| File name: | nircmd.exe |
| Full analysis: | https://app.any.run/tasks/56be9a48-7829-40dd-a297-aedeb62155d9 |
| Verdict: | Malicious activity |
| Analysis date: | March 20, 2024, 03:42:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | A1CD6A64E8F8AD5D4B6C07DC4113C7EC |
| SHA1: | 60E2F48A51C061BBA72A08F34BE781354F87AA49 |
| SHA256: | B994AE5CBFB5AD308656E9A8BF7A4A866FDEB9E23699F89F048D7F92E6BB8577 |
| SSDEEP: | 768:UDR7drWxRrYJAgERvFAREX5DyzaccyOkVDIBF9K/phcanwUaajMIWCW2jsV/:2A3cJAgmSRC5DcLxIBLGwUgIW2sV/ |
MALICIOUS
Drops the executable file immediately after the start
- nircmd.exe (PID: 2648)
SUSPICIOUS
Checks for Java to be installed
- NCALayer.exe (PID: 2672)
- NCALayer.exe (PID: 2060)
Process requests binary or script from the Internet
- javaw.exe (PID: 956)
Reads the Internet Settings
- javaw.exe (PID: 956)
- javaw.exe (PID: 1900)
Reads settings of System Certificates
- javaw.exe (PID: 956)
- javaw.exe (PID: 1900)
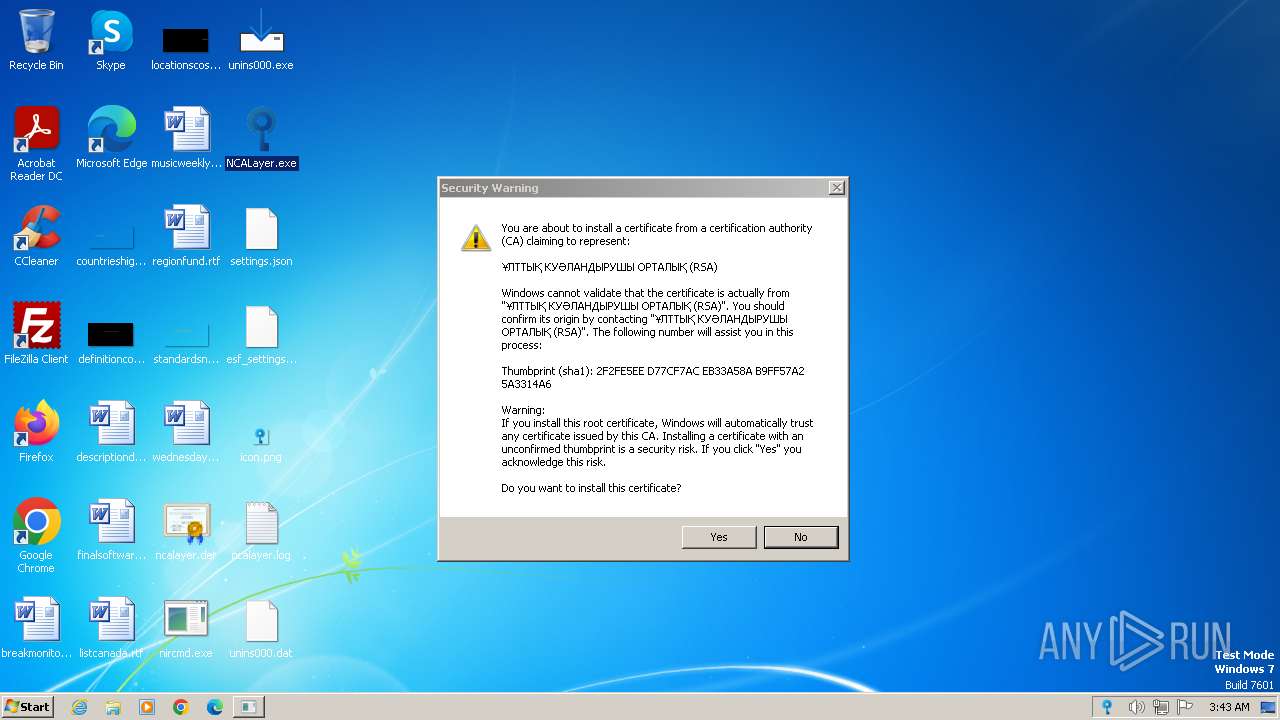
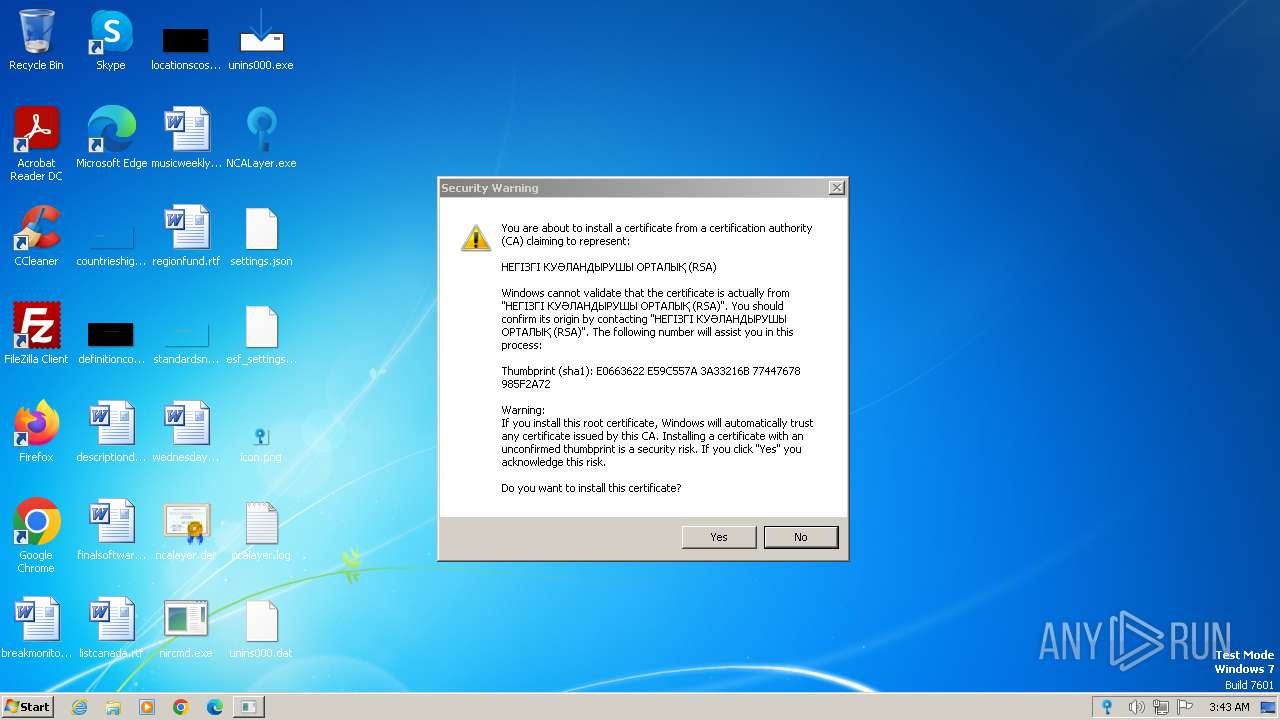
Adds/modifies Windows certificates
- javaw.exe (PID: 956)
- javaw.exe (PID: 1900)
INFO
Checks supported languages
- nircmd.exe (PID: 2648)
- nircmd.exe (PID: 2292)
- javaw.exe (PID: 956)
- NCALayer.exe (PID: 2672)
- NCALayer.exe (PID: 2060)
- javaw.exe (PID: 1900)
Manual execution by a user
- nircmd.exe (PID: 2292)
- NCALayer.exe (PID: 2672)
NirSoft software is detected
- nircmd.exe (PID: 2648)
- nircmd.exe (PID: 2292)
Create files in a temporary directory
- javaw.exe (PID: 956)
- javaw.exe (PID: 1900)
Creates files in the program directory
- javaw.exe (PID: 956)
Reads the computer name
- javaw.exe (PID: 956)
- javaw.exe (PID: 1900)
Creates files or folders in the user directory
- javaw.exe (PID: 956)
- javaw.exe (PID: 1900)
Checks proxy server information
- javaw.exe (PID: 956)
- javaw.exe (PID: 1900)
Reads the machine GUID from the registry
- javaw.exe (PID: 956)
- javaw.exe (PID: 1900)
Reads the software policy settings
- javaw.exe (PID: 956)
- javaw.exe (PID: 1900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (39.3) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (38.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.5) |
| .exe | | | Win32 Executable (generic) (6.5) |
| .exe | | | Generic Win/DOS Executable (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:08:01 17:53:49+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 45056 |
| InitializedDataSize: | 4096 |
| UninitializedDataSize: | 61440 |
| EntryPoint: | 0x19ef0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.8.6.231 |
| ProductVersionNumber: | 2.8.6.231 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | NirSoft |
| FileDescription: | NirCmd |
| FileVersion: | 2.86 |
| InternalName: | NirCmd |
| LegalCopyright: | Copyright © 2003 - 2019 Nir Sofer |
| OriginalFileName: | NirCmd.exe |
| ProductName: | NirCmd |
| ProductVersion: | 2.86 |
Total processes
44
Monitored processes
7
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 956 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar "C:\Users\admin\Desktop\NCALayer.exe" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | NCALayer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 1900 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar "C:\Users\admin\Desktop\NCALayer.exe" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | NCALayer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 2060 | "C:\Users\admin\Desktop\NCALayer.exe" | C:\Users\admin\Desktop\NCALayer.exe | — | javaw.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2292 | "C:\Users\admin\Desktop\nircmd.exe" | C:\Users\admin\Desktop\nircmd.exe | — | explorer.exe | |||||||||||
User: admin Company: NirSoft Integrity Level: MEDIUM Description: NirCmd Exit code: 0 Version: 2.86 Modules
| |||||||||||||||
| 2648 | "C:\Users\admin\AppData\Local\Temp\nircmd.exe" | C:\Users\admin\AppData\Local\Temp\nircmd.exe | — | explorer.exe | |||||||||||
User: admin Company: NirSoft Integrity Level: MEDIUM Description: NirCmd Exit code: 0 Version: 2.86 Modules
| |||||||||||||||
| 2672 | "C:\Users\admin\Desktop\NCALayer.exe" | C:\Users\admin\Desktop\NCALayer.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2688 | C:\Windows\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
16 139
Read events
16 069
Write events
50
Delete events
20
Modification events
| (PID) Process: | (956) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: javaw.exe | |||
| (PID) Process: | (956) javaw.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (956) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\SystemCertificates\Root\Certificates |
| Operation: | delete value | Name: | C7C20953EB5AC83C81CA388170EEC982E577F810 |
Value: | |||
| (PID) Process: | (956) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\SystemCertificates\Root\Certificates\C7C20953EB5AC83C81CA388170EEC982E577F810 |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000F7998935234BC4DE2CB672C84BD550341900000001000000100000000FED148DCA9288CFE9E8CFEDE332D41E0F00000001000000200000003940FA3A00F54D92B7F88E2D48C2772C8ABB2A13E49A0D26CD13424C4B551832030000000100000014000000C7C20953EB5AC83C81CA388170EEC982E577F810140000000100000014000000396A962A0D9CA2D65CF53FD9D5915A728280AB800200000001000000CC0000001C0000006C00000001000000000000000000000000000000010000007B00410032003900380043003100300039002D0036004300440030002D0034004600410044002D0042003300370046002D004600430039003500360045003100340046004200440036007D00000000004D006900630072006F0073006F0066007400200045006E00680061006E006300650064002000430072007900700074006F0067007200610070006800690063002000500072006F00760069006400650072002000760031002E0030000000000020000000010000004C0300003082034830820230A0030201020209009BC2D79761F68C84300D06092A864886F70D01010B05003039310B30090603550406130241553113301106035504080C0A536F6D652D537461746531153013060355040A0C0C536F6D652D436F6D70616E79301E170D3230303932383036333030355A170D3330303932363036333030355A3039310B30090603550406130241553113301106035504080C0A536F6D652D537461746531153013060355040A0C0C536F6D652D436F6D70616E7930820122300D06092A864886F70D01010105000382010F003082010A0282010100A20B189EC9265492B7621FFE83B82E05923AB02D2DEE3E20C24BB7D8923FA45D5D62E0925DAF5EABBDD7C870E4D1229FF08A2D78D685E81450475802410F692FBBD1DFA12CE5E60EE26583458D949D7C0EDC212A1DCADB4426B6F6C2BE40B90B95BED978CC99FCBE9C00035C8FEE07200B20EA4B86FD3E9FFE42AAD926D2D381CC4C95AF963C3A19A7C90BC1C084F7434A83B0626E41A8E4EB3AC624E5DBB3D3214D535FC45294D746609F6E69B44DA48305DE63BA6FEF283E2778254E8579ABB0295629954E228B18AB5355FEF0F664D9DCD2C4A5047D4879BE8587687E37DE690C4E0D45927B2384E1BF09BE1F2744B50D54D5CD0B1223F5D31A446401D1A90203010001A3533051301D0603551D0E04160414396A962A0D9CA2D65CF53FD9D5915A728280AB80301F0603551D23041830168014396A962A0D9CA2D65CF53FD9D5915A728280AB80300F0603551D130101FF040530030101FF300D06092A864886F70D01010B0500038201010089391C5F3A6B3AA5CCD58C62CE4DC5E71A59F014066678C1ECB7959D4F5F5ACDF23E1EAD032ECC41C459B54A991C40E23F546C64C424BF954035D94C0F30EA7172E98E40F5D8A9B389A56360D837BDF5149754095403EE1AC7BE6415DEA18C10E98113868D6BD01C1FCA8A7704AAB167D9BA70D4FBCCC8E1836CC11AF03E8A62E13DB2EBF7038E469ED65D1D46B3074D92BB304F8FF41068DEC4BB499974635A8C524E4DA418B524529C641DBA82918A55FFBC82B8688B0838C3CEB24647B6142CDB17837E3978D7C551803638DE839DC9B2F9B368773E9148364ABEACF9ABB4A20A3D72122F22E3E17F0969B4C8C2CAF88C5B5D74EC82C19FA533D01ADD79A3 | |||
| (PID) Process: | (956) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\SystemCertificates\Root\Certificates\C7C20953EB5AC83C81CA388170EEC982E577F810 |
| Operation: | write | Name: | Blob |
Value: 5C0000000100000004000000000800000200000001000000CC0000001C0000006C00000001000000000000000000000000000000010000007B00410032003900380043003100300039002D0036004300440030002D0034004600410044002D0042003300370046002D004600430039003500360045003100340046004200440036007D00000000004D006900630072006F0073006F0066007400200045006E00680061006E006300650064002000430072007900700074006F0067007200610070006800690063002000500072006F00760069006400650072002000760031002E00300000000000140000000100000014000000396A962A0D9CA2D65CF53FD9D5915A728280AB80030000000100000014000000C7C20953EB5AC83C81CA388170EEC982E577F8100F00000001000000200000003940FA3A00F54D92B7F88E2D48C2772C8ABB2A13E49A0D26CD13424C4B5518321900000001000000100000000FED148DCA9288CFE9E8CFEDE332D41E040000000100000010000000F7998935234BC4DE2CB672C84BD5503420000000010000004C0300003082034830820230A0030201020209009BC2D79761F68C84300D06092A864886F70D01010B05003039310B30090603550406130241553113301106035504080C0A536F6D652D537461746531153013060355040A0C0C536F6D652D436F6D70616E79301E170D3230303932383036333030355A170D3330303932363036333030355A3039310B30090603550406130241553113301106035504080C0A536F6D652D537461746531153013060355040A0C0C536F6D652D436F6D70616E7930820122300D06092A864886F70D01010105000382010F003082010A0282010100A20B189EC9265492B7621FFE83B82E05923AB02D2DEE3E20C24BB7D8923FA45D5D62E0925DAF5EABBDD7C870E4D1229FF08A2D78D685E81450475802410F692FBBD1DFA12CE5E60EE26583458D949D7C0EDC212A1DCADB4426B6F6C2BE40B90B95BED978CC99FCBE9C00035C8FEE07200B20EA4B86FD3E9FFE42AAD926D2D381CC4C95AF963C3A19A7C90BC1C084F7434A83B0626E41A8E4EB3AC624E5DBB3D3214D535FC45294D746609F6E69B44DA48305DE63BA6FEF283E2778254E8579ABB0295629954E228B18AB5355FEF0F664D9DCD2C4A5047D4879BE8587687E37DE690C4E0D45927B2384E1BF09BE1F2744B50D54D5CD0B1223F5D31A446401D1A90203010001A3533051301D0603551D0E04160414396A962A0D9CA2D65CF53FD9D5915A728280AB80301F0603551D23041830168014396A962A0D9CA2D65CF53FD9D5915A728280AB80300F0603551D130101FF040530030101FF300D06092A864886F70D01010B0500038201010089391C5F3A6B3AA5CCD58C62CE4DC5E71A59F014066678C1ECB7959D4F5F5ACDF23E1EAD032ECC41C459B54A991C40E23F546C64C424BF954035D94C0F30EA7172E98E40F5D8A9B389A56360D837BDF5149754095403EE1AC7BE6415DEA18C10E98113868D6BD01C1FCA8A7704AAB167D9BA70D4FBCCC8E1836CC11AF03E8A62E13DB2EBF7038E469ED65D1D46B3074D92BB304F8FF41068DEC4BB499974635A8C524E4DA418B524529C641DBA82918A55FFBC82B8688B0838C3CEB24647B6142CDB17837E3978D7C551803638DE839DC9B2F9B368773E9148364ABEACF9ABB4A20A3D72122F22E3E17F0969B4C8C2CAF88C5B5D74EC82C19FA533D01ADD79A3 | |||
| (PID) Process: | (956) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\SystemCertificates\Root\Certificates |
| Operation: | delete value | Name: | 6F6F4432B6BC37F335C82D6B0C1219041C22C59A |
Value: | |||
| (PID) Process: | (956) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\SystemCertificates\Root\Certificates\6F6F4432B6BC37F335C82D6B0C1219041C22C59A |
| Operation: | write | Name: | Blob |
Value: 0400000001000000100000008DC78EF45964A5D510057390C267BE5714000000010000001400000098C394ABA698BBE7992045125078BCDDEE869E3A0200000001000000CC0000001C0000006C00000001000000000000000000000000000000010000007B00320030004300350036003300420037002D0036004100370031002D0034003700420037002D0039003800310038002D003400440046004600420033004500310035003900300033007D00000000004D006900630072006F0073006F0066007400200045006E00680061006E006300650064002000430072007900700074006F0067007200610070006800690063002000500072006F00760069006400650072002000760031002E003000000000000300000001000000140000006F6F4432B6BC37F335C82D6B0C1219041C22C59A0F000000010000002000000066484E8F1A538437B1826386C4540FC4E5EA6B1D4D3D1594D0E642B8C03C33C51900000001000000100000008608468C464062C8926AF2A5C2A2949F2000000001000000230300003082031F30820207A00302010202146D26DBDCE96462D8C6C71B8C3E77F5A5373667D7300D06092A864886F70D01010B0500301F310E300C06035504080C054561727468310D300B060355040A0C0446616B65301E170D3233303932373135353632395A170D3238303932353135353632395A301F310E300C06035504080C054561727468310D300B060355040A0C0446616B6530820122300D06092A864886F70D01010105000382010F003082010A0282010100C563F0F98A8B34BF506FE322F3C2F30ED9A7F46A7CE94EACC8538AEF3F13329B9CB2CEF305F20995CA6E7DC1A3A6DC9DDF9C9C28FBBD301FDD72D45C18B9798B320D1F2002B489C2DF483BD505D3208E3305570C67041AB8CA04912A2072E36E9F39A1BFD039460ABED597D4B3C8D8EF68B4338CFE4239EFE35AF82D4D20BDF89161F792470507D5E5625AFFBDD860E4D5203864D12E40E247EA36D09DB6D60E0F344119F232425268A5DA9AAAEDDD4C0DF09BFA0EE99A9A5E1F7460AC452BC6140AD9C2A0343FD501A238B216504D9C93455A92D7460B9970AE54F0C899E5155E94C2E03E0EA8DC9A3AD2DEC04B83D5FEE5DD1EA0D3D22D9A06824DB8BD954F0203010001A3533051301D0603551D0E0416041498C394ABA698BBE7992045125078BCDDEE869E3A301F0603551D2304183016801498C394ABA698BBE7992045125078BCDDEE869E3A300F0603551D130101FF040530030101FF300D06092A864886F70D01010B050003820101000DE7587203EC5FBAED29262654A01E38EE709A574680F848C80A26F58C72F231E6FC8A90C01DC342288F6E5B85D9B85A72074957786331E2F54FD13FAEA920514004D3F167025DE5FAFE250C7F604858586C228A4A5936E25C645E6048C2B361B6F4CD3D5048B5419D4134E76F99B115A74E4D9A7FB86F2B82EBF89F3678C8DF4F01070F88922AC28419AD31FCAEE5D19CBDF7797EE87E5E1E3B9F920B88E32CD3DBF8FFA1A5AA9AF07869951ADACA3FC83653F68B0FE6B49D0531C82B9FE03C90134F839B7EC8E536D91956C79CF9D7429D11F0AC1123E9C443D2215691084ECABC5093E3376F707E136BB21B37B5E16C84A01A619CB69B0A7DAEA8B704C2A6 | |||
| (PID) Process: | (956) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\SystemCertificates\Root\Certificates\6F6F4432B6BC37F335C82D6B0C1219041C22C59A |
| Operation: | write | Name: | Blob |
Value: 5C0000000100000004000000000800001900000001000000100000008608468C464062C8926AF2A5C2A2949F0F000000010000002000000066484E8F1A538437B1826386C4540FC4E5EA6B1D4D3D1594D0E642B8C03C33C50300000001000000140000006F6F4432B6BC37F335C82D6B0C1219041C22C59A0200000001000000CC0000001C0000006C00000001000000000000000000000000000000010000007B00320030004300350036003300420037002D0036004100370031002D0034003700420037002D0039003800310038002D003400440046004600420033004500310035003900300033007D00000000004D006900630072006F0073006F0066007400200045006E00680061006E006300650064002000430072007900700074006F0067007200610070006800690063002000500072006F00760069006400650072002000760031002E0030000000000014000000010000001400000098C394ABA698BBE7992045125078BCDDEE869E3A0400000001000000100000008DC78EF45964A5D510057390C267BE572000000001000000230300003082031F30820207A00302010202146D26DBDCE96462D8C6C71B8C3E77F5A5373667D7300D06092A864886F70D01010B0500301F310E300C06035504080C054561727468310D300B060355040A0C0446616B65301E170D3233303932373135353632395A170D3238303932353135353632395A301F310E300C06035504080C054561727468310D300B060355040A0C0446616B6530820122300D06092A864886F70D01010105000382010F003082010A0282010100C563F0F98A8B34BF506FE322F3C2F30ED9A7F46A7CE94EACC8538AEF3F13329B9CB2CEF305F20995CA6E7DC1A3A6DC9DDF9C9C28FBBD301FDD72D45C18B9798B320D1F2002B489C2DF483BD505D3208E3305570C67041AB8CA04912A2072E36E9F39A1BFD039460ABED597D4B3C8D8EF68B4338CFE4239EFE35AF82D4D20BDF89161F792470507D5E5625AFFBDD860E4D5203864D12E40E247EA36D09DB6D60E0F344119F232425268A5DA9AAAEDDD4C0DF09BFA0EE99A9A5E1F7460AC452BC6140AD9C2A0343FD501A238B216504D9C93455A92D7460B9970AE54F0C899E5155E94C2E03E0EA8DC9A3AD2DEC04B83D5FEE5DD1EA0D3D22D9A06824DB8BD954F0203010001A3533051301D0603551D0E0416041498C394ABA698BBE7992045125078BCDDEE869E3A301F0603551D2304183016801498C394ABA698BBE7992045125078BCDDEE869E3A300F0603551D130101FF040530030101FF300D06092A864886F70D01010B050003820101000DE7587203EC5FBAED29262654A01E38EE709A574680F848C80A26F58C72F231E6FC8A90C01DC342288F6E5B85D9B85A72074957786331E2F54FD13FAEA920514004D3F167025DE5FAFE250C7F604858586C228A4A5936E25C645E6048C2B361B6F4CD3D5048B5419D4134E76F99B115A74E4D9A7FB86F2B82EBF89F3678C8DF4F01070F88922AC28419AD31FCAEE5D19CBDF7797EE87E5E1E3B9F920B88E32CD3DBF8FFA1A5AA9AF07869951ADACA3FC83653F68B0FE6B49D0531C82B9FE03C90134F839B7EC8E536D91956C79CF9D7429D11F0AC1123E9C443D2215691084ECABC5093E3376F707E136BB21B37B5E16C84A01A619CB69B0A7DAEA8B704C2A6 | |||
| (PID) Process: | (956) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\SystemCertificates\Root\Certificates |
| Operation: | delete value | Name: | 1AD19E83B5CBE31C167AC2D1A3B39556D9D5BBA8 |
Value: | |||
| (PID) Process: | (956) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\SystemCertificates\Root\Certificates\1AD19E83B5CBE31C167AC2D1A3B39556D9D5BBA8 |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000326D6193BF898E3DD1206D92E82BCE941400000001000000140000005B58AACB6285C8DA5FEB67AE64F380D2FDF2D1F90200000001000000CC0000001C0000006C00000001000000000000000000000000000000010000007B00440042004600420045003500460030002D0039004100430034002D0034004400370037002D0039003700440036002D004400360030004300410038003200320037003200380032007D00000000004D006900630072006F0073006F0066007400200045006E00680061006E006300650064002000430072007900700074006F0067007200610070006800690063002000500072006F00760069006400650072002000760031002E003000000000000300000001000000140000001AD19E83B5CBE31C167AC2D1A3B39556D9D5BBA80F00000001000000200000001CF3A0AEC1F739093FE97B9E8B77DC9365C5CCD0F726D165CECE7D688D7F2575190000000100000010000000988DECE9A422B1408893FCFCEC642FBB20000000010000007D0300003082037930820261A003020102021433491C4ADC568732917D1A48B1C45C497C992143300D06092A864886F70D01010B0500304C310B30090603550406130255533113301106035504080C0A43616C69666F726E696131133011060355040A0C0A436F6D5369676E2043413113301106035504030C0A436F6D5369676E204341301E170D3230313132363130353730325A170D3330313132343130353730325A304C310B30090603550406130255533113301106035504080C0A43616C69666F726E696131133011060355040A0C0A436F6D5369676E2043413113301106035504030C0A436F6D5369676E20434130820122300D06092A864886F70D01010105000382010F003082010A02820101009DC29041363C826AB5C6B6A161B41D580E749DC723C472121930361D1BF033124CB57764262A4BB4A982BE8FDE0BA1EB248FFF4EA011DFB3ED2B6B0C26D5F2EDFDAA7527F639799C315F748703939979EF689778EF45AC368C45C7F8B5FB9C72577150D44C7F3C95BCAA44E19E448F6AAEB5804D9F3CAFEF397602287B5B9C0AEC689B06F882867053BC20ACEF17AA6E7FAF0B08383D7AF96AC90D491287E1E7ED014AC0C447AF13DBC84F81E4355500284859656299D219A3F02AAA00E533696A4699D99F74ABF690219167F37E9D44BEF3DD3BD8AE6552A648CF5838E4B40DF3E5C952B5AA06721BF1E4C03D22B886E20473EA04AE941AA78BFAC0A00AFF490203010001A3533051301D0603551D0E041604145B58AACB6285C8DA5FEB67AE64F380D2FDF2D1F9301F0603551D230418301680145B58AACB6285C8DA5FEB67AE64F380D2FDF2D1F9300F0603551D130101FF040530030101FF300D06092A864886F70D01010B05000382010100163A9B27CDC22544DB104B30D2E368911B87549B58DFAA5E06FC42000606D118E0B6EA1773E7D898FAC2B4AFD56495F47E3EF68548D4FF6A9E7FFFCBC5B30D6A395A4D987BD9DE44E1FB7C0075723E6893E8D5ADEE600FE1D0F6EF25B15F99E6569E72B2E556CF4ED5C007D77E1096C944AC7E9508F6EB9893FEB900DBBA119816E6F93C3472E1F1A528A53A5D12175539B841831B595DF465708F5D7299A98F98609D7A80ADA0182BE5248056A00236E6B479B6454F449600E805AC59F380A2D887A3F253EB2C21C0FC2D71ADAE2E769364D62FADD4892F77224AEFA755B98D8E9A25920DCD1C16C46E25472DE04FF4D9D87E05894492973854C6F2424B578D | |||
Executable files
0
Suspicious files
25
Text files
38
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 956 | javaw.exe | C:\Users\admin\AppData\Roaming\NCALayer\ncalayer-cache\bundle0\security\tmp\tmp9172165592101753915.tmp | — | |
MD5:— | SHA256:— | |||
| 956 | javaw.exe | C:\Users\admin\AppData\Roaming\NCALayer\ncalayer-cache\bundle0\security\tmp\tmp5940180607363694716.tmp | text | |
MD5:9D217F087D926C4DC428F2A34DB6E6EA | SHA256:AE2FAAA7246F4ECC914C38A6C7415DC65A67A5EADDA3208B25A07E985B34BC27 | |||
| 956 | javaw.exe | C:\Users\admin\AppData\Roaming\NCALayer\ncalayer-cache\bundle0\last.java.version | text | |
MD5:26141F1075928AF4ACDB1190F8B274F3 | SHA256:E0C18A6A8D48DA87994C100BBB324C758D413E95F0FA5135BD0738A692B4D56F | |||
| 956 | javaw.exe | C:\Users\admin\AppData\Roaming\NCALayer\ncalayer.log | text | |
MD5:B63298BF3DEF83832FD66AD31F12BC9A | SHA256:6DDF11CDBDA1D8EFB0F25118E66A15DCD5FA87A027D43F2DBF4D29D0D5F5FFD3 | |||
| 956 | javaw.exe | C:\Users\admin\AppData\Roaming\NCALayer\ncalayer.der | cat | |
MD5:DB12521E2B761BD0FB899F460A354275 | SHA256:1A4C990798305EB76A889478D264DF3F8A877ED5EA7BD895E7521B5514B3124C | |||
| 956 | javaw.exe | C:\Users\admin\AppData\Roaming\NCALayer\ncalayer-cache\bundle0\bundle.id | binary | |
MD5:C81E728D9D4C2F636F067F89CC14862C | SHA256:— | |||
| 956 | javaw.exe | C:\Users\admin\AppData\Roaming\NCALayer\ncalayer-cache\bundle1\bundle.info | text | |
MD5:B9A0A3CC44657F426E7EDFEE6D4789B8 | SHA256:4F90D6015421C05CBC4891BBC8FC2D02BE50F88275238CE6ED7F1E1B85953915 | |||
| 956 | javaw.exe | C:\Users\admin\AppData\Roaming\NCALayer\bundles\kalkancrypt-0.6.2.jar | compressed | |
MD5:56A9EBFB76C0C61F3DF4CDCC118E623F | SHA256:768D729CF807B9A9C1EAA2C59167D8377E776E4ADA531274101BE86E08964CDD | |||
| 956 | javaw.exe | C:\Users\admin\AppData\Roaming\NCALayer\bundles\kalkancrypt_xmldsig-osgi-0.3.1.jar | compressed | |
MD5:43C27F78F67E52B551EBB6E8CA8B4F7A | SHA256:E03AAB9A97FAE0A4A5D9693A82FA5CF54E6A5648CC9BD01385DE0E410E2E625E | |||
| 956 | javaw.exe | C:\Users\admin\AppData\Roaming\NCALayer\bundles\knca_provider_util-0.7.5.jar | compressed | |
MD5:EB57E99CC2C11C3F1A63736FDB117F5A | SHA256:1F632FC12B67D9B592CD018FD841FA601E34482531CB49B0F7218949483E56D7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
8
DNS requests
1
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
956 | javaw.exe | GET | 200 | 195.12.123.42:80 | http://crl.pki.gov.kz/updates/kncabundles/kalkancrypt-0.7.5.jar | unknown | compressed | 1.92 Mb | unknown |
956 | javaw.exe | GET | 200 | 195.12.123.42:80 | http://crl.pki.gov.kz/updates/kncabundles/kalkancrypt_xmldsig-osgi-0.4.jar | unknown | compressed | 762 Kb | unknown |
956 | javaw.exe | GET | 200 | 195.12.123.42:80 | http://crl.pki.gov.kz/updates/kncabundles/knca_provider_util-0.8.5.jar | unknown | compressed | 138 Kb | unknown |
956 | javaw.exe | GET | 200 | 195.12.123.42:80 | http://crl.pki.gov.kz/updates/kncabundles/knca_applet-0.4.6.jar | unknown | compressed | 513 Kb | unknown |
956 | javaw.exe | GET | 200 | 195.12.123.42:80 | http://crl.pki.gov.kz/updates/kncabundles/NCAWebSocket-0.3.8.jar | unknown | compressed | 102 Kb | unknown |
956 | javaw.exe | GET | 200 | 195.12.123.42:80 | http://crl.pki.gov.kz/updates/ncalayer.der | unknown | binary | 27.5 Kb | unknown |
1900 | javaw.exe | GET | 200 | 195.12.123.42:80 | http://crl.pki.gov.kz/updates/ncalayer.der | unknown | binary | 27.5 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
956 | javaw.exe | 195.12.123.42:443 | crl.pki.gov.kz | National Information Technologies Joint-Stock Company | KZ | unknown |
956 | javaw.exe | 195.12.123.42:80 | crl.pki.gov.kz | National Information Technologies Joint-Stock Company | KZ | unknown |
1900 | javaw.exe | 195.12.123.42:443 | crl.pki.gov.kz | National Information Technologies Joint-Stock Company | KZ | unknown |
1900 | javaw.exe | 195.12.123.42:80 | crl.pki.gov.kz | National Information Technologies Joint-Stock Company | KZ | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.pki.gov.kz |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
956 | javaw.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
956 | javaw.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
956 | javaw.exe | Misc activity | ET INFO JAVA - Java Archive Download By Vulnerable Client |