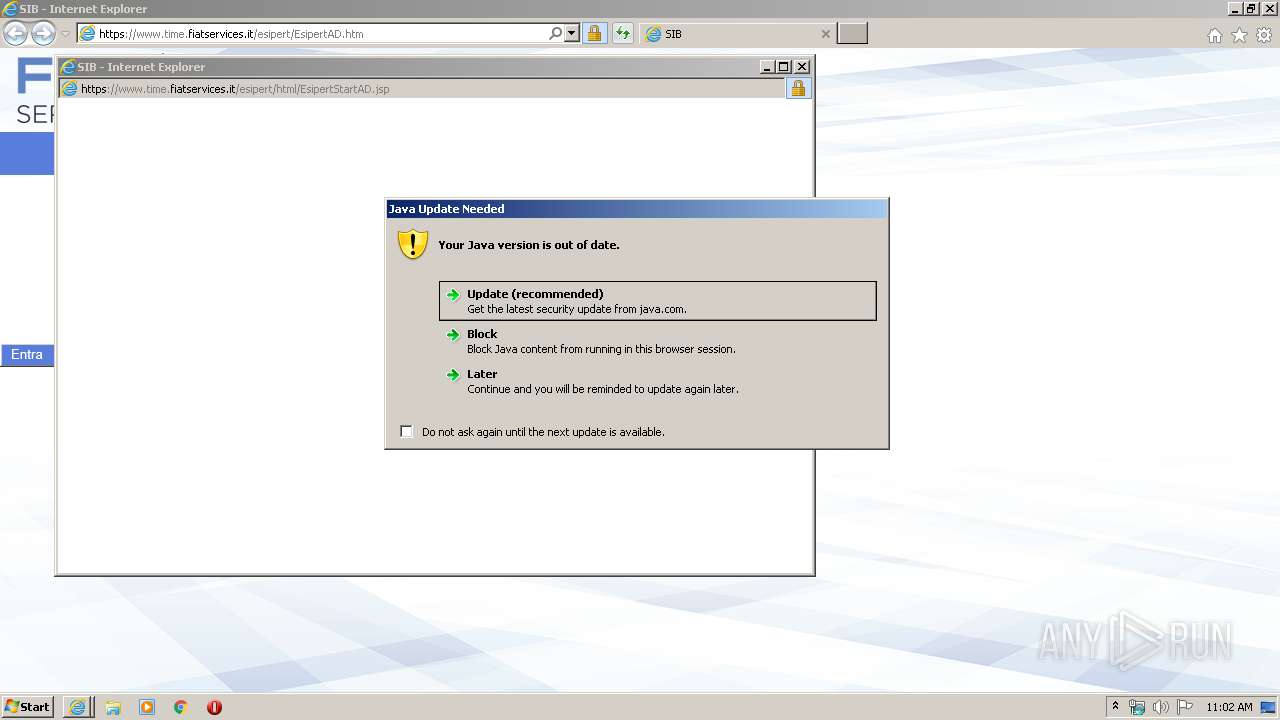
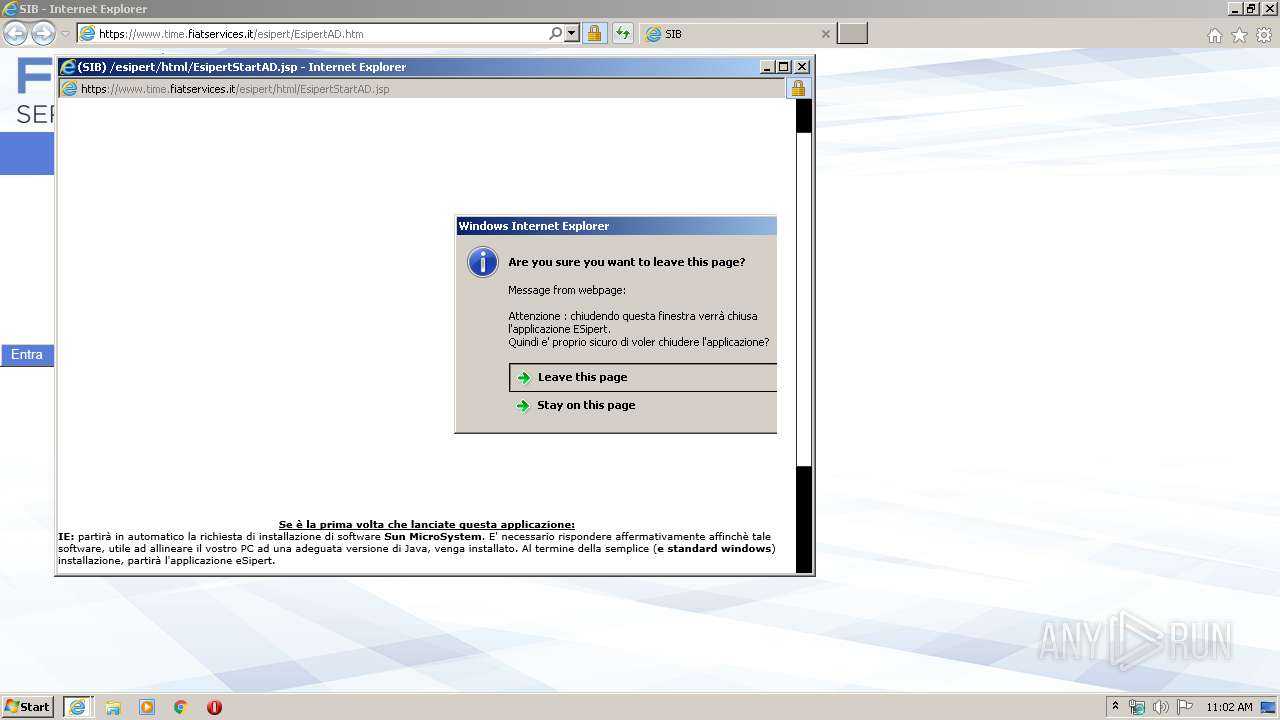
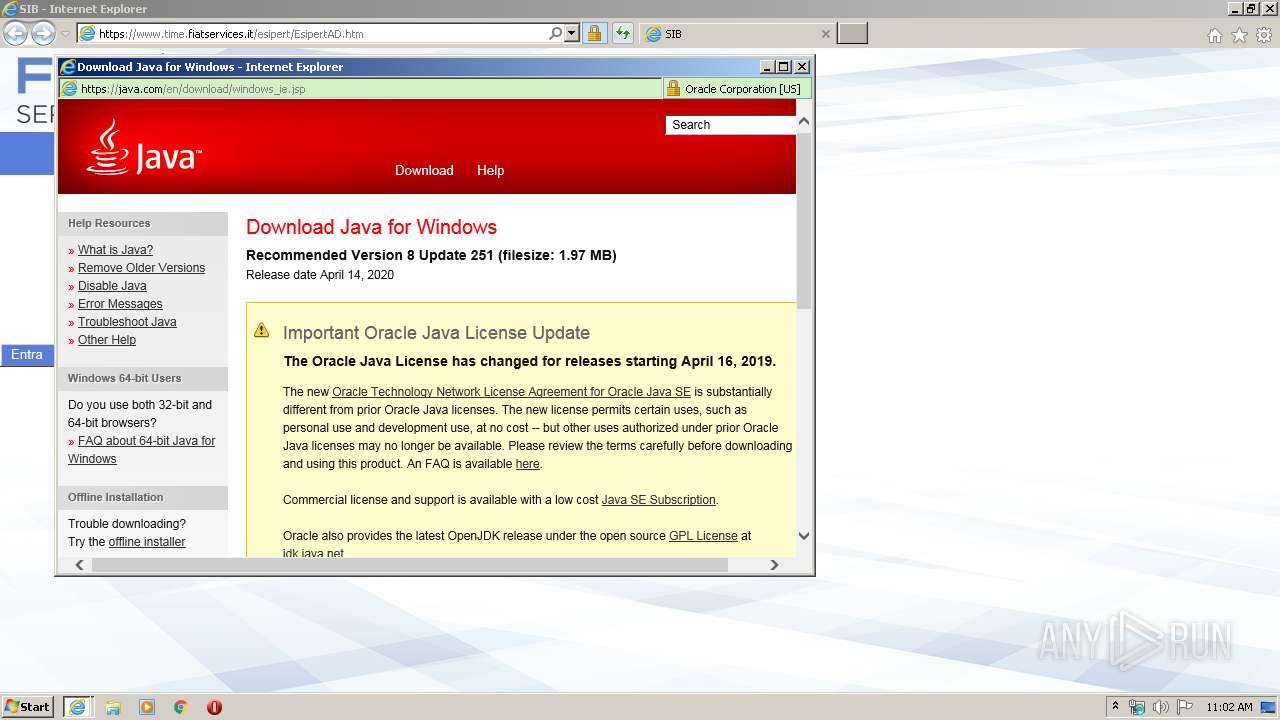
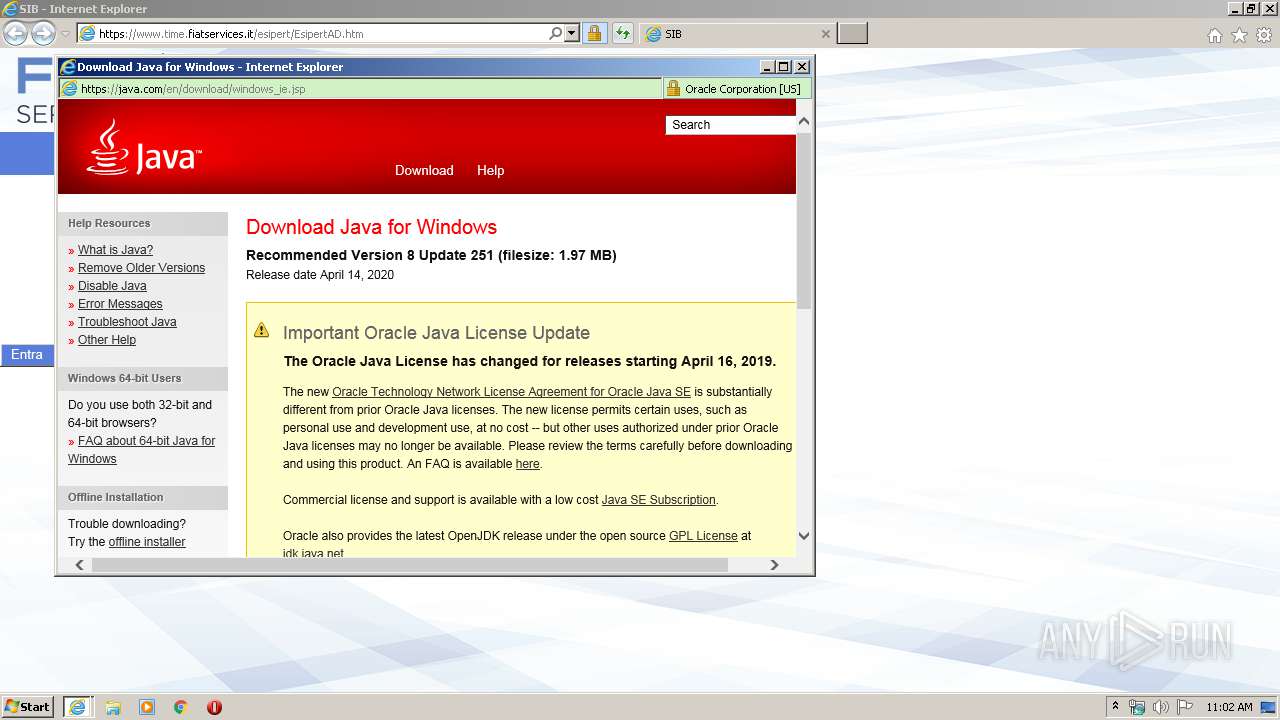
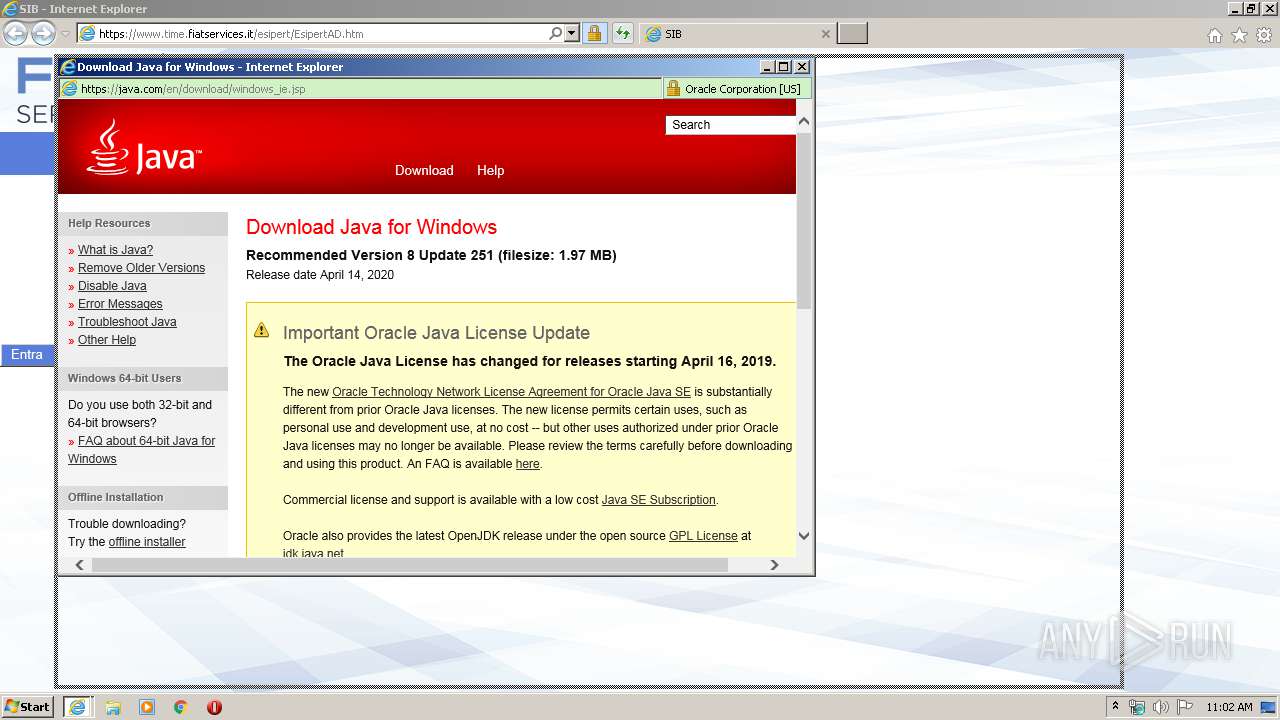
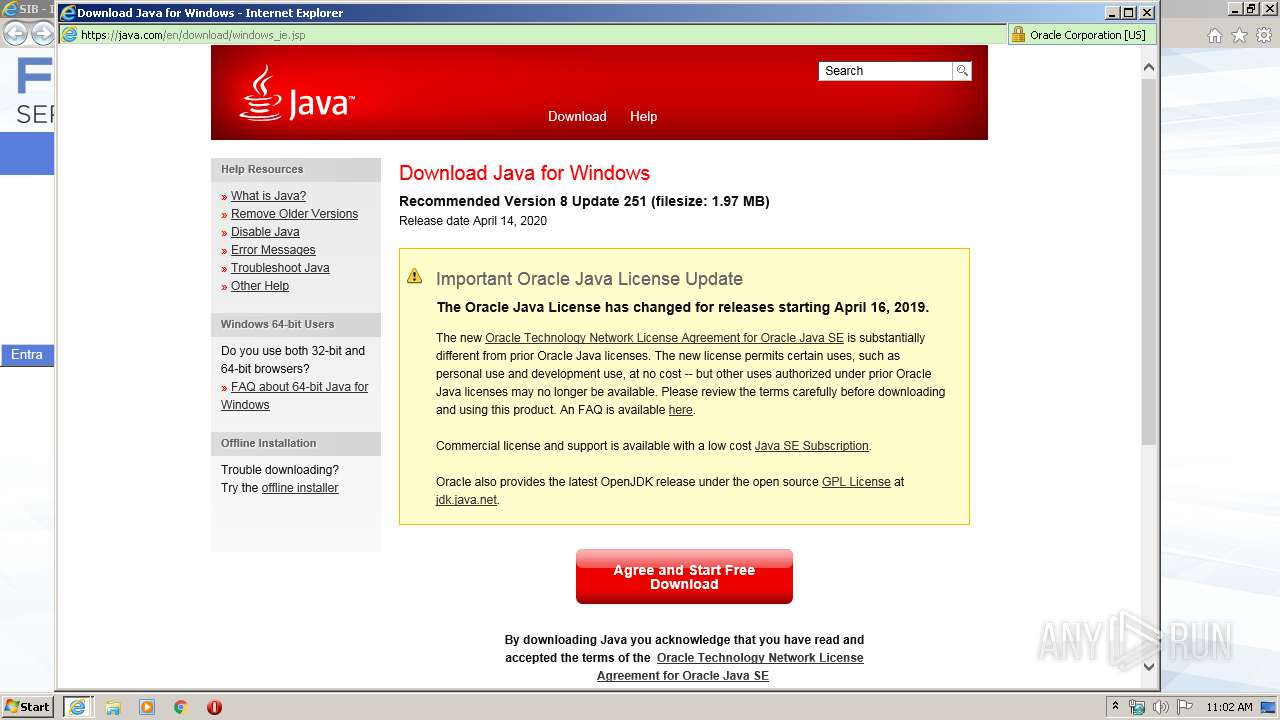
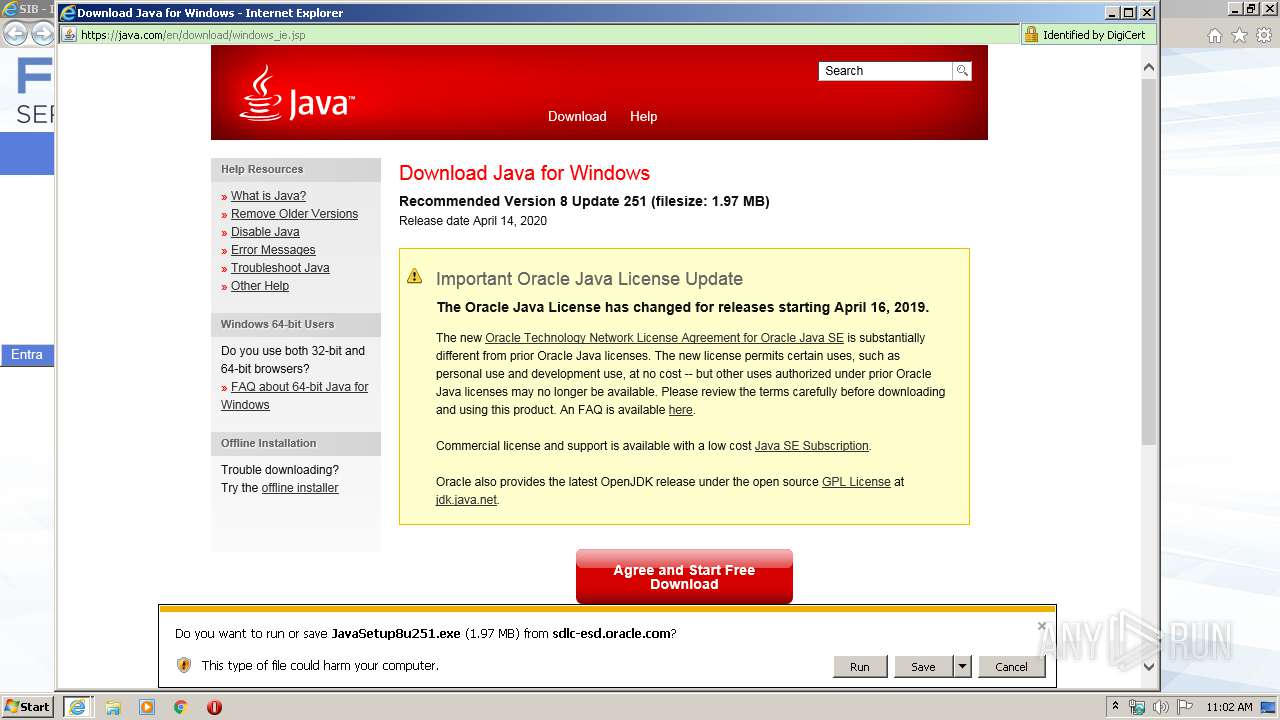
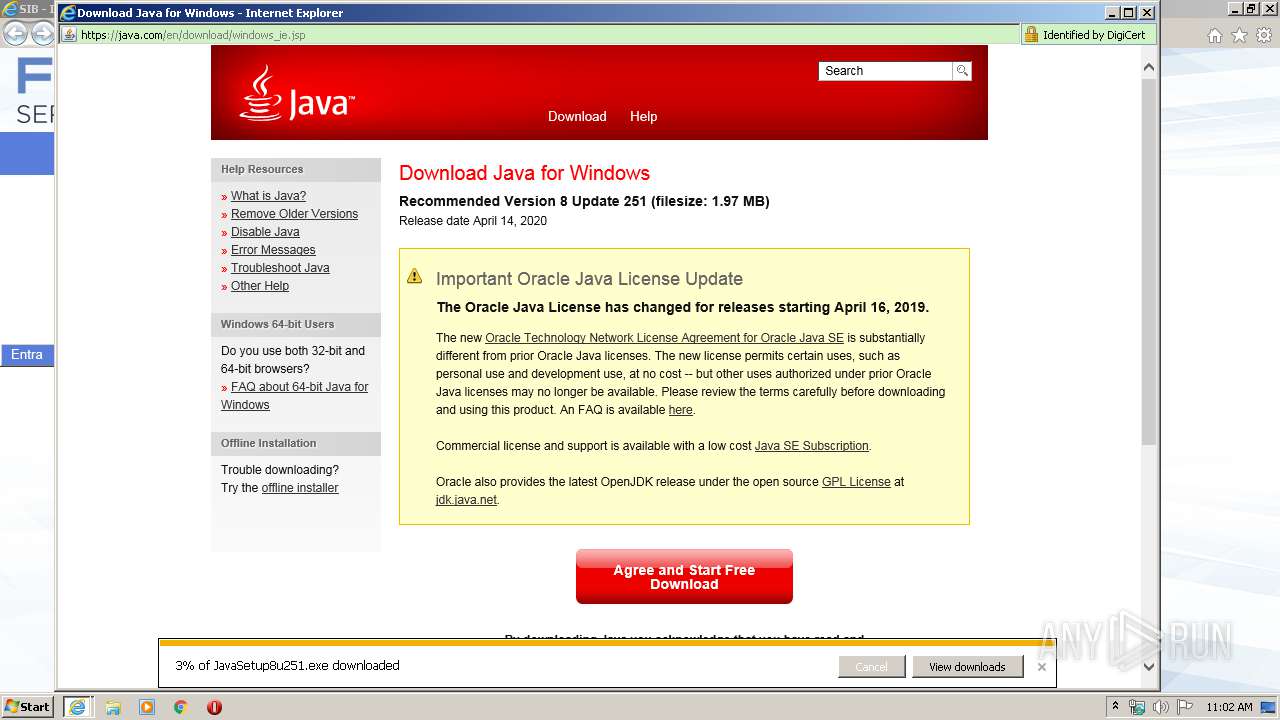
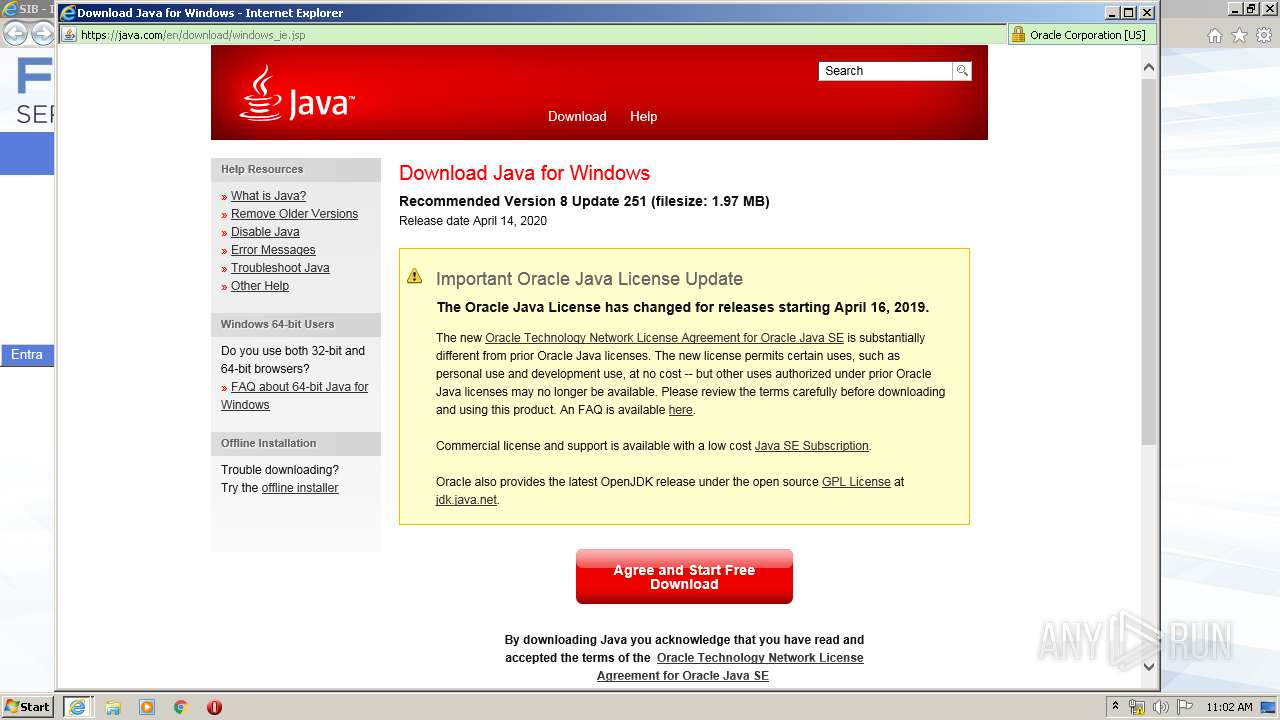
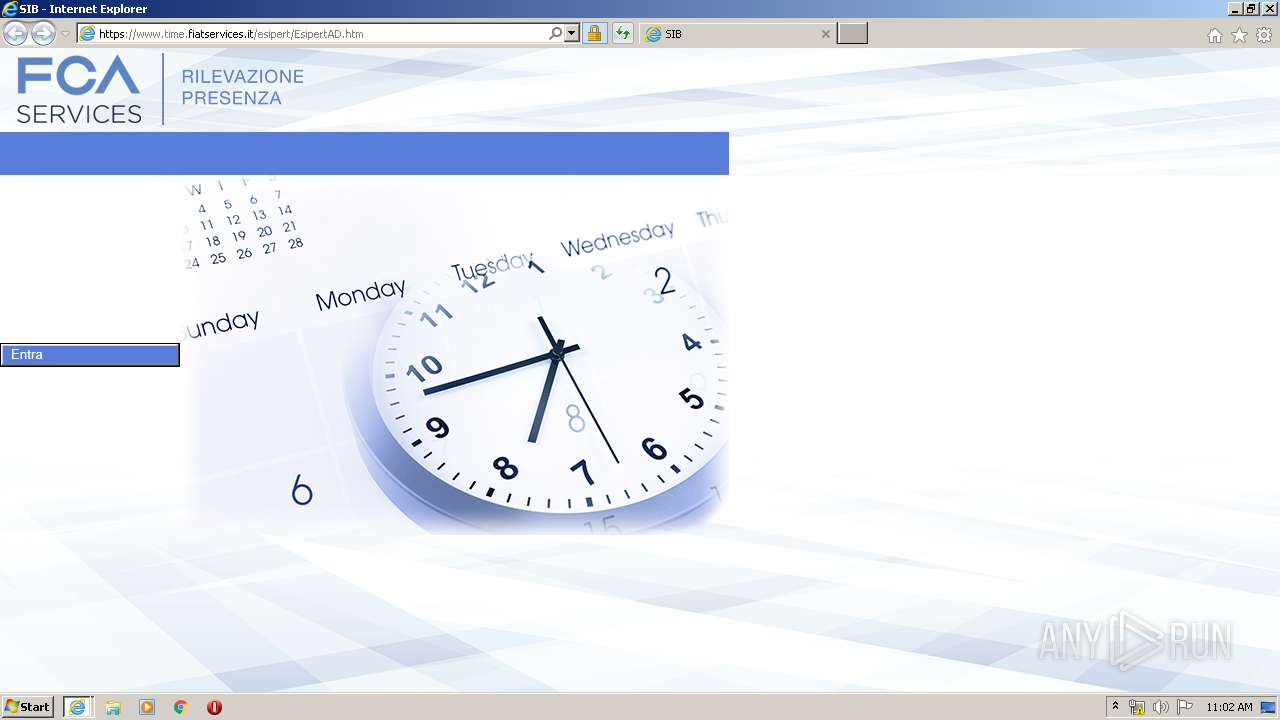
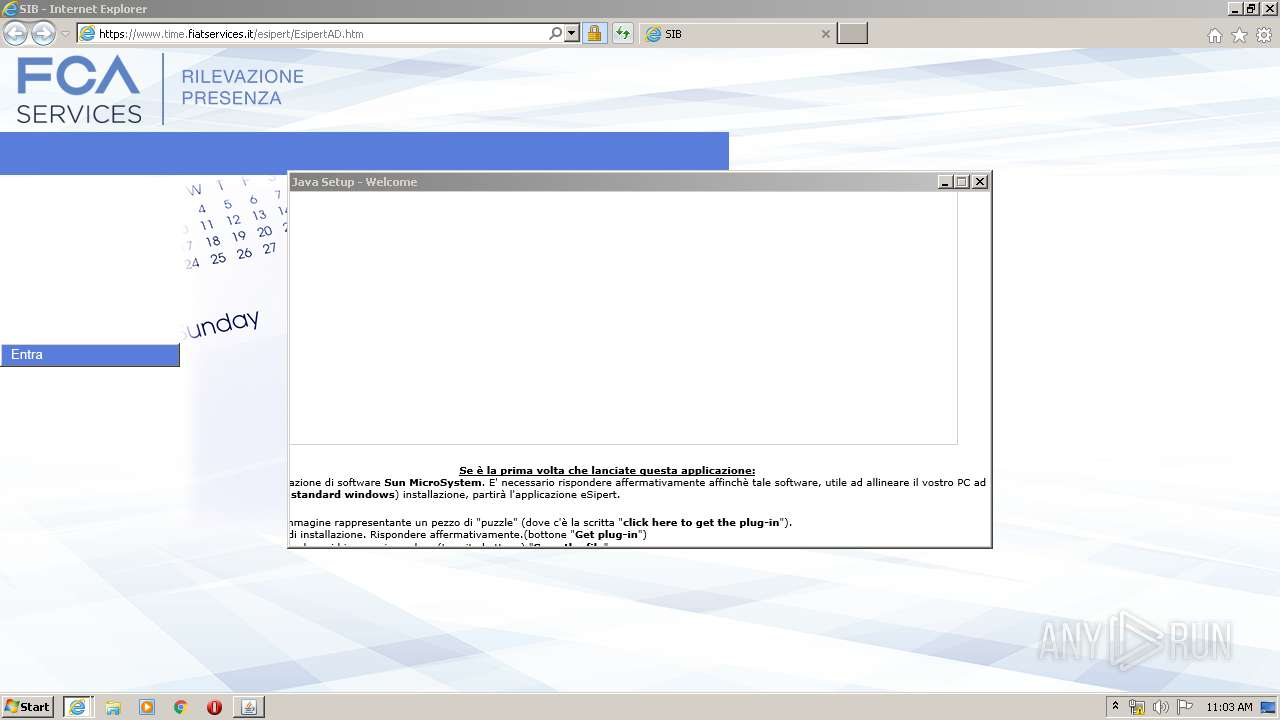
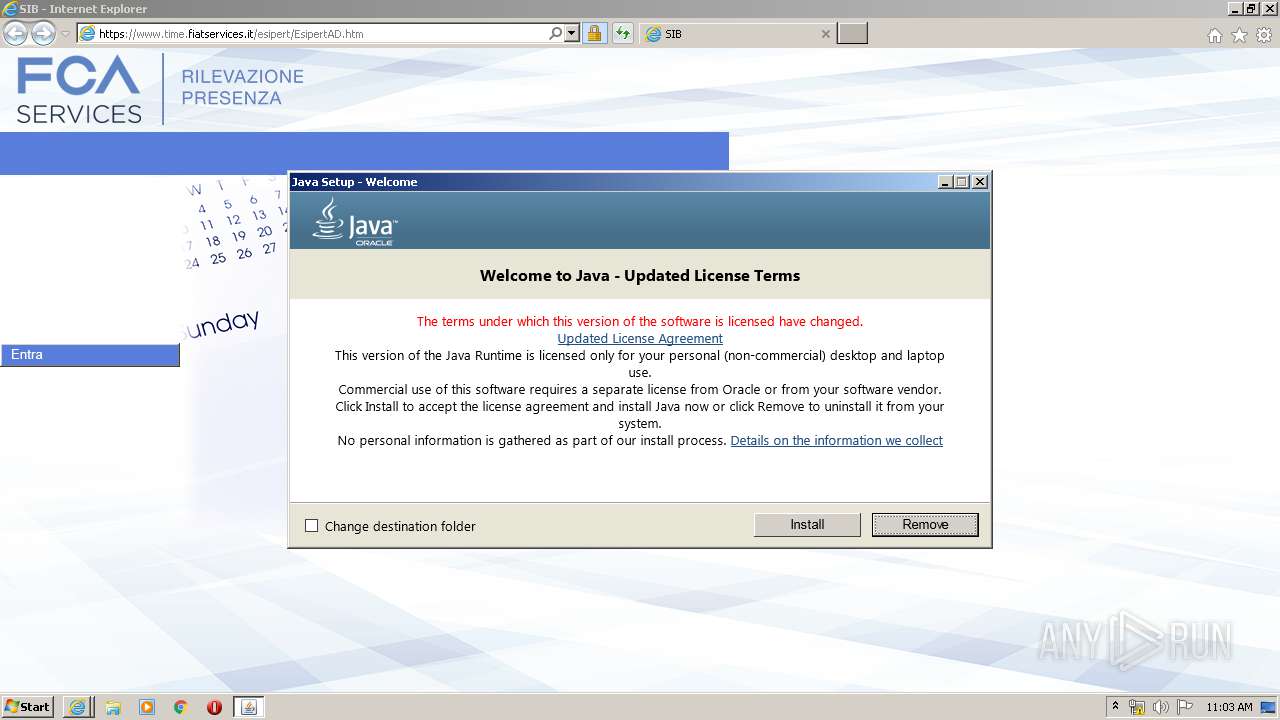
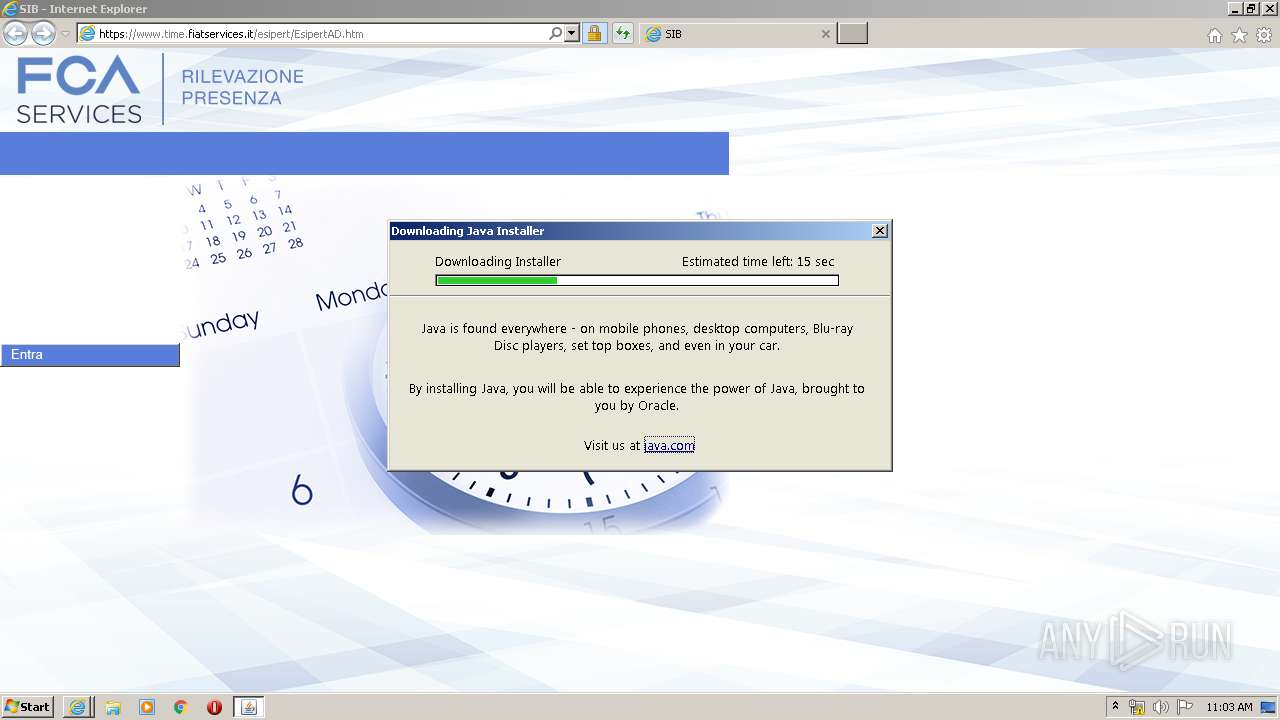
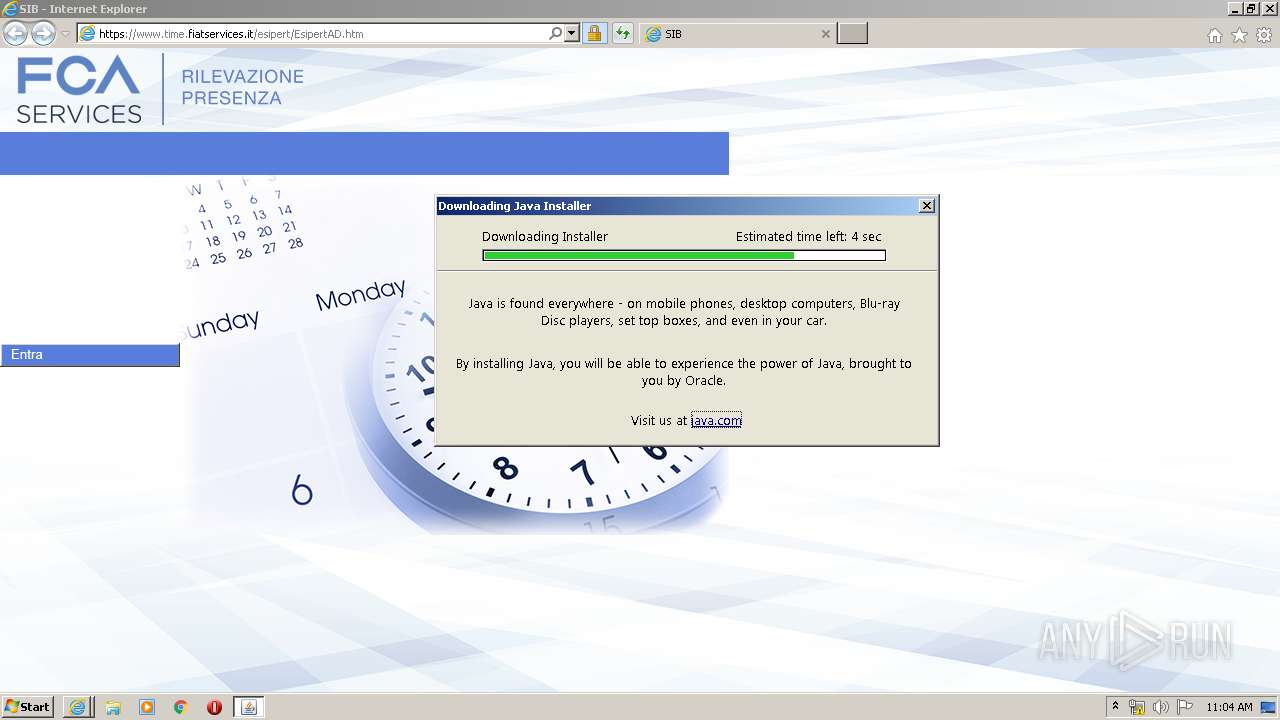
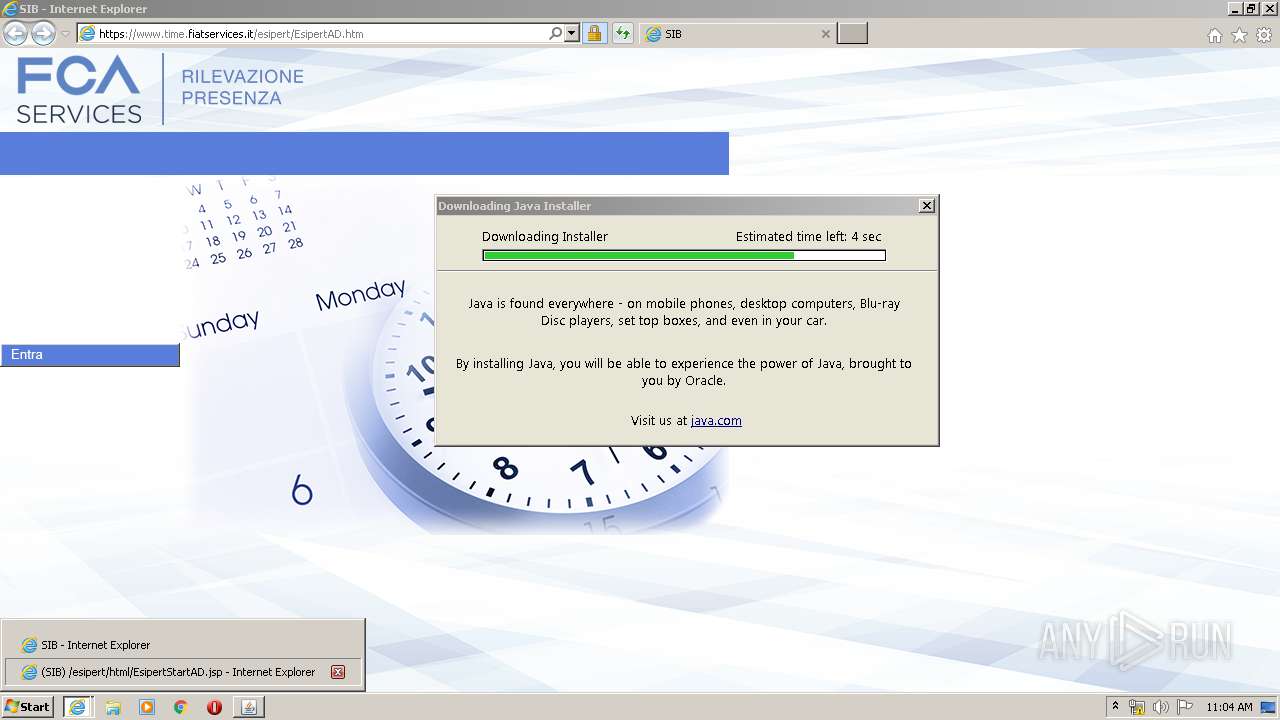
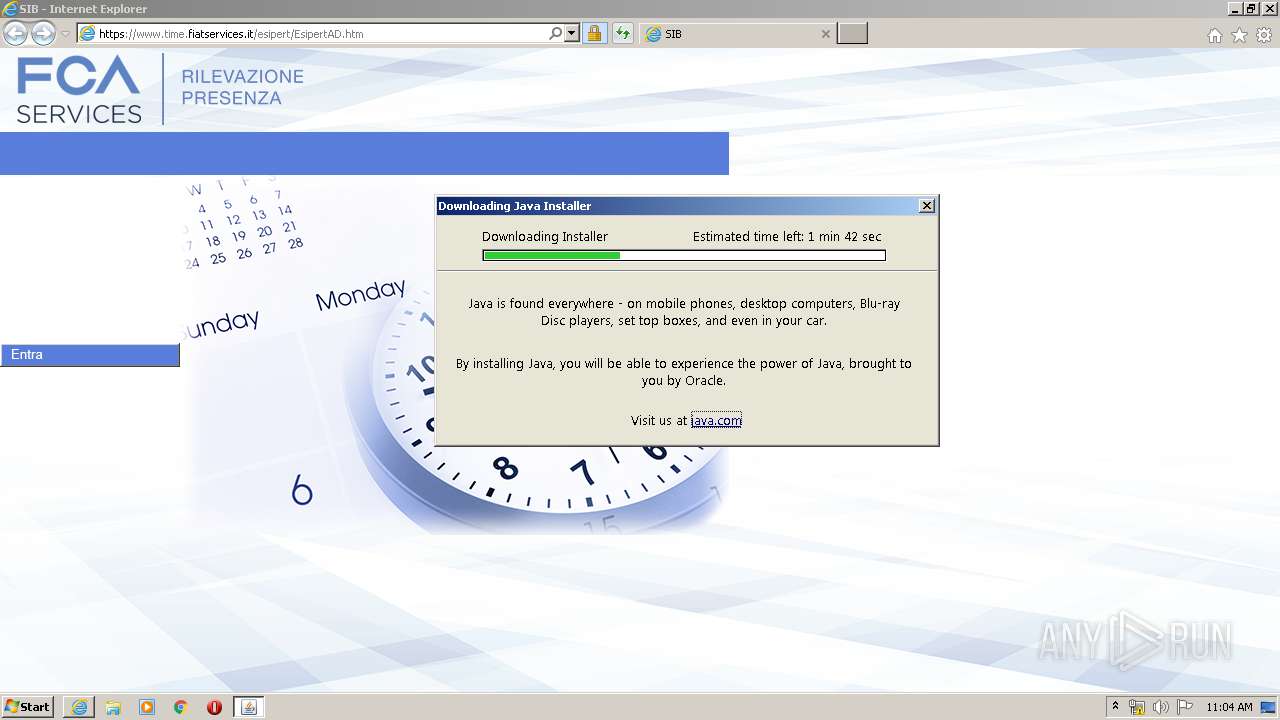
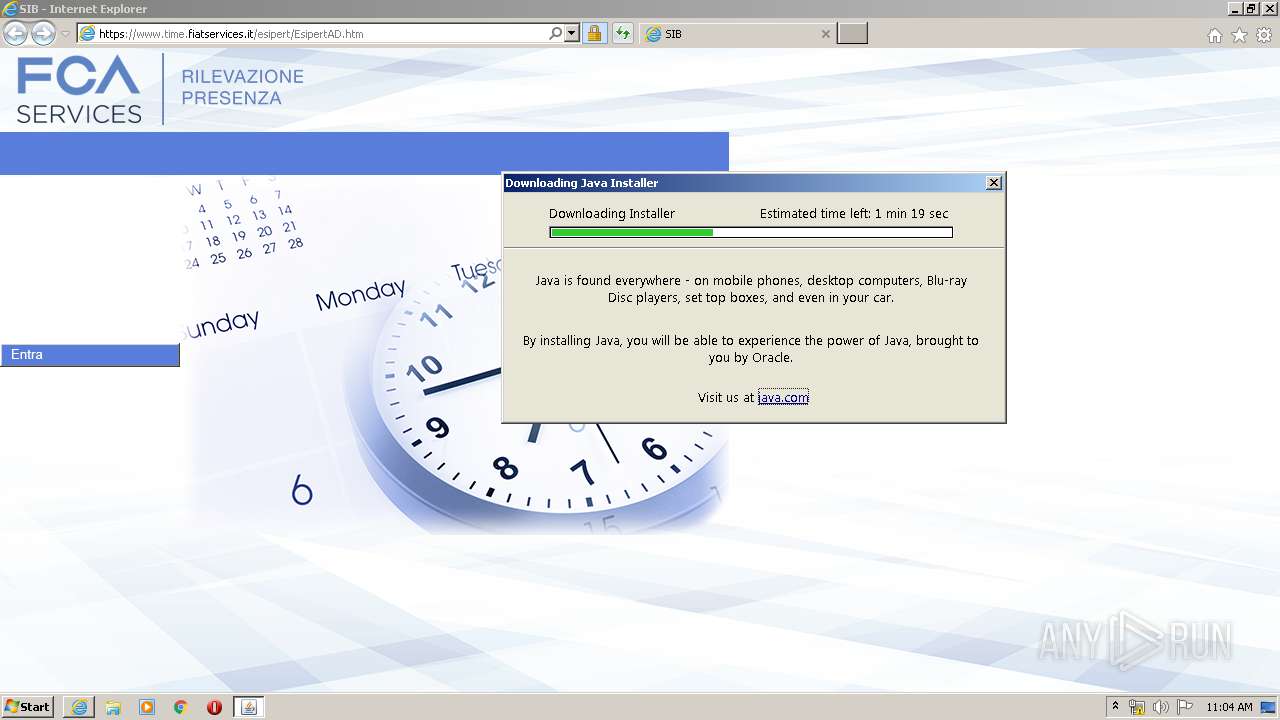
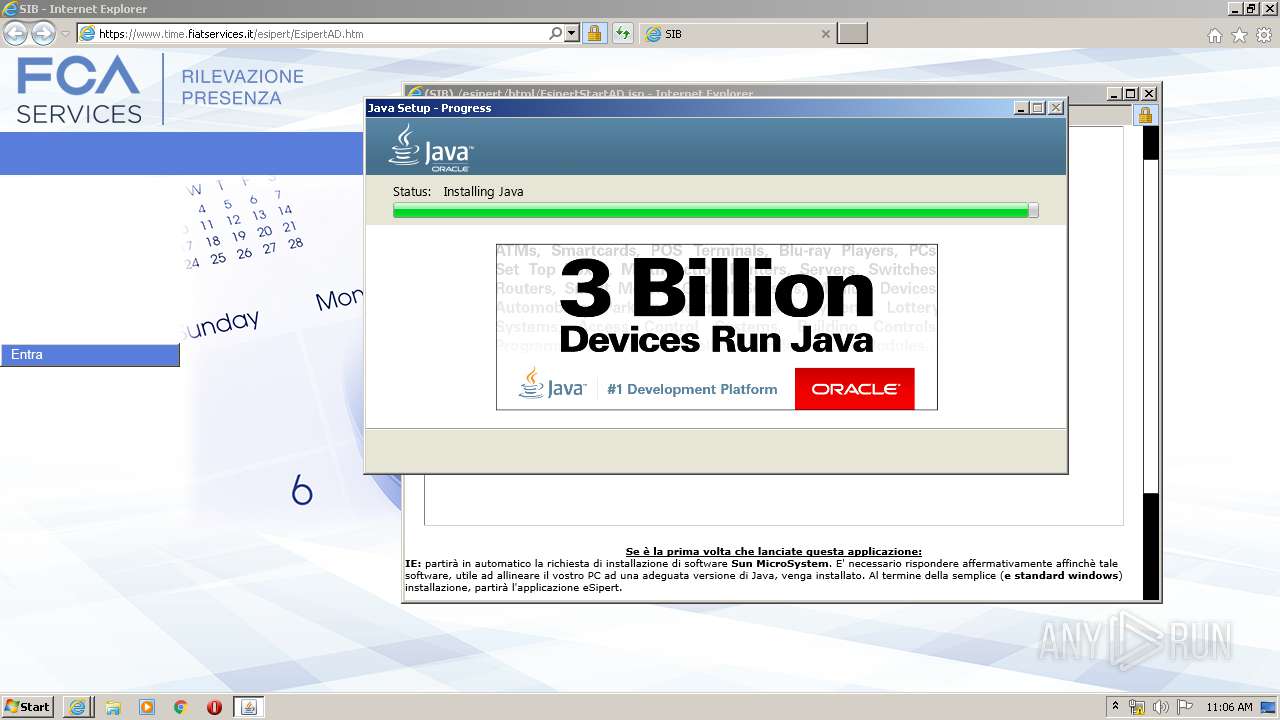
| URL: | https://www.time.fiatservices.it/esipert/EsipertAD.htm |
| Full analysis: | https://app.any.run/tasks/e28be559-d2ca-441c-8d14-09c9e2170ba6 |
| Verdict: | Malicious activity |
| Analysis date: | April 24, 2020, 10:01:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | F029195E2B0B3732FF60B0B8746CBB6A |
| SHA1: | F4686F572E736C6159525699E1E4AC14A33FCEE8 |
| SHA256: | B9978C7E169A698C7B92287749850D776ED96DC11D3E7AEF4D354CD11AAF0F0F |
| SSDEEP: | 3:N8DSLBEdAG4VyRjDI:2OLBE9lRjU |
MALICIOUS
Application was dropped or rewritten from another process
- JavaSetup8u251.exe (PID: 3020)
- JavaSetup8u251.exe (PID: 3460)
- JavaSetup8u251.exe (PID: 2192)
- LZMA_EXE (PID: 1748)
- LZMA_EXE (PID: 4088)
- bspatch.exe (PID: 2376)
- javaw.exe (PID: 1928)
- unpack200.exe (PID: 2340)
- unpack200.exe (PID: 3344)
- unpack200.exe (PID: 3576)
- unpack200.exe (PID: 3288)
- unpack200.exe (PID: 628)
- unpack200.exe (PID: 2792)
- unpack200.exe (PID: 3240)
Loads dropped or rewritten executable
- javaw.exe (PID: 1928)
- unpack200.exe (PID: 628)
- unpack200.exe (PID: 3576)
- unpack200.exe (PID: 3288)
- unpack200.exe (PID: 2340)
- installer.exe (PID: 2360)
- unpack200.exe (PID: 3240)
- unpack200.exe (PID: 3344)
- unpack200.exe (PID: 2792)
Changes settings of System certificates
- JavaSetup8u251.exe (PID: 2192)
SUSPICIOUS
Executes JAVA applets
- iexplore.exe (PID: 2868)
- installer.exe (PID: 2360)
Executable content was dropped or overwritten
- iexplore.exe (PID: 2868)
- iexplore.exe (PID: 3980)
- JavaSetup8u251.exe (PID: 3020)
- JavaSetup8u251.exe (PID: 2192)
- installer.exe (PID: 2360)
Reads Internet Cache Settings
- JavaSetup8u251.exe (PID: 2192)
Starts application with an unusual extension
- JavaSetup8u251.exe (PID: 2192)
Reads internet explorer settings
- JavaSetup8u251.exe (PID: 2192)
Creates files in the program directory
- unpack200.exe (PID: 2340)
- unpack200.exe (PID: 3288)
- unpack200.exe (PID: 3344)
- unpack200.exe (PID: 3240)
- unpack200.exe (PID: 628)
- bspatch.exe (PID: 2376)
- unpack200.exe (PID: 2792)
- unpack200.exe (PID: 3576)
- javaw.exe (PID: 1928)
- installer.exe (PID: 2360)
Modifies the open verb of a shell class
- installer.exe (PID: 2360)
Removes files from Windows directory
- installer.exe (PID: 2360)
Creates files in the Windows directory
- installer.exe (PID: 2360)
Check for Java to be installed
- installer.exe (PID: 2360)
Adds / modifies Windows certificates
- JavaSetup8u251.exe (PID: 2192)
Creates COM task schedule object
- installer.exe (PID: 2360)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 3980)
- iexplore.exe (PID: 2868)
Reads internet explorer settings
- iexplore.exe (PID: 2868)
Application launched itself
- iexplore.exe (PID: 3980)
- msiexec.exe (PID: 1500)
Changes internet zones settings
- iexplore.exe (PID: 3980)
Creates files in the user directory
- iexplore.exe (PID: 2868)
- iexplore.exe (PID: 3980)
Reads settings of System Certificates
- JavaSetup8u251.exe (PID: 2192)
- iexplore.exe (PID: 2868)
- iexplore.exe (PID: 3980)
Creates files in the program directory
- msiexec.exe (PID: 1500)
Creates a software uninstall entry
- msiexec.exe (PID: 1500)
Dropped object may contain Bitcoin addresses
- JavaSetup8u251.exe (PID: 2192)
- installer.exe (PID: 2360)
- MsiExec.exe (PID: 2592)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3980)
Changes settings of System certificates
- iexplore.exe (PID: 3980)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3980)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
71
Monitored processes
22
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 628 | "C:\Program Files\Java\jre1.8.0_251\bin\unpack200.exe" -r "C:\Program Files\Java\jre1.8.0_251\lib/ext/localedata.pack" "C:\Program Files\Java\jre1.8.0_251\lib/ext/localedata.jar" | C:\Program Files\Java\jre1.8.0_251\bin\unpack200.exe | installer.exe | ||||||||||||
User: SYSTEM Company: Oracle Corporation Integrity Level: SYSTEM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2510.8 Modules
| |||||||||||||||
| 1500 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1748 | "C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_251\LZMA_EXE" d "C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_251\au.msi" "C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_251\msi.tmp" | C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_251\LZMA_EXE | — | JavaSetup8u251.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1928 | "C:\Program Files\Java\jre1.8.0_251\bin\javaw.exe" -Xshare:dump -Djdk.disableLastUsageTracking | C:\Program Files\Java\jre1.8.0_251\bin\javaw.exe | installer.exe | ||||||||||||
User: SYSTEM Company: Oracle Corporation Integrity Level: SYSTEM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2510.8 Modules
| |||||||||||||||
| 2192 | "C:\Users\admin\AppData\Local\Temp\jds10992281.tmp\JavaSetup8u251.exe" | C:\Users\admin\AppData\Local\Temp\jds10992281.tmp\JavaSetup8u251.exe | JavaSetup8u251.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java Platform SE binary Exit code: 0 Version: 8.0.2510.8 Modules
| |||||||||||||||
| 2340 | "C:\Program Files\Java\jre1.8.0_251\bin\unpack200.exe" -r "C:\Program Files\Java\jre1.8.0_251\lib/plugin.pack" "C:\Program Files\Java\jre1.8.0_251\lib/plugin.jar" | C:\Program Files\Java\jre1.8.0_251\bin\unpack200.exe | installer.exe | ||||||||||||
User: SYSTEM Company: Oracle Corporation Integrity Level: SYSTEM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2510.8 Modules
| |||||||||||||||
| 2360 | "C:\Program Files\Java\jre1.8.0_251\installer.exe" /s INSTALLDIR="C:\Program Files\Java\jre1.8.0_251\\" INSTALL_SILENT=1 REPAIRMODE=0 ProductCode={26A24AE4-039D-4CA4-87B4-2F32180251F0} | C:\Program Files\Java\jre1.8.0_251\installer.exe | msiexec.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java Platform SE binary Exit code: 0 Version: 8.0.2510.8 Modules
| |||||||||||||||
| 2376 | "bspatch.exe" baseimagefam8 newimage diff | C:\ProgramData\Oracle\Java\installcache\11170046.tmp\bspatch.exe | installer.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 2524 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_9\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.11.92.2" "update" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | — | iexplore.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: LOW Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2592 | C:\Windows\system32\MsiExec.exe -Embedding 5F3215E9B231A46303DCA000201C4E3C | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
16 284
Read events
2 270
Write events
10 599
Delete events
3 415
Modification events
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 1813143328 | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30808607 | |||
| (PID) Process: | (2868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\LowCache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\LowCache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
Executable files
157
Suspicious files
55
Text files
434
Unknown types
29
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2868 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab2C2.tmp | — | |
MD5:— | SHA256:— | |||
| 2868 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar2C3.tmp | — | |
MD5:— | SHA256:— | |||
| 3980 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2868 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\EsipertAD[1].htm | html | |
MD5:— | SHA256:— | |||
| 2868 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_D975BBA8033175C8D112023D8A7A8AD6 | der | |
MD5:— | SHA256:— | |||
| 2868 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\fca_service_rilevazione_presenze[1].png | image | |
MD5:— | SHA256:— | |||
| 2868 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\EsipertStartAD[1].htm | html | |
MD5:— | SHA256:— | |||
| 2868 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\1E11E75149C17A93653DA7DC0B8CF53F_D112A7898E2B00A9AE5B6E335558B3D8 | der | |
MD5:— | SHA256:— | |||
| 2868 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\FCA_sfondo_solo_linee[1].png | image | |
MD5:— | SHA256:— | |||
| 2868 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EDC238BFF48A31D55A97E1E93892934B_C31B2498754E340573F1336DE607D619 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
79
DNS requests
42
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2868 | iexplore.exe | GET | 301 | 23.67.139.162:80 | http://java.com/inst-dl-redirect | NL | — | — | whitelisted |
2868 | iexplore.exe | GET | 200 | 192.124.249.24:80 | http://ocsp.godaddy.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTkIInKBAzXkF0Qh0pel3lfHJ9GPAQU0sSw0pHUTBFxs2HLPaH%2B3ahq1OMCAxvnFQ%3D%3D | US | der | 1.66 Kb | whitelisted |
2868 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/DigiCertGlobalRootCA.crl | US | der | 581 b | whitelisted |
2868 | iexplore.exe | GET | 200 | 192.124.249.24:80 | http://ocsp.godaddy.com//MEkwRzBFMEMwQTAJBgUrDgMCGgUABBS2CA1fbGt26xPkOKX4ZguoUjM0TgQUQMK9J47MNIMwojPX%2B2yz8LQsgM4CCEJfUEAx8qrg | US | der | 1.73 Kb | whitelisted |
2868 | iexplore.exe | GET | 301 | 23.67.139.162:80 | http://java.com/inst-dl-redirect/ | NL | — | — | whitelisted |
3980 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2868 | iexplore.exe | GET | 200 | 192.124.249.24:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | der | 1.69 Kb | whitelisted |
2868 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQQX6Z6gAidtSefNc6DC0OInqPHDQQUD4BhHIIxYdUvKOeNRji0LOHG2eICEAQW2O4WvoepO0Q943hguDk%3D | US | der | 471 b | whitelisted |
3980 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
3980 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2868 | iexplore.exe | 151.91.36.62:443 | www.time.fiatservices.it | Fiat Information Technology, Excellence and Methods S.p.A. | IT | unknown |
2868 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2868 | iexplore.exe | 23.67.139.162:80 | java.com | Akamai International B.V. | NL | suspicious |
2868 | iexplore.exe | 13.35.253.92:443 | consent.trustarc.com | — | US | unknown |
3980 | iexplore.exe | 151.91.36.62:443 | www.time.fiatservices.it | Fiat Information Technology, Excellence and Methods S.p.A. | IT | unknown |
2868 | iexplore.exe | 192.124.249.24:80 | ocsp.godaddy.com | Sucuri | US | suspicious |
2868 | iexplore.exe | 23.67.139.162:443 | java.com | Akamai International B.V. | NL | suspicious |
2868 | iexplore.exe | 143.204.202.56:443 | consent-st.trustarc.com | — | US | malicious |
3980 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2868 | iexplore.exe | 23.67.141.135:443 | static.oracle.com | Akamai International B.V. | NL | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.time.fiatservices.it |
| unknown |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
java.com |
| whitelisted |
static.oracle.com |
| whitelisted |
consent.trustarc.com |
| shared |
c.oracleinfinity.io |
| whitelisted |
ocsp.godaddy.com |
| whitelisted |