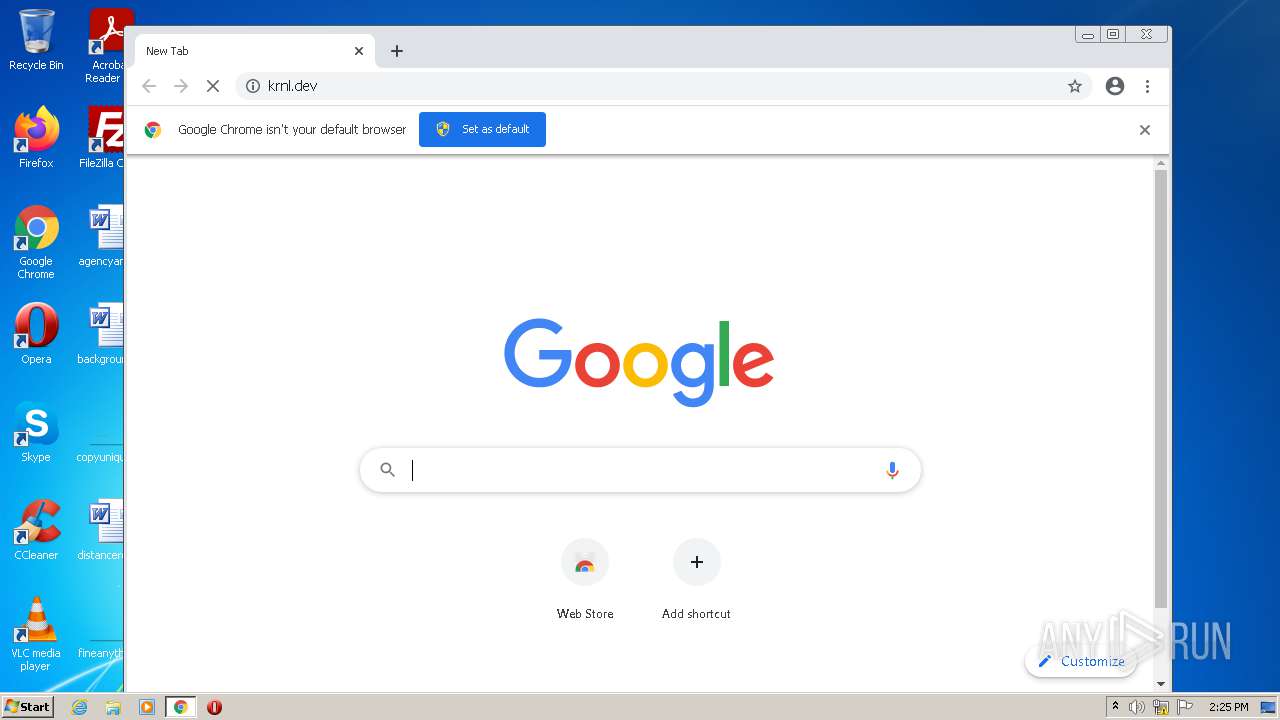
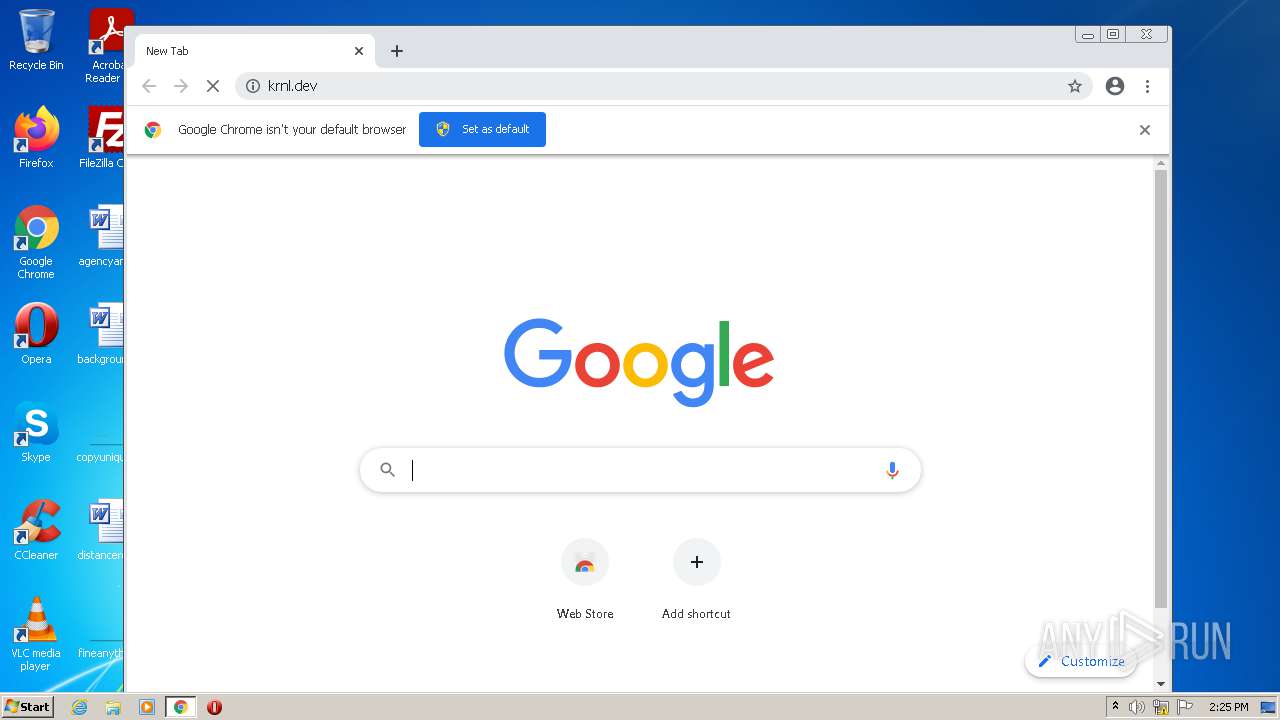
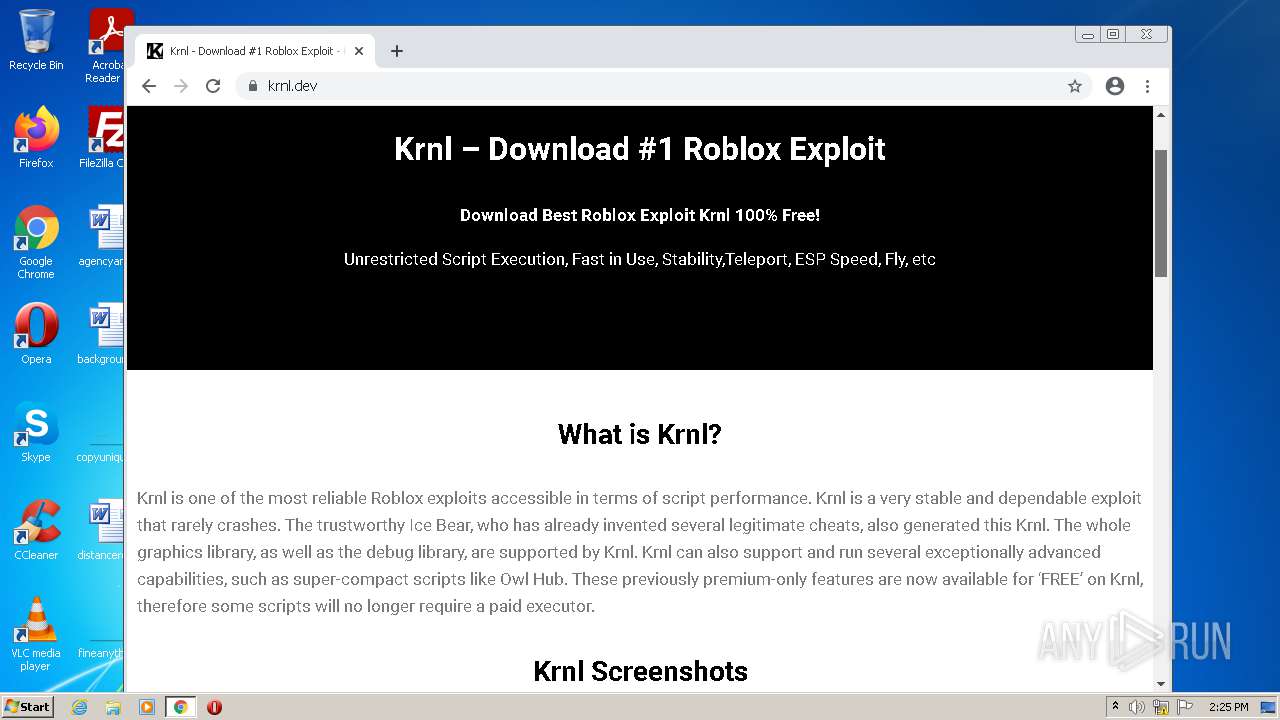
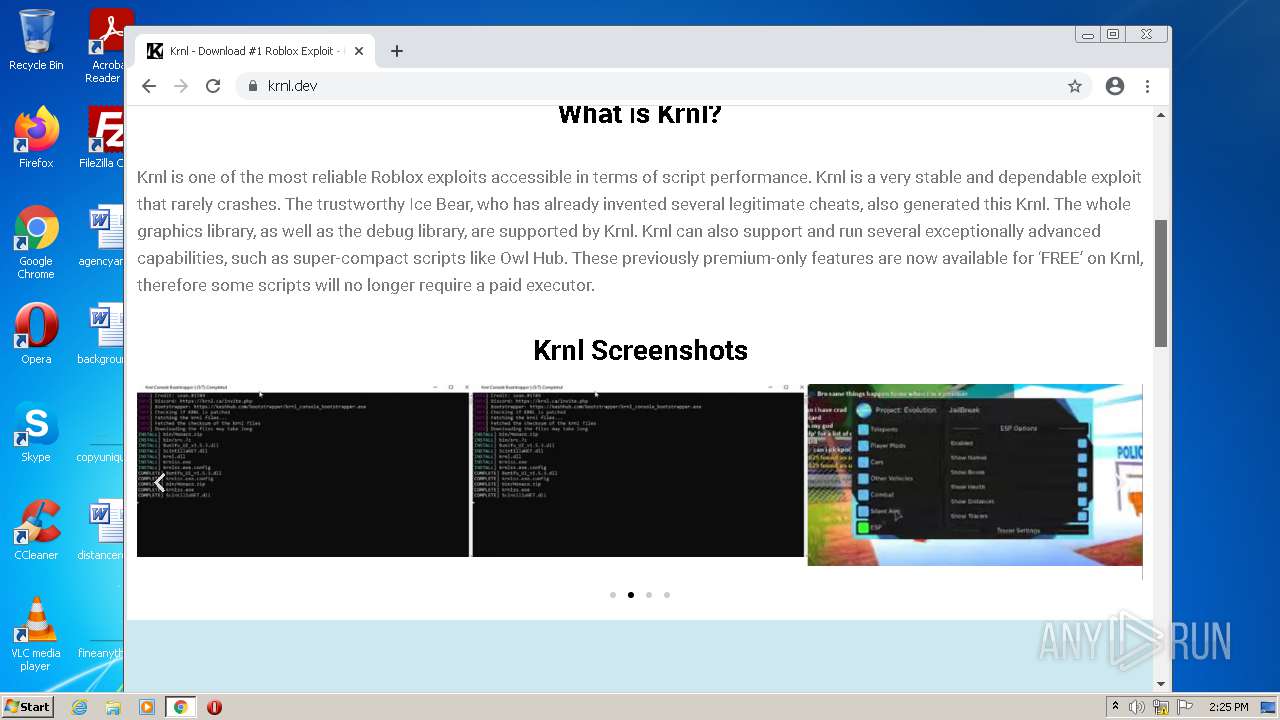
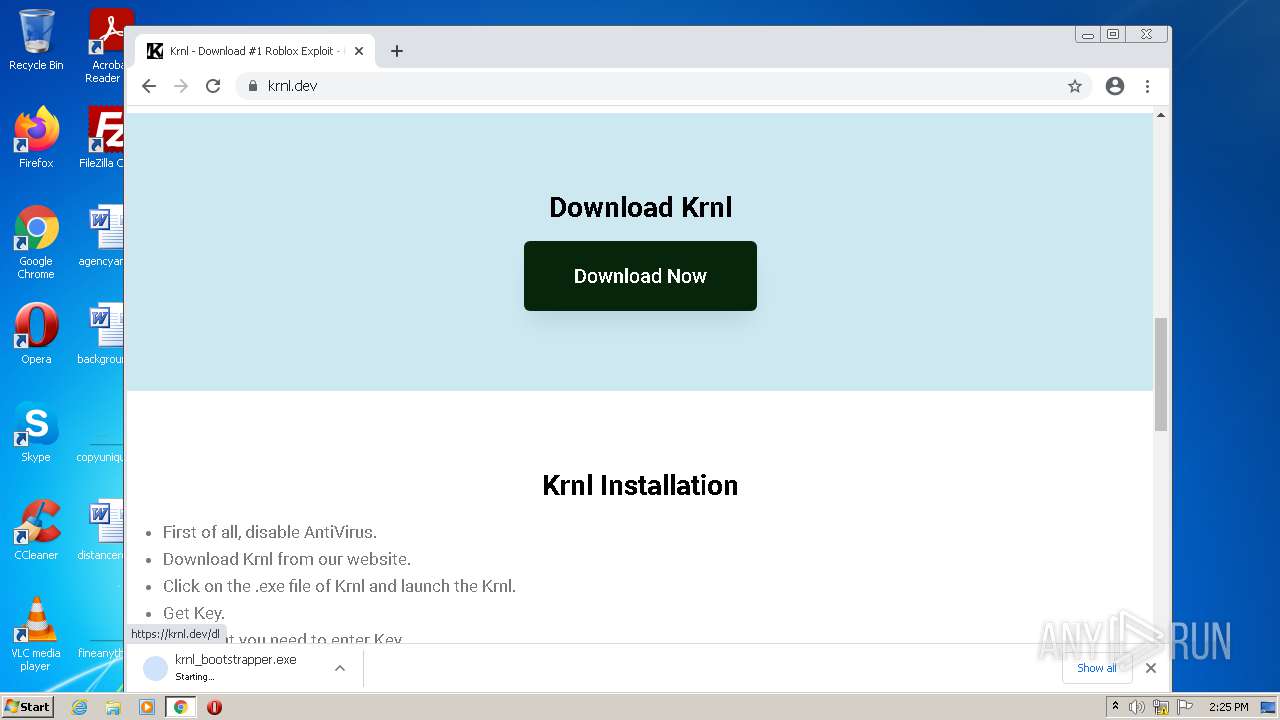
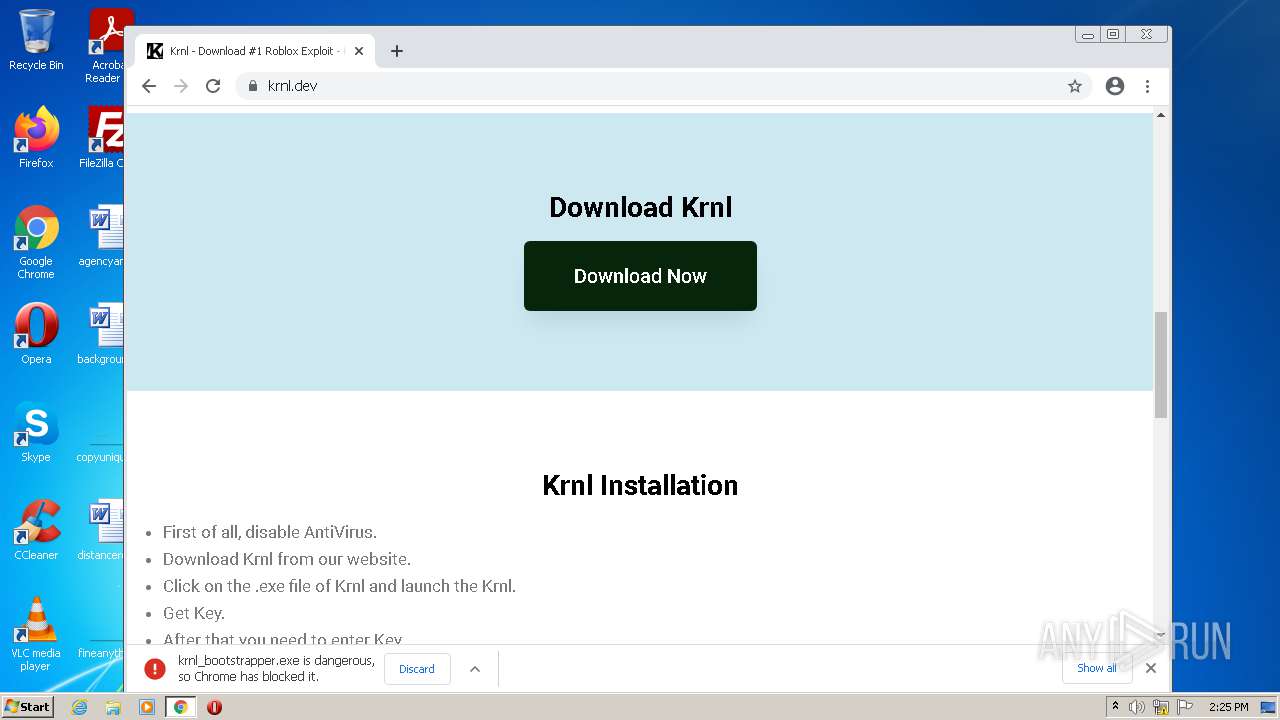
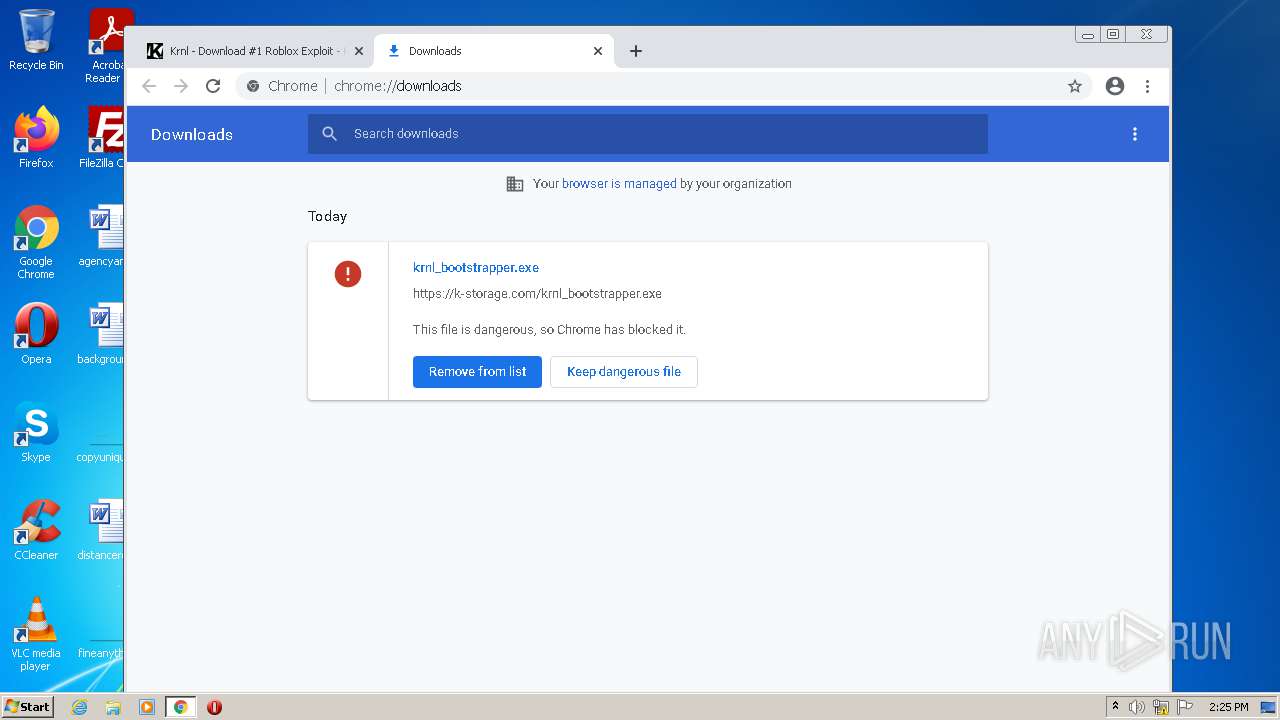
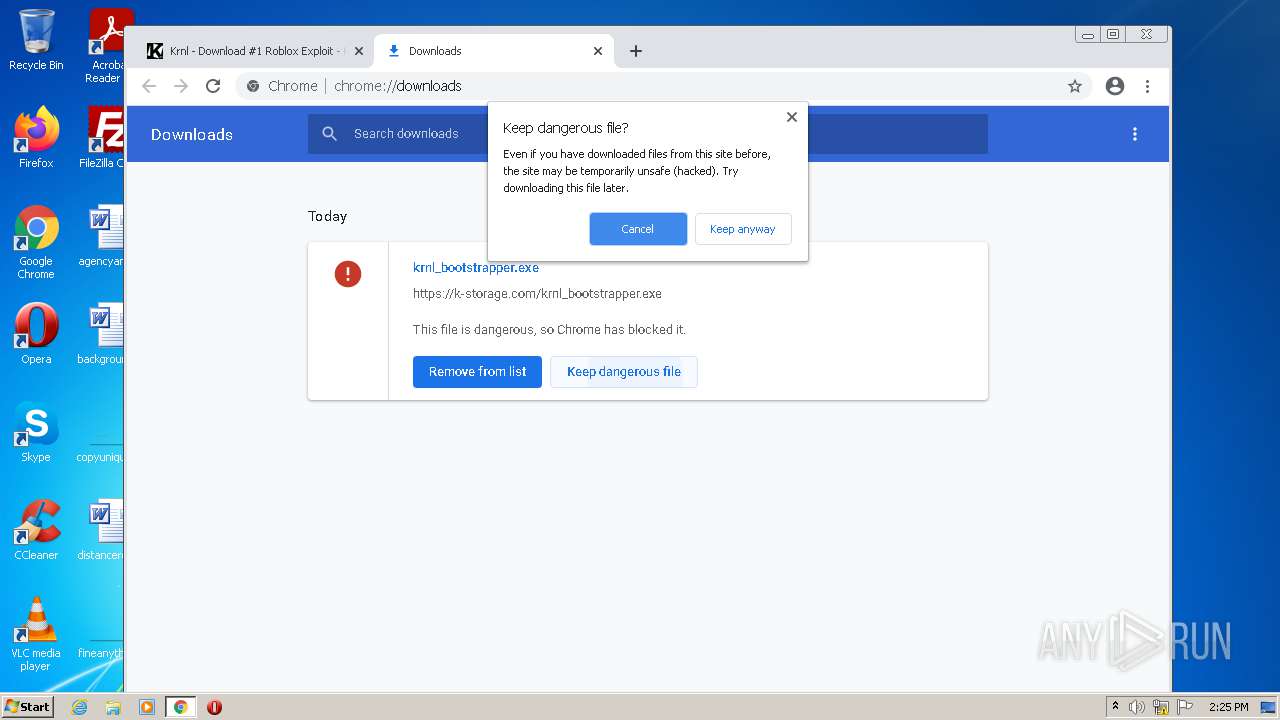
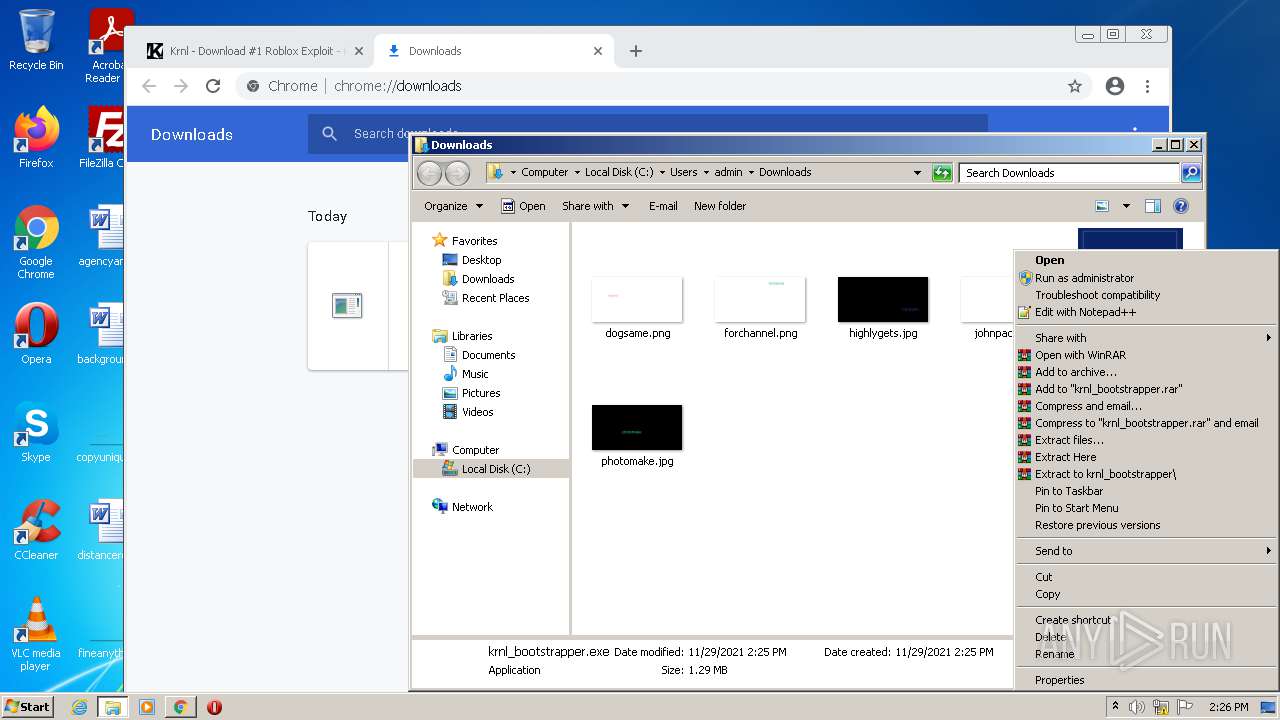
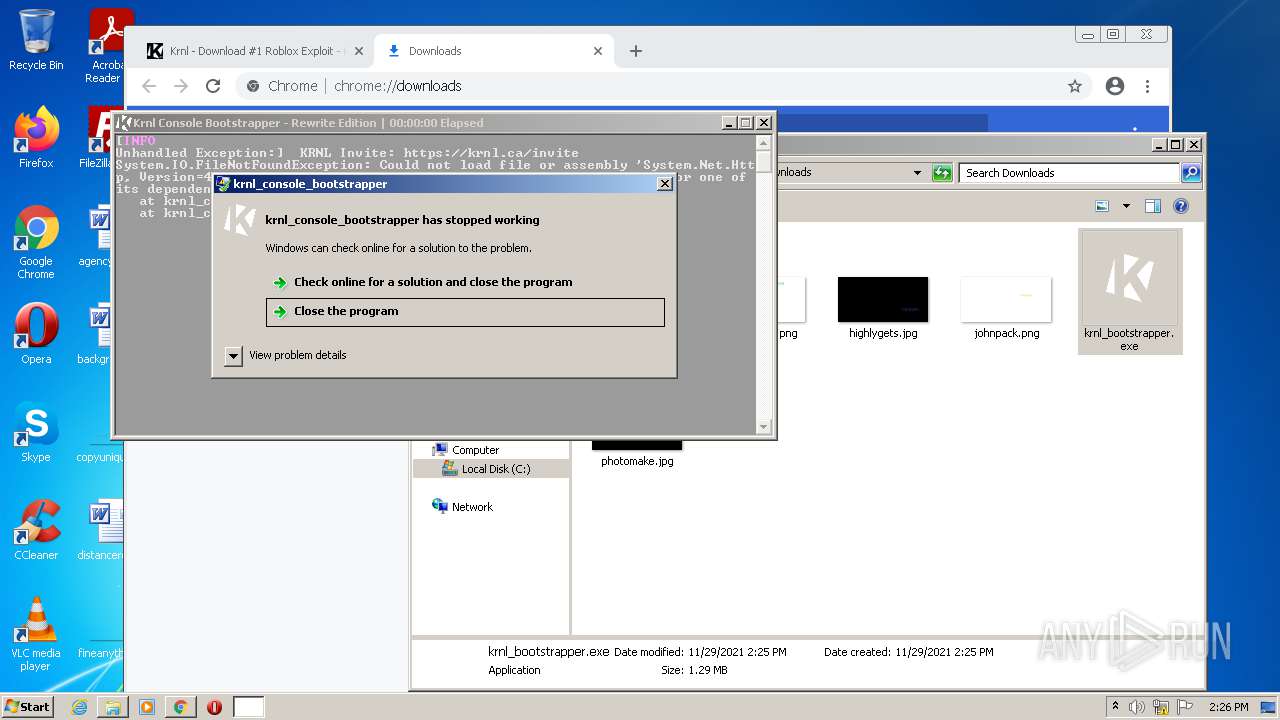
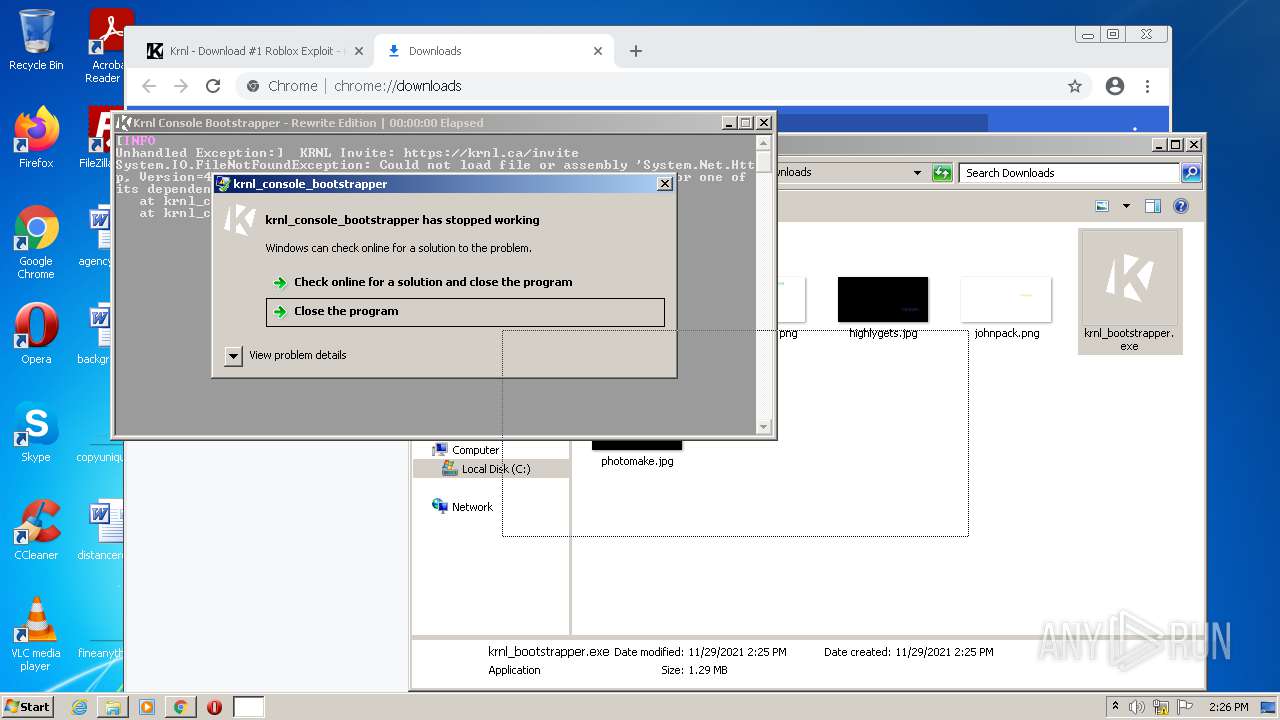
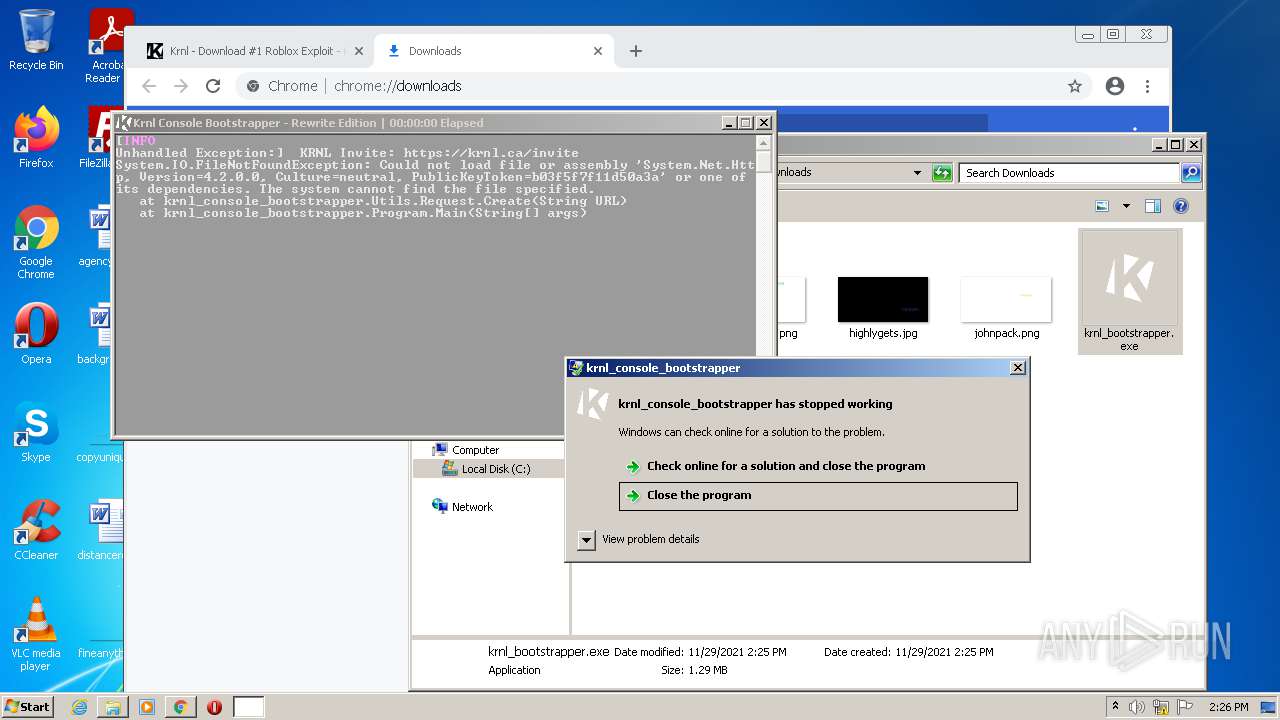
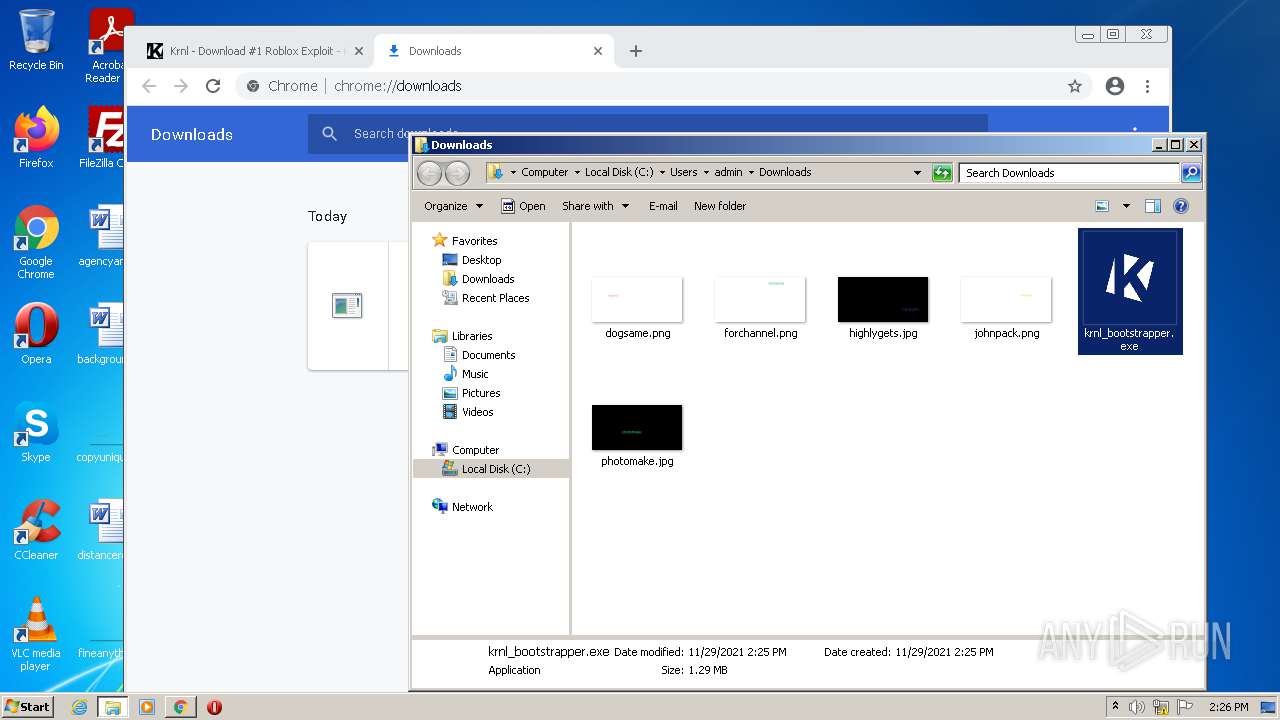
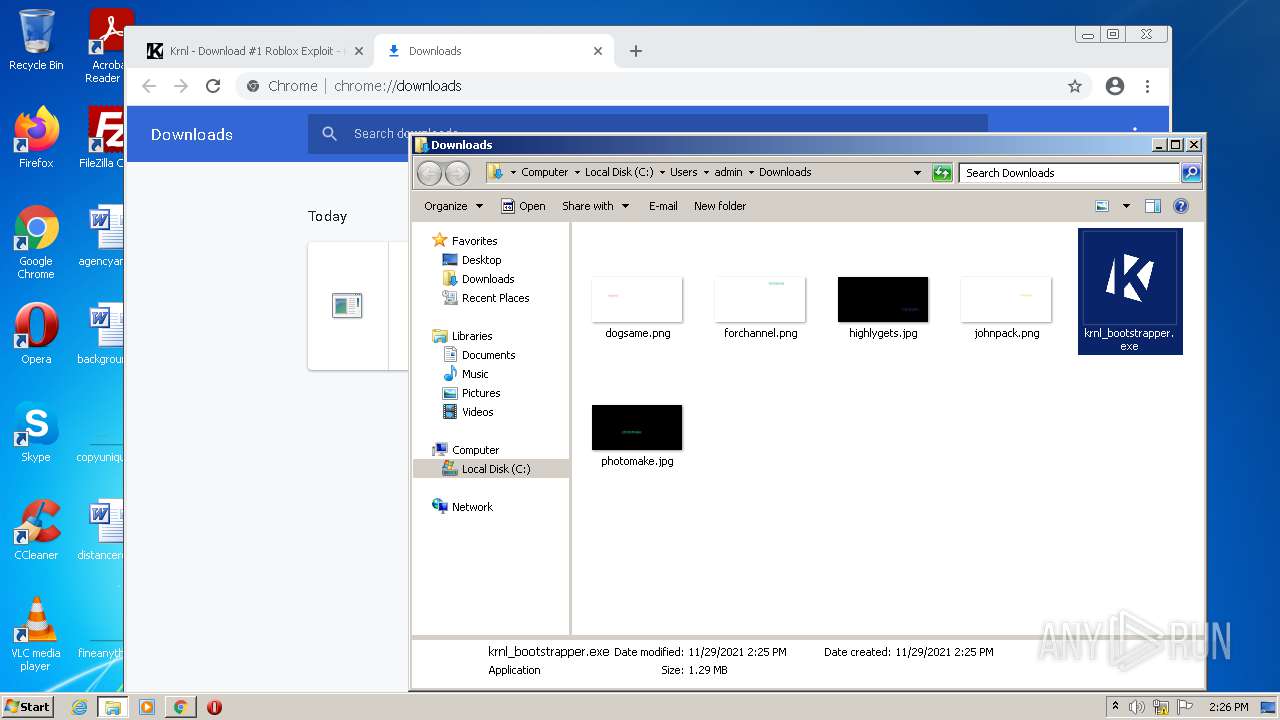
| URL: | https://krnl.dev/ |
| Full analysis: | https://app.any.run/tasks/a5775ee0-f531-486a-aa10-4e45bc8d4fb8 |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2021, 14:23:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | C165743C10C6E616626EB86B67EC2ED8 |
| SHA1: | 466AB32DAC5203E79B6BBA36AF6A2611BA2161A4 |
| SHA256: | B99DE618DEA5D96EDAC89020D7FB333B62AF1986AB540D7A8CB1F7739E5816DD |
| SSDEEP: | 3:N8SvATK:2SvATK |
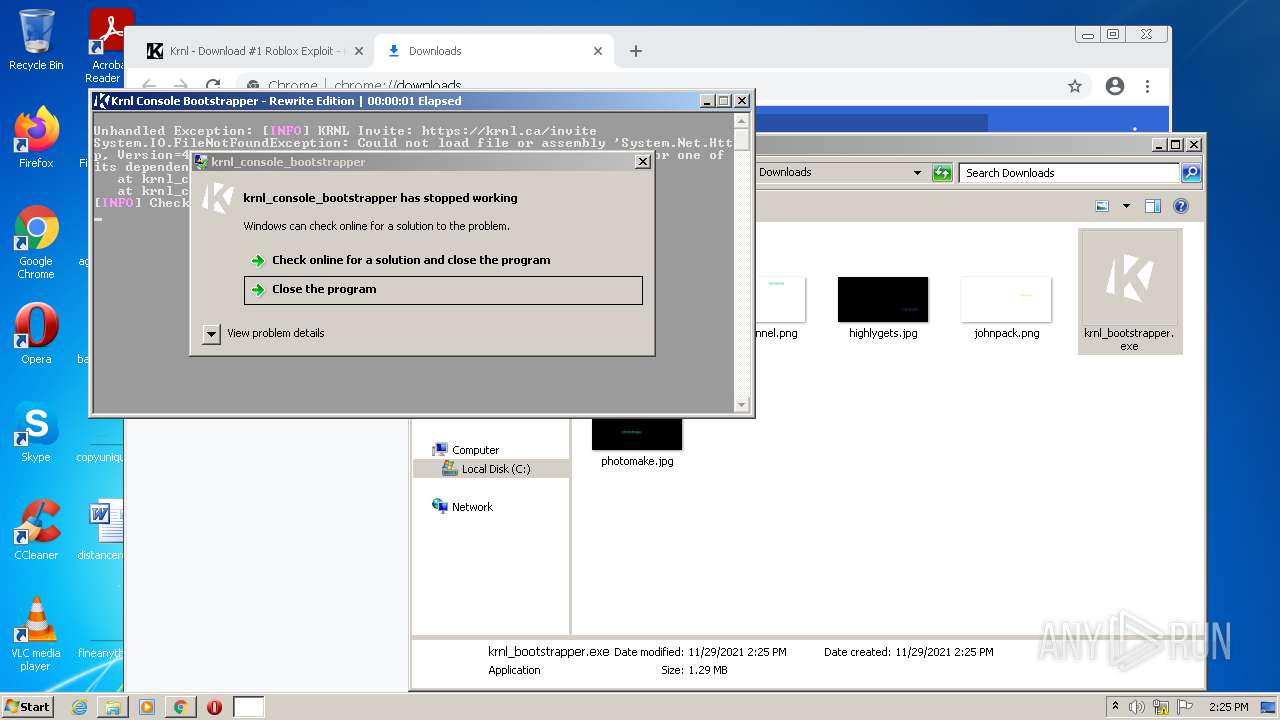
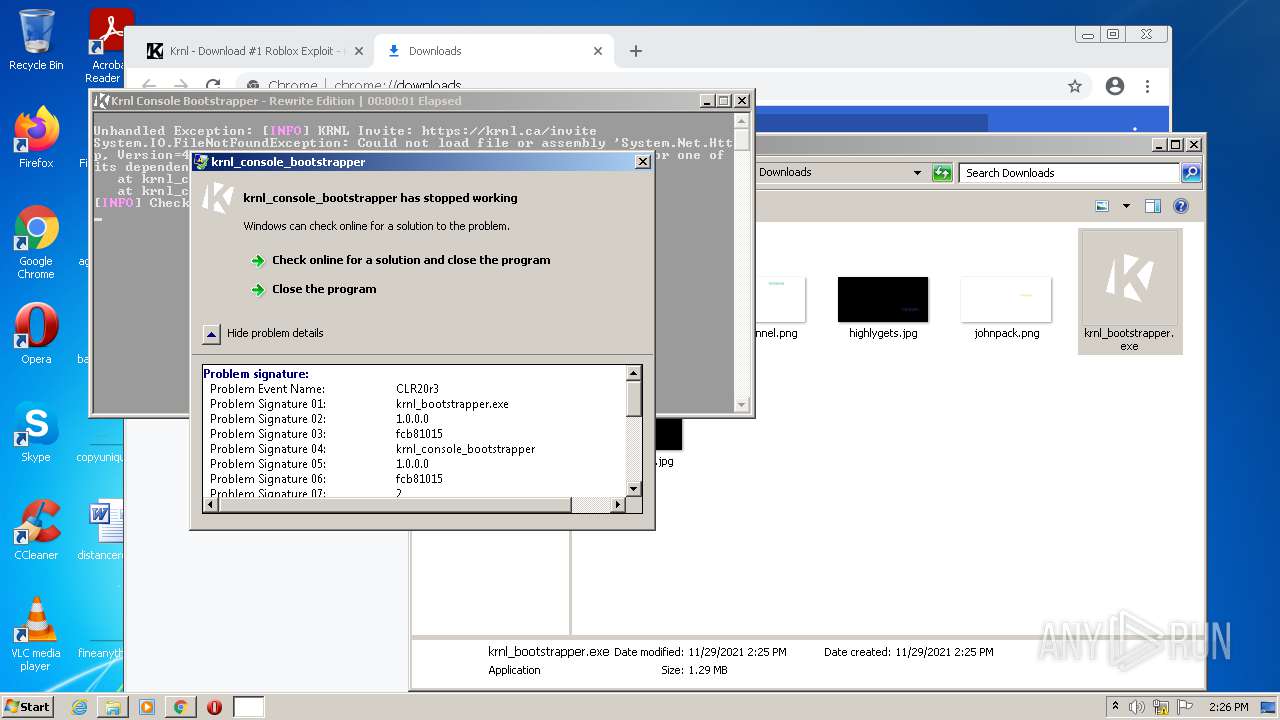
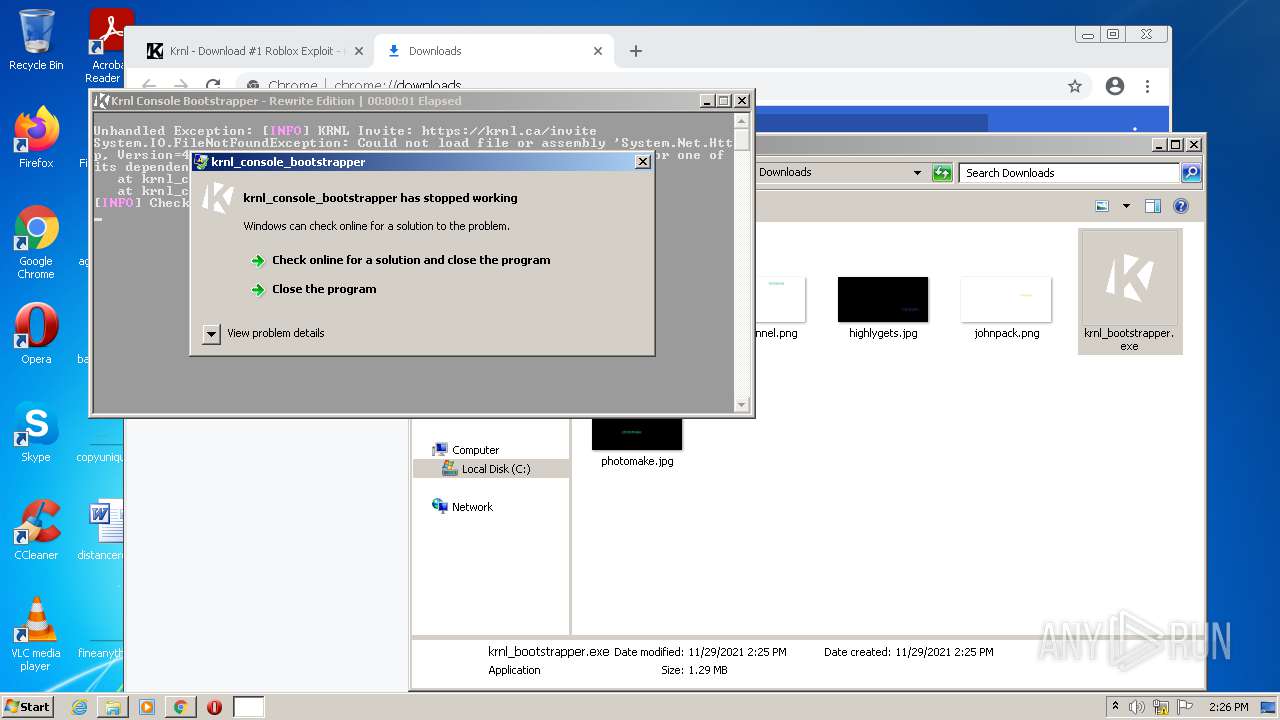
MALICIOUS
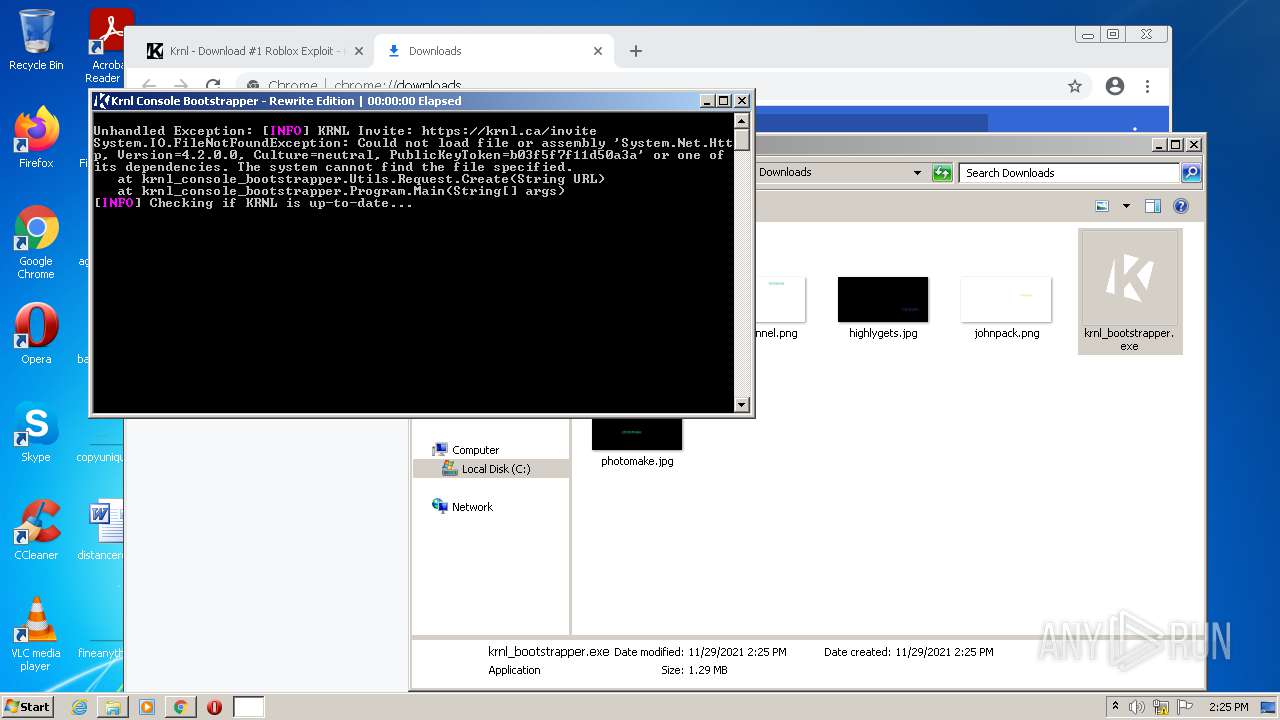
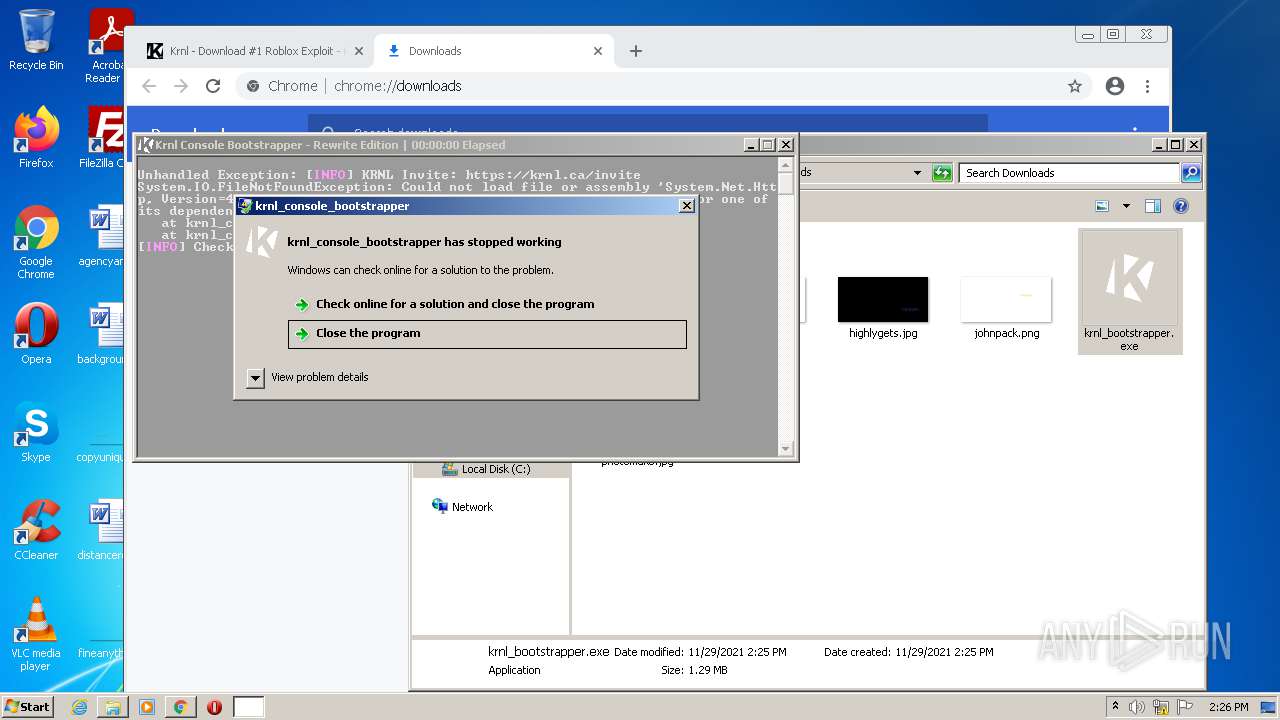
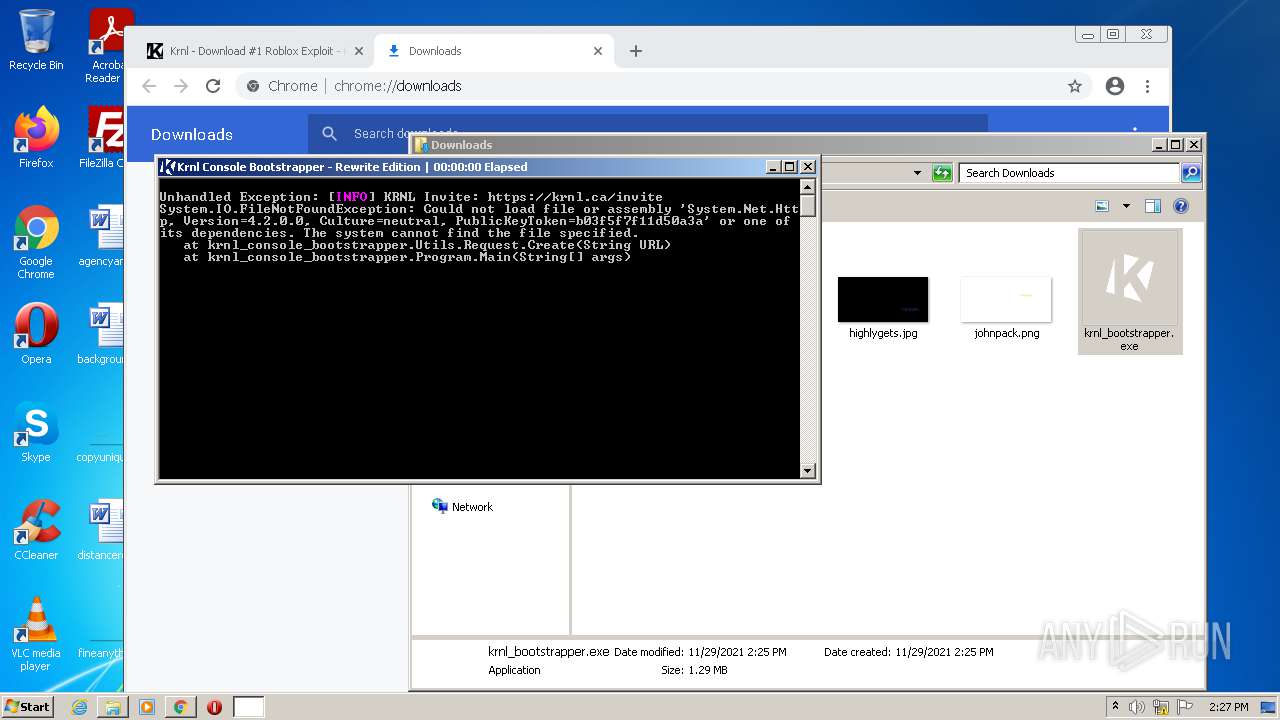
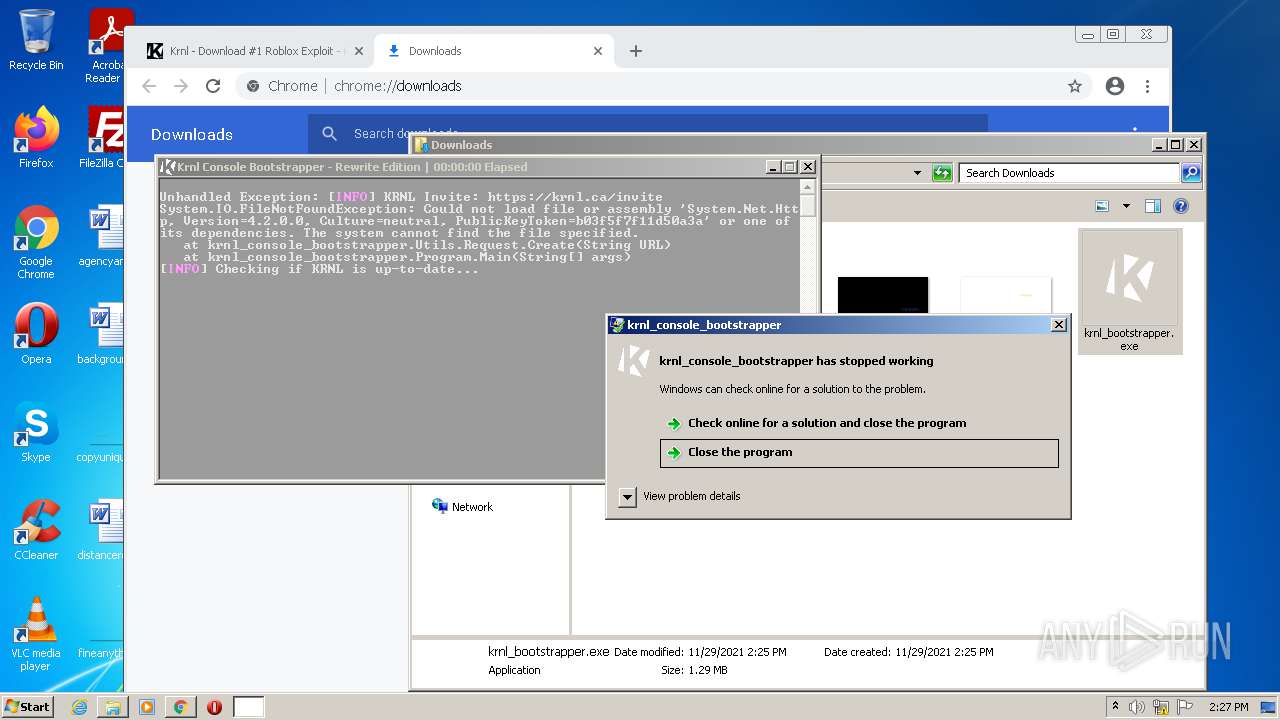
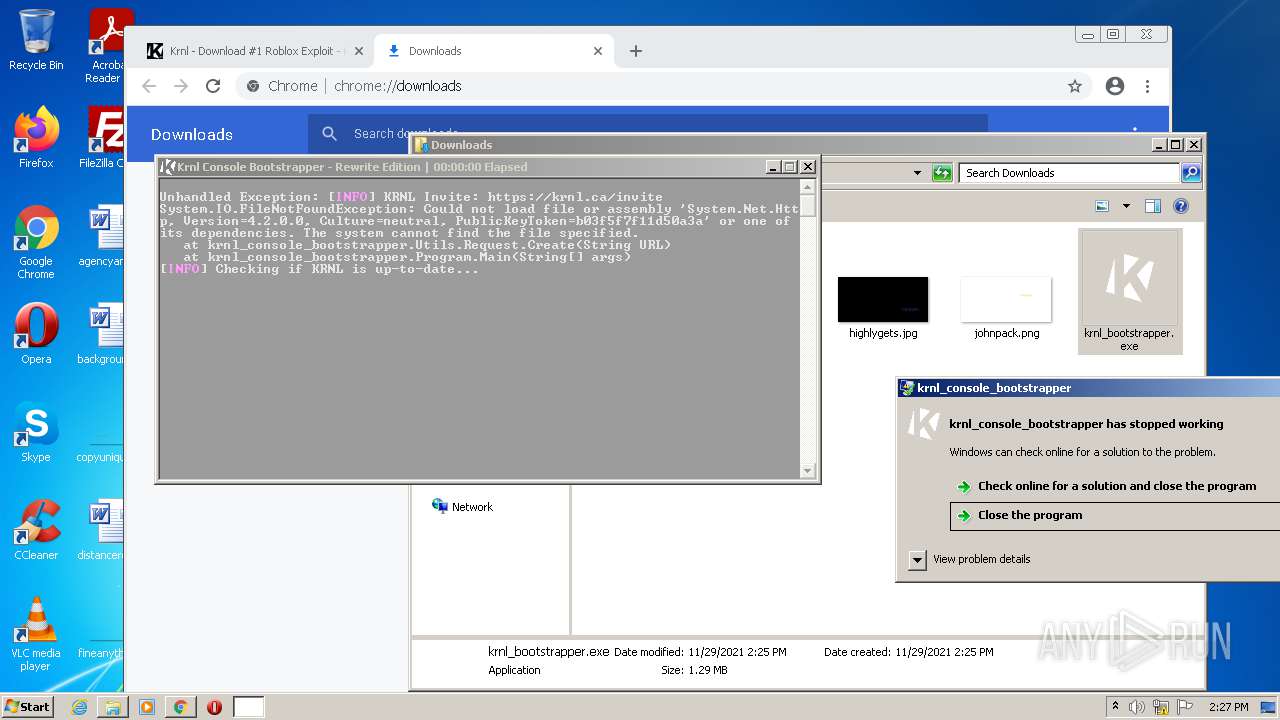
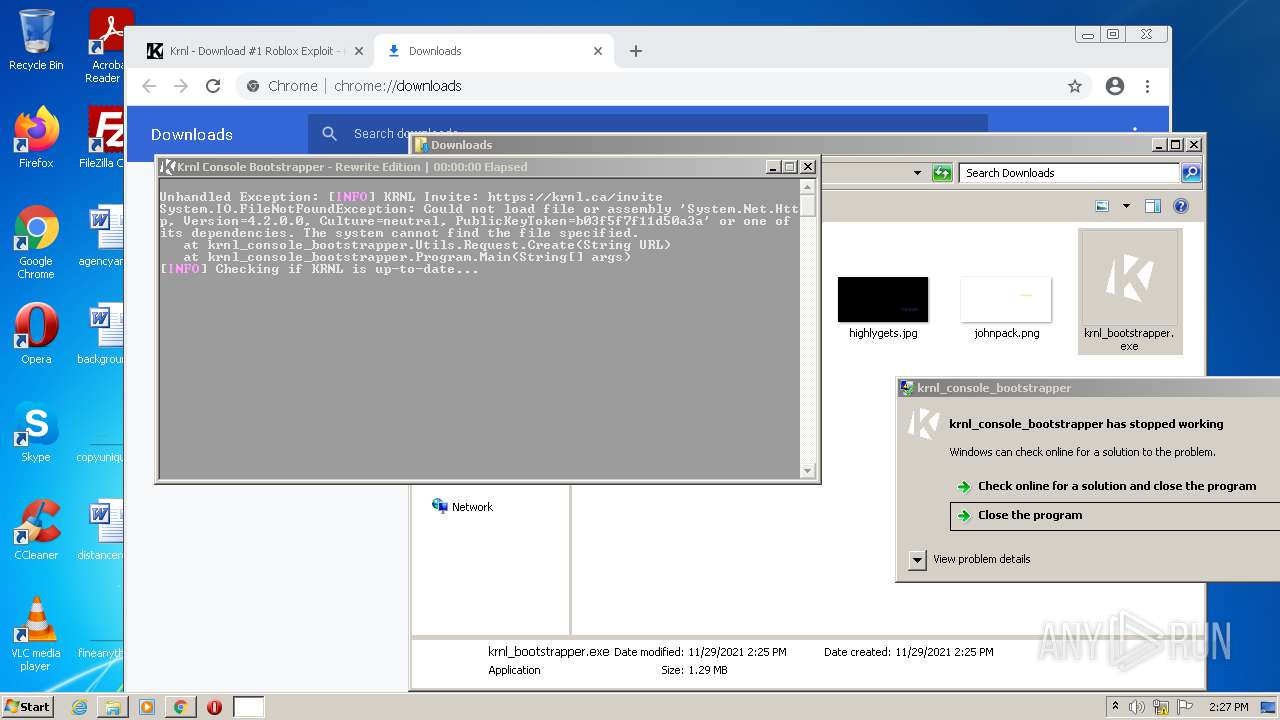
Application was dropped or rewritten from another process
- krnl_bootstrapper.exe (PID: 2720)
- krnl_bootstrapper.exe (PID: 2520)
- krnl_bootstrapper.exe (PID: 2184)
- krnl_bootstrapper.exe (PID: 2272)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 1708)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3840)
Executable content was dropped or overwritten
- chrome.exe (PID: 3840)
- chrome.exe (PID: 2260)
Drops a file with a compile date too recent
- chrome.exe (PID: 3840)
- chrome.exe (PID: 2260)
Drops a file that was compiled in debug mode
- chrome.exe (PID: 2260)
- chrome.exe (PID: 3840)
Reads the computer name
- krnl_bootstrapper.exe (PID: 2720)
- krnl_bootstrapper.exe (PID: 2520)
- krnl_bootstrapper.exe (PID: 2184)
- krnl_bootstrapper.exe (PID: 2272)
Checks supported languages
- krnl_bootstrapper.exe (PID: 2720)
- krnl_bootstrapper.exe (PID: 2520)
- krnl_bootstrapper.exe (PID: 2184)
- krnl_bootstrapper.exe (PID: 2272)
INFO
Changes internet zones settings
- iexplore.exe (PID: 3208)
Checks supported languages
- iexplore.exe (PID: 3208)
- iexplore.exe (PID: 1708)
- chrome.exe (PID: 3840)
- chrome.exe (PID: 3836)
- chrome.exe (PID: 4048)
- chrome.exe (PID: 2260)
- chrome.exe (PID: 3688)
- chrome.exe (PID: 1088)
- chrome.exe (PID: 2348)
- chrome.exe (PID: 3748)
- chrome.exe (PID: 272)
- chrome.exe (PID: 2892)
- chrome.exe (PID: 744)
- chrome.exe (PID: 1404)
- chrome.exe (PID: 3268)
- chrome.exe (PID: 3488)
- chrome.exe (PID: 3440)
- chrome.exe (PID: 1500)
- chrome.exe (PID: 2092)
- chrome.exe (PID: 2856)
- chrome.exe (PID: 672)
- chrome.exe (PID: 3212)
- chrome.exe (PID: 2872)
- chrome.exe (PID: 3272)
- chrome.exe (PID: 852)
- chrome.exe (PID: 3792)
- chrome.exe (PID: 2944)
- chrome.exe (PID: 4056)
- chrome.exe (PID: 1436)
- chrome.exe (PID: 3940)
- chrome.exe (PID: 672)
- chrome.exe (PID: 852)
- chrome.exe (PID: 2092)
- chrome.exe (PID: 3940)
- chrome.exe (PID: 2764)
- chrome.exe (PID: 3056)
- chrome.exe (PID: 1660)
- chrome.exe (PID: 3856)
- chrome.exe (PID: 2960)
- chrome.exe (PID: 1828)
- chrome.exe (PID: 2348)
Reads the computer name
- iexplore.exe (PID: 3208)
- iexplore.exe (PID: 1708)
- chrome.exe (PID: 3840)
- chrome.exe (PID: 4048)
- chrome.exe (PID: 2260)
- chrome.exe (PID: 1404)
- chrome.exe (PID: 2892)
- chrome.exe (PID: 672)
- chrome.exe (PID: 3272)
- chrome.exe (PID: 852)
- chrome.exe (PID: 1436)
- chrome.exe (PID: 672)
Application launched itself
- iexplore.exe (PID: 3208)
- chrome.exe (PID: 3840)
Reads settings of System Certificates
- iexplore.exe (PID: 1708)
- iexplore.exe (PID: 3208)
- chrome.exe (PID: 2260)
Checks Windows Trust Settings
- iexplore.exe (PID: 3208)
- iexplore.exe (PID: 1708)
- chrome.exe (PID: 3840)
Reads the date of Windows installation
- iexplore.exe (PID: 3208)
- chrome.exe (PID: 3272)
Reads internet explorer settings
- iexplore.exe (PID: 1708)
Creates files in the user directory
- iexplore.exe (PID: 3208)
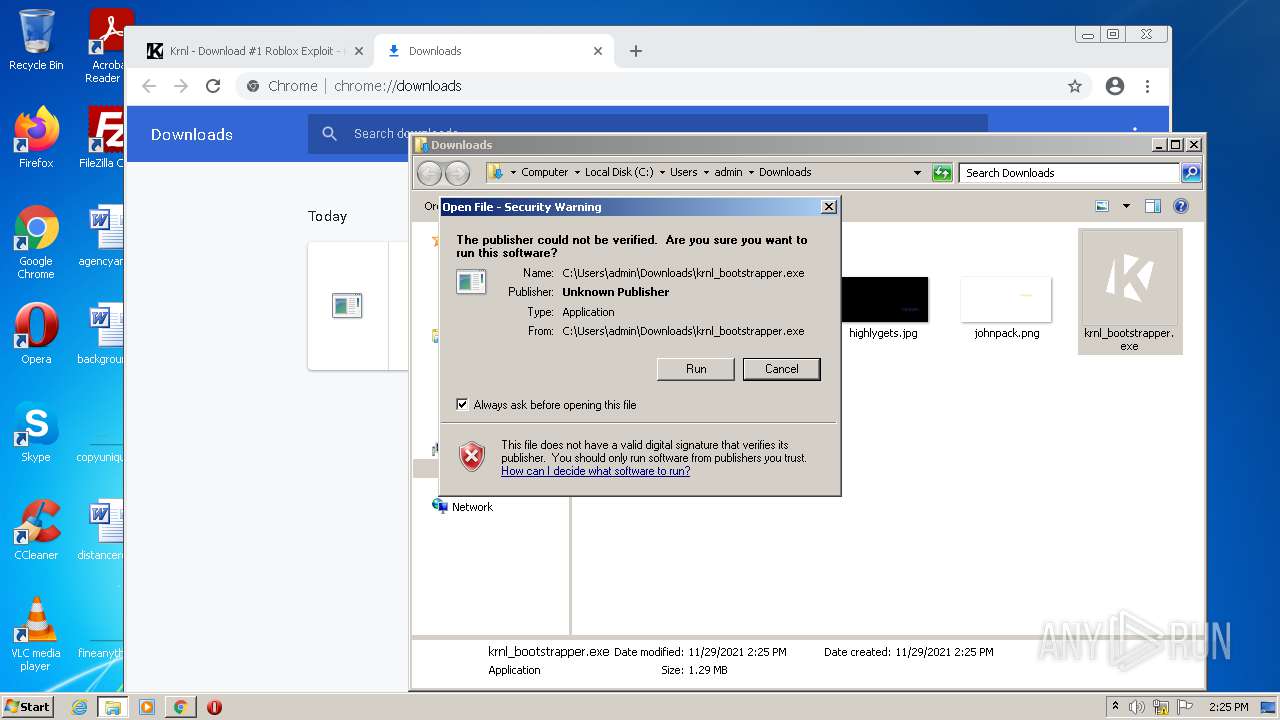
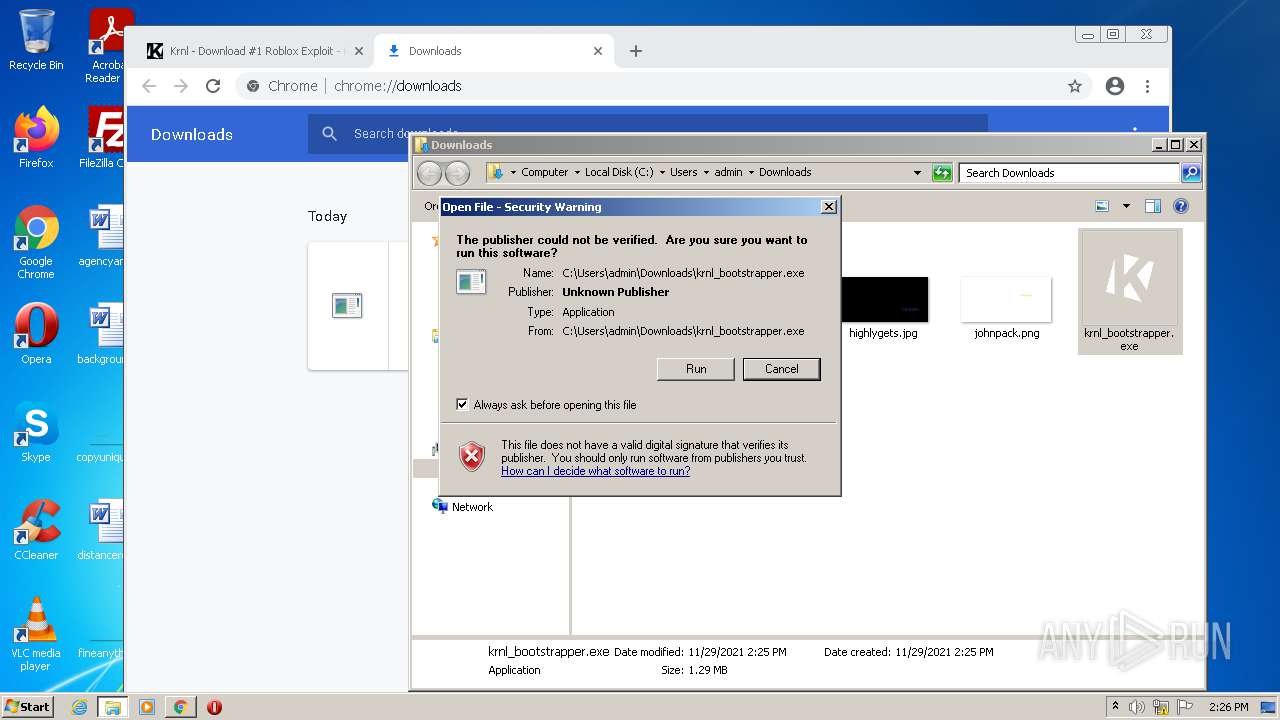
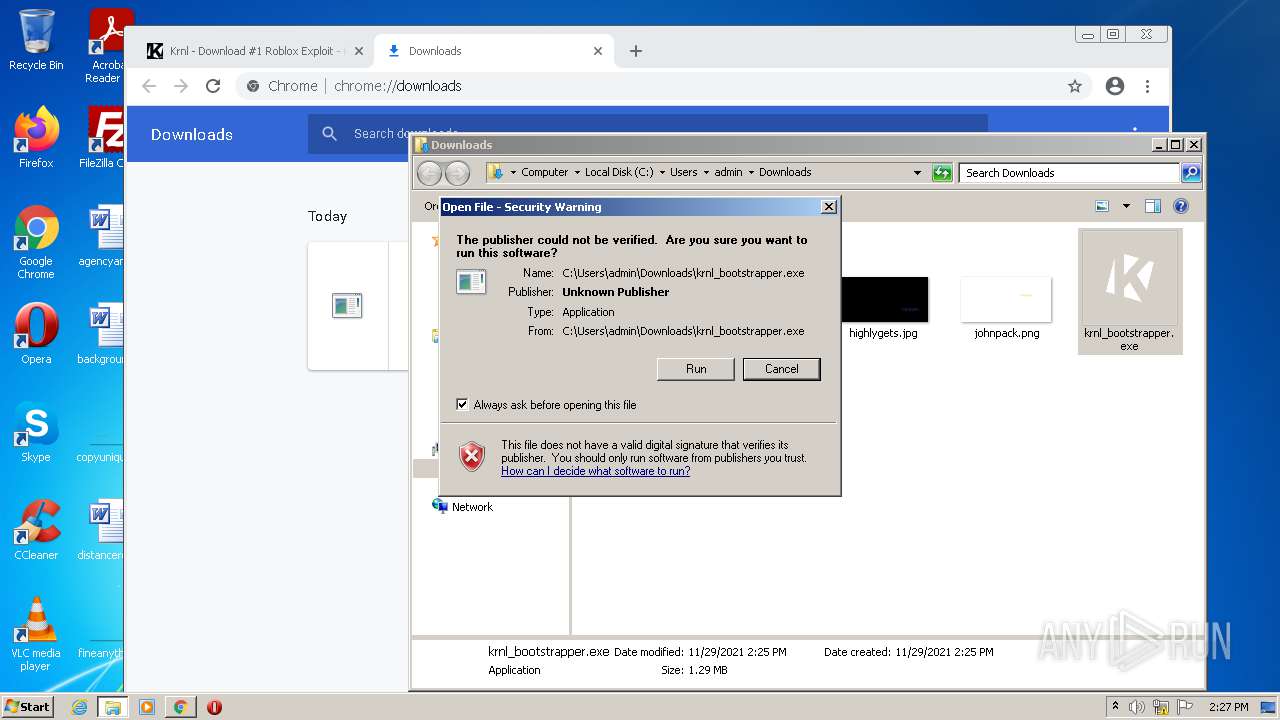
Manual execution by user
- chrome.exe (PID: 3840)
- krnl_bootstrapper.exe (PID: 2720)
- krnl_bootstrapper.exe (PID: 2520)
- krnl_bootstrapper.exe (PID: 2184)
- krnl_bootstrapper.exe (PID: 2272)
Reads the hosts file
- chrome.exe (PID: 3840)
- chrome.exe (PID: 2260)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
100
Monitored processes
45
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1020,11105468550978731304,7355726273868346124,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2372 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 672 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1020,11105468550978731304,7355726273868346124,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4228 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 672 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1020,11105468550978731304,7355726273868346124,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3276 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 744 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1020,11105468550978731304,7355726273868346124,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2204 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 852 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --field-trial-handle=1020,11105468550978731304,7355726273868346124,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3460 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 852 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1020,11105468550978731304,7355726273868346124,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3292 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1088 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1020,11105468550978731304,7355726273868346124,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2304 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1404 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1020,11105468550978731304,7355726273868346124,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=1036 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1436 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1020,11105468550978731304,7355726273868346124,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3260 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1500 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1020,11105468550978731304,7355726273868346124,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3792 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
28 017
Read events
27 726
Write events
281
Delete events
10
Modification events
| (PID) Process: | (3208) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3208) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3208) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30926124 | |||
| (PID) Process: | (3208) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3208) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30926124 | |||
| (PID) Process: | (3208) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3208) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3208) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3208) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3208) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
4
Suspicious files
203
Text files
163
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3208 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:— | SHA256:— | |||
| 1708 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3208 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:— | SHA256:— | |||
| 1708 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 1708 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:— | SHA256:— | |||
| 3208 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_1DC6D7385EA816C957BA2B715AC5C442 | binary | |
MD5:— | SHA256:— | |||
| 1708 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8C9B143C20042A3D63AAF8B7F61C22E2 | binary | |
MD5:— | SHA256:— | |||
| 1708 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8C9B143C20042A3D63AAF8B7F61C22E2 | der | |
MD5:— | SHA256:— | |||
| 3208 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_1DC6D7385EA816C957BA2B715AC5C442 | der | |
MD5:— | SHA256:— | |||
| 1708 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
64
DNS requests
54
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2260 | chrome.exe | GET | 301 | 172.67.214.76:80 | http://krnl.dev/ | US | — | — | malicious |
924 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | — | — | whitelisted |
924 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 43.4 Kb | whitelisted |
3208 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
924 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 9.69 Kb | whitelisted |
924 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 5.63 Kb | whitelisted |
3208 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
924 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 88.5 Kb | whitelisted |
924 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 9.70 Kb | whitelisted |
924 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 20.9 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2260 | chrome.exe | 142.250.185.78:443 | clients2.google.com | Google Inc. | US | whitelisted |
2260 | chrome.exe | 142.250.185.196:443 | www.google.com | Google Inc. | US | whitelisted |
2260 | chrome.exe | 142.250.186.99:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2260 | chrome.exe | 172.217.16.141:443 | accounts.google.com | Google Inc. | US | suspicious |
— | — | 142.250.185.196:443 | www.google.com | Google Inc. | US | whitelisted |
2260 | chrome.exe | 172.67.214.76:443 | krnl.dev | — | US | suspicious |
— | — | 172.67.214.76:443 | krnl.dev | — | US | suspicious |
2260 | chrome.exe | 142.250.185.131:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2260 | chrome.exe | 172.67.214.76:80 | krnl.dev | — | US | suspicious |
2260 | chrome.exe | 142.250.186.42:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
krnl.dev |
| malicious |
www.microsoft.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
dns.msftncsi.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |