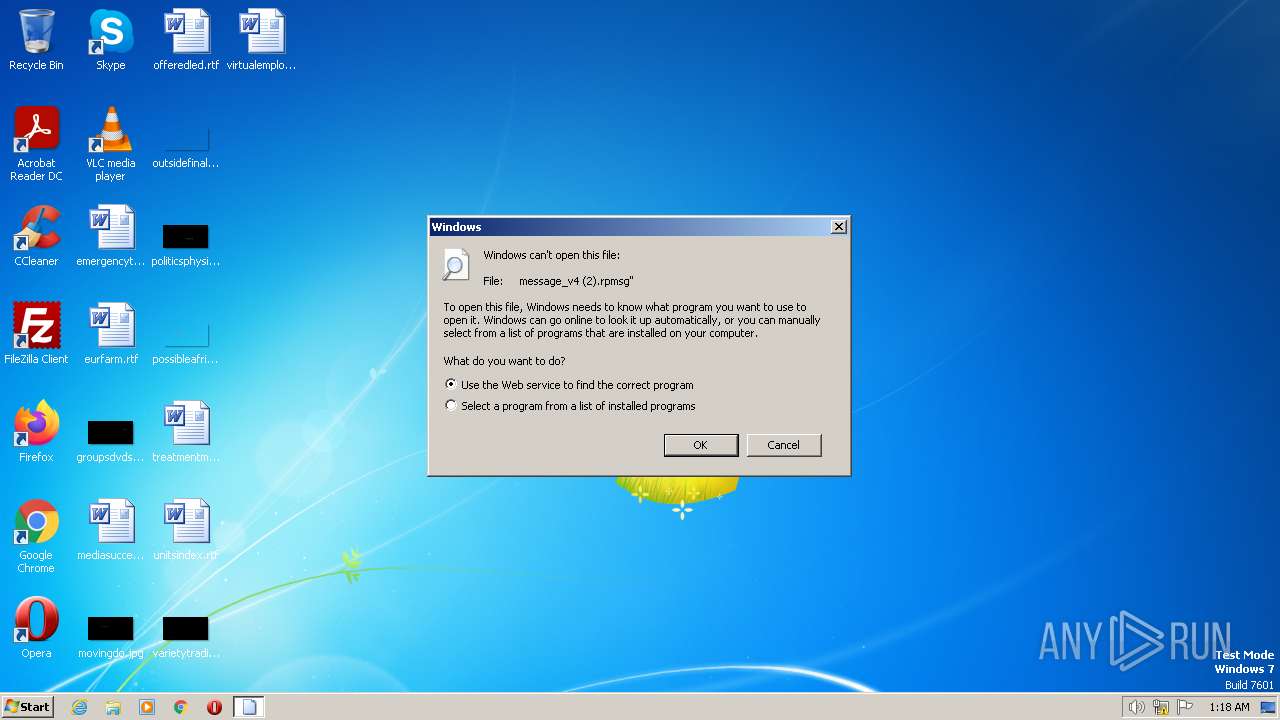
| File name: | message_v4 (2).rpmsg |
| Full analysis: | https://app.any.run/tasks/e96aaa88-07b6-40c5-a056-1cc049b3099d |
| Verdict: | Malicious activity |
| Analysis date: | May 12, 2023, 00:18:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | rpmsg Restricted Permission Message |
| MD5: | E43BDBBAFA860A526CC21037406FE33A |
| SHA1: | 22CE1D882F996BD137DCAF8A6A69440EDE50FE21 |
| SHA256: | B9B7B15E0D9D8CF655E32273249E22B8D62BE51A4C25AFACC226360AE0C29FD5 |
| SSDEEP: | 1536:yAwRmxQ5ccYMCpI3hz+2qgQWpCWWdPDFPsvbmhMDHsOlqb:smxeYMCK3N+2qgQWpCH5UvbE6HFW |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Internet Settings
- wmplayer.exe (PID: 1756)
- setup_wm.exe (PID: 2644)
- rundll32.exe (PID: 3308)
- wmplayer.exe (PID: 3828)
INFO
Create files in a temporary directory
- setup_wm.exe (PID: 2644)
- iexplore.exe (PID: 3292)
- wmplayer.exe (PID: 3828)
Reads the computer name
- wmplayer.exe (PID: 1756)
- setup_wm.exe (PID: 2644)
- wmpshare.exe (PID: 3940)
- wmplayer.exe (PID: 3828)
Checks supported languages
- setup_wm.exe (PID: 2644)
- wmplayer.exe (PID: 1756)
- wmplayer.exe (PID: 3828)
- wmpshare.exe (PID: 3940)
Process checks computer location settings
- setup_wm.exe (PID: 2644)
- wmplayer.exe (PID: 3828)
Reads the machine GUID from the registry
- setup_wm.exe (PID: 2644)
- wmplayer.exe (PID: 3828)
Application launched itself
- iexplore.exe (PID: 3292)
Reads Environment values
- setup_wm.exe (PID: 2644)
Manual execution by a user
- wmplayer.exe (PID: 1756)
The process checks LSA protection
- unregmp2.exe (PID: 3756)
- wmplayer.exe (PID: 1756)
- unregmp2.exe (PID: 4076)
- setup_wm.exe (PID: 2644)
- wmpshare.exe (PID: 3940)
- wmplayer.exe (PID: 3828)
Checks proxy server information
- wmplayer.exe (PID: 3828)
Creates files or folders in the user directory
- wmplayer.exe (PID: 3828)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rpmsg | | | Restricted-Permission Message (100) |
|---|
Total processes
47
Monitored processes
9
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1756 | "C:\Program Files\Windows Media Player\wmplayer.exe" /prefetch:1 | C:\Program Files\Windows Media Player\wmplayer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Exit code: 0 Version: 12.0.7601.23517 (win7sp1_ldr.160812-0732) Modules
| |||||||||||||||
| 2360 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3292 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2644 | "C:\Program Files\Windows Media Player\setup_wm.exe" /RunOnce:"C:\Program Files\Windows Media Player\wmplayer.exe" /prefetch:1 | C:\Program Files\Windows Media Player\setup_wm.exe | — | wmplayer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Media Configuration Utility Exit code: 1 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3292 | "C:\Program Files\Internet Explorer\iexplore.exe" http://go.microsoft.com/fwlink/?LinkId=57426&Ext=rpmsg" | C:\Program Files\Internet Explorer\iexplore.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3308 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL "C:\Users\admin\AppData\Local\Temp\message_v4 (2).rpmsg" | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3756 | C:\Windows\system32\unregmp2.exe /ShowWMP /SetShowState /CreateMediaLibrary | C:\Windows\System32\unregmp2.exe | — | setup_wm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Media Player Setup Utility Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3828 | "C:\Program Files\Windows Media Player\wmplayer.exe" /Relaunch /prefetch:1 | C:\Program Files\Windows Media Player\wmplayer.exe | setup_wm.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Exit code: 0 Version: 12.0.7601.23517 (win7sp1_ldr.160812-0732) Modules
| |||||||||||||||
| 3940 | "C:\Program Files\Windows Media Player\wmpshare.exe" | C:\Program Files\Windows Media Player\wmpshare.exe | — | wmplayer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Folder Sharing Executable Exit code: 0 Version: 12.0.7601.24499 (win7sp1_ldr.190612-0600) Modules
| |||||||||||||||
| 4076 | "C:\Windows\system32\unregmp2.exe" /PerformIndivIfNeeded | C:\Windows\System32\unregmp2.exe | — | setup_wm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Media Player Setup Utility Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
36 121
Read events
35 705
Write events
414
Delete events
2
Modification events
| (PID) Process: | (3292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
27
Text files
236
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2360 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80237EE4964FC9C409AAF55BF996A292_E503B048B745DFA14B81FCFC68D6DECE | binary | |
MD5:DC1B9D40DD537E4CEE9124C18456492F | SHA256:1315EA77FF7B30D0D671DC612C1C884D39CA612062B1C63EB6A6CC9E56F8E517 | |||
| 2360 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:F1F8C3725F50C41FBA97791E6E505FC4 | SHA256:7B77791AE1D9D588AD73AA9FD305DE4BA00CC4845628DB7D74DEF5BFD40B4563 | |||
| 2360 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 2360 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\OB93JEAP.txt | text | |
MD5:F541CA4B875CFF52E5655B8FCFE3D0D1 | SHA256:F136A5D8CFF6E50764B37C044009B33B578CE96A00B70C3F80EA91028780B1F4 | |||
| 2360 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:A74B0BFDCBB756C3B1D388619D1C07FB | SHA256:05852594129B0C220D9A11AAE5F71C0C85DF701F1E9A7A658A5C585C888CFF35 | |||
| 2360 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\3JS3scyHYOsbHYTUTZDQNS8N8Xw.gz[1].js | text | |
MD5:56B91EAB01144DB91D100617BA0EF2A6 | SHA256:EE7F4B86A5C2B3D2781D6A0BA8F3DEFF6EF943D21A5A92F435453C87B99F9509 | |||
| 2360 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\4ZS5D9N6.txt | text | |
MD5:2DB156B1CE290EF1642A4DF3384AE2A7 | SHA256:D82F7F426E7B2B1A3F39D6FAA324338922FF3B0F0B908BF5E893C26769B1411C | |||
| 2360 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\6WhG5kBfBZsDwUbrxVQplRLS1b0.gz[1].js | text | |
MD5:1E2C0702C1245FB906C74E95D4841EF2 | SHA256:B7607C3C95C96BC713D487E91A9FD2FCF4B1981593AC9FCE5725B8129091C579 | |||
| 2360 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\JF1R2IU6.txt | text | |
MD5:370FFD05DBA8561F940C34FFD224FE1D | SHA256:6EB2C7F4DE4177C4AE62F6978A8A1122AC5EFAD93CE9CEE3952CFA2DFF131797 | |||
| 2360 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\80237EE4964FC9C409AAF55BF996A292_E503B048B745DFA14B81FCFC68D6DECE | binary | |
MD5:0704BEB02D6E1E4B5BFFE088D4804D16 | SHA256:49627F0D0C25AF0660996980A2AC235E91E64EE68CD78BE3937397029B079FF0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
27
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2360 | iexplore.exe | GET | 301 | 23.33.118.33:80 | http://shell.windows.com/fileassoc/fileassoc.asp?Ext=rpmsg%22 | US | — | — | whitelisted |
3828 | wmplayer.exe | GET | 200 | 23.33.118.11:80 | http://images.windowsmedia.com/svcswitch/media_guide_16x16.png | US | image | 897 b | whitelisted |
2360 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3828 | wmplayer.exe | GET | 200 | 23.33.118.16:80 | http://onlinestores.metaservices.microsoft.com/serviceswitching/AllServices.aspx?sv=5&locale=409&geoid=f4&version=12.0.7601.24499&userlocale=409 | US | xml | 546 b | whitelisted |
3828 | wmplayer.exe | GET | 200 | 23.33.118.16:80 | http://onlinestores.metaservices.microsoft.com/bing/bing.xml?locale=409&geoid=f4&version=12.0.7601.24499&userlocale=409 | US | text | 523 b | whitelisted |
2360 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
2360 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?dbc1c67960d08081 | US | compressed | 4.70 Kb | whitelisted |
2360 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3267496a6f178f37 | US | compressed | 4.70 Kb | whitelisted |
2360 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | binary | 471 b | whitelisted |
3828 | wmplayer.exe | GET | 302 | 23.33.118.11:80 | http://redir.metaservices.microsoft.com/redir/allservices/?sv=5&locale=409&geoid=f4&version=12.0.7601.24499&userlocale=409 | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2360 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2360 | iexplore.exe | 40.126.31.67:443 | login.microsoftonline.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2360 | iexplore.exe | 2.22.197.32:443 | go.microsoft.com | AKAMAI-AS | FR | unknown |
— | — | 23.33.118.11:80 | redir.metaservices.microsoft.com | Akamai International B.V. | CH | suspicious |
— | — | 23.33.118.16:80 | onlinestores.metaservices.microsoft.com | Akamai International B.V. | CH | unknown |
3292 | iexplore.exe | 92.123.100.177:443 | www.bing.com | Akamai International B.V. | FR | unknown |
2360 | iexplore.exe | 92.123.100.177:443 | www.bing.com | Akamai International B.V. | FR | unknown |
3828 | wmplayer.exe | 23.33.118.11:80 | redir.metaservices.microsoft.com | Akamai International B.V. | CH | suspicious |
2360 | iexplore.exe | 95.101.110.57:443 | r.bing.com | TELXIUS TELXIUS Cable | NL | unknown |
2360 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
shell.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
api.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
th.bing.com |
| whitelisted |
login.microsoftonline.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |