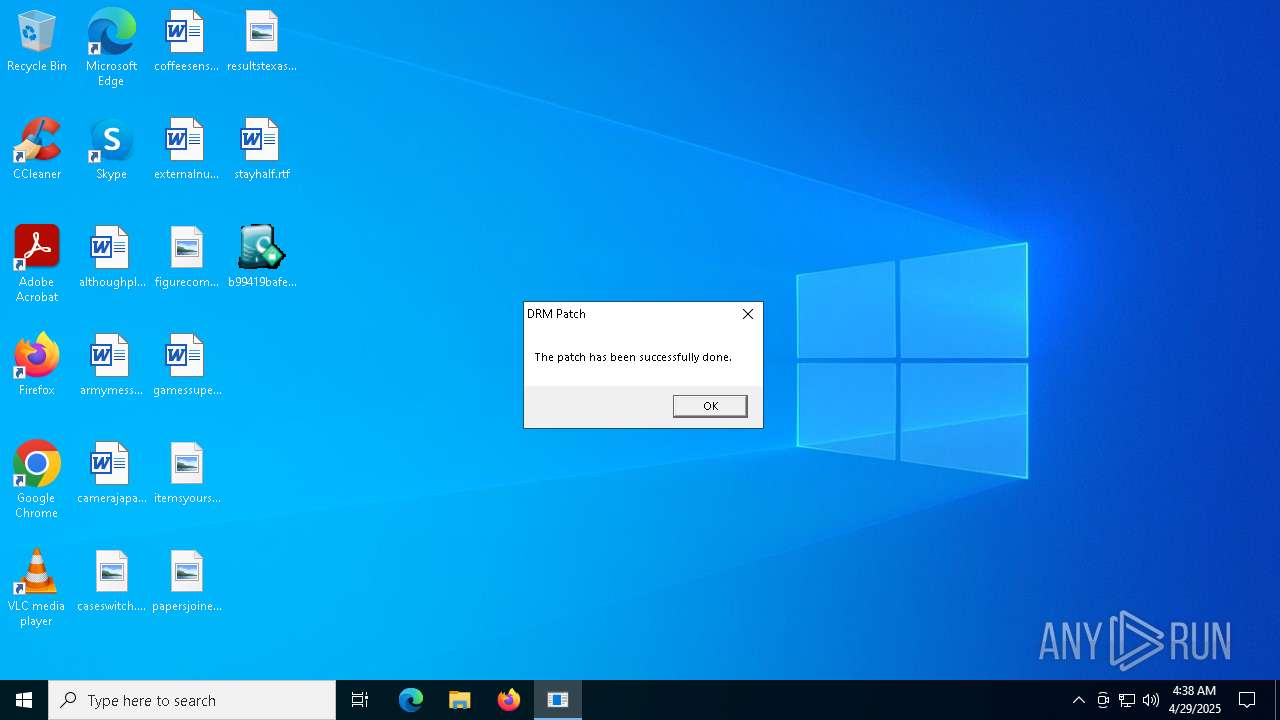
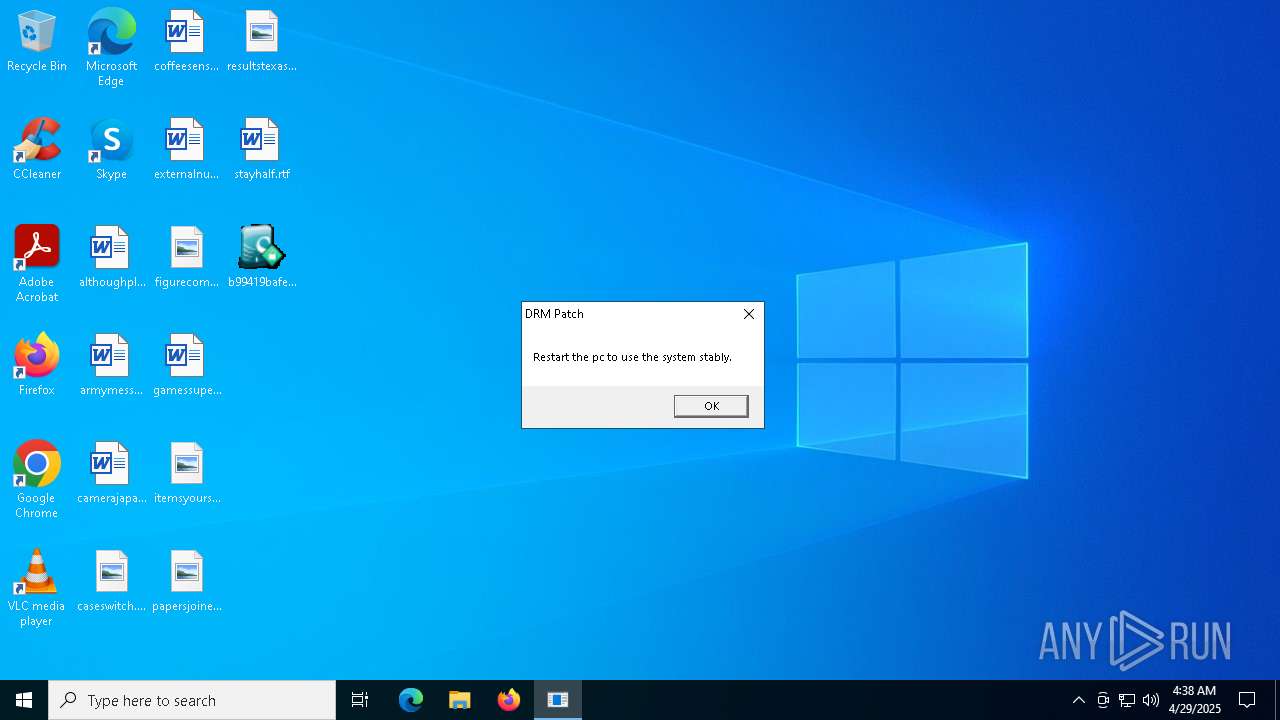
| File name: | b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240 |
| Full analysis: | https://app.any.run/tasks/6e78dde0-7524-45fe-bf96-38533fa4f327 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 04:37:57 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | A7BF51CB40E5266802E428DD21ED6243 |
| SHA1: | C1827F2CFE43086E74946175DE3E429EA2B681BA |
| SHA256: | B99419BAFE3732427A4B5F5361B979C94AFB64DEE5AF194FCED6A07A9494B240 |
| SSDEEP: | 12288:j5akOlm2472AJMu0O2fBYlIliZC4tGtsGzw:j5Fn2472AJMuQICPw |
MALICIOUS
NESHTA mutex has been found
- b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe (PID: 7768)
- FileCoAuth.exe (PID: 8164)
Executing a file with an untrusted certificate
- FileCoAuth.exe (PID: 7232)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe (PID: 7768)
Reads security settings of Internet Explorer
- FileCoAuth.exe (PID: 8164)
- b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe (PID: 7768)
Process drops legitimate windows executable
- FileCoAuth.exe (PID: 8164)
Mutex name with non-standard characters
- FileCoAuth.exe (PID: 8164)
- b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe (PID: 7768)
Starts a Microsoft application from unusual location
- FileCoAuth.exe (PID: 7232)
Executable content was dropped or overwritten
- FileCoAuth.exe (PID: 8164)
- b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe (PID: 7928)
- b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe (PID: 7768)
INFO
Reads the computer name
- b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe (PID: 7768)
- FileCoAuth.exe (PID: 7232)
Checks supported languages
- b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe (PID: 7768)
- FileCoAuth.exe (PID: 7232)
Create files in a temporary directory
- b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe (PID: 7768)
- FileCoAuth.exe (PID: 7232)
Process checks computer location settings
- FileCoAuth.exe (PID: 8164)
- b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe (PID: 7768)
The sample compiled with english language support
- FileCoAuth.exe (PID: 8164)
Reads the machine GUID from the registry
- FileCoAuth.exe (PID: 7232)
Creates files or folders in the user directory
- FileCoAuth.exe (PID: 7232)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (60.4) |
|---|---|---|
| .scr | | | Windows screen saver (18.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.2) |
| .exe | | | Win32 Executable (generic) (6.3) |
| .exe | | | Generic Win/DOS Executable (2.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:09:25 20:33:06+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 29696 |
| InitializedDataSize: | 10752 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x80e4 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
127
Monitored processes
6
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7188 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7232 | "C:\Users\admin\AppData\Local\Temp\3582-490\FileCoAuth.exe" -Embedding | C:\Users\admin\AppData\Local\Temp\3582-490\FileCoAuth.exe | — | FileCoAuth.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneDriveFile Co-Authoring Executable Exit code: 0 Version: 19.043.0304.0013 Modules
| |||||||||||||||
| 7768 | "C:\Users\admin\Desktop\b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe" | C:\Users\admin\Desktop\b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 7928 | "C:\Users\admin\AppData\Local\Temp\3582-490\b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe" | C:\Users\admin\AppData\Local\Temp\3582-490\b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe | b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe | ||||||||||||
User: admin Company: SoftCamp Co., Ltd. Integrity Level: HIGH Description: Packer Exit code: 0 Version: 3, 5, 2, 1 | |||||||||||||||
| 7984 | "C:\Users\admin\AppData\Local\Temp\SCPacker0097812\SCSET.EXE" | C:\Users\admin\AppData\Local\Temp\SCPacker0097812\scset.exe | — | b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe | |||||||||||
User: admin Company: corama Integrity Level: HIGH Description: DSSDSCpy Exit code: 0 Version: 1, 0, 0, 1(09032600a) | |||||||||||||||
| 8164 | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe -Embedding | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
3 979
Read events
3 979
Write events
0
Delete events
0
Modification events
Executable files
10
Suspicious files
3
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7928 | b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe | C:\Users\admin\AppData\Local\Temp\SCPacker0097812\scset.exe | executable | |
MD5:8903D5770BA8C628F58691BD7B1F3927 | SHA256:288170702E26A4D7A2821F5A50CEA1AF3E43F672E4A90806D8DCF72B61067DDA | |||
| 7928 | b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe | C:\Users\admin\AppData\Local\Temp\SCPacker0097812\DSCOOZC.dll | text | |
MD5:90262CA2939C4CD284974428CE3DF07D | SHA256:39055A0E75C1025E3200B4717685470DF4F82D5E2930FCA105BE6566FFA8E7B9 | |||
| 7928 | b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe | C:\Users\admin\AppData\Local\Temp\SCPacker0097812\DSSDSCpy.ini | binary | |
MD5:1A95818F13215E4081795DBAE16BA5CA | SHA256:91105A4E0C273EAE56ABC3DD3415F82C3E0311906FFA53A8C8B7F7D3B73D33E7 | |||
| 7768 | b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileSyncConfig.exe | executable | |
MD5:8D084F7FA09DA02176BDCB5E1DBC001B | SHA256:409FBED24FA646AD06909C7612031F0DA8CACF8E00515B14362BFE60DE7C7C60 | |||
| 7768 | b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe | C:\Users\admin\AppData\Local\Temp\3582-490\b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe | executable | |
MD5:720EFC90B2E7E97D25B839596286A6D4 | SHA256:BE8B620BCDCA27E61F944D57788875A42651D0F00654E46528552D113C64D42A | |||
| 7768 | b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe | C:\ProgramData\Adobe\ARM\S\388\AdobeARMHelper.exe | executable | |
MD5:8A353FC28F024290F7A0E09B933FB332 | SHA256:CB8F08B2755CC52440B77C8DD609CC48A6DE3D926329A5870E4B7EAED5DCA157 | |||
| 7768 | b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\OneDriveUpdaterService.exe | executable | |
MD5:5E02ECA629D0D5EDCE49E7111D5CE6AB | SHA256:7F8A5490252913803B9FEAE7C15186A0CC137A7C39E8FE9262C167DDFFA24045 | |||
| 7768 | b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe | executable | |
MD5:29E7A8ADC957C3C5931CCAA9EAC9FFC9 | SHA256:345C7429461BE80D69F016B06AF384545EBCF55190FBEEAFC83445A3D466FB2F | |||
| 7984 | scset.exe | C:\Users\admin\AppData\Local\Temp\~TPC8D0.tmp | text | |
MD5:90262CA2939C4CD284974428CE3DF07D | SHA256:39055A0E75C1025E3200B4717685470DF4F82D5E2930FCA105BE6566FFA8E7B9 | |||
| 7768 | b99419bafe3732427a4b5f5361b979c94afb64dee5af194fced6a07a9494b240.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileSyncHelper.exe | executable | |
MD5:D9EB1951E8516F1FA5316FA948292981 | SHA256:837B3F72749B61D947387EF695564FE855EB7174A311843A50AEA67FAA219944 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
41
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4880 | SIHClient.exe | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 4.175.87.197:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
4880 | SIHClient.exe | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4880 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
4880 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
4880 | SIHClient.exe | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
4880 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 4.175.87.197:443 | https://slscr.update.microsoft.com/sls/ping | unknown | — | — | unknown |
4880 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 40.69.42.241:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4880 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4880 | SIHClient.exe | 2.16.164.72:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4880 | SIHClient.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4880 | SIHClient.exe | 40.69.42.241:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7432 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |