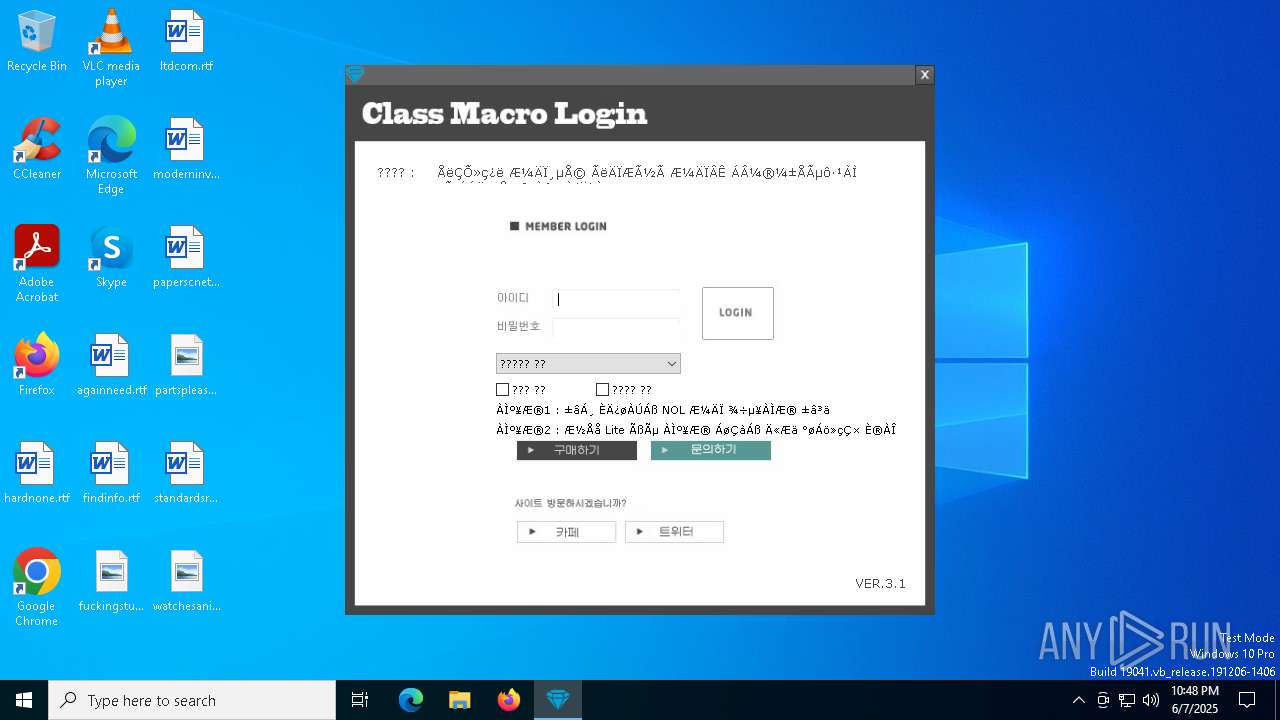
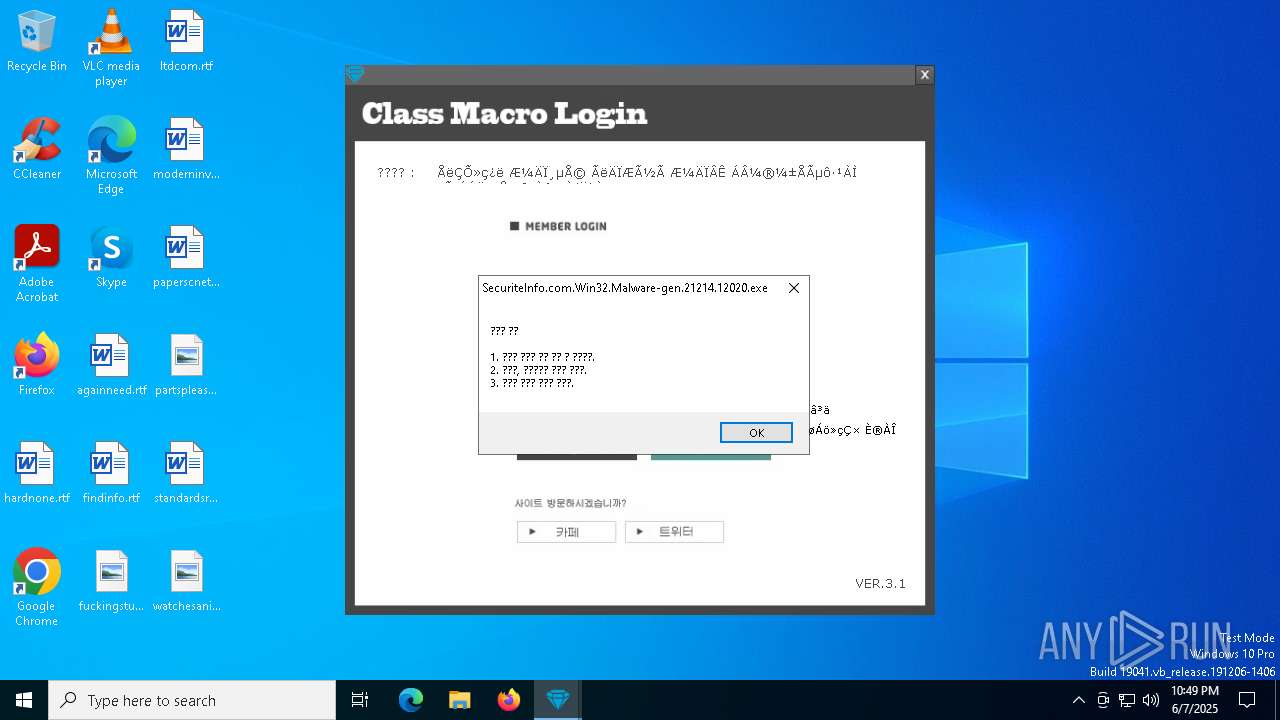
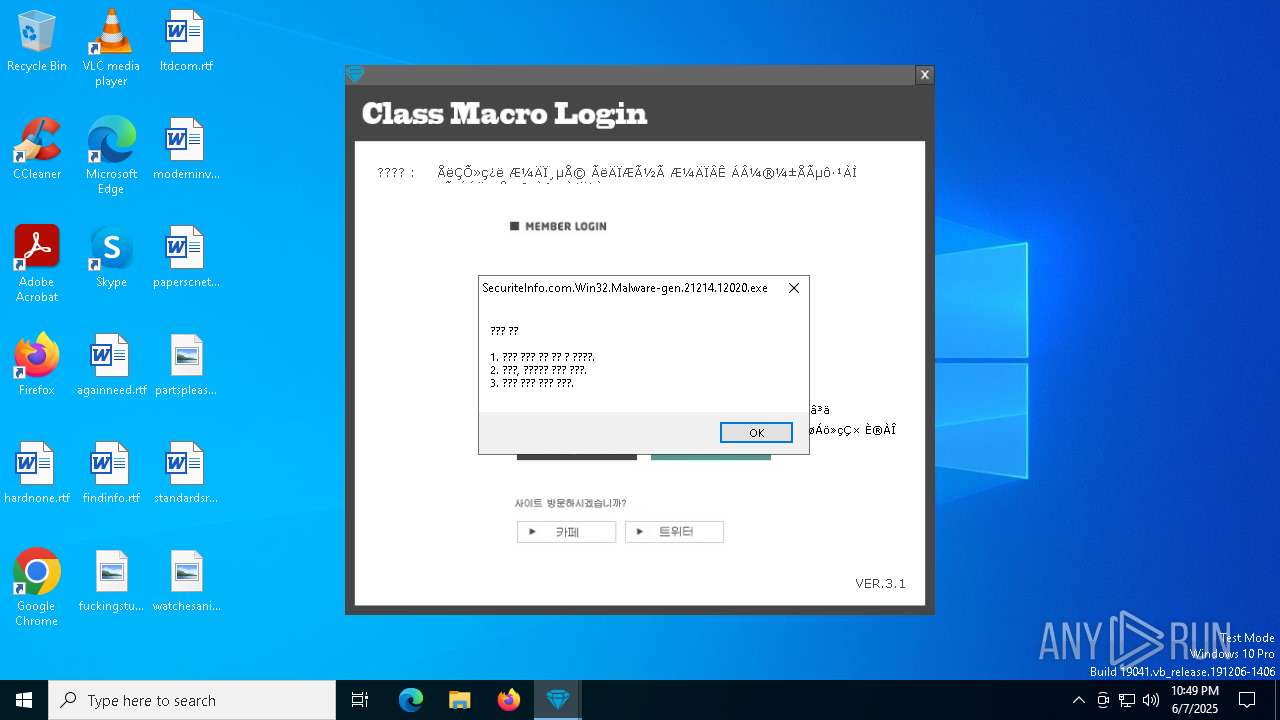
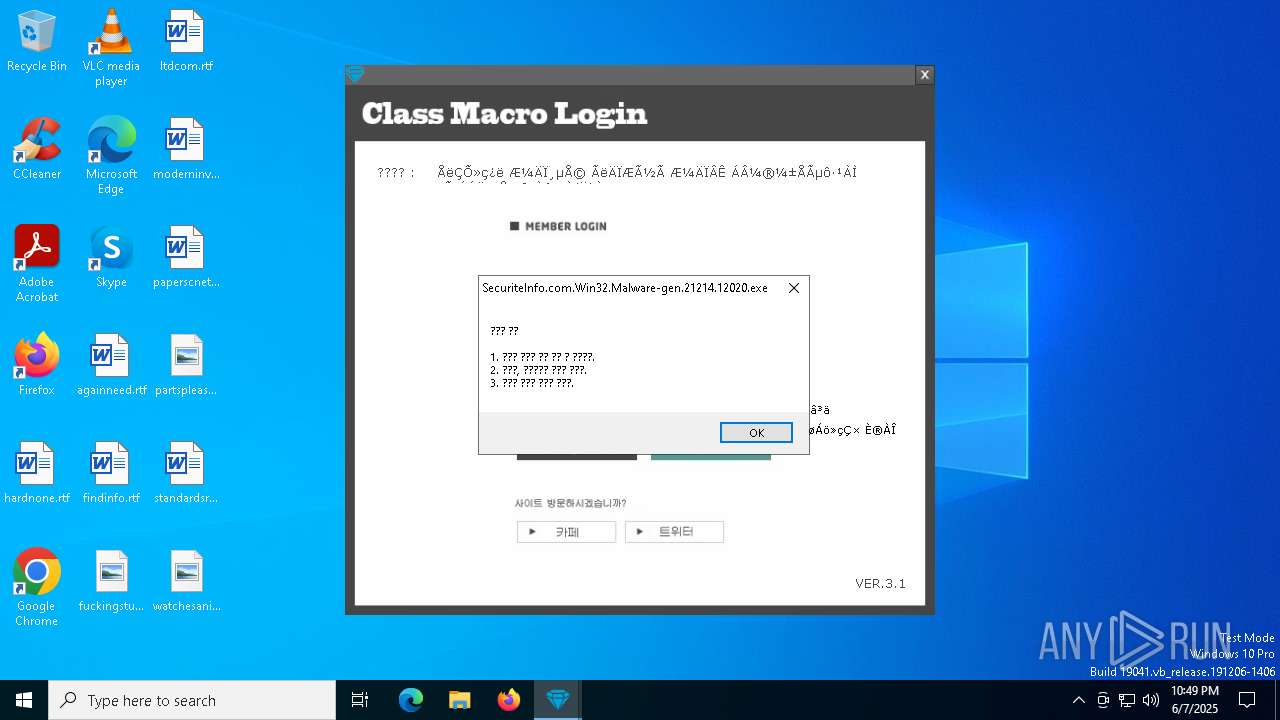
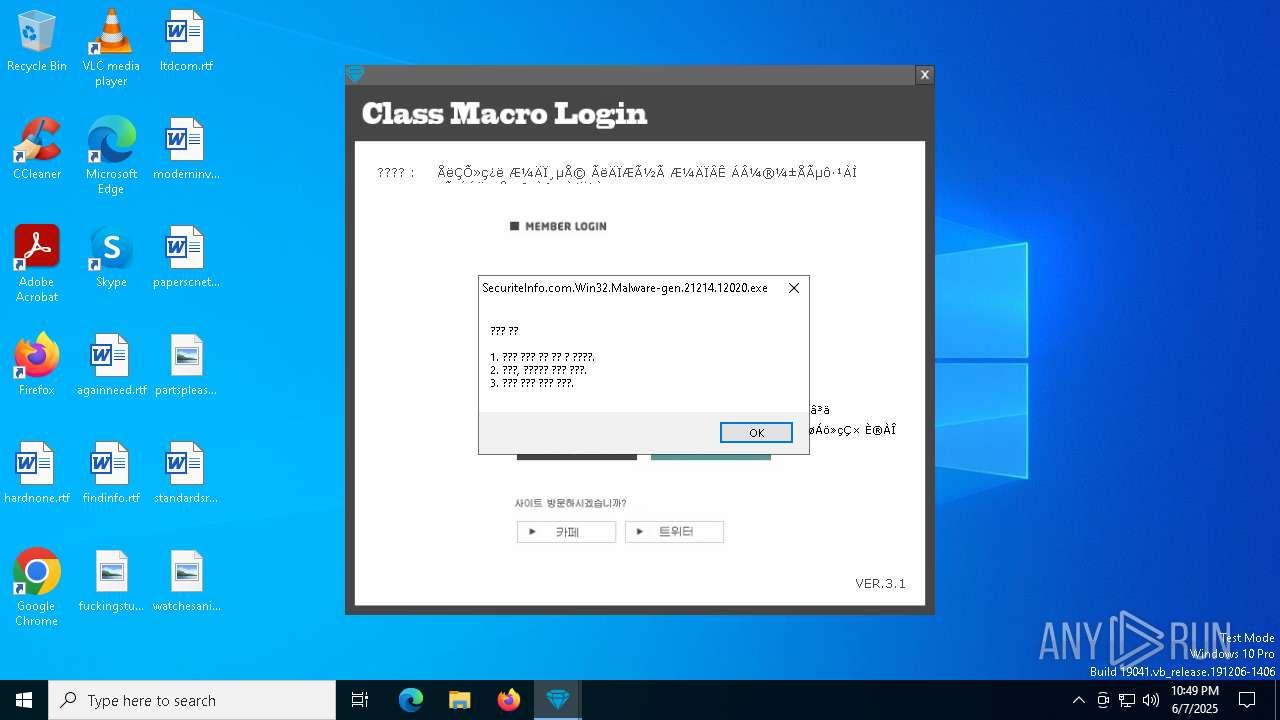
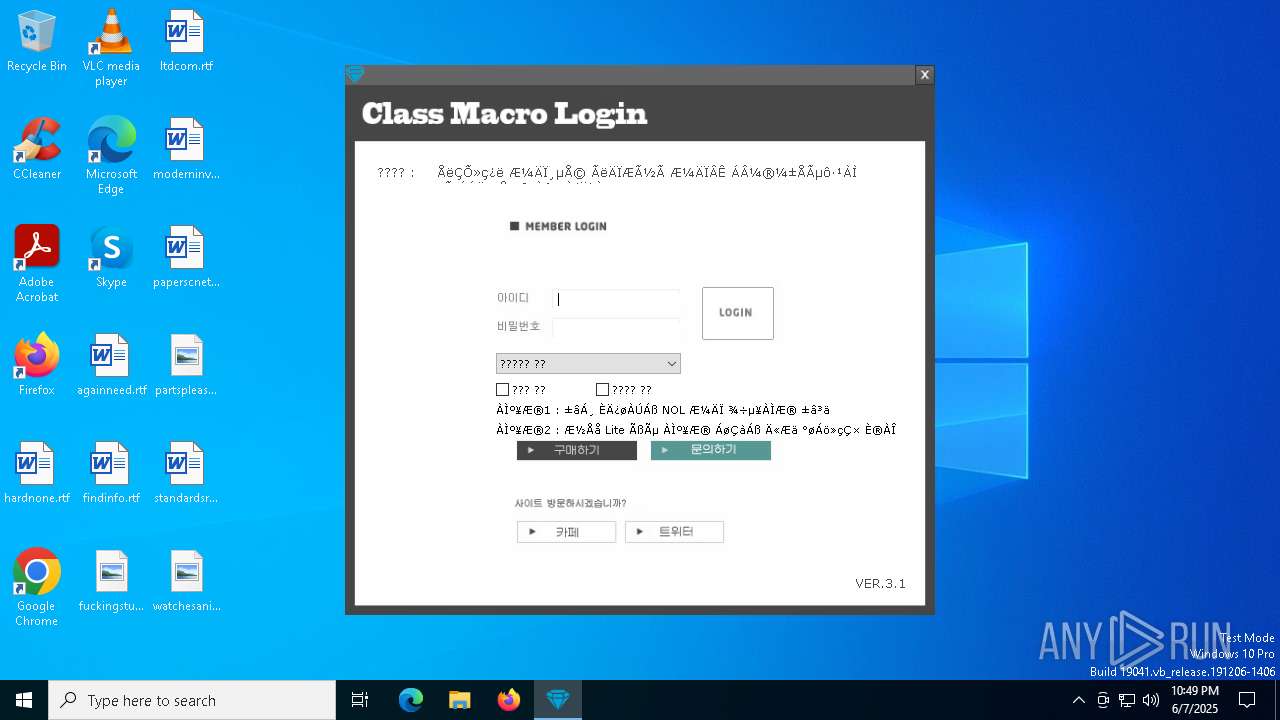
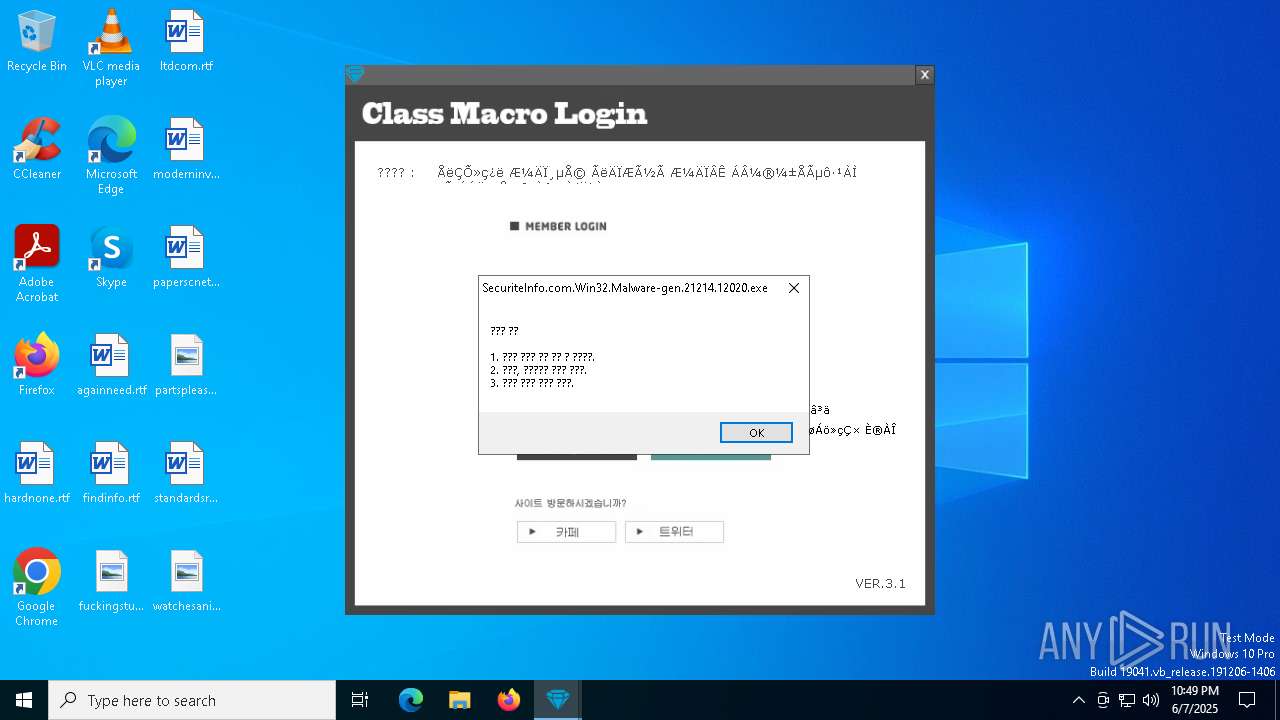
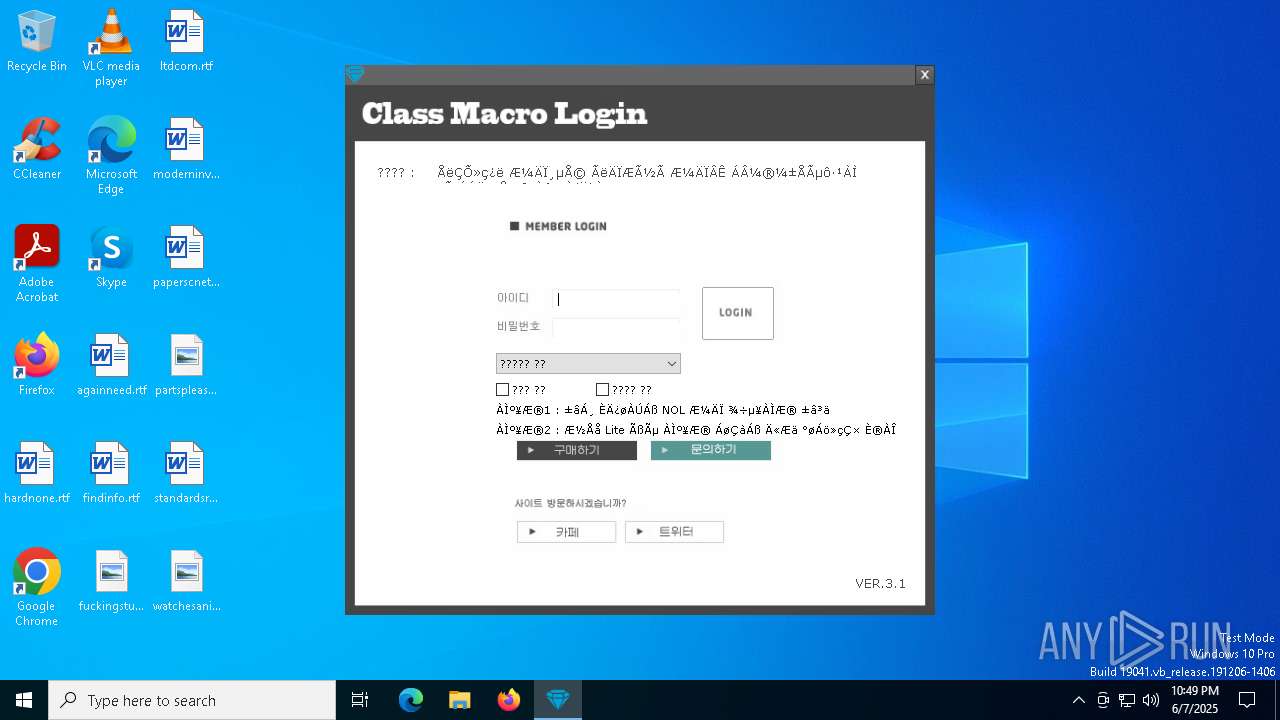
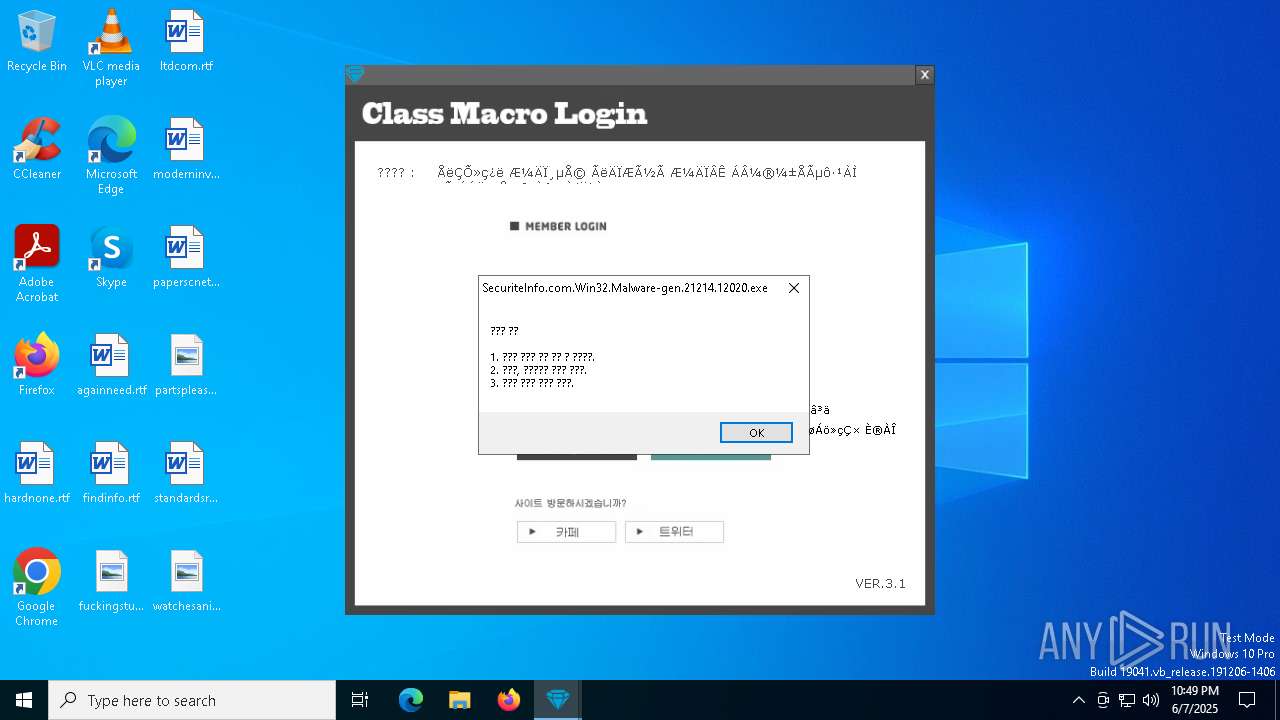
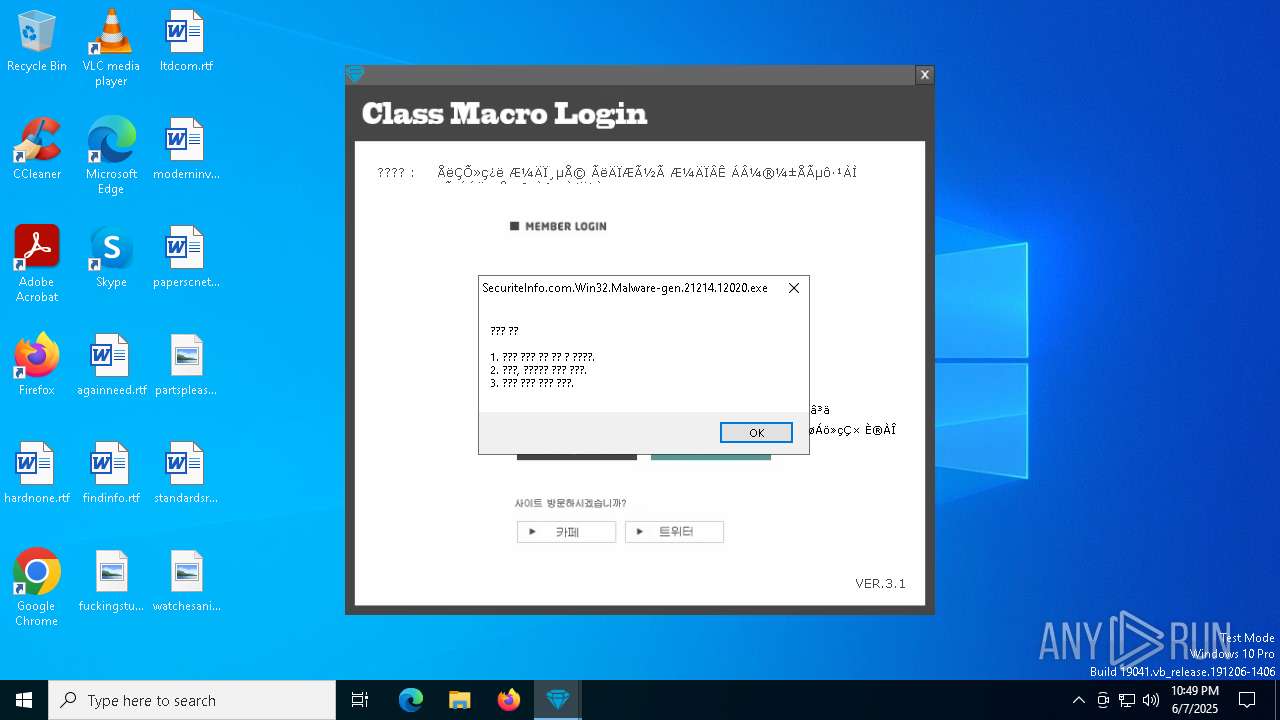
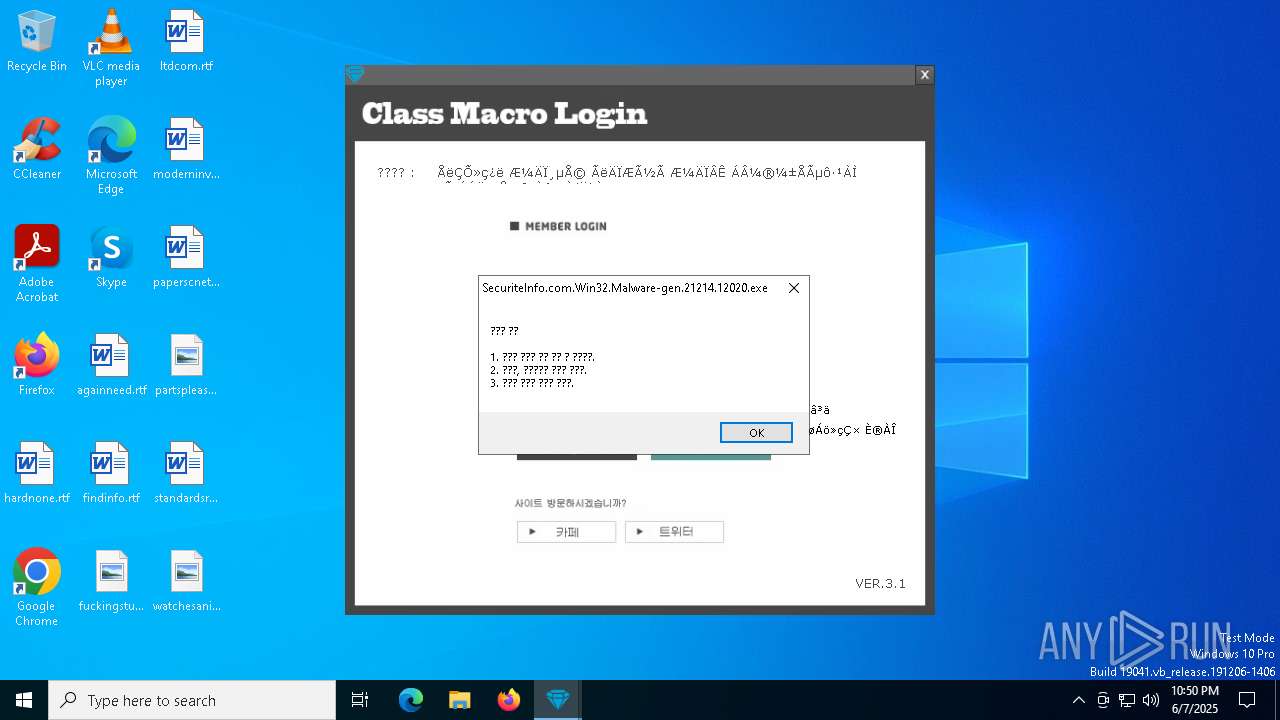
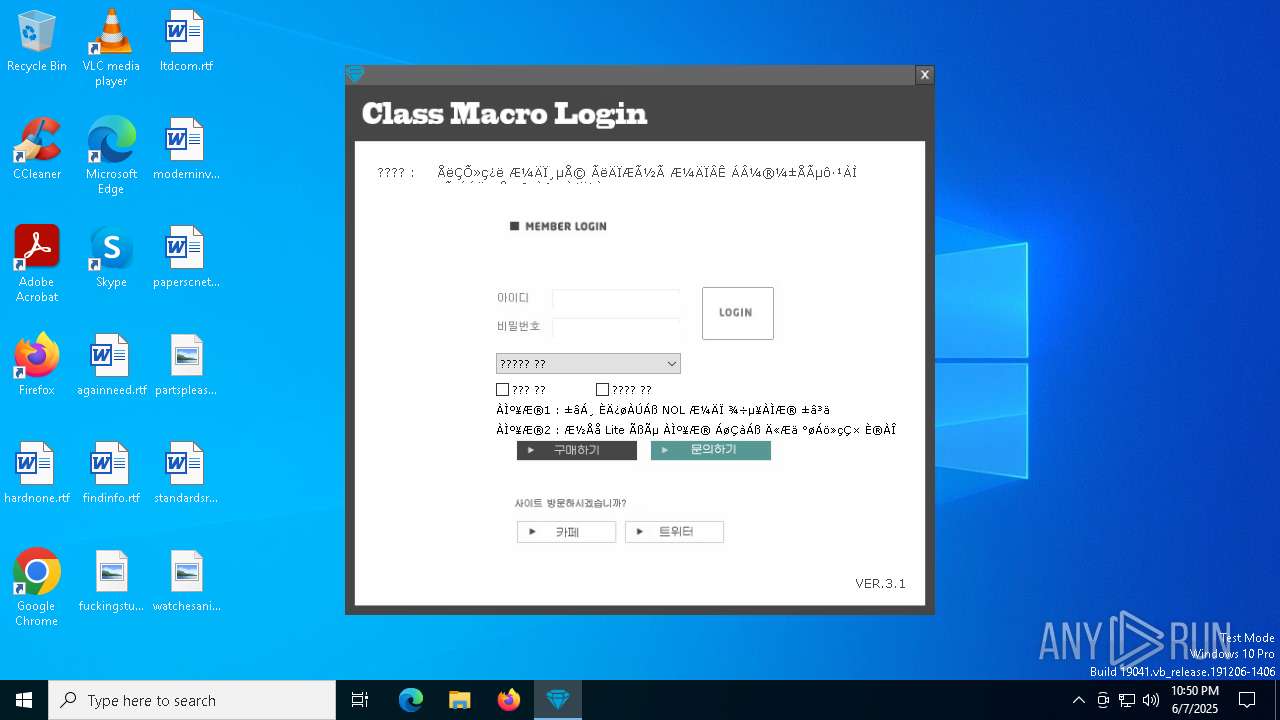
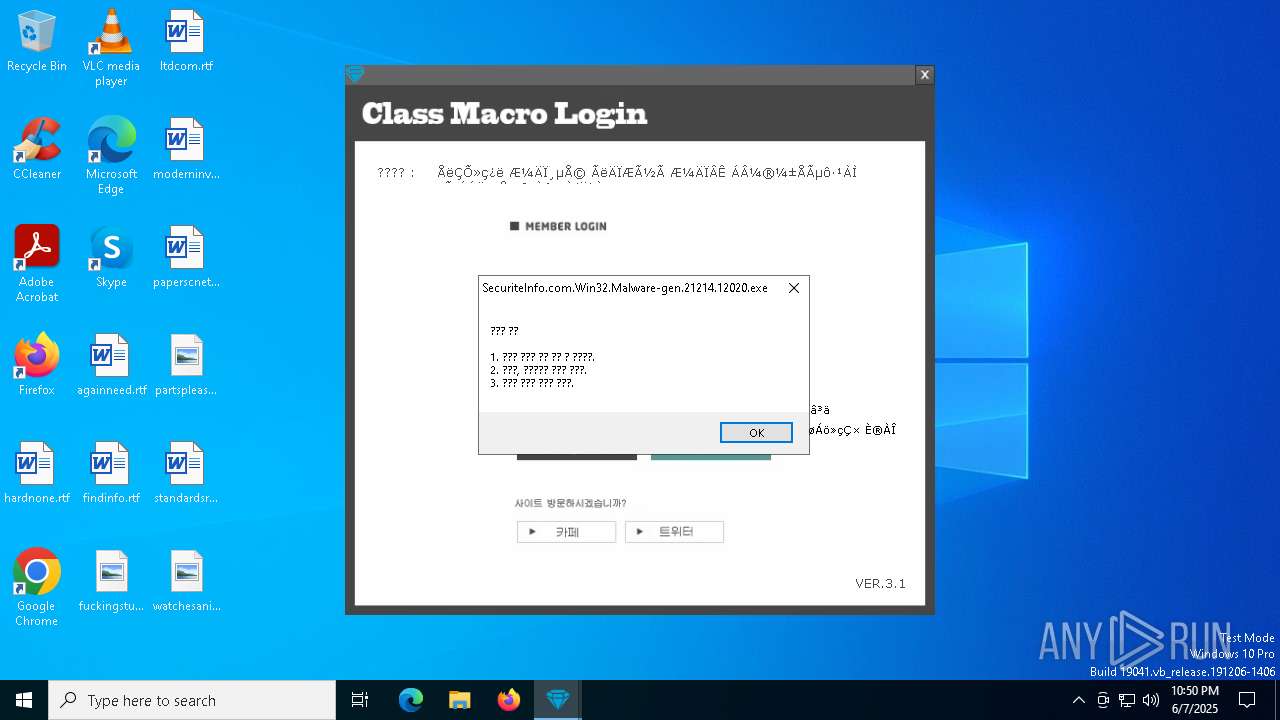
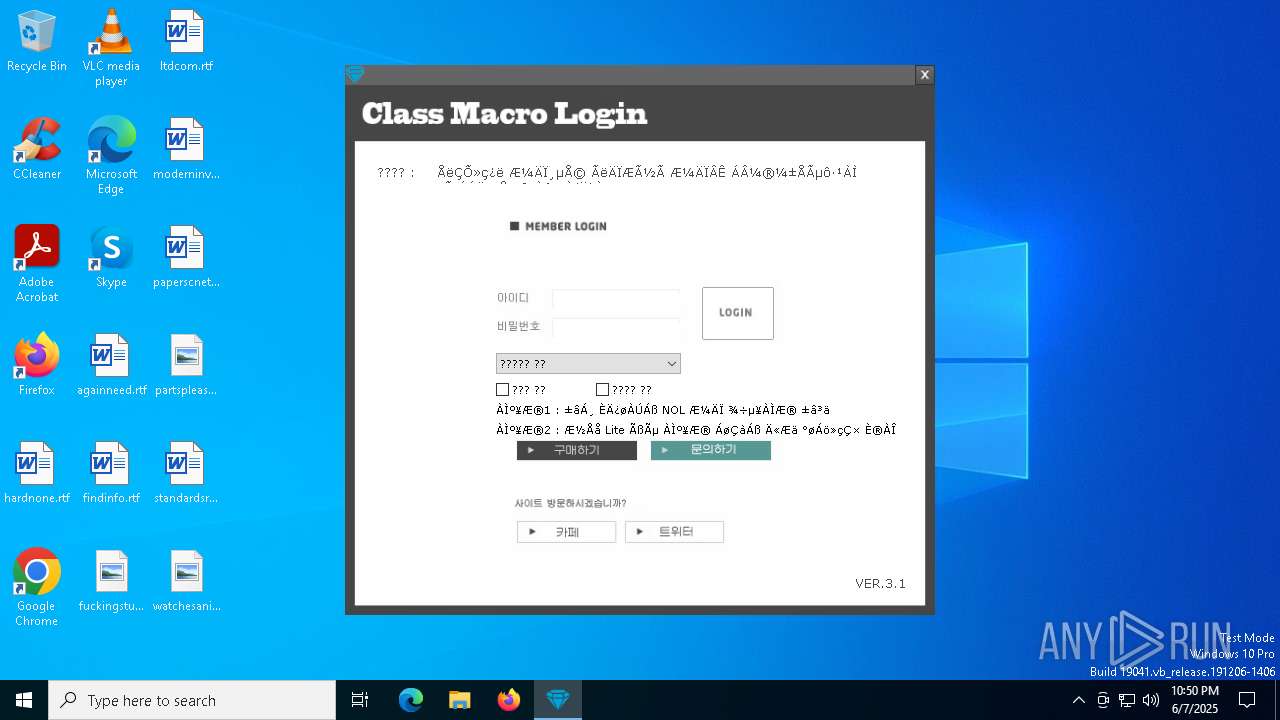
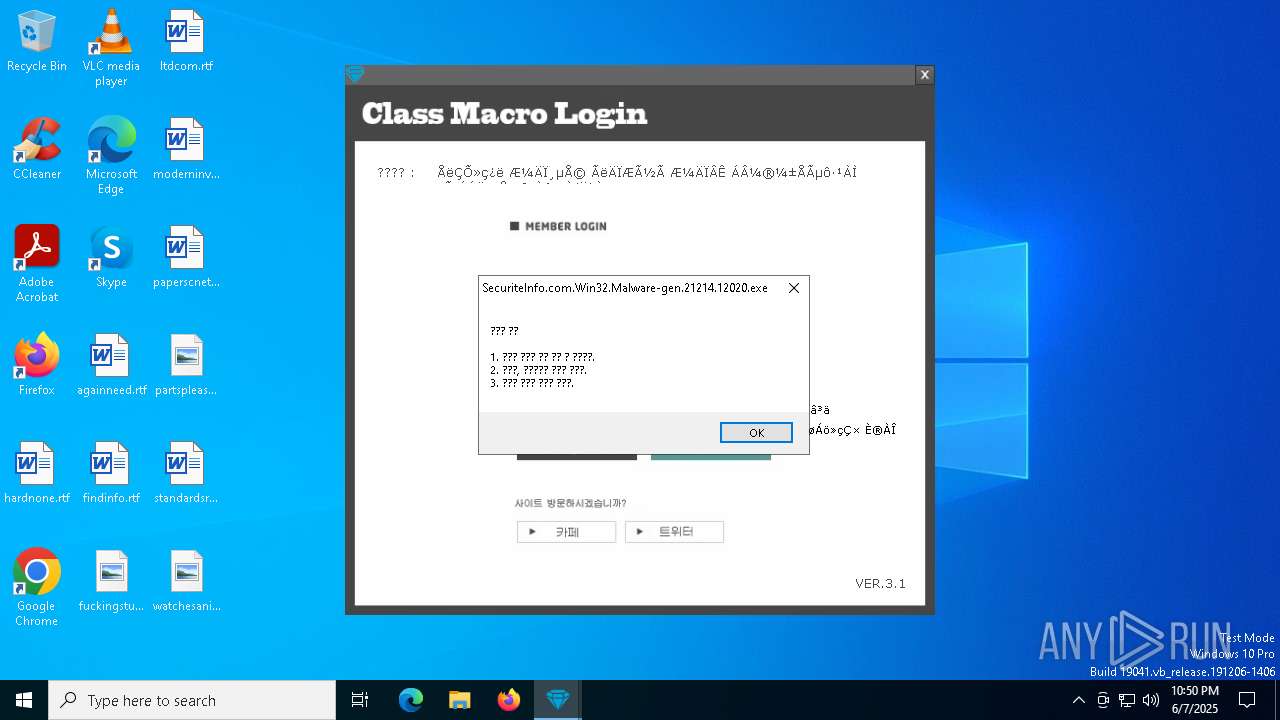
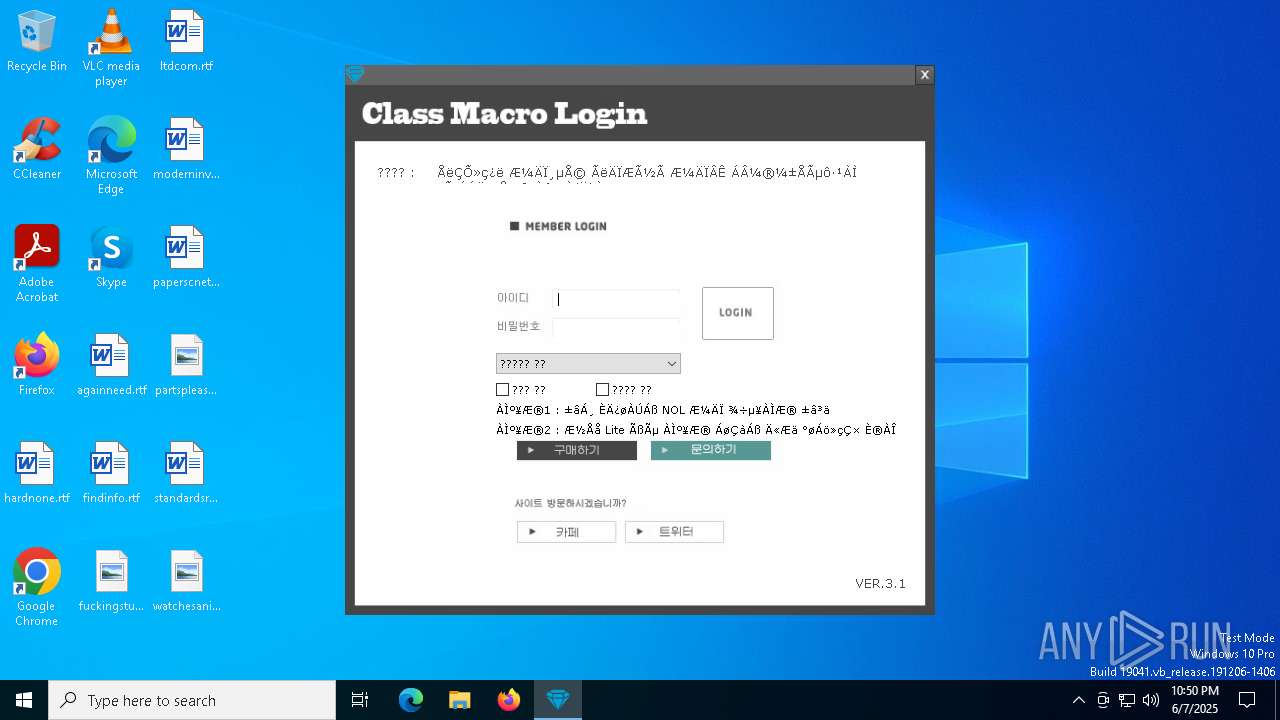
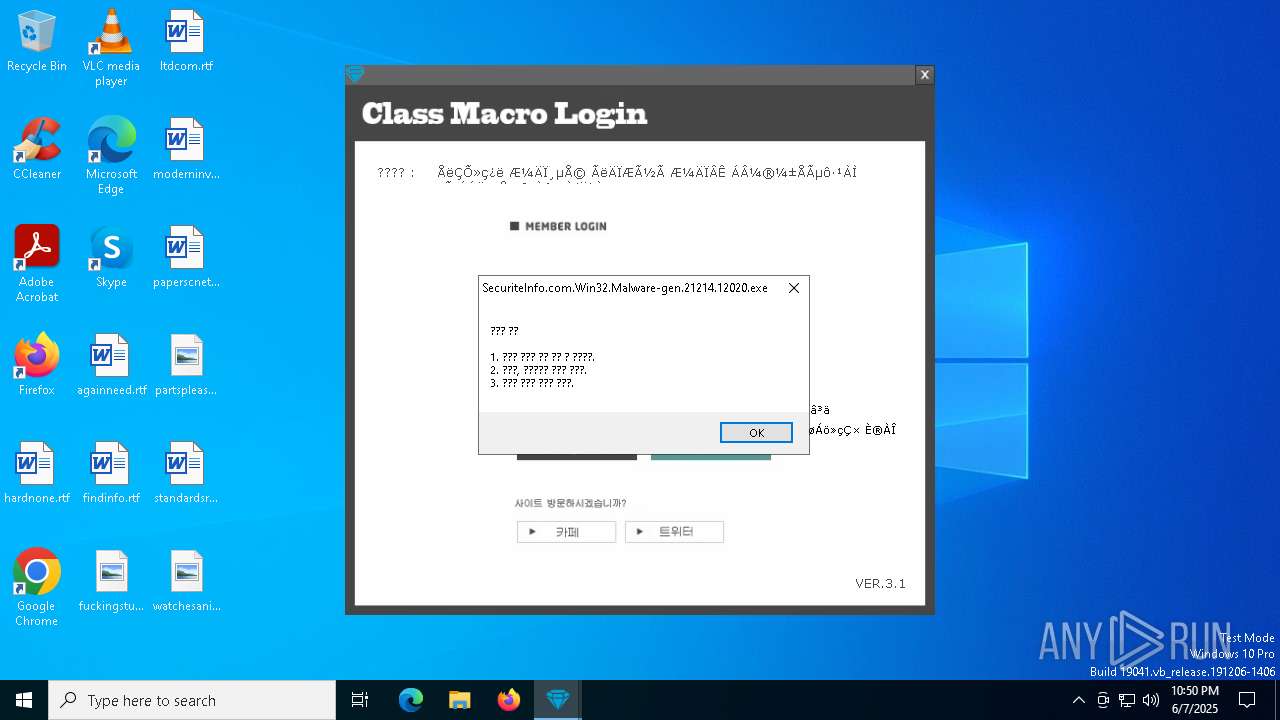
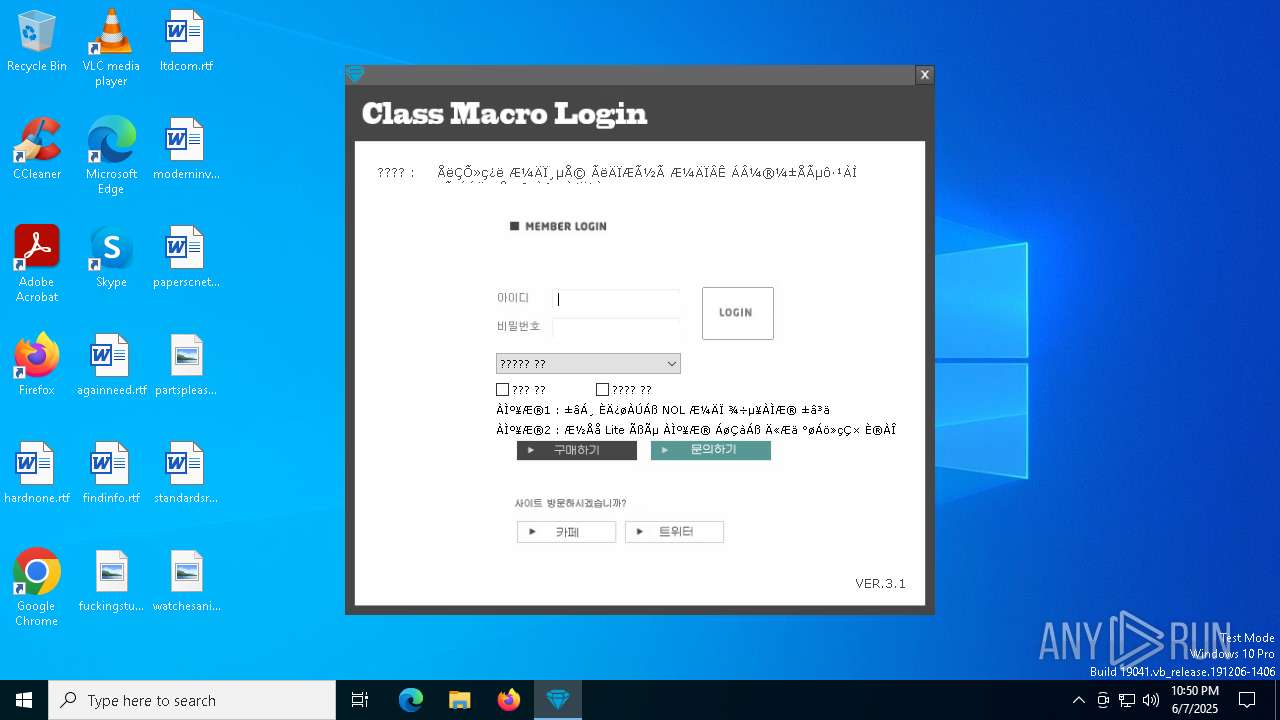
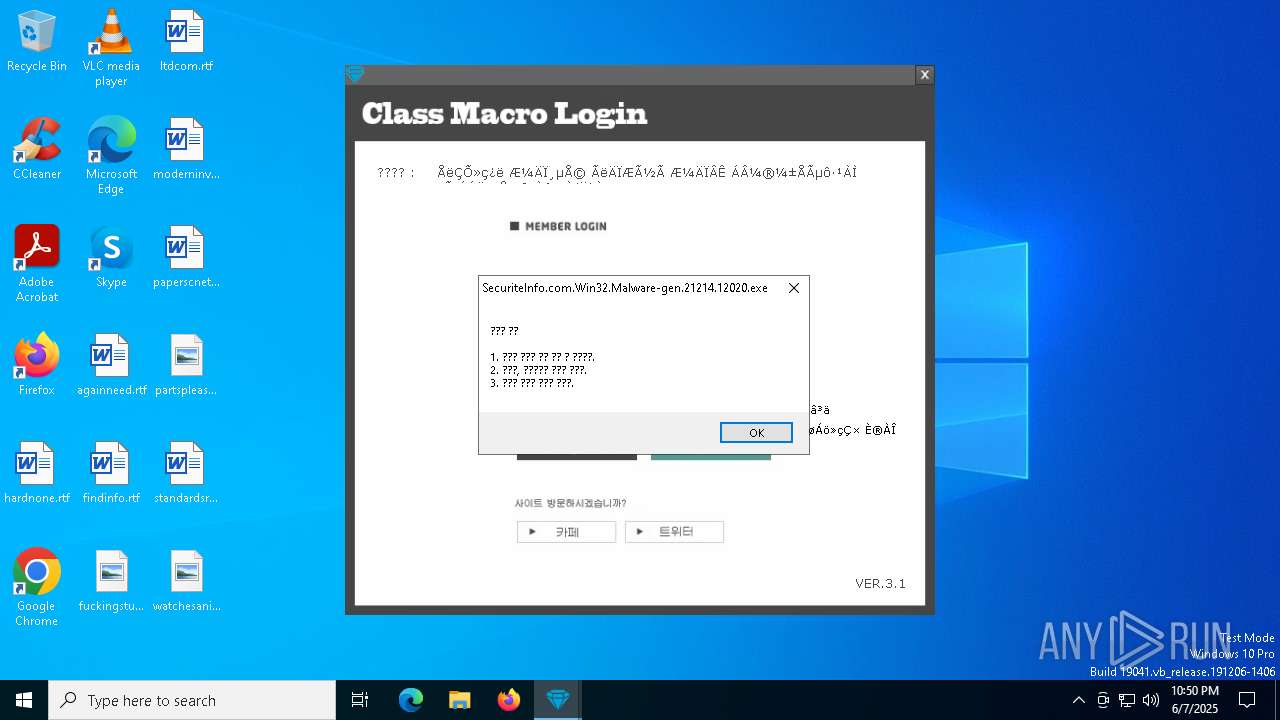
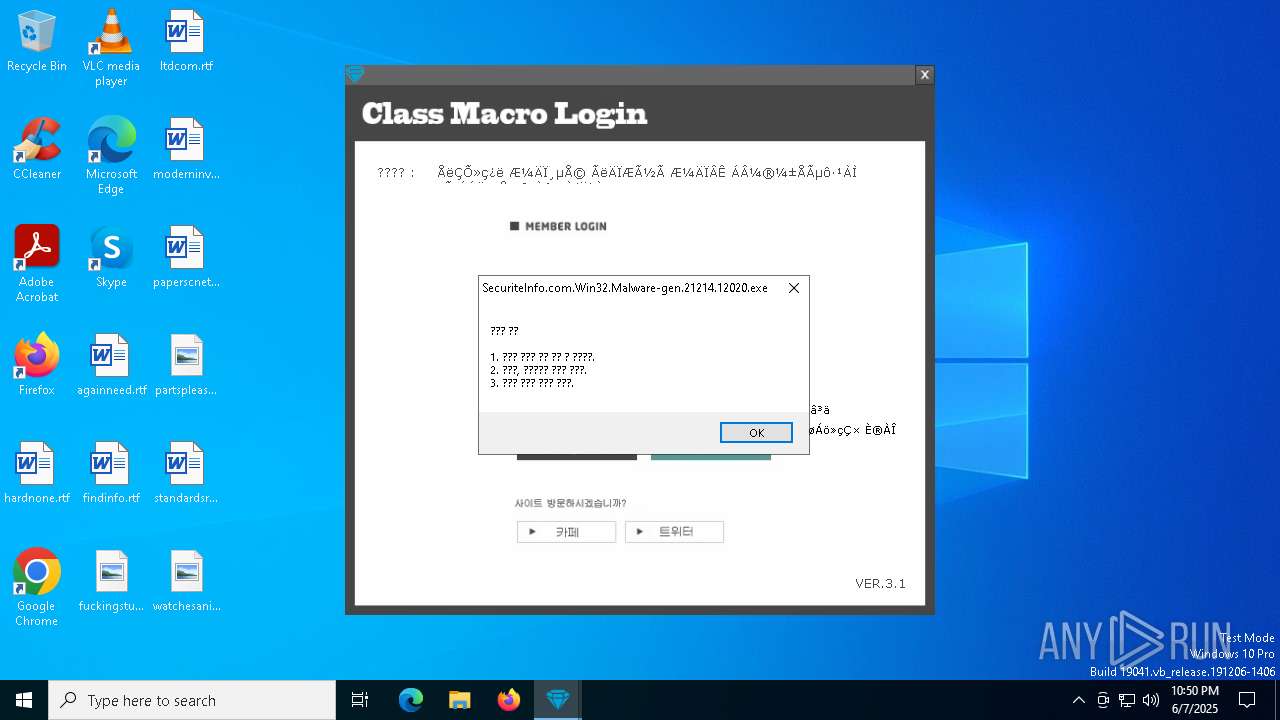
| File name: | SecuriteInfo.com.Win32.Malware-gen.21214.12020 |
| Full analysis: | https://app.any.run/tasks/896acca6-284d-4c6c-9927-df9e170bc121 |
| Verdict: | Malicious activity |
| Analysis date: | June 07, 2025, 22:48:45 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 33B2C10781736AFC9E2593A2D31A30AF |
| SHA1: | 3882BD76493F68C8BF68409A6C2B9EA00B0414F7 |
| SHA256: | B9A984DFE108A6CB2DC4D728216112BC84B93407449AE790B7DE3DE457D88170 |
| SSDEEP: | 49152:sIh9yO6PRcFmoLBEW25rxeS/zaVlUF/+8IwiWLwsoWVmMJSMFaQQgxhSlEb:VFmoLBE3eyWVl/3wpwsrFaQQgXyEb |
MALICIOUS
XORed URL has been found (YARA)
- SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe (PID: 2084)
SUSPICIOUS
Reads security settings of Internet Explorer
- SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe (PID: 2084)
There is functionality for taking screenshot (YARA)
- SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe (PID: 2084)
INFO
Checks supported languages
- SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe (PID: 2084)
The sample compiled with english language support
- SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe (PID: 2084)
Reads the computer name
- SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe (PID: 2084)
Checks proxy server information
- SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe (PID: 2084)
Create files in a temporary directory
- SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe (PID: 2084)
Reads the software policy settings
- slui.exe (PID: 5972)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(2084) SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe
Decrypted-URLs (2)https://autohotkey.com
https://autohotkey.comIIIIIIIIIICould
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (52.5) |
|---|---|---|
| .scr | | | Windows screen saver (22) |
| .dll | | | Win32 Dynamic Link Library (generic) (11) |
| .exe | | | Win32 Executable (generic) (7.5) |
| .exe | | | Generic Win/DOS Executable (3.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:05:30 06:52:22+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 865280 |
| InitializedDataSize: | 315904 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xbe298 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.1.32.0 |
| ProductVersionNumber: | 1.1.32.0 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | - |
| FileVersion: | 1.1.32.00 |
| InternalName: | - |
| LegalCopyright: | - |
| OriginalFileName: | - |
| ProductName: | - |
| ProductVersion: | 1.1.32.00 |
Total processes
131
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2084 | "C:\Users\admin\AppData\Local\Temp\SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe" | C:\Users\admin\AppData\Local\Temp\SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 1.1.32.00 Modules
xor-url(PID) Process(2084) SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe Decrypted-URLs (2)https://autohotkey.com https://autohotkey.comIIIIIIIIIICould | |||||||||||||||
| 5972 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7048 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7508 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
990
Read events
987
Write events
3
Delete events
0
Modification events
| (PID) Process: | (2084) SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2084) SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2084) SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
0
Suspicious files
0
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2084 | SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | C:\Users\admin\AppData\Local\Temp\logindir\1.png | image | |
MD5:5C1D4A87E10DEADCF5D46B564FC38EA3 | SHA256:7CD6E2C0BF0E76206AEF92E1F22A3D350E0B23A39E8029FEECA843C8099D2B46 | |||
| 2084 | SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | C:\Users\admin\AppData\Local\Temp\logindir\7.png | image | |
MD5:FDECFF49F84AFBC8B9173B6292056B3D | SHA256:AECE702A968E4B50F80C4E3D55EB8044530C675AA3395D1DBA8E8BD26F0EA77B | |||
| 2084 | SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | C:\Users\admin\AppData\Local\Temp\logindir\9.png | image | |
MD5:341EF8DD66315D68E1262D0C714CEAF4 | SHA256:E67BAA0F75A14038B69AC34CEF86F8C64FF9A617ACEE1049E7B6F253380B4220 | |||
| 2084 | SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | C:\Users\admin\AppData\Local\Temp\ver.txt | text | |
MD5:5B068A95442C7D5505B4166A77357EA5 | SHA256:35EFC6DED4E13F29A8D86E4F33294BE0F59FCAAF3A56B538F9E34E60E3AE4F44 | |||
| 2084 | SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | C:\Users\admin\AppData\Local\Temp\logindir\5.png | image | |
MD5:349E1D18508C73EB9EEDD0E30E61A567 | SHA256:FA368C671DEB5B16BD4BAC15BF2C5790B059C977D4DFC6542A4B428EF3EB03F3 | |||
| 2084 | SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | C:\Users\admin\AppData\Local\Temp\logindir\8.png | image | |
MD5:F664D0E13EC81A40EEDD42BD4DB08749 | SHA256:6FD7CCE72C1B8F896432A78D8A86D50FF0282DE1AA48AACA75480CF445BEFDDC | |||
| 2084 | SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | C:\Users\admin\AppData\Local\Temp\logindir\Event2.txt | text | |
MD5:450845683C81487885AC75DD122F3FE2 | SHA256:856D941260BB37A6F55140742F85B4A42B7E675968C1C9011D00BFC99D4BCCC4 | |||
| 2084 | SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | C:\Users\admin\AppData\Local\Temp\logindir\10.png | image | |
MD5:4DC7FBDF0ED94071BA09F30BBE0A35A8 | SHA256:60697FA59D09D11CE7E53F89876CD870D99517A1D41A253930004DFB360F6BD0 | |||
| 2084 | SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | C:\Users\admin\AppData\Local\Temp\logindir\6.png | image | |
MD5:A22A82240BAC464F6B9532BC295E2645 | SHA256:253D7CBC1E3450B048FF6CD52E6C679AB026766B452A2336A9E69727A7E5114E | |||
| 2084 | SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | C:\Users\admin\AppData\Local\Temp\logindir\Notice.txt | text | |
MD5:70581F91CEFFADD4ADA0460ED522B1FF | SHA256:8DBFF85ADC4E8D28710DAD19715B44EDBC24187286F85EE2B5A6DDB65EE6548F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
34
DNS requests
14
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2084 | SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | GET | 200 | 223.26.138.8:80 | http://class1004.dothome.co.kr/ver.txt | unknown | — | — | malicious |
2084 | SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | GET | 200 | 223.26.138.8:80 | http://class1004.dothome.co.kr/rhdwltkgkd.txt | unknown | — | — | malicious |
2084 | SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | GET | 200 | 223.26.138.8:80 | http://class1004.dothome.co.kr/dlqpsxm1.txt | unknown | — | — | unknown |
2084 | SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | GET | 200 | 223.26.138.8:80 | http://class1004.dothome.co.kr/dlqpsxm2.txt | unknown | — | — | unknown |
2084 | SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | GET | 404 | 223.26.138.8:80 | http://class1004.dothome.co.kr/login/.txt | unknown | — | — | unknown |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2084 | SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | GET | 404 | 223.26.138.8:80 | http://class1004.dothome.co.kr/login/.txt | unknown | — | — | unknown |
2084 | SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | GET | 404 | 223.26.138.8:80 | http://class1004.dothome.co.kr/login/.txt | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
7560 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2516 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2084 | SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | 223.26.138.8:80 | class1004.dothome.co.kr | HyosungITX | KR | malicious |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7560 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
class1004.dothome.co.kr |
| malicious |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2084 | SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (AutoHotkey) |
2084 | SecuriteInfo.com.Win32.Malware-gen.21214.12020.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (AutoHotkey) |