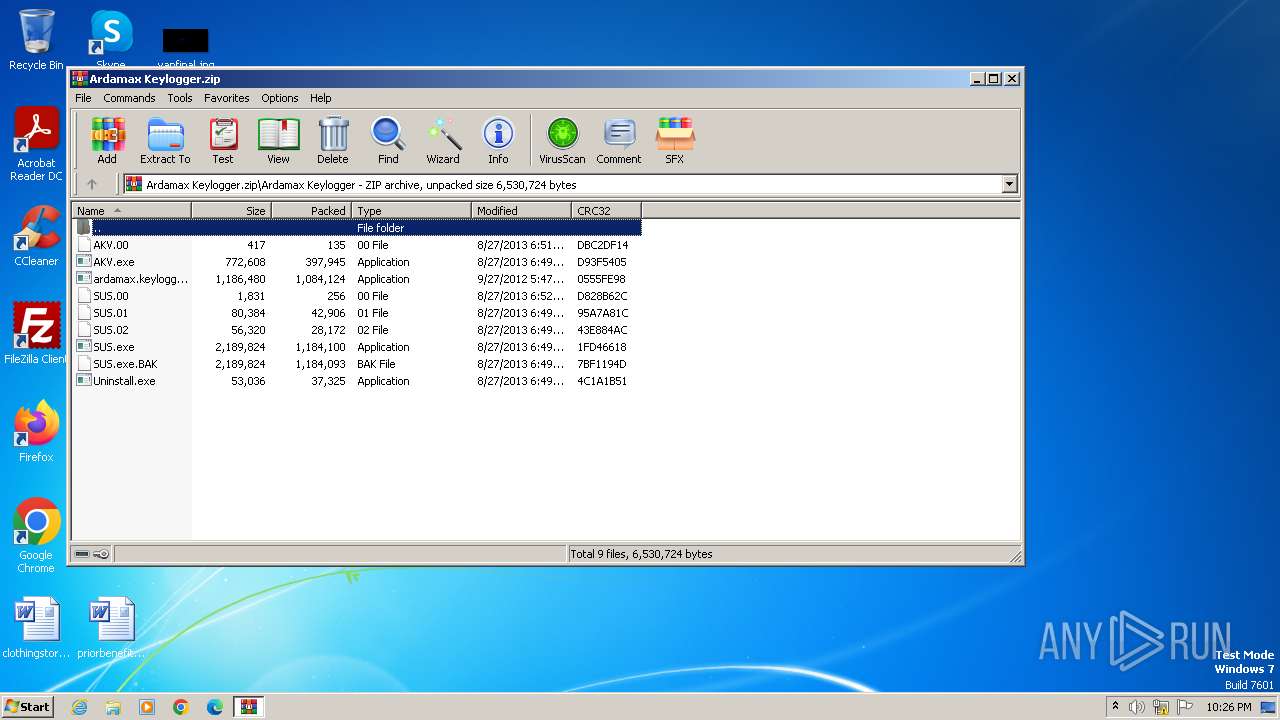
| File name: | Ardamax Keylogger.zip |
| Full analysis: | https://app.any.run/tasks/e6e64f44-9d8d-4f5f-b2bd-cb6d12ac109a |
| Verdict: | Malicious activity |
| Analysis date: | November 17, 2023, 22:26:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 68FA47E0E4DB8E51E4B8830C73D56749 |
| SHA1: | 791CDC9747AD93B6B6CE01F4A3441DD9A27CC2F9 |
| SHA256: | B9875815B28AAB3FE4D583DF7F604C9099822B46C593C2592BC30B8774E7EA18 |
| SSDEEP: | 98304:YaQ91ypZRm2Aoe5VlzwrjdYSHSf9RF1M0VmjqnXJd6B2rdSLm2DVQ6OljSJTo0+S:E+GJFbbeR |
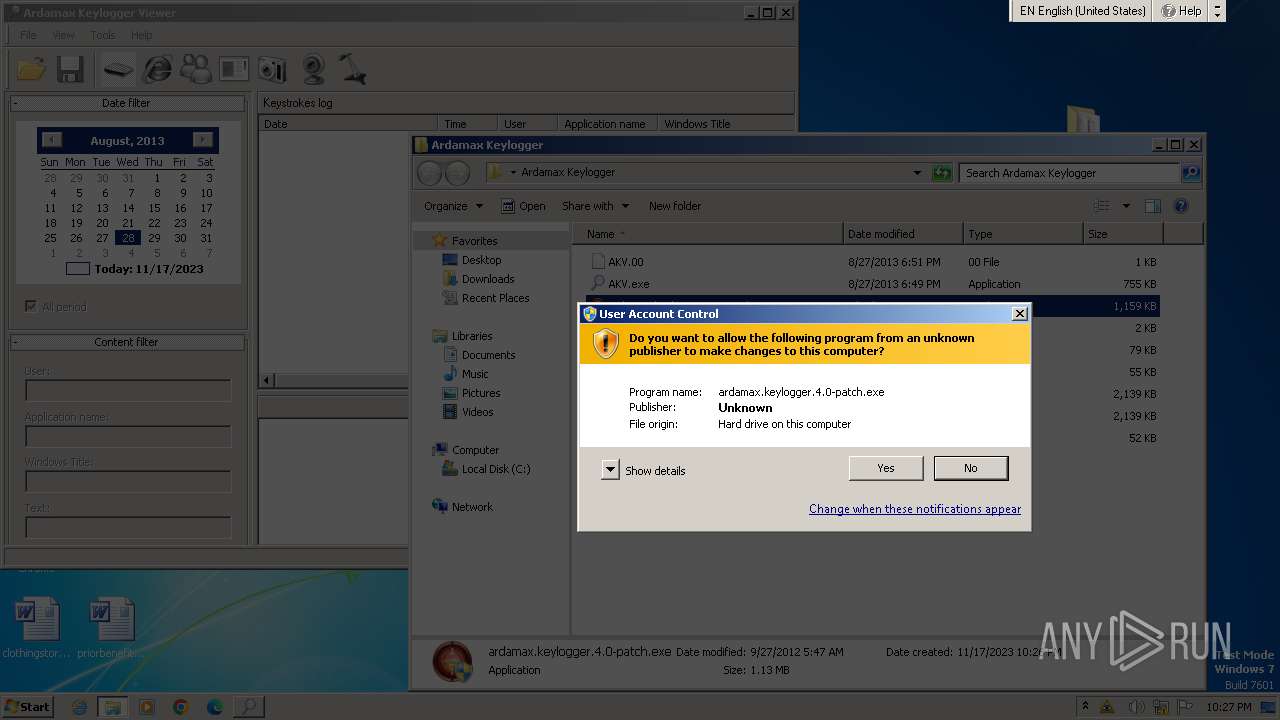
MALICIOUS
Drops the executable file immediately after the start
- ardamax.keylogger.4.0-patch.exe (PID: 3696)
SUSPICIOUS
No suspicious indicators.INFO
Checks supported languages
- SUS.exe (PID: 3876)
- AKV.exe (PID: 3912)
- ardamax.keylogger.4.0-patch.exe (PID: 3696)
Create files in a temporary directory
- ardamax.keylogger.4.0-patch.exe (PID: 3696)
- AKV.exe (PID: 3912)
Creates files or folders in the user directory
- SUS.exe (PID: 3876)
Manual execution by a user
- ardamax.keylogger.4.0-patch.exe (PID: 3696)
- WinRAR.exe (PID: 2424)
- SUS.exe (PID: 3876)
- AKV.exe (PID: 3912)
- ardamax.keylogger.4.0-patch.exe (PID: 3900)
Reads the computer name
- SUS.exe (PID: 3876)
Creates files in the program directory
- SUS.exe (PID: 3876)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2424)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2013:08:27 18:51:02 |
| ZipCRC: | 0xdbc2df14 |
| ZipCompressedSize: | 135 |
| ZipUncompressedSize: | 417 |
| ZipFileName: | Ardamax Keylogger/AKV.00 |
Total processes
48
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2424 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Ardamax Keylogger.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3448 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL "C:\Users\admin\Desktop\Ardamax Keylogger.zip.xpi" | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3696 | "C:\Users\admin\Desktop\Ardamax Keylogger\ardamax.keylogger.4.0-patch.exe" | C:\Users\admin\Desktop\Ardamax Keylogger\ardamax.keylogger.4.0-patch.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3876 | "C:\Users\admin\Desktop\Ardamax Keylogger\SUS.exe" | C:\Users\admin\Desktop\Ardamax Keylogger\SUS.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3900 | "C:\Users\admin\Desktop\Ardamax Keylogger\ardamax.keylogger.4.0-patch.exe" | C:\Users\admin\Desktop\Ardamax Keylogger\ardamax.keylogger.4.0-patch.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3912 | "C:\Users\admin\Desktop\Ardamax Keylogger\AKV.exe" | C:\Users\admin\Desktop\Ardamax Keylogger\AKV.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
Total events
1 126
Read events
1 107
Write events
19
Delete events
0
Modification events
| (PID) Process: | (2424) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
9
Suspicious files
5
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2424.48404\Ardamax Keylogger\SUS.00 | binary | |
MD5:0A84ACA4D67E14C3074F325E9BF373B2 | SHA256:588511AC2D28F82F103ABCADA72EED30DDE88300ABF2B1F4DDD1461A87990A9D | |||
| 2424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2424.48404\Ardamax Keylogger\AKV.exe | executable | |
MD5:BAEC3A04CF5ADCFF017D3465FA45EE4A | SHA256:4922A04C4C88DAA3ECE6DA0845957F73AEE8BF373A86A66FF47DD914D2CD7A6E | |||
| 2424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2424.48404\Ardamax Keylogger\SUS.02 | executable | |
MD5:DAD4D733FBC7BB35C39BE08F922A95BD | SHA256:D6A5D6DE4BE7D8C6E5649FF58479D34BC833F5443B63B9AF7C2DE89ADF4A3D29 | |||
| 2424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2424.48404\Ardamax Keylogger\Uninstall.exe | executable | |
MD5:79354FC5E77FC7B3EC10089C99C897D6 | SHA256:87ADB0D696CB0E3A3010FE2B3C85620E162AC636669A698D66D37151CE18F299 | |||
| 2424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2424.48404\Ardamax Keylogger\ardamax.keylogger.4.0-patch.exe | executable | |
MD5:0E9BBF3419EFD1D9BE9A405F4F65AE5B | SHA256:DD2B0A0AD91EC54C644ACC338074F3B8A8CEA431A2F8F9EC14B5BEED65E1BAA3 | |||
| 2424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2424.48404\Ardamax Keylogger\SUS.exe | executable | |
MD5:3710BDB7E3BA37A6773E2F9920BB0D94 | SHA256:4CAD85CE83720349FA63DB46C3D741CD0C250E8C57E32FDD0C31C48E241F4C4F | |||
| 2424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2424.48404\Ardamax Keylogger\AKV.00 | binary | |
MD5:C832CBAF644D8ED3541CB8BBBB83AAEE | SHA256:5D697758BE97F37929931CEF04E7F0CF8A9C16C8F8A80AEEBA6855C1EDE96E41 | |||
| 2424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2424.48404\Ardamax Keylogger\SUS.01 | executable | |
MD5:8942289FE2D65D66FB8BBBD8F5F1BD5B | SHA256:7CE1A145642EDF185FBABB5852F779A4968A21EEAEBDBAC11AB714561A259FF1 | |||
| 3876 | SUS.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Ardamax Keylogger 4.0\Ardamax Keylogger 4.0.lnk | binary | |
MD5:B73F00A3D42E9D90E88A22BED7894176 | SHA256:A8649D7932CBA19BB3EFAFD3346A6C4A87932FD3FFB20CB8A2B8AB4F68AAFE09 | |||
| 2424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2424.48404\Ardamax Keylogger\SUS.exe.BAK | executable | |
MD5:8B219B16188A4D83AFAD19B2AD473A89 | SHA256:3B6580F41F195B493B6E435CBC95C78F96185BF3060A448AF7F9F1E82B9B32A9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |