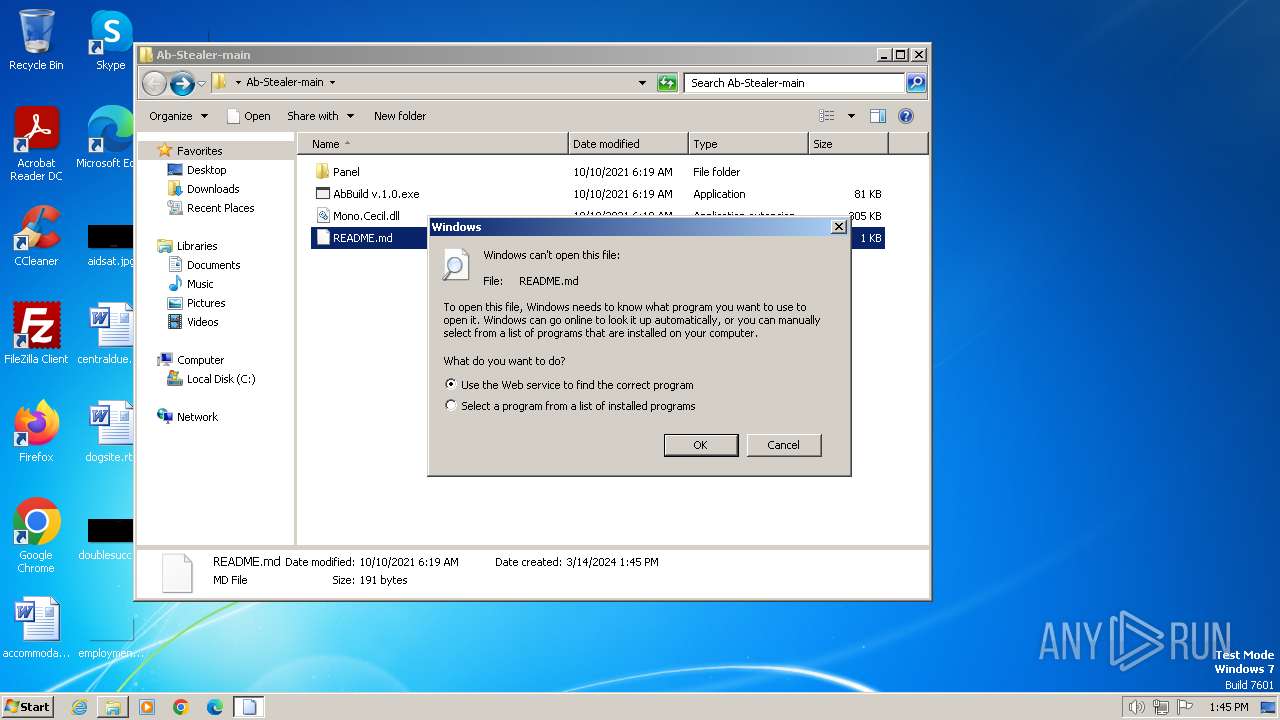
| 1656 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\Ab-Stealer-main\README.md | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1768 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
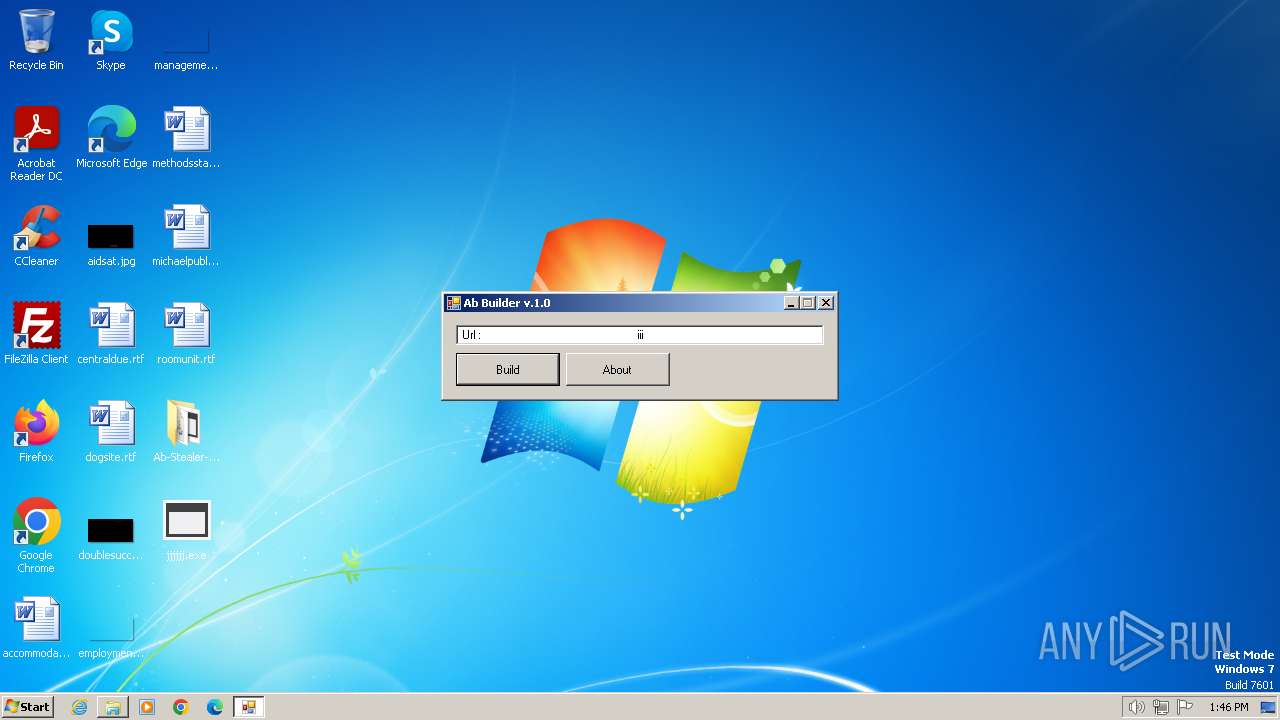
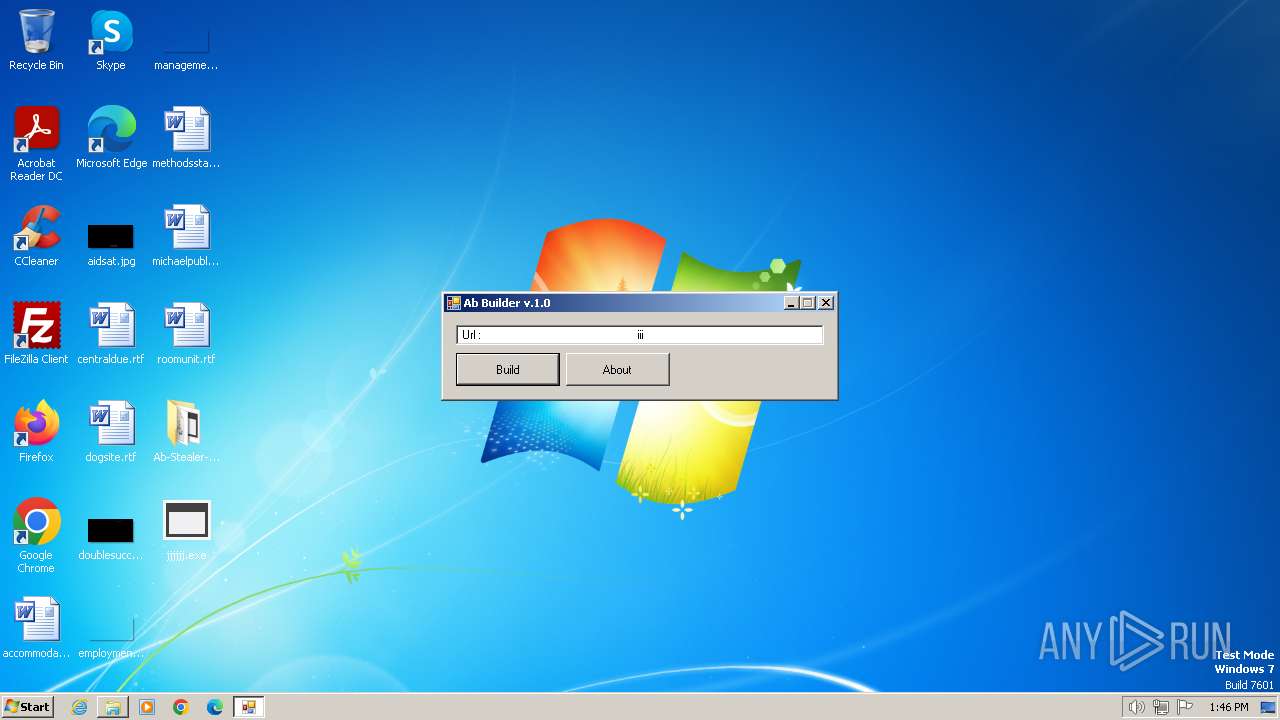
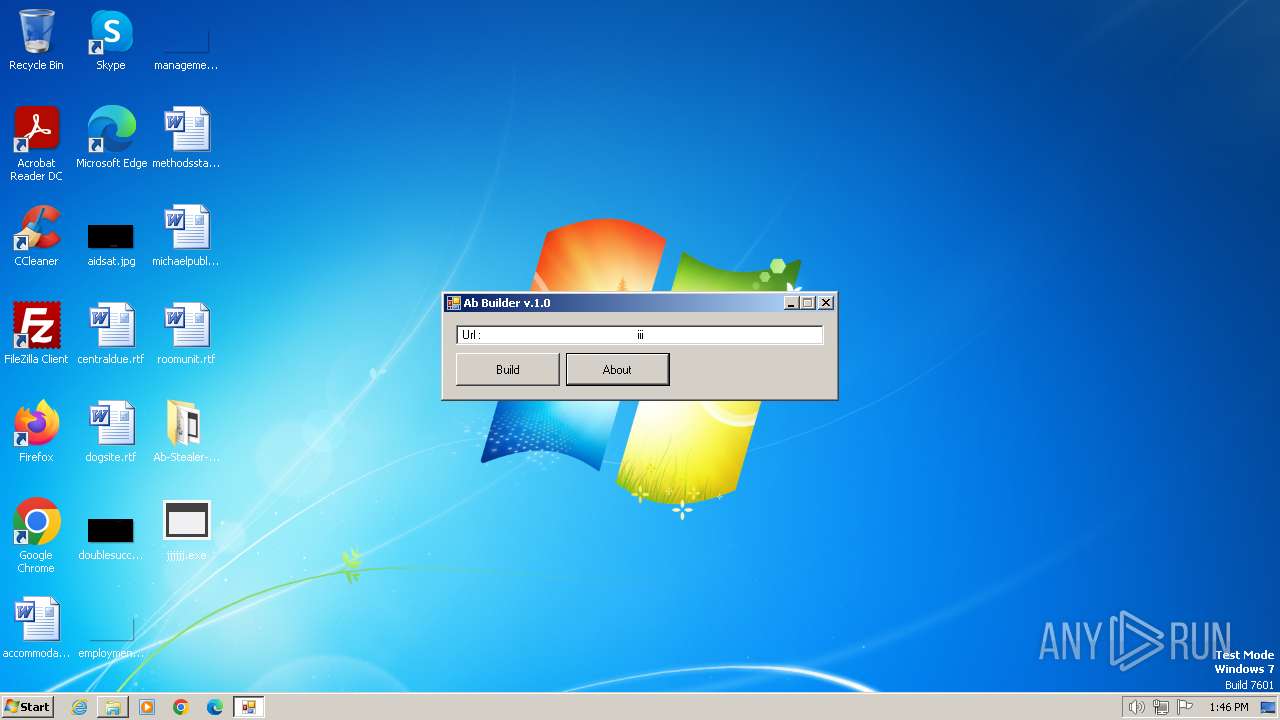
| 2072 | "C:\Users\admin\Desktop\Ab-Stealer-main\AbBuild v.1.0.exe" | C:\Users\admin\Desktop\Ab-Stealer-main\AbBuild v.1.0.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: AbBuilder Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2304 | "C:\Users\admin\Desktop\Ab-Stealer-main\AbBuild v.1.0.exe" | C:\Users\admin\Desktop\Ab-Stealer-main\AbBuild v.1.0.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: AbBuilder Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3656 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\AbStealer Builder.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
14 402
Read events
14 294
Write events
102
Delete events
6
Modification events
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\AbStealer Builder.7z | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
5
Suspicious files
1
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3656 | WinRAR.exe | C:\Users\admin\Desktop\Ab-Stealer-main\README.md | text | |
MD5:6181E961173FDA7E271D6449320BB518 | SHA256:2EBDE333A71B25D1058EFB1A419D479E751F05321A5711116E643316F8AA0E5C | |||
| 3656 | WinRAR.exe | C:\Users\admin\Desktop\Ab-Stealer-main\Mono.Cecil.dll | executable | |
MD5:851EC9D84343FBD089520D420348A902 | SHA256:CDADC26C09F869E21053EE1A0ACF3B2D11DF8EDD599FE9C377BD4D3CE1C9CDA9 | |||
| 3656 | WinRAR.exe | C:\Users\admin\Desktop\Ab-Stealer-main\AbBuild v.1.0.exe | executable | |
MD5:9E44C10307AA8194753896ECF8102167 | SHA256:E1DECC2F7B00CA0AE9055A28D3E3A464D95158A2BED01BEBAE28BD6658870074 | |||
| 3656 | WinRAR.exe | C:\Users\admin\Desktop\Ab-Stealer-main\Panel\Panel.php | text | |
MD5:7053F732191EDF96FD4512762DDF0845 | SHA256:0C7D070541161E43AB3EF8A87723865BF638965B2BD961A6D08125FE12F1ED98 | |||
| 3656 | WinRAR.exe | C:\Users\admin\Desktop\Ab-Stealer-main\Panel\img\AbBuild v.1.0\Mono.Cecil.dll | executable | |
MD5:851EC9D84343FBD089520D420348A902 | SHA256:CDADC26C09F869E21053EE1A0ACF3B2D11DF8EDD599FE9C377BD4D3CE1C9CDA9 | |||
| 3656 | WinRAR.exe | C:\Users\admin\Desktop\Ab-Stealer-main\Panel\logout.php | text | |
MD5:5BCBAA8CBA49A91786BEE395780E9A75 | SHA256:4C88F4B31B7027E03FF6C3DC5A932DEDF2B65F350FD0C66F95F36295DF5C4DFD | |||
| 2072 | AbBuild v.1.0.exe | C:\Users\admin\Desktop\jjjjjj.exe | executable | |
MD5:8786D98CC2822A6938FF272FE585E70D | SHA256:0BCBCC726A52AA98CD469766461BACF1EF4865A02719630755BFAD7C8ED54D91 | |||
| 3656 | WinRAR.exe | C:\Users\admin\Desktop\Ab-Stealer-main\Panel\img\Logo.png | image | |
MD5:9EC35234F894111839CB6325762B022D | SHA256:A7D277AFFBC6AF9148515EE1DF84C0552971C200A2F255AA04B9B33A3663C2FC | |||
| 3656 | WinRAR.exe | C:\Users\admin\Desktop\Ab-Stealer-main\Panel\info.php | text | |
MD5:A629991B6585F3F6BE19B90B900BBF8F | SHA256:E3A7DBFA0A61CFC36B4D59FD7092487E714AD1468F9C1044F403C5B4EEDE9946 | |||
| 3656 | WinRAR.exe | C:\Users\admin\Desktop\Ab-Stealer-main\Panel\img\AbBuild v.1.0.rar | compressed | |
MD5:3AF21FA5DAE9E972DC99FB529BBB28BC | SHA256:E891E103891C3B2409C6BB3E3E4A6797BBDEEEF7691CC9238B630E91F52D1532 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
5
DNS requests
1
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1340 | jjjjjj.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | binary | 315 b | unknown |
1340 | jjjjjj.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | binary | 315 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1340 | jjjjjj.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1340 | jjjjjj.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
1340 | jjjjjj.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
1340 | jjjjjj.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
1340 | jjjjjj.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |