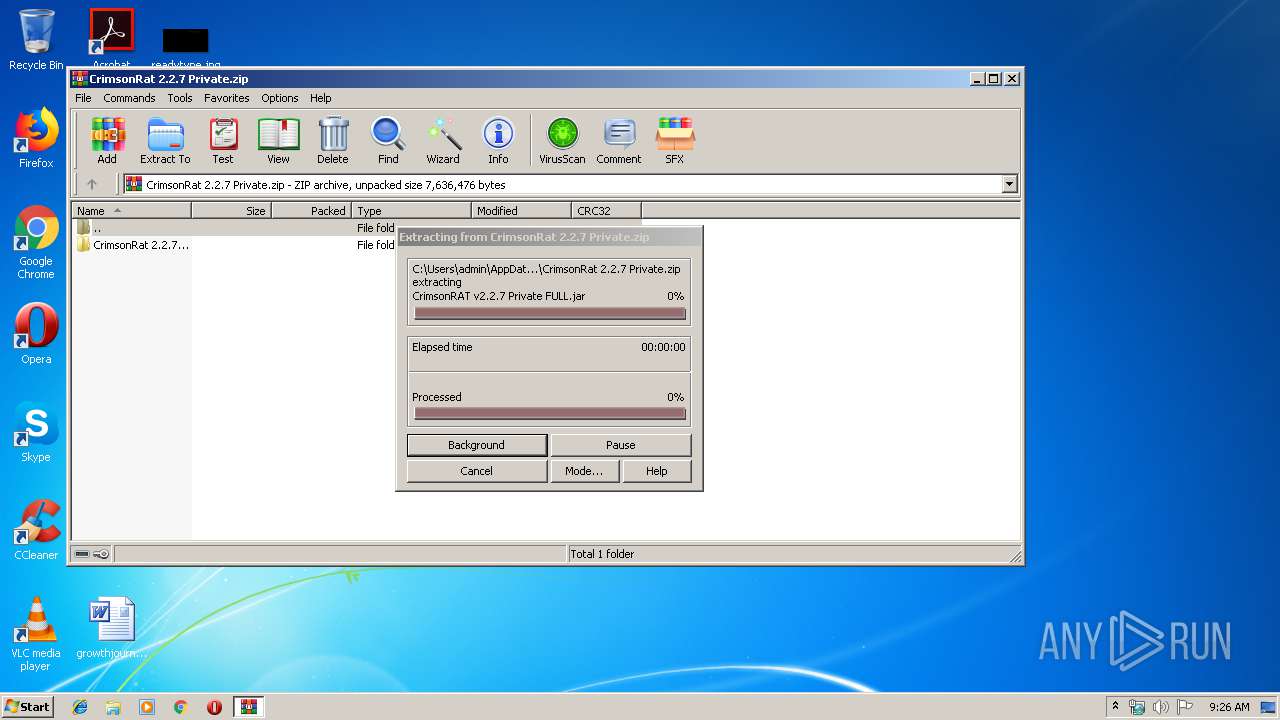
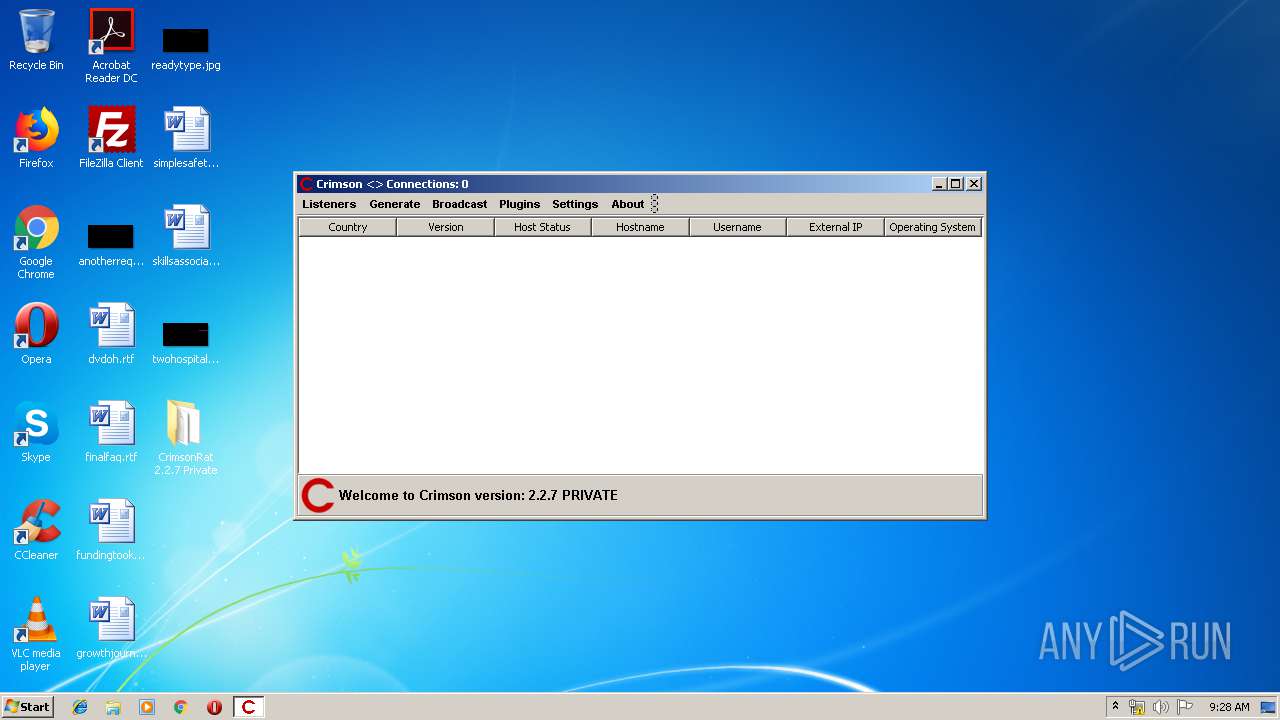
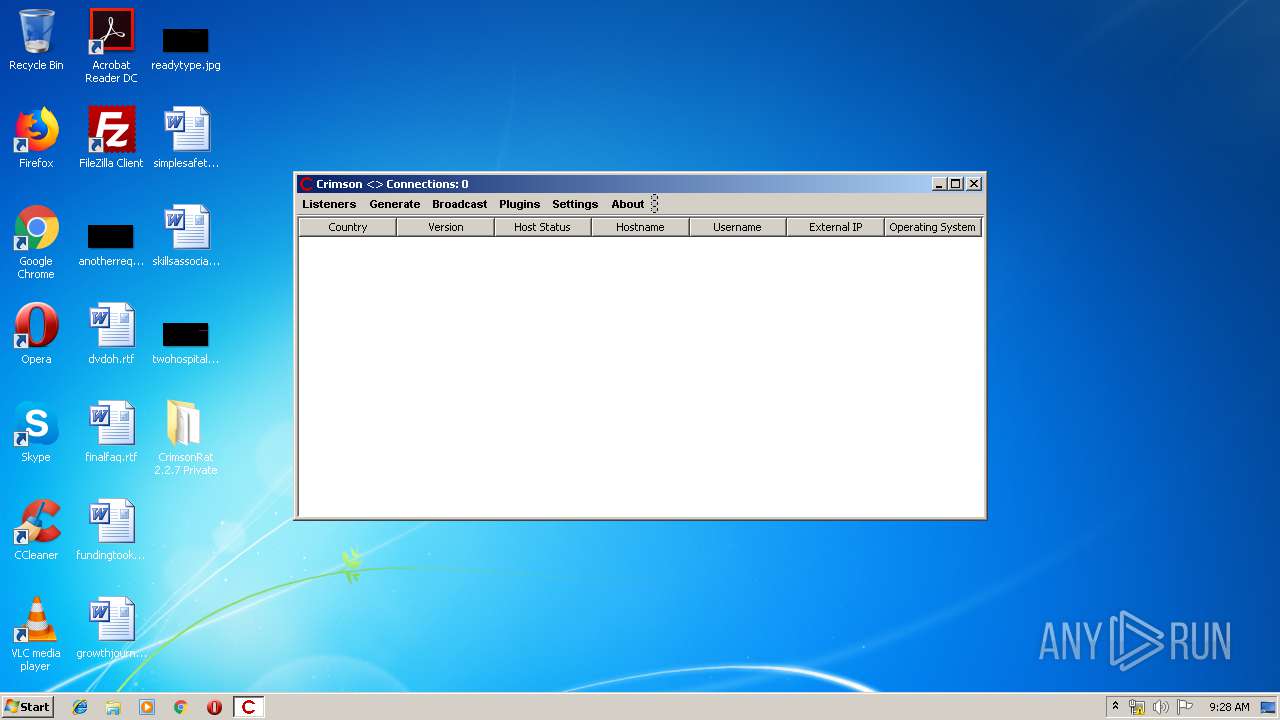
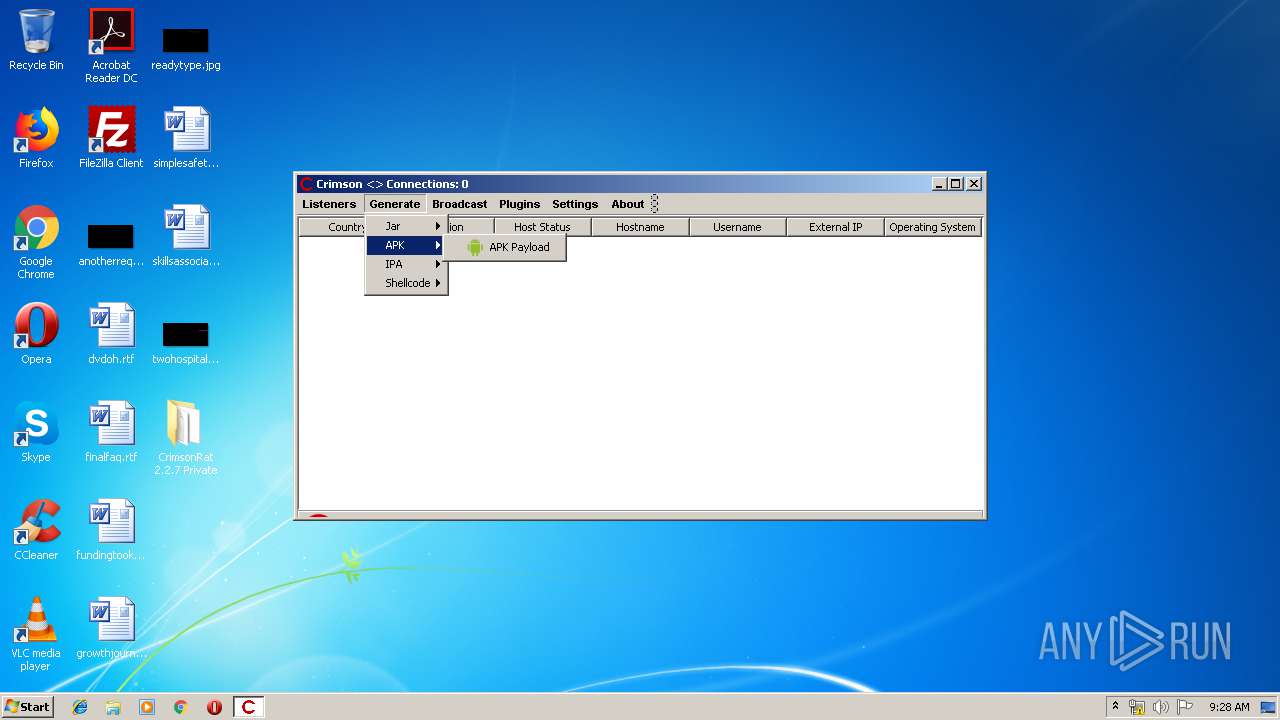
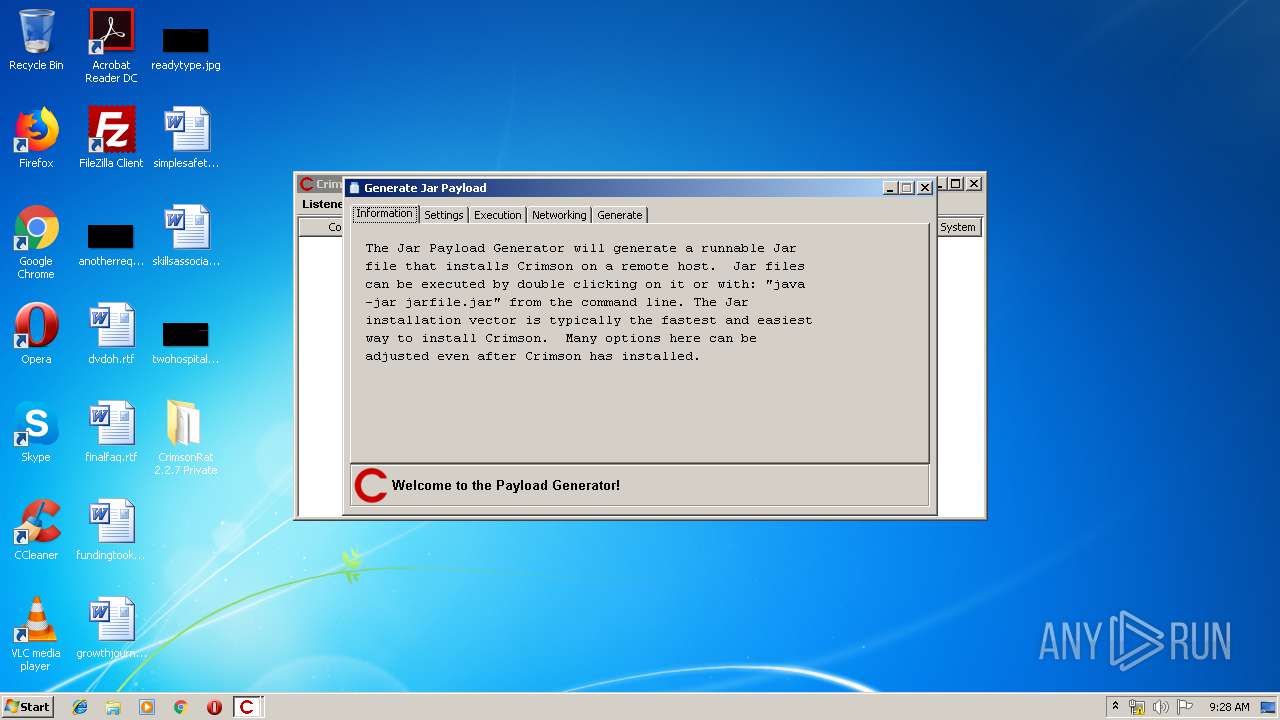
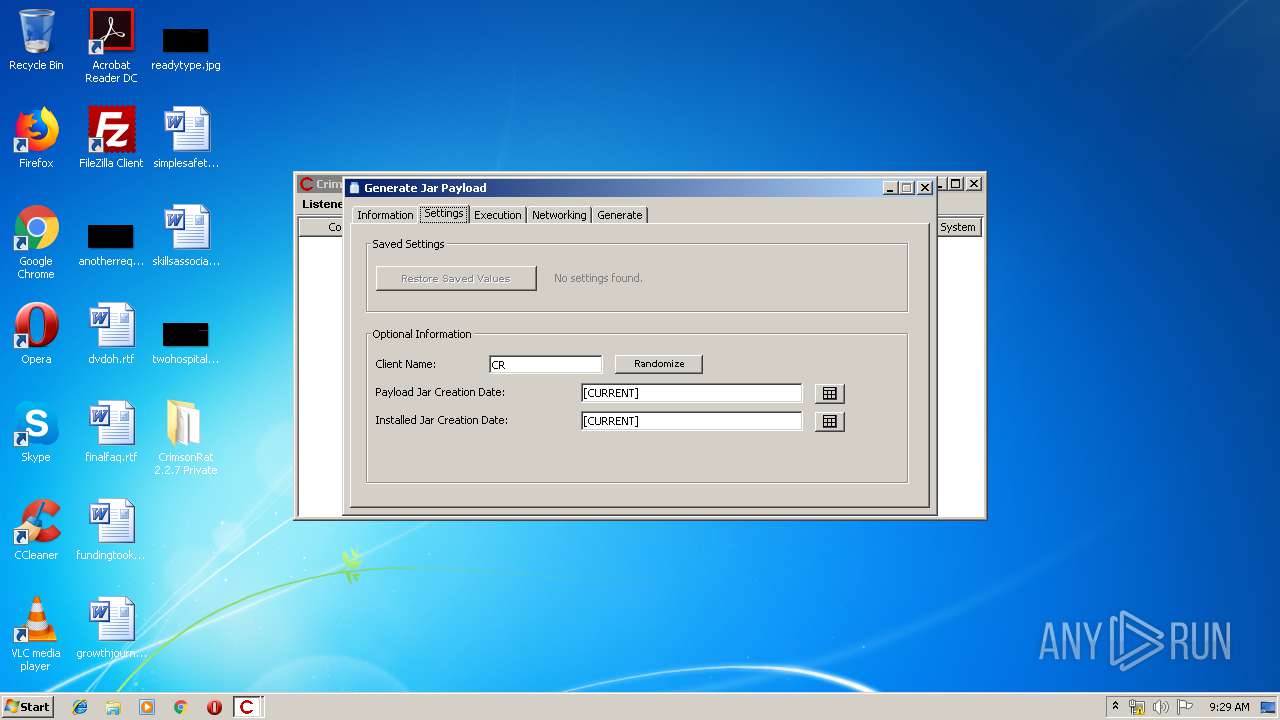
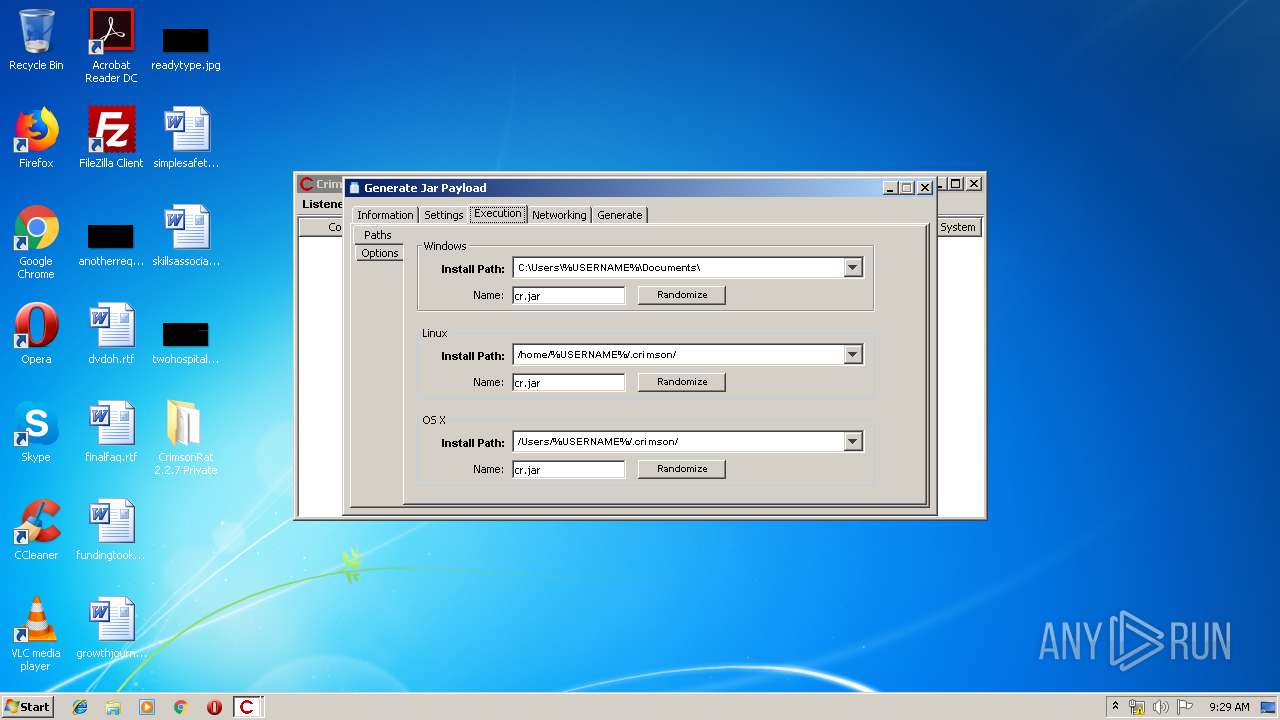
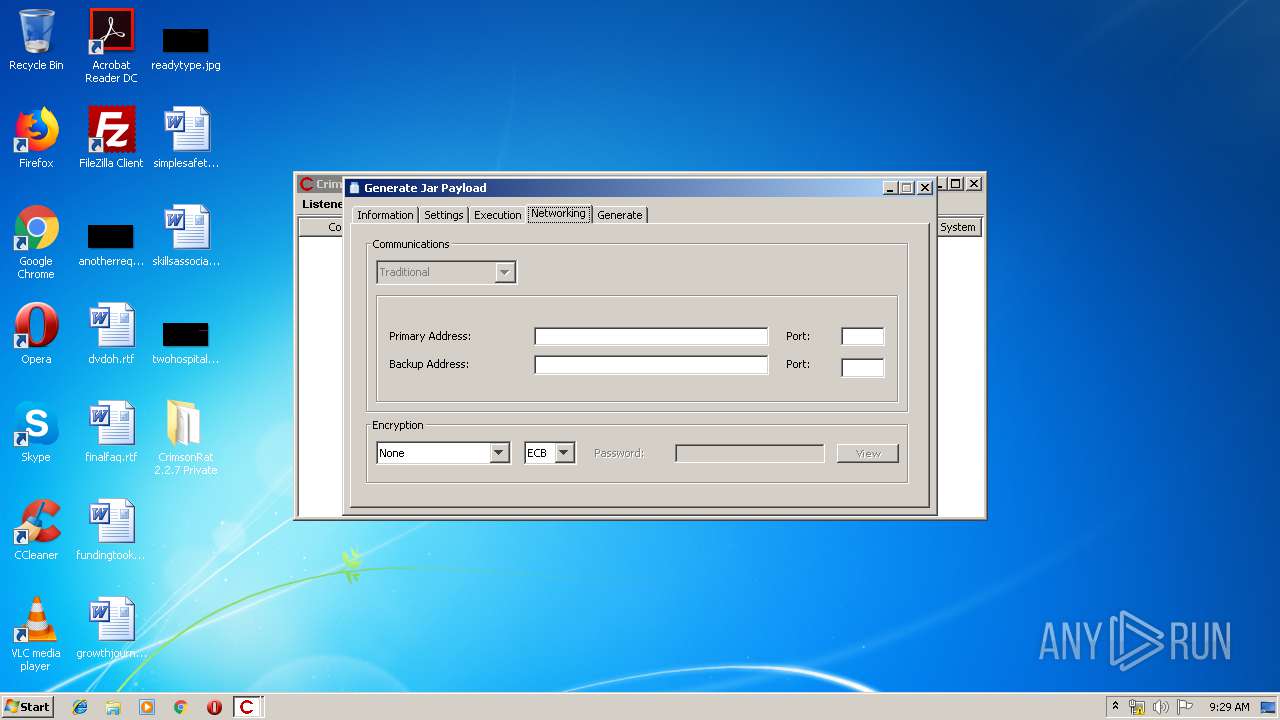
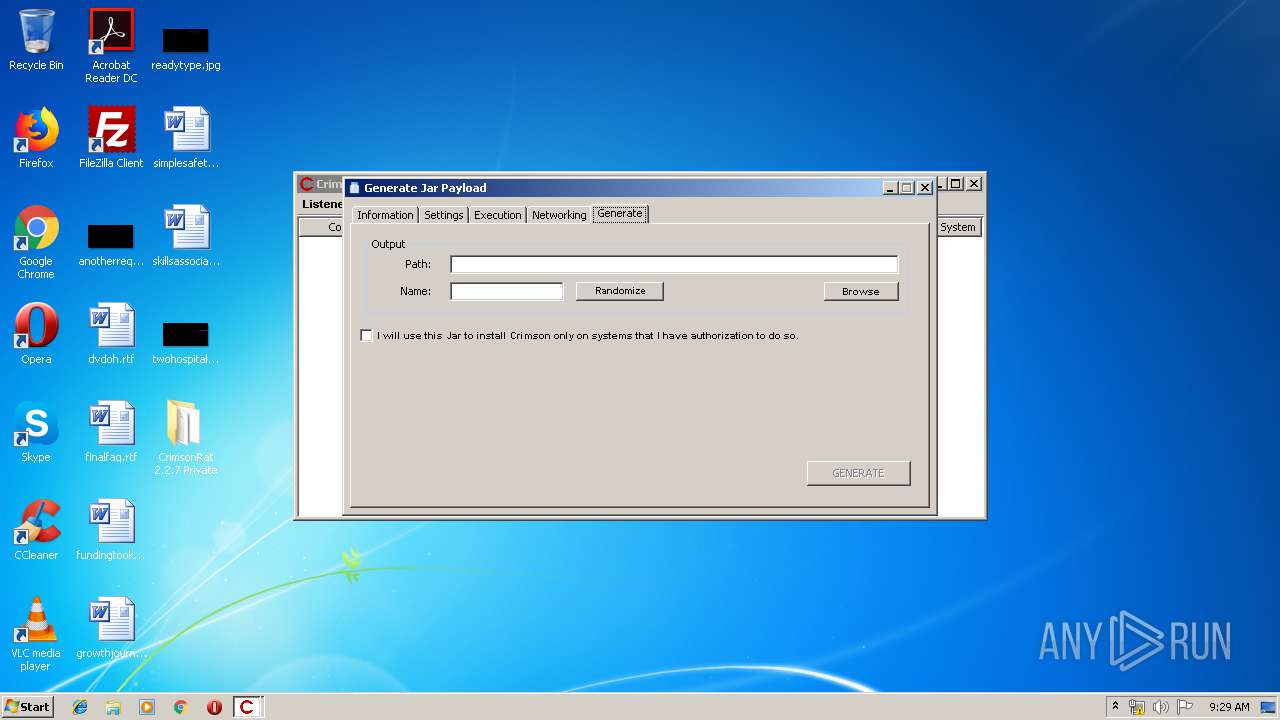
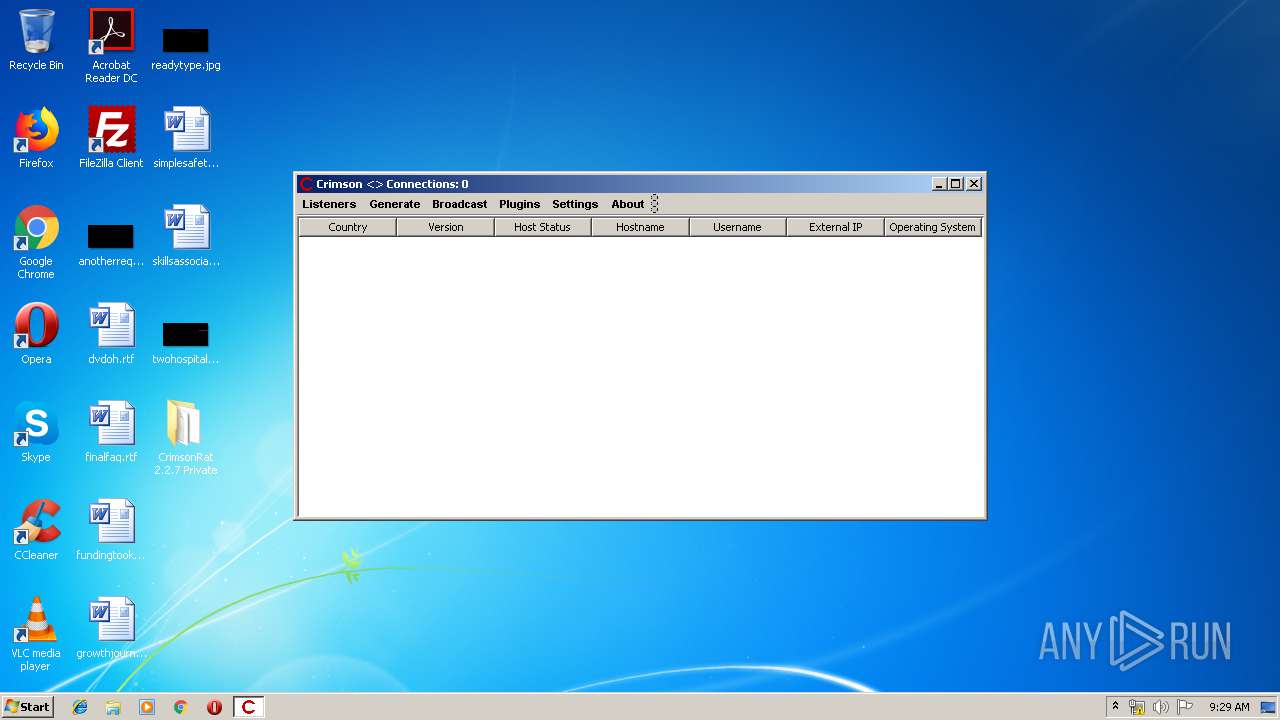
| File name: | CrimsonRat 2.2.7 Private.zip |
| Full analysis: | https://app.any.run/tasks/e019a90f-1b20-4767-aa0d-1a118c83f698 |
| Verdict: | Malicious activity |
| Analysis date: | November 16, 2019, 09:25:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | B2326F902283F2639F324A5403E6FBEA |
| SHA1: | 28E3ACC154082EBD07F8A3C572C354D6A493BD7A |
| SHA256: | B99040C2008B78775C46DA7FEAE12D83E6D324FEFB4F6D437BD61DD48D08BFD7 |
| SSDEEP: | 98304:lbhEHzKJ9cXIjaKsctNBTYNIS5/goNIHPN7:/ETKJ9cXIjswfEb9IHN |
MALICIOUS
Actions looks like stealing of personal data
- javaw.exe (PID: 1788)
Changes the autorun value in the registry
- reg.exe (PID: 2964)
SUSPICIOUS
Uses ATTRIB.EXE to modify file attributes
- javaw.exe (PID: 1788)
- javaw.exe (PID: 2620)
Creates files in the user directory
- javaw.exe (PID: 1788)
- javaw.exe (PID: 2620)
Application launched itself
- javaw.exe (PID: 1788)
- javaw.exe (PID: 2620)
Executes JAVA applets
- javaw.exe (PID: 1788)
- javaw.exe (PID: 2620)
Checks for external IP
- javaw.exe (PID: 1788)
Uses REG.EXE to modify Windows registry
- javaw.exe (PID: 2620)
Writes to a desktop.ini file (may be used to cloak folders)
- javaw.exe (PID: 2620)
INFO
Manual execution by user
- javaw.exe (PID: 1788)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .kmz | | | Google Earth saved working session (60) |
|---|---|---|
| .zip | | | ZIP compressed archive (40) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0808 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:11:16 17:25:09 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 2 |
| ZipUncompressedSize: | - |
| ZipFileName: | CrimsonRat 2.2.7 Private/ |
Total processes
52
Monitored processes
8
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1412 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\AppData\Roaming\mgYMAZRR9oAQWE\9zlMmaTQcHQQQWE.txt" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | — | javaw.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
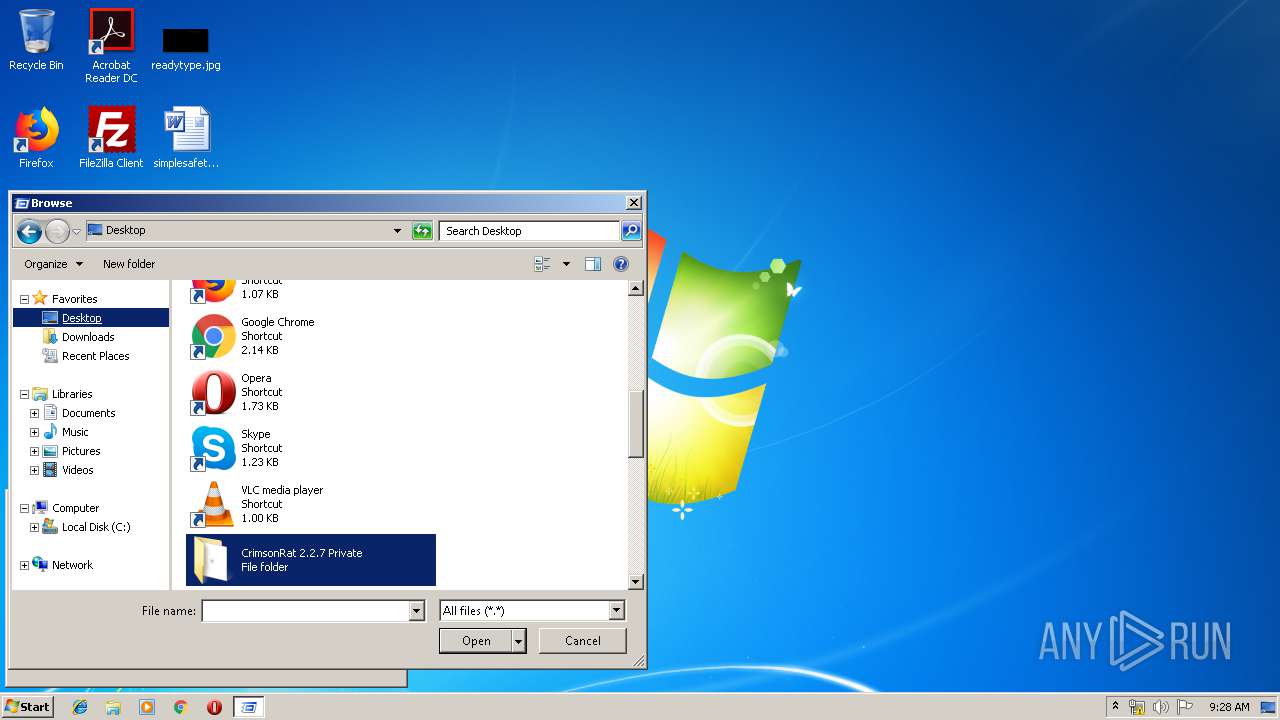
| 1788 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\Desktop\CrimsonRat 2.2.7 Private\CrimsonRAT v2.2.7 Private FULL.jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2004 | attrib +h .Ssettings.properties | C:\Windows\system32\attrib.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2304 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\CrimsonRat 2.2.7 Private.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2620 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\AppData\Local\Temp\Windows7552542972655710588.png" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | — | javaw.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2708 | attrib +s +h +r "C:\Users\admin\AppData\Roaming\mgYMAZRR9oAQWE\*.*" | C:\Windows\system32\attrib.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2964 | reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v bFnTnqeht7QWEQW /t REG_SZ /d "\"C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe\" -jar \"C:\Users\admin\AppData\Roaming\mgYMAZRR9oAQWE\9zlMmaTQcHQQQWE.txt\"" /f | C:\Windows\system32\reg.exe | javaw.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3892 | attrib +s +h +r "C:\Users\admin\AppData\Roaming\mgYMAZRR9oAQWE" | C:\Windows\system32\attrib.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
901
Read events
876
Write events
25
Delete events
0
Modification events
| (PID) Process: | (2304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2304) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\CrimsonRat 2.2.7 Private.zip | |||
| (PID) Process: | (2304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (2304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
9
Suspicious files
0
Text files
12
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
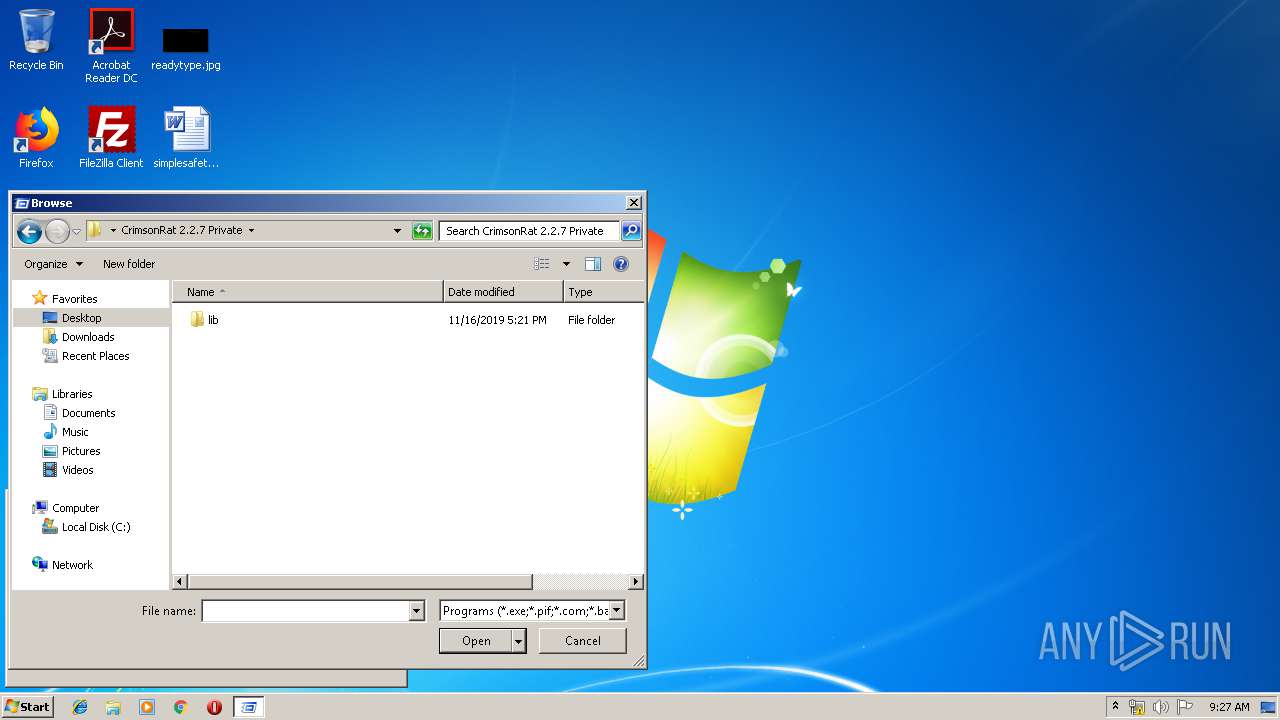
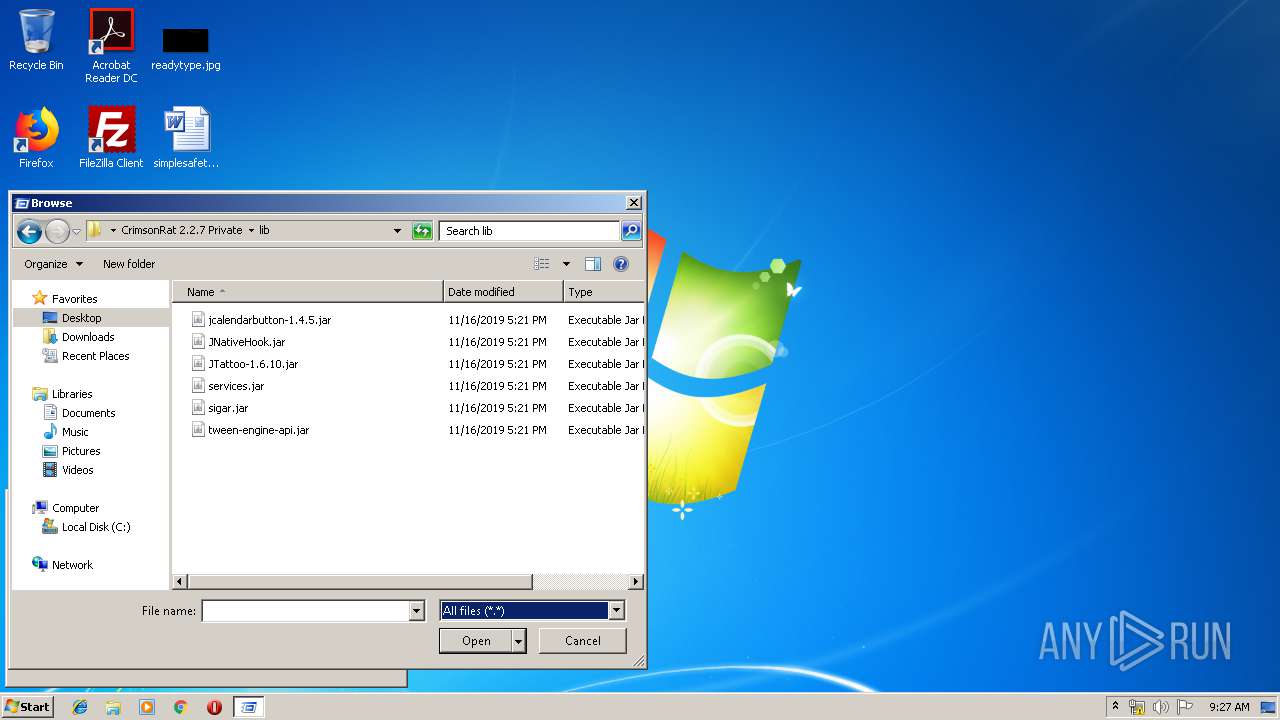
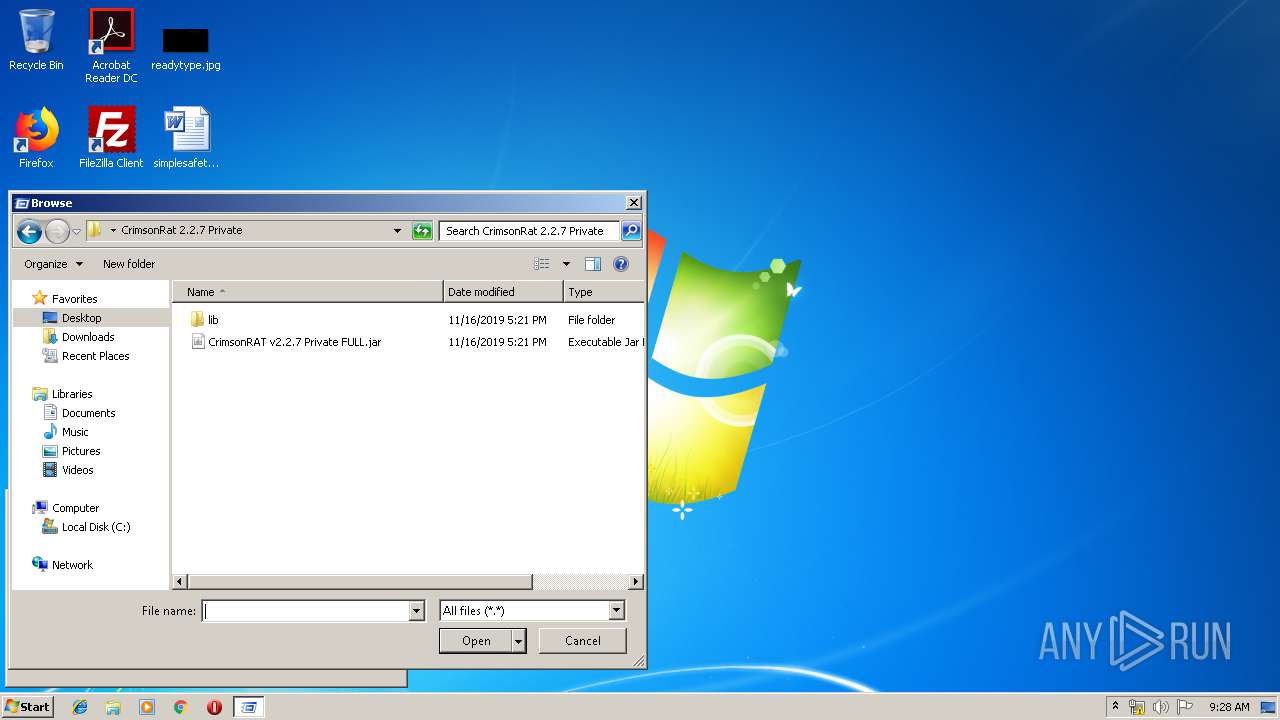
| 2304 | WinRAR.exe | C:\Users\admin\Desktop\CrimsonRat 2.2.7 Private\lib\services.jar | java | |
MD5:— | SHA256:— | |||
| 2304 | WinRAR.exe | C:\Users\admin\Desktop\CrimsonRat 2.2.7 Private\lib\tween-engine-api.jar | java | |
MD5:— | SHA256:— | |||
| 2304 | WinRAR.exe | C:\Users\admin\Desktop\CrimsonRat 2.2.7 Private\lib\JNativeHook.jar | java | |
MD5:— | SHA256:— | |||
| 2304 | WinRAR.exe | C:\Users\admin\Desktop\CrimsonRat 2.2.7 Private\CrimsonRAT v2.2.7 Private FULL.jar | java | |
MD5:— | SHA256:— | |||
| 2304 | WinRAR.exe | C:\Users\admin\Desktop\CrimsonRat 2.2.7 Private\lib\JTattoo-1.6.10.jar | java | |
MD5:— | SHA256:— | |||
| 2304 | WinRAR.exe | C:\Users\admin\Desktop\CrimsonRat 2.2.7 Private\lib\jcalendarbutton-1.4.5.jar | java | |
MD5:5FCCDEED0F4F76022F320592A378C561 | SHA256:0CE6019B261C00E7D4B383AA257BADA229AEEB80CF62E5B1DEDFE5EAEDBAF4BB | |||
| 1412 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 2304 | WinRAR.exe | C:\Users\admin\Desktop\CrimsonRat 2.2.7 Private\lib\sigar.jar | java | |
MD5:85D4A580BCD31802064024D33F668E9A | SHA256:DE8725B3BE2C25D44BA41A9450CD03842FAC9466D92DC582CB37691EEEA1F8DB | |||
| 1412 | javaw.exe | C:\Users\admin\2YmY99xxmY.tmp | text | |
MD5:— | SHA256:— | |||
| 2620 | javaw.exe | C:\Users\admin\2YmY99xxmY.tmp | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
3
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1788 | javaw.exe | GET | 301 | 104.26.15.73:80 | http://freegeoip.net/xml/Unknown | US | — | — | malicious |
1788 | javaw.exe | GET | 403 | 104.26.15.73:80 | http://freegeoip.net/shutdown | US | text | 1.51 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1788 | javaw.exe | 104.26.15.73:80 | freegeoip.net | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
checkip.amazonaws.csom |
| unknown |
freegeoip.net |
| malicious |
crimsonrat.org |
| unknown |
Threats
3 ETPRO signatures available at the full report