analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
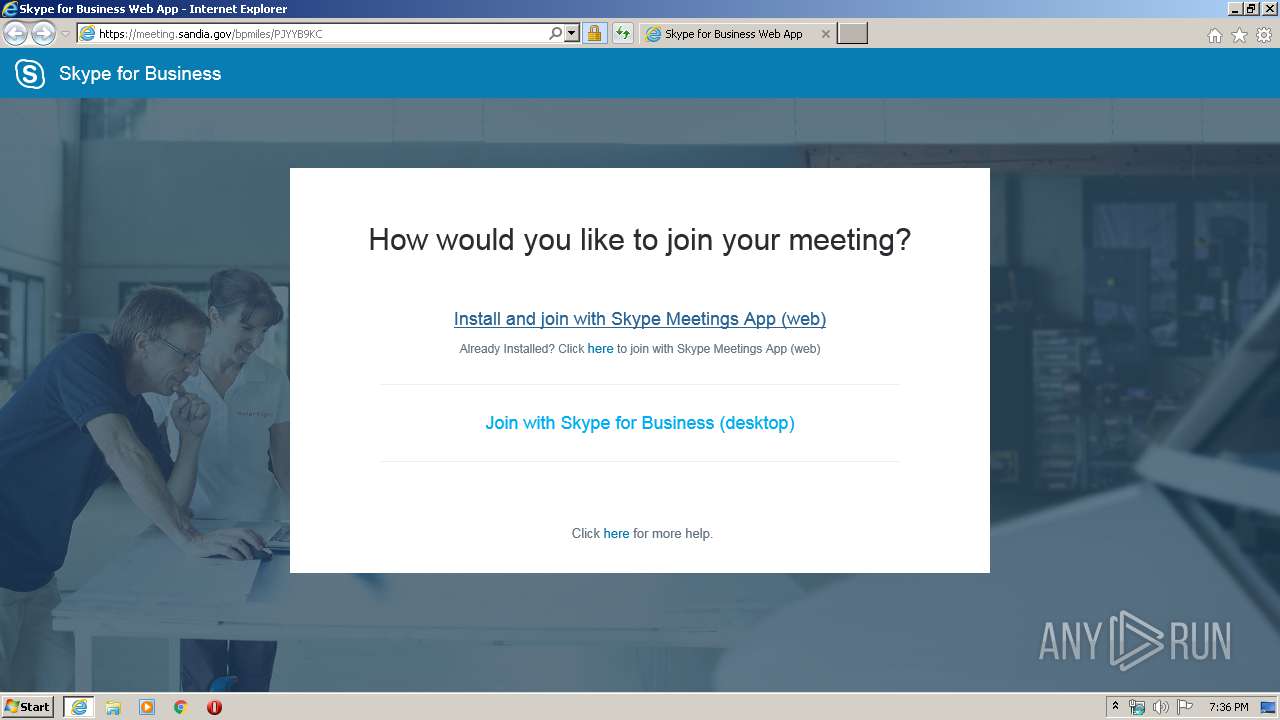
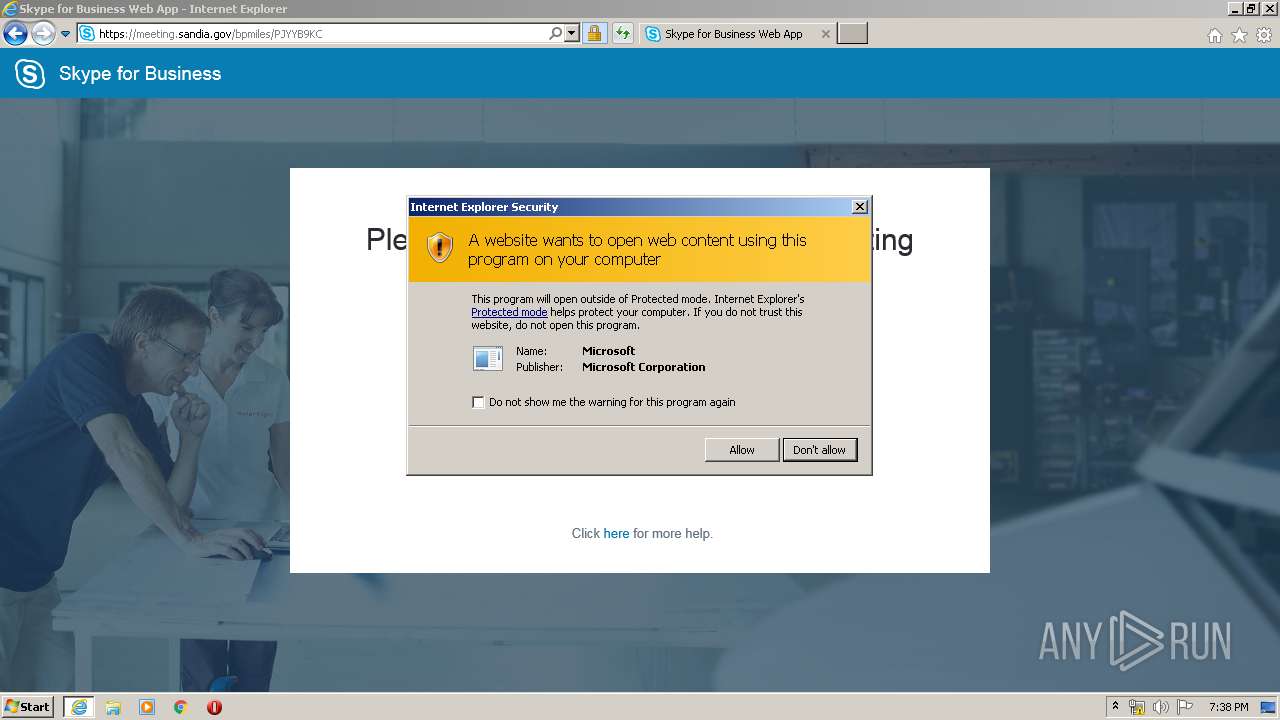
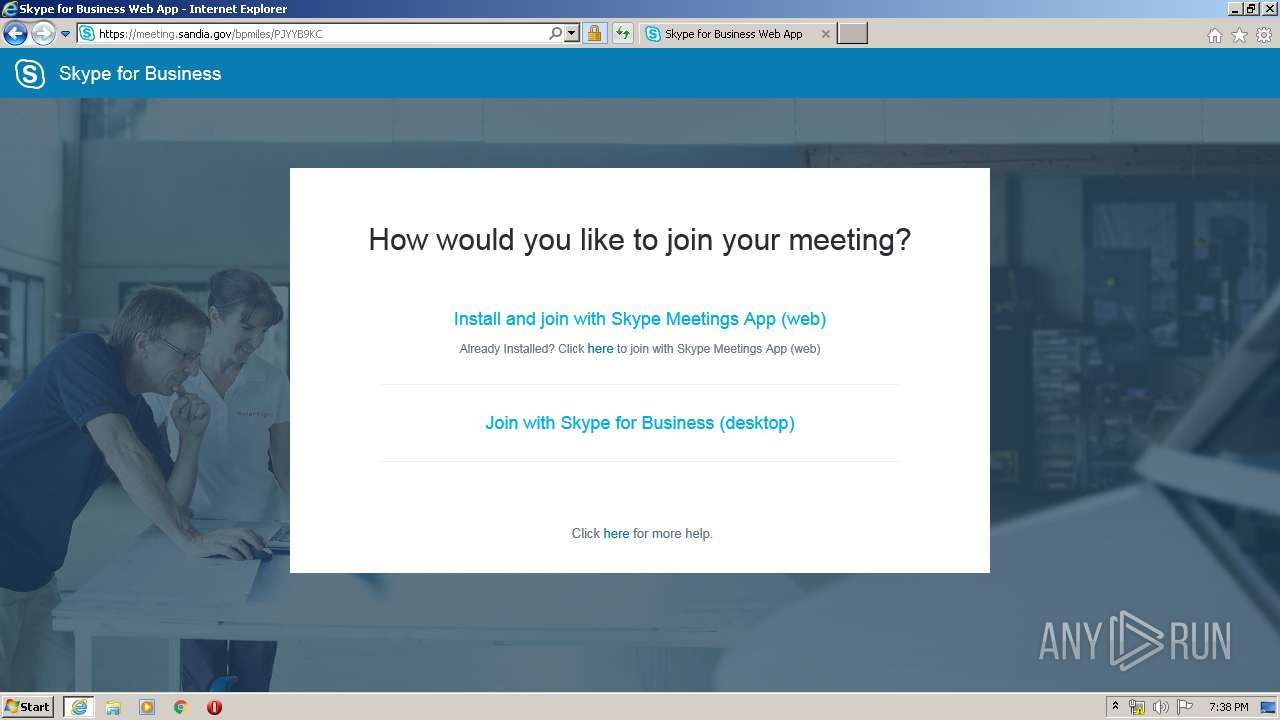
| URL: | https://meeting.sandia.gov/bpmiles/PJYYB9KC |
| Full analysis: | https://app.any.run/tasks/9fcc302c-fdfe-4f58-9936-94e1171bd668 |
| Verdict: | Malicious activity |
| Analysis date: | March 30, 2020, 18:35:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 7740306DA8F0A3EBCC34DC6C7C0213B0 |
| SHA1: | 8648D4BF079C09E263A2EE0145113250A5D0CDF9 |
| SHA256: | B9824FBB31A48940133146E99800A6F2B86B1FACBACC50FFD24005BBC70D651E |
| SSDEEP: | 3:N81iFtGBgVcpn:21ctGBgon |
MALICIOUS
Loads dropped or rewritten executable
- Skype Meetings App.exe (PID: 3100)
- GatewayVersion.exe (PID: 3596)
- Skype Meetings App.exe (PID: 3632)
- GatewayVersion.exe (PID: 1492)
- Skype Meetings App.exe (PID: 2276)
- PluginHost.exe (PID: 1332)
Application was dropped or rewritten from another process
- Skype Meetings App.exe (PID: 3100)
- Skype Meetings App.exe (PID: 3300)
- GatewayVersion.exe (PID: 3596)
- Skype Meetings App.exe (PID: 3632)
- GatewayVersion.exe (PID: 1492)
- Skype Meetings App.exe (PID: 3968)
- Skype Meetings App.exe (PID: 2276)
- PluginHost.exe (PID: 1332)
Changes settings of System certificates
- PluginHost.exe (PID: 1332)
SUSPICIOUS
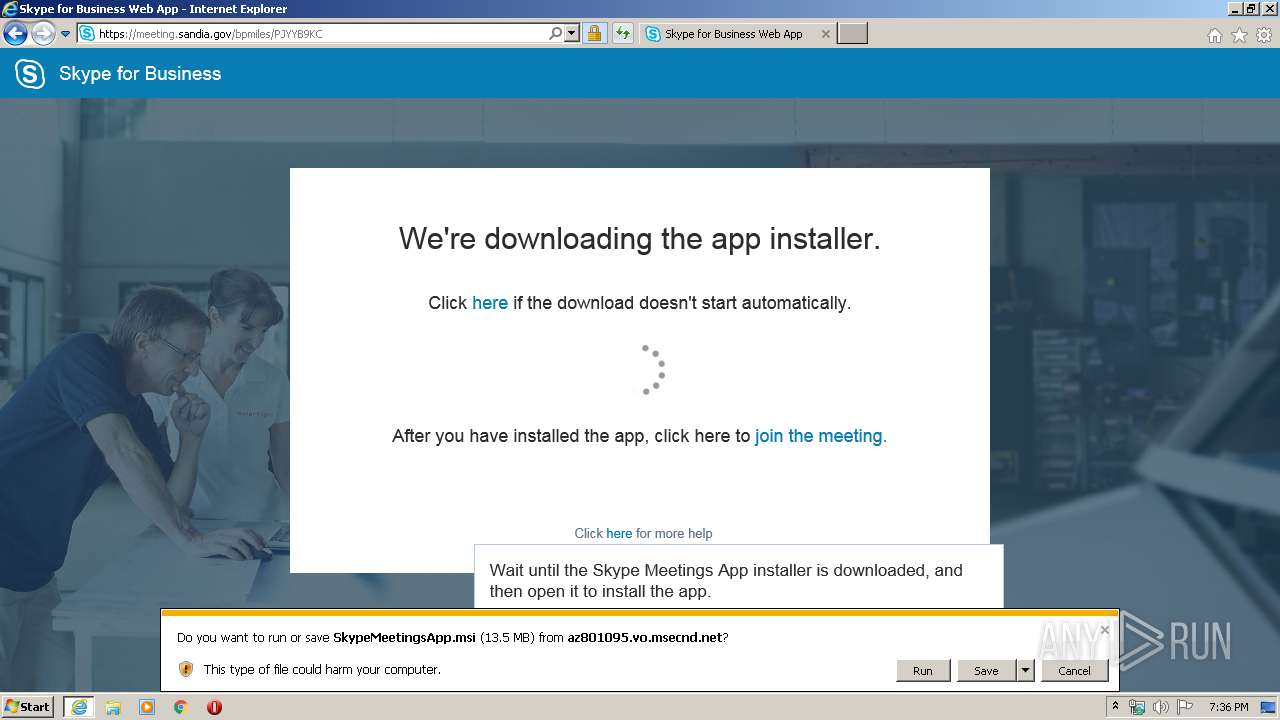
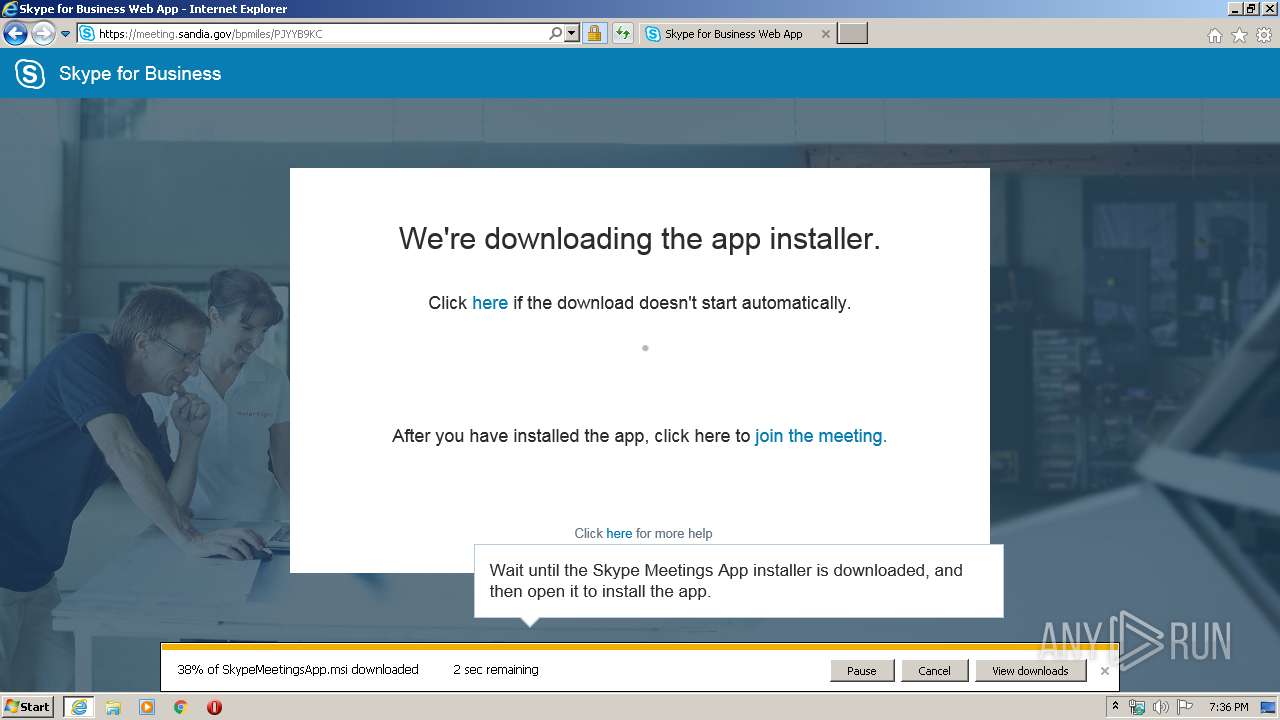
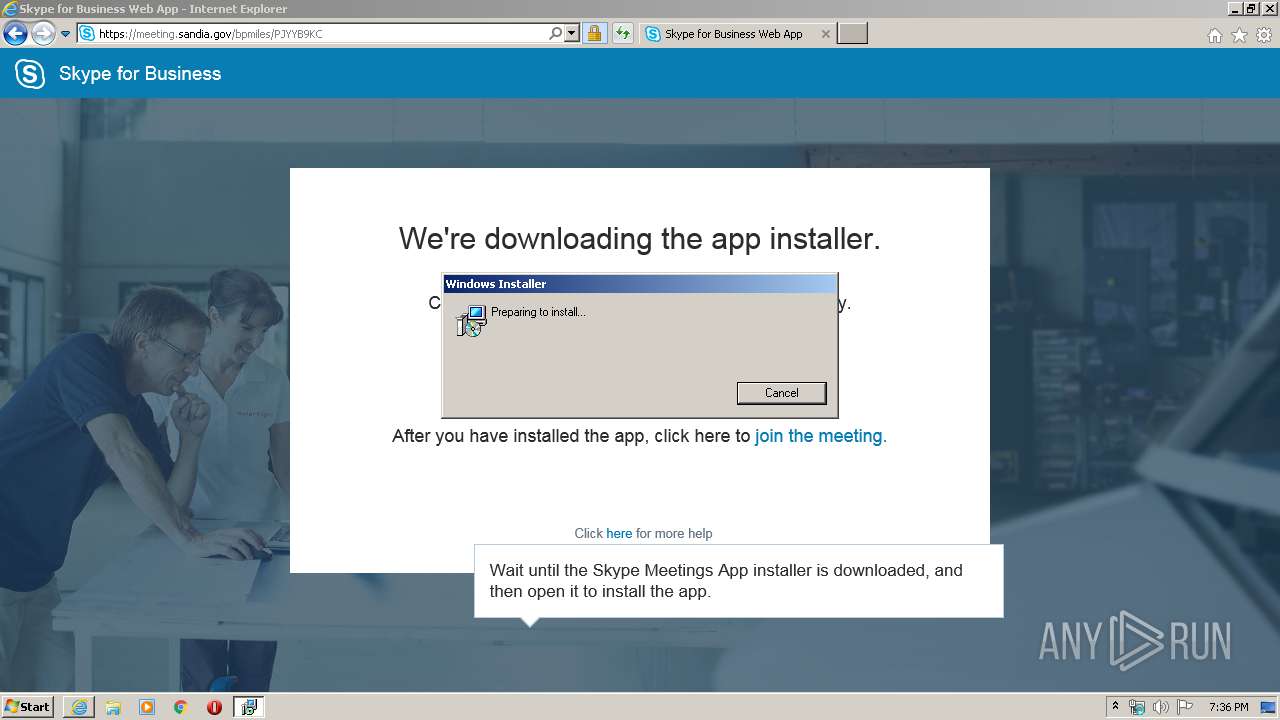
Starts Microsoft Installer
- iexplore.exe (PID: 3736)
Executable content was dropped or overwritten
- msiexec.exe (PID: 820)
Reads Internet Cache Settings
- Skype Meetings App.exe (PID: 3100)
- Skype Meetings App.exe (PID: 3632)
- Skype Meetings App.exe (PID: 2276)
- PluginHost.exe (PID: 1332)
Executed via COM
- GatewayVersion.exe (PID: 3596)
- GatewayVersion.exe (PID: 1492)
- PluginHost.exe (PID: 1332)
Creates files in the user directory
- msiexec.exe (PID: 820)
- Skype Meetings App.exe (PID: 3632)
- PluginHost.exe (PID: 1332)
- Skype Meetings App.exe (PID: 2276)
Modifies the open verb of a shell class
- msiexec.exe (PID: 820)
Creates COM task schedule object
- msiexec.exe (PID: 820)
Reads internet explorer settings
- Skype Meetings App.exe (PID: 3632)
- Skype Meetings App.exe (PID: 2276)
Connects to unusual port
- PluginHost.exe (PID: 1332)
Adds / modifies Windows certificates
- PluginHost.exe (PID: 1332)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 3736)
- iexplore.exe (PID: 4060)
Changes internet zones settings
- iexplore.exe (PID: 3736)
Application launched itself
- msiexec.exe (PID: 820)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3736)
Reads internet explorer settings
- iexplore.exe (PID: 4060)
Creates files in the user directory
- iexplore.exe (PID: 4060)
- iexplore.exe (PID: 3736)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 2760)
Creates a software uninstall entry
- msiexec.exe (PID: 820)
Reads settings of System Certificates
- Skype Meetings App.exe (PID: 3632)
- iexplore.exe (PID: 4060)
- PluginHost.exe (PID: 1332)
- iexplore.exe (PID: 3736)
- Skype Meetings App.exe (PID: 2276)
Dropped object may contain Bitcoin addresses
- Skype Meetings App.exe (PID: 3100)
- PluginHost.exe (PID: 1332)
- Skype Meetings App.exe (PID: 2276)
Changes settings of System certificates
- iexplore.exe (PID: 3736)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3736)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
52
Monitored processes
13
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 3736 | "C:\Program Files\Internet Explorer\iexplore.exe" https://meeting.sandia.gov/bpmiles/PJYYB9KC | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | ||||
| 4060 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3736 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | ||||
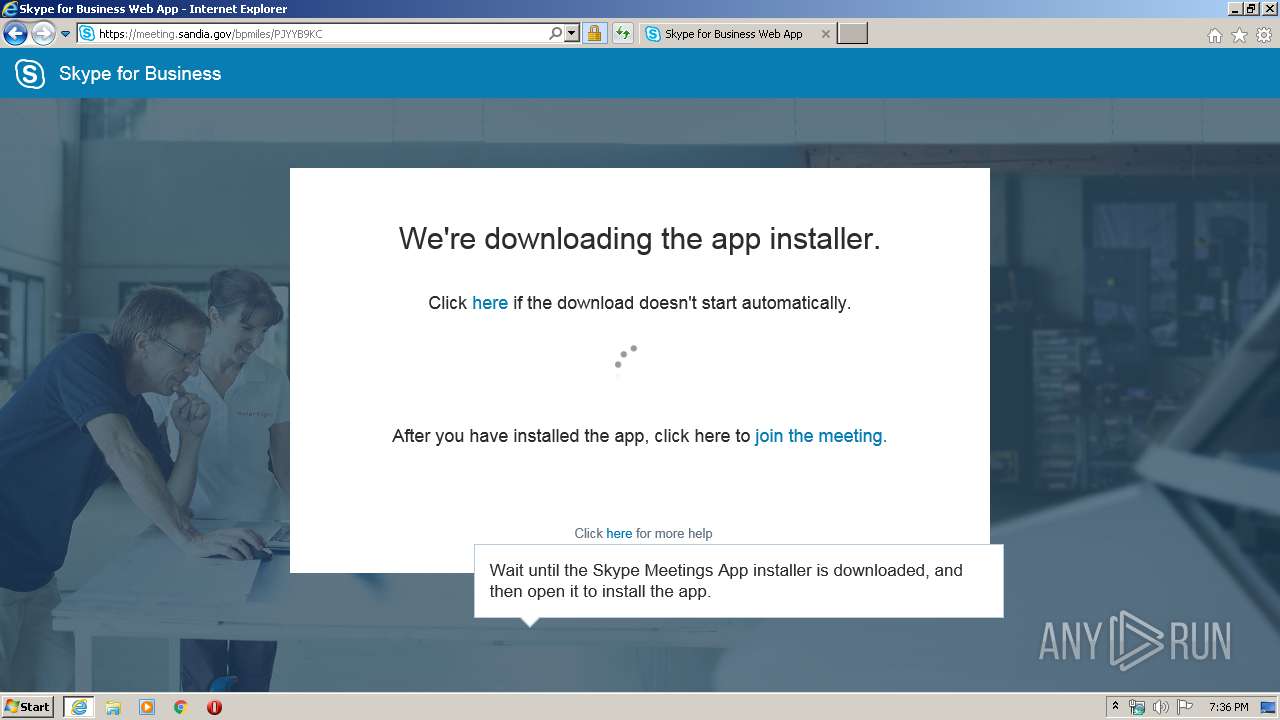
| 2376 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\SkypeMeetingsApp.msi" | C:\Windows\System32\msiexec.exe | — | iexplore.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) | ||||
| 820 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.7600.16385 (win7_rtm.090713-1255) | ||||
| 2760 | C:\Windows\system32\MsiExec.exe -Embedding CE5681AA0EE8A7DC278E34AA5E9F86BA | C:\Windows\system32\MsiExec.exe | msiexec.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) | ||||
| 3100 | "C:\Users\admin\AppData\Local\Microsoft\SkypeForBusinessPlugin\16.2.0.511\Skype Meetings App.exe" -autostart | C:\Users\admin\AppData\Local\Microsoft\SkypeForBusinessPlugin\16.2.0.511\Skype Meetings App.exe | msiexec.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Skype Meetings App Exit code: 0 Version: 16.2.0.511 | ||||
| 3596 | C:\Users\admin\AppData\Local\Microsoft\SkypeForBusinessPlugin\16.2.0.511\GatewayVersion.exe -Embedding | C:\Users\admin\AppData\Local\Microsoft\SkypeForBusinessPlugin\16.2.0.511\GatewayVersion.exe | — | svchost.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Skype for Business Web App Version Plug-in Exit code: 0 Version: 16.2.0.511 | ||||
| 3300 | "C:\Users\admin\AppData\Local\Microsoft\SkypeForBusinessPlugin\16.2.0.511\Skype Meetings App.exe" sfb:https://lync13-ext.sandia.gov/lwa/tgt-f848e9e2498759518eb384f631ad1083/WebPages/LwaClient.aspx?legacy=RmFsc2U!&meeturl=aHR0cHM6Ly9seW5jMTMtZXh0LnNhbmRpYS5nb3YvTWVldC8_b3JpZ3VybD1hSFIwY0hNNkx5OXRaV1YwYVc1bkxuTmhibVJwWVM1bmIzWXZZbkJ0YVd4bGN5OVFTbGxaUWpsTFF3ISE!&wk=2&telemetryid=b8d5d9a4-bb88-4cdb-8615-5b30da51d008&enabletelem=true&browser=MSIE&JLversion=1.31&pagename=Download | C:\Users\admin\AppData\Local\Microsoft\SkypeForBusinessPlugin\16.2.0.511\Skype Meetings App.exe | — | iexplore.exe |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Skype Meetings App Exit code: 0 Version: 16.2.0.511 | ||||
| 3632 | "C:\Users\admin\AppData\Local\Microsoft\SkypeForBusinessPlugin\16.2.0.511\Skype Meetings App.exe" sfb:https://lync13-ext.sandia.gov/lwa/tgt-f848e9e2498759518eb384f631ad1083/WebPages/LwaClient.aspx?legacy=RmFsc2U!&meeturl=aHR0cHM6Ly9seW5jMTMtZXh0LnNhbmRpYS5nb3YvTWVldC8_b3JpZ3VybD1hSFIwY0hNNkx5OXRaV1YwYVc1bkxuTmhibVJwWVM1bmIzWXZZbkJ0YVd4bGN5OVFTbGxaUWpsTFF3ISE!&wk=2&telemetryid=b8d5d9a4-bb88-4cdb-8615-5b30da51d008&enabletelem=true&browser=MSIE&JLversion=1.31&pagename=Download | C:\Users\admin\AppData\Local\Microsoft\SkypeForBusinessPlugin\16.2.0.511\Skype Meetings App.exe | iexplore.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Skype Meetings App Exit code: 3489660927 Version: 16.2.0.511 | ||||
| 1492 | C:\Users\admin\AppData\Local\Microsoft\SkypeForBusinessPlugin\16.2.0.511\GatewayVersion.exe -Embedding | C:\Users\admin\AppData\Local\Microsoft\SkypeForBusinessPlugin\16.2.0.511\GatewayVersion.exe | — | svchost.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Skype for Business Web App Version Plug-in Version: 16.2.0.511 | ||||
Total events
11 132
Read events
3 103
Write events
0
Delete events
0
Modification events
Executable files
82
Suspicious files
1 634
Text files
106
Unknown types
29
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3736 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 4060 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabBD5D.tmp | — | |
MD5:— | SHA256:— | |||
| 4060 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarBD5E.tmp | — | |
MD5:— | SHA256:— | |||
| 4060 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\5457A8CE4B2A7499F8299A013B6E1C7C_CE50F893881D43DC0C815E4D80FAF2B4 | binary | |
MD5:B9FE226913520BF1CFFEA9F46DCE80E2 | SHA256:56D3B19F02B59B153E86A2B7B4F802ECAB45C8D86567C3347D4AA870BCB574AF | |||
| 4060 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\5080DC7A65DB6A5960ECD874088F3328_2908F682DFC81A793BD240CF29711C77 | binary | |
MD5:D1CD052BA7468DC92DE00BDAA7A2A16C | SHA256:220B9470BD46B992DE642B6F4AE0990DBB206BDB4CA2C65FD72E3BE9B52D3D52 | |||
| 4060 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\024823B39FBEACCDB5C06426A8168E99_2A5EBC23AAC269FC1AACD6E1DAE215F4 | binary | |
MD5:52BFCEEFD773882E0CA6DEE07CC65BDD | SHA256:02350CB4B6E6F4F4DB6E7BFC47A15265ED93C45532D569A46B1118B12E612FD5 | |||
| 4060 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\024823B39FBEACCDB5C06426A8168E99_2A5EBC23AAC269FC1AACD6E1DAE215F4 | der | |
MD5:1ADA582A9FA41B46ED8DB4957124E52F | SHA256:BB048372F6F65C29A669B5970AFFFA5E4D2C1C6EF7B52311EA49855EF71CFD61 | |||
| 4060 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\5457A8CE4B2A7499F8299A013B6E1C7C_CE50F893881D43DC0C815E4D80FAF2B4 | der | |
MD5:8E7D3EFB01313E3007F38BE1219E1751 | SHA256:9E61938AFB6497D6FE9AE1AC66A919A85D92A6DB6C7762E8FB572A49A7B6A6A5 | |||
| 4060 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\5080DC7A65DB6A5960ECD874088F3328_2908F682DFC81A793BD240CF29711C77 | der | |
MD5:DFC08454E76E8CEE89392B13F50CB84C | SHA256:F058CFA174E4B63F151C09C59179B633679B1F43A65B0D8175860D561D5AC8C4 | |||
| 4060 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\app[1].css | text | |
MD5:6BFAE63A089D609CD97E1E39DE6D7B78 | SHA256:052508CBB7EB6CCE70E9456473E5B6818478E3D7CB5A8D6DE79C472947DDAC08 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
80
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4060 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCECdm7lbrSfOOq9dwovyE3iI%3D | US | der | 471 b | whitelisted |
4060 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
4060 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQLqIKj6Gi5thHaqKC1ECU9aXsCRQQUmvMr2s%2BtT7YvuypISCoStxtCwSQCEEVptF5%2BsbpTePrgQ%2FMYmi0%3D | US | der | 471 b | whitelisted |
4060 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQLqIKj6Gi5thHaqKC1ECU9aXsCRQQUmvMr2s%2BtT7YvuypISCoStxtCwSQCEEVptF5%2BsbpTePrgQ%2FMYmi0%3D | US | der | 471 b | whitelisted |
4060 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCECdm7lbrSfOOq9dwovyE3iI%3D | US | der | 471 b | whitelisted |
4060 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36pvE8hI6t7jiY7NkyMtQCEDaCXn%2B1pIGTfvbRc2u5PKY%3D | US | der | 727 b | whitelisted |
4060 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36pvE8hI6t7jiY7NkyMtQCEDaCXn%2B1pIGTfvbRc2u5PKY%3D | US | der | 727 b | whitelisted |
3736 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
4060 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
3632 | Skype Meetings App.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAiIzVJfGSRETRSlgpHeuVI%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4060 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3736 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
4060 | iexplore.exe | 198.102.154.15:443 | meeting.sandia.gov | Sandia National Laboratories | US | unknown |
4060 | iexplore.exe | 151.139.128.14:80 | ocsp.usertrust.com | Highwinds Network Group, Inc. | US | suspicious |
4060 | iexplore.exe | 52.114.76.35:443 | browser.pipe.aria.microsoft.com | Microsoft Corporation | IE | whitelisted |
4060 | iexplore.exe | 198.102.154.14:443 | lync13-ext.sandia.gov | Sandia National Laboratories | US | unknown |
3736 | iexplore.exe | 198.102.154.15:443 | meeting.sandia.gov | Sandia National Laboratories | US | unknown |
4060 | iexplore.exe | 152.199.19.160:443 | meetings.sfbassets.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3736 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3100 | Skype Meetings App.exe | 52.114.7.36:443 | mobile.pipe.aria.microsoft.com | Microsoft Corporation | HK | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
meeting.sandia.gov |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
meetings.sfbassets.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
lync13-ext.sandia.gov |
| unknown |
iecvlist.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Skype Meetings App.exe | 3100, 3376, 2020-03-30 19:36:58.591, TL_INFO, <no file info>, Other, telemetryId:0 |
Skype Meetings App.exe | 3100, 3376, 2020-03-30 19:36:59.638, TL_INFO, <no file info>, Other, Sending App Start Event for JLVersion unknown |
Skype Meetings App.exe | 3100, 3376, 2020-03-30 19:36:59.684, TL_INFO, <no file info>, Other, MSHTML version: 11.0.9600.17842 |
Skype Meetings App.exe | 3100, 3376, 2020-03-30 19:36:59.684, TL_ERROR, <no file info>, Other, Unable to open the key for allowed domains |
Skype Meetings App.exe | 3100, 3376, 2020-03-30 19:36:59.684, TL_ERROR, <no file info>, Other, Unable to open the key for allowed domains |
Skype Meetings App.exe | 3100, 3376, 2020-03-30 19:36:59.684, TL_INFO, <no file info>, Other, Autostart, start new thread and wait for websocket |
Skype Meetings App.exe | 3100, 3484, 2020-03-30 19:36:59.700, TL_INFO, <no file info>, Other, Waiting to accept the connections from client |
Skype Meetings App.exe | 3632, 2348, 2020-03-30 19:37:04.153, TL_INFO, <no file info>, Other, telemetryId:1 |
Skype Meetings App.exe | 3632, 2348, 2020-03-30 19:37:04.153, TL_INFO, <no file info>, Other, telemetryId:b |
Skype Meetings App.exe | 3632, 2348, 2020-03-30 19:37:05.200, TL_INFO, <no file info>, Other, Initiating Browser: M |