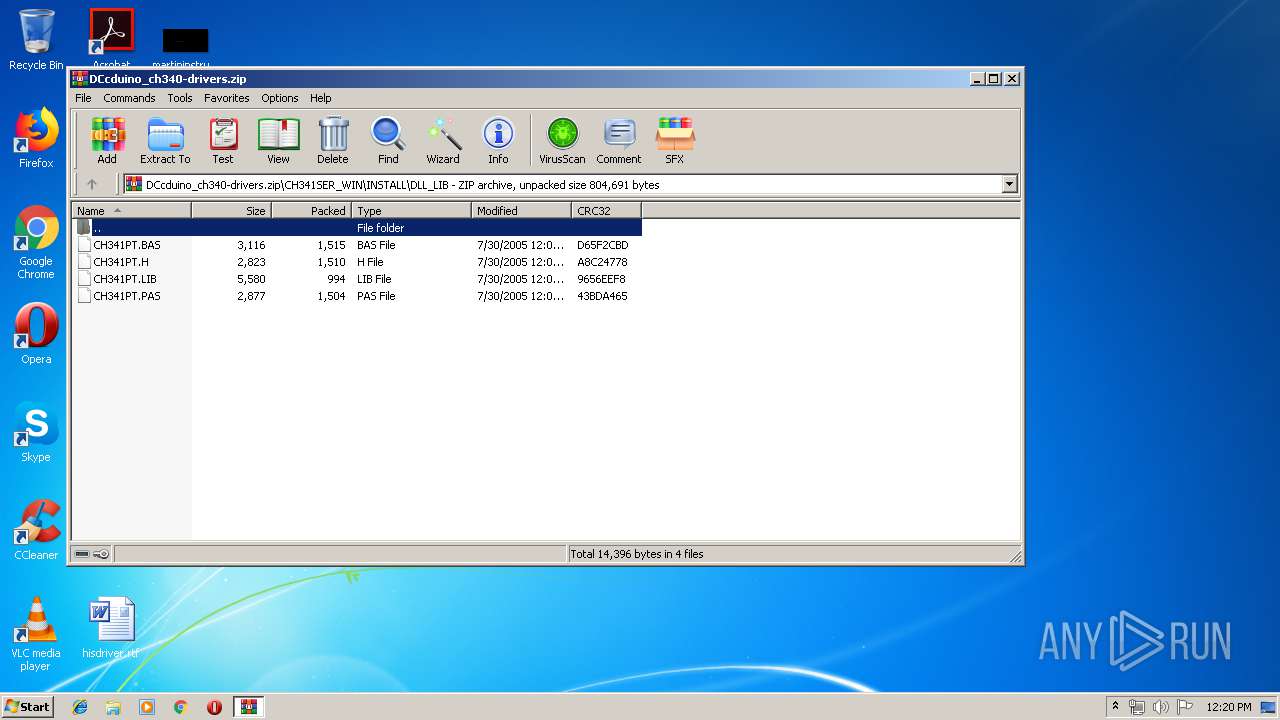
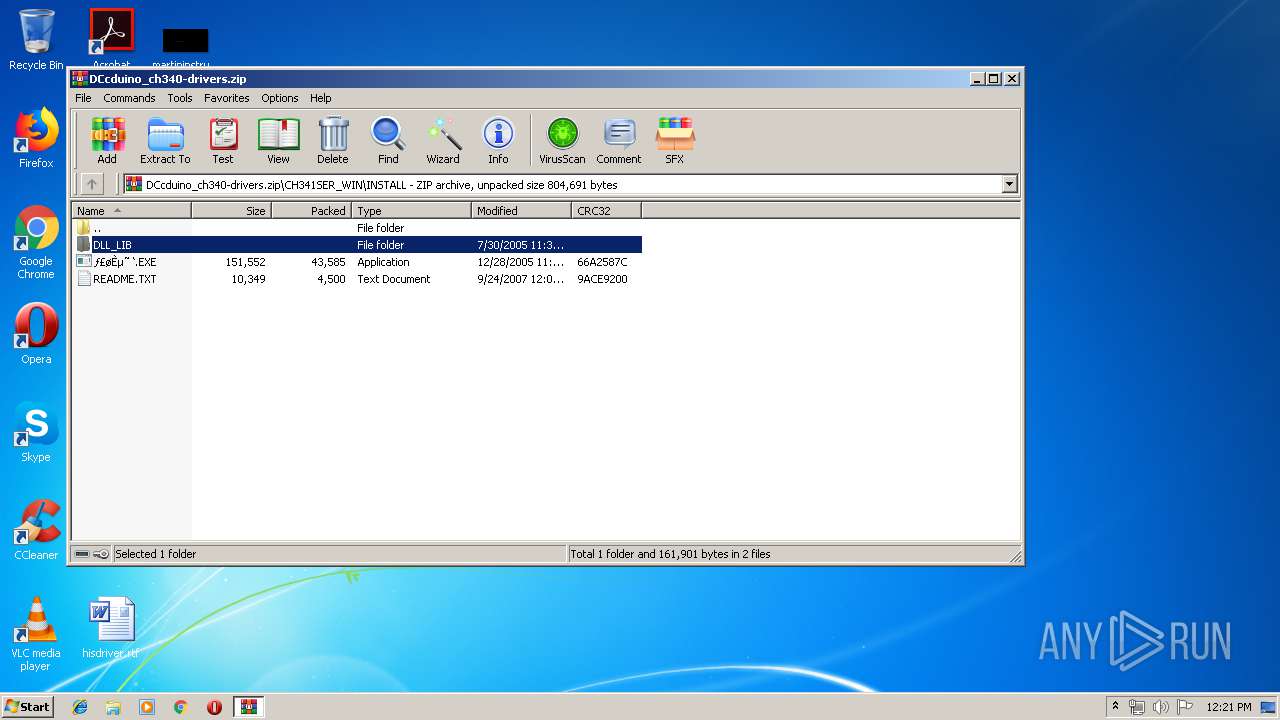
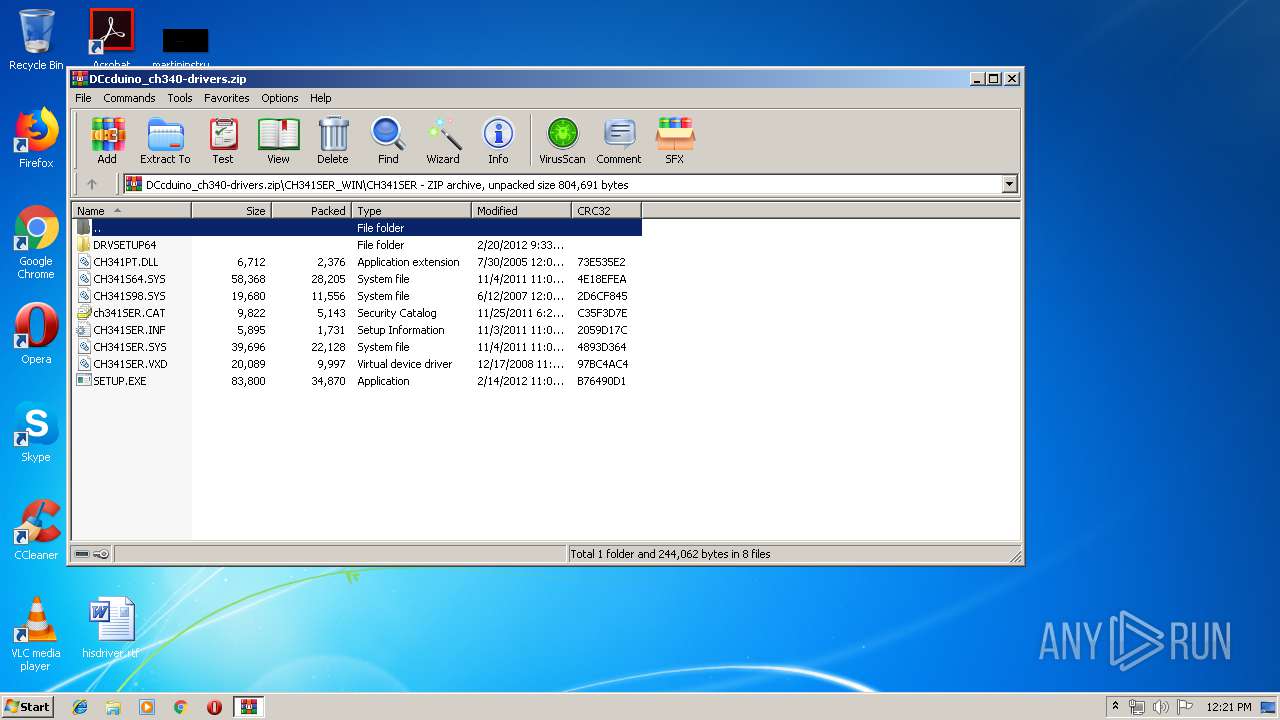
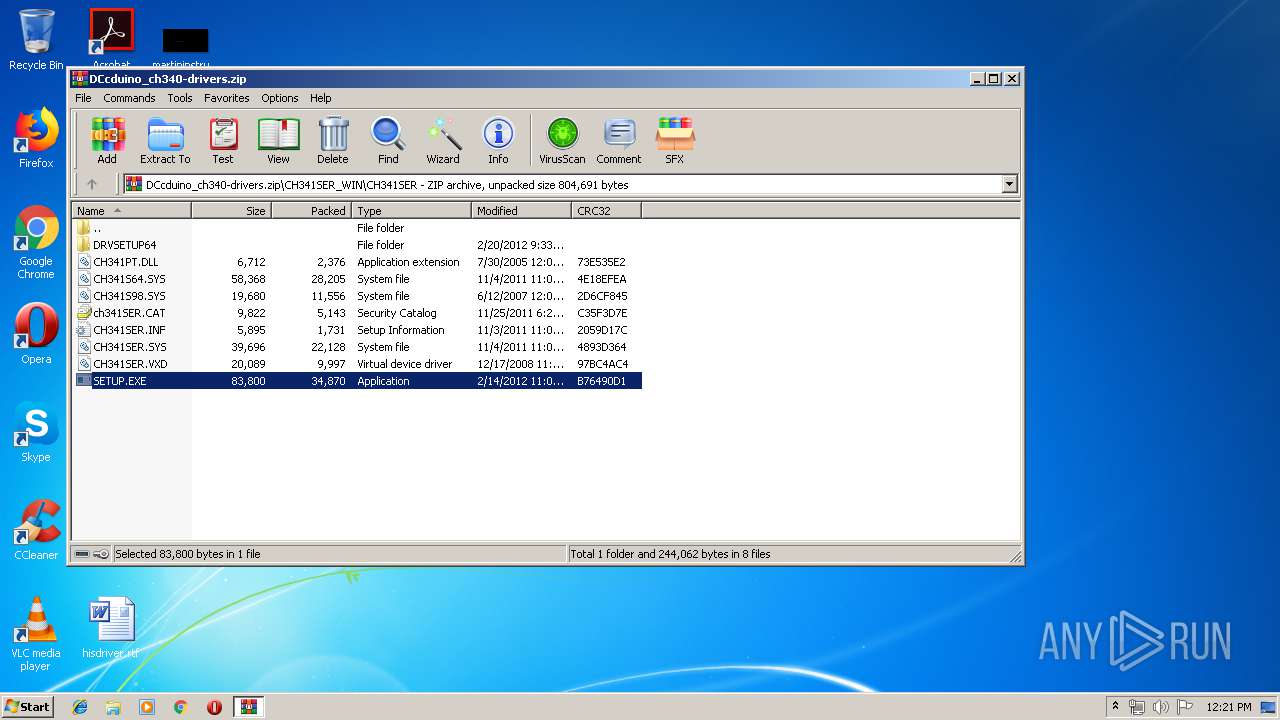
| download: | DCcduino_ch340-drivers.zip |
| Full analysis: | https://app.any.run/tasks/87414982-cf0b-43dc-b2f6-a58f7b6a73b0 |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2019, 11:18:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
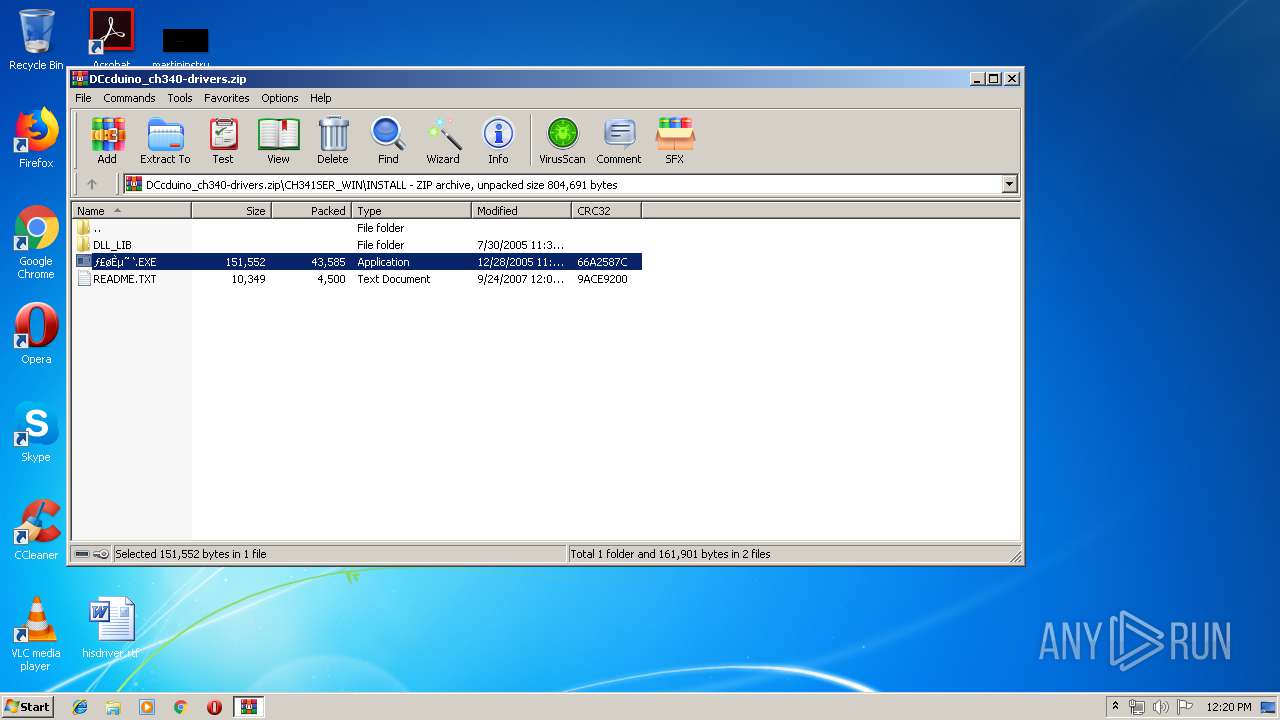
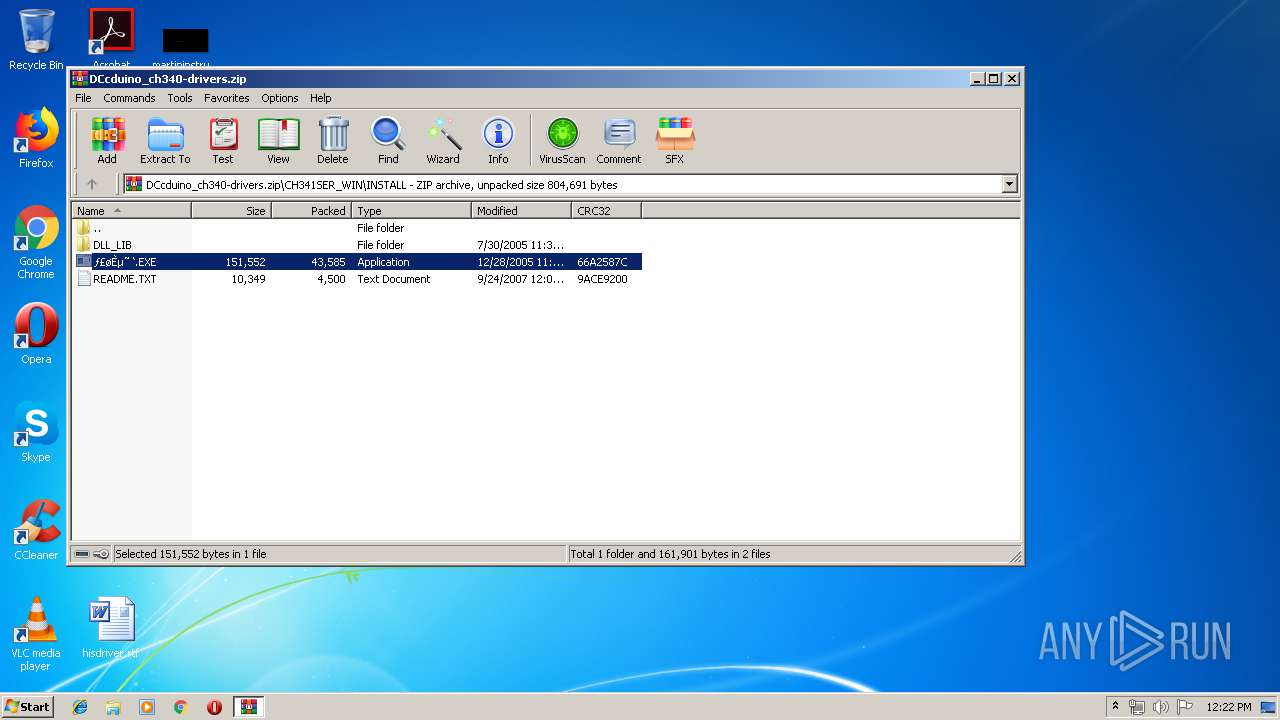
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | BB4B0F3F428B17CCEC69B29E38F5386D |
| SHA1: | 4007B7152907389CA8CC35FF36CFEA49D1710AF6 |
| SHA256: | B9CEDB1C0F122DE38E9A3AEE93ABC02085F91B678077AE75BFCCC594F301BC0C |
| SSDEEP: | 12288:UPi9BYuhKwax04Z6RZHyianxi47XZ5VLe/CgSqvkoSdF:UwSAnyHZze/BSqvkHF |
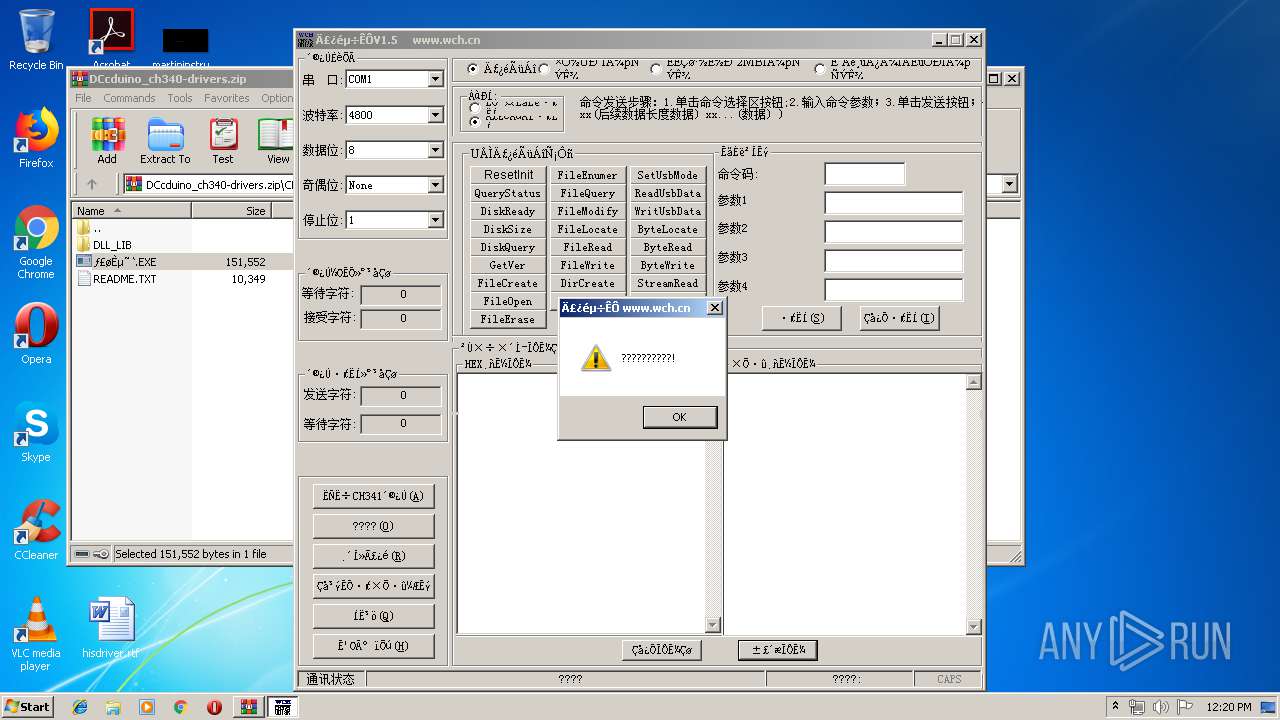
MALICIOUS
Application was dropped or rewritten from another process
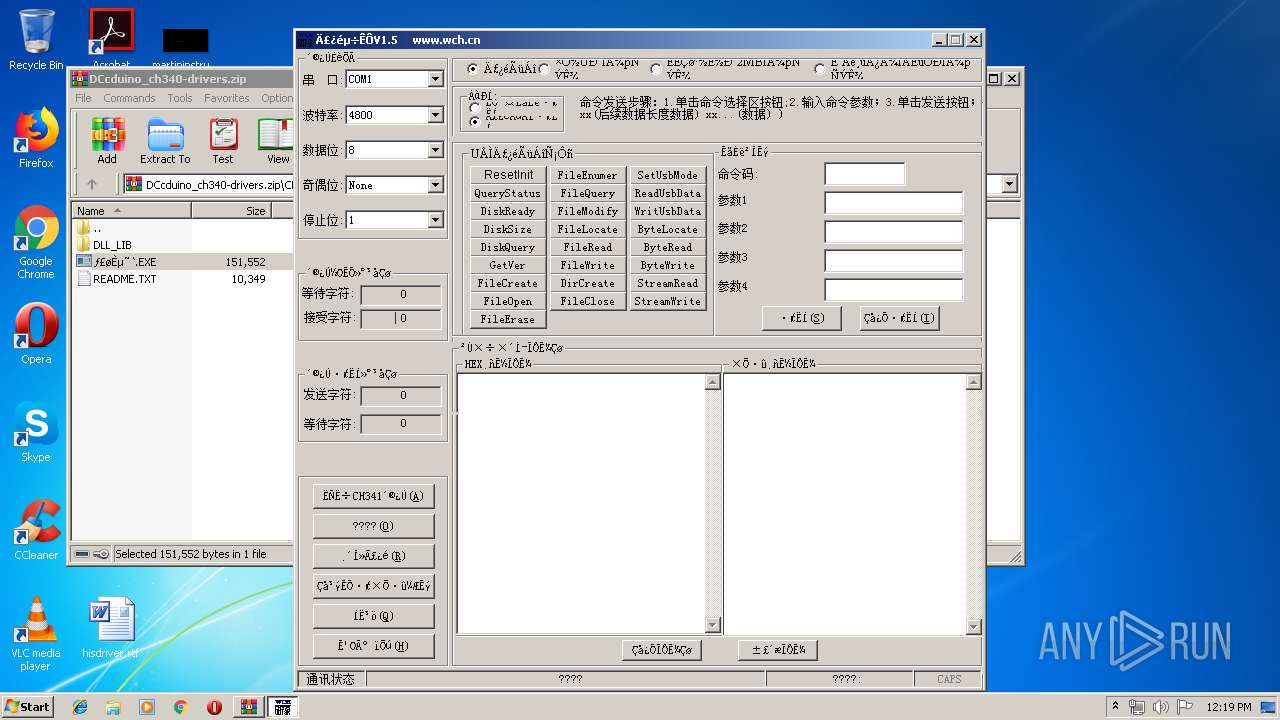
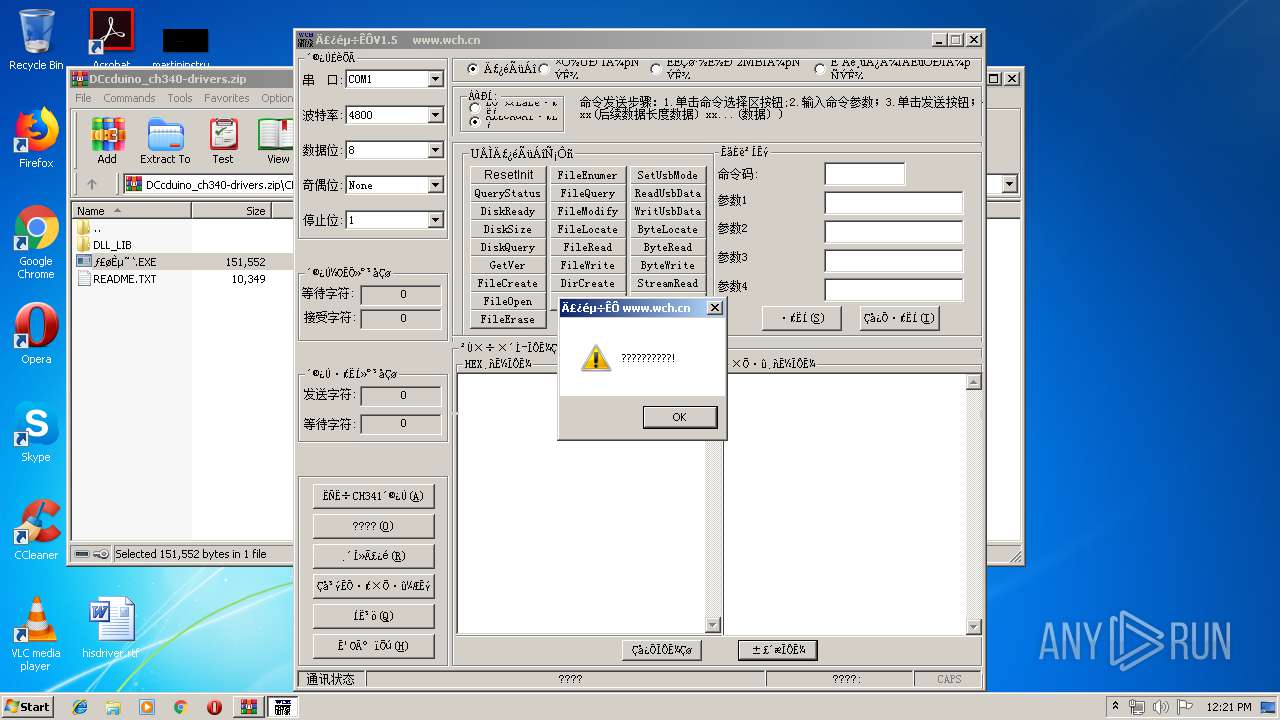
- ƒ£øȵ˜ ‘.EXE (PID: 2360)
- SETUP.EXE (PID: 3176)
- SETUP.EXE (PID: 1592)
- ƒ£øȵ˜ ‘.EXE (PID: 2924)
Loads dropped or rewritten executable
- SETUP.EXE (PID: 1592)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2664)
- SETUP.EXE (PID: 1592)
Creates files in the Windows directory
- DrvInst.exe (PID: 1472)
- SETUP.EXE (PID: 1592)
Creates files in the driver directory
- DrvInst.exe (PID: 1472)
- SETUP.EXE (PID: 1592)
Removes files from Windows directory
- DrvInst.exe (PID: 1472)
- SETUP.EXE (PID: 1592)
INFO
Adds / modifies Windows certificates
- DrvInst.exe (PID: 1472)
Changes settings of System certificates
- DrvInst.exe (PID: 1472)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2013:08:09 21:26:06 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | CH341SER_LINUX/ |
Total processes
40
Monitored processes
7
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1472 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{789d9362-9a73-169b-4457-d91cd3005365}\CH341SER.INF" "0" "606613b1f" "0000055C" "WinSta0\Default" "000005BC" "208" "C:\Users\admin\AppData\Local\Temp\Rar$EXa2664.26815\CH341SER_WIN\CH341SER" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
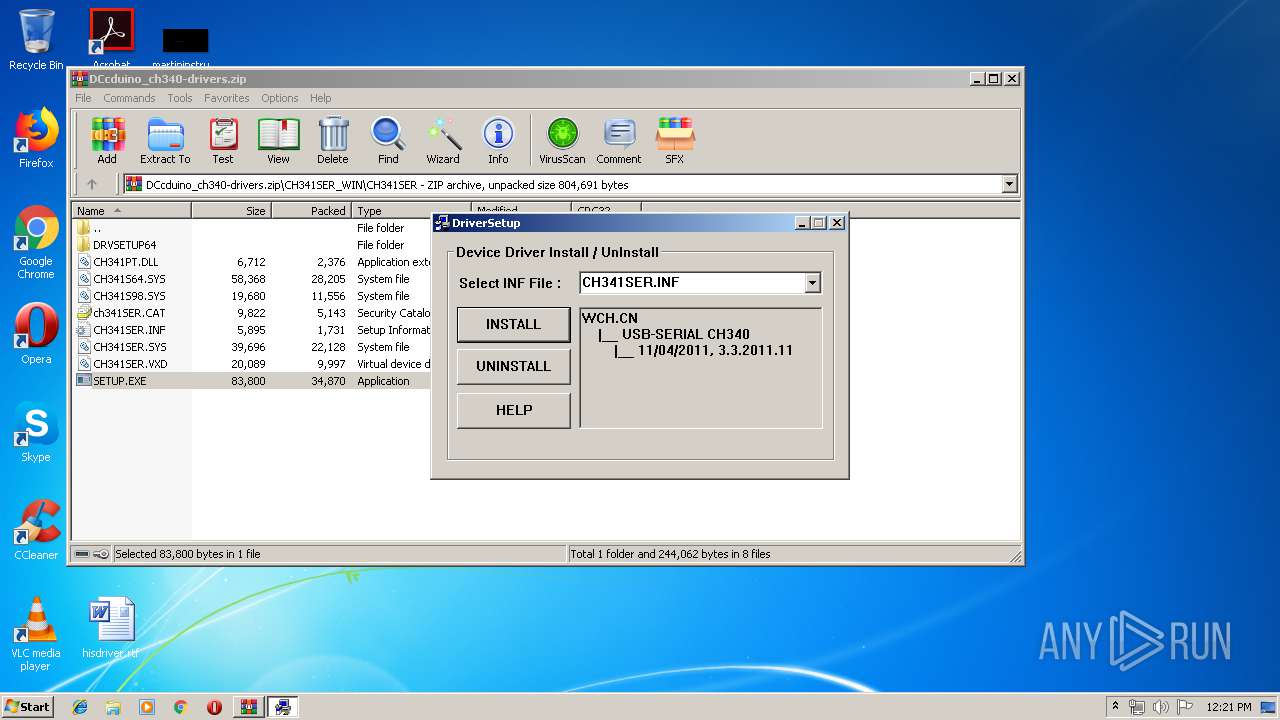
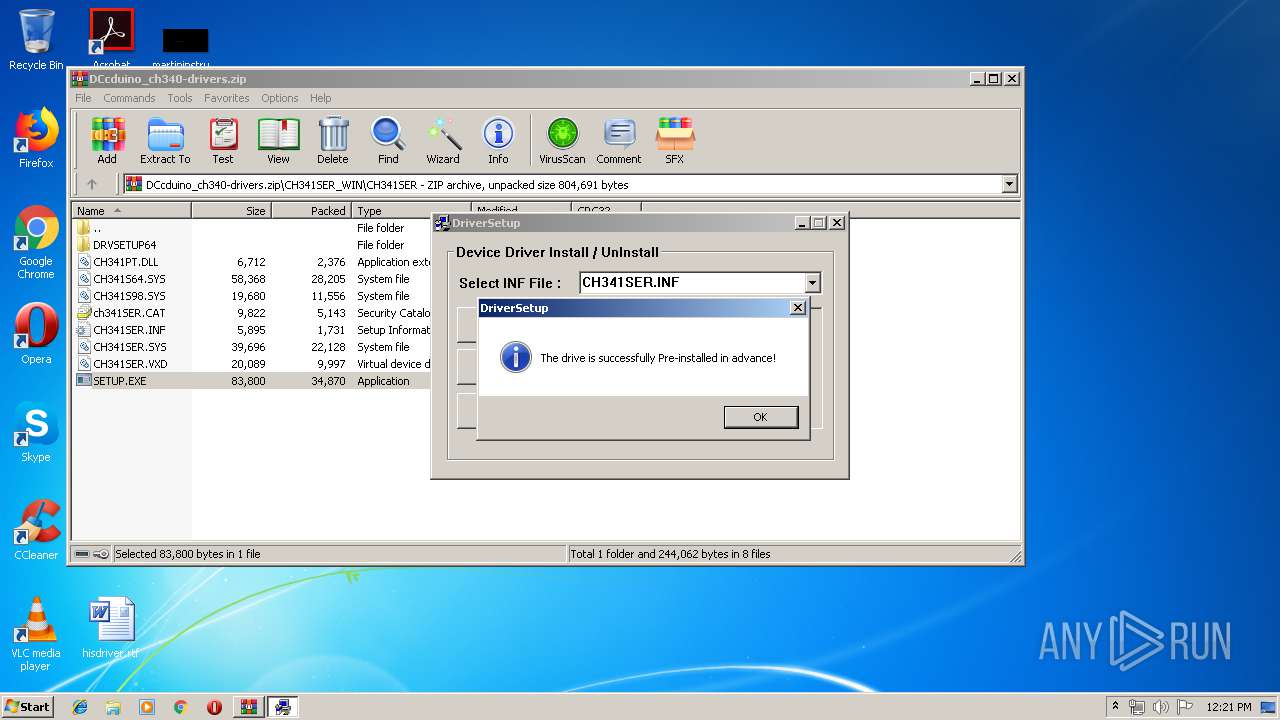
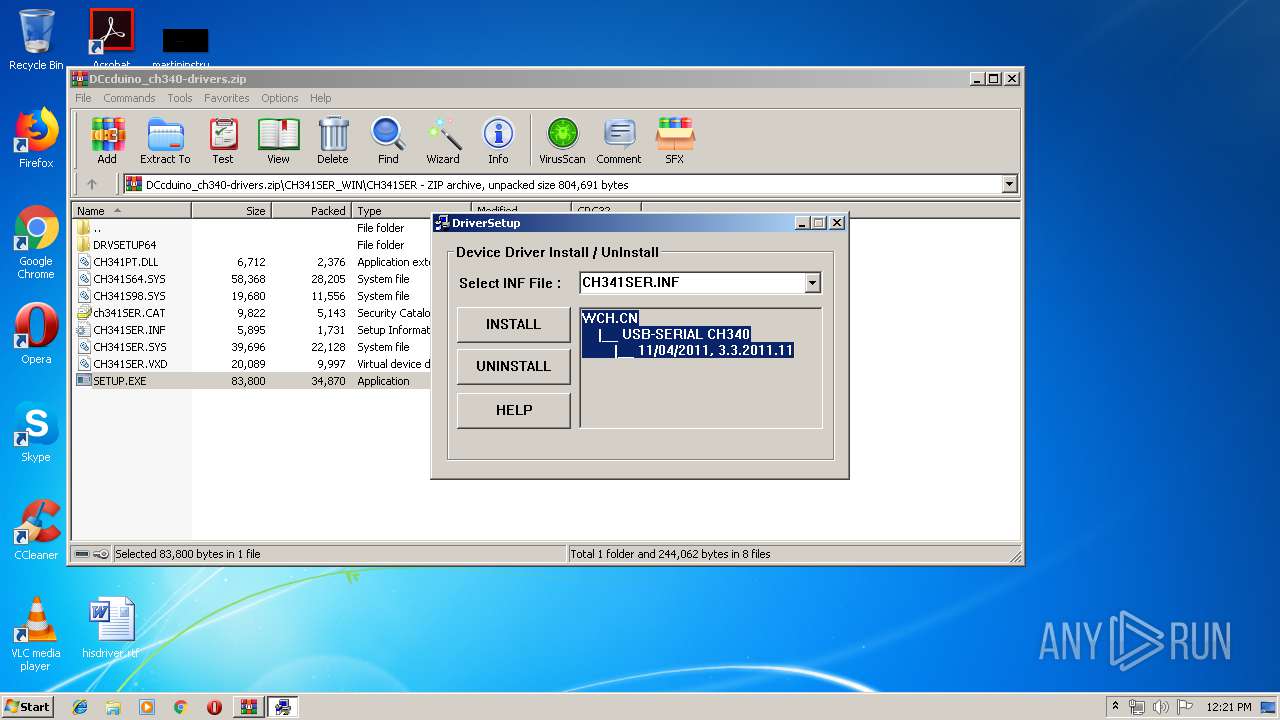
| 1592 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2664.26815\CH341SER_WIN\CH341SER\SETUP.EXE" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2664.26815\CH341SER_WIN\CH341SER\SETUP.EXE | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: EXE For Driver Installation Exit code: 1 Version: 1, 6, 0, 0 Modules
| |||||||||||||||
| 2360 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2664.18750\CH341SER_WIN\INSTALL\ƒ£øȵ˜ ‘.EXE" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2664.18750\CH341SER_WIN\INSTALL\ƒ£øȵ˜ ‘.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: 南京沁恒电子有限公司 Integrity Level: MEDIUM Description: 1.5 Exit code: 0 Version: 1.50 Modules
| |||||||||||||||
| 2664 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\DCcduino_ch340-drivers.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2924 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2664.29089\CH341SER_WIN\INSTALL\ƒ£øȵ˜ ‘.EXE" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2664.29089\CH341SER_WIN\INSTALL\ƒ£øȵ˜ ‘.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: 南京沁恒电子有限公司 Integrity Level: MEDIUM Description: 1.5 Exit code: 0 Version: 1.50 Modules
| |||||||||||||||
| 3176 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2664.26815\CH341SER_WIN\CH341SER\SETUP.EXE" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2664.26815\CH341SER_WIN\CH341SER\SETUP.EXE | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: EXE For Driver Installation Exit code: 3221226540 Version: 1, 6, 0, 0 Modules
| |||||||||||||||
| 3360 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa2664.25470\README.TXT | C:\Windows\system32\NOTEPAD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
520
Read events
463
Write events
57
Delete events
0
Modification events
| (PID) Process: | (2664) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2664) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2664) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2664) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\DCcduino_ch340-drivers.zip | |||
| (PID) Process: | (2664) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2664) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2664) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2664) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2664) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
| (PID) Process: | (2664) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
32
Suspicious files
13
Text files
153
Unknown types
93
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2664 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2664.18750\CH341SER_LINUX\ch34x.c | text | |
MD5:— | SHA256:— | |||
| 2664 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2664.18750\__MACOSX\CH341SER_LINUX\._ch34x.c | ad | |
MD5:— | SHA256:— | |||
| 2664 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2664.18750\__MACOSX\CH341SER_LINUX\._readme.txt | ad | |
MD5:— | SHA256:— | |||
| 2664 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2664.18750\__MACOSX\._CH341SER_LINUX | ad | |
MD5:— | SHA256:— | |||
| 2664 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2664.18750\__MACOSX\CH341SER_LINUX\._Makefile | ad | |
MD5:— | SHA256:— | |||
| 2664 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2664.18750\__MACOSX\CH341SER_MAC\.___MACOSX | ad | |
MD5:— | SHA256:— | |||
| 2664 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2664.18750\CH341SER_LINUX\readme.txt | text | |
MD5:— | SHA256:— | |||
| 2664 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2664.18750\CH341SER_MAC\ch34xInstall.pkg | xar | |
MD5:— | SHA256:— | |||
| 2664 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2664.18750\__MACOSX\CH341SER_MAC\._ch34xInstall.pkg | ad | |
MD5:— | SHA256:— | |||
| 2664 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2664.18750\CH341SER_MAC\readme.pdf | ||
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report