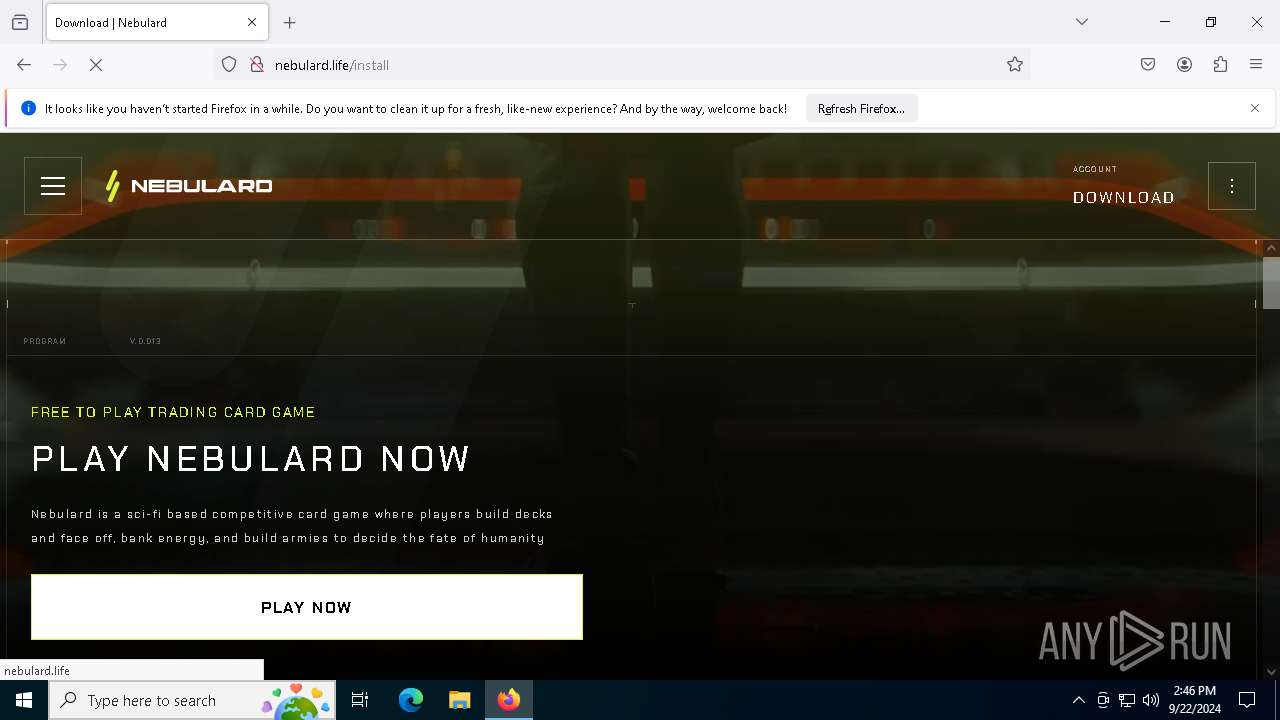
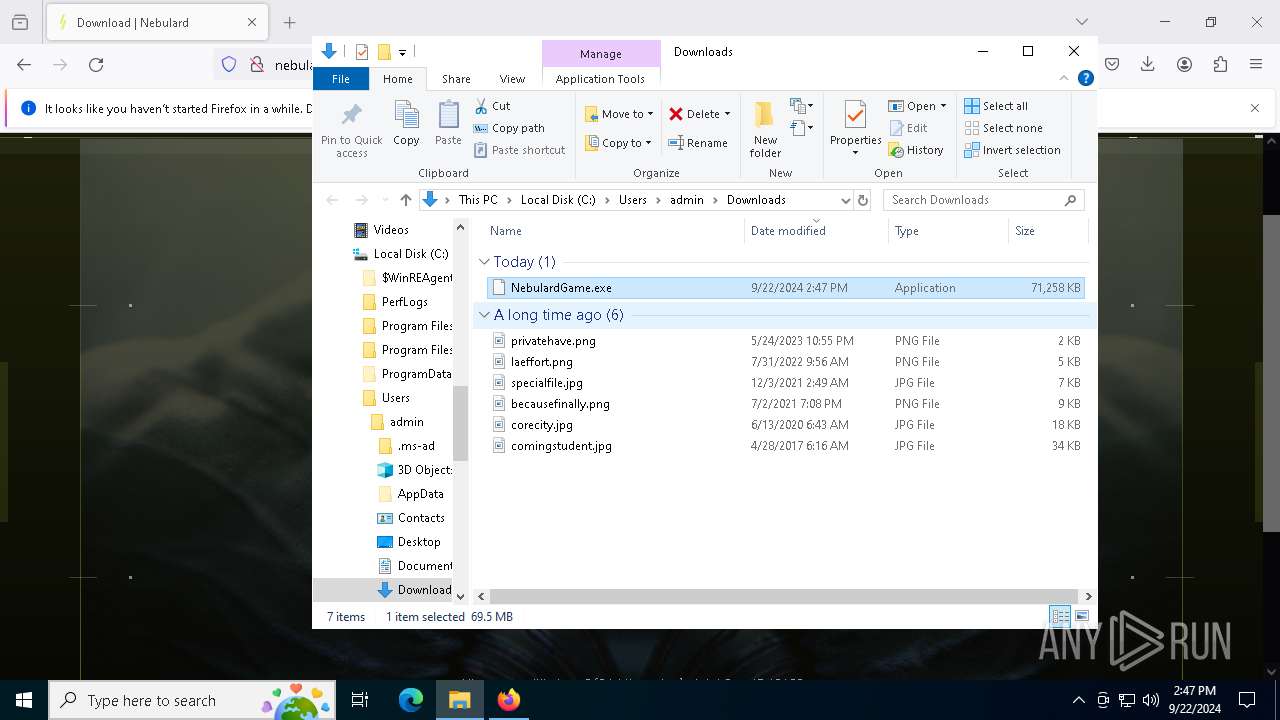
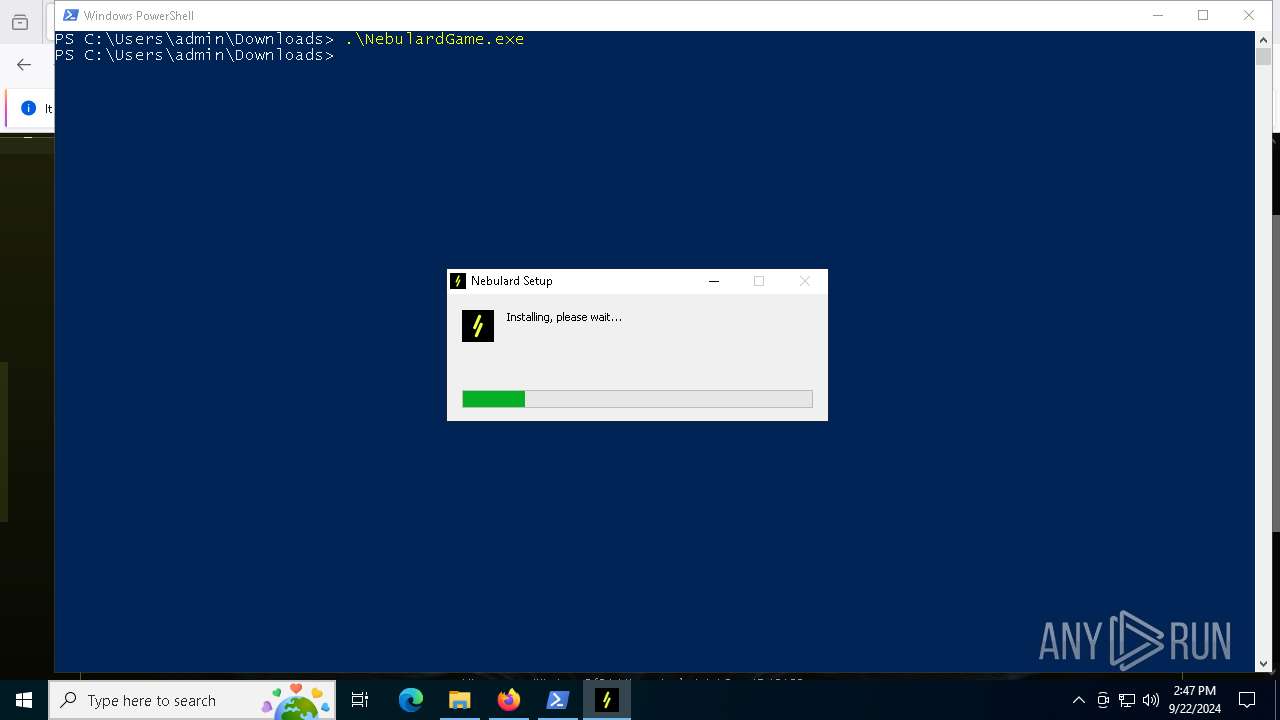
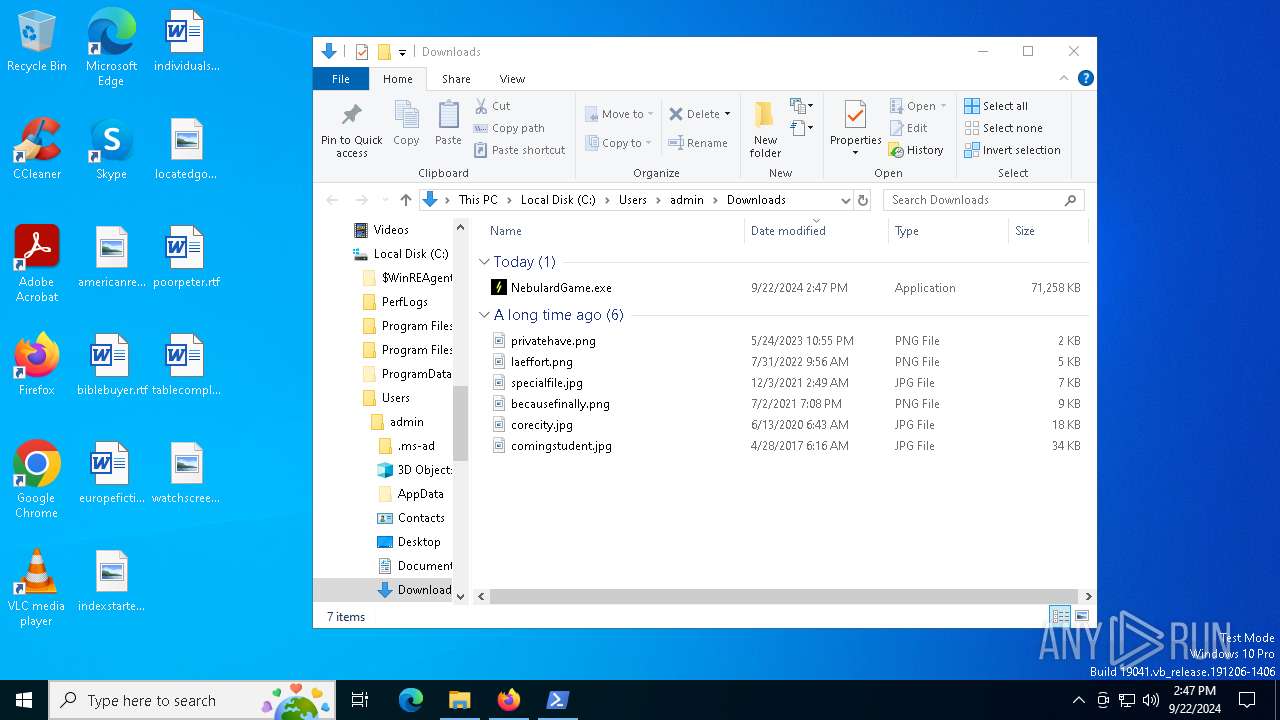
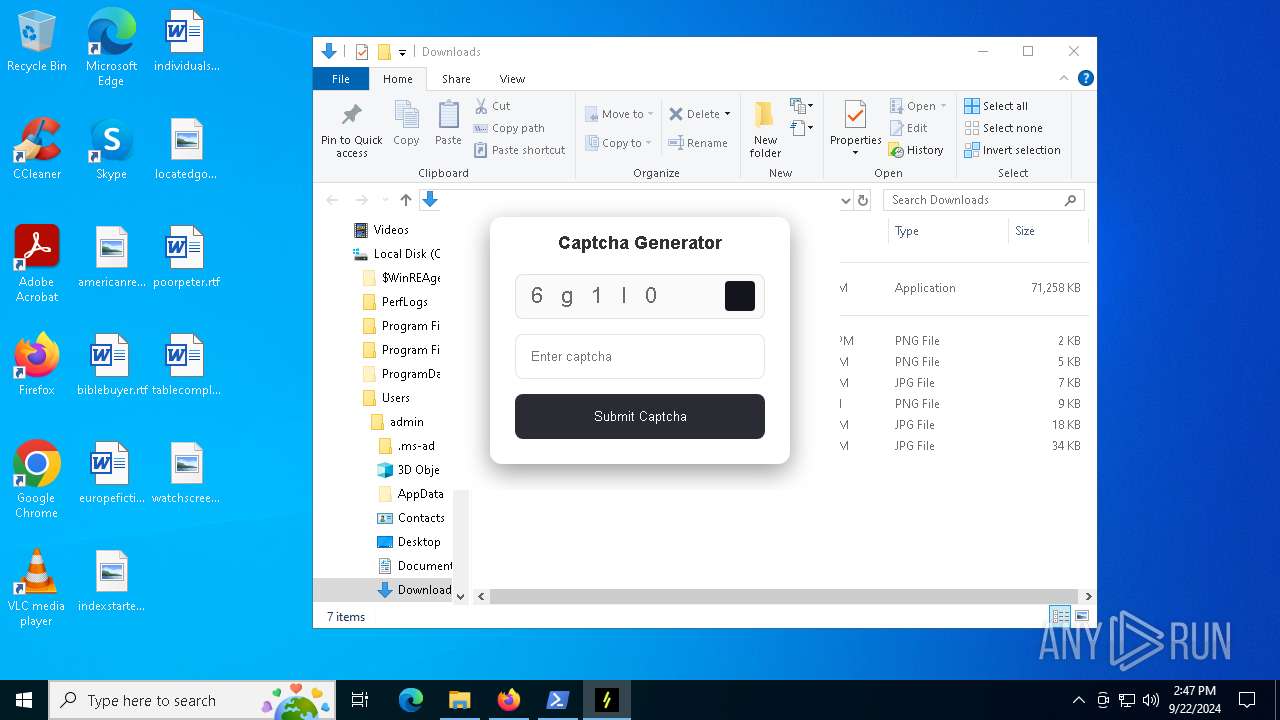
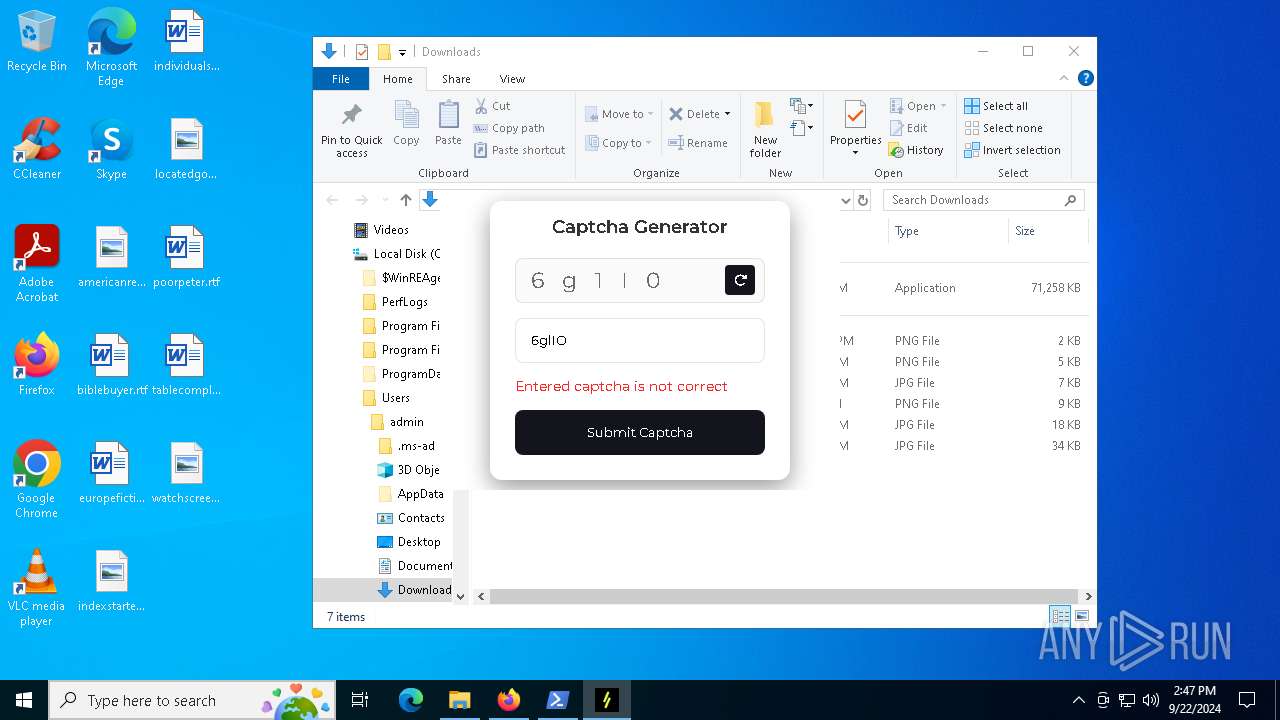
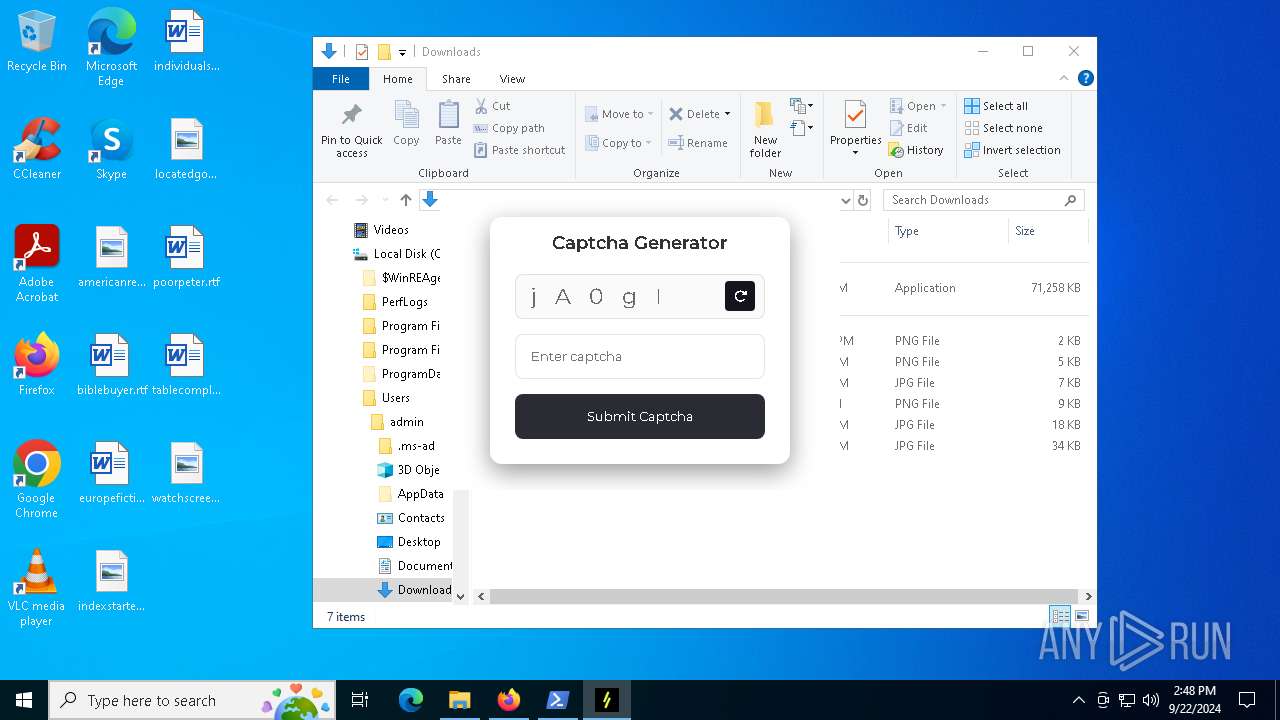
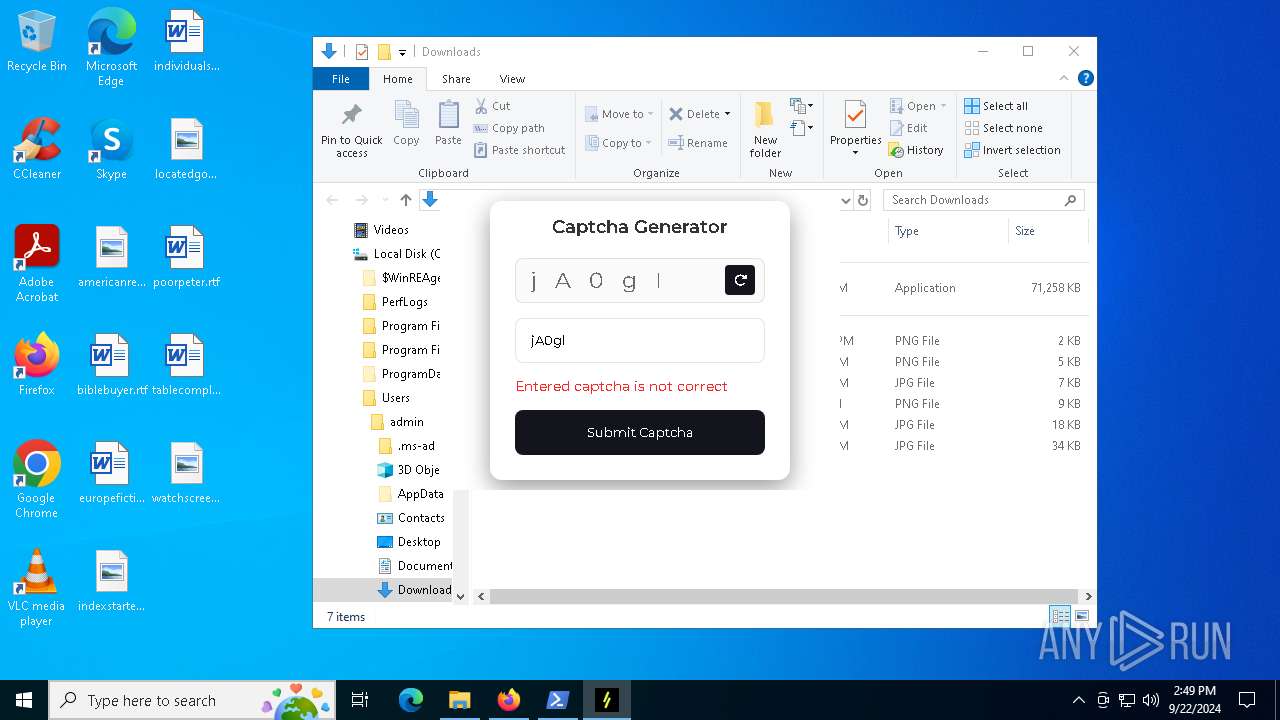
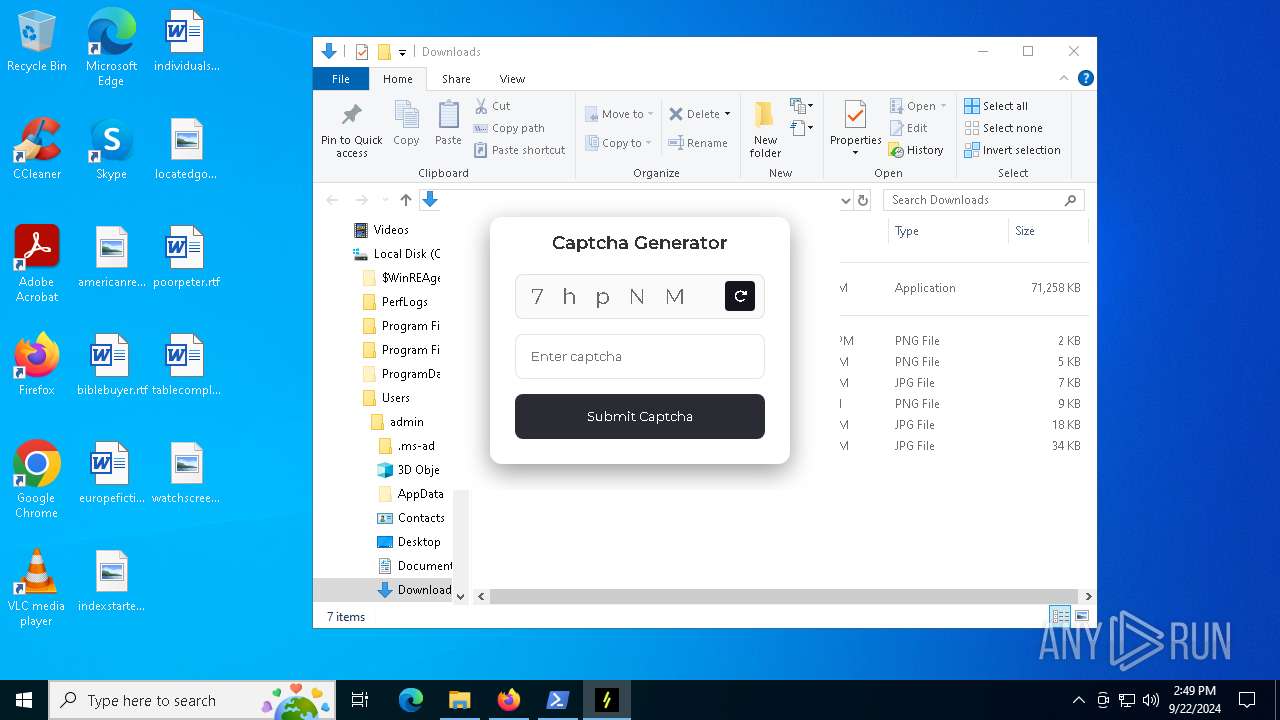
| URL: | nebulard.life |
| Full analysis: | https://app.any.run/tasks/7c210931-a038-402e-bef6-363db20d803a |
| Verdict: | Malicious activity |
| Analysis date: | September 22, 2024, 14:46:04 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 9B1B9B56B1CFE83D5ADD769045740B5C |
| SHA1: | BE7816D40CCF95CC19E81A4193E984BB7F68C18A |
| SHA256: | B9CE9DCBACDFA3F0F57313016E161FE365E883266CE3C3B0E0C0BFD7296052E7 |
| SSDEEP: | 3:i7CA:i+A |
MALICIOUS
Changes powershell execution policy (Unrestricted)
- Nebulard.exe (PID: 5276)
- Nebulard.exe (PID: 8388)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- NebulardGame.exe (PID: 7268)
- NebulardGame.exe (PID: 7820)
- old-uninstaller.exe (PID: 9084)
Get information on the list of running processes
- NebulardGame.exe (PID: 7268)
- cmd.exe (PID: 7140)
- NebulardGame.exe (PID: 7820)
- cmd.exe (PID: 3352)
- cmd.exe (PID: 8484)
- old-uninstaller.exe (PID: 9084)
Starts CMD.EXE for commands execution
- Nebulard.exe (PID: 4328)
- Nebulard.exe (PID: 5276)
- old-uninstaller.exe (PID: 9084)
- NebulardGame.exe (PID: 7820)
- Nebulard.exe (PID: 8388)
- Nebulard.exe (PID: 9204)
- NebulardGame.exe (PID: 7268)
Application launched itself
- Nebulard.exe (PID: 7832)
- Nebulard.exe (PID: 2368)
The process bypasses the loading of PowerShell profile settings
- Nebulard.exe (PID: 5276)
- Nebulard.exe (PID: 8388)
Starts POWERSHELL.EXE for commands execution
- Nebulard.exe (PID: 5276)
- Nebulard.exe (PID: 8388)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6388)
- cmd.exe (PID: 1692)
Executable content was dropped or overwritten
- NebulardGame.exe (PID: 7820)
- old-uninstaller.exe (PID: 9084)
- NebulardGame.exe (PID: 7268)
Starts application with an unusual extension
- cmd.exe (PID: 1712)
- cmd.exe (PID: 6388)
- cmd.exe (PID: 6344)
- cmd.exe (PID: 4820)
The process hides Powershell's copyright startup banner
- Nebulard.exe (PID: 5276)
- Nebulard.exe (PID: 8388)
Process drops legitimate windows executable
- NebulardGame.exe (PID: 7820)
- old-uninstaller.exe (PID: 9084)
- NebulardGame.exe (PID: 7268)
Drops 7-zip archiver for unpacking
- NebulardGame.exe (PID: 7820)
- NebulardGame.exe (PID: 7268)
INFO
Executable content was dropped or overwritten
- firefox.exe (PID: 5072)
Application launched itself
- firefox.exe (PID: 5524)
- firefox.exe (PID: 5072)
Manual execution by a user
- powershell.exe (PID: 4308)
- Nebulard.exe (PID: 7832)
- Nebulard.exe (PID: 2368)
Connects to unusual port
- firefox.exe (PID: 5072)
Changes the display of characters in the console
- cmd.exe (PID: 1712)
- cmd.exe (PID: 6388)
- cmd.exe (PID: 6344)
- cmd.exe (PID: 4820)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
292
Monitored processes
152
Malicious processes
4
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 736 | findstr /C:"Detected boot environment" "C:\WINDOWS\Panther\setupact.log" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 864 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2856 -childID 1 -isForBrowser -prefsHandle 2912 -prefMapHandle 2964 -prefsLen 26706 -prefMapSize 244343 -jsInitHandle 1280 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {ecaf8e3b-bfbc-4b58-a414-cc8ea8d10939} 5072 "\\.\pipe\gecko-crash-server-pipe.5072" 27621c6d150 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 904 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1048 | powershell.exe -NoProfile -NoLogo -InputFormat Text -NoExit -ExecutionPolicy Unrestricted -Command - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Nebulard.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1048 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1108 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=6360 -parentBuildID 20240213221259 -sandboxingKind 1 -prefsHandle 6120 -prefMapHandle 6344 -prefsLen 34713 -prefMapSize 244343 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {d001122b-e83b-4985-aabc-7bf8cbf4a334} 5072 "\\.\pipe\gecko-crash-server-pipe.5072" 2762750dd10 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1420 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=6072 -parentBuildID 20240213221259 -prefsHandle 6308 -prefMapHandle 6140 -prefsLen 34713 -prefMapSize 244343 -appDir "C:\Program Files\Mozilla Firefox\browser" - {acece758-632e-48de-b21c-e9641125e1e5} 5072 "\\.\pipe\gecko-crash-server-pipe.5072" 27627b33d10 rdd | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1488 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1500 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
Total events
37 192
Read events
37 161
Write events
13
Delete events
18
Modification events
| (PID) Process: | (5072) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (7268) NebulardGame.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\9564a7c5-e811-5054-8531-3e0680b94024 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Local\Programs\Nebulard | |||
| (PID) Process: | (7268) NebulardGame.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\9564a7c5-e811-5054-8531-3e0680b94024 |
| Operation: | write | Name: | KeepShortcuts |
Value: true | |||
| (PID) Process: | (7268) NebulardGame.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\9564a7c5-e811-5054-8531-3e0680b94024 |
| Operation: | write | Name: | ShortcutName |
Value: Nebulard | |||
| (PID) Process: | (7268) NebulardGame.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\9564a7c5-e811-5054-8531-3e0680b94024 |
| Operation: | write | Name: | DisplayName |
Value: Nebulard 3.5.4 | |||
| (PID) Process: | (7268) NebulardGame.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\9564a7c5-e811-5054-8531-3e0680b94024 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Users\admin\AppData\Local\Programs\Nebulard\Uninstall Nebulard.exe" /currentuser | |||
| (PID) Process: | (7268) NebulardGame.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\9564a7c5-e811-5054-8531-3e0680b94024 |
| Operation: | write | Name: | QuietUninstallString |
Value: "C:\Users\admin\AppData\Local\Programs\Nebulard\Uninstall Nebulard.exe" /currentuser /S | |||
| (PID) Process: | (7268) NebulardGame.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\9564a7c5-e811-5054-8531-3e0680b94024 |
| Operation: | write | Name: | DisplayVersion |
Value: 3.5.4 | |||
| (PID) Process: | (7268) NebulardGame.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\9564a7c5-e811-5054-8531-3e0680b94024 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Users\admin\AppData\Local\Programs\Nebulard\Nebulard.exe,0 | |||
| (PID) Process: | (7268) NebulardGame.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\9564a7c5-e811-5054-8531-3e0680b94024 |
| Operation: | write | Name: | Publisher |
Value: Nebulard | |||
Executable files
56
Suspicious files
512
Text files
146
Unknown types
29
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 5072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 5072 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 5072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:7A97B8DBC4F98D175F958C00F463A52A | SHA256:92074D2ED1AA1FD621287E35DB9EF1AE3DC04777EFAE5F09E7A3B4534C201548 | |||
| 5072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:7A97B8DBC4F98D175F958C00F463A52A | SHA256:92074D2ED1AA1FD621287E35DB9EF1AE3DC04777EFAE5F09E7A3B4534C201548 | |||
| 5072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:4BE1FE51AEB1B76CBC933BAE359EDD80 | SHA256:B87DF4A58F0D9AB013E26482E07D8C05158E20C649476A7845B69DDACB42DBB8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
157
TCP/UDP connections
140
DNS requests
191
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5072 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
5072 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
5072 | firefox.exe | POST | 200 | 184.24.77.73:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
5072 | firefox.exe | GET | 200 | 172.67.143.13:80 | http://nebulard.life/ | unknown | — | — | unknown |
5072 | firefox.exe | POST | 200 | 184.24.77.73:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
5072 | firefox.exe | POST | 200 | 216.58.206.67:80 | http://o.pki.goog/s/wr3/XjA | unknown | — | — | unknown |
5072 | firefox.exe | POST | 200 | 184.24.77.73:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
5072 | firefox.exe | POST | 200 | 216.58.206.67:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
5072 | firefox.exe | GET | 200 | 172.67.143.13:80 | http://nebulard.life/_next/static/media/ca47a8ce01299a91-s.p.woff2 | unknown | — | — | unknown |
5072 | firefox.exe | GET | — | 172.67.143.13:80 | http://nebulard.life/_next/static/chunks/webpack-605032c08c2b5ea2.js | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
740 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6908 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5072 | firefox.exe | 172.67.143.13:80 | nebulard.life | CLOUDFLARENET | US | unknown |
5072 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
5072 | firefox.exe | 34.117.188.166:443 | contile.services.mozilla.com | — | — | whitelisted |
5072 | firefox.exe | 142.250.181.234:443 | safebrowsing.googleapis.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
nebulard.life |
| unknown |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
ipv4only.arpa |
| whitelisted |
example.org |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
prod.ads.prod.webservices.mozgcp.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
2256 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
2256 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |