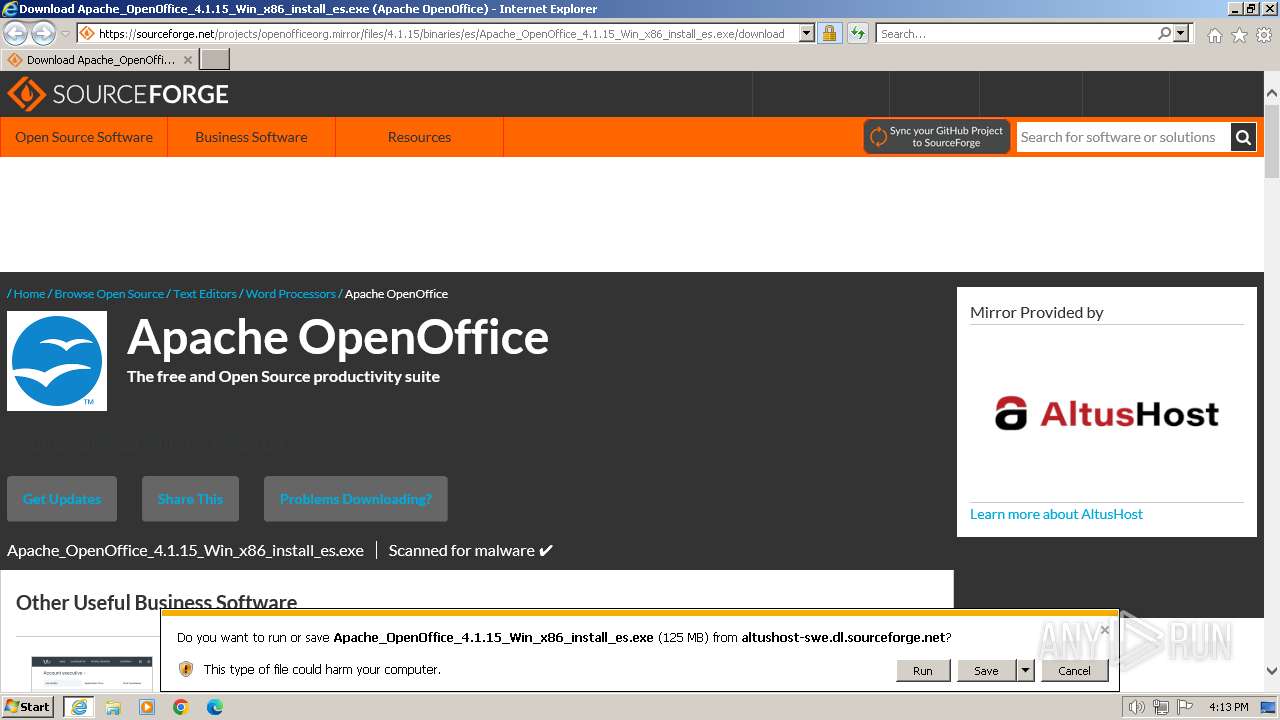
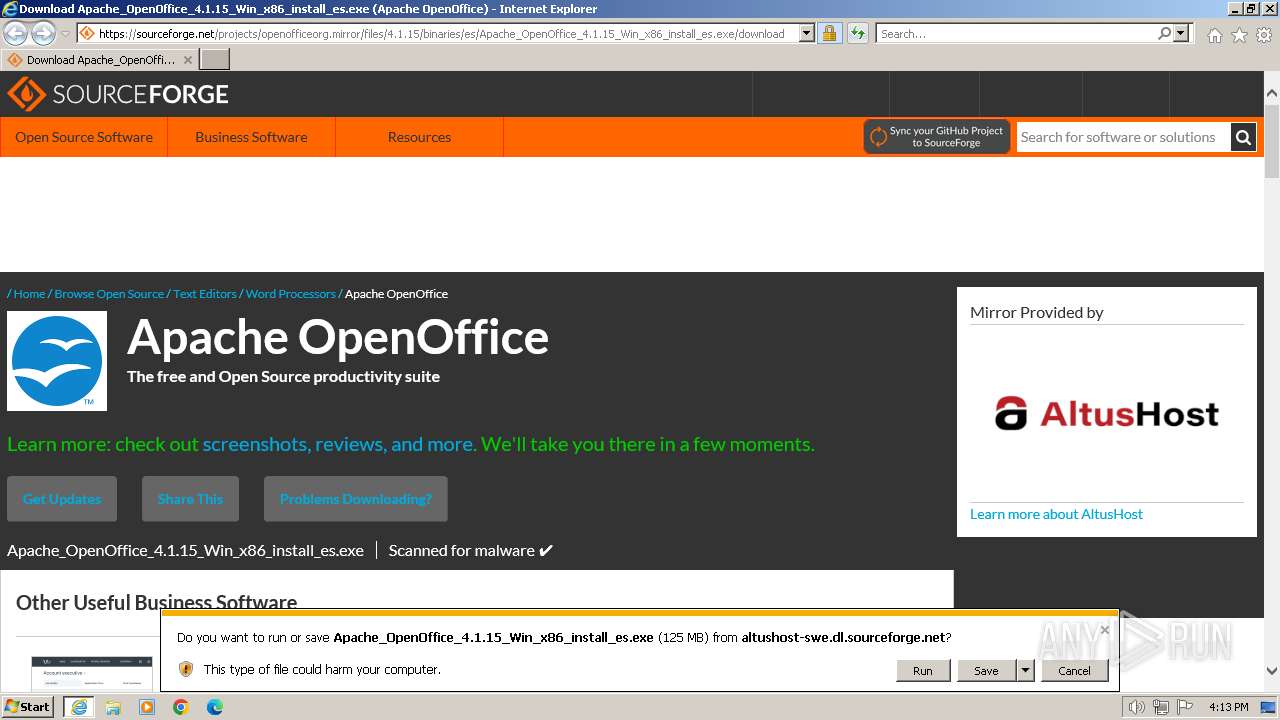
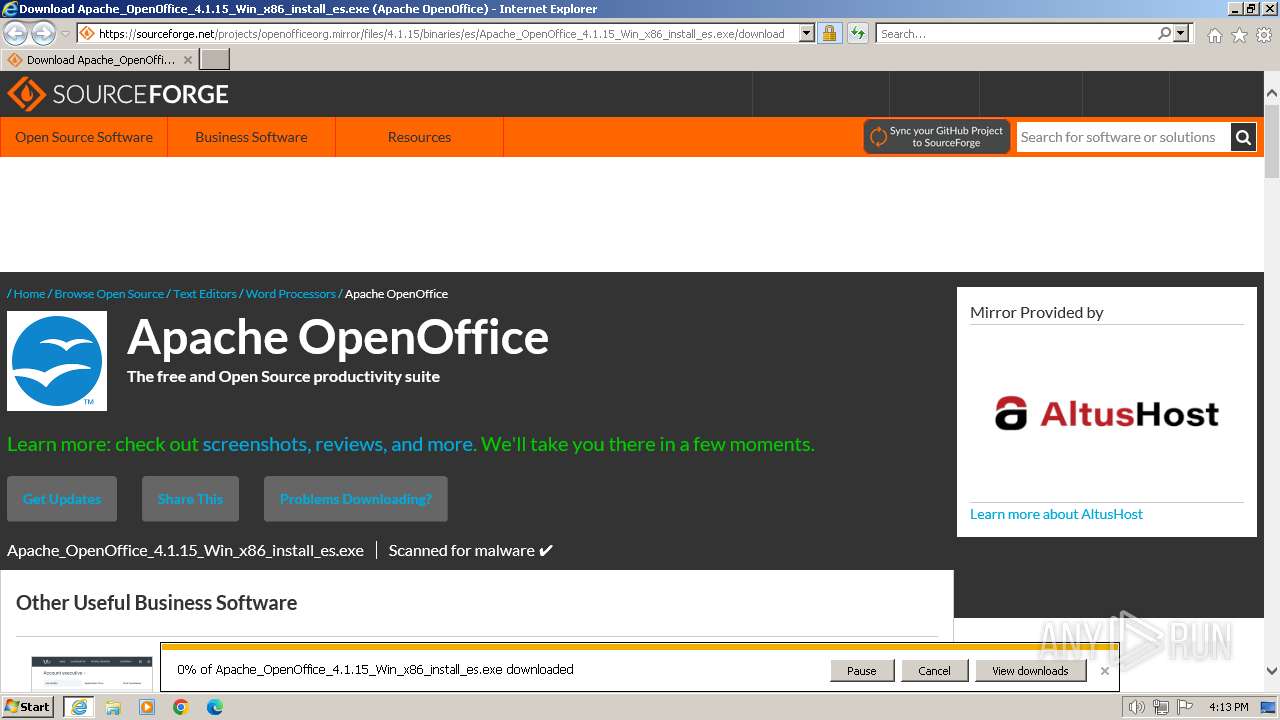
| URL: | https://sourceforge.net/projects/openofficeorg.mirror/files/4.1.15/binaries/es/Apache_OpenOffice_4.1.15_Win_x86_install_es.exe |
| Full analysis: | https://app.any.run/tasks/71118cbb-abc7-4e75-9ba3-a289d5f0b1cd |
| Verdict: | Malicious activity |
| Analysis date: | January 19, 2024, 16:12:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | F4EB4E3407842F3C8BD030A99633D80D |
| SHA1: | 6446DF84921F77198F6E1B8644E9FDE1C9969DE8 |
| SHA256: | B9C336A32FDC75AF376324A275DF09121C395A1610ED58528298A742C3A6EBAA |
| SSDEEP: | 3:N8HCGSuLAuUt6DMzLxKXYMURggBWiSBVlfggUK3k0nAdA:2iGnCt6QzLqIg7BVORK3k04A |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 120)
Executable content was dropped or overwritten
- iexplore.exe (PID: 392)
Drops the executable file immediately after the start
- iexplore.exe (PID: 392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
36
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://sourceforge.net/projects/openofficeorg.mirror/files/4.1.15/binaries/es/Apache_OpenOffice_4.1.15_Win_x86_install_es.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 392 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:120 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
19 501
Read events
19 422
Write events
77
Delete events
2
Modification events
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
1
Suspicious files
35
Text files
61
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:D807B476C5C907173B5F29F0F9E661F3 | SHA256:013DE98E6DC947A698044BC4BDEFDE062543082116FAA883EC4D9D8F7EE70A56 | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\CO2ZQRAV.txt | text | |
MD5:7495C9566B073E090019B3EA49063C79 | SHA256:E62155122A7BBD1E8C77B540837480B19EE3A3D55C43BD50279C8ACEB1C34AC3 | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\sf.sandiego-cmp-top[1].js | html | |
MD5:C3C9DA61F2361CC9A5CC5FB102565F53 | SHA256:1D48F195B9979C2845D7E803A67DD5ADD33B7CF136770ECE36C9F78EEAA593D3 | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\sf.sandiego-head[1].js | text | |
MD5:D05F98B211F1AC879F9378468F3D6649 | SHA256:981BB3EEE156C83AFDED72FAD8F7CD5ECCE65B769E1FA842AC9E356CBA4530D9 | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\download[1].htm | html | |
MD5:877455BDC7378D499B09D08D7A23CD6A | SHA256:984B956C4F53BB40B0A1B5610F3790B54C60A65D2E7C2676ADAD3E2ACA3956DE | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\sf.sandiego-foundation-base[1].js | text | |
MD5:F23FBD469BB0D9569486B62E2C50D996 | SHA256:D30C030593AEE31E4BDD1A458E6739DF804F6D50012D2E3141D585B4ACF91A08 | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\altushost-xlarge[1].png | image | |
MD5:294EAF667826B502295BA3FA9AF91846 | SHA256:AC7CB388ED6E57EC2EF2E9F3E7981EEC5D5FCFB8BAE6A34B1D7B0D351F9626A6 | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\github-sync[1].png | image | |
MD5:4A6DCE1E1233DA9CE4605000A63B81DC | SHA256:DA0649DC53EAE2E0F5982186C3D53DFBF9D11BE57B69127C6BB2DC18D11BF309 | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\cmp[1].css | text | |
MD5:38C8ACF2B4EF7DEF65BACFB6E9A26E8E | SHA256:4BAAE150A27BC5716BA8F5160FBD2414F5B731C470D8EE0956612DAFA106E950 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
54
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
392 | iexplore.exe | GET | 200 | 2.19.105.18:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
392 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?8755180817ac8ab5 | unknown | compressed | 65.2 Kb | unknown |
392 | iexplore.exe | GET | 200 | 95.101.54.137:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgR%2B5rJNDRLPmf6wKNriwkmuQQ%3D%3D | unknown | binary | 503 b | unknown |
120 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1a6e676fbb64f2cc | unknown | — | — | unknown |
120 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a85e8d0c2f0a71a5 | unknown | — | — | unknown |
392 | iexplore.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIAjrICMzZli2TN25s%3D | unknown | binary | 724 b | unknown |
392 | iexplore.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
392 | iexplore.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
392 | iexplore.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIAjrICMzZli2TN25s%3D | unknown | binary | 724 b | unknown |
120 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 312 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
392 | iexplore.exe | 172.64.150.145:443 | sourceforge.net | CLOUDFLARENET | US | unknown |
392 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
392 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
392 | iexplore.exe | 172.64.147.47:443 | a.fsdn.com | CLOUDFLARENET | US | unknown |
392 | iexplore.exe | 104.16.57.101:443 | static.cloudflareinsights.com | CLOUDFLARENET | — | unknown |
392 | iexplore.exe | 87.230.98.76:443 | d.delivery.consentmanager.net | PlusServer GmbH | DE | unknown |
392 | iexplore.exe | 212.102.56.178:443 | cdn.consentmanager.net | Datacamp Limited | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
sourceforge.net |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
a.fsdn.com |
| whitelisted |
static.cloudflareinsights.com |
| whitelisted |
d.delivery.consentmanager.net |
| unknown |
cdn.consentmanager.net |
| malicious |
x1.c.lencr.org |
| whitelisted |
c.sf-syn.com |
| whitelisted |
r3.o.lencr.org |
| shared |