| File name: | brbbot.exe |
| Full analysis: | https://app.any.run/tasks/1ac8c34e-023a-461a-85df-520b8630b52c |
| Verdict: | Malicious activity |
| Analysis date: | May 24, 2025, 19:03:07 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 11DD7DA7FAA0130DAC2560930E90C8B1 |
| SHA1: | 2C9E509DE4B3EC03589B5C95BABA06A9387195E6 |
| SHA256: | B9CFD5F89BD282452F82CC8D323F39C6932E55CAB98065BB3C2CF97BB585DC2D |
| SSDEEP: | 384:CPLOy0zT24aPIboBjLs2lPGejkEB8uLD6M0:CPwT2HP44jxPGYkE+AD6M0 |
MALICIOUS
No malicious indicators.SUSPICIOUS
There is functionality for taking screenshot (YARA)
- brbbot.exe (PID: 6640)
Reads security settings of Internet Explorer
- brbbot.exe (PID: 6640)
- Procmon.exe (PID: 7724)
Executable content was dropped or overwritten
- Procmon.exe (PID: 7724)
- Procmon64.exe (PID: 7840)
Creates or modifies Windows services
- Procmon64.exe (PID: 7840)
Drops a system driver (possible attempt to evade defenses)
- Procmon64.exe (PID: 7840)
Creates files in the driver directory
- Procmon64.exe (PID: 7840)
INFO
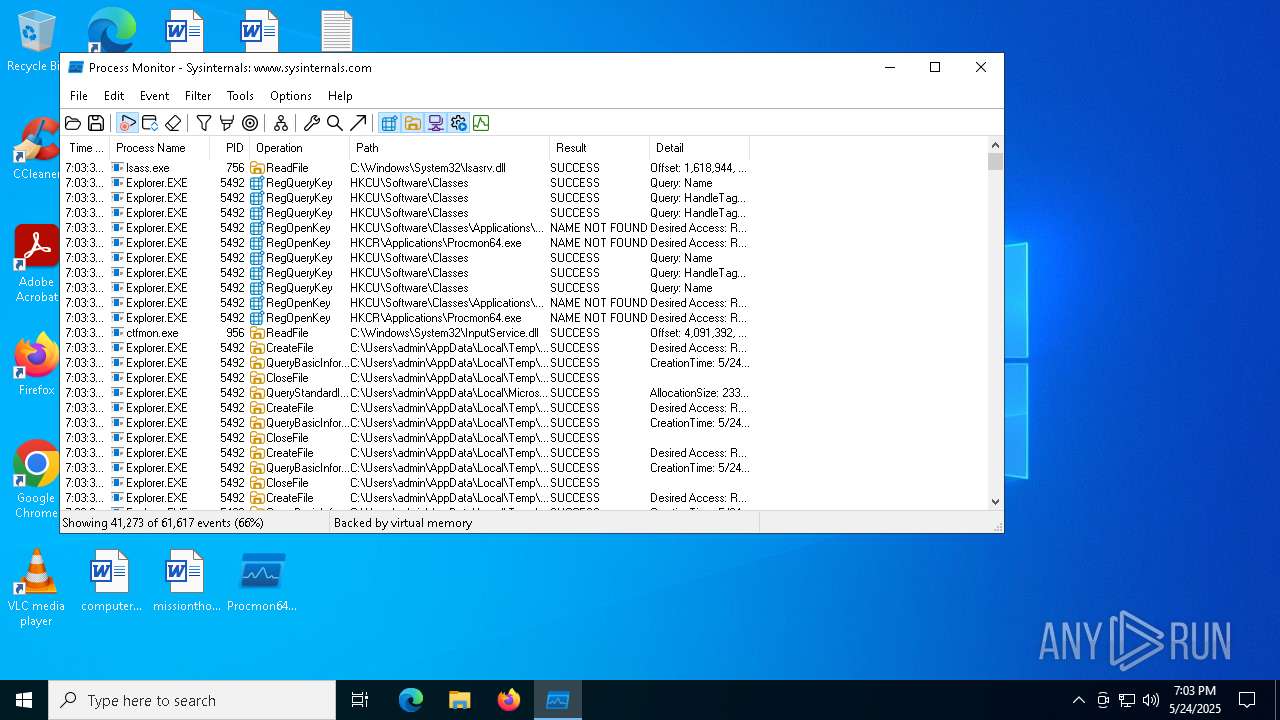
Create files in a temporary directory
- brbbot.exe (PID: 6640)
- Procmon.exe (PID: 7724)
Manual execution by a user
- WinRAR.exe (PID: 7656)
- Procmon.exe (PID: 7724)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7656)
Reads the machine GUID from the registry
- brbbot.exe (PID: 6640)
Checks supported languages
- brbbot.exe (PID: 6640)
- Procmon.exe (PID: 7724)
- Procmon64.exe (PID: 7840)
Reads the computer name
- brbbot.exe (PID: 6640)
- Procmon.exe (PID: 7724)
- Procmon64.exe (PID: 7840)
Failed to create an executable file in Windows directory
- brbbot.exe (PID: 6640)
The sample compiled with english language support
- WinRAR.exe (PID: 7656)
- Procmon64.exe (PID: 7840)
Checks proxy server information
- brbbot.exe (PID: 6640)
- slui.exe (PID: 5512)
Process checks whether UAC notifications are on
- Procmon.exe (PID: 7724)
Process checks computer location settings
- Procmon.exe (PID: 7724)
Reads the software policy settings
- slui.exe (PID: 7300)
- slui.exe (PID: 5512)
Reads CPU info
- Procmon64.exe (PID: 7840)
Reads the time zone
- Procmon64.exe (PID: 7840)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:03:15 20:23:10+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 14336 |
| InitializedDataSize: | 5632 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x34cd |
| OSVersion: | 6.1 |
| ImageVersion: | 6.1 |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
141
Monitored processes
8
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5512 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6640 | "C:\Users\admin\AppData\Local\Temp\brbbot.exe" | C:\Users\admin\AppData\Local\Temp\brbbot.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 7264 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7300 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
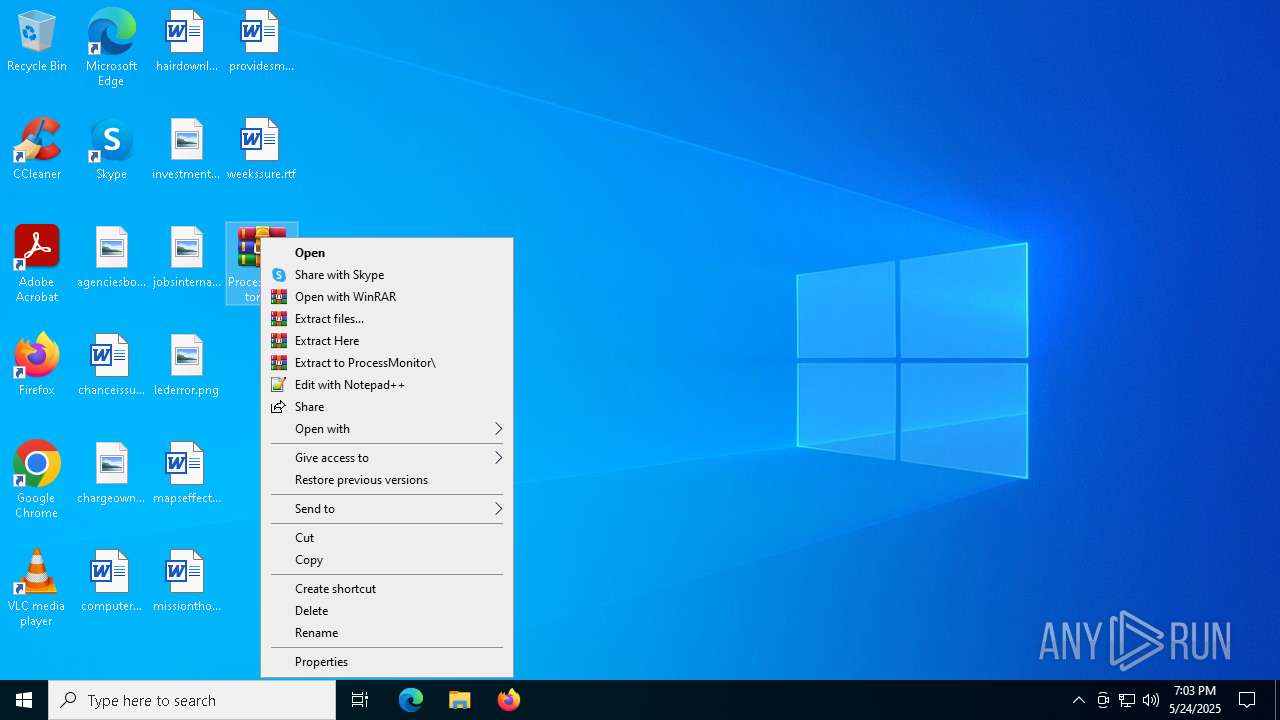
| 7656 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\ProcessMonitor.zip" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7724 | "C:\Users\admin\Desktop\Procmon.exe" | C:\Users\admin\Desktop\Procmon.exe | explorer.exe | ||||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Process Monitor Version: 4.01 Modules
| |||||||||||||||
| 7840 | "C:\Users\admin\AppData\Local\Temp\Procmon64.exe" /originalpath "C:\Users\admin\Desktop\Procmon.exe" | C:\Users\admin\AppData\Local\Temp\Procmon64.exe | Procmon.exe | ||||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: HIGH Description: Process Monitor Version: 4.01 Modules
| |||||||||||||||
Total events
3 076
Read events
3 056
Write events
16
Delete events
4
Modification events
| (PID) Process: | (7656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7724) Procmon.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\Process Monitor |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (7724) Procmon.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (7840) Procmon64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\Process Monitor |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (7840) Procmon64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 18 | |||
| (PID) Process: | (7840) Procmon64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\PROCMON24 |
| Operation: | write | Name: | Type |
Value: 2 | |||
| (PID) Process: | (7840) Procmon64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\PROCMON24 |
| Operation: | write | Name: | ErrorControl |
Value: 1 | |||
Executable files
5
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7656 | WinRAR.exe | C:\Users\admin\Desktop\Procmon64.exe | executable | |
MD5:223B222CE387A7F446D49A1EE9B572BB | SHA256:3E15995894F38B2EEAD95F7FF714585471F34F3AF3D8F50A7F83344781502468 | |||
| 7724 | Procmon.exe | C:\Users\admin\AppData\Local\Temp\Procmon64.exe | executable | |
MD5:223B222CE387A7F446D49A1EE9B572BB | SHA256:3E15995894F38B2EEAD95F7FF714585471F34F3AF3D8F50A7F83344781502468 | |||
| 7656 | WinRAR.exe | C:\Users\admin\Desktop\Procmon64a.exe | executable | |
MD5:03A3A7C0F0534D7F56FB50D486FE8CEF | SHA256:36085927CA98B9B7D630EDEAD37671208E01978CA38974FB3FD435F42E709702 | |||
| 6640 | brbbot.exe | C:\Users\admin\AppData\Local\Temp\brbconfig.tmp | binary | |
MD5:FEFC78962CFAEE3B2A9472B1357CE648 | SHA256:EE20EC1F9A574280270C0045CAA6EDA5B35B35D131E7A45DB7D0AFDAEF131E08 | |||
| 7656 | WinRAR.exe | C:\Users\admin\Desktop\Eula.txt | text | |
MD5:8C24C4084CDC3B7E7F7A88444A012BFC | SHA256:8329BCBADC7F81539A4969CA13F0BE5B8EB7652B912324A1926FC9BFB6EC005A | |||
| 7840 | Procmon64.exe | C:\Windows\System32\drivers\PROCMON24.SYS | executable | |
MD5:03480D56A090F0CD397677251F747929 | SHA256:2A5A61BDA7B7B5D6E69B588FFBF625A1534D5A94F39801F6E0376774AA103DD9 | |||
| 7656 | WinRAR.exe | C:\Users\admin\Desktop\Procmon.exe | executable | |
MD5:C3E77B6959CC68BAEE9825C84DC41D9C | SHA256:3B7EA4318C3C1508701102CF966F650E04F28D29938F85D74EC0EC2528657B6E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
31
DNS requests
45
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8188 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8188 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
brb.3dtuts.by |
| malicious |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
255.100.168.192.in-addr.arpa |
| unknown |
75.159.190.20.in-addr.arpa |
| unknown |