| File name: | 1.ps1 |
| Full analysis: | https://app.any.run/tasks/e05b4b2b-00e9-40a8-bef2-1ea0301536f5 |
| Verdict: | Malicious activity |
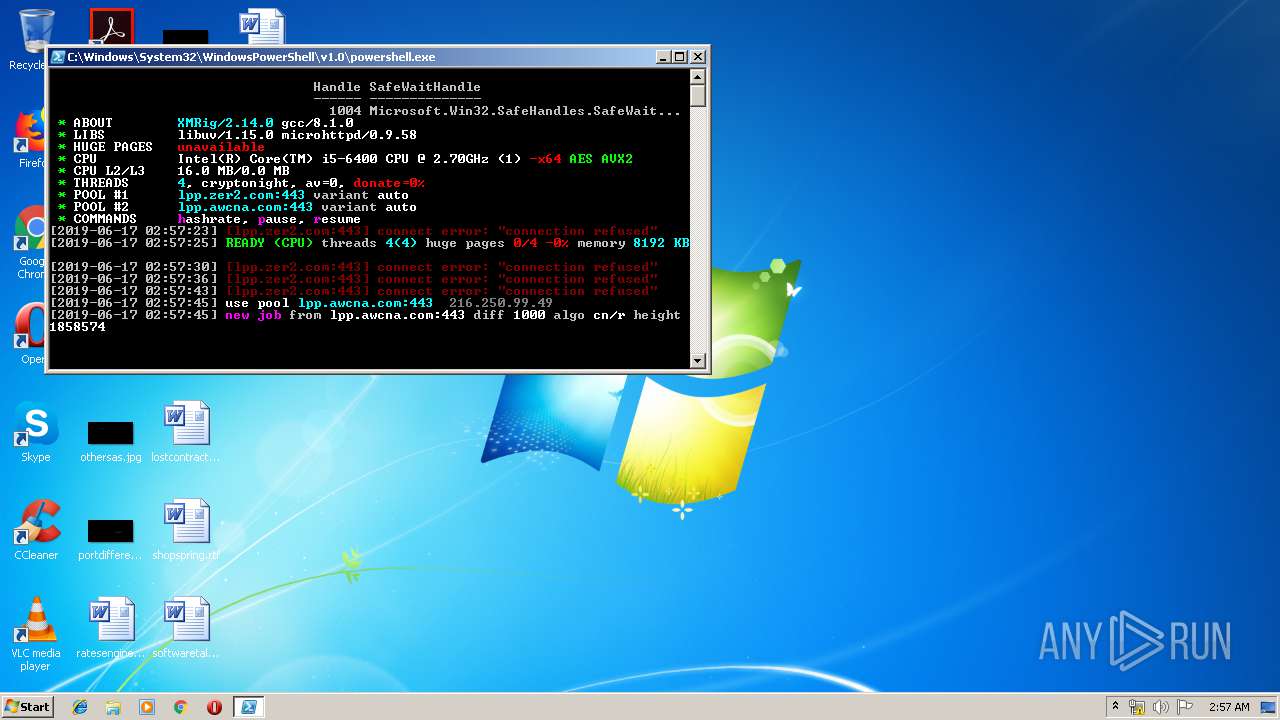
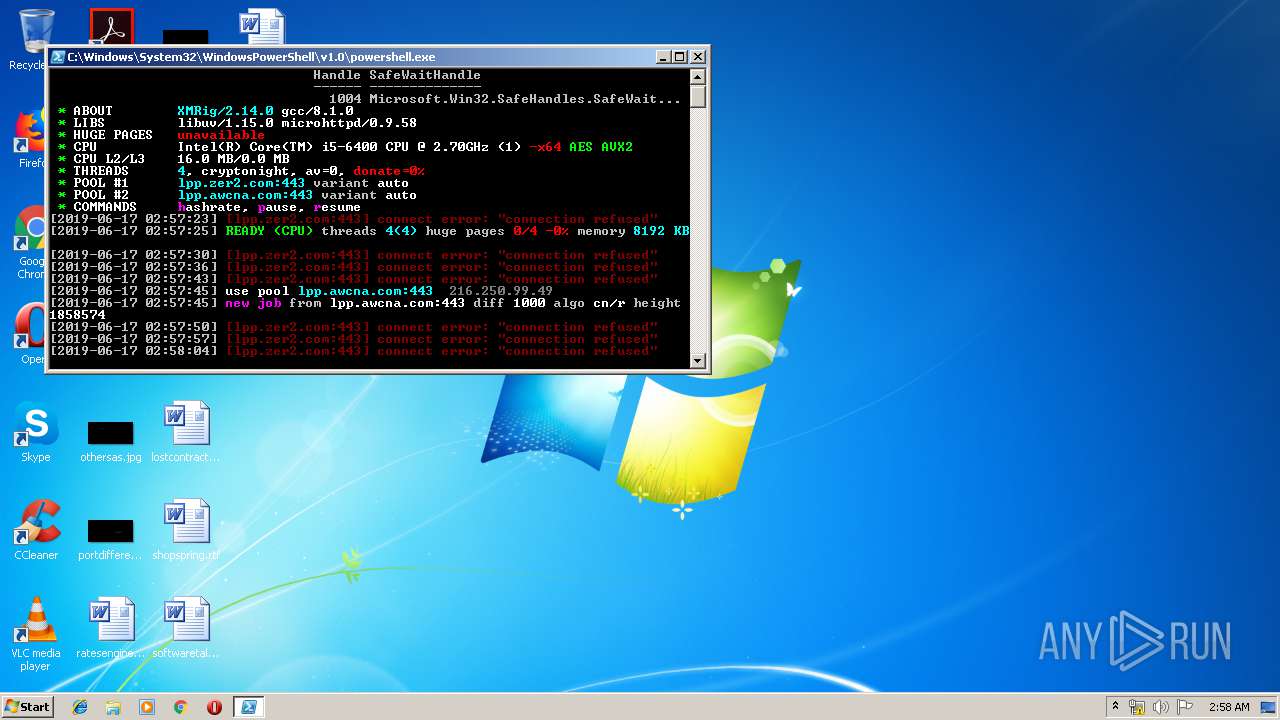
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | June 17, 2019, 01:56:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF, CR, LF line terminators |
| MD5: | 10B77B651D4DEB83AF13F9A60C3E3E0E |
| SHA1: | E942FB1D7D817B2ED8CE1990E78C390D71E2A525 |
| SHA256: | B9A25533CE8702B472EFF3B8B96F8DF5BB6331C311BCA98C7D5774B0EF5A43CE |
| SSDEEP: | 12288:w6CSnESzCqF8HFrMZhmOKuUGWMQfwkCvpC678sfLd9OdOZHSwmAX6Rs955FnhYyi:wtStzsKgFurWNyV8sDdqoHSi6RAnRi |
MALICIOUS
Connects to CnC server
- powershell.exe (PID: 3972)
MINER was detected
- powershell.exe (PID: 3972)
SUSPICIOUS
PowerShell script executed
- powershell.exe (PID: 3972)
Creates files in the user directory
- powershell.exe (PID: 3972)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
33
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3972 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "-file" "C:\Users\admin\AppData\Local\Temp\1.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
201
Read events
142
Write events
59
Delete events
0
Modification events
| (PID) Process: | (3972) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3972) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3972) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3972 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\DT8CTJ5UBXVRBDJ43242.temp | — | |
MD5:— | SHA256:— | |||
| 3972 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF11ed4b.TMP | binary | |
MD5:— | SHA256:— | |||
| 3972 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
2
Threats
5
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3972 | powershell.exe | 216.250.99.49:443 | lpp.awcna.com | — | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
lpp.zer2.com |
| unknown |
lpp.awcna.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3972 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
3972 | powershell.exe | Misc activity | MINER [PTsecurity] CoinMiner CryptoNight XMRig JSON_RPC Client Login |
3972 | powershell.exe | Misc activity | MINER [PTsecurity] Riskware/CoinMiner JSON_RPC Response |
3972 | powershell.exe | Misc activity | MINER [PTsecurity] Risktool.W32.coinminer!c |
3972 | powershell.exe | Misc activity | MINER [PTsecurity] CoinMiner CryptoNight algo JSON_RPC server Response |